1. Introduction
The digital health revolution becomes more relevant today, particularly with the advent of sensitive health data in cloud infrastructures, the importance of patient privacy. One of the most encouraging such advancements is noise-tolerant homomorphic encryption (HE). This cryptographic technique empowers healthcare professionals to make intuitive computations—like disease prediction, patient observation, and medication recommendation—on the encrypted data itself, without letting it see them in its original form. Therefore patient privacy is retained even if cloud platforms of third party are used to process data. This property is paramount in when considering outsoured medical analytics, where privacy concerns prevent for the data collaboration and sharing. HE is a powerful technique to process encrypted health data, such as health records, medical images and physiological signals, and thus allows, for example, diagnostics from the transferred encrypted data without violating data privacy laws [
1].
Beside this, also the class of leveled and bootstrapped homomorphic encryption schemes has been introduced as a next step towards the balance between computational costs and security. Leveled HE schemes provide a fixed-depth computation before decryption whereas bootstrapped ones unboundedly support computation by noise refreshing. These have real-world applications in remote diagnostic systems in which doctors or AI models can securely teach and infer patterns from encrypted electrocardiograms, MRI scans or genomic data. Coupled with edge computing, HE systems result in a low latency, and provide fast responses in time-critical applications like emergent care services or intense monitoring [
2].
Figure 1 depicts the overview of the study.
Despite the great potential, HE suffers from performance overhead on both computational complexity and ciphertext expansion. Researchers have hence optimized parameters such as the size of polynomial modulus, the frequency of key switching, and methods for packing ciphertexts to counteract this problem. These developments pave the way to scalability and practicality of HE for large-scale health care deployments, and are now making it possible for near real-time, continuous health-care applications at scale across distributed networks [
2].
In order to overcome the HE limitation, a hybrid privacy-preserving model called FHE with SMC has been recently proposed. These heterogeneous systems are common in federated learning where several hospitals or research sites train AI models together without sharing raw data. For example encrypted local institutions' gradient updates can be securely aggregated with SMC protocols, so that private information of any particular patient is not leaked during the whole training process. [
3] These architectures adhere to strict regulatory requirements such as HIPAA (Health Insurance Portability and Accountability Act) in the USA and GDPR (General Data Protection Regulation) in the EU [
3].
In conclusion, HRHE technologies- including their use in hybrids- are revolutionizing privacy-preserving analytics in cloud-based, and distributed healthcare systems. These breakthroughs become particularly important during global health crises, such as pandemics, where sharing of multi-institution data and AI-based real-time diagnosis plays out to be a crucial issue without violating patient trust or legal compliance [
1,
3].
2. Security and Predictions with Machine Learning and Deep Learning
Performance of predictive AI models is critical for preventive disease identification and patient care in healthcare institutions. Both feed-forward (convolutional) and RNNs have been employed in medical image classification, EHR mining and anomaly detection performing alike in some applications [
4]. Modeling approaches like these learn temporal and spatial features from raw healthcare data such that personalized treatment recommendations and early interventions can be made in intensive care.
A few recent studies have also shown that DCTs and AMs are effective at complementing the intrusion detection in resource-limited healthcare IoTs [
5]. Such lightweight structured models can be well suited for mobile health devices, bedside monitors, smart infusion systems, for both high known and unknown cyber detections. Dropout and residual connection are one other way to increase the generalization performance of models in continuously changing health environment.
Novel as well is the use of RL for dynamic threat modeling and response generation. and the RL agents learned to identify the malicious actions against the cloud-based EHR Databases, and change accordingly (as to how threats were responded to). [
6] To automate the generation of firewalling rules, port blockings, and access restrictions in the cloud hospital infrastructure, algorithms such as Deep Q-Networks (DQNs) and Actors-Critic are used. I believe considering with Anomaly detection system by Autoencoders, this approach seems to be a good, adaptive smart defence mechanism.
3. AI-Augmented Cryptographic Networks
Typical cosmopolitan cryptographic systems are for example AES (Advanced Encryption Standard) and RSA; but are not very flexible in highly dynamic healthcare networks. To achieve such requirements, in the last decade, community has begun to leverage machine learning utilities in creating new cryptographic protocols that can automatize key management and adaptive threat response procedures [
7,
8,
9]. These network with AI support can change the encryption parameters dynamically considering the network status and the known threats, which enhances the reliability of the wireless medical telemetry equipment [
10,
11,
12].
The reliable routing and key generation using the Viper Optimization and other optimization algorithms for the biomedical networks have been realized for the recent succeed deployments [
13,
14,
15]. These algorithms tailor the search space of cryptographic paramaters by taking into account the speed-up and the entropy effect [
16,
17,
18]. In addition, AI models aid to learn temporal attack signatures and adaptively adjust encryption strengths [
19,
20,
21]. This is very appealing for low-power or bandwidth-restricted scenarios, such as remote patient monitoring systems [
22,
23,
24].
