Submitted:
18 May 2025
Posted:
19 May 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Materials and Methods
3. Results and Discussion
3.1. Compiling Keyword Lists from Text of Abstracts Using Yake
- YAKE! is an unsupervised keyword extraction method, meaning it does not require any labeled training data or prior knowledge about the text [32].
- YAKE! does not depend on dictionaries, thesauri, or any external linguistic resources [33].
- The method is lightweight and computationally efficient, making it suitable for real-time or large-scale processing of abstracts. In our case, the "YAKE!" task was completed in less than a minute.
- YAKE! can identify both single-word and multi-word keyphrases.
- YAKE! takes into account the context of words and phrases in the text, which allows you to identify meaningful keywords rather than frequently occurring words that may not reflect the meaning of the text.
- YAKE! is implemented both in Python and Rust.
3.2. Compiling Keyword Lists from Text of Abstracts Using KeyphraseVectorizers PatternRank
- The method relies on a set of the most well-known text processing software packages: texts are annotated with part-of-speech tags using spaCy (star 31.3K on GitHub), and KeyBERT (star 3.8K on GitHub) to extract key phrases.
- According to the authors' assertion PatternRank: "texts are annotated with spaCy part-of-speech tags", "Extract grammatically accurate keyphases based on their part-of-speech tags", "The advantage of using KeyphraseVectorizers in addition to KeyBERT is that it allows users to get grammatically correct keyphrases instead of simple n-grams of pre-defined lengths".
- Tests11 conducted by the authors of this package show the best results in comparison with KeyBERT, YAKE (the fastest keyphrase extraction), and SingleRank. TF-IDF, YAKE, RAKE - statistical methods, SingleRank, TextRank - based on graphs, and KeyBERT - deep learning method. Note: the package pytextrank12 was also tested. It has a high rating on GitHub (star 2.2K) [34], which gives good results on texts of several hundred abstracts, but in our case, ~10 thousand abstracts, it worked extremely slowly, the work was interrupted after more than two hours of waiting.
