1. Dependency Graph (What Depends on What)
We make the logical dependency explicit:
Axioms: locality (A1), stationary KMS/steady reference (A2), conserved charge/slow sector (A3).
Predicate: certified hydrodynamic window (Def. 3) on a specified dataset and interval.
Theorems gated by : diffusion (Thm. 2), scaling (Thm. 3), lower bounds (Cor. 1).
Optional model Axioms: thermal modular bridge (M1), Higgs portal matching (M2), plus non-circularity predicate .
Only under M1+M2+NC: Golden Relation (Thm. A1) and benchmark band (Cor. A1).
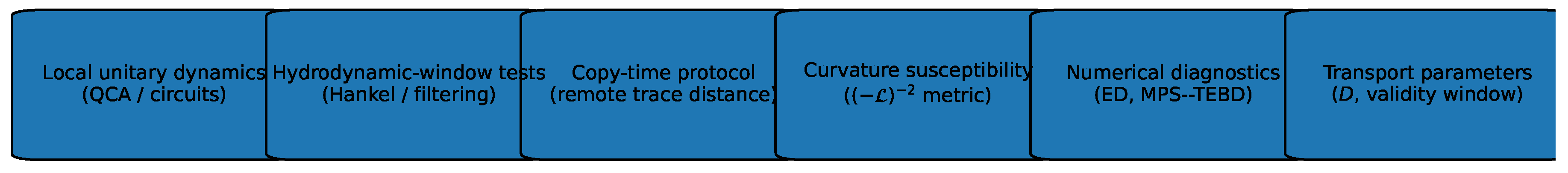
Figure 1.
Program-level schematic (robustness bundle): operational → certified micro–macro closure → optional bridges.
Figure 1.
Program-level schematic (robustness bundle): operational → certified micro–macro closure → optional bridges.
2. Standard Axioms (Minimal and Conventional)
Axiom. (Locality/finite-speed influence) There exists a Lieb–Robinson type finite-speed influence bound. [
4,
5]
Axiom. (Stationary reference and Kubo–Mori structure) There exists a faithful stationary reference state
(KMS or steady state) and the Kubo–Mori inner product
is well-defined. [
9,
14]
Axiom. (Conserved charge/slow mode) There exists an extensive charge
producing a slow sector in the sense of projection-operator methods. [
6,
7]
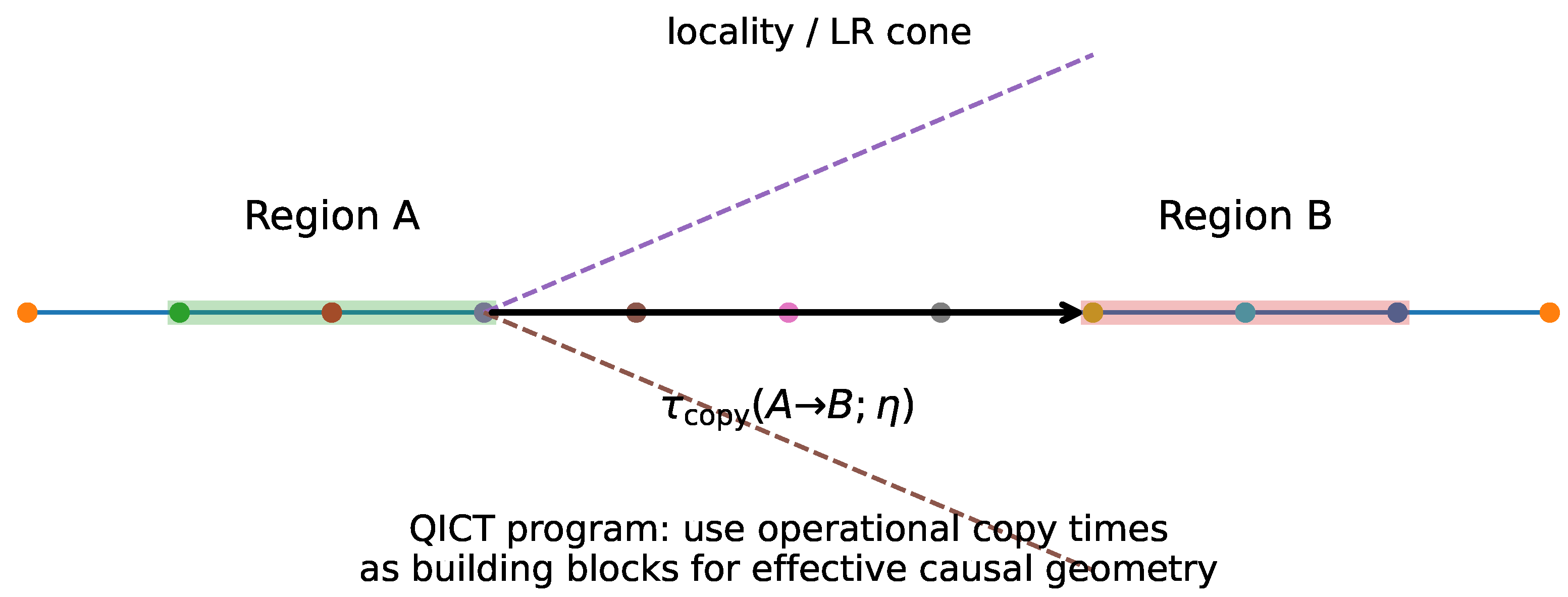
3. Operational Copy Time
Definition 1 (Perturbation and Helstrom signal). Let with and . Let and . Define .