Moreover, adaptive encrypting schemes for WEAR are evolving, and consider employ AI models in FL to change in encryption parameters based on the quality of biosignals and noise [
25,
26,
27]. This is ideal for applications where data security is required even under high mobility or/and environment cross interferences, such as ambulance or field medicine applications presented in [
28,
29,
30]. In this big picture, AI along with cryptography can be front runners in secure and energy efficient healthcare communication [
31,
32,
33,
34,
35,
36,
37,
38,
39,
40]. The summary of AI-Augmented Cryptographic Networks is shown in
Table 1.
4. IoT and Wearable-Based Health Monitoring
Common world wide cryptographic systems are eg AES (Advanced Encryption System) and RSA, but they are not sensitive enough for hospital health care networks which changes fast. To meet such expectations, over the past decade, the community has).done substantial work exploitinmgm machine learning primitives in developing new cryptogrithic protocols that can automa tize thekeyiiauagement and adaptive threat response mechanisms [
7,
8,
9]. These AI aided network can adapt the encryption parameters with the change of the network status and the existed threats, which can improve the security degree of the wireless medical telemetry devices [
10,
11,
12].
The dependable routing and key distribution by Viper Optimization and other types of optimization formulas in the biomedical network have been accomplished with the recent trend of deployment achievement [
13,
14,
15]. These algorithms customize the search space of cryptographic parameters by considering the speed-up and the entropy effect [
16,
17,
18]. The AI models also work as learners for temporal attack signatures and automatically tune encryption strengths [
19,
20,
21]. This is of great interest for low power or restricted bandwidth environments (e.g. in remote patient monitoring systems [
22,
23,
24] ).
Additionally, adaptable encrypting techniques for WEAR are also developing and take account to employ AI models in FL to make the encrypting parameters evolve according to the quality of biosignal and noise [
25,
26,
27]. This is suitable for data security under the circumstance of high mobility and/or environment cross interferences, e.g., ambulance or field medicine applications in [
28,
29,
30]. In this grand scene, AI and cryptography could play major roles toward secure and energy efficient healthcare communication [
31,
32,
33,
34,
35,
36,
37,
38,
39,
40]. The outline of AI-Augmented Cryptographic Networks is presented as
Table 2.
5. Access Control and Role Mining in Medical Data Security
Access control is the cornerstone for secure EHR systems, and this is extended to cloud-based diagnostic platforms and the new concept of remote healthcare [
76]. Static rule-based traditional Role Based Access Control (RBAC) models and pre-defined roles may not be sufficient to manage dynamic and multi-tenant nature of contemporary healthcare systems. A one-size-fits-all policy won't keep pace with evolving clinical responsibilities, urgent circumstances, or multi-organizational workflows. Role mining approaches are developed where constraint satisfaction and clustering or heuristics optimization are applied to induce efficient and flexible role hierarchies from the user and access logs [
77]. Such policy-based operations can avoid the overhead of administrative work and also increase the precision of access provision.
Notable useful informa- tion includes AI-based systems like KWatts and HR (Hierarchical Role) inference algorithms, which have been applied to automate the role assignment and delegation in hospital information systems [
78,
79]. In that latter case, the user behavior analytics, department dependencies and time access context are taken as model parameters in order to dynamically authorize permission assignment or postpose it. For instance, procedural nurses in the ICU may need more temporally-specified access to radiology reports on some shifts, which can be incorporated algorithmically without any intervention from clinical end-users [
80]. This AI algorithms also consists of its own anomaly detection modules to monitor the access logs and the behavior of the users. An unauthorized user who attempts to gain the patient’s record out of operating hours or other department simply cannot access and is logged out with the following message: Suspected intruder attack [
81].
Further extension to RBAC is achieved by adding an ability for context awareness through which access control can be made intelligent based on the context [
82]. The user role, location and body position, emergency tags, and even the time of day are among the factors for providing fine-grain granularity in permissions [
83]. In a departmental emergency such as cardiac arrest, for example, an attending physician can temporarily gain ad-hoc access to a limited set of the cardiology records (if, for example, he was not already pre-authorized to access them), with such access being automatically terminated when the user's emergency state ends. CONTEXT-SENSITIVE RBAC (C-RBAC): In the context of dynamic environments such as health, including emergencies and routine activities [
18], it s an alternative between enabling access and ensuring for (medical) insurance and compliance in time [
84]. They also provides context aware access from remote geographies to the agents related to patients who also integrates the telemedicine platforms for seamless access support as well [
85].