- The KeyphraseVectorizers PatternRank package is arranged so that it picks up keyphrases for each of the abstracts. This is useful for later use in programs such as VOSviewer. The results can be interpreted as index keywords.
- On a computer with 8-core AMD Ryzen 7 5700G; 32 GB RAM, KeyphraseVectorizer PatternRank processing of the collected abstract texts was completed in 20-25 minutes.
3.3. Some Characteristics of Keywords/Keyphrases
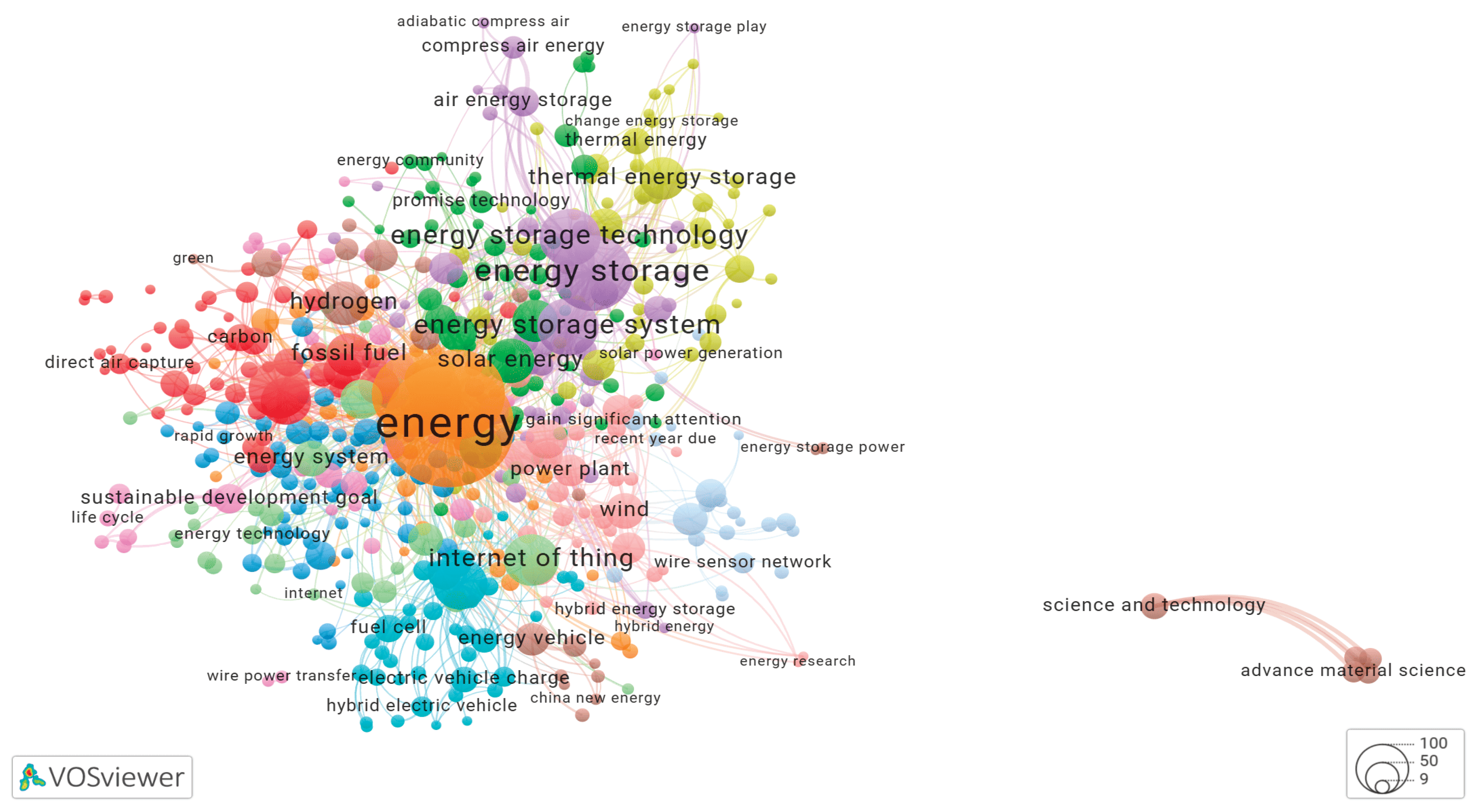
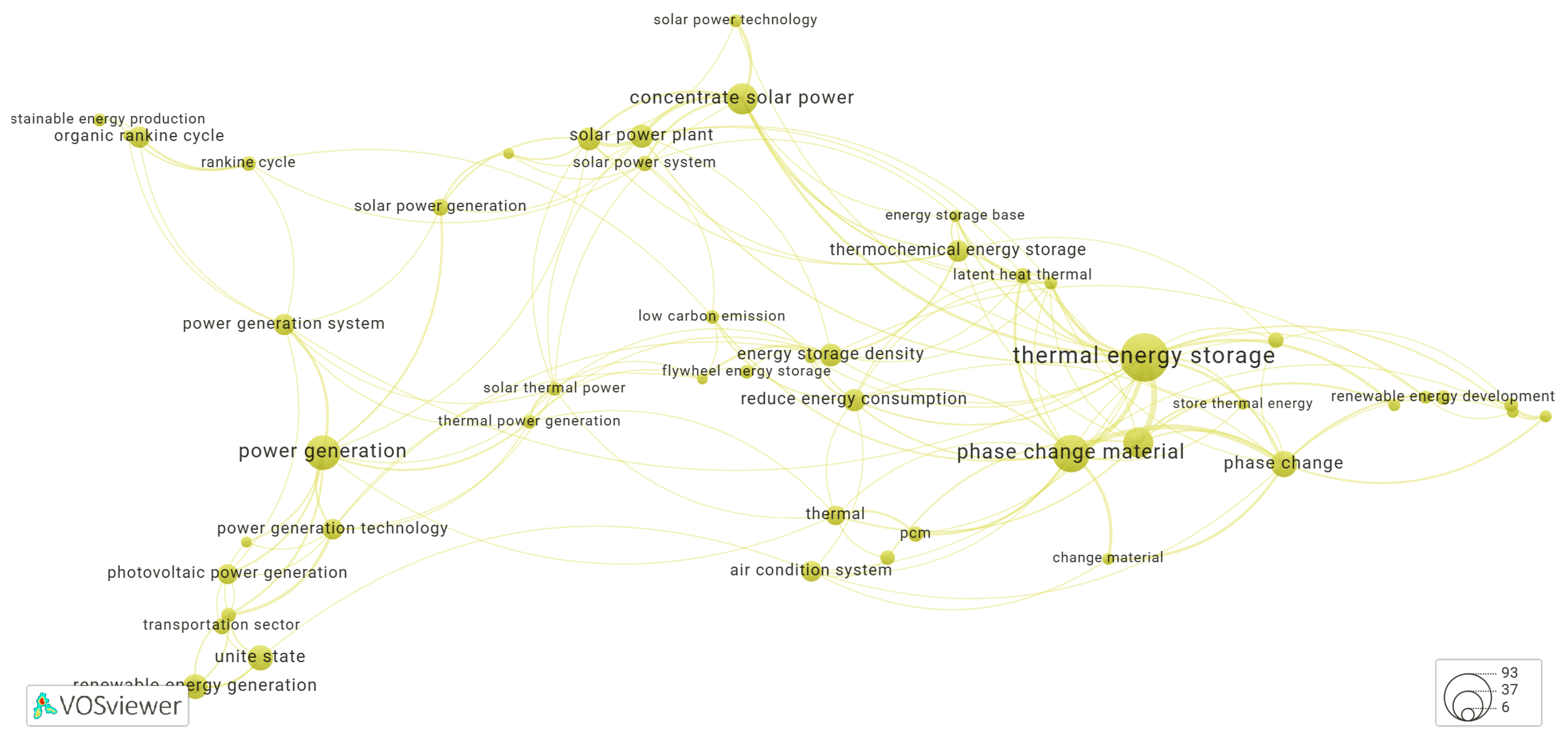
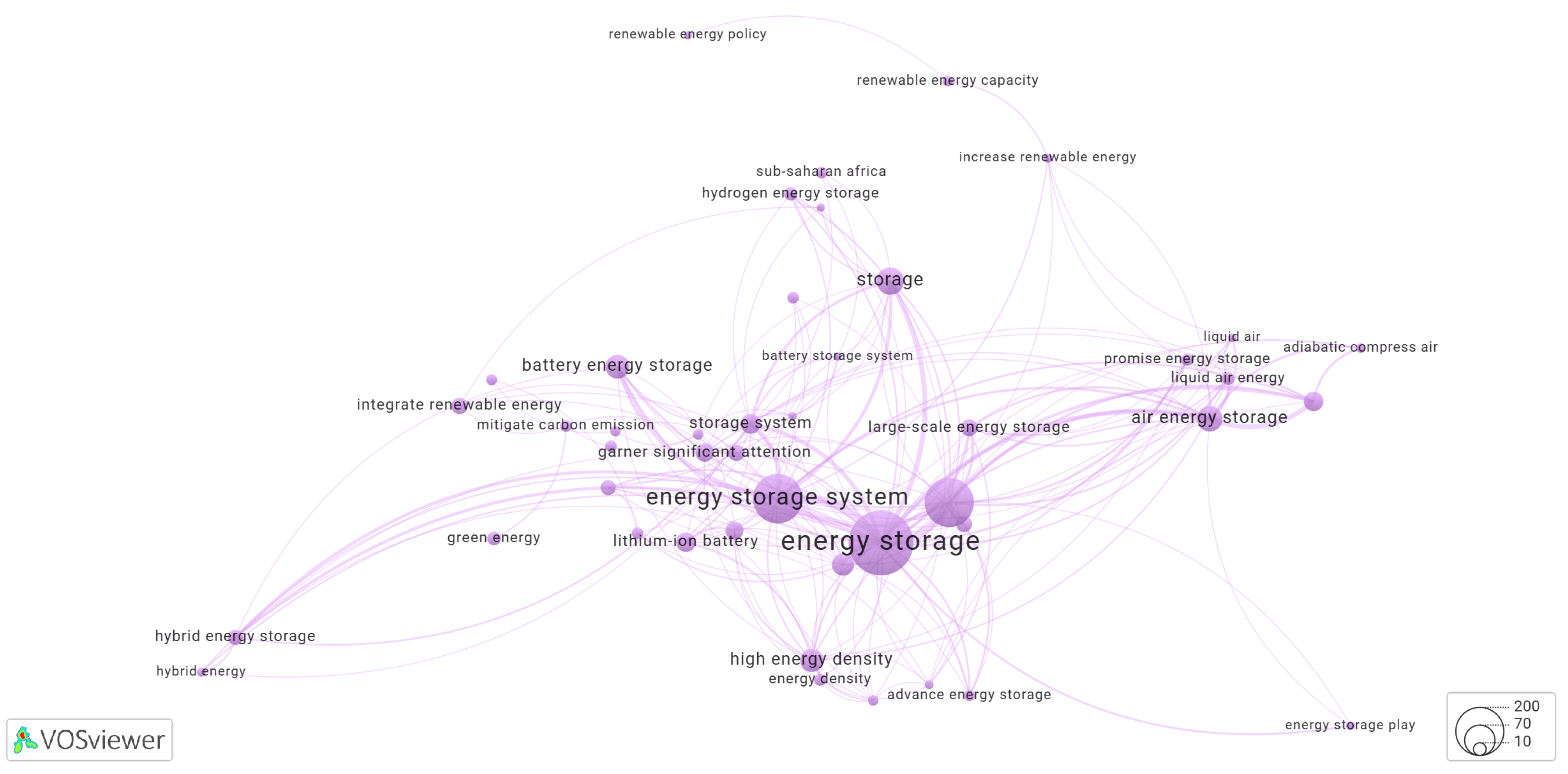
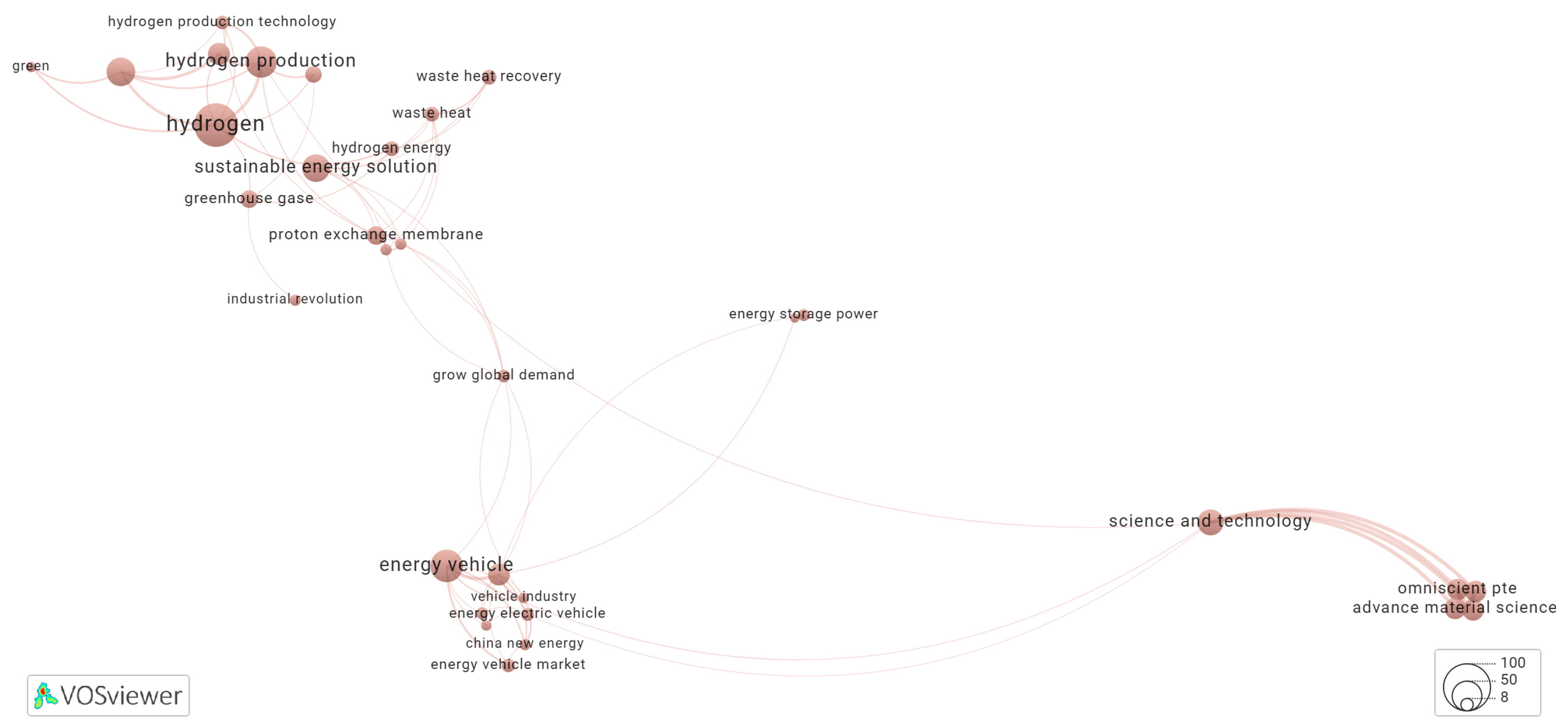
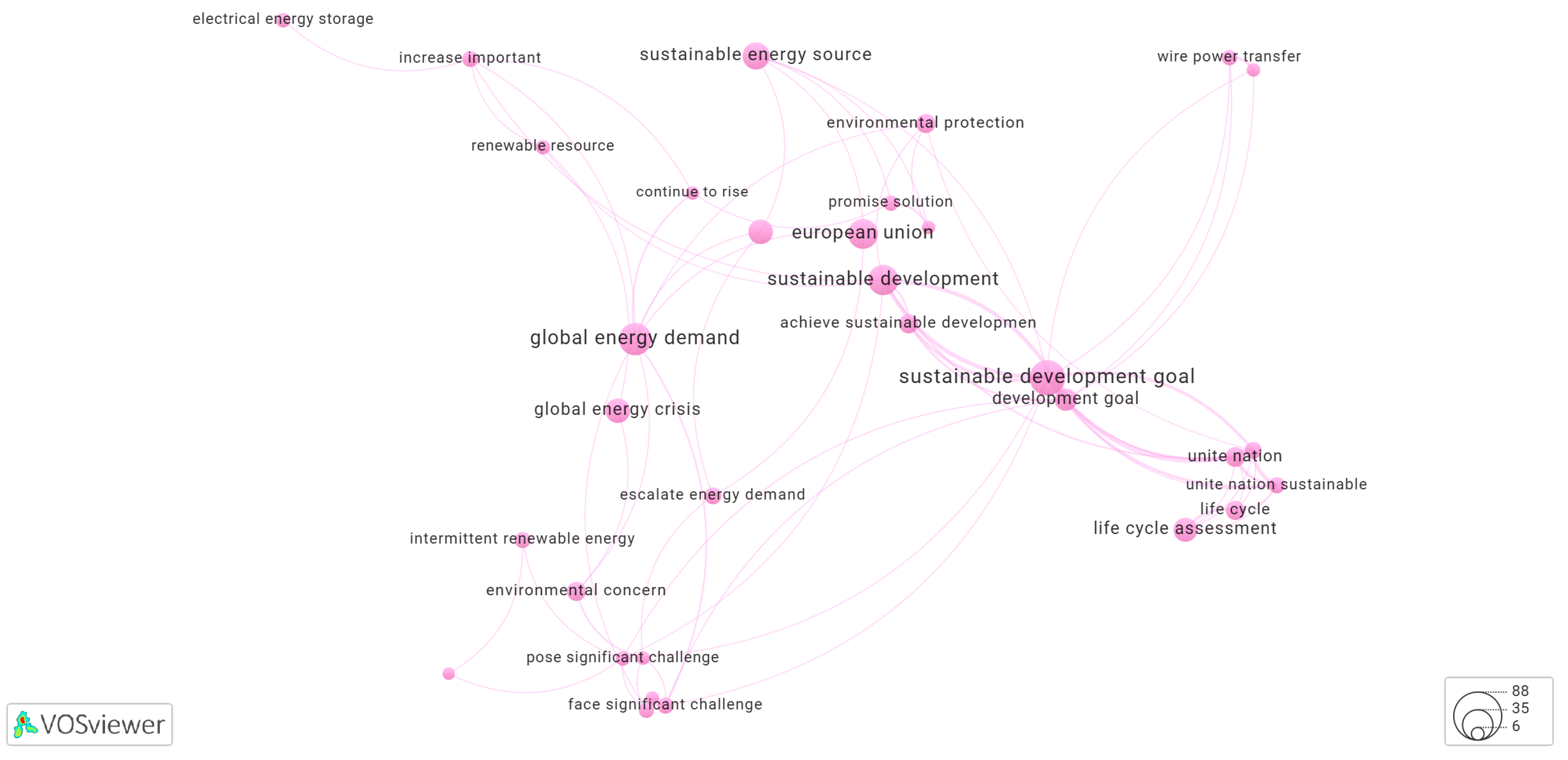
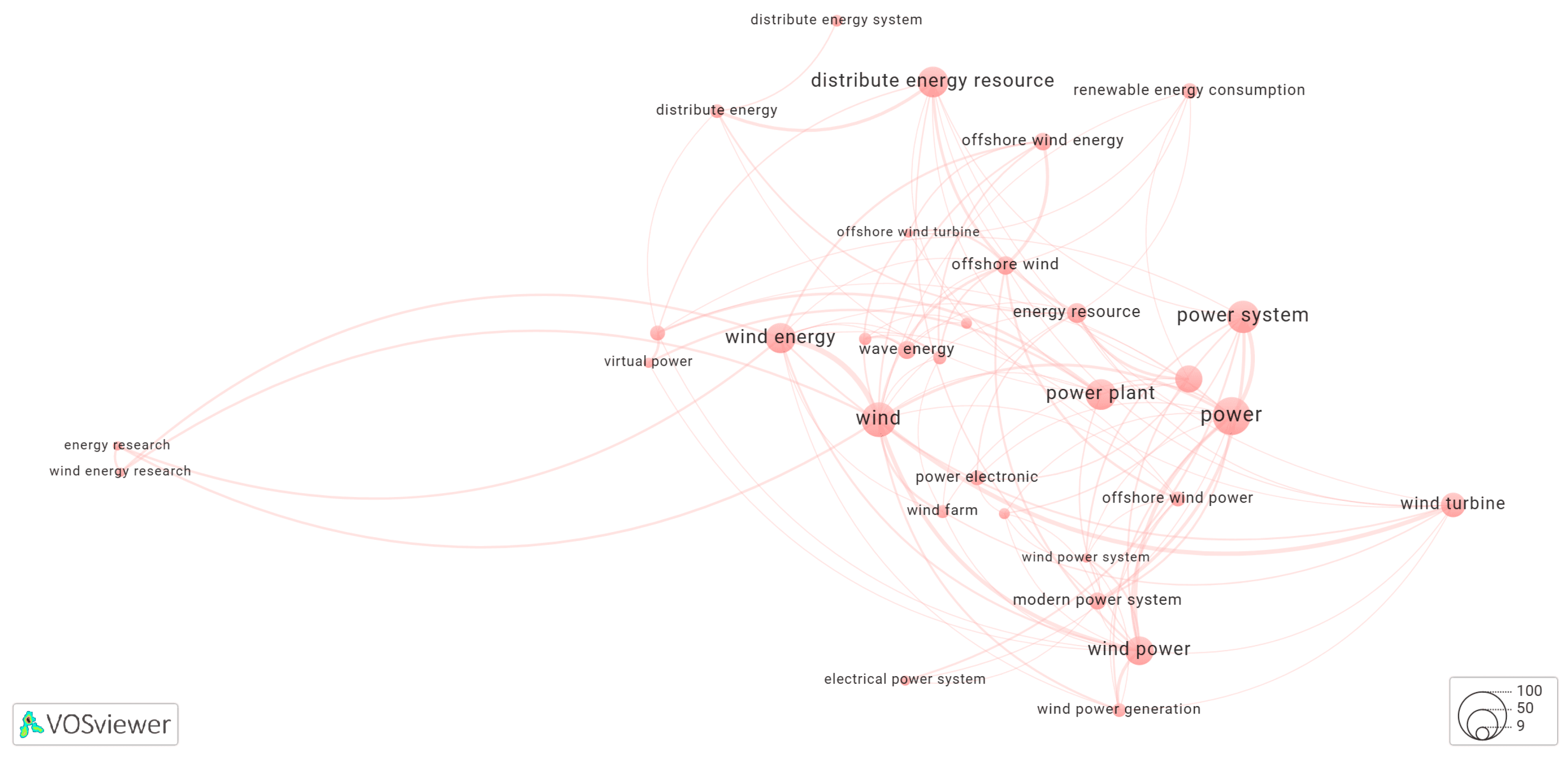
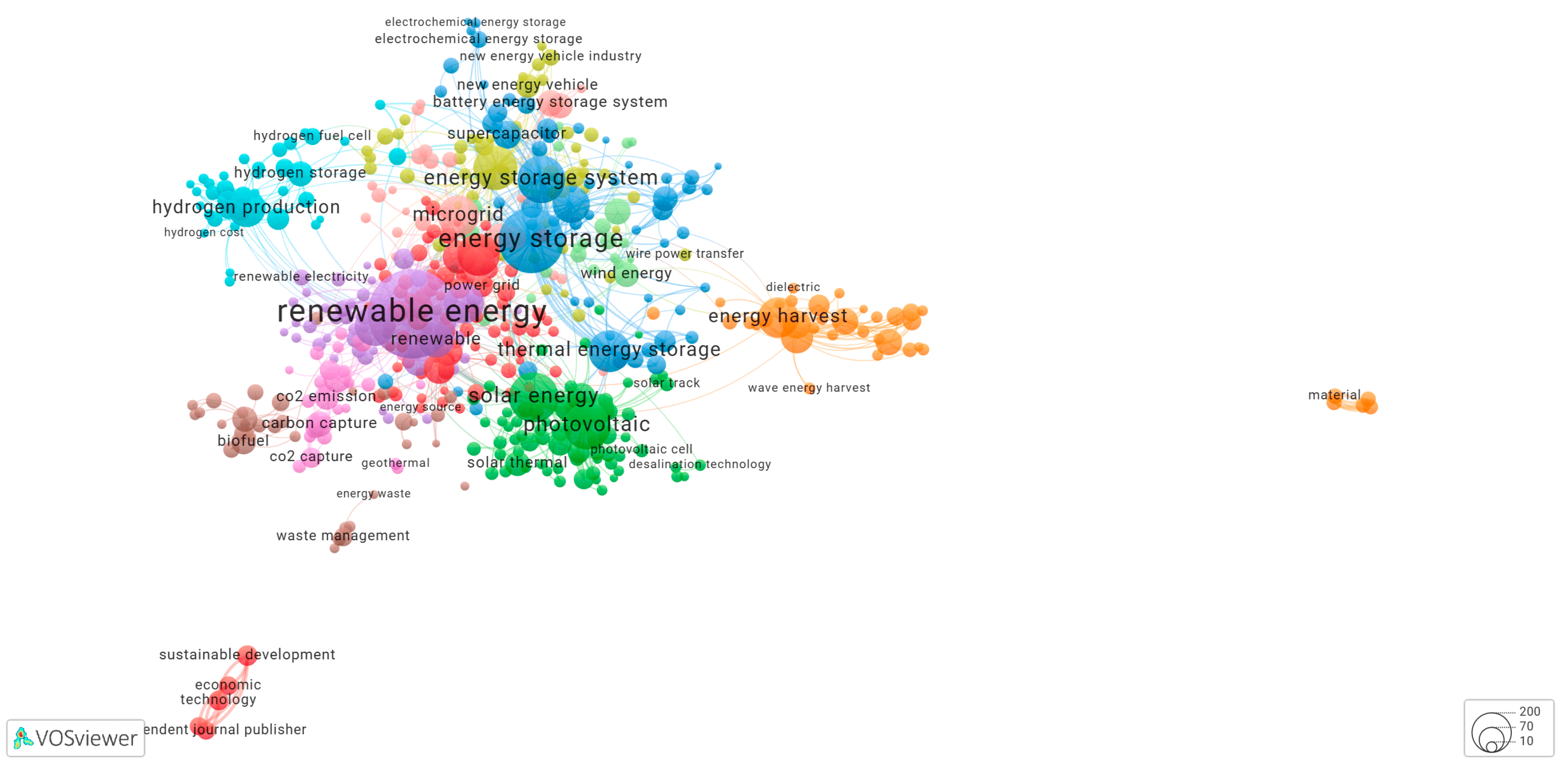
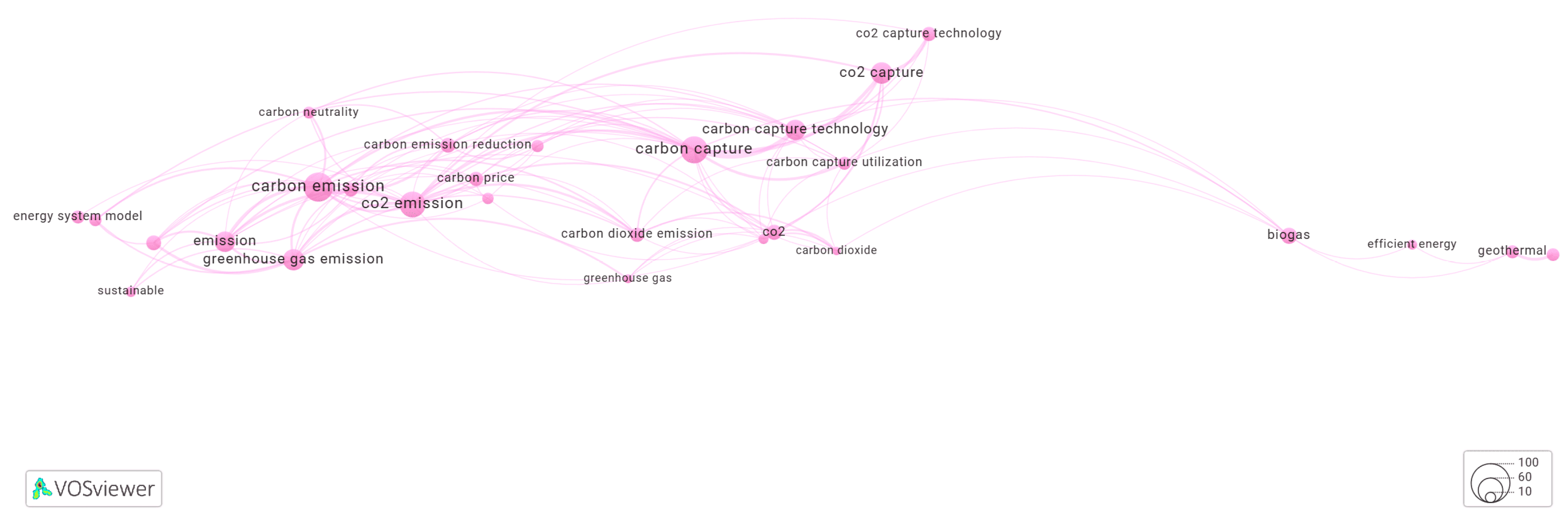
3.4. Keyword Co-Occurrence Networks Generated by Yake! Algorithm
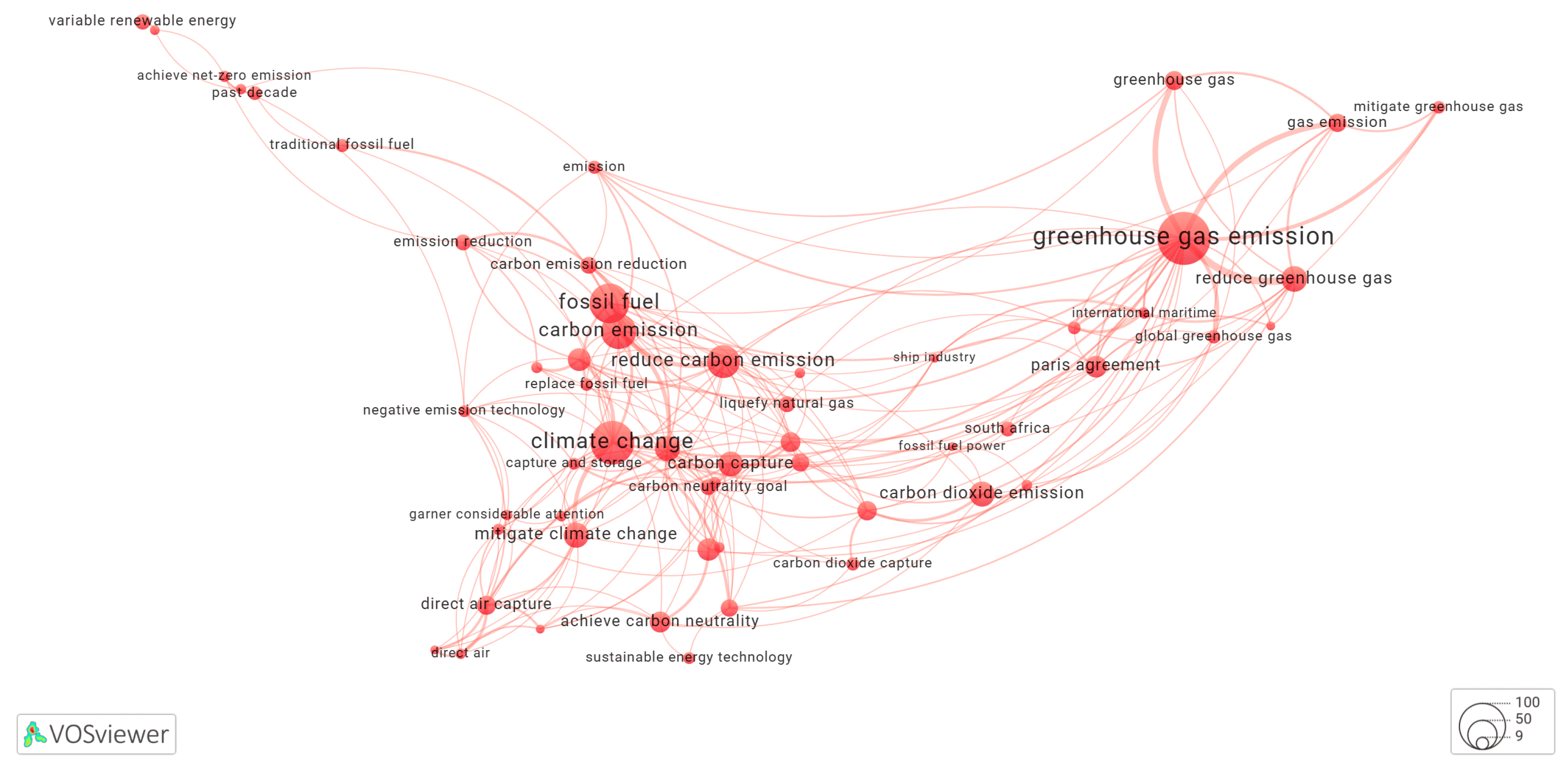
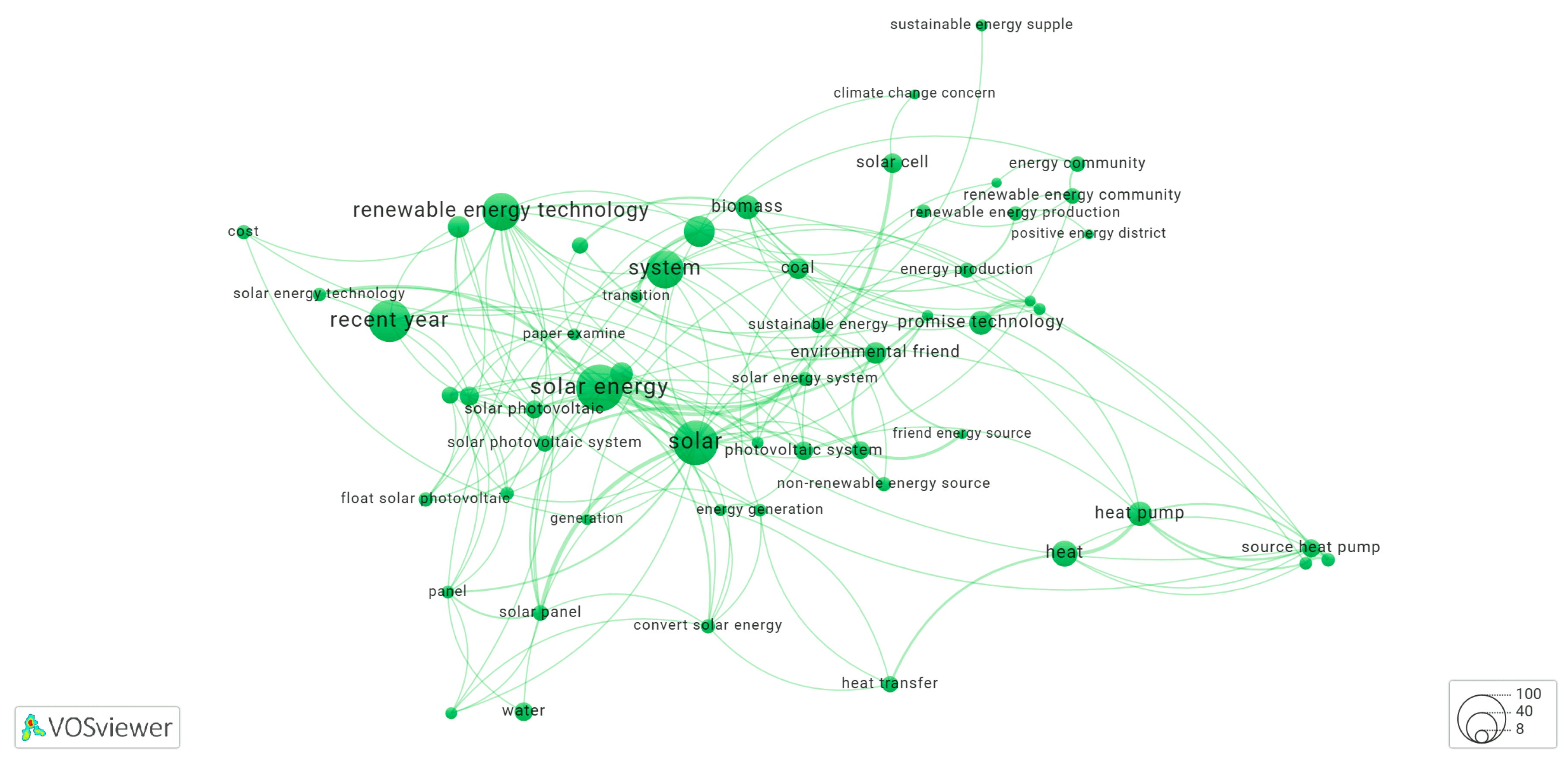
3.5. Clusters of the Keyword Co-Occurrence Network Identified by Yake-Rust
3.5.1. Cluster-1 of Network Shown in Figure 1
3.5.2. Cluster-2 of Network Shown in Figure 1
3.5.3. Cluster-3 of Network Shown in Figure 1
3.5.4. Cluster-4 of Network Shown in Figure 1
3.5.5. Cluster-5 of Network Shown in Figure 1
3.5.6. Cluster-6 of Network Shown in Figure 1
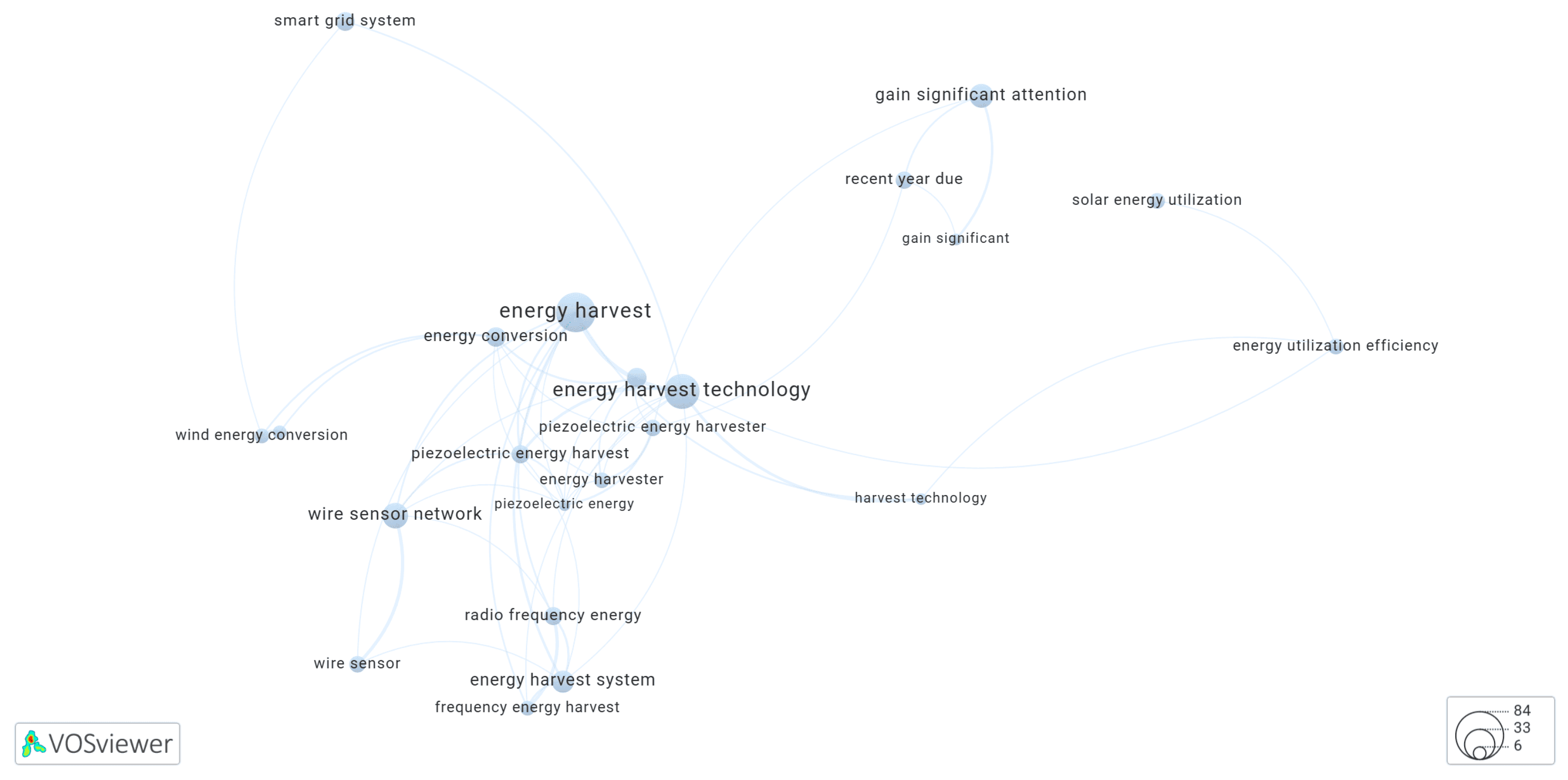
3.5.7. Cluster-7 of Network Shown in Figure 1
3.5.8. Cluster-8 of Network Shown in Figure 1
3.5.9. Cluster-9 of Network Shown in Figure 1
3.5.10. Cluster-10 of Network Shown in Figure 1
3.5.11. Cluster-11 of Network Shown in Figure 1
3.5.12. Cluster-12 of Network Shown in Figure 1
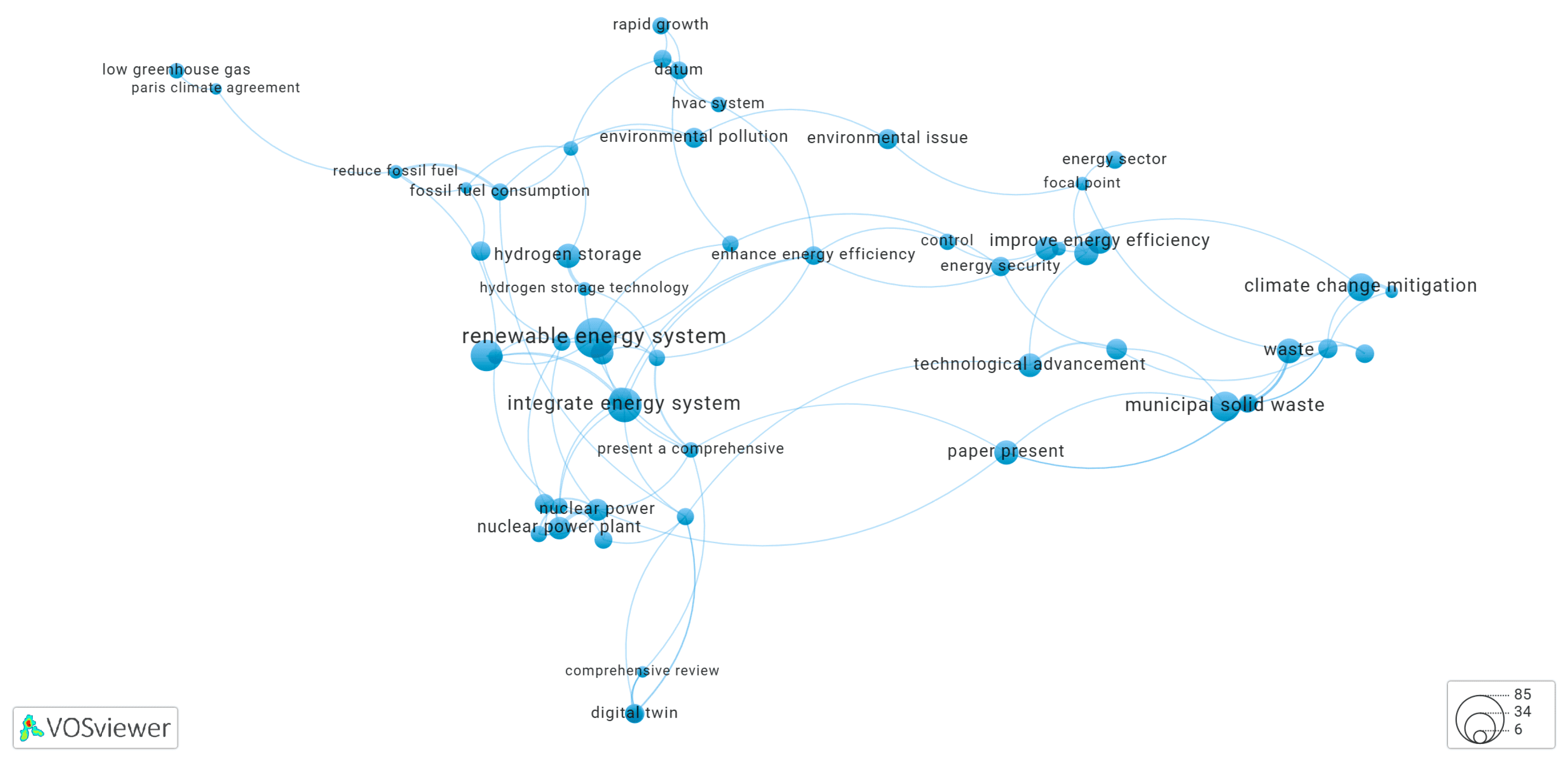
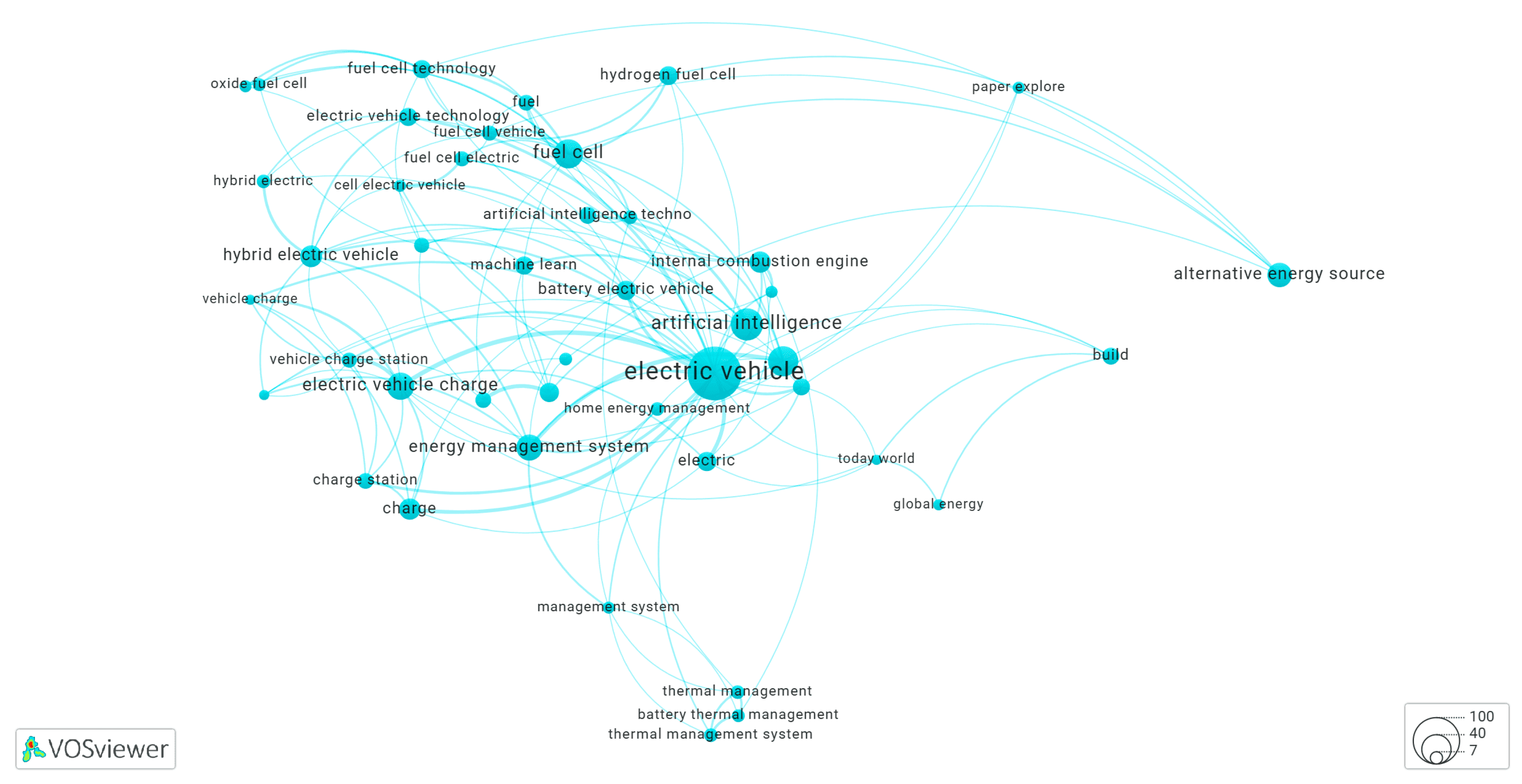
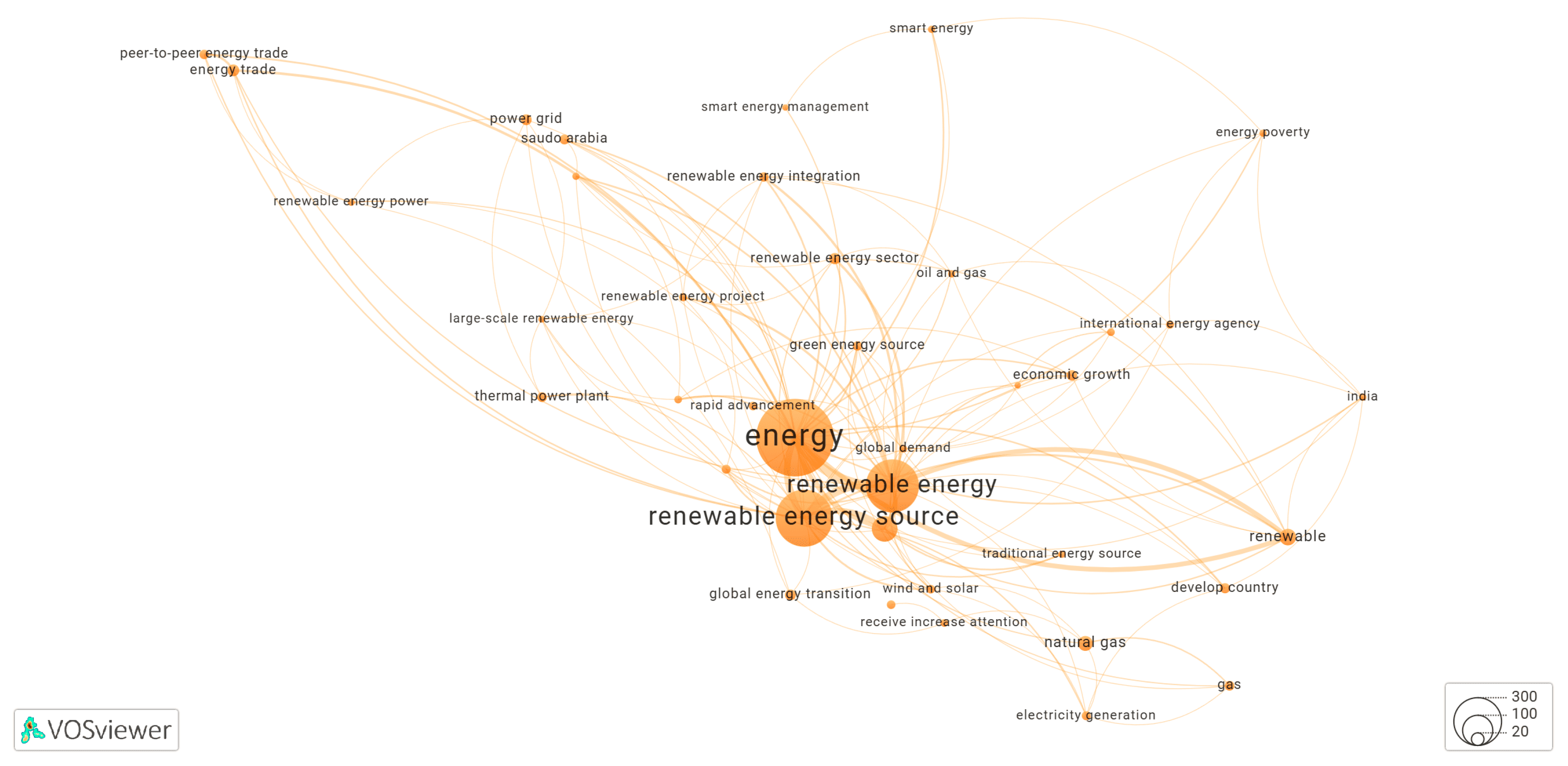