Definition 2 (Copy time). Given , define as the minimal t such that .
Theorem 1 (Operational meaning (Helstrom)).
At time t, the optimal binary measurement distinguishes from with success probability . [1,2]
4. Certified-Window Predicate
Definition 3 (Certified Hydrodynamic Window
).
Fix , an observable set used for diagnostics, and tolerances . holds iff the dataset passes simultaneously: (i) Hankel-rank saturation (within ), (ii) completeness proxy , (iii) residual/closure , (iv) Gaussianity proxy (TV-to-Gauss) , (v) late-time Helstrom ratio . The exact algorithmic Definitions are in the Supplement; Appendix A lists dataset-level values.
Figure 2.
Reproducible pipeline overview (robustness bundle). Theorems are invoked only when is satisfied.
Figure 2.
Reproducible pipeline overview (robustness bundle). Theorems are invoked only when is satisfied.
5. Micro–Macro Theorems (Invoked Only Under CHW)
Lemma 1 (Mori–Zwanzig identity).
Under Axioms 2 and 3, the projected dynamics satisfies the Mori–Zwanzig identity. [6,7]
Theorem 2 (Certified diffusion).
Assume Axioms 1–3 and . Then, on that window, the conserved-density mode obeys an effective diffusion equation with constant extracted within the same certification, and the retarded correlator exhibits a diffusive pole. [12] Error terms are controlled by the tolerances η.
