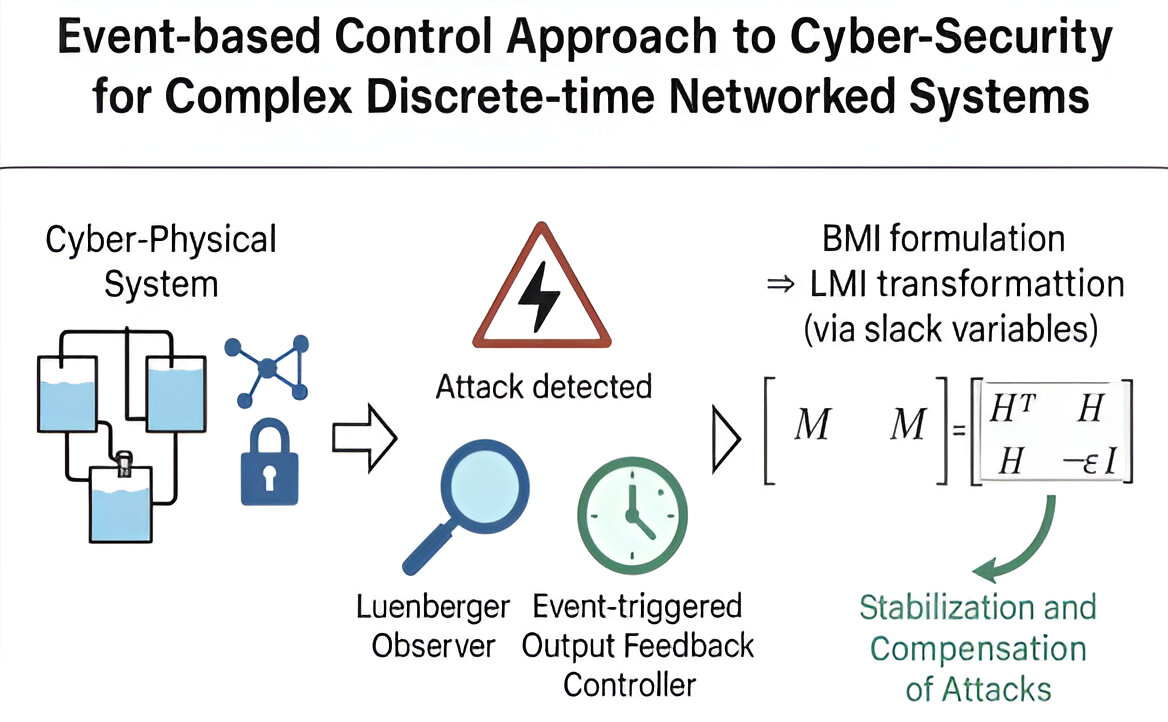
1. Introduction
Advances in mathematics, physics, computer science, and engineering over the last twenty years have enabled the development of novel stabilization and monitoring techniques for complex systems [
1,
2,
3,
4,
5,
6,
7]. This progress has significantly increased the importance and sophistication of Control-Supervision Systems, particularly in communication networks [
8,
9,
10]. Given the growing need for safety and resilience, research has increasingly focused on Fault-Tolerant and FTA systems [
11,
12,
13,
14]. Ensuring resilience in FTA design is critical for maintaining operational efficiency under abnormal conditions, a necessity for modern industrial supervision systems [
15,
16]. Unlike conventional systems, where cyber-security primarily safeguards data, NCSs face threats from CA that manipulate physical processes via feedback mechanisms [
17]. This distinction highlights the importance of integrating control approaches to improve NCS security by analyzing the interplay between CA and control algorithms, particularly their physical impacts [
18,
19,
20].
Extensive research has explored CA detection and mitigation, with particular attention to false data injection and physical attack models. These studies emphasize mathematical modeling of CA and their disruptive effects on controlled processes. Using dynamic process models and control algorithms, CAs can be effectively identified. Among the most studied attack vectors are physical intrusions, which remain key considerations in NCS security analysis [
21]. For instance, numerous methodologies have been proposed to detect and assess such attacks in CPS:
Graph-Theoretic Analysis: Using graph theory [
22] to model complex system structures and pinpoint vulnerabilities in network control systems.
Secure Set Theory: Employ maximal robustly controlled invariant sets [
23] to strengthen the resilience of the system against external disturbances and uncertainties.
Frequency-Domain Attack Analysis: Investigating the effects of CA on control inputs and outputs using frequency domain techniques [
24,
25].
Distributed Consensus Control: Applying discontinuous observation-based control consensus principles to linear multi-agent systems [
26] for enhanced reliability in distributed architectures.
Event-Triggered-State Feedback: Implement consensus control via event-triggered state feedback [
27] to reduce network congestion while maintaining system performance.
Adaptive Fault-Tolerant Control: Design of controllers that depend on the state in time [
28] to improve robustness against faults and dynamic uncertainties.
Observer-Based Protocol Synthesis: Developing topology-dependent Lyapunov functions for observer-based protocols with nonlinear Lipschitz dynamics [
29], ensuring stability in large-scale networked systems.
Sampled-Data Observers: Utilizing programmable sampled-data observers [
30,
31] for real-time CA detection and mitigation.
While extensive research has addressed continuous-time systems, complex discrete-time systems have received comparatively limited attention in the literature [
32,
33]. Furthermore, existing observer-based approaches predominantly utilize state feedback mechanisms rather than output feedback strategies. To bridge these research gaps, this study introduces novel security measures employing observer-based output feedback controls specifically designed for discrete-time systems. The proposed framework simultaneously addresses both safety and security considerations through model-based attack detection using observers. By comparing estimated process outputs with actual measurements, the method identifies discrepancies and triggers appropriate corrective actions, enabling effective attack and fault detection.
The key contributions of this work include:
Developments of an innovative Event-Triggered with output feedback control strategy for cyber-physical discrete-time systems, contrasting with conventional continuous-time approaches. The proposed method specifically resolves the technical challenges of implementing output feedback in faulty system models, advancing beyond traditional state feedback limitations.
Significant generalization capabilities, being successfully adapted to both nonlinear Lipschitz systems and decentralized architectures. This extension substantially broadens the method’s potential applications in complex networked environments.
The introduction of supplementary decision variables enhances the convex optimization formulation, providing greater design flexibility. Through innovative slack variable techniques, the linearization of complex bilinear terms in the BMI formulation is formulated, yielding more computationally tractable solutions.