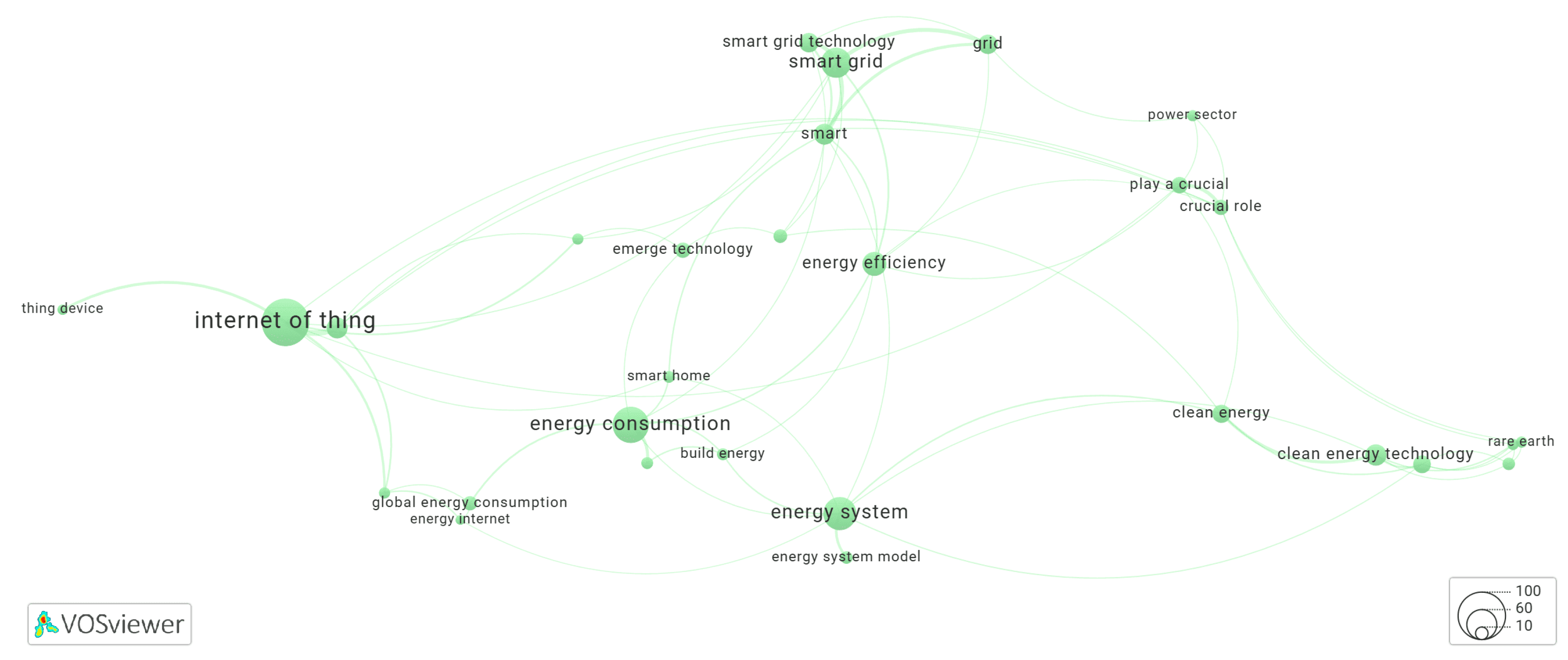
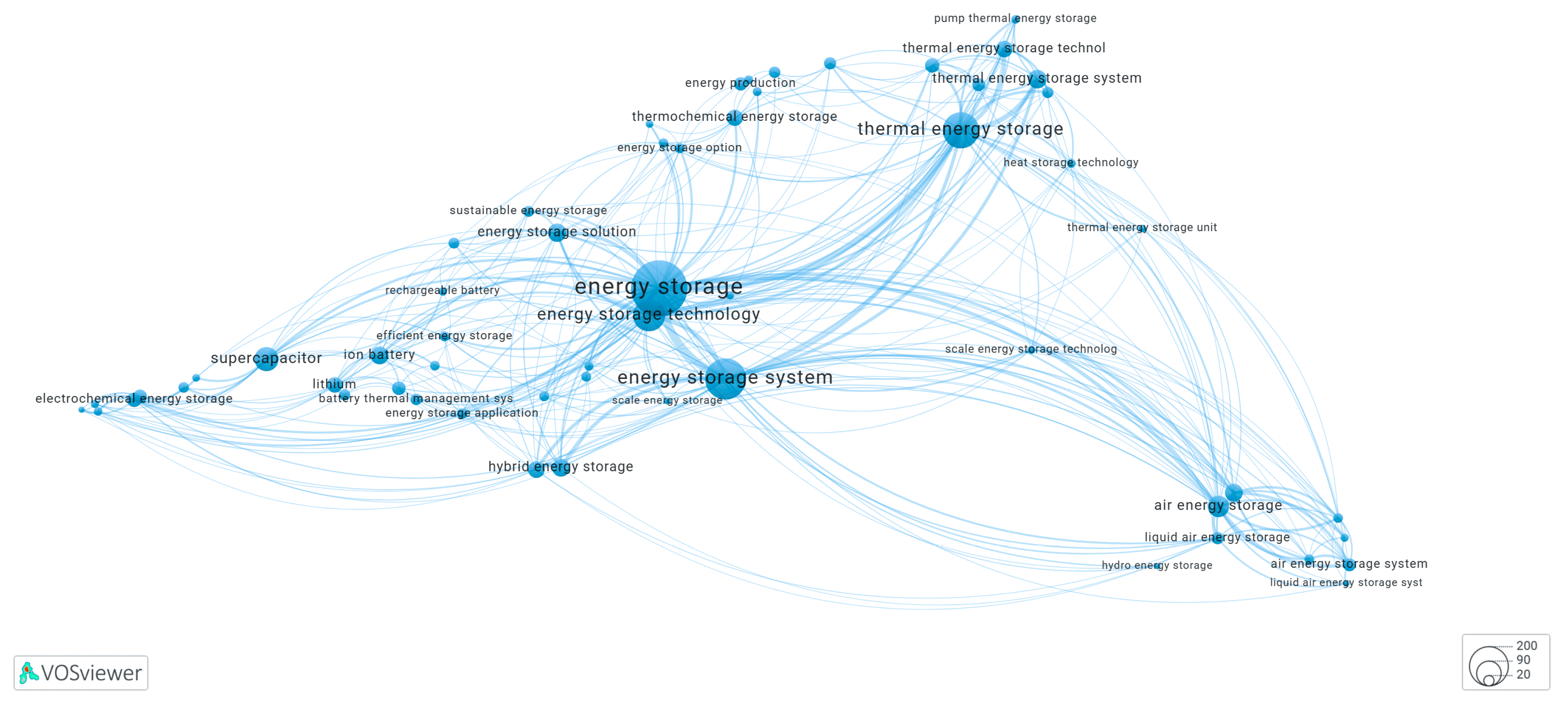
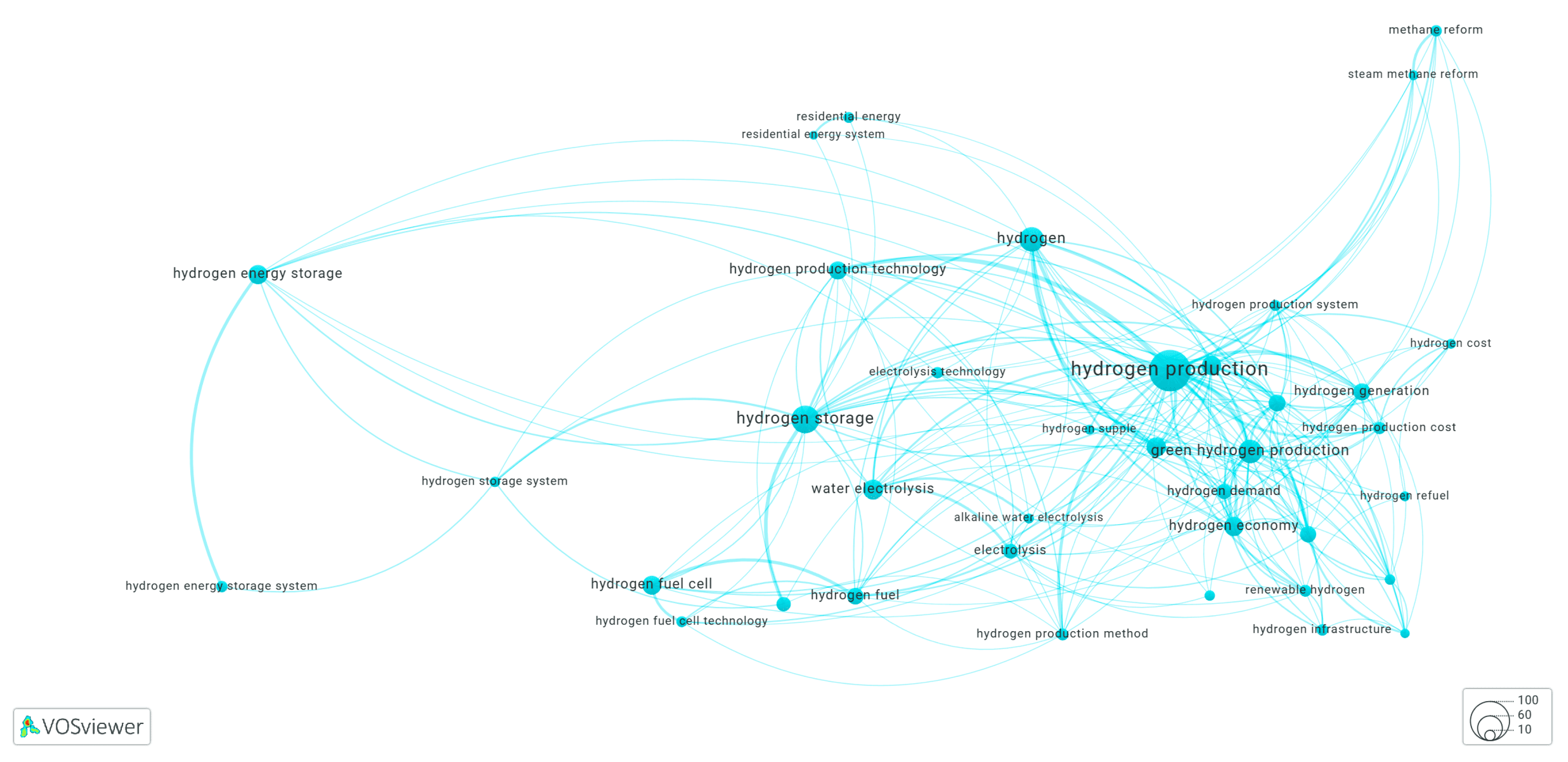
3.6. Clusters of the Keyword Co-Occurrence Network Identified by KeyphraseVectorizers PatternRank
3.6.1. Cluster-3 of Network Shown in Figure 14
3.6.2. Cluster-6 of Network Shown in Figure 14
3.6.3. Cluster-9 of Network Shown in Figure 14
3.7. A Few Preliminary Thoughts on the Results Obtained in This Paper
4. Conclusions
On the Need for Further Research
Supplementary Materials
Funding
| 1 | |
| 2 |
https://www.iea.org/reports/energy-and-ai IEA (2025), Energy and AI, IEA, Paris |
| 3 | |
| 4 | |
| 5 | |
| 6 | |
| 7 |
https://github.com/Shivanandroy/KeyPhraseTransformer — KeyPhraseTransformer is built on T5 Transformer architecture |
| 8 |
https://github.com/anyascii/anyascii — Unicode to ASCII transliteration |
| 9 | |
| 10 |
https://github.com/sharkdp/hyperfine — A command-line benchmarking tool |
| 11 |
https://towardsdatascience.com/unsupervised-keyphrase-extraction-with-patternrank-28ec3ca737f0/ — Unsupervised Keyphrase Extraction with PatternRank |
| 12 | |
| 13 | |
| 14 | |
| 15 |
References
- H. Hauser, ‘Technology, Sovereignty and Realpolitik’, in Consensus or Conflict?, H. Wang and A. Michie, Eds., Singapore: Springer Nature Singapore, 2021, pp. 233–242. [CrossRef]
- P. Grant, ‘TECHNOLOGICAL SOVEREIGNTY: FORGOTTEN FACTOR IN THE “HI-TECH” RAZZAMATAZZ’, Prometheus, vol. 1, no. 2, 1983. [CrossRef]
- Е. А. Капoгузoв and А. М. Пахалoв, ‘Технoлoгический суверенитет: кoнцептуальные пoдхoды и вoсприятие рoссийскими академическими экспертами: Technological sovereignty: Conceptual approaches and perceptions by the Russian academic experts’, Journal of the New Economic Association, no. 3(64), pp. 244–250, Oct. 2024. [CrossRef]
- H. Gu, ‘Data, Big Tech, and the New Concept of Sovereignty’, J OF CHIN POLIT SCI, vol. 29, no. 4, pp. 591–612, Dec. 2024. [CrossRef]