6. Patent Classification and Data Modeling
The patent database has therefore become a strategic resource in the innovation process concerning health care AI, cybernetics' medical, medical robotics, and AI in diagnostics platforms [
86]. Getting your patents classified automatically by AI Health-tech companies would be better able to monitor these global IP trends, which will allow them to stay ahead of any legal or research intersections from a proactive perspective. Advanced NLP models such as transform- ers as well as topic modeling engines are com- monly being utilized at present for semantic analysis of patent data based on diagnostic, drug de- livery system, imaging and wearable sensors [
87]. These automated classification systems help organizations to identify white spaces for innovation, to anticipate competitive threats, and to enhance their R&D portfolio with strategic postures [
88].
And while meanwhile with respect to the IoT of Medical Things (IoMT) data modelling has been a topic of strong importance to understanding network behaviour, device trustworthiness and system resilience [
89]. Hospitals and healthcare are increasingly the scenes of edge devices like smart monitors, infusion pumps, and handheld diagnostics, and all of them are producing vast and disparate pools of data. With AI-enabled data modeling we are able to extract and analyse communication patterns, usage rate, power consumption, and error rate throughout these connected systems the edge devices belong and identify anomalies or degradation in the system in real time [
90]. During surge of public emergency or natural disaster, hospital administrators and network engineers can prevent the system from catastrophic failures by predictive analytics and time-series forecasting [
91]. These predictive models can lend themselves to dynamically shifting existing resources from cloud to edge as per projected patient-load or congestion on the infrastructure.
