1. Introduction
A. Essential information regarding National Power System (
Figure 1):
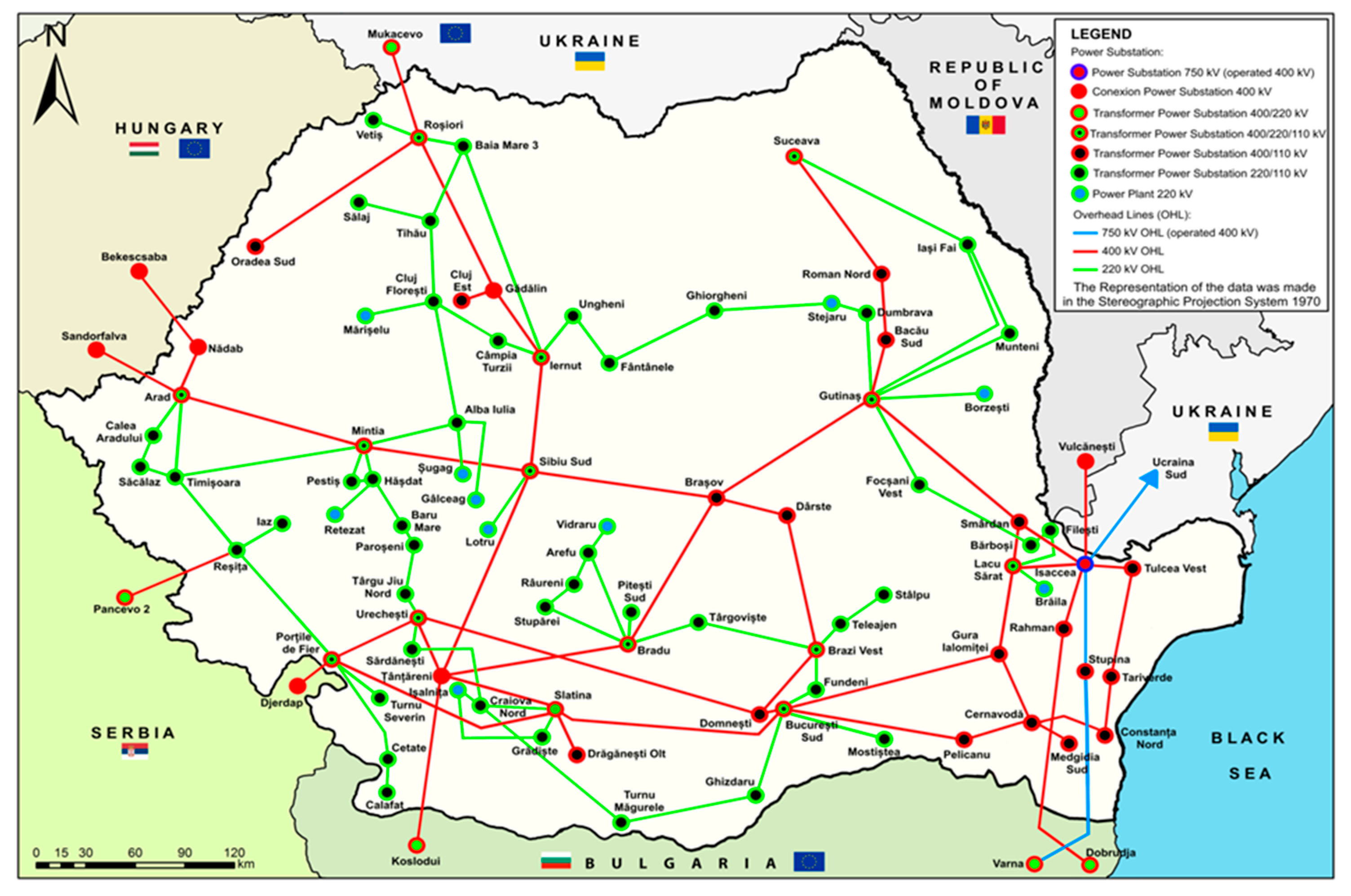
Romania is integrated into the European electricity transmission network, part of the European Network of Transmission System Operators for Electricity (ENTSO-E). International interconnections enable energy exchanges, optimisation of energy resources and contribute to system stability in the event of major variations in consumption or production. The structure of the National Power System is the set of interconnected components that ensure the production, transmission, distribution and consumption of electricity. Electricity production in Romania is based on a combination of energy sources, and the energy landscape of the country has evolved over time, based on conventional and renewable energy sources. Romania has a diversified energy infrastructure, with power plants that use several energy sources, including nuclear energy, hydropower, fossil fuel energy (lignite, hard coal, natural gas) and renewable energy (wind, solar, biomass). Electricity transmission is carried out through the National Power Grid, which plays a key role in the transmission of electricity from producers to distributors and is responsible for the safety and reliability of the National Power System. The structure of the power grid includes very and high voltage overhead power lines, power substations and dispatching. The power infrastructure is composed of 81 power substations, of which 1 power substation at 750 kV (working at 400 kV), 38 power substation at 400 kV and 42 power substations at 220 kV. The distribution of electricity is carried out through the Power Distribution Network, which is an essential part of the national power infrastructure, responsible for the distribution of electricity to consumers. This network includes overhead power lines and power substations at 110 kV providing power to both urban and rural areas. [
1,
2].