- P. Hummel, M. Braun, M. Tretter, and P. Dabrock, ‘Data sovereignty: A review’, Big Data & Society, vol. 8, no. 1, p. 2053951720982012, Jan. 2021. [CrossRef]
- F. Musiani, ‘Infrastructuring digital sovereignty: a research agenda for an infrastructure-based sociology of digital self-determination practices’, Information, Communication & Society, vol. 25, no. 6, pp. 785–800, Apr. 2022. [CrossRef]
- L. Van Vliet, J. Herzog-Hawelka, and C. McDonnell, ‘Neo-colonialism and leaving fossil fuels underground: a discourse analysis of the potential German-Senegalese gas partnership’, Energy Research & Social Science, vol. 125, p. 104121, Jul. 2025. [CrossRef]
- J. Wang, S. Ghosh, O. A. Olayinka, B. Doğan, M. I. Shah, and K. Zhong, ‘Achieving energy security amidst the world uncertainty in newly industrialized economies: The role of technological advancement’, Energy, vol. 261, p. 125265, Dec. 2022. [CrossRef]
- Moscow Aviation Institute (National Research University) and R. S. Golov, ‘Energy saving as a factor of energy security: personnel support’, Scient. Work. Fr. Econom. Soc. Rus., vol. 249, no. 5, pp. 126–145, 2024. [CrossRef]
- R. Prăvălie and G. Bandoc, ‘Nuclear energy: Between global electricity demand, worldwide decarbonisation imperativeness, and planetary environmental implications’, Journal of Environmental Management, vol. 209, pp. 81–92, Mar. 2018. [CrossRef]
- M. Asif, B. Solomon, and C. Adulugba, ‘Prospects of Nuclear Power in a Sustainable Energy Transition’, Arab J Sci Eng, vol. 50, no. 5, pp. 3467–3477, Mar. 2025. [CrossRef]
- Manowska, M. Boros, M. W. Hassan, A. Bluszcz, and K. Tobór-Osadnik, ‘A Modern Approach to Securing Critical Infrastructure in Energy Transmission Networks: Integration of Cryptographic Mechanisms and Biometric Data’, Electronics, vol. 13, no. 14, p. 2849, Jul. 2024. [CrossRef]