6. Susceptibility and Central Scaling
Definition 4 (Second-moment fast-complement susceptibility).
Define and its square pseudo-inverse on the fast complement (well-defined on certified windows). For a charge perturbation , define
Theorem 3 (Central QICT scaling (two-sided bound)). Assume Axioms ??–?? and . Then there exist constants (depending only on certified parameters and the receiver family) such that , equivalently on the certified window.
Corollary 1 (Diffusive lower bound). Under Thm. 2, for a receiver at distance ℓ, (constants controlled by η).
Remark 1 (Convention lock). Definition 4 is locked. If one defines , then . Mixing these without a dictionary is referee-fatal.
7. Evidence: Window-Sensitivity and Certification Tables
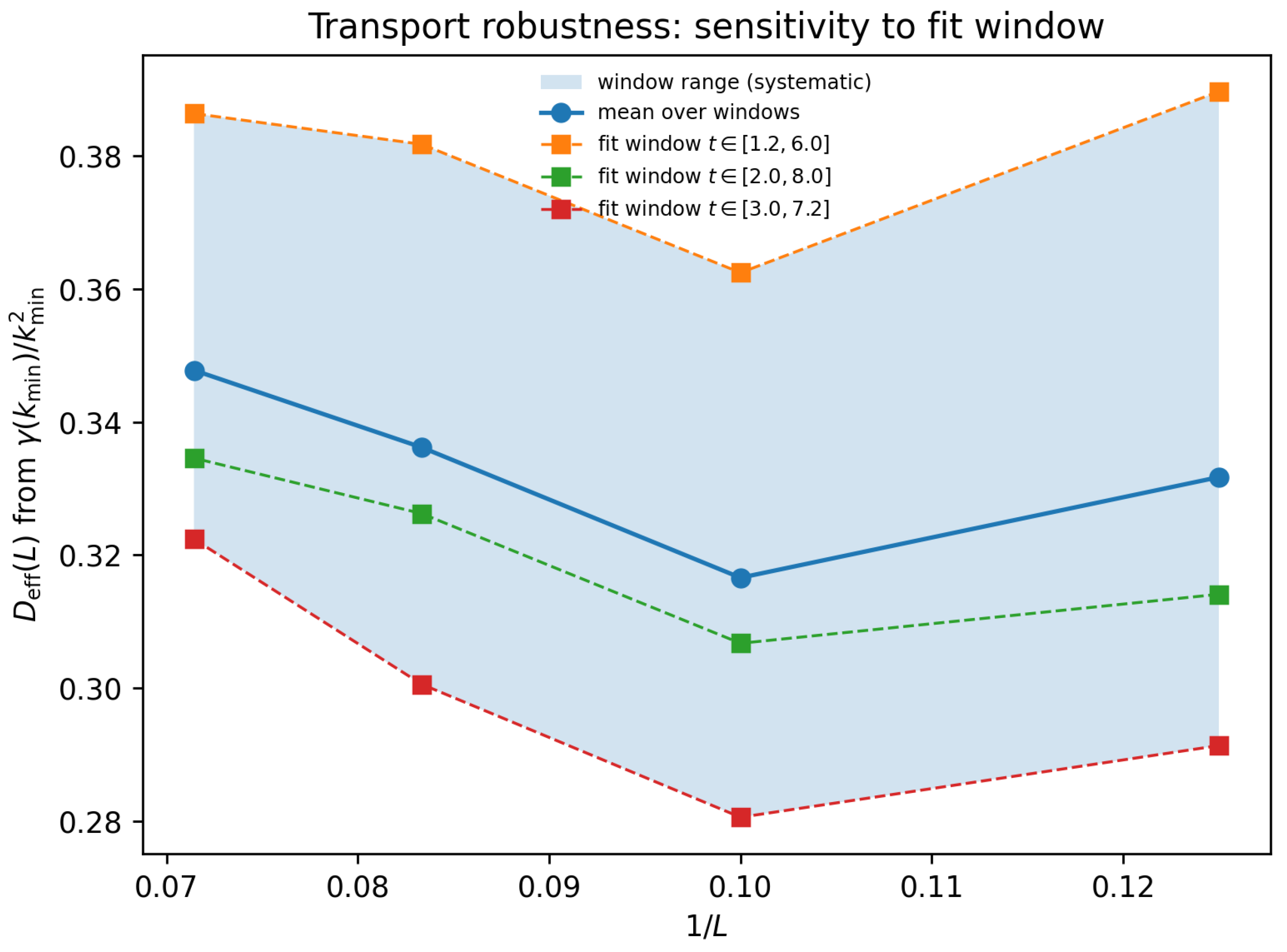
7.1. Diffusion Window Sensitivity
Table 1.
Window-sensitivity robustness test for (robustness bundle source).
Table 1.
Window-sensitivity robustness test for (robustness bundle source).
| L |
|
|
|
|
| 8 |
0.125000 |
0.3317 |
0.2913 |
0.3897 |
| 10 |
0.100000 |
0.3166 |
0.2805 |
0.3625 |
| 12 |
0.083333 |
0.3362 |
0.3005 |
0.3818 |
| 14 |
0.071429 |
0.3478 |
0.3224 |
0.3864 |
Figure 3.
Visualization of the window-sensitivity test for (robustness bundle).
Figure 3.
Visualization of the window-sensitivity test for (robustness bundle).