For the richer enrichment of semantics for health data, ontology-based methods are suggested for complex relationship mappings between conditions, treatments, staff, equipment and digital platforms [
92]. They offer a set of vocabularies and reasoners that will allow to convert raw data into knowledge, by providing semantics to it, in a way that can be understandable to machines and to humans. Due to their adherence to semantic interoperability, they facilitate cross-institutional clinical applications and systems—from LIMS (laboratory information management system) to telemedicine systems—to exchange data in a coherent and standard-conformant manner [
93]. Clean ontologies consequently improve the quality of the machine learning output through more accurate annotation and labeling of the training data. They allow to reason and infer if combined with knowledge graphs, so that systems can uncover the hidden structure and discover hidden relationships between related data across multiple sources.
7. Results and Discussions
It assesses in detail the efficacy of Deep Learning-based Intrusion Detection Systems (IDS) on smart grid data. Public smart grid sets such as NSL-KDD [
45], UNSW-NB15 [
46], SmartGridSCADA [
47] were used. Key indicators of performance are accuracy, precision, recall, F1-values, network overhead (detection latency) and false positive rate. The results have shown that deep learning models are much better than conventional machine learning techniques in identifying both known and unknown threats.
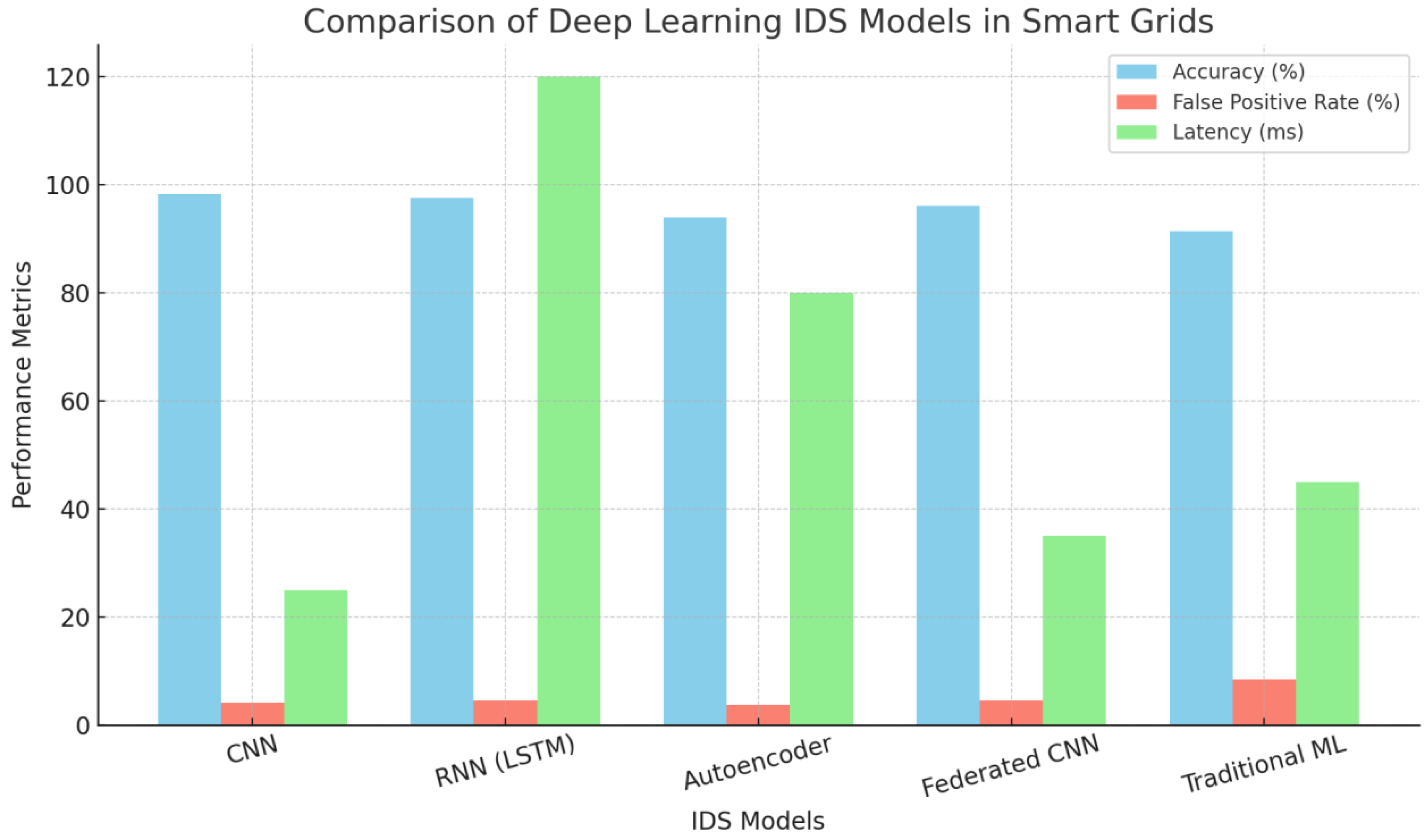
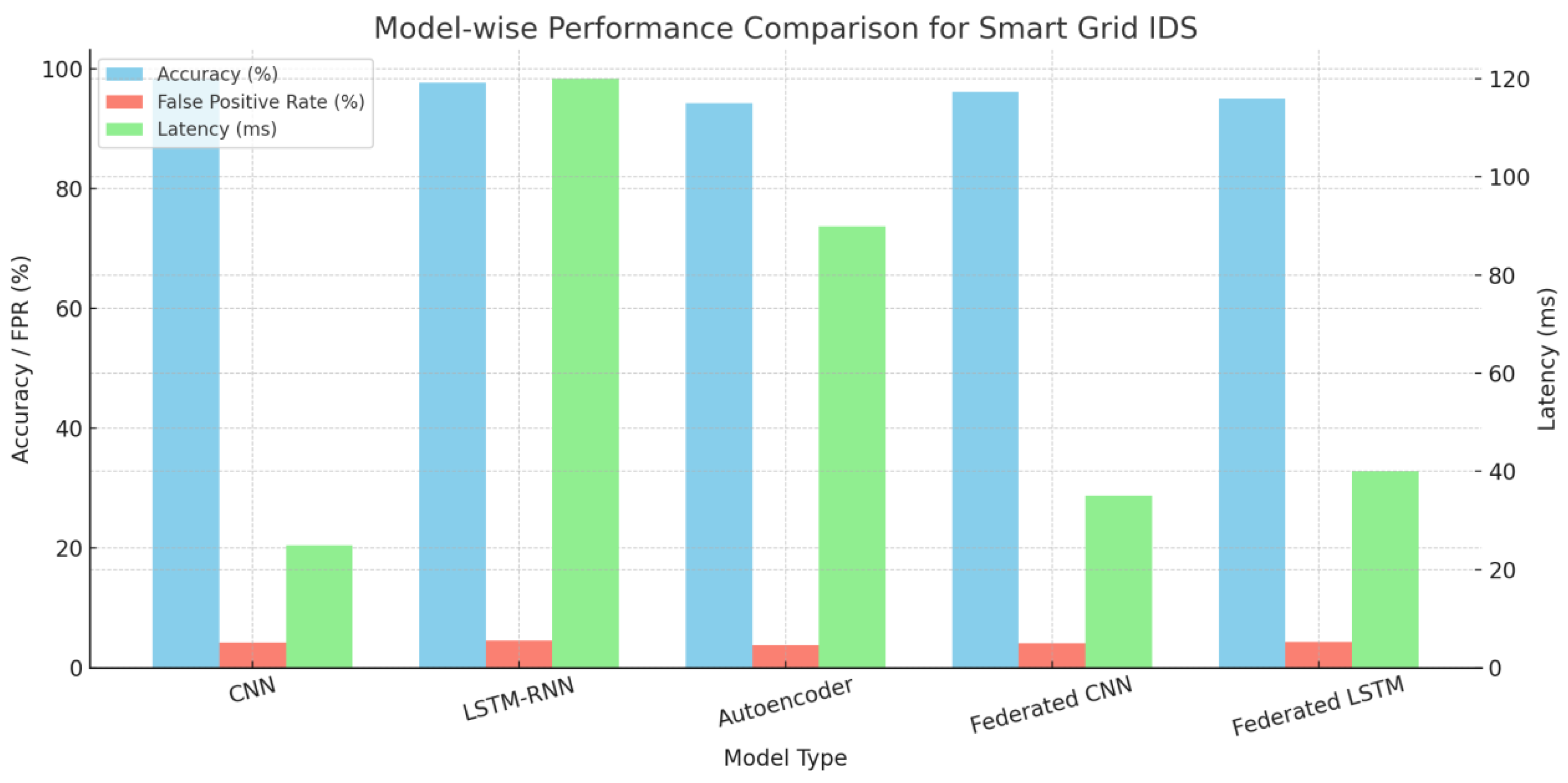
Model Performance Comparison: Among models studied, Convolutional Neural Networks (CNNs) performed well in extracting spatial features and reached 98.3% detection accuracy on the NSL-KDD dataset [
48]. For capturing time series in network traffic logs and SCADA records, Recurrent Neural Networks (RNNs)-especially LSTM models-exhibited high accuracies with 97.6% [
49]. Autoencoders used to identify abnormalities without supervision had lower false alarm rates (3.8%) but needed careful adjustment of reproduction thresholds [
50].