- Yewande Mariam Ogunsuji, Olamide Raimat Amosu, Divya Choubey, Bibitayo Ebunlomo Abikoye, Praveen Kumar, and Stanley Chidozie Umeorah, ‘Sourcing renewable energy components: building resilient supply chains, reducing dependence on foreign suppliers, and enhancing energy security’, World J. Adv. Res. Rev., vol. 23, no. 2, pp. 251–262, Aug. 2024. [CrossRef]
- S. O. Akpasi, I. M. Smarte Anekwe, E. K. Tetteh, U. O. Amune, S. I. Mustapha, and S. L. Kiambi, ‘Hydrogen as a clean energy carrier: advancements, challenges, and its role in a sustainable energy future’, Clean Energy, vol. 9, no. 1, pp. 52–88, Jan. 2025. [CrossRef]
- S. Ganguly and U. Bhan, ‘Scope of Geothermal Energy in Indian Energy Security’, in Energy Storage and Conservation, A. K. Sahu, B. C. Meikap, and V. K. Kudapa, Eds., Singapore: Springer Nature Singapore, 2023, pp. 15–19. [CrossRef]
- J. Govea, W. Gaibor-Naranjo, and W. Villegas-Ch, ‘Transforming Cybersecurity into Critical Energy Infrastructure: A Study on the Effectiveness of Artificial Intelligence’, Systems, vol. 12, no. 5, p. 165, May 2024. [CrossRef]
- P. D. Szymczak, ‘CNPC, Sinopec Drill Ultra Deep in Search of Energy Security’, Journal of Petroleum Technology, vol. 75, no. 07, pp. 20–25, Jul. 2023. [CrossRef]
- Y. Huang et al., ‘Forecast of Fossil Fuel Demand Based On Low Carbon Emissions from the Perspective of Energy Security’, Chem Technol Fuels Oils, vol. 58, no. 6, pp. 1075–1082, Jan. 2023. [CrossRef]
- K. M.A., N. N.L., and N. A.N., ‘The Use of Energy Storage to Improve Controllability and Security of the Belarusian Power System’, Energy Systems Research, vol. 6, no. 3(23), pp. 28–35, Oct. 2023. [CrossRef]
- Z. Yan, Y. Zhang, and J. Yu, ‘Allocative approach to multiple energy storage capacity for integrated energy systems based on security region in buildings’, Journal of Energy Storage, vol. 84, p. 110951, Apr. 2024. [CrossRef]
- Z. Yang, C. Hao, S. Shao, Z. Chen, and L. Yang, ‘Appropriate technology and energy security: From the perspective of biased technological change’, Technological Forecasting and Social Change, vol. 177, p. 121530, Apr. 2022. [CrossRef]
