Submitted:
20 April 2023
Posted:
21 April 2023
You are already at the latest version
Abstract
Keywords:
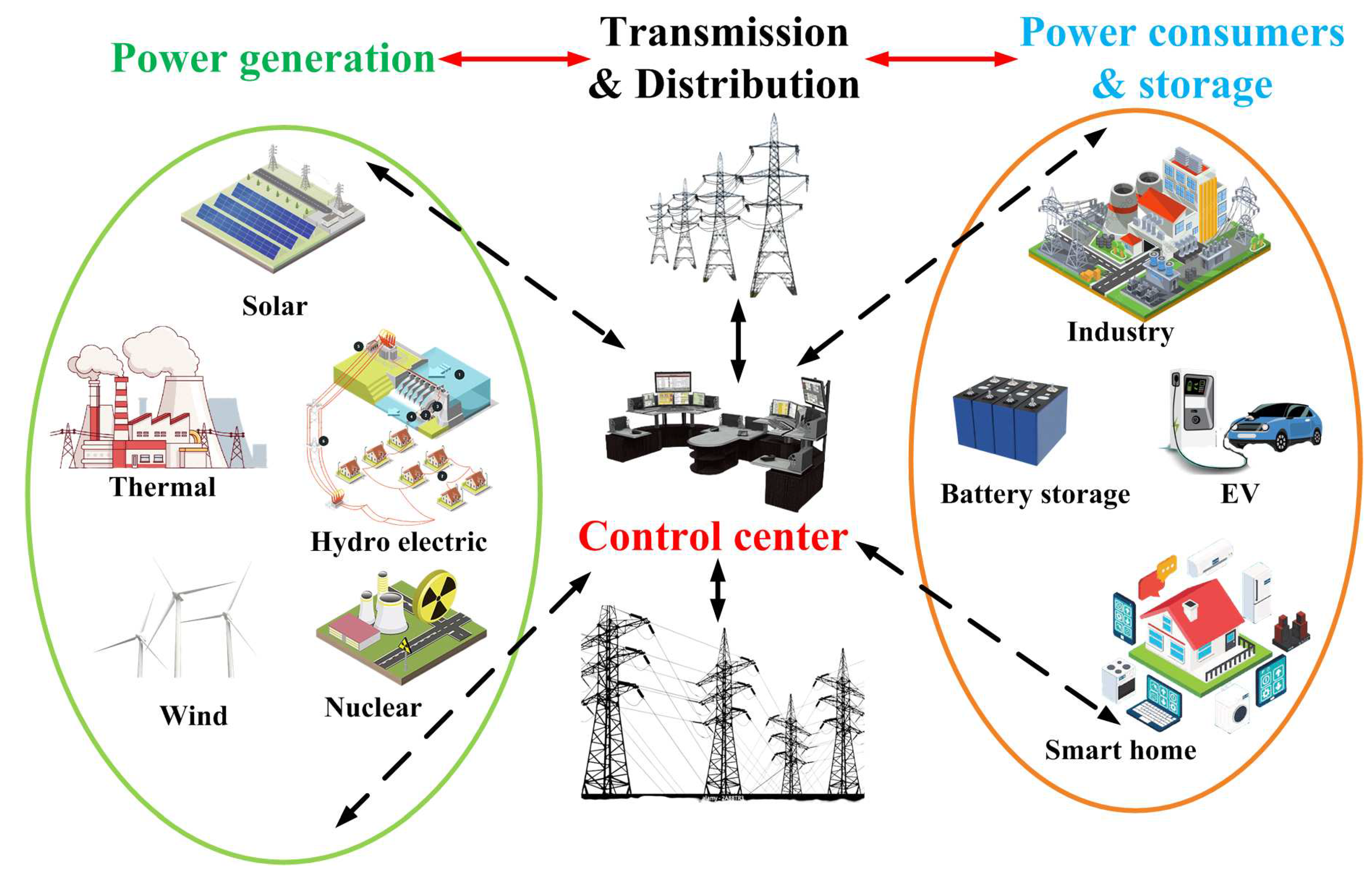
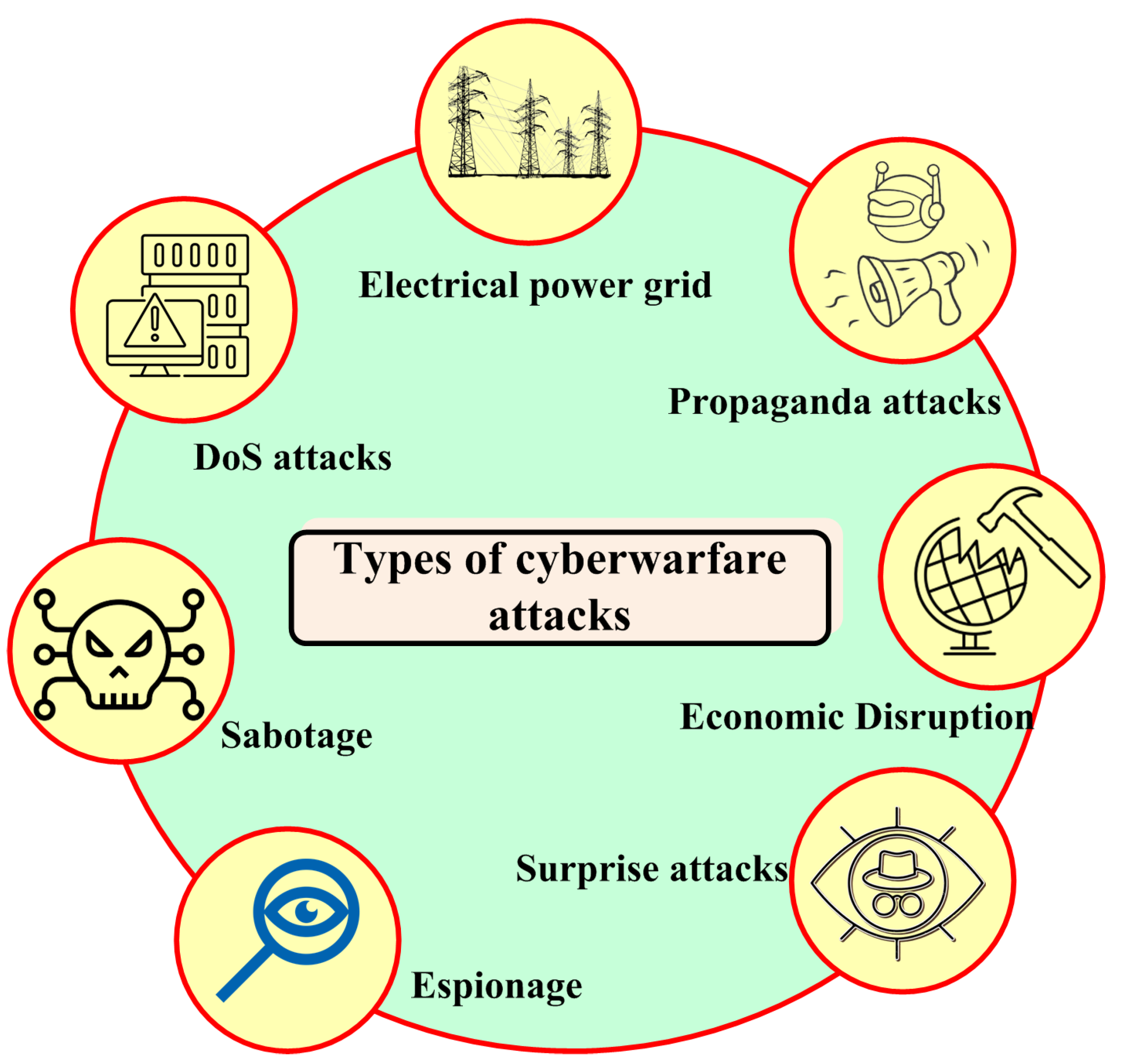
1. Introduction
2. Real-World Cyber Attack Scenarios
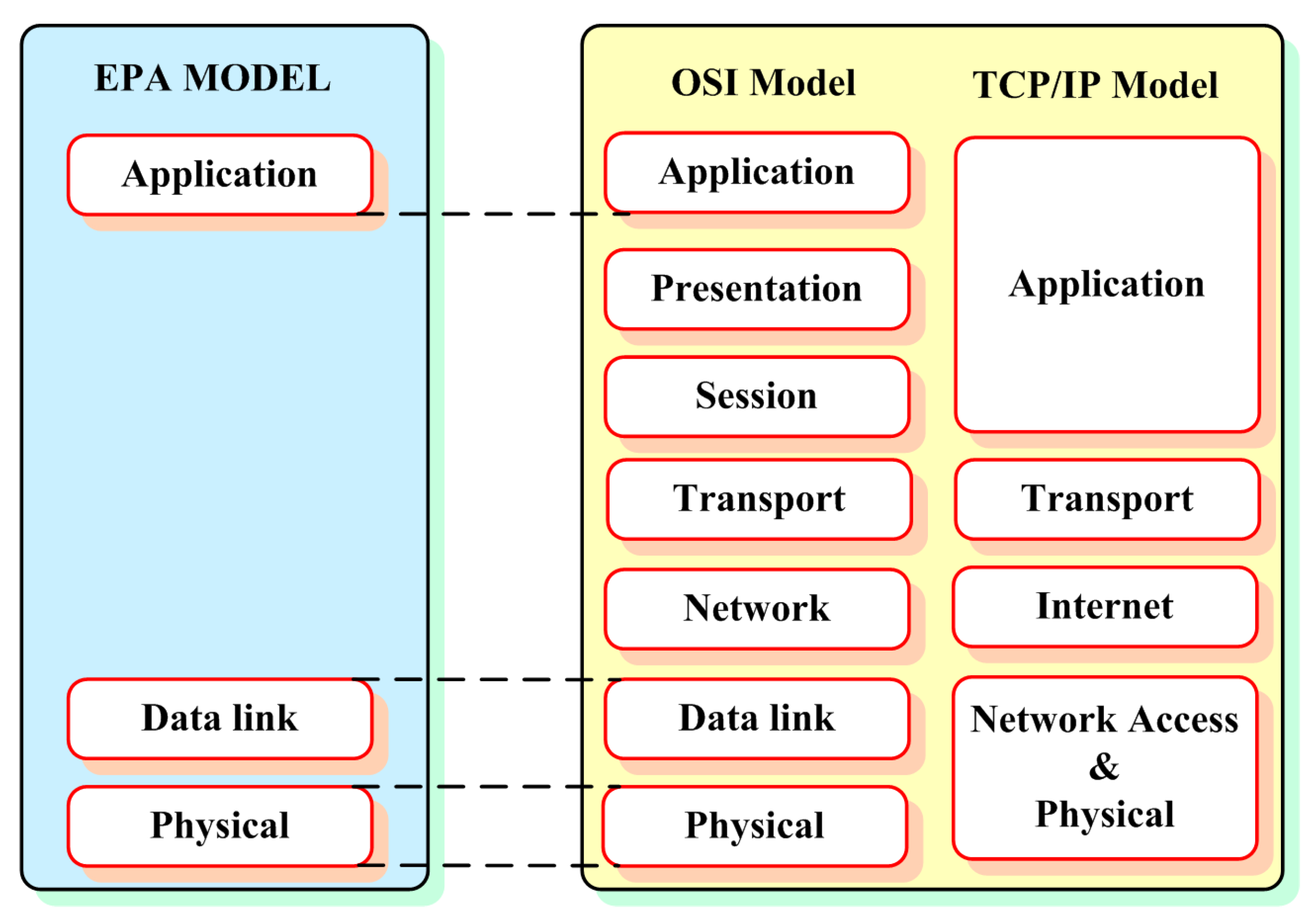
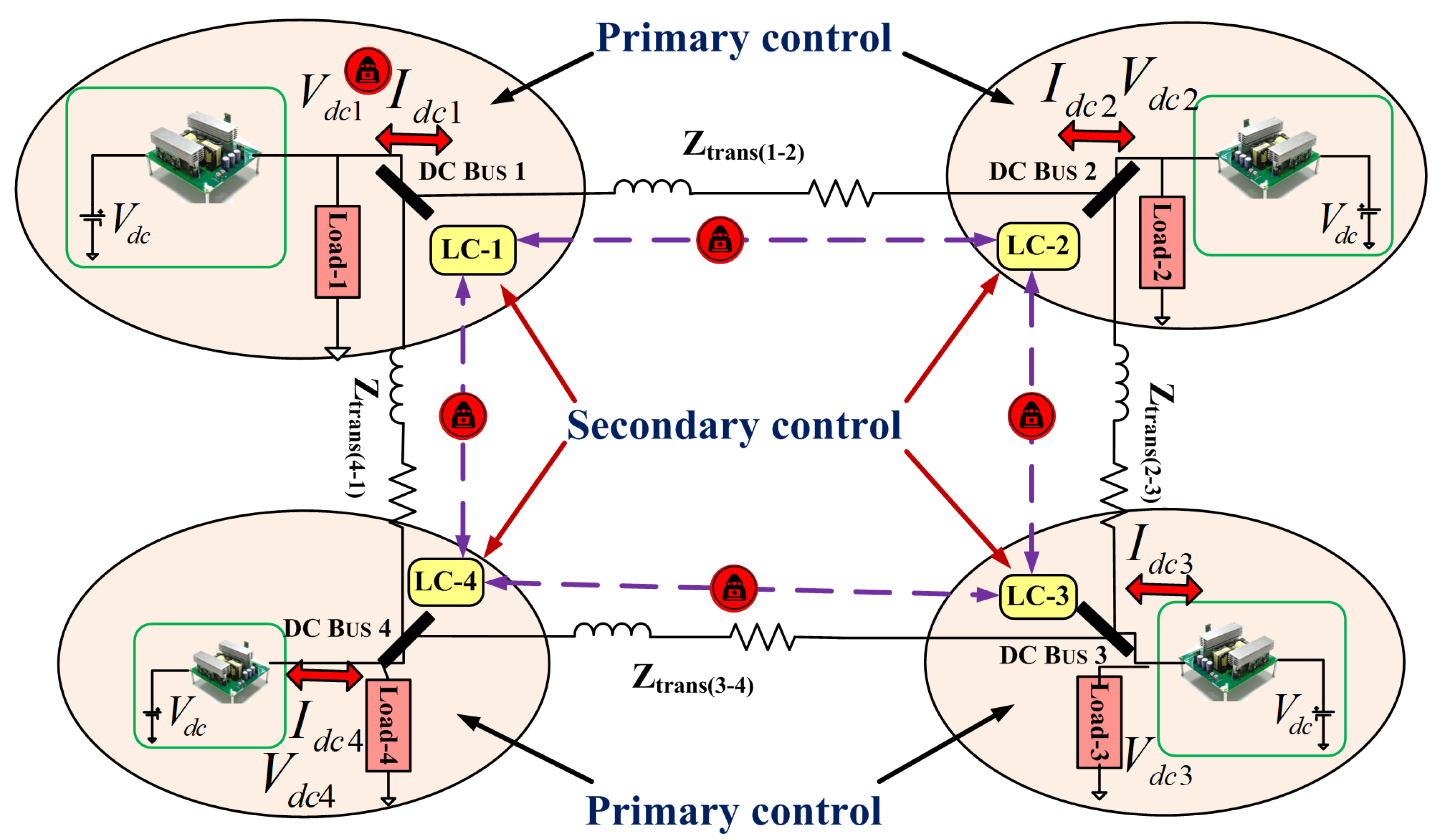
3. DC Microgrid Control and Architecture
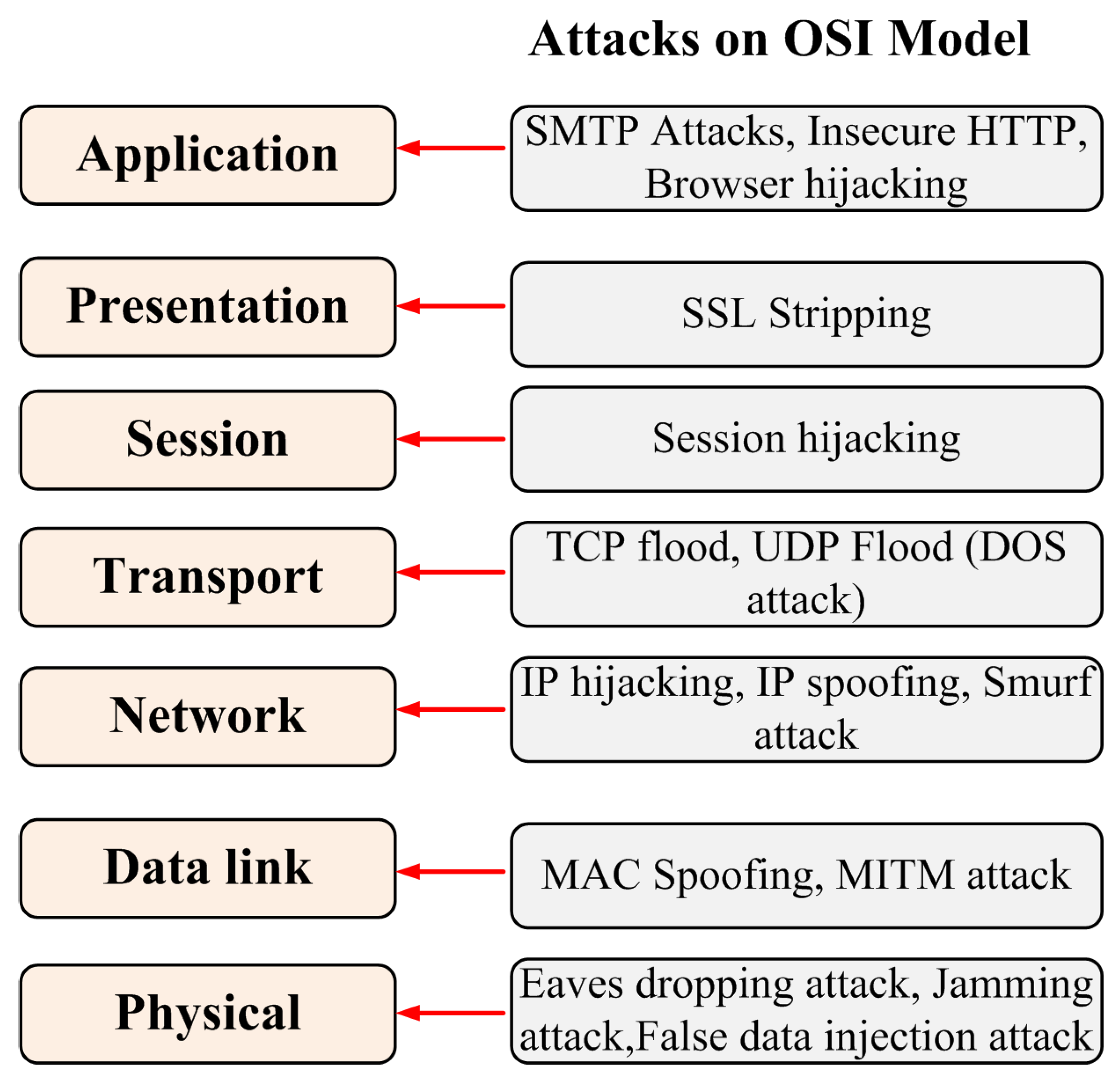
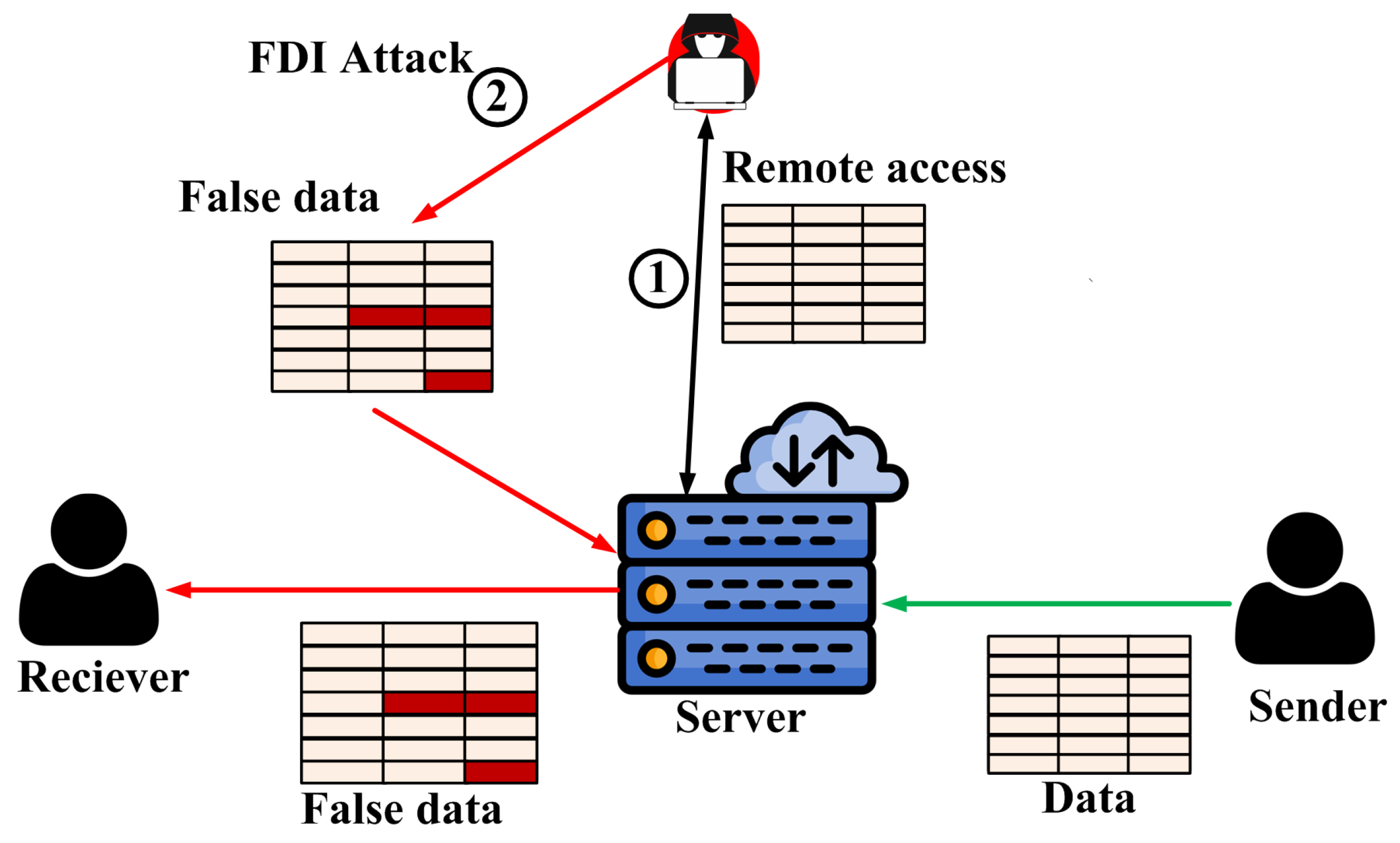
3.1. False Data Injection Attacks