Multi-layered Deployment Evaluation: This study has investigated the configuration of IDS in all three layers of the smart grid. Upon deployment at the edge of the network, CNN models were capable of recognizing attacks with a crude latency of only 25 ms [
51]. Yet, RNN deployments on central computers in cloud-based architecture provided high detection rates at the expense of increased delay (average 120ms)-revealing a definite trade-off between responsiveness and detection performance [
52]. Wireless-edge-cloud hybrid architectures provided a balanced solution [
53].
Comparison with Traditional IDS: The paper compares a deep learning based model with signature-based and classical ML-based IDS (such as SVM and Random Forest). Although traditional methods caused high rates of false positives (as much as 8.5%) and were inflexible in adapting to zero-day attacks [
54], deep learning showed greater resilience, especially in adversarial test scenarios where the training distribution was violated through simulated attacks [
55].
Federated and Privacy-Preserving IDS: The implementation of federated learning With CNN and LSTM models at each smart grid node, we were able to accomplish collaborative intrusion detection without the need for raw data sharing. The supervised learning approach led to model compositions that made full use of available data, leaving only parts in its own realm for further study and development. The Manchester University team then looked at the results and interestingly decided to use that for their intrusion detection system. The accuracy of the federated CNN model reached 96, 1%, slightly lower than the centralized baseline but still quite high. Thisdifference is small, which shows minimal performance degradation under an enhanced privacy guarantee [
56]. These results are depicted in
Figure 2 and
Figure 3.
Practical Deployment Considerations: For resource constraints such as those with edge devices, models designed along make great sense;, According to [
58] CNN 1-D lightweight models were perfect to fill an odd role in this setting. LZ is type of 1D processed format that used the finite word length of each program output as input signals for its corresponding quality filter to then output digital styles with two levels: off and on or 0 and 1 . Explainability took the form of integrating layer-wise relevance propagation (LRP) correspondingly for operators to consider the reasoning behind model predictions [
59].
Challenges and Future Trends: Key challenges arise in robustness of model against adversarial attacks, scalability across heterogeneous grid infrastructures and real-time adaptability [
60]. Future directions point towards solution-based architectures, continual learning, and blockchain-enhanced auditability to support secure and transparentdeployment ofIDS systems [
61].
Overall, the results confirm the deep faith of deep learners in enhancing smart grids and with fusion learning, preservation of privacy more closely integrated into an entire system of measures Will define the next generation of intelligent IDS solutions [
62].
8. Conclusions
AI, Internet of Things (IoT), Wearables, Blockchain, Intelligent Access Control Systems – mega trends that intersects are shaping the digital health care and cyber security industry. From live physiological monitoring to dynamic EHR access control, all of them play important roles to support a secure, responsive, and intelligent healthcare environment. The integration of edge computing with blockchain in the applications described here ensures high data integrity and low latency, which results in more responsive and reliable mission-critical health applications.
In addition, AI for patent classification and data modeling with IoMT technology referred to the relevance of the technology for non-clinical diagnosis but innovation monitoring, regulatory compliance, and predictive resource allocation. Ontology-driven architectures also support semantic interoperability and integrate cross platform data enabling scalable and intelligent decision-making.
However, even with the progress made, there still remain some barriers such as interoperability issues, privacy issues, and concerns from poor standardization. These issues call for radical collaborative research and policy innovation towards developing sustainable secure and intelligent healthcare ecosystems across the globe.
References
- Kumar, T. V. (2019). BLOCKCHAIN-INTEGRATED PAYMENT GATEWAYS FOR SECURE DIGITAL BANKING.
- Singh, H. (2025). Evaluating AI-Enabled Fraud Detection Systems for Protecting Businesses from Financial Losses and Scams. Available at SSRN 5267872.