- W. Lu, Z. Liu, Y. Huang, Y. Bu, X. Li, and Q. Cheng, ‘How do authors select keywords? A preliminary study of author keyword selection behavior’, Journal of Informetrics, vol. 14, no. 4, p. 101066, Nov. 2020. [CrossRef]
- Esmat Babaii, Yoones Taase, ‘Author-assigned Keywords in Research Articles: Where Do They Come from?’ Iranian Journal of Applied Linguistics (IJAL), vol. 16, no. 2, pp. 1-19, 2013 url: https://ijal.khu.ac.ir/article-1-1786-fa.pdf.
- Morozov D.A., Glazkova A.V., Tyutyulnikov M.A., Iomdin B.L. Keyphrase Generation for Abstracts of the Russian-Language Scientific Articles. NSU Vestnik. Series: Linguistics and Intercultural Communication. vol. 21, no 1, pp. 54-66, 2023, (In Russ.). [CrossRef]
- Roy and S. Ghosh, ‘Freedom Versus Standard in Article Keyword Generation: An Empirical Study’, Journal of Library Metadata, vol. 24, no. 4, pp. 291–305, Oct. 2024. [CrossRef]
- U. Ahmed, C. Alexopoulos, M. Piangerelli, and A. Polini, ‘BRYT: Automated keyword extraction for open datasets’, Intelligent Systems with Applications, vol. 23, p. 200421, Sep. 2024. [CrossRef]
- V. Glazkova, D. A. Morozov, M. S. Vorobeva, and A. Stupnikov, ‘Keyphrase generation for the Russian-language scientific texts using mT5’, Model. anal. inf. sist., vol. 30, no. 4, pp. 418–428, Dec. 2023. [CrossRef]
- D. Machado, T. Barbosa, S. Pais, B. Martins, and G. Dias, ‘Universal Mobile Information Retrieval’, in Universal Access in Human-Computer Interaction. Intelligent and Ubiquitous Interaction Environments, vol. 5615, C. Stephanidis, Ed., Berlin, Heidelberg: Springer Berlin Heidelberg, 2009, pp. 345–354. [CrossRef]
- T. Schopf, S. Klimek, and F. Matthes, ‘PatternRank: Leveraging Pretrained Language Models and Part of Speech for Unsupervised Keyphrase Extraction’:, in Proceedings of the 14th International Joint Conference on Knowledge Discovery, Knowledge Engineering and Knowledge Management, Valletta, Malta: SCITEPRESS - Science and Technology Publications, 2022, pp. 243–248. [CrossRef]