Simulation studies validate the proposed approach’s effectiveness, with results indicating strong potential for real-time implementation using digital signal processing platforms. These findings demonstrate practical feasibility for industrial applications.
The paper is organized as follows: preliminary concepts and the problem statement are presented, followed by the synthesis of an attack-tolerant controller. Numerical validation on an example is then provided, concluding with insights for future research directions.
Notation: The following notation will be used throughout this paper:
In a matrix, the notation (🟉) is used for the blocks induced by symmetry.
is the transposed matrix of , if is a square matrix then the notation ) means that is positive definite (negative definite).
The set is the convex hull of .
2. Problem Statement and Preliminaries
This section outlines a modeling framework to address various types of attacks with event trigged control systems. The cyber-physical system can be represented by:
The global system is :
Where
represent the sate vector,
is the output vector,
is the control vector,
is the unknown inputs represents the effect of faults,
are constant matrices of appropriate dimensions.
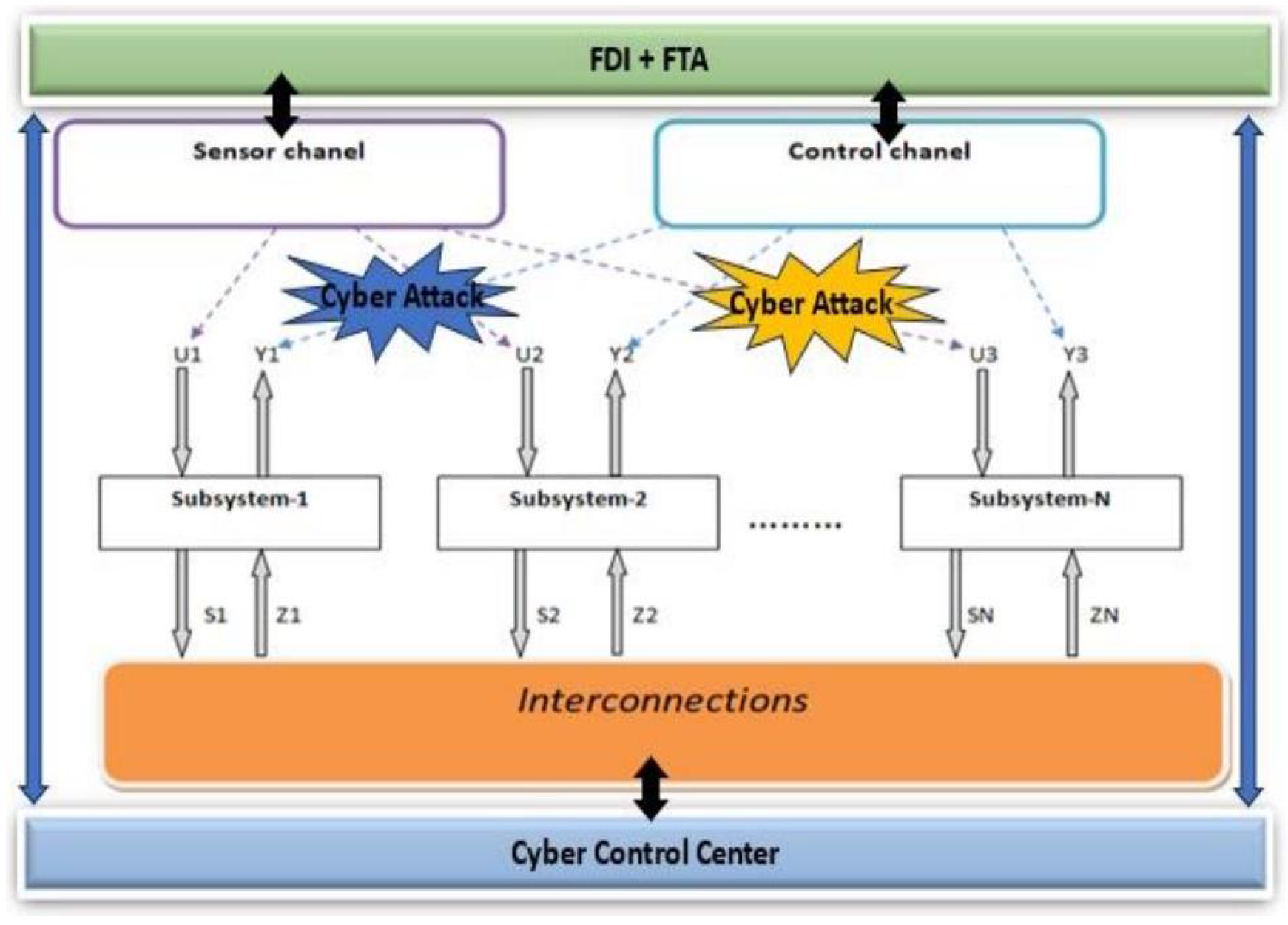
In this particular system, our focus lies in exploring a method for detecting and identifying attacks primarily through a model designed to detect and estimate attack signals within two communication channels. The diagram in
Figure 1 provides an overview of the general control/supervision structure of interconnected cyber-physical systems.
Cyber-attacks can simultaneously impact control and/or observation communication chains, as well as interconnection functions. The latter will be modeled in the following by: and which represent the data corruption / modification on the control sequences and measurements respectively. Following this, the FDI function will be executed through the synthesized observers. This will furnish the Cyber Control Center with crucial information regarding the nature and location of the cyber-attack, thereby enabling it to compute or update the command via a event-trigged strategy.
For this, the designed Luenberger observer is :
The control signal, by principle of output feedback, is designed with the following form:
The faults and attacks are modeled as follows:
- -
simulates errors modeling, faults, unknown input, disturbances.
- -
Since data corruption / modification can change the control sequences and measurements provided by the different sensors from their actual calculations or values , to corrupted signals and .
False attacks are modelled by:
With
and
represents the pirated data.
and
are the binary impact matrices indicating which data strings can be accessed by the ‘hacker’.
Now we define a new variable
, group the fault/attack signals as follows:
. This allows us to rewrite the augmented system (system + observer) as follows:
With
Then the following lemmas are considered:
Lemma 1: [
34] Given two matrices
, of appropriate dimensions, then the following inequality holds for any constant
Lemma 2: [
34] Consider a nonlinear function
, the following two items are equivalent:
h is globally Lipschitz with respect to its argument, i.e.,
There exist constants
and
so that for all
there exist
and functions
satisfying the following equality:
And
where
and
3. FTA Control Synthesis
This section is dedicated to the development of the new FTA synthesis. The main result is given by the following Theorem:
Theorem 1: There exists an asymptotic stable observer of the form (3) and an event-based fault-attack tolerant controller (4), with a triggering condition , for the system (2), if there exist positive symmetric matrices , matrices , , and a positive scalar , solution if the following BMI is feasible:
With:
Proof
To determine the different control and observer gains, a stability analysis is based on the Lyapunov function:
With
.