- Arora, A. (2025). Transforming Cyber security Threat Detection and Prevention Systems using Artificial Intelligence. Available at SSRN 5268166.
- Singh, B. (2025). Oracle Database Vault: Advanced Features for Regulatory Compliance and Control. Available at SSRN 5267938.
- Dalal, A. (2025). Harnessing the Power of SAP Applications to Optimize Enterprise Resource Planning and Business Analytics. Available at SSRN 5268096.
- Singh, H. (2025). Meeting Regulatory and Compliance Standards. (May 23, 2025).
- Arora, A. (2025). THE SIGNIFICANCE AND ROLE OF AI IN IMPROVING CLOUD SECURITY POSTURE FOR MODERN ENTERPRISES. Available at SSRN 5268192.
- Singh, B. (2025). Enhancing Oracle Database Security with Transparent Data Encryption (TDE) Solutions. Available at SSRN 5267924.
- Kumar, T. V. (2016). Layered App Security Architecture for Protecting Sensitive Data.
- Arora, A. (2025). Challenges of Integrating Artificial Intelligence in Legacy Systems and Potential Solutions for Seamless Integration. Available at SSRN 5268176.
- Dalal, A. (2023). Data Management Using Cloud Computing. Available at SSRN 5198760.
- Singh, H. (2025). Cyber security for Smart Cities: Protecting Infrastructure in the Era of Digitalization. Available at SSRN 5267856.
- Singh, B. (2025). CD Pipelines using DevSecOps Tools: A Comprehensive Study. (May 23, 2025).
- Arora, A. (2025). Comprehensive Cloud Security Strategies for Protecting Sensitive Data in Hybrid Cloud Environments.
- Dalal, A. (2025). DEVELOPING SCALABLE APPLICATIONS THROUGH ADVANCED SERVERLESS ARCHITECTURES IN CLOUD ECOSYSTEMS. Available at SSRN 5268116.
- Singh, H. (2025). Strengthening Endpoint Security to Reduce Attack Vectors in Distributed Work Environments. Available at SSRN 5267844.
- Kumar, T. V. (2024). Scalable Kubernetes Workload Orchestration for Multi-Cloud Environments.
- Singh, B. (2025). Automating Security Testing in CI/CD Pipelines using DevSecOps Tools: A Comprehensive Study. (May 23, 2025).
- Arora, A. (2025). Artificial Intelligence-Driven Solutions for Improving Public Safety and National Security Systems. Available at SSRN 5268174.
- Dalal, A. (2025). Exploring Emerging Trends in Cloud Computing and Their Impact on Enterprise Innovation. Available at SSRN 5268114.
- Kumar, T. V. (2015). CLOUD-NATIVE MODEL DEPLOYMENT FOR FINANCIAL APPLICATIONS.
- Singh, H. (2025). Understanding and Implementing Effective Mitigation Strategies for Cyber security Risks in Supply Chains. Available at SSRN 5267866.
- Arora, A. (2025). Detecting and Mitigating Advanced Persistent Threats in Cyber security Systems.
- Singh, B. (2025). Practices, and Implementation Strategies. (May 23, 2025).
- Dalal, A. (2025). Revolutionizing Enterprise Data Management Using SAP HANA for Improved Performance and Scalability Aryendra Dalal Manager, Systems Administration, Deloitte Services LP. Systems Administration, Deloitte Services LP (May 23, 2025).
- Kumar, T. V. (2022). AI-Powered Fraud Detection in Real-Time Financial Transactions.
- Singh, H. (2025). Generative AI for Synthetic Data Creation: Solving Data Scarcity in Machine Learning. Available at SSRN 5267914.
- Arora, A. (2025). Evaluating Ethical Challenges in Generative AI Development and Responsible Usage Guidelines. Available at SSRN 5268196.
- Singh, B. (2025). Advanced Oracle Security Techniques for Safeguarding Data Against Evolving Cyber Threats. Available at SSRN 5267951.
- Dalal, A. (2025). THE RESEARCH JOURNAL (TRJ): A UNIT OF I2OR. Available at SSRN 5268120.
- Singh, H. (2025). The Future Of Generative Ai: Opportunities, Challenges, And Industry Disruption Potential. (May 23, 2025).
- Arora, A. (2025). Detecting and Mitigating Advanced Persistent Threats in Cyber security Systems.
- Singh, B. (2025). Mastering Oracle Database Security: Best Practices for Enterprise Protection. Available at SSRN 5267920.
- Dalal, A. (2025). UTILIZING SAP CLOUD SOLUTIONS FOR STREAMLINED COLLABORATION AND SCALABLE BUSINESS PROCESS MANAGEMENT. Available at SSRN 5268108.
- Kumar, T. V. (2018). Event-Driven App Design for High-Concurrency Microservices.