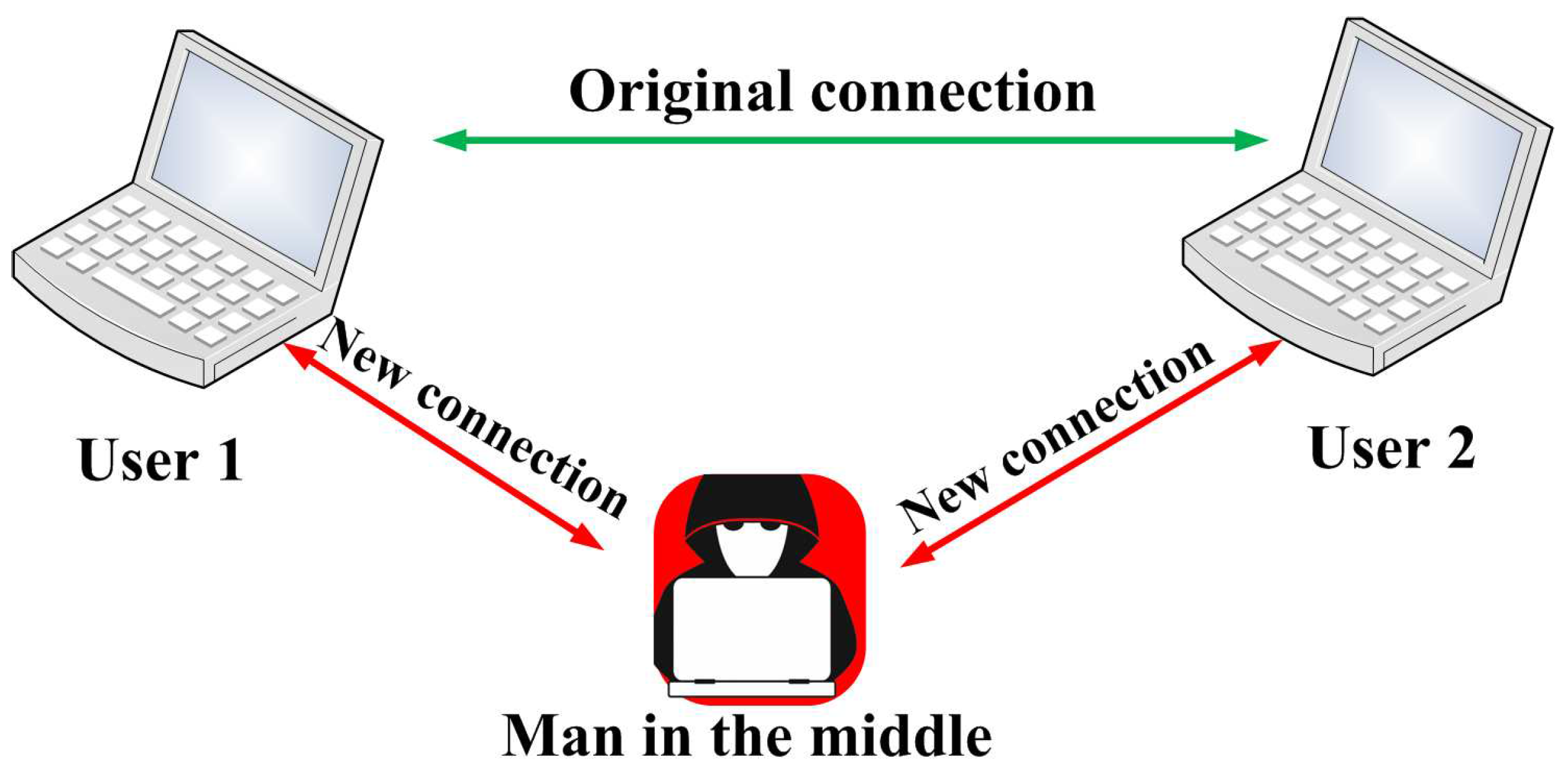
3.2. Man in the Middle Attack
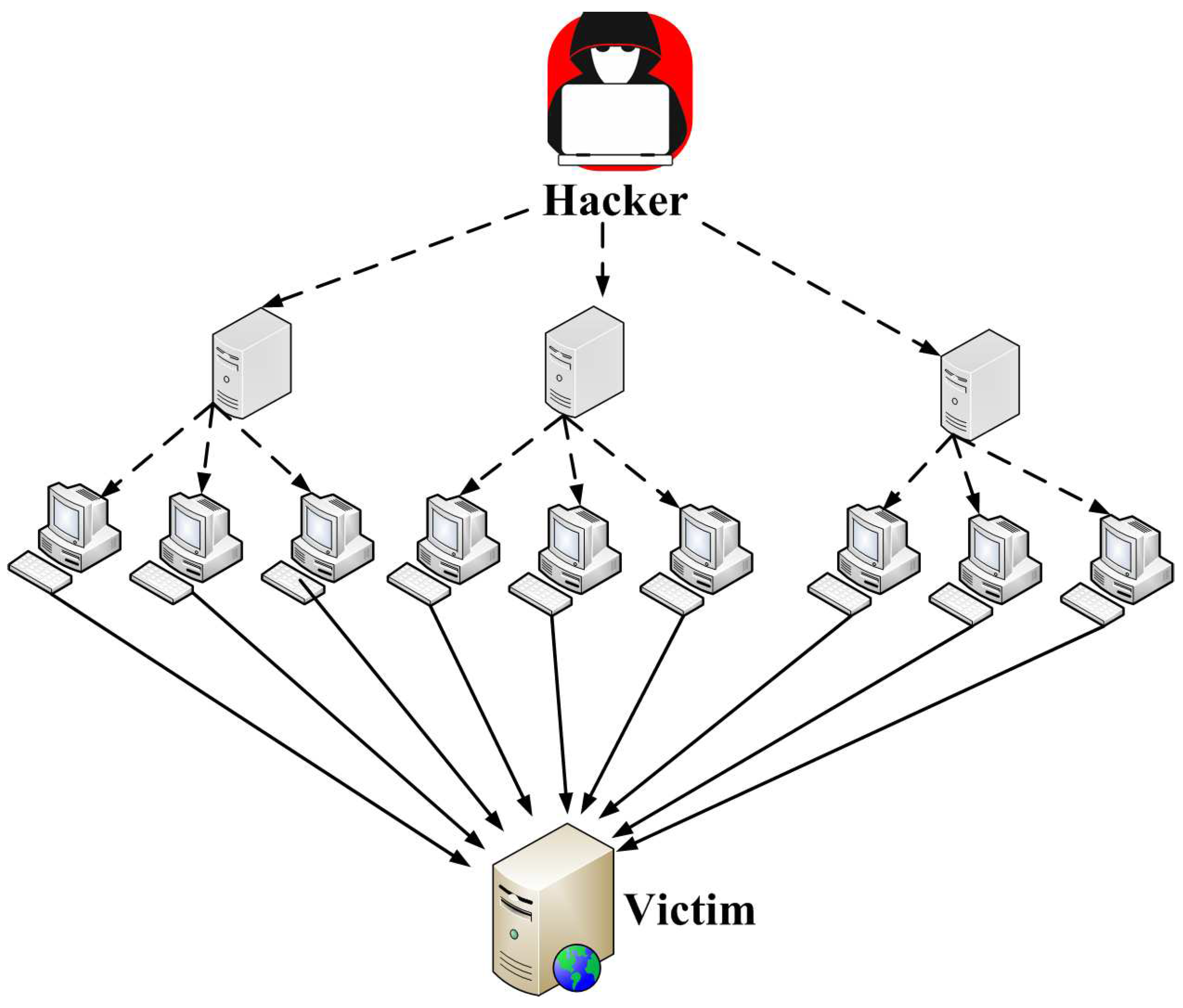
3.3. Denial of Service Attack
4. Defense Mechanisms
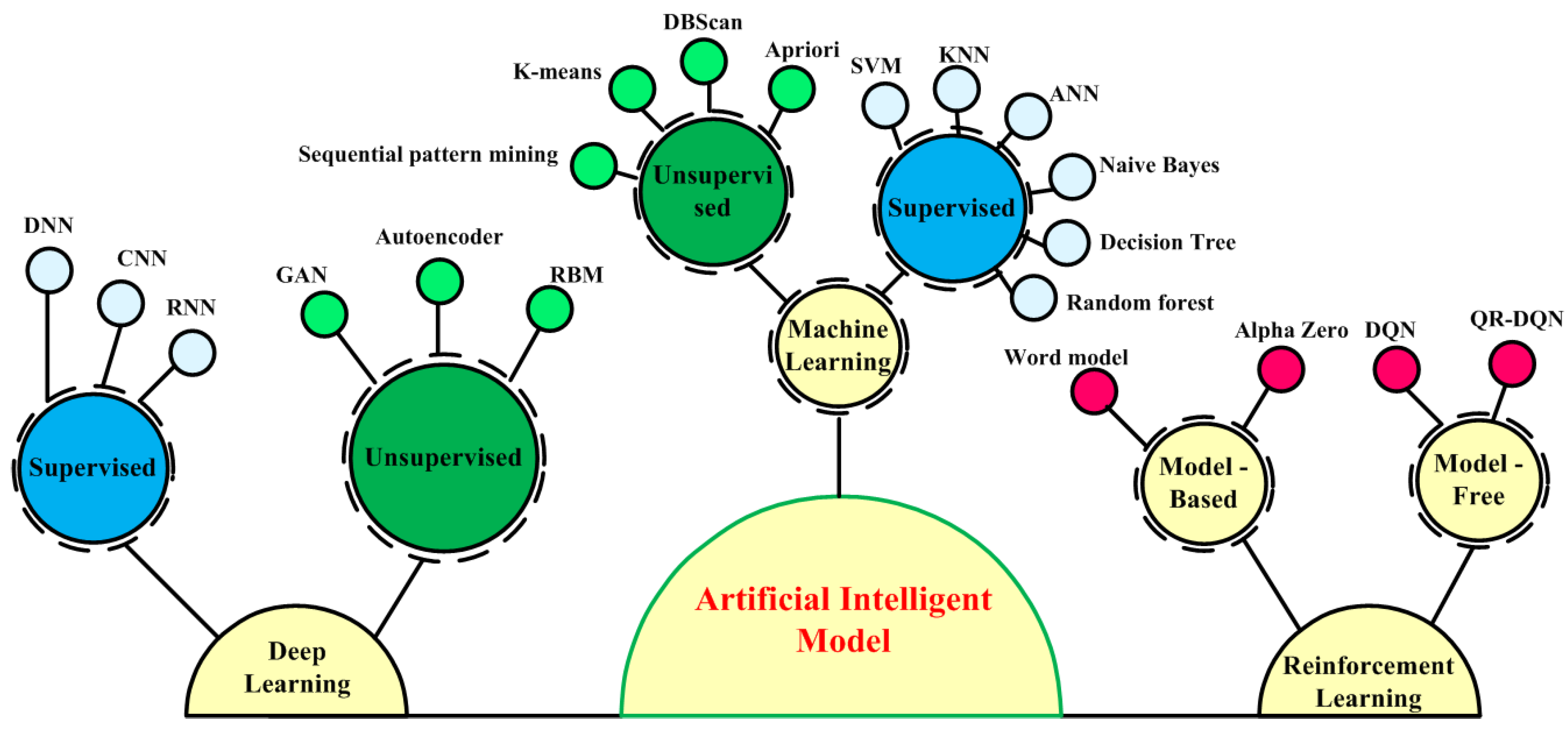
4.1. Artificial Intelligence for Cyber Security
5. Case Study of Stealth Fdi Attack on DC-DC Converter
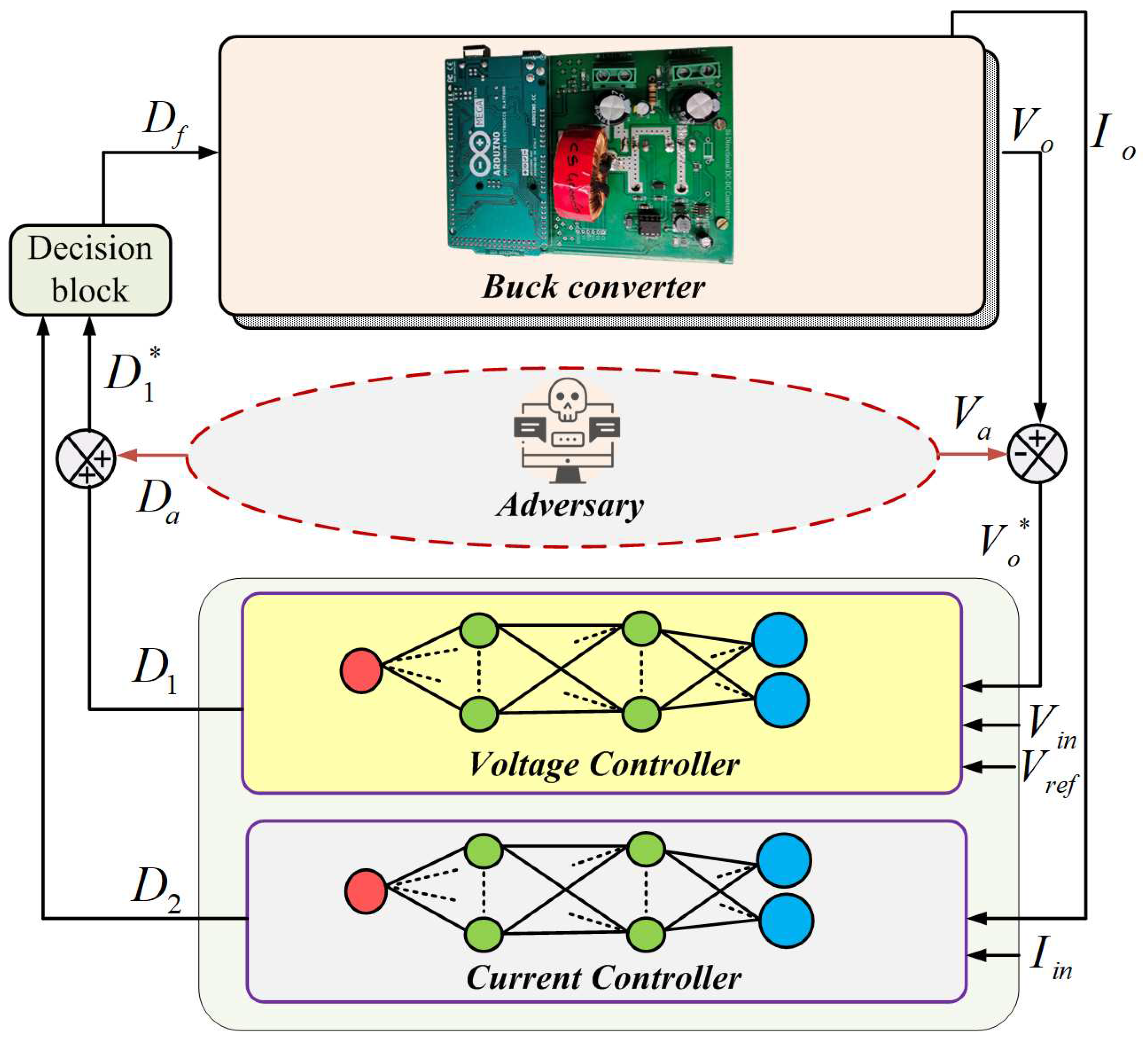
5.1. Proposed Methodology
5.1.1. Modelling of Stealth Local Covert Fdi Attack (Slca-Fdia)
5.1.2. Deep Learning Controller Design
- A set of training examples is collected.
- Design the deep learning model architecture by determining the hyperparameters such as the number of hidden layers, the number of hidden neurons in each layer and the learning rate.
- Initialization of weights and biases.
- Determining the training parameters of the model such as activation function, optimizer and loss function.
- Train the model with training data.
- Evaluate the deep learning model with testing data.
- Deploy the trained deep learning model.