Now using
lemma 1 on
, the latter becomes:
Thus, the stability condition can be given by
We apply Schur’s complement using
, we obtain:
Where:
•
with:
and:
•
With:
•
Then, contrary to the various synthesis approaches considered in the literature and to give more degrees of freedom to the optimization problem, we propose the following form of the matrix
:
Where
The final step, let’s consider the following proposed variables changes:
Then, inequality (
10) is easily obtained.
4. Event-Triggered Mechanisms
To implement Event-based control [
35], it’s necessary to recompute the control gains and update the signal whenever (
10) nears a violation. To express this equality conveniently, we assume that the input remains constant between successive recomputation of the FTA. This practice is commonly known in the literature as ‘sample and hold’.
Or the sequence
represents the moment when the command is recalculated. Subsequently, we introduce the error
defined by:
which means that
Such as:
: is the pseudo-inverse of
: Arbitrary vector represents the disturbances.
From equation (
6), the dynamics of the system in the interval
[ is given by:
Using (
13) and (
19), held to:
With
Subsequently, the
trigger time can now be defined as the moment that this equality is satisfied:
With
5. Discussion and Comments
-
This article examines the closed-loop system dynamics, which can be extended and generalized to accommodate the case of (by adjusting the matrix dimensions):
• Lipschitz nonlinear discrete-time systems where the basic idea is to use the DMVT on the nonlinear function [
34] to transform the global nonlinear system to LPV system using
Lemma 2. Then, if the nonlinear function verify
, the dynamic matrix
becomes
where the parameter
lies inside the bounded convex set of
variation.
• Decentralized systems with the consideration of the nonlinear interconnection function in the synthesis of the proposed control.
In this work, two gains ( and ) have been synthesized separately to stabilize the overall system during cyber-attacks on the two communications chains of control and observation (representing the interconnections). To reduce the complexity of the BMI to be solved, a proposal can ensure this by admitting that (like the proposed form of the matrix where ). This will make it possible to linearize several expressions in the BMI while guaranteeing a more optimal solution (scalar variables to be searched instead of matrices).
6. Numerical Simulation and Results