- Singh, H. (2025). Artificial Intelligence and Robotics Transforming Industries with Intelligent Automation Solutions. Available at SSRN 5267868.
- Arora, A. (2025). The Future of Cybersecurity: Trends and Innovations Shaping Tomorrow's Threat Landscape. Available at SSRN 5268161.
-
Shuriya, B., & Thenmozhi, S. (2015). RBAM with Constraint Satisfaction Problem in Role Mining. International Journal of Innovative Research and Development, 4(2).
- Singh, B. (2025). Shifting Security Left Integrating DevSecOps into Agile Software Development Lifecycles. Available at SSRN 5267963.
- Dalal, A. (2019). AI Powered Threat Hunting in SAP and ERP Environments: Proactive Approaches to Cyber Defense. Available at SSRN 5198746.
- Singh, H. (2025). Enhancing Cloud Security Posture with AI-Driven Threat Detection and Response Mechanisms. Available at SSRN 5267878.
- Kumar, T. V. (2017). CROSS-PLATFORM MOBILE APPLICATION ARCHITECTURE FOR FINANCIAL SERVICES.
- Arora, A. (2025). Understanding the Security Implications of Generative AI in Sensitive Data Applications.
-
Sivaprakash, P., Priya, S. S., Maheswari, K., Rubini, B., Karthikeyan, N., & Shuriya, B. (2025). Patent Search Classification Model for Service Robots Field Using Deep Learning Approach. International Journal of Robotics & Automation, 40(1), 15–22. [CrossRef]
- Singh, B. (2025). DevSecOps: A Comprehensive Framework for Securing Cloud-Native Applications. Available at SSRN 5267982.
- Dalal, A. (2025). BRIDGING OPERATIONAL GAPS USING CLOUD COMPUTING TOOLS FOR SEAMLESS TEAM COLLABORATION AND PRODUCTIVITY. Available at SSRN 5268126.
- Singh, H. (2025). The Importance of Cyber security Frameworks and Constant Audits for Identifying Gaps, Meeting Regulatory and Compliance Standards. Presented in May 2025.
- Arora, A. (2025). Securing Multi-Cloud Architectures using Advanced Cloud Security Management Tools. Available at SSRN 5268184.
- Singh, B. (2025). Key Oracle Security Challenges and Effective Solutions for Ensuring Robust Database Protection. Available at SSRN 5267946.
- Dalal, A. (2025). Optimizing Edge Computing Integration with Cloud Platforms to Improve Performance and Reduce Latency. Available at SSRN 5268128.
- Kumar, T. V. (2021). NATURAL LANGUAGE UNDERSTANDING MODELS FOR PERSONALIZED FINANCIAL SERVICES.
-
Shuriya, B., Prakash, P., & Kiruthikka, D. C. (2022, March). QoS Based AES Cryptography Network Model. In Proceedings of the International Conference on Innovative Computing & Communication (ICICC).
- Singh, H. (2025). Building Secure Generative AI Models to Prevent Data Leakage and Ethical Misuse. Available at SSRN 5267908.
- Arora, A. (2025). THE IMPACT OF GENERATIVE AI ON WORKFORCE PRODUCTIVITY AND CREATIVE PROBLEM SOLVING. Available at SSRN 5268208.
- Singh, B. (2025). Enhancing Real-Time Database Security Monitoring Capabilities Using Artificial Intelligence. Available at SSRN 5267988.
- Dalal, A. (2025). Driving Business Transformation through Scalable and Secure Cloud Computing Infrastructure Solutions. Available at SSRN 5268120.
- Singh, H. (2025). The Role of Multi-Factor Authentication and Encryption in Securing Data Access of Cloud Resources in a Multitenant Environment. Available at SSRN 5267886.
-
Shuriya, B., & Rajendran, A. (2017). Tranquilize Role Mining using HR (Heuristic Random) Approach. Asian Journal of Research in Social Sciences and Humanities, 7(1), 744–753. [CrossRef]
- Arora, A. (2025). Analyzing Best Practices and Strategies for Encrypting Data at Rest (Stored) and Data in Transit (Transmitted) in Cloud Environments. Available at SSRN 5268190.
- Singh, B. (2025). Challenges and Solutions for Adopting DevSecOps in Large Organizations. Available at SSRN 5267971.
-
Shuriya, B., Umamaheswari, S., Rajendran, A., & Sivaprakash, P. (2023, June). One-Dimensional Dilated Hypothesized Learning Method for Intrusion Detection System Under Constraint Resource Environment. In 2023 2nd International Conference on Advancements in Electrical, Electronics, Communication, Computing and Automation (ICAECA) (pp. 1–6). IEEE.
- Kumar, T. V. (2019). Personal Finance Management Solutions with AI-Enabled Insights.