B. The importance of the study in the context of ensuring energy security: [
3]
The essential purpose of this paper is to identify all the all elements of instability and insecurity to critical infrastructures within The National Power System, by next actions:
identifies the possible systemic dysfunctions, deficiencies and non-compliances;
identifies the possible vulnerabilities originated from systemic dysfunctions, deficiencies and non-compliances;
identifies the possible risks originated from vulnerabilities;
identifies the possible threats originated from risks ;
identifies the possible hazards orginated from threats;
identifies the possible aggressions originated from dangers.
Knowing all the instability and insecurity elements the following actions can be carried out:
the assessment of the vulnerabilities;
the assessment of the risks;
the assessment of the threats;
the assessment of the hazards;
the assessment of the agressions.
Following the assessment of the vulnerabilities, risks, threats, hazards and aggressions, the following actions can be carried out:
Types of national security strategies:
- a)
The national strategy of security and protection of the critical infrastructures within the National Power System:
power plants for producing electricity;
power substations for transmission of electricity;
overhead power lines for transmission of electricity.
- b)
The national strategy of power safety focused on The National Power System:
power plants for producing electricity;
power substations for transmission of electricity;
overhead power lines for transmission of electricity.
Because The National Power System is vulnerable, it can be, at any time, the target of terrorist threats or attacks (bomb or cyber attacks), natural risks (calamities caused by nature) and anthropic risks (caused by man), which could endanger the proper functioning, or in the most unfortunate case, its total outage – black-out, generating a major crisis that could cause extreme damage to the citizen, society and state.
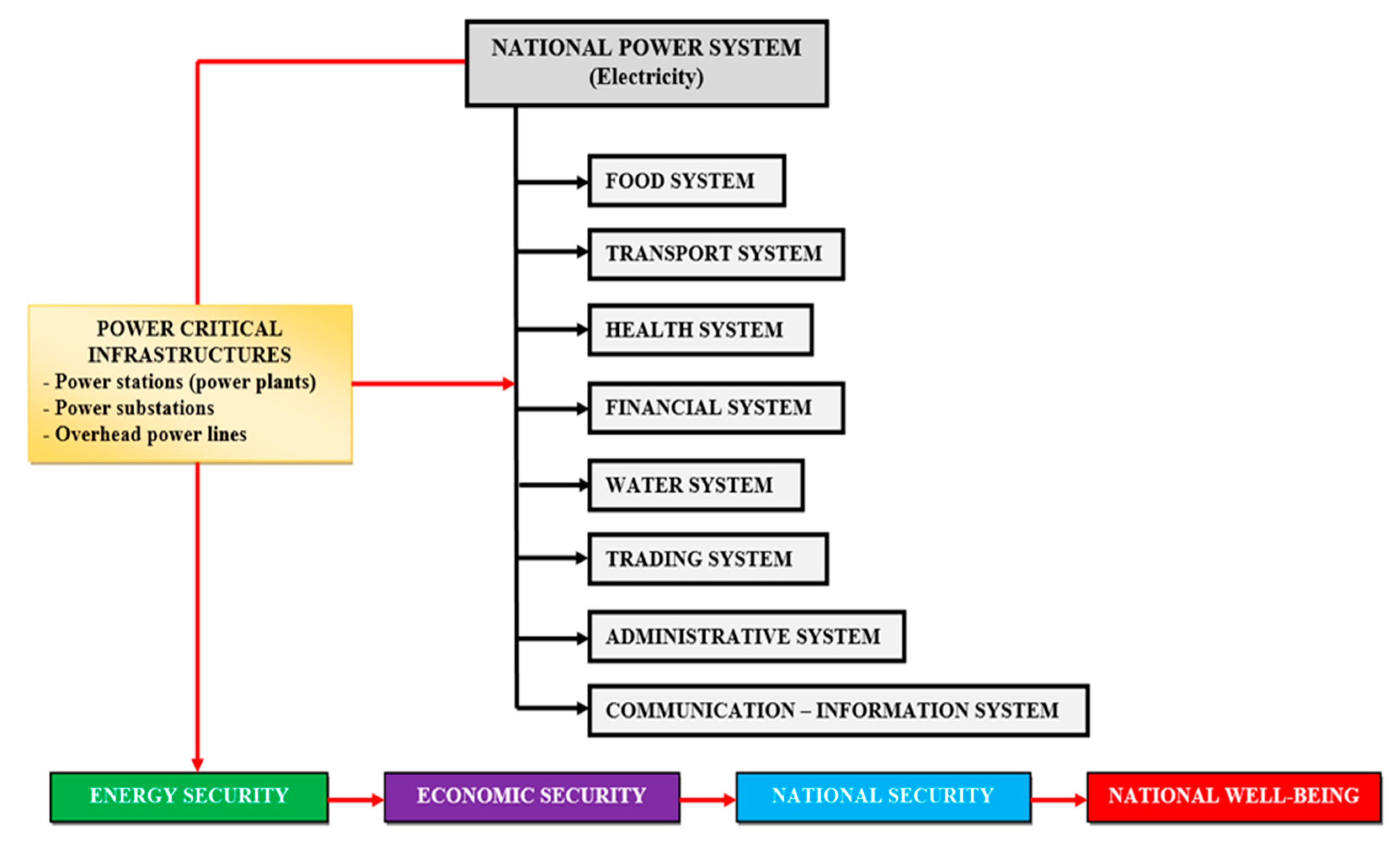
The National Power System is the generator of critical infrastructures (power plants, power substations and overhead power lines), because it ensures the health and safety of the citizens by supplying all of the state systems, the industry and the national economy with electricity and has a substantial contribution to ensuring national security and well-being, as shown in
Figure 2. [
4].
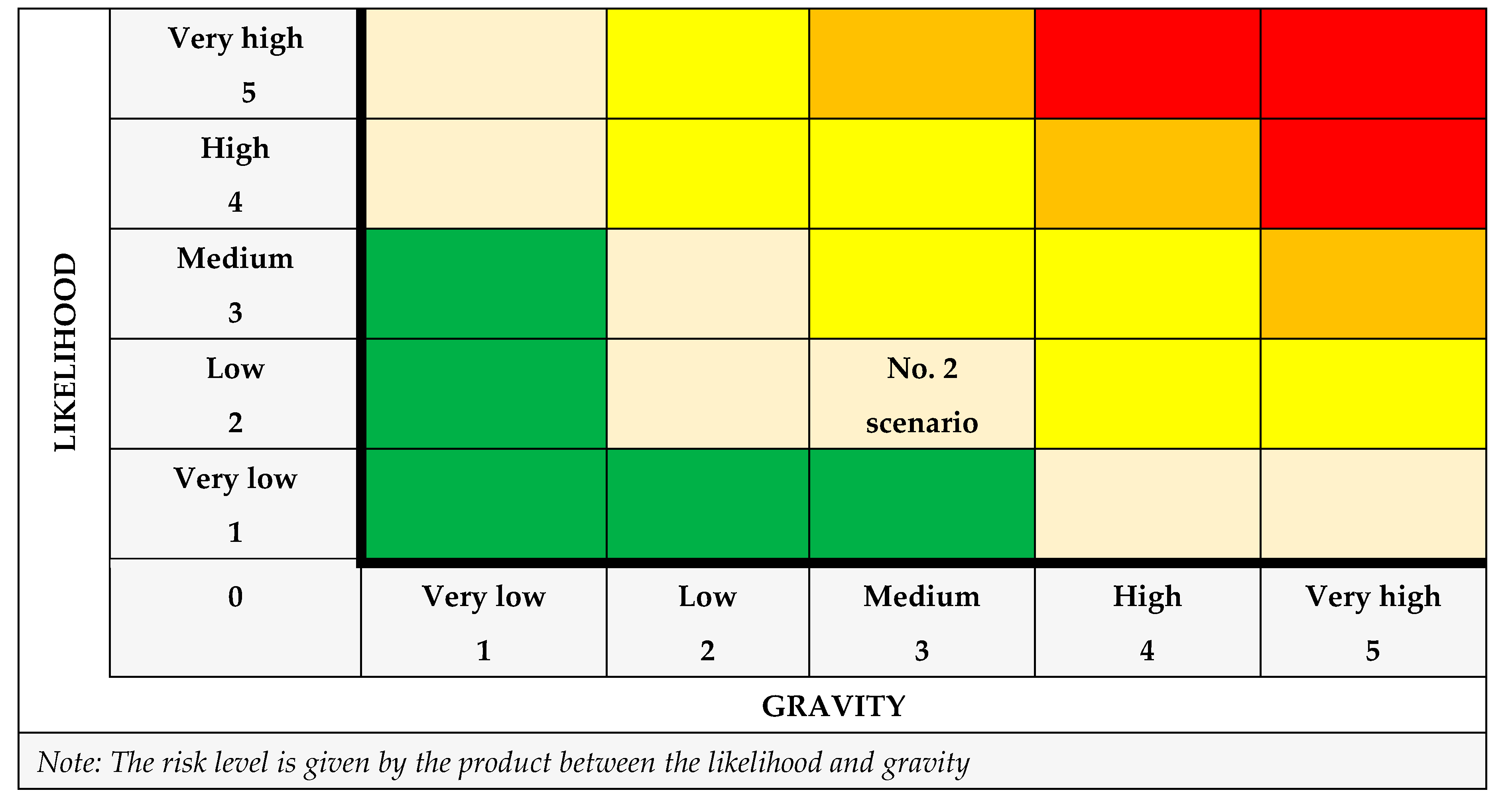
C. The risk analysis – Quantitative risk matrix on 5 levels: [
5]
Defining likelihood and impact levels:
A. Likelihood (L):
1: Very low;
2: Low;
3: Medium;
4: High;
5: Very high.
B. Impact (I):
1: Very low;
2: Low;
3: Medium;
4: High;
5: Very high.
Building the risk matrix:
where:
Following the calculations, we get:
The classification of the risks:
The risks shall be classified according to the FR value obtained:
FR between 1 and 3: Very low risk;
FR between 4 and 6: Low risk;
FR between 7 and 12: Medium risk;
FR between 13 and 16: High risk;
FR between 17 and 25: Very high risk.
Example: Suppose we have a risk with:
medium likelihood: 3;
high impact: 4;
FR = 3∙4 = 12;
medium risk level: 12.
This matrix model allows for a clear and structured risk assessment, facilitating their identification and effective management.
The residual risk calculation:
Residual risk (RR) is the remaining risk after applying the control factors.
The control factors are used to reduce the risk.
These factors may include preventive, detector, and corrective measures.
Each control factor has an efficiency (E) between 0 and 1, where 1 means maximum efficiency.
Example: Suppose we have a risk with:
The assessment of the combined risk:
For multiple risks, we evaluate the combined risk (CR) using an aggregation method, such as the weighted amounts of individual risks:
where:
(FRi) is the risk factor for the risk i;
(Wi) is the weight assigned to risk i.
Note:
To develop previous relationships, a risk factor must be identified.
The identification of risk factors relevant to the specific context (for example, environmental, financial, operational, technological risk, etc.).
2. State of Art—Recent Evolution
Identifying the instability and insecurity elements (dysfunction, deficiences, non-compliances, vulnerabilities, risks, threats, hazards and agression) of a power system is crucial to ensuring energy security, reducing risks and promoting sustainability. Here are some main reasons why this analysis is crucial: Ensuring Energy Security (the vulnerabilities of an power system can lead to power supply disruptions, affecting the economy and quality of life, while identifying weak points allows for the development of resilience strategies), Managing Geopolitical Risks (electricity is often used as a geopolitical tool, and excessive dependence on fossil fuel imports from certain regions can expose states to major risks in the event of international conflicts or economic sanctions), Adapting to Climate Change (climate change affects power infrastructure through extreme weather events, and assessing vulnerabilities enables the development of adaptation solutions and investments in renewable sources), Protection Against Cyber and Physical Attacks (power systems are increasingly digitalized, making them vulnerable to cyberattacks; additionally, physical infrastructure: power stations and high-voltage overhead and underground power lines, can be targeted by terrorist attacks or sabotage), Ensuring Equitable Access to Energy (many regions of the world still lack stable access to electricity, and identifying vulnerabilities helps in developing effective electrification and economic development policies), Stabilizing Energy Markets and Preventing Economic Crises (electricity prices are influenced by the vulnerabilities of power