This section presents an application on a pilot system comprising three tanks. A plant model is introduced, and the proposed control design is implemented on the system. Numerical findings are provided to demonstrate the effectiveness of the developed methodology.
The dynamic equation for the system is given as:
simulates errors modeling, faults, unknown input, disturbances, where the weighing matrix is defined as:
and
is equal to the identity matrix
I. The event condition
rate was chosen to be equal to
. The initial conditions of the system and the observer are:
with
By solving (
10) with (
15)using YALMIP
®, an optimal solution is found such that the gains found are as follows:
6.1. No-Attacks Case:
First, during the implementation phase, noise was introduced into the system in the form of sinusoidal signals characterized by a random varying frequencies (between 02 and 42 Hz) and amplitudes
. Now,
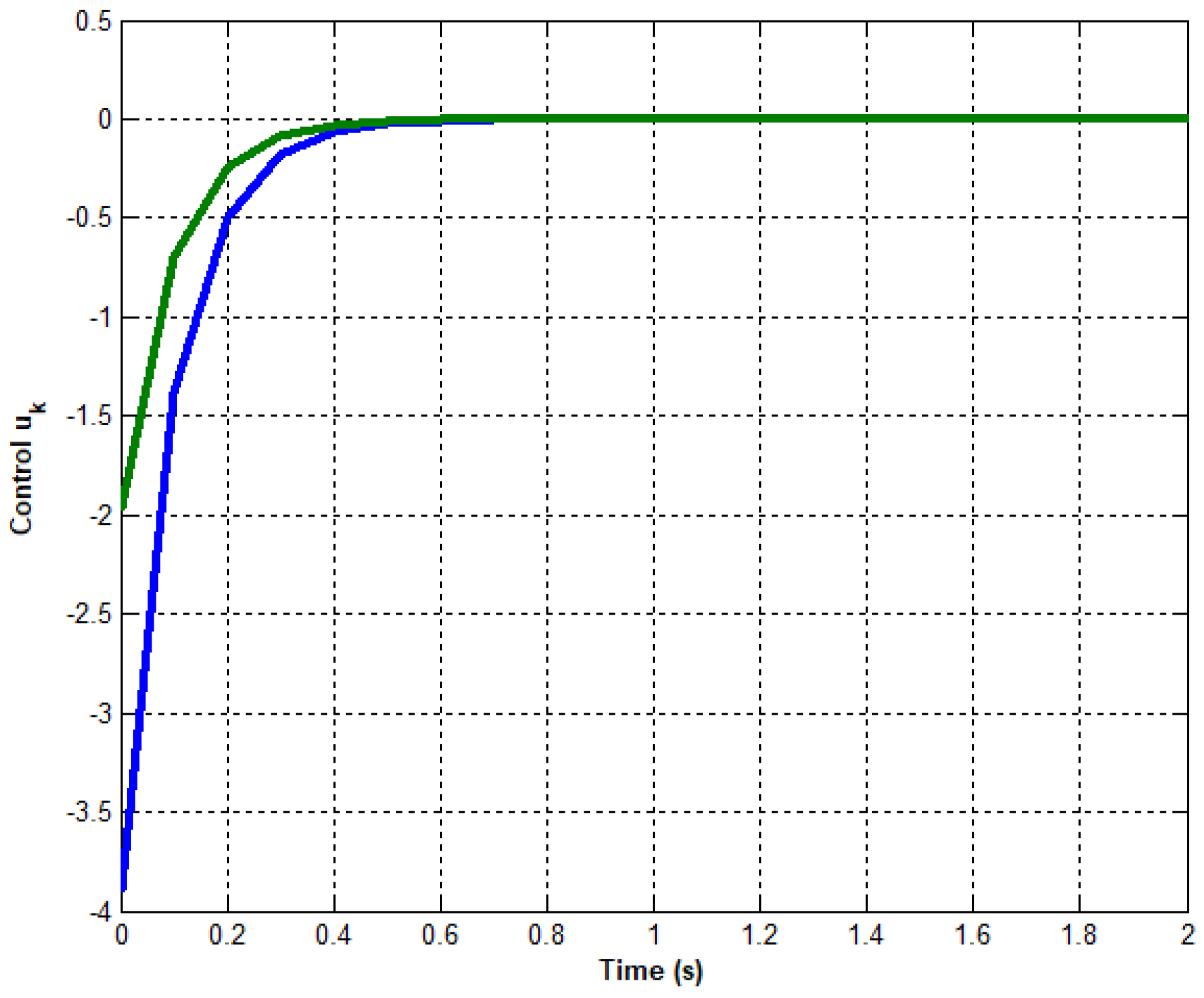
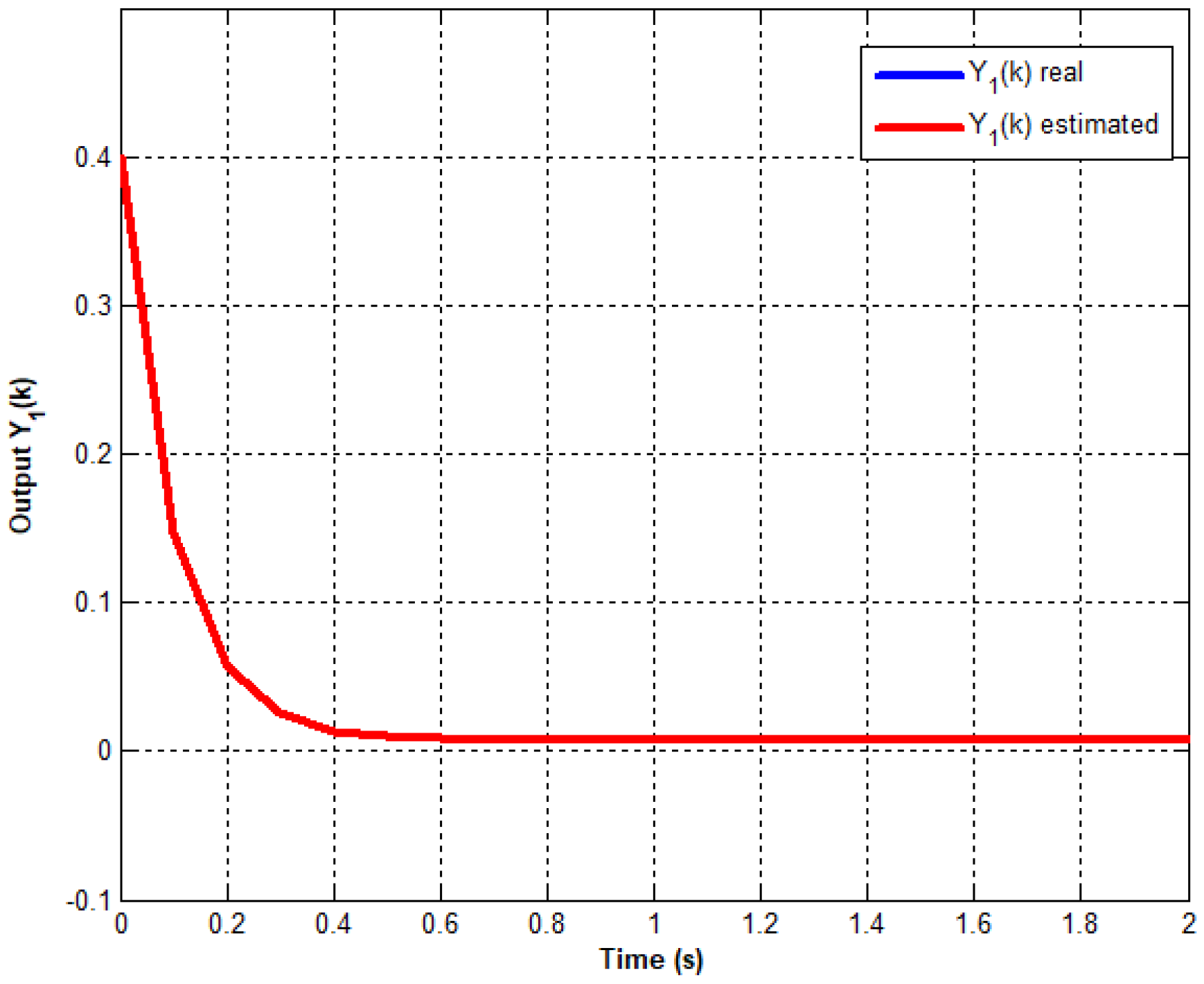
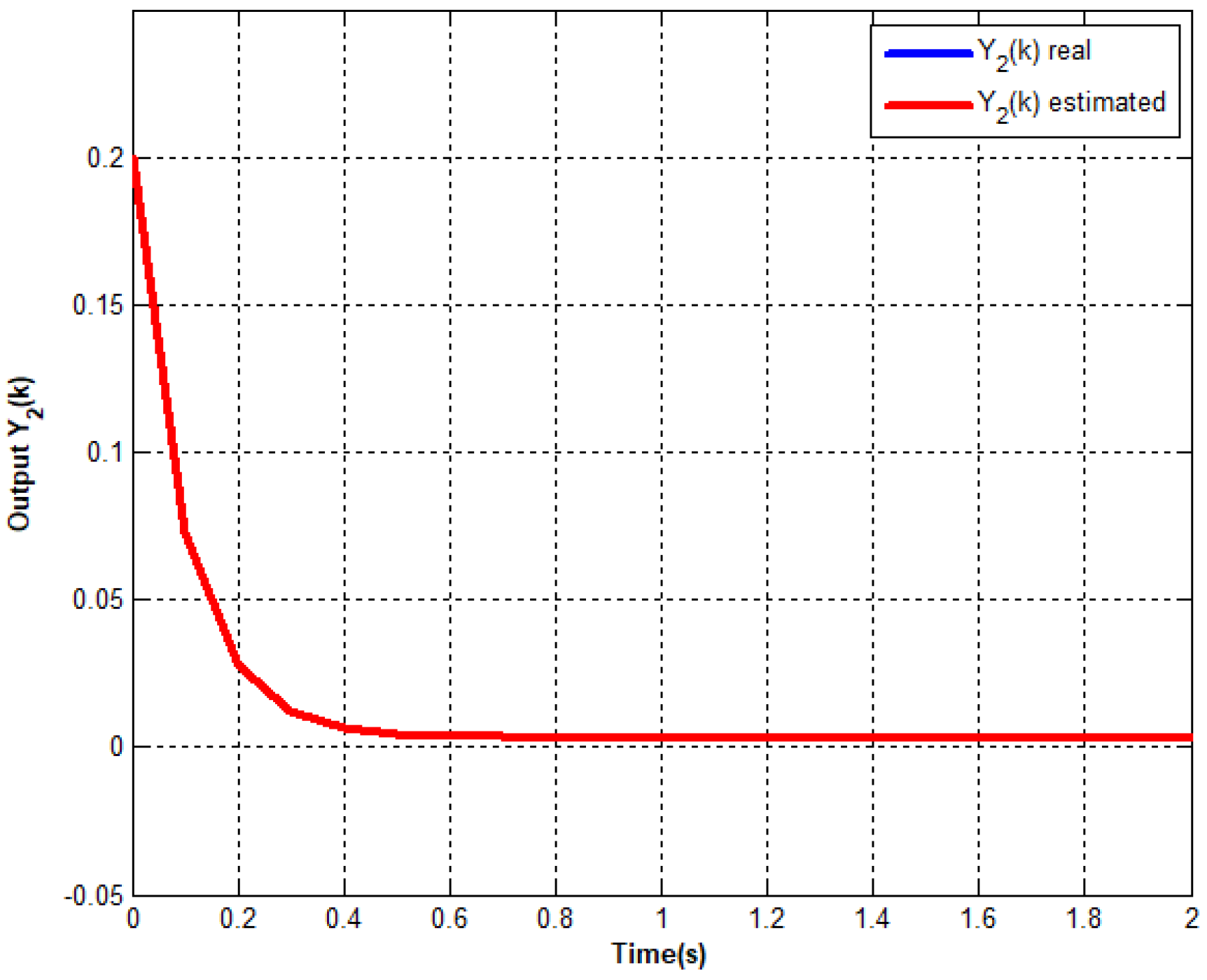
Figure 2,
Figure 3 and
Figure 4 show the evolution of the control
and various outputs
without attacks:
From
Figure 2,
Figure 3 and
Figure 4, it is clear that the proposed output feedback control ensures the stabilization despite injected disturbances. Effectively, According to