5.1.3. Detection and Mitigation of SLCA-FDIA
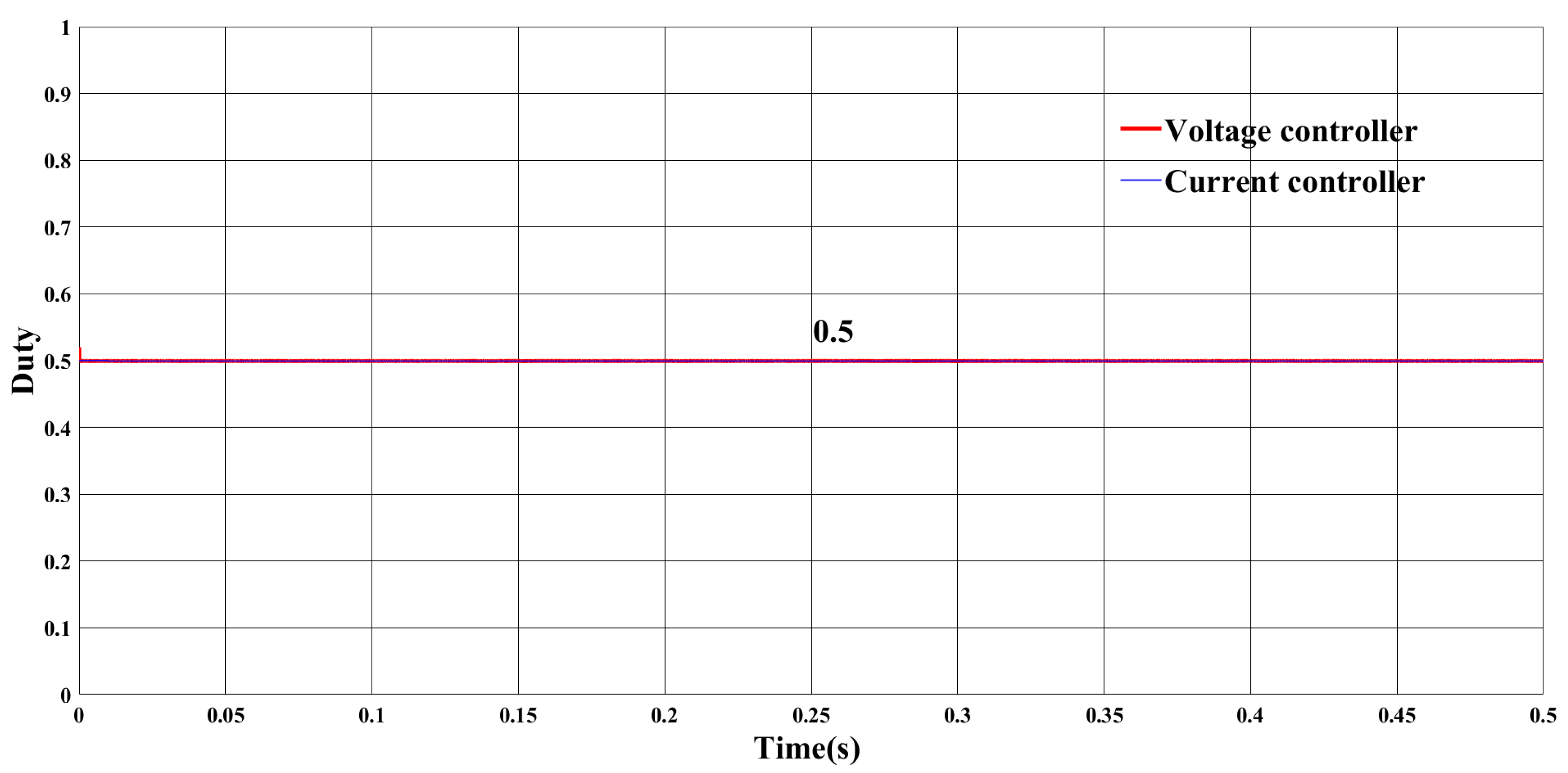
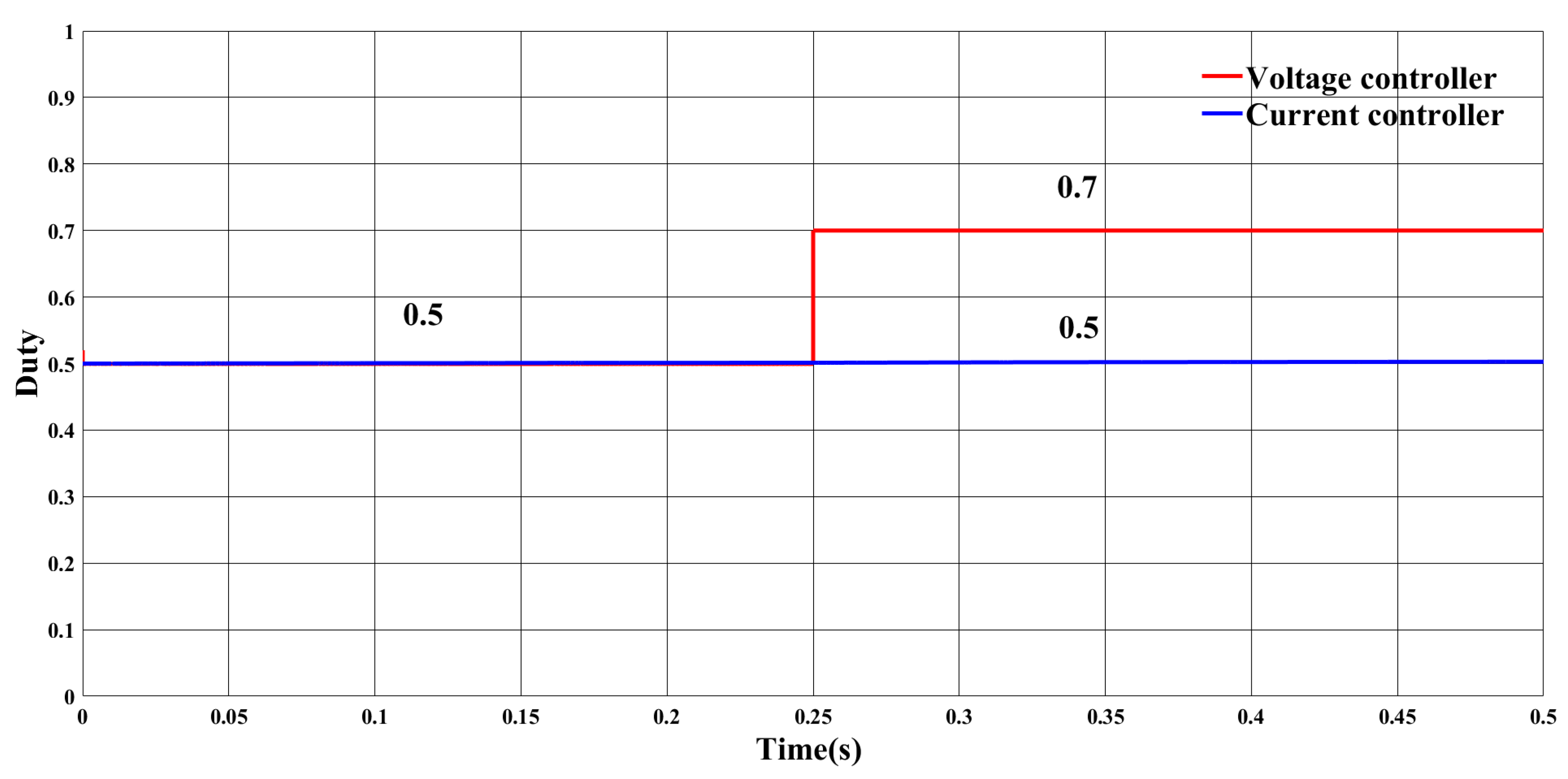
5.2. Simulation Results
5.2.1. FDI Attack on Output Voltage Sensor
5.2.2. FDI Attack on Input Voltage Sensor
5.2.3. FDI Attack on Input Voltage Sensor and Stealth Attack
5.3. Hardware Implementation
6. Conclusion
Funding
Abbreviations
| ARP | Address resolution protocol |
| CCS | Change cipher spec |
| CPS | Cyber-physical systems |
| DARPA | Defense advanced research projects agency |
| DNS | Domain name server |
| EAP | Extensible authentication protocol |
| EV | Electric vehicle |
| HTTP | Hypertext transfer protocol |
| HTTPS | Hypertext transfer protocol secure |
| IP | Internet protocol |
| KDD99 | Knowledge discovery in databases 1999 |
| MAC | Media access control |
| OSI | open system interconnection |
| PLC | Programmable logical controller |
| RES | Renewable energy sources |
| SSL | Secure socket layer |
| TCP | Transfer control protocol |
| FDI | False data injection |
| SLCA | Stealthy local covert attack |
References
- Bong, C.P.; Hashim, H.; Ho, W.S.; Ab Muis, Z.B.; Yunus, N.A.B.; Demoral, A.; Tirta, A.; Kresnawan, M.R.; Safrina, R.; Rosalia, S.A. Integration of Variable Renewable Energy, Electric Vehicle, and Smart Microgrid in ASEAN: A Focus Group Discussion Approach. In Proceedings of the IOP Conference Series: Earth and Environmental Science. IOP Publishing, 2022, Vol. 997, p. 012013. [CrossRef]
- Kulkarni, S.V.; Gaonkar, D.N. Operation and control of a microgrid in isolated mode with multiple distributed generation systems. In Proceedings of the 2017 International Conference on Technological Advancements in Power and Energy ( TAP Energy); 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Hossain, E.; Kabalcı, E.; Bayindir, R.; Perez, R. A comprehensive study on microgrid technology. International Journal of Renewable Energy Research 2014, 4, 1094–1104. [Google Scholar]
- Bani-Ahmed, S.; Weber, L.; Nasiri, A.; Hosseini, H. Microgrid communications: State of the art and future trends. 2015, pp. 780–785. [CrossRef]
- Kumar, S.; Islam, S.; Jolfaei, A. , Microgrid communications - protocols and standards; 2019; pp. 291–326. [CrossRef]
- Serban, I.; Céspedes, S.; Marinescu, C.; Azurdia-Meza, C.A.; Gómez, J.S.; Hueichapan, D.S. Communication Requirements in Microgrids: A Practical Survey. IEEE Access 2020, 8, 47694–47712. [Google Scholar] [CrossRef]
- Robinson, M.; Jones, K.; Janicke, H. Cyber warfare: Issues and challenges. Computers & Security 2015, 49, 70–94. [Google Scholar] [CrossRef]
- Zwilling, M.; Klien, G.; Lesjak, D.; Wiechetek, .; Cetin, F.; Basim, H.N. Cyber security awareness, knowledge and behavior: A comparative study. Journal of Computer Information Systems 2022, 62, 82–97. [CrossRef]
- Chasanah, B.; Candiwan, C. Analysis of College Students’ Cybersecurity Awareness In Indonesia. SISFORMA 2020, 7, 49. [Google Scholar] [CrossRef]
- Hong, W.C.H.; Chi, C.; Liu, J.; Zhang, Y.; Lei, V.N.L.; Xu, X. The influence of social education level on cybersecurity awareness and behaviour: a comparative study of university students and working graduates. Education and Information Technologies, 2022; 1–32. [Google Scholar] [CrossRef]
- Cyber security research report 2020, 2021.
- Freet, D.; Agrawal, R. , Cyber Espionage; 2017. [CrossRef]
- Schaefer, T.; Brown, B.; Graessle, F.; Salzsieder, L. Cybersecurity: common risks: a dynamic set of internal and external threats includes loss of data and revenue, sabotage at the hands of current or former employees, and a PR nightmare. Strategic Finance 2017, 99, 54–62. [Google Scholar]
- Hamid, A. Denial of Service Attacks: Tools and Categories. International Journal of Engineering Research and 2020, V9. [Google Scholar] [CrossRef]
- Nguyen, T.; Wang, S.; Alhazmi, M.; Nazemi, M.; Estebsari, A.; Dehghanian, P. Electric Power Grid Resilience to Cyber Adversaries: State of the Art. IEEE Access 2020, PP, 1–1. [Google Scholar] [CrossRef]
- Goswami, M. , Fake News and Cyber Propaganda: A Study of Manipulation and Abuses on Social Media; 2018; pp. 535–544.