- R. Campos, V. Mangaravite, A. Pasquali, A. Jorge, C. Nunes, and A. Jatowt, ‘YAKE! Keyword extraction from single documents using multiple local features’, Information Sciences, vol. 509, pp. 257–289, Jan. 2020. [CrossRef]
- N. J. Van Eck and L. Waltman, ‘Software survey: VOSviewer, a computer program for bibliometric mapping’, Scientometrics, vol. 84, no. 2, pp. 523–538, Aug. 2010. [CrossRef]
- R. Campos, V. Mangaravite, A. Pasquali, A. M. Jorge, C. Nunes, and A. Jatowt, ‘A Text Feature Based Automatic Keyword Extraction Method for Single Documents’, in Advances in Information Retrieval, vol. 10772, G. Pasi, B. Piwowarski, L. Azzopardi, and A. Hanbury, Eds., Cham: Springer International Publishing, 2018, pp. 684–691. [CrossRef]
- R. Campos, V. Mangaravite, A. Pasquali, A. M. Jorge, C. Nunes, and A. Jatowt, ‘YAKE! Collection-Independent Automatic Keyword Extractor’, in Advances in Information Retrieval, vol. 10772, G. Pasi, B. Piwowarski, L. Azzopardi, and A. Hanbury, Eds., Cham: Springer International Publishing, 2018, pp. 806–810. [CrossRef]
- P. Nathan, DerwenAI/pytextrank: v3.1.1 release on PyPi. (Mar. 25, 2021). Zenodo. [CrossRef]
- M. Luo, B. Xue, and B. Niu, ‘A comprehensive survey for automatic text summarization: Techniques, approaches and perspectives’, Neurocomputing, vol. 603, p. 128280, Oct. 2024. [CrossRef]
- P. Widyassari et al., ‘Review of automatic text summarization techniques & methods’, Journal of King Saud University - Computer and Information Sciences, vol. 34, no. 4, pp. 1029–1046, Apr. 2022. [CrossRef]
- R. Hu, J. Wu, and X. Lu, ‘Word-Combination-Based Measures of Phraseological Diversity, Sophistication, and Complexity and Their Relationship to Second Language Chinese Proficiency and Writing Quality’, Language Learning, vol. 72, no. 4, pp. 1128–1169, Dec. 2022. [CrossRef]