Figure 3 and
Figure 4, the estimated states converge to the real ones around the equilibrium point, despite the injection of random perturbations on the system dynamics and output. This is also validated through the variation of the control signals
Figure 2, which show the convergence of the control without amplitude variation and even in terms of convergence time.
Remark 3:
In the dynamics of the proposed system, the eigenvalues are on the stability limit . The output feedback control strategy (even without cyber-attacks on the control/observation chains) guarantees the overall stability of the system towards the equilibrium point despite injected disturbances such as .
6.2. Case With Attacks
For this case, we apply the attack on the actuator chain and then on the sensor chain such as and . Now, the cyber-attacks will be applied to the control chain and the sensor chain in the time interval .
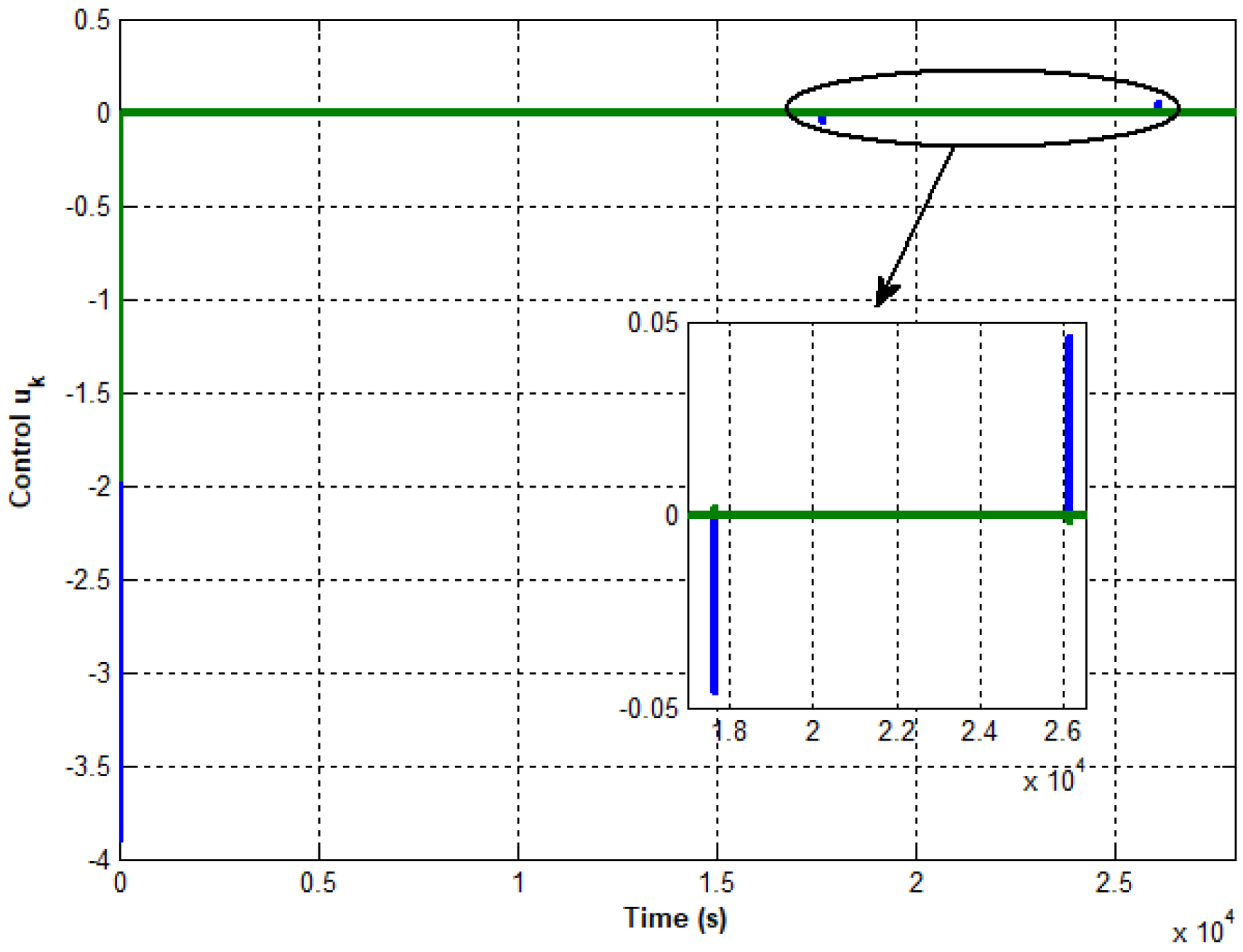
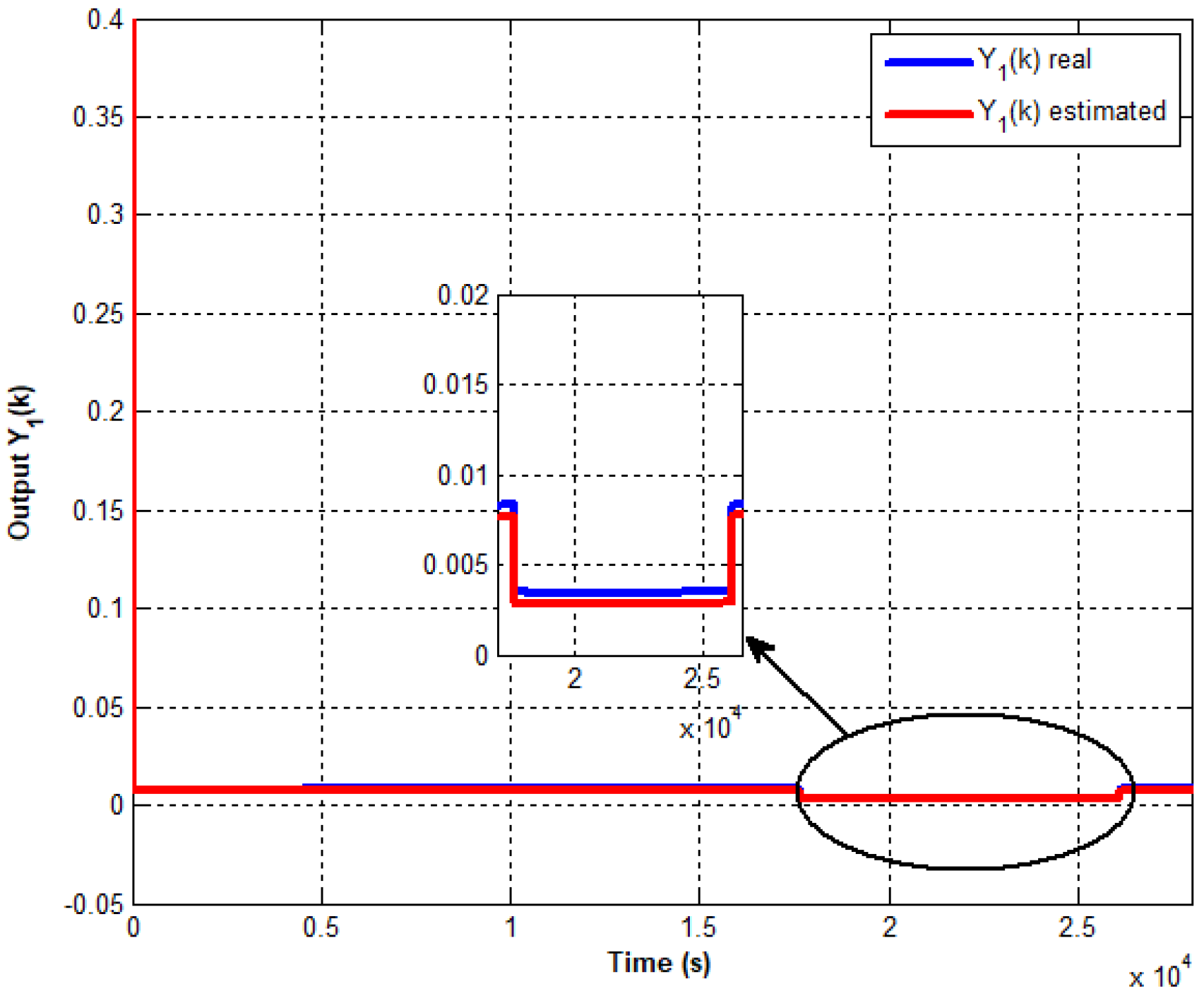
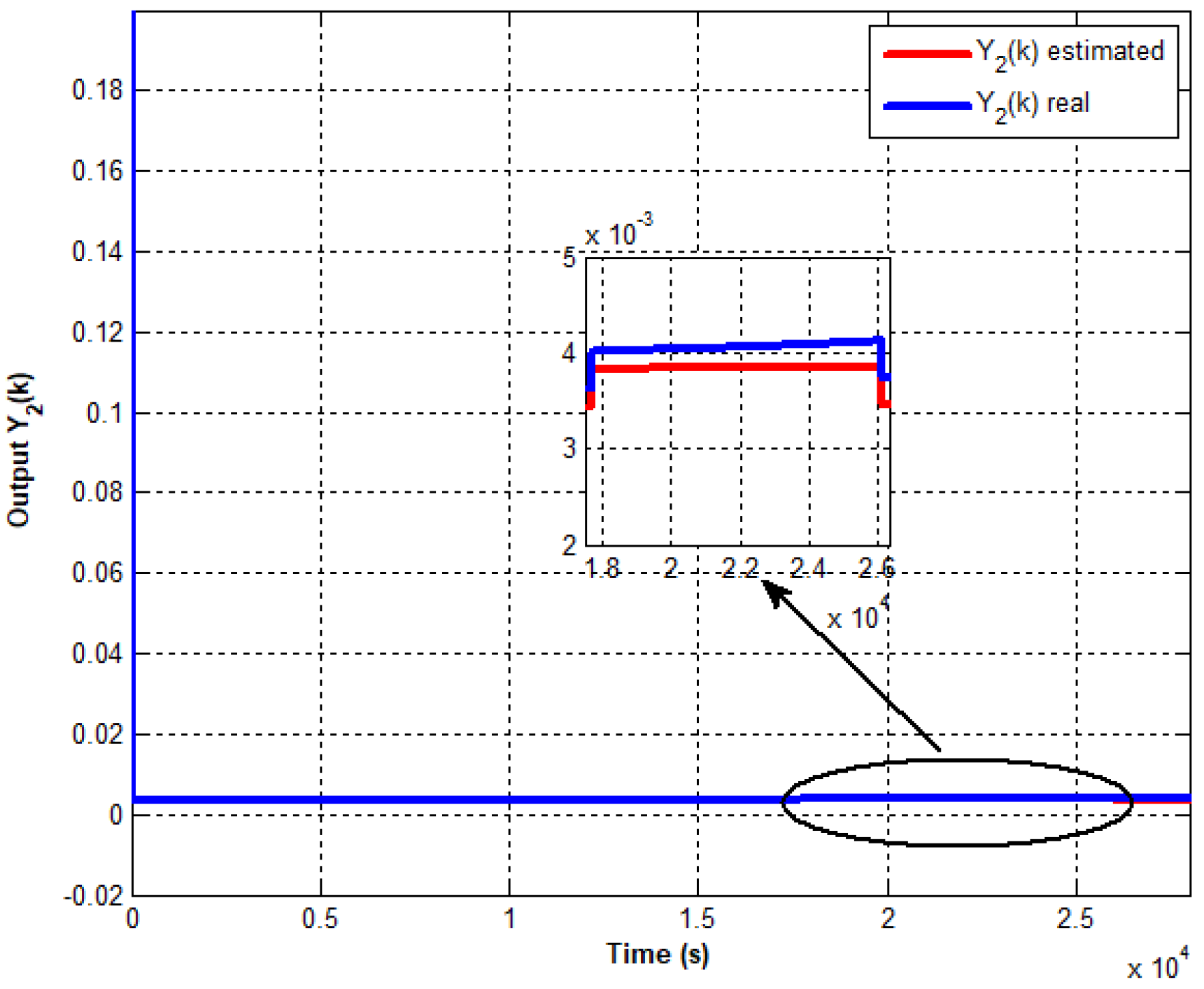
Figure 5,
Figure 6 and
Figure 7 illustrate the evolution of the control
to reduce the impact of cyber-attacks on control and observer chains and the various outputs
using the trigger condition (
).