- Eling, M.; Elvedi, M.; Falco, G. The economic impact of extreme cyber risk scenarios. North American Actuarial Journal 2022, pp. 1–15. [CrossRef]
- Collins, S.; McCombie, S. Stuxnet: the emergence of a new cyber weapon and its implications. Journal of Policing, Intelligence and Counter Terrorism 2012, 7, 80–91. [Google Scholar] [CrossRef]
- Dehlawi, Z.; Abokhodair, N. Saudi Arabia’s response to cyber conflict: A case study of the Shamoon malware incident. 2013, pp. 73–75. [CrossRef]
- Guo, Q.; Xin, S.; Wang, J. Comprehensive security assessment for a cyber physical energy system: a lesson from Ukraine’s blackout. Dianli Xitong Zidonghua/Automation of Electric Power Systems 2016, 40, 145–147. [Google Scholar] [CrossRef]
- Cherepanov, A.; Lipovsky, R. Blackenergy–what we really know about the notorious cyber attacks. Virus Bulletin October 2016. [Google Scholar]
- Halevi, T.; Memon, N.; Nov, O. Spear-Phishing in the Wild: A Real-World Study of Personality, Phishing Self-Efficacy and Vulnerability to Spear-Phishing Attacks. SSRN Electronic Journal 2015. [Google Scholar] [CrossRef]
- Cherepanov, A.; Lipovsky, R. Industroyer: Biggest threat to industrial control systems since Stuxnet. WeLiveSecurity, ESET 2017, 12. [Google Scholar]
- Dudley, R.; Golden, D. The colonial pipeline ransomware hackers had a secret weapon: self-promoting cybersecurity firms. MIT Technology Review and ProPublica 2021. [Google Scholar]
- Khoshnood, A. The Attack on Natanz and the JCPOA. BESA Center Perspectives Paper 2021. [Google Scholar]
- Espina, E.; Llanos, J.; Burgos-Mellado, C.; Cárdenas-Dobson, R.; Martínez-Gómez, M.; Sáez, D. Distributed Control Strategies for Microgrids: An Overview. IEEE Access 2020, 8, 193412–193448. [Google Scholar] [CrossRef]
- Nasirian, V.; Moayedi, S.; Davoudi, A.; Lewis, F.L. Distributed Cooperative Control of DC Microgrids. IEEE Transactions on Power Electronics 2015, 30, 2288–2303. [Google Scholar] [CrossRef]
- Tan, S.; Wu, Y.; Xie, P.; Guerrero, J.M.; Vasquez, J.C.; Abusorrah, A. New challenges in the design of microgrid systems: Communication networks, cyberattacks, and resilience. IEEE Electrification Magazine 2020, 8, 98–106. [Google Scholar] [CrossRef]
- Liang, G.; Zhao, J.; Luo, F.; Weller, S.; Dong, Z. A Review of False Data Injection Attacks Against Modern Power Systems. IEEE Transactions on Smart Grid 2016, 8, 1–1. [Google Scholar] [CrossRef]
- Halfond, W.G.; Viegas, J.; Orso, A.; et al. A.; et al. A classification of SQL-injection attacks and countermeasures. In Proceedings of the Proceedings of the IEEE international symposium on secure software engineering.; pp. 2006113–15.
- Endler, D. The evolution of cross site scripting attacks. Technical report, Technical report, iDEFENSE Labs, 2002.
- Wlazlo, P.; Sahu, A.; Mao, Z.; Huang, H.; Goulart, A.; Davis, K.; Zonouz, S. Man-in-the-middle attacks and defence in a power system cyber-physical testbed. IET Cyber-Physical Systems: Theory & Applications 2021, 6, 164–177. [Google Scholar]
- Ali, F. IP spoofing. The Internet Protocol Journal 2007, 10, 1–9. [Google Scholar]
- Whalen, S. An introduction to arp spoofing. Node99 [Online Document].
- Steinhoff, U.; Wiesmaier, A.; Araújo, R. The state of the art in DNS spoofing. In Proceedings of the Proc. 4th Intl. Conf. Applied Cryptography and Network Security (ACNS); 2006. [Google Scholar]
- Gangan, S. A review of man-in-the-middle attacks. arXiv 2015, arXiv:1504.02115. [Google Scholar]
- Elleithy, K.M.; Blagovic, D.; Cheng, W.K.; Sideleau, P. Denial of service attack techniques: analysis, implementation and comparison 2005.
- Long, N.; Thomas, R. Trends in denial of service attack technology. CERT Coordination Center 2001, 648, 651. [Google Scholar]
- Lau, F.; Rubin, S.H.; Smith, M.H.; Trajkovic, L. Distributed denial of service attacks. In Proceedings of the Smc 2000 conference proceedings. 2000 ieee international conference on systems, man and cybernetics.’cybernetics evolving to systems, humans, organizations, and their complex interactions’(cat. no. 0. IEEE, 2000, Vol. 3, pp. 2275–2280.
- Neupane, K.; Haddad, R.; Chen, L. Next generation firewall for network security: a survey. In Proceedings of the SoutheastCon 2018. IEEE; 2018; pp. 1–6. [Google Scholar]
- Liao, H.J.; Lin, C.H.R.; Lin, Y.C.; Tung, K.Y. Intrusion detection system: A comprehensive review. Journal of Network and Computer Applications 2013, 36, 16–24. [Google Scholar] [CrossRef]
- Khraisat, A.; Gondal, I.; Vamplew, P.; Kamruzzaman, J. Survey of intrusion detection systems: techniques, datasets and challenges. Cybersecurity 2019, 2, 1–22. [Google Scholar] [CrossRef]
- Ioulianou, P.; Vasilakis, V.; Moscholios, I.; Logothetis, M. A signature-based intrusion detection system for the internet of things. Information and Communication Technology Form 2018. [Google Scholar]
- Gyanchandani, M.; Rana, J.; Yadav, R. Taxonomy of anomaly based intrusion detection system: a review. International Journal of Scientific and Research Publications 2012, 2, 1–13. [Google Scholar]
- Wang, Z.; Li, X. Intrusion prevention system design. In Proceedings of the Proceedings of the International Conference on Information Engineering and Applications (IEA) 2012: Volume 3.; pp. 2013375–382.
- Zhang, Z.; Ning, H.; Shi, F.; Farha, F.; Xu, Y.; Xu, J.; Zhang, F.; Choo, K.K.R. Artificial intelligence in cyber security: research advances, challenges, and opportunities. Artificial Intelligence Review 2022, pp. 1–25.
- Shrestha Chitrakar, A.; Petrović, S. Efficient k-means using triangle Efficient k-means using triangle inequality on spark for cyber security analytics. In Proceedings of the Proceedings of the ACM international workshop on security and privacy analytics, 2019, pp. 37–45on spark for cyber security analytics. [CrossRef]
- Husák, M.; Kašpar, J.; Bou-Harb, E.; Čeleda, P. On the sequential pattern and rule mining in the analysis of cyber security alerts. In Proceedings of the Proceedings of the 12th International Conference on Availability, Reliability and Security, 2017, pp. 1–10. [CrossRef]
- Azeez, N.A.; Ayemobola, T.J.; Misra, S.; Maskeliūnas, R.; Damaševičius, R. Network intrusion detection with a hashing based apriori algorithm using Hadoop MapReduce. Computers 2019, 8, 86. [Google Scholar] [CrossRef]
- Aung, Y.Y.; Min, M.M. Hybrid intrusion detection system using K-means and K-nearest neighbors algorithms. In Proceedings of the 2018 IEEE/ACIS 17th International Conference on Computer and Information Science (ICIS). IEEE, 2018, pp. 34–38. [CrossRef]
- Majeed, R.; Abdullah, N.A.; Mushtaq, M.F. IoT-based Cyber-security of Drones using the Naïve Bayes Algorithm. International Journal of Advanced Computer Science and Applications 2021, 12. [Google Scholar] [CrossRef]
- Meyer, D.; Wien, F. Support vector machines. The Interface to libsvm in package e1071 2015, 28, 20. [Google Scholar]
- Al-Omari, M.; Rawashdeh, M.; Qutaishat, F.; Alshira’H, M.; Ababneh, N. An intelligent tree-based intrusion detection model for cyber security. Journal of Network and Systems Management 2021, 29, 1–18. [Google Scholar] [CrossRef]
- Rahman, C.M.; Farid, D.M.; Harbi, N.; Bahri, E.; Rahman, M.Z. Attacks classification in adaptive intrusion detection using decision tree 2010.
- Ferrag, M.A.; Maglaras, L.; Ahmim, A.; Derdour, M.; Janicke, H. Rdtids: Rules and decision tree-based intrusion detection system for internet-of-things networks. Future internet 2020, 12, 44. [Google Scholar] [CrossRef]
- Choubisa, M.; Doshi, R.; Khatri, N.; Hiran, K.K. A simple and robust approach of random forest for intrusion detection system in cyber security. In Proceedings of the 2022 International Conference on IoT and Blockchain Technology (ICIBT). IEEE, 2022, pp. 1–5. 2022; 1–5. [Google Scholar] [CrossRef]
- Chen, Z.; Zhou, L.; Yu, W. ADASYN- Random Forest Based Intrusion Detection Model. In Proceedings of the 2021 4th International Conference on Signal Processing and Machine Learning, 2021, pp. 152–159. [CrossRef]
- Apruzzese, G.; Andreolini, M.; Colajanni, M.; Marchetti, M. Hardening random forest cyber detectors against adversarial attacks. IEEE Transactions on Emerging Topics in Computational Intelligence 2020, 4, 427–439. [Google Scholar] [CrossRef]
- Shrestha, A.; Mahmood, A. Review of deep learning algorithms and architectures. IEEE access 2019, 7, 53040–53065. [Google Scholar] [CrossRef]
- Bapiyev, I.M.; Aitchanov, B.H.; Tereikovskyi, I.A.; Tereikovska, L.A.; Korchenko, A.A. Deep neural networks in cyber attack detection systems. International Journal of Civil Engineering and Technology (IJCIET) 2017, 8, 1086–1092. [Google Scholar]
- Zhou, L.; Ouyang, X.; Ying, H.; Han, L.; Cheng, Y.; Zhang, T. Cyber-attack classification in smart grid via deep neural network. In Proceedings of the Proceedings of the 2nd international conference on computer science and application engineering, 2018, pp. 1–5. [CrossRef]
- Jemal, I.; Haddar, M.A.; Cheikhrouhou, O.; Mahfoudhi, A. Performance evaluation of Convolutional Neural Network for web security. Computer Communications 2021, 175, 58–67. [Google Scholar] [CrossRef]
- Alabadi, M.; Celik, Y. Anomaly detection for cyber-security based on convolution neural network: A survey. In Proceedings of the 2020 International Congress on Human-Computer Interaction, Optimization and Robotic Applications (HORA). IEEE, 2020, pp. 1–14. [CrossRef]
- Tang, T.A.; McLernon, D.; Mhamdi, L.; Zaidi, S.A.R.; Ghogho, M. Intrusion detection in sdn-based networks: Deep recurrent neural network approach. Deep Learning Applications for Cyber Security 2019, pp. 175–195. [CrossRef]
- Feltus, C. Learning algorithm recommendation framework for IS and CPS security: Analysis of the RNN, LSTM, and GRU contributions. International Journal of Systems and Software Security and Protection (IJSSSP) 2022, 13, 1–23. [Google Scholar] [CrossRef]
- Tasneem, S.; Gupta, K.D.; Roy, A.; Dasgupta, D. Generative Adversarial Networks (GAN) for Cyber Security: Challenges and Opportunities.
- Chen, D.; Wawrzynski, P.; Lv, Z. Cyber security in smart cities: a review of deep learning-based applications and case studies. Sustainable Cities and Society 2021, 66, 102655. [Google Scholar] [CrossRef]
- Yousefi-Azar, M.; Varadharajan, V.; Hamey, L.; Tupakula, U. Autoencoder-based feature learning for cyber security applications. In Proceedings of the 2017 International joint conference on neural networks (IJCNN). IEEE; 2017; pp. 3854–3861. [Google Scholar]
- Li, C.; Qiu, M.; Li, C. Reinforcement Learning for Cybersecurity. Reinf. Learn. Cyber-Phys. Syst 2019, pp. 155–168.
- Amor, N.B.; Benferhat, S.; Elouedi, Z. Naive bayes vs decision trees in intrusion detection systems. In Proceedings of the Proceedings of the 2004 ACM symposium on Applied computing, 2004, pp. 420–424. [CrossRef]
- Amiri, F.; Yousefi, M.R.; Lucas, C.; Shakery, A.; Yazdani, N. Mutual information-based feature selection for intrusion detection systems. Journal of Network and Computer Applications 2011, 34, 1184–1199. [Google Scholar] [CrossRef]
- Zhang, J.; Zulkernine, M.; Haque, A. Random-forests-based network intrusion detection systems. IEEE Transactions on Systems, Man, and Cybernetics, Part C (Applications and Reviews) 2008, 38, 649–659. [Google Scholar] [CrossRef]
- Ravipati, R.D.; Abualkibash, M. Intrusion detection system classification using different machine learning algorithms on KDD-99 and NSL-KDD datasets-a review paper. International Journal of Computer Science & Information Technology (IJCSIT) Vol 2019, 11. [Google Scholar]
- Gao, N.; Gao, L.; Gao, Q.; Wang, H. An intrusion detection model based on deep belief networks. In Proceedings of the 2014 Second international conference on advanced cloud and big data. IEEE; 2014; pp. 247–252. [Google Scholar]
- Choudhary, S.; Kesswani, N. Analysis of KDD-Cup’99, NSL-KDD and UNSW-NB15 datasets using deep learning in IoT. Procedia Computer Science 2020, 167, 1561–1573. [Google Scholar] [CrossRef]
- Ahsan, M.; Nygard, K.E. Convolutional Neural Networks with LSTM for Intrusion Detection. In Proceedings of the CATA, 2020, Vol. 69, pp. 69–79.