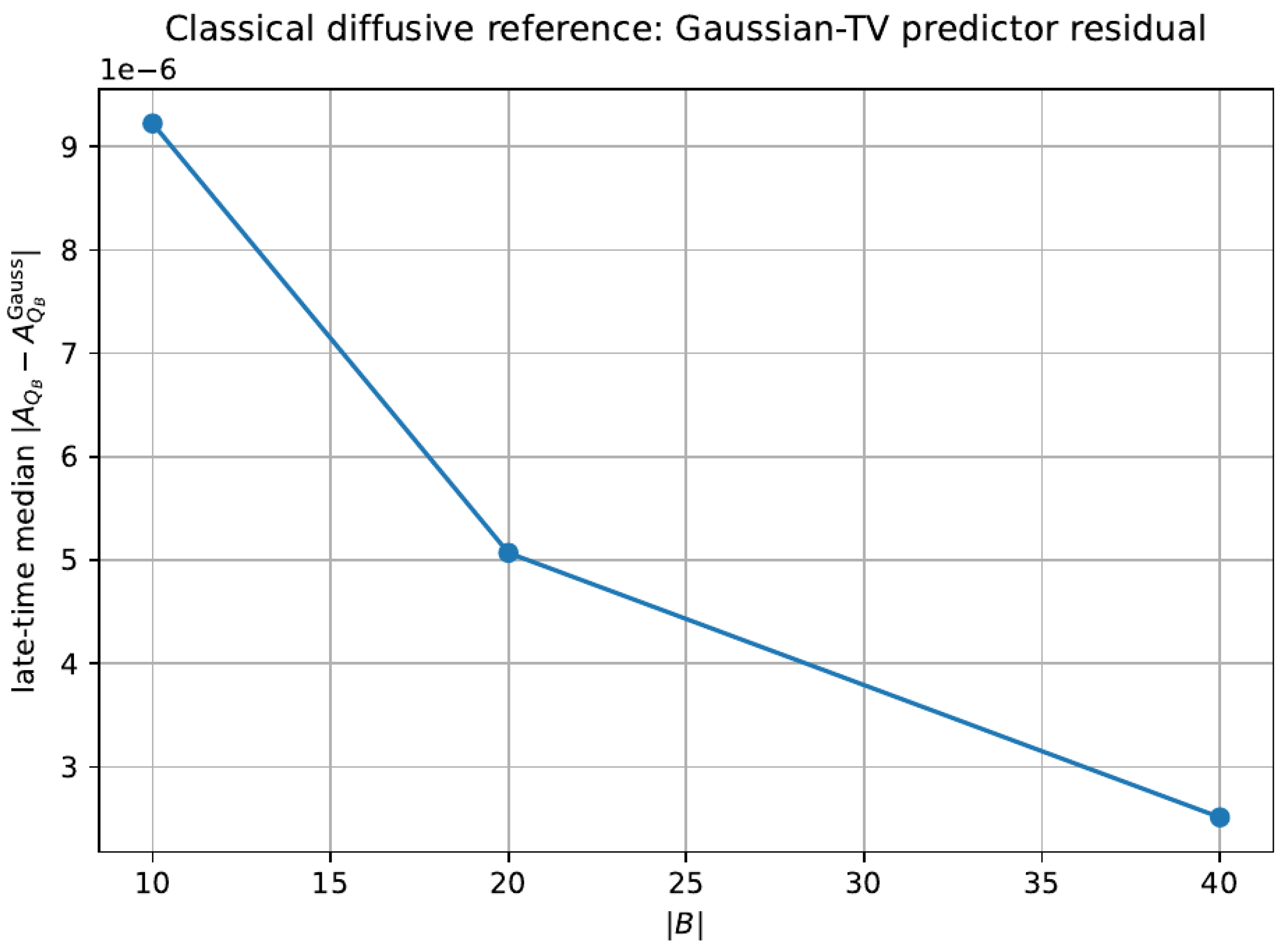
7.2. Certified-Window Table from Validation Outputs
Figure 4.
Example residual/closure diagnostic (robustness bundle).
Figure 4.
Example residual/closure diagnostic (robustness bundle).
Appendix A. Certified-Window Appendix (Dataset-Level Values)
Table A1 is generated directly from the bundled validation outputs and provides auditable values for key certification proxies (late-time Helstrom ratio, advantage residual, and TV-to-Gauss). Thresholds used in this package are:
,
,
.
Table A1.
Dataset-level certification proxies from bundled validation outputs (subset shown). “CHW” indicates whether the predicate passes under the stated thresholds.
Table A1.
Dataset-level certification proxies from bundled validation outputs (subset shown). “CHW” indicates whether the predicate passes under the stated thresholds.