Figure 5,
Figure 6 and
Figure 7 depict the progression of control and different outputs utilizing the event-triggered approach. This strategy aims to minimize the effects of attacks on sensors and actuators while ensuring the stabilization of the interconnected system around its equilibrium point. Thus, it is evident that the initial phase of attack detection and identification has been successfully achieved
Figure 6 and
Figure 7. Moreover, the impact of attacks on both communication chains (control/observation) in terms of amplitude spikes and even control signal
Figure 5 has been reduced through the proposed approach while avoiding a very important parameter which is the switching phenomenon in actuators.
Another point related to convergence speed/time is shown in the presented figures. Effectively, comparing the convergence times
of an approach that handles the continuous-time case [
8] such that
s while the proposed discrete version converges to only 0.189 s for the same example system.
A comparison of convergence times with approaches dealing with the discrete case is as follows:
• Unamed Ground Vehicle [
33] with
where the proposed approach converges in 0.9824 s.
• Modular Servo System [
32] with
where the proposed approach converges in 0.5771 s.
7. Conclusion
This paper introduces an attack/fault-tolerant control system based on an event-triggered control framework. Through an examination of stability using the BMIs framework and the design of an observer, a feedback controller is derived to compute control inputs. The triggering mechanism for control input activation is determined based on a predefined threshold for error occurrence. A numerical validation is conducted using a three-tank system subjected to disturbances and attempts at sensor and actuator data falsification, yielding satisfactory results. Additionally, fault detection and attack isolation are facilitated through the utilization of a residual generator and observer. Future studies may explore extending the proposed synthesis methods to accommodate nonlinear output and generalizing the approach for robust schemes.
Author Contributions
Conceptualization and methodology, A.T. and E.H.; software, N.G., A.T. and G.B.H.F.; supervision and validation, A.T. and N.G.; writing original draft preparation, E.H.; writing review and editing, G.B.H.F. and E.H. All authors have read and agreed to the final version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable
Informed Consent Statement
Not applicable.
Data Availability Statement
No new data were created or analyzed in this study. Data sharing is not applicable to this article.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| FTA |
Fault Tolerant Attack |
| ETM |
Event-Triggered Mechanisms |
| CPS |
Cyber-Physical Systems |
| BMI |
Bilinear Matrix Inequality |
| LMI |
Linear Matrix Inequality |
| CA |
Cyber-Attacks |
| NCS |
Network Control Systems |
References
- Ilioudis, V.C. ’A Study of MTPA Applied to Sensorless Control of the Synchronous Reluctance Machine (SynRM)’. Automation 2025., Vol.6(11). [CrossRef]
- Duo, W.; Zhou, M.; Abusorrah, A. A survey of cyber attacks on cyber physical systems: Recent advances and challenges. IEEE/CAA Journal of Automatica Sinica 2022, 9, 784–800. [Google Scholar] [CrossRef]
- Saif, A. W. A. Strong stabilisation: an LMI approach. International Journal of Modelling, Identification and Control 2007, 2, 3–8. [Google Scholar] [CrossRef]
- M.A., Rahman; et al. A Cloud-Based Cyber-Physical System with Industry 4.0: Remote and Digitized Additive Manufacturing. Automation 2022, 3(3), 400–425. [Google Scholar] [CrossRef]
- Thabet, A; Frej, G.B.H.; Mansouri, K.; Chauveau, E.; Abdallah, S.B.H. Estimation des defauts pour les systèmes non lineaires interconnectes : Application a un reseau Electrique.’,,SGE21, Symposium de Genie Electrique, Nantes, France. 2021. [Google Scholar]
- Gupta, P.; Singh, N.; Mahajan, V. Intrusion Detection in Cyber-Physical Layer of Smart Grid Using Intelligent Loop Based Artificial Neural Network Technique. International Journal of Engineering 2021, 34(5), 1250–1256. [Google Scholar]
- Zou, X.; Ding, H; Li, J. Sliding mode speed control of permanent magnet synchronous motor based on improved reaching law. COMPEL-The international journal for computation and mathematics in electrical and electronic engineering 2023, 42, 1335–1348. [Google Scholar] [CrossRef]
- Rebai, S.B.; Voos, H.; Darouach, M. (2017), ‘A contribution to Cyber-Security of Networked Control Systems: an Event-based Control Approach.’, In Proc. The 3rd International Conferenceon Event-Based Control, Communication and Signal Processing, Madeira, Portugal.