- Gurung, S.; Ghose, M.K.; Subedi, A. Deep learning approach on network intrusion detection system using NSL-KDD dataset. International Journal of Computer Network and Information Security 2019, 11, 8–14. [Google Scholar] [CrossRef]
- Ding, Y.; Zhai, Y. Intrusion detection system for NSL-KDD dataset using convolutional neural networks. In Proceedings of the Proceedings of the 2018 2nd International conference on computer science and artificial intelligence, 2018, pp. 81–85. [CrossRef]
- Amin, M.; El-Sousy, F.F.; Aziz, G.A.A.; Gaber, K.; Mohammed, O.A. CPS attacks mitigation approaches on power electronic systems with security challenges for smart grid applications: a review. IEEE Access 2021, 9, 38571–38601. [Google Scholar] [CrossRef]
- Cazorla, L.; Alcaraz, C.; Lopez, J. Cyber stealth attacks in critical information infrastructures. IEEE Systems Journal 2016, 12, 1778–1792. [Google Scholar] [CrossRef]
- Mikhaylenko, D.; Zhang, P. Stealthy local covert attacks on cyber-physical systems. IEEE Transactions on Automatic Control 2021. [Google Scholar]
- Sun, K.; Esnaola, I.; Perlaza, S.M.; Poor, H.V. Stealth attacks on the smart grid. IEEE Transactions on Smart Grid 2019, 11, 1276–1285. [Google Scholar] [CrossRef]
- Annavaram, D.; Sahoo, S.; Mishra, S. Stealth Attacks in Microgrids: Modeling Principles and Detection. In Proceedings of the 2021 9th IEEE International Conference on Power Systems (ICPS). IEEE; 2021; pp. 1–6. [Google Scholar]
- Pasetti, M.; Ferrari, P.; Bellagente, P.; Sisinni, E.; de Sá, A.O.; do Prado, C.B.; David, R.P.; Machado, R.C.S. Artificial neural network-based