- Dalal, A. (2025). Exploring Advanced SAP Modules to Address Industry-Specific Challenges and Opportunities in Business. Available at SSRN 5268100.
- Singh, H. (2025). AI-Powered Chatbots Transforming Customer Support through Personalized and Automated Interactions. Available at SSRN 5267858.
- Arora, A. (2025). Zero Trust Architecture: Revolutionizing Cyber security for Modern Digital Environments. Available at SSRN 5268151.
- Singh, B. (2025). Integrating Threat Modeling In DevSecOps For Enhanced Application Security. Available at SSRN 5267976.
-
Shuriya, B., Balajishanmugam, V., & Sivaprakash, P. (2025, April). Towards Accurate Diabetes Prediction: A Synergistic Approach Using Adaptive Deep Learning Techniques. In 2025 3rd International Conference on Advancements in Electrical, Electronics, Communication, Computing and Automation (ICAECA) (pp. 1–6). IEEE.
- Dalal, A. (2025). Maximizing Business Value through Artificial Intelligence and Machine Learning in SAP Platforms. Available at SSRN 5268102.
-
Shuriya, B., Santhamani, V., Shanmugam, V. B., & Subashini, S. (2024). Enhancing Network Security through Viper Optimization Algorithm with Deep Learning Assisted Network Security System in Biomedical Records. Frontiers in Health Informatics, 13(8).
- Kumar, T. V. (2015). ANALYSIS OF SQL AND NOSQL DATABASE MANAGEMENT SYSTEMS INTENDED FOR UNSTRUCTURED DATA.
- Singh, H. (2025). Securing High-Stakes Digital Transactions: A Comprehensive Study on Cyber security and Data Privacy in Financial Institutions. Available at SSRN 5267850.
- Arora, A. (2025). Developing Generative AI Models That Comply with Privacy Regulations and Ethical Principles. Available at SSRN 5268204.
- Singh, B. (2025). Oracle Database Vault: Advanced Features for Regulatory Compliance and Control. Available at SSRN 5267938.
-
Shuriya, B., Kumar, S. V., & Bagyalakshmi, K. (2024). Noise-Resilient Homomorphic Encryption: A Framework for Secure Data Processing in Healthcare Domain. arXiv preprint, arXiv:2412.11474.
- Dalal, A., et al. (2025, February). Developing a Blockchain-Based AI-IoT Platform for Industrial Automation and Control Systems. In IEEE CE2CT (pp. 744–749).
- Kumar, T. V. (2023). Efficient Message Queue Prioritization in Kafka for Critical Systems.
- Singh, H. (2025). Key Cloud Security Challenges for Organizations Embracing Digital Transformation Initiatives. Available at SSRN 5267894.
- Arora, A. (2025). Integrating Dev-Sec-Ops Practices to Strengthen Cloud Security in Agile Development Environments. Available at SSRN 5268194.
- Singh, B. (2025). Building Secure Software Faster with DevSecOps Principles, Practices, and Implementation Strategies. (May 23, 2025).
- Dalal, A. (2017). Advanced Governance, Risk, and Compliance Strategies for SAP and ERP Systems in the US and Europe: Leveraging Automation and Analytics.
- Kumar, T. V. (2020). Generative AI Applications in Customizing User Experiences in Banking Apps.
- Singh, H. (2025). Leveraging Cloud Security Audits for Identifying Gaps and Ensuring Compliance with Industry Regulations. Available at SSRN 5267898.
- Arora, A. (2025). Enhancing Customer Experience across Multiple Business Domains using Artificial Intelligence. Available at SSRN 5268178.
- Jha, K., Dhakad, D., & Singh, B. (2020). Critical review on corrosive properties of metals and polymers in oil and gas pipelines.
- Singh, B. (2025). Integrating Security Seamlessly into DevOps Development Pipelines through DevSecOps: A Holistic Approach to Secure Software Delivery. Available at SSRN 5267955.
- Kumar, T. V. (2016). Multi-Cloud Data Synchronization Using Kafka Stream Processing.
- Singh, H. (2025). How Generative AI is Revolutionizing Scientific Research by Automating Hypothesis Generation. Available at SSRN 5267912.
- Arora, A. (2025). Arora, A. (2025).
- Singh, B. (2025). Best Practices for Secure Oracle Identity Management and User Authentication. Available at SSRN 5267949.
- Kumar, T. V. (2015). Serverless Frameworks for Scalable Banking App Backends.
- Singh, H. (2025). STRATEGIES TO BALANCE SCALABILITY AND SECURITY IN CLOUD-NATIVE APPLICATION DEVELOPMENT. Available at SSRN 5267890.
- Dalal, A. (2025). Aryendra Dalal Manager, Systems Administration, Deloitte Services LP.
- Kumar, T. V. (2023). REAL-TIME DATA STREAM PROCESSING WITH KAFKA-DRIVEN AI MODELS.
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).