- Das, D.; Savier, J. A Multi-Objective Method for Network Reconfiguration (TECHNICAL NOTE). International Journal of Engineering 2009, 22(4), 333–350. [Google Scholar]
- Liu, Y. Robust adaptive control of uncertain non-linear systems with non-linear parameterisation. International Journal of Modelling, Identification and Control 2006, 1, 151–156. [Google Scholar] [CrossRef]
- Liu, K.; Guo, H.; Zhang, Q.; Xia, Y. A Survey of Cyber Attacks on Cyber Physical Systems: Recent Advances and Challenges. IEEE/CAA J. of Automatica Sinica 2022, 9, 784–800. [Google Scholar]
- Dadi, L.; Ethabet, H.; Aoun, M. Interval observer-based fault tolerant control for discrete-time switched linear system. International Journal of Modelling, Identification and Control 2024, 44, 341–349. [Google Scholar] [CrossRef]
- Barik, S.K.; Nanda, S.; Samal, P.; Senapati, R. Detection and localization of fault in DC microgrid using discrete Teager energy and generalized least square method. COMPEL - The international journal for computation and mathematics in electrical and electronic engineering 2024, 47, 227–246. [Google Scholar] [CrossRef]
- Neupane, S.R.; Sun, W. (2025). ’Advanced Data Classification Framework for Enhancing Cyber Security in Autonomous Vehicles’. Automation 2025. , Vol6(1). [CrossRef]
- Hassine, E.; Thabet, A.; Gasmi, N.; Frej, G. B. H.; Thabet, H. (2023), ‘Reconfiguration and Cyber-Attack Tolerant Control for Nonlinear Multi-Agent Systems’, In 2023 IEEE International Workshop on Mechatronic Systems Supervision (IW-MSS), p. 1-6.
- Mo, Y.; Weerakkody, S.; Sinopoli, B. Physical authentication of control systems designing watermarked control inputs to detect counterfeit sensor outputs. IEEE Control Systems 2015, 93–109. [Google Scholar]
- Zhang, K.; Braverman, E.; Gharesifard, B. Event-triggered control for discrete-time delay systems. Automatica 2023, 147, 110688. [Google Scholar] [CrossRef]
- Keshavarz, M.; Doroudi, A.; Kazemi, M.; Mahdian D., N. A New Consensus-based Distributed Adaptive Control for Islanded Microgrids’, International Journal of Engineering. 2021, 34(7), 1725–1735. [Google Scholar]
- Moufaddal, M.; Benghabrit, A.; Bouhaddou, I. Towards a novel cyber physical control system framework: a deep learning driven use case. International Journal of Intelligent Unmanned Systems 2023, 16, 233–240. [Google Scholar] [CrossRef]
- Ghansah, F. A.; Lu, W. (2023), ‘Cyber-physical systems and digital twins for a cognitive building in the construction industry’, Construction Innovation.
- Teixeira, A.; Shames, I.; Sandberg, H.; Johansson, K.H. (2015), ‘A secure control framework for resource-limited adversaries. Automatica 51, 135–148. [CrossRef]
- Pasqualetti, F.; Darfer, F.; Bullo, F. (2012), ‘Cyber-physical security via geometric control: Distributed monitoring and malicious attacks.’, In IEEE Conference on Decision and Control, Hawai, USA.
- Rosich, A.; Voos, H.; Darouach, M. (2014), ‘Cyber-attack detection based on controlled invariant sets.’, In European Control Conference, Strasbourg, France.
- RSmith, R.S. Covert misappropriation of networked control systems. IEEE Control Systems 2015, 35(1), 82–92. [Google Scholar]
- Asgari, S.; Menhaj, M.; Suratgar, A. A.; Kazemi, M. A Disturbance Observer Based Fuzzy Feedforward Proportional Integral Load Frequency Control of Microgrids. International Journal of Engineering 2021, 34(7), 1694–1702. [Google Scholar]
- Wen, G.; Li, Z.; Duan, Z.; Chen, G. (2013), ‘Distributed consensus control for linear multi-agent systems with discontinuous observations. Int. J. Control.Vol. 86, 95–106. [CrossRef]
- Ding, D.; Wang, Z.; Ho, D. W.; Wei, G. Observer-based event-triggering consensus control for multiagent systems with lossy sensors and cyber-attacks. IEEE transactions on cybernetics 2016, 47(8), 1936–1947. [Google Scholar] [CrossRef]
- Chao, D.; Qi, R.; et Jiang, B. Adaptive fault-tolerant control for the ascent phase of hypersonic vehicle with time-varying full state constraints. Aerospace Science and Technology 2022, 131, 108–116. [Google Scholar] [CrossRef]
- Wen, G.; Yu, W.; Xia, Y.; Yu, X.; Hu, J. (2017), ‘Distributed tracking of nonlinear multiagent systems under directed switching topology: An observer-based protocol. IEEE Trans. Syst. Man, Cybern. Syst, Vol. 47, 869–881. [CrossRef]
- Wan, Y.; Cao, J.; Wen, G. Quantized synchronization of chaotic neural networks with scheduled output feedback control. IIEEE Trans. Neural Netw. Learn. Syst 2016. [Google Scholar] [CrossRef]
- Wan, Y.; Cao, J.; Alsaedi, A.; Hayat, T. (2017), ‘Distributed observer-based stabilization of nonlinear multi-agent systems with sampled-data control Vol. Asian J. Control, 19, 918–928. [CrossRef]
- Zhao, D.; Zidong, W.; Ho, D.W.C.; Ho, Guoliang, W. (2019), ‘Observer-Based PID Security Control for Discrete Time-Delay Systems Under Cyber-Attacks. IEEE Transactions on Systems, Man, and Cybernetics: Systems 51, 3926–3938. [CrossRef]
- Zhu, Y.; Zheng, W. X. Observer-Based Control for Cyber-Physical Systems With Periodic DoS Attacks via a Cyclic Switching Strategy. IEEE Transactions on Automatic Control 2020, 65, 3714–3721. [Google Scholar] [CrossRef]
- Thabet, A.; Hassine, E.; Gasmi, N.; Frej, G.B.H.; Boutayeb, M. (2023), ‘LMI-Based Designs for Feedback Stabilization of Linear/Nonlinear Discrete-Time Systems in Reciprocal State Space: Synthesis and Experimental Validation.’, In: State Estimation and Stabilization of Nonlinear Systems: Theory and Applications. Cham: Springer Nature Switzerland,p. 205-219.
- Zhang, K.; Braverman, E. Delayed impulsive stabilization of discrete-time systems: a periodic event-triggering algorithm. International Journal of Control 2023, 147, 1–11. [Google Scholar]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).