stealth attack on battery energy storage systems. IEEE Transactions on Smart Grid 2021, 12, 5310–5321. [Google Scholar] [CrossRef]
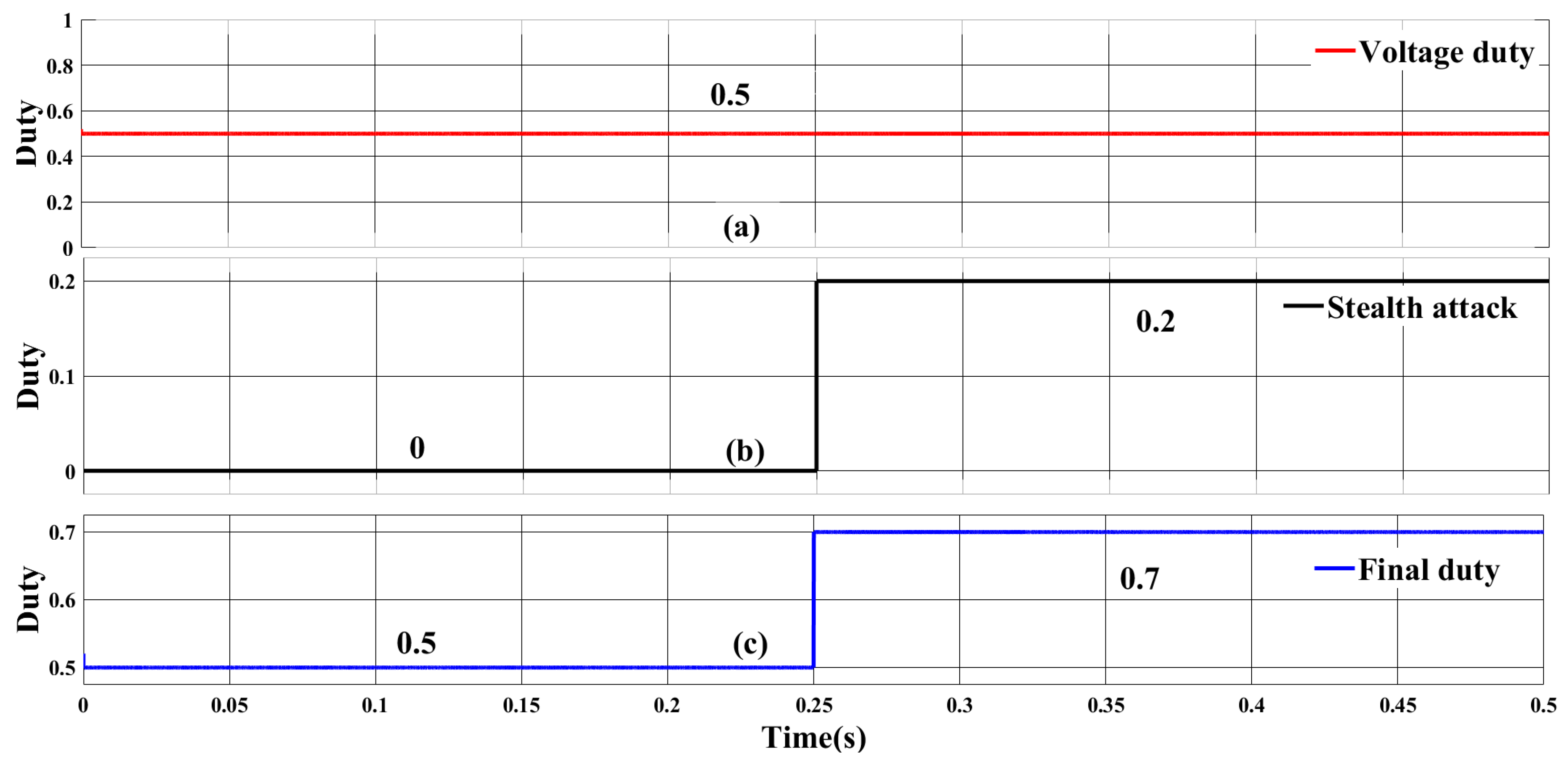
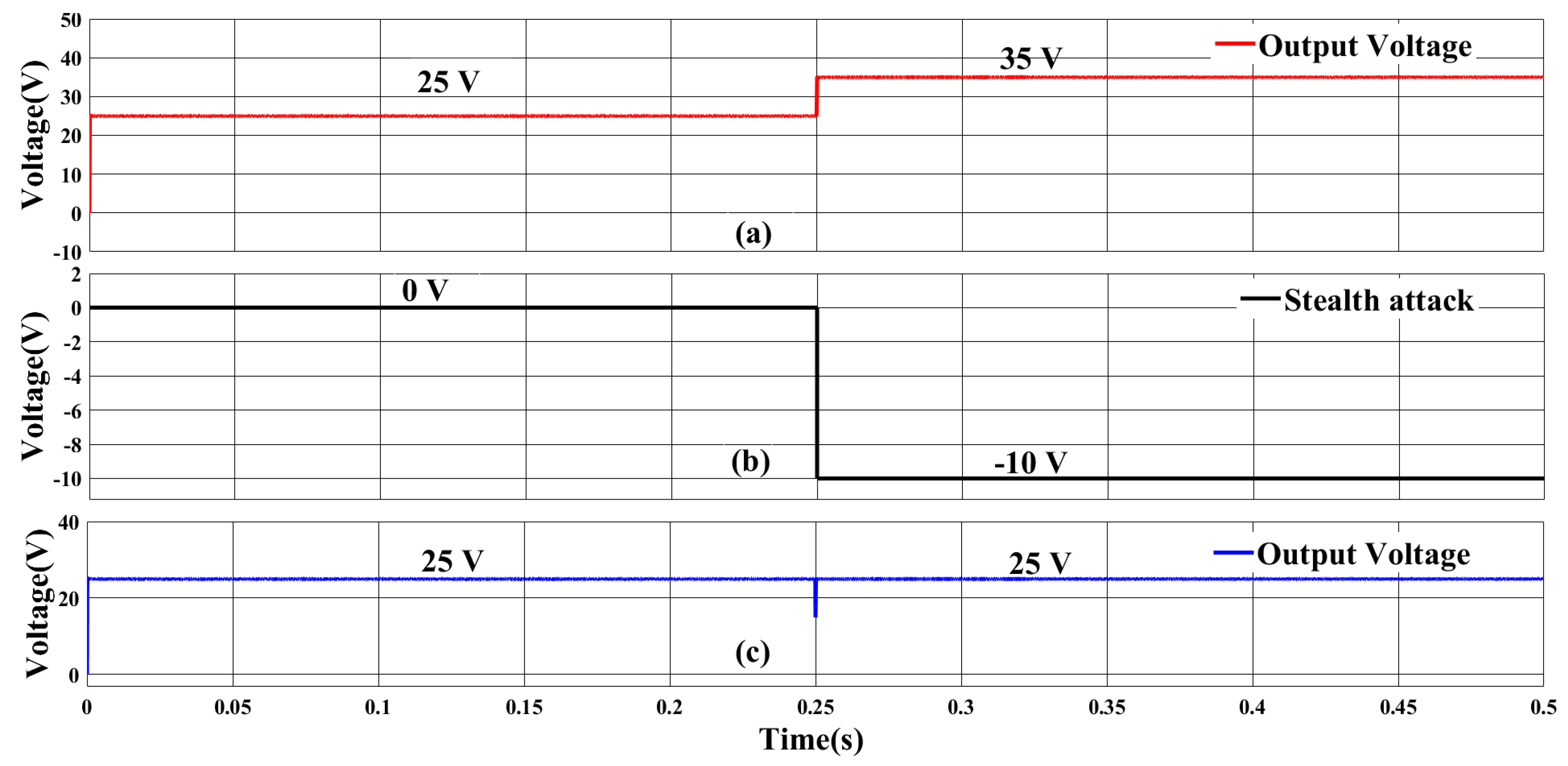
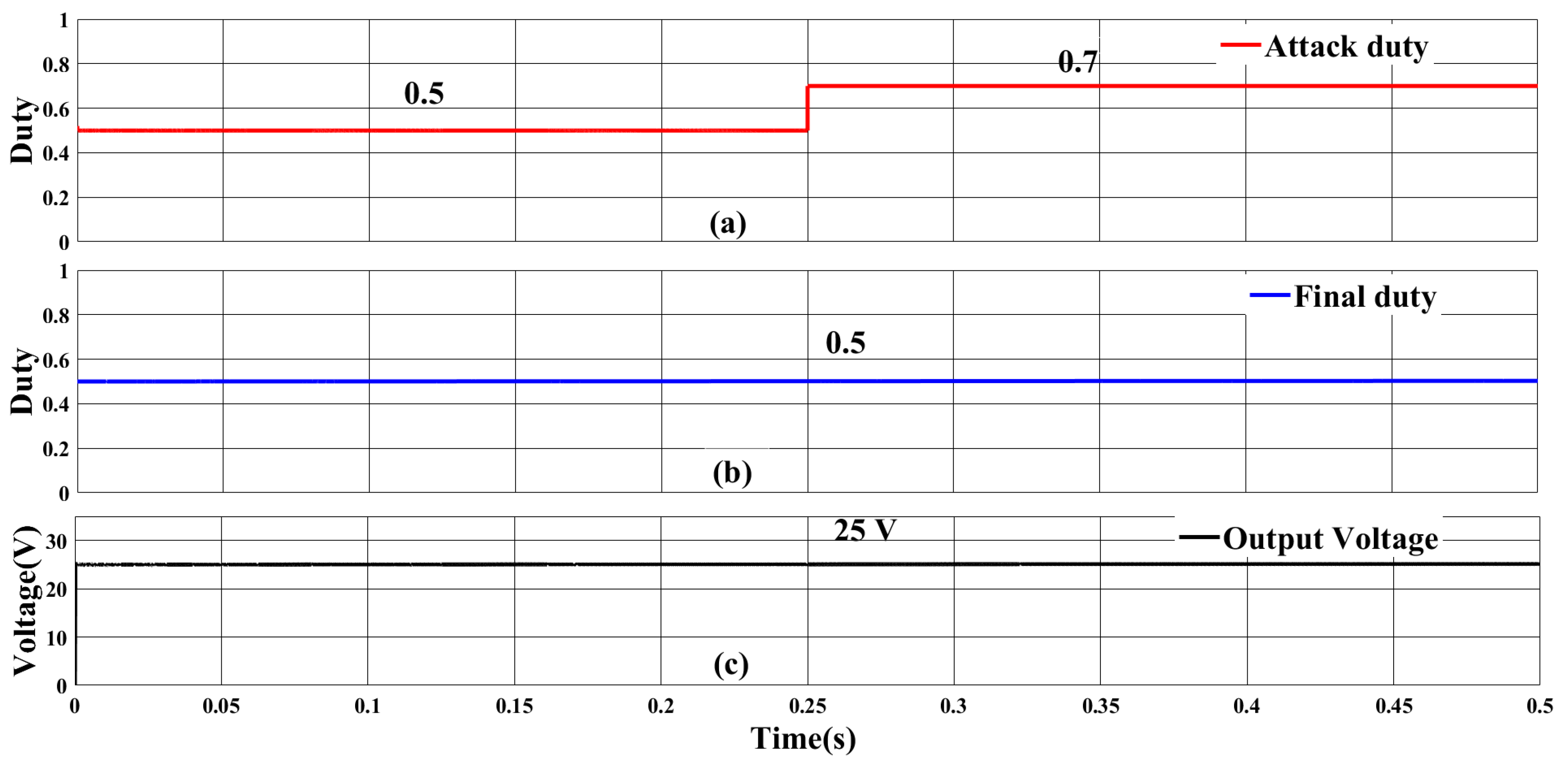
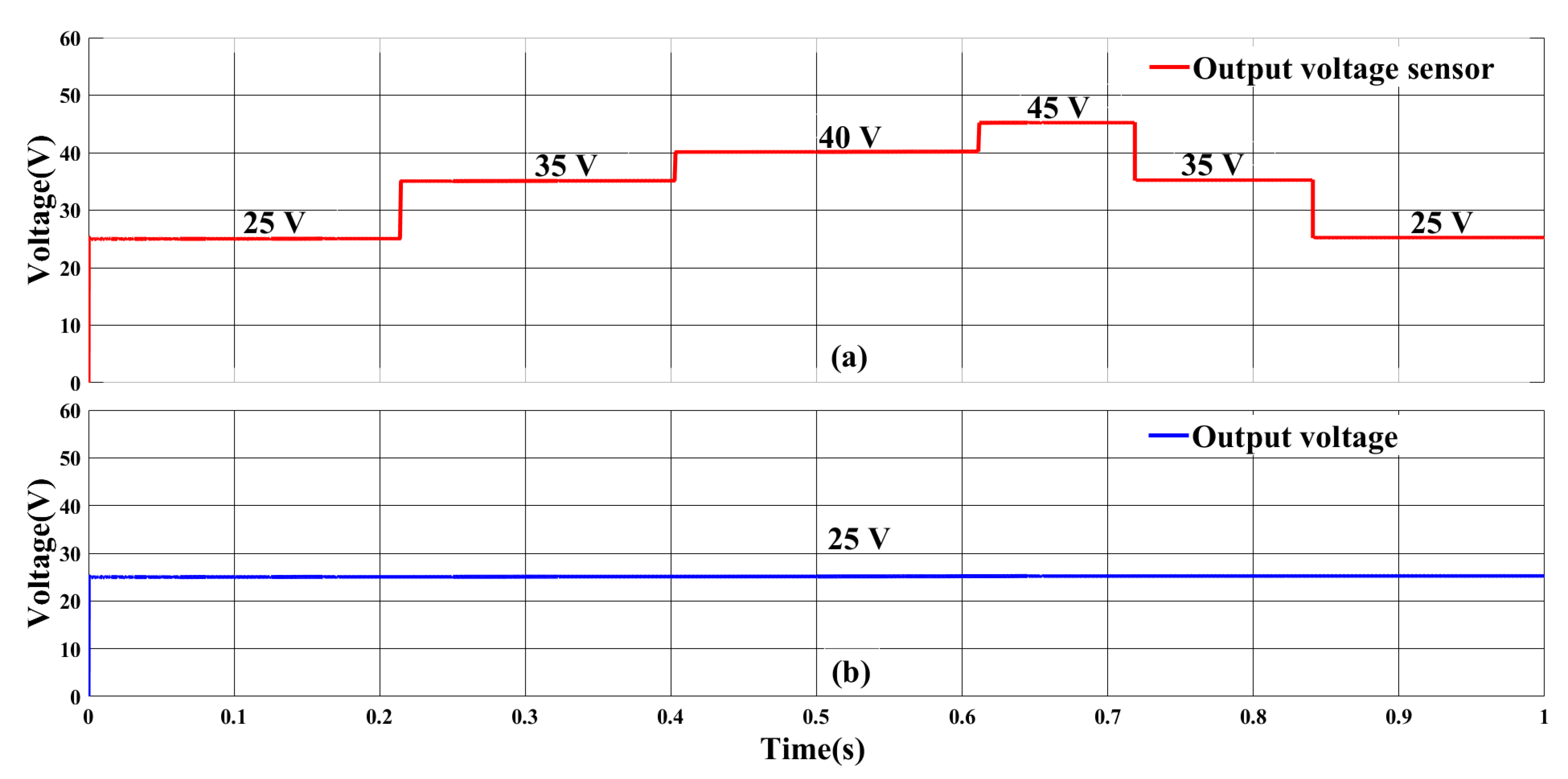
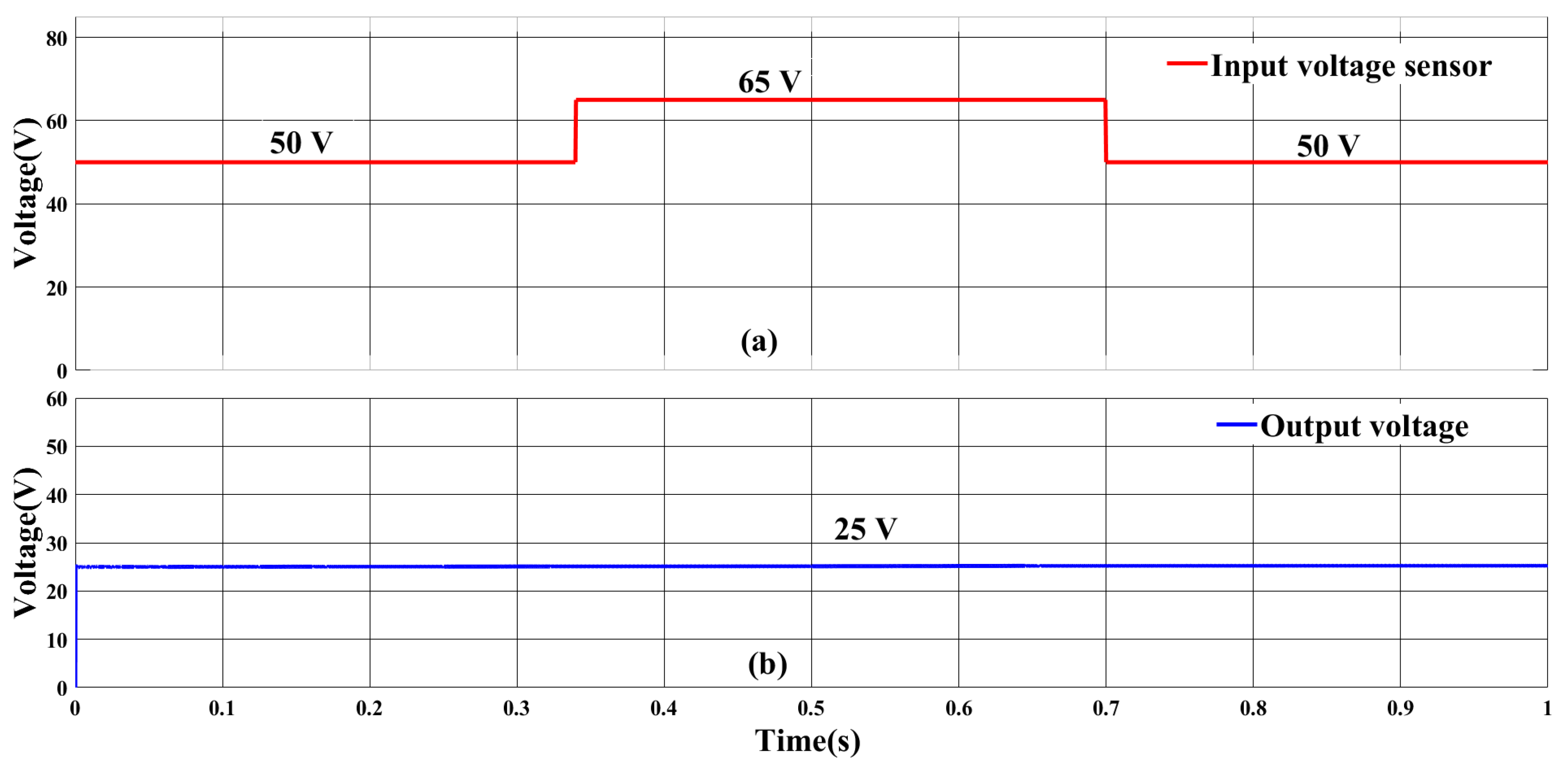
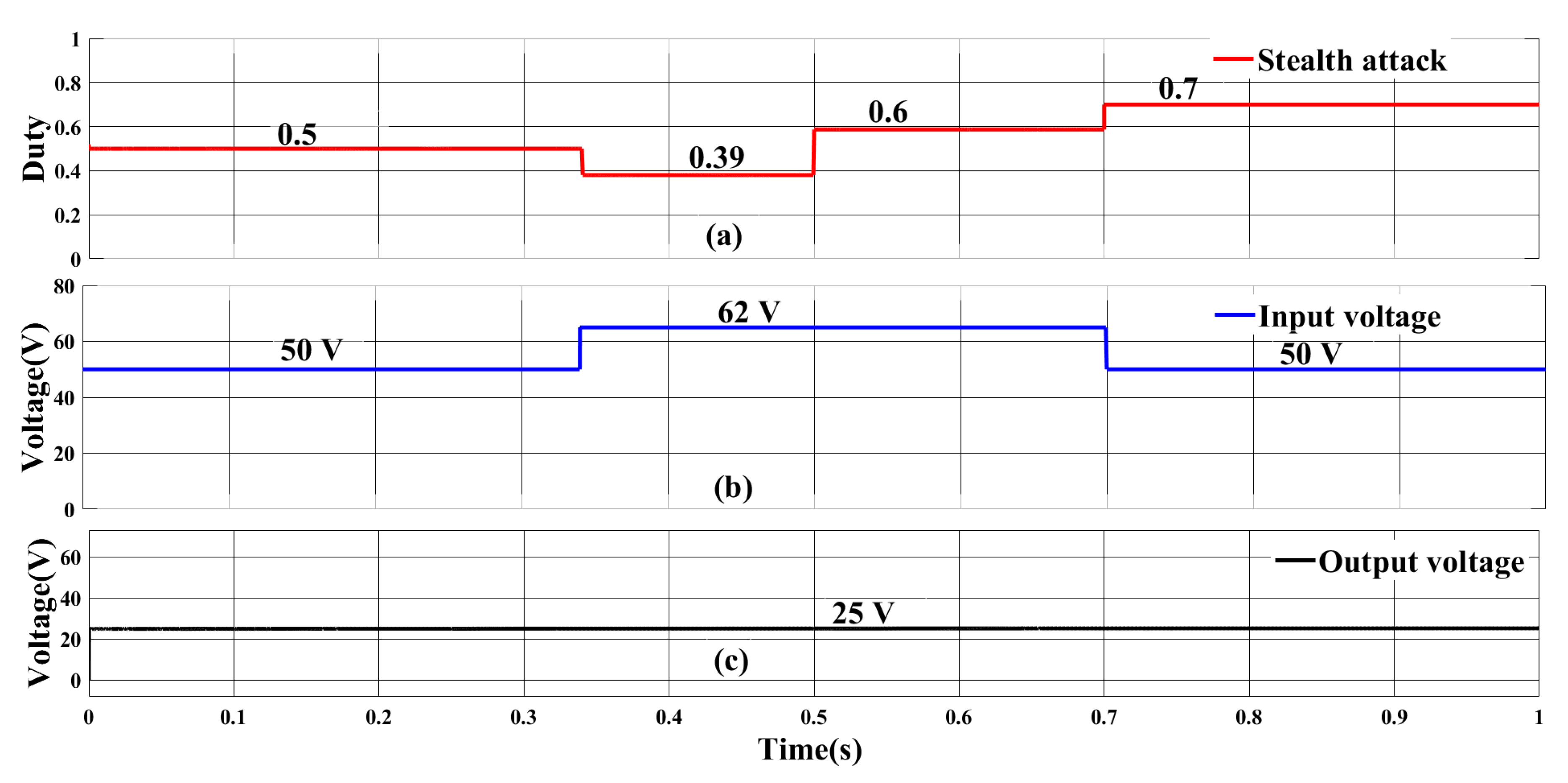
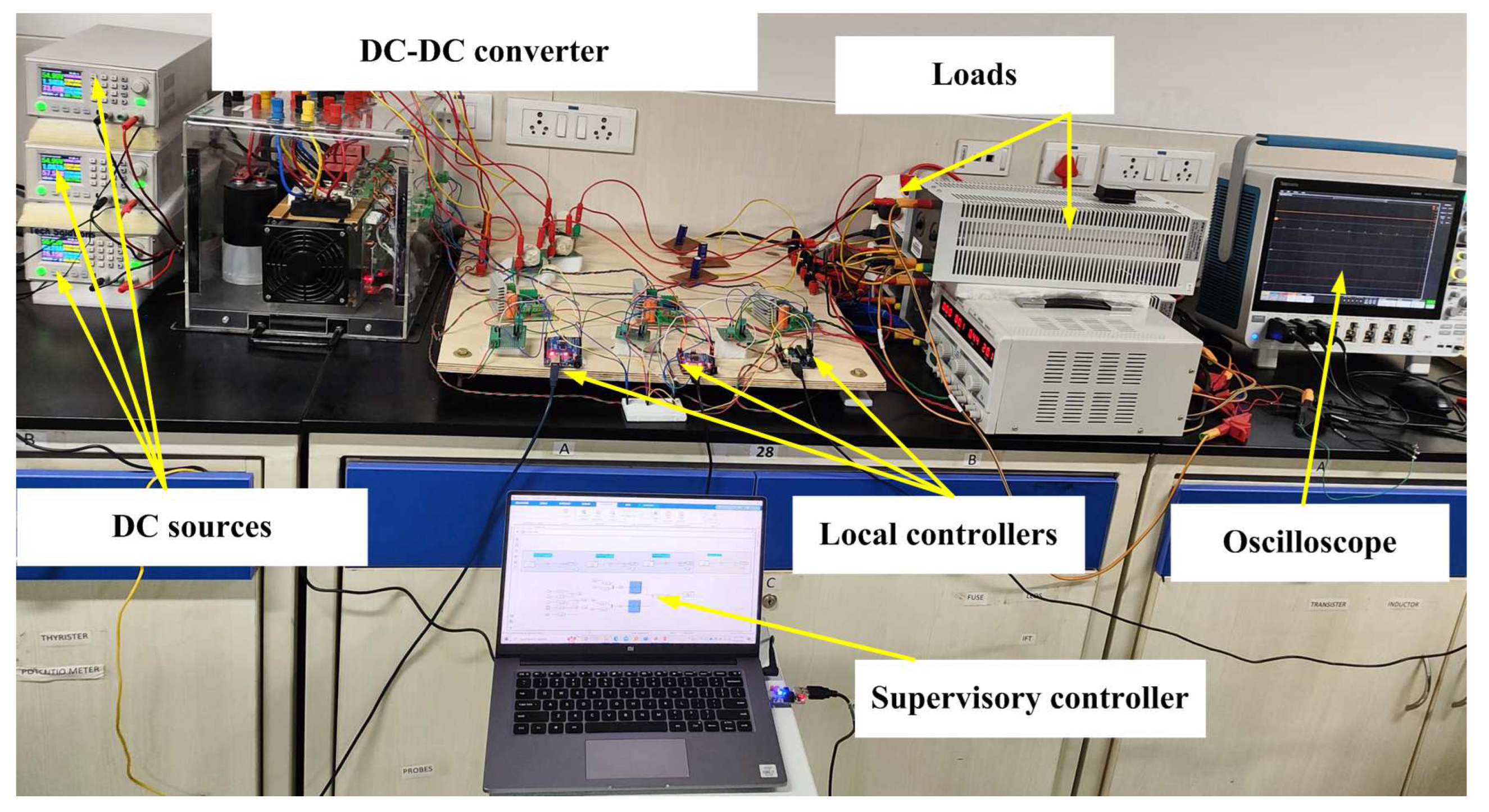
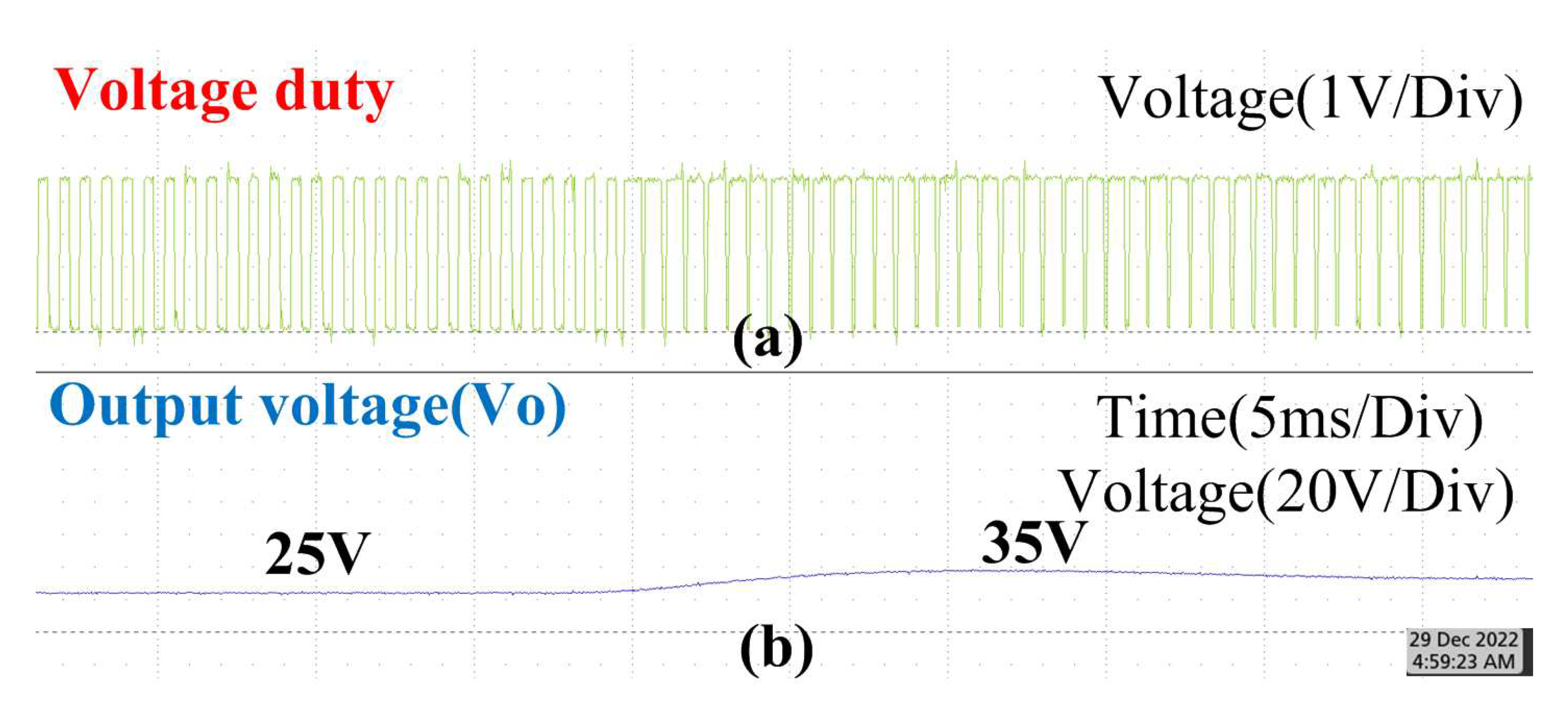
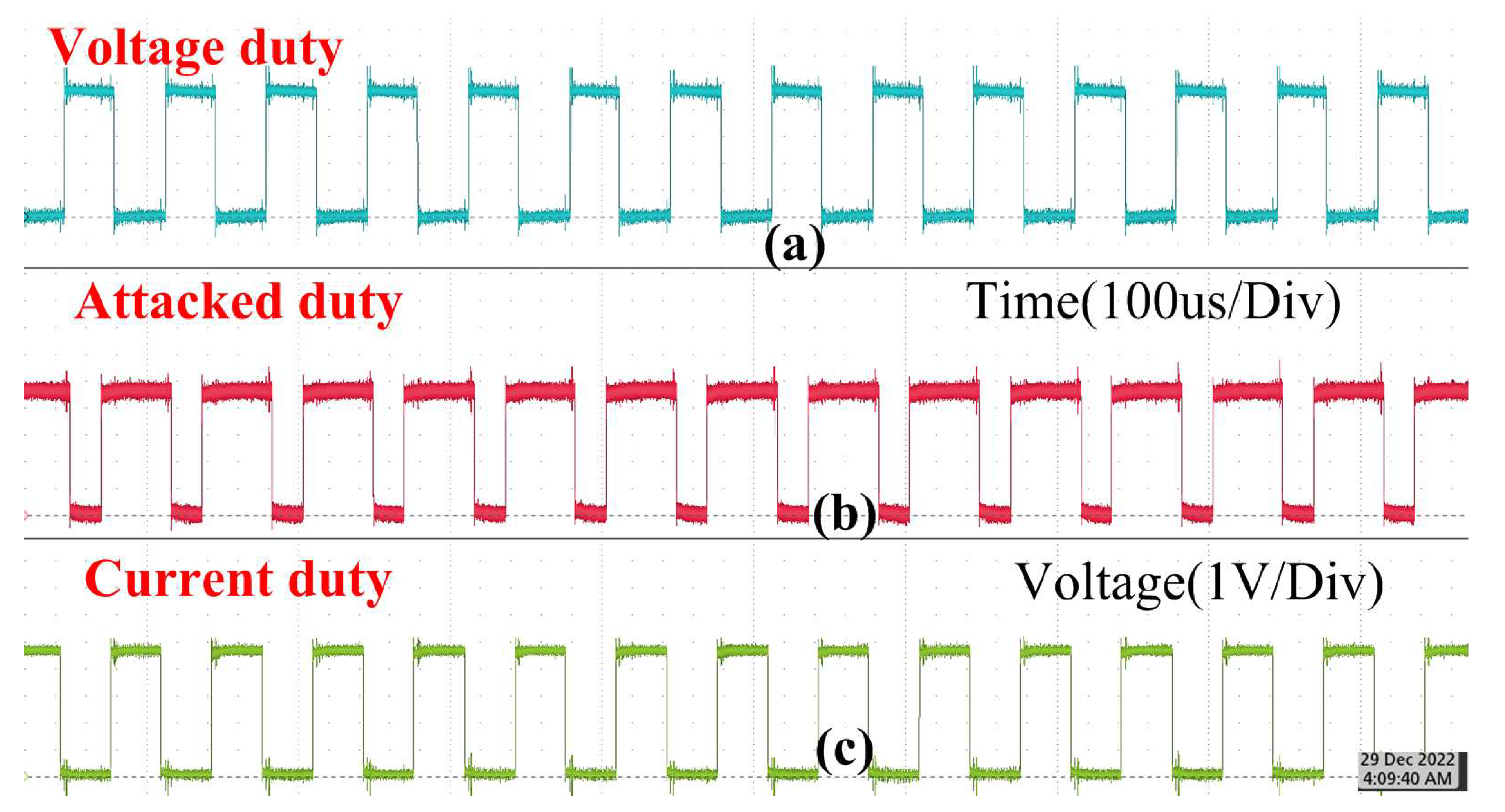
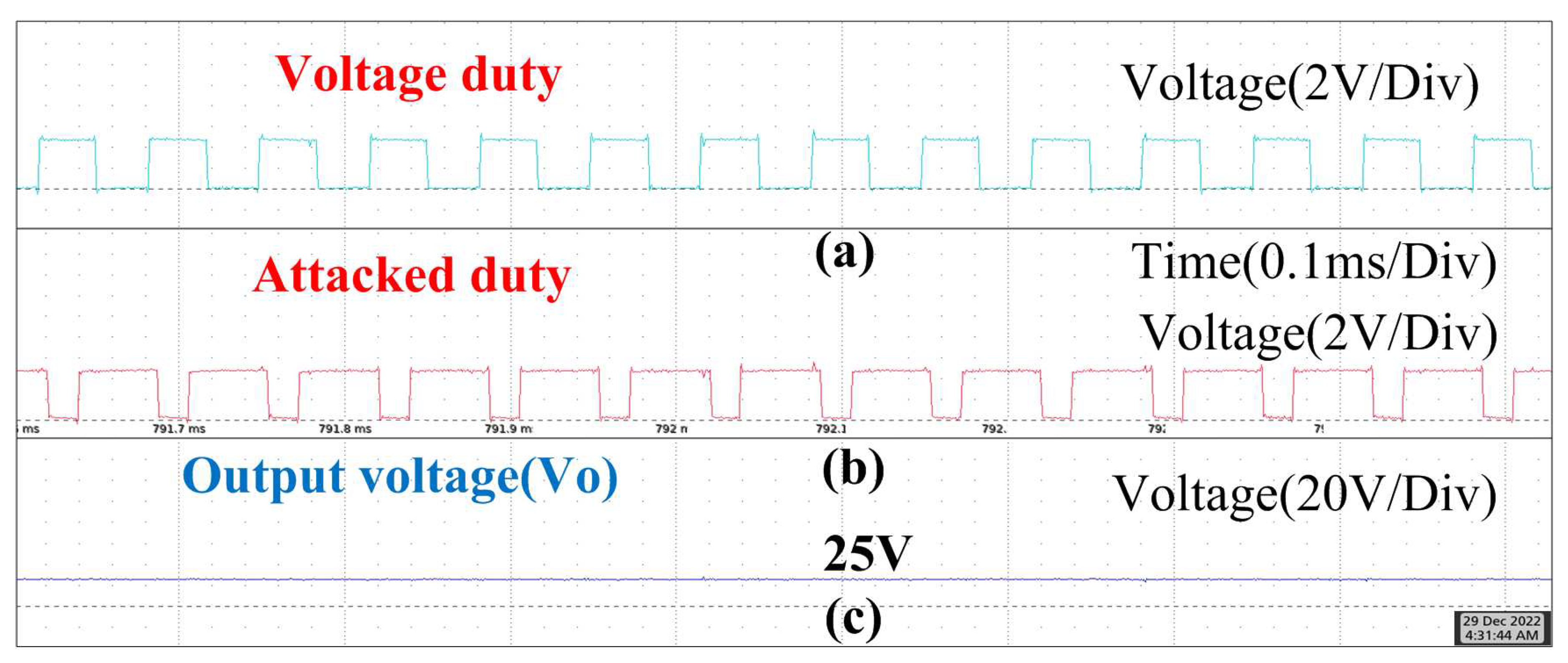
| Component | Rating |
|---|---|
| Inductor L | |
| Capacitor C | |
| Input voltage | |
| Output voltage | |
| Voltage ripple | 1% of |
| Current ripple | 15% of (peak) |
| Load range | 50W of 200W |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