- Y. D. Severina, V. A. Shakirov, and L. N. Takaishvili, ‘Modeling the Development of Energy Systems of Remote Areas in the Context of the Energy Transition’, Energy Systems Research, vol. 7, no. 4(28), pp. 38–48, Dec. 2024. [CrossRef]
- D. I.S., ‘Methods for Analyzing and Increasing Cyber Resilience of Smart Energy System Facilities’, Energy Systems Research, vol. 6, no. 3(23), pp. 75–81, Oct. 2023. [CrossRef]
- Chigarev, B.N., ‘A Brief Analysis of Topics of the IEEE Conference on Energy Internet and Energy System Integration in 2017–2021’, Energy Systems Research, vol. 6, no. 3(23), pp. 36–49, Oct. 2023. [CrossRef]
- V. Lundaev, A. A. Solomon, T. Le, A. Lohrmann, and C. Breyer, ‘Review of critical materials for the energy transition, an analysis of global resources and production databases and the state of material circularity’, Minerals Engineering, vol. 203, p. 108282, Nov. 2023. [CrossRef]
- J. Edler, K. Blind, H. Kroll, and T. Schubert, ‘Technology sovereignty as an emerging frame for innovation policy. Defining rationales, ends and means’, Research Policy, vol. 52, no. 6, p. 104765, Jul. 2023. [CrossRef]
- Technology Development Center for Fuel and Energy Complex under the Ministry of Energy of the Russian Federation, RF, Moscow, The Diplomatic Academy of the Ministry of Foreign Affairs of Russia, RF, Moscow, O. V. Zhdaneev, K. N. Frolov, and Technology Development Center for Fuel and Energy Complex under the Ministry of Energy of the Russian Federation, RF, Moscow, ‘Scientific and technological priorities of the fuel and energy complex of the Russian Federation until 2050’, OIJ, no. 10, pp. 6–13, 2023. [CrossRef]
- State University of Management RF, Moscow, V. Ya. Afanasyev, D. A. Suslov, State University of Management RF, Moscow, S. V. Chuev, and State University of Management RF, Moscow, ‘Soviet experience in the development of economic and industrial potential under sanctions’, OIJ, no. 12, pp. 156–160, 2022. [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