| Model |
N |
|
r |
|
|
|
median ratio |
median adv resid |
median TV→Gauss |
CHW |
| II_exchange |
6 |
0.1 |
2 |
3 |
inf |
inf |
1 |
0.0007548 |
0.01785 |
PASS |
| II_exchange |
6 |
0.1 |
2 |
3 |
inf |
inf |
1 |
0.0007683 |
0.01785 |
PASS |
| II_exchange |
6 |
0.1 |
2 |
3 |
inf |
inf |
1 |
0.0007846 |
0.01785 |
PASS |
| II_exchange |
6 |
0.1 |
2 |
3 |
inf |
inf |
1 |
0.001503 |
0.01785 |
PASS |
| II_exchange |
6 |
0.1 |
2 |
3 |
inf |
inf |
1 |
0.00153 |
0.01785 |
PASS |
| II_exchange |
6 |
0.1 |
2 |
3 |
inf |
inf |
1 |
0.001562 |
0.01785 |
PASS |
| II_exchange |
6 |
0.1 |
3 |
3 |
inf |
inf |
1 |
0.000679 |
0.01785 |
PASS |
| II_exchange |
6 |
0.1 |
3 |
3 |
inf |
inf |
1 |
0.0007498 |
0.01785 |
PASS |
| II_exchange |
6 |
0.1 |
3 |
3 |
inf |
inf |
1 |
0.0007975 |
0.01785 |
PASS |
| II_exchange |
6 |
0.1 |
3 |
3 |
inf |
inf |
1 |
0.001352 |
0.01785 |
PASS |
| II_exchange |
6 |
0.1 |
3 |
3 |
inf |
inf |
1 |
0.001493 |
0.01785 |
PASS |
| II_exchange |
6 |
0.1 |
3 |
3 |
inf |
inf |
1 |
0.001588 |
0.01785 |
PASS |
| II_exchange |
7 |
0.1 |
3 |
3 |
inf |
inf |
1 |
0.000661 |
0.01785 |
PASS |
| II_exchange |
7 |
0.1 |
3 |
3 |
inf |
inf |
1 |
0.001317 |
0.01785 |
PASS |
| II_exchange |
7 |
0.1 |
4 |
3 |
inf |
inf |
1 |
0.0006573 |
0.01785 |
PASS |
| II_exchange |
7 |
0.1 |
4 |
3 |
inf |
inf |
1 |
0.001309 |
0.01785 |
PASS |
Appendix B. Optional Model Bridges (Explicit Boundaries)
Axiom. (Thermal modular bridge (model Axiom)) In a specified bridge regime, the optimal discrimination channel is dominated by thermal modular flow, yielding a thermal bound
. [
13,
14]
Axiom. (Higgs-portal matching (model Axiom)) Higgs-portal EFT matching yields
, with
determined independently of the target mass. [
15]
Definition A1 (Non-circularity predicate NC) NC holds iff and are obtained independently of the dark-sector inference.
Theorem A1 (Golden Relation (model-conditional, non-circular)). Assume Axioms 4 and 5 andNC. Then .
Corollary A1 (Benchmark band). Under the benchmark calibration used in the DM bundle, GeV (1σ).
References
- C. W. Helstrom. In Quantum Detection and Estimation Theory; Academic Press: New York, 1976.
-
A. S. Holevo, Probabilistic and Statistical Aspects of Quantum Theory; Edizioni della Normale: Pisa, 2011.
- Nielsen, M. A.; Chuang, I. L. Quantum Computation and Quantum Information; Cambridge University Press: Cambridge, 2010. [Google Scholar]
- Lieb, E. H.; Robinson, D. W. The finite group velocity of quantum spin systems. Commun. Math. Phys. 1972, 28, 251. [Google Scholar] [CrossRef]
- Bravyi, S.; Hastings, M. B.; Verstraete, F. Lieb–Robinson bounds and the generation of correlations and topological quantum order. Phys. Rev. Lett. 2006, 97, 050401. [Google Scholar] [CrossRef] [PubMed]
- H. Mori, “Transport, collective motion, and Brownian motion. Prog. Theor. Phys. 1965, 33, 423. [CrossRef]
- Zwanzig, R. Ensemble method in the theory of irreversibility. J. Chem. Phys. 1960, 33, 1338. [Google Scholar] [CrossRef]
- Kubo, R. Statistical-mechanical theory of irreversible processes. I. J. Phys. Soc. Jpn. 1957, 12, 570. [Google Scholar] [CrossRef]
- Araki, H. Relative entropy of states of von Neumann algebras. Publ. RIMS Kyoto Univ. 1976, 11, 809. [Google Scholar] [CrossRef]
- Spohn, H. Entropy production for quantum dynamical semigroups. J. Math. Phys. 1978, 19, 1227. [Google Scholar] [CrossRef]
- Breuer, H.-P.; Petruccione, F. The Theory of Open Quantum Systems; Oxford University Press: Oxford, 2002. [Google Scholar]
- Kadanoff, L. P.; Martin, P. C. Hydrodynamic equations and correlation functions. Ann. Phys. 1963, 24, 419. [Google Scholar] [CrossRef]
- Deffner, S.; Campbell, S. Quantum speed limits: from Heisenberg’s uncertainty principle to optimal quantum control. J. Phys. A 2017, 50, 453001. [Google Scholar] [CrossRef]
- Bratteli, O.; Robinson, D. W. Operator Algebras and Quantum Statistical Mechanics; Springer: Berlin, 1997; Vol. 2. [Google Scholar]
- (Placeholder) Higgs-portal dark matter reviews to be aligned with the submission bibliography.
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2026 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).