systems, and energy crises can destabilize entire economies, making continuous risk analysis essential), Developing Resilient and Sustainable Energy Systems (identifying vulnerabilities helps build flexible systems based on energy source diversification, energy storage, and the development of smart grids). The analysis of instability and insecurity elements within an power system is essential for ensuring energy security, economic stability, and environmental protection. It allows for the identification of risks, threats, hazards, and aggressions that may affect energy supply and provides solutions to mitigate their impact. [
6,
7,
8,
9,
10,
11,
12,
13,
14,
15,
16,
17,
18,
19,
20,
21,
22,
23,
24,
25,
26,
27,
28,
29,
30,
31]
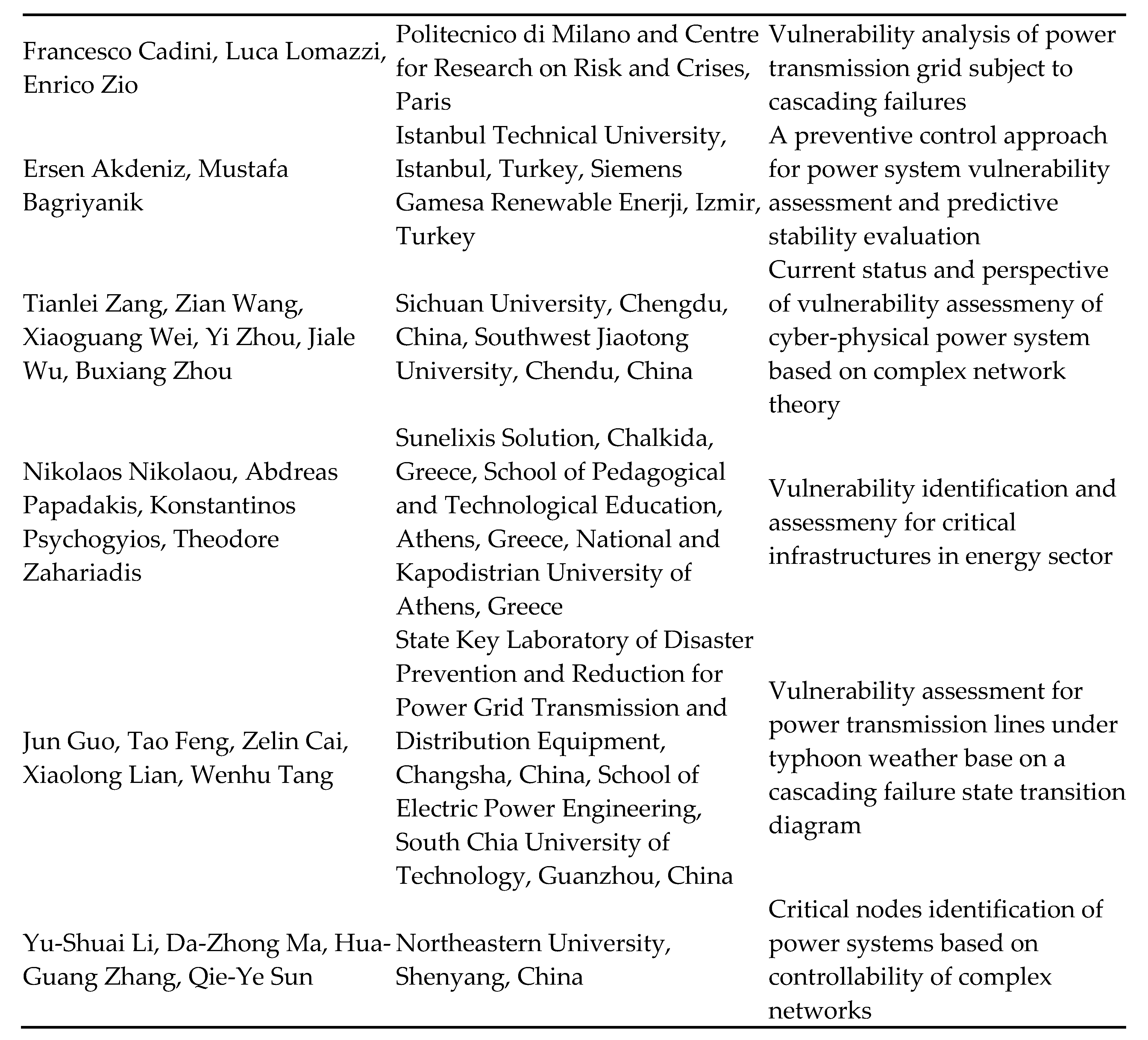
Worldwide research on the insecurity and instability of power systems, as well as the analysis and identification of vulnerabilities, risks, dangers and aggressions on them, are summarized:
3. Identification and Definition of the Instability and Insecurity Elements
3.1. Identification
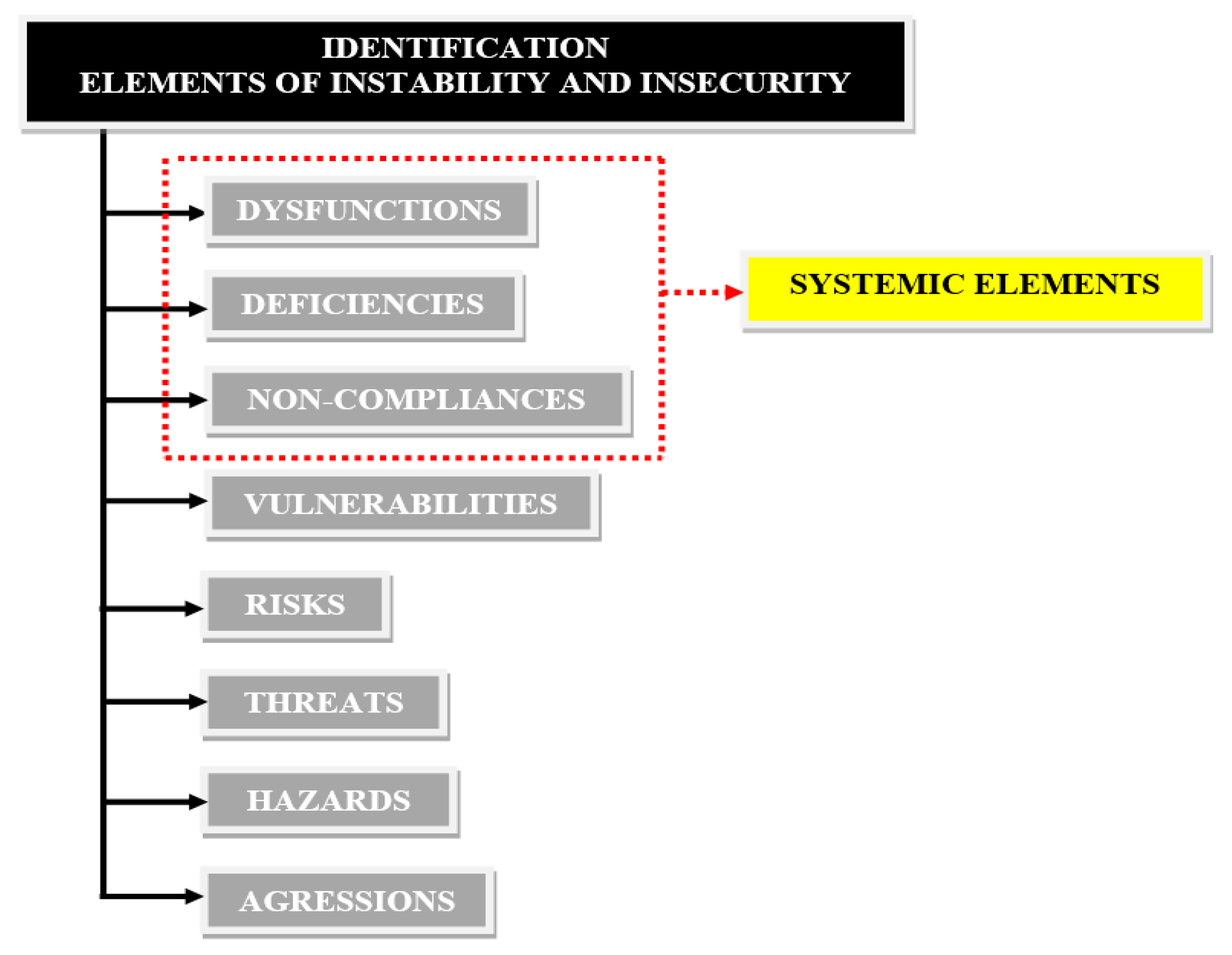
The following instability and insecurity elements are identified for critical infrastructures within The National Power System, through The Power Transmission Grid, as shown in
Figure 3: [
29]
- a)
-
Systemic elements:
dysfunctions;
deficiencies;
non-compliances.
- b)
Vulnerabilities
- c)
Risks;
- d)
Threats;
- e)
Hazards;
- f)
Agressions.
3.2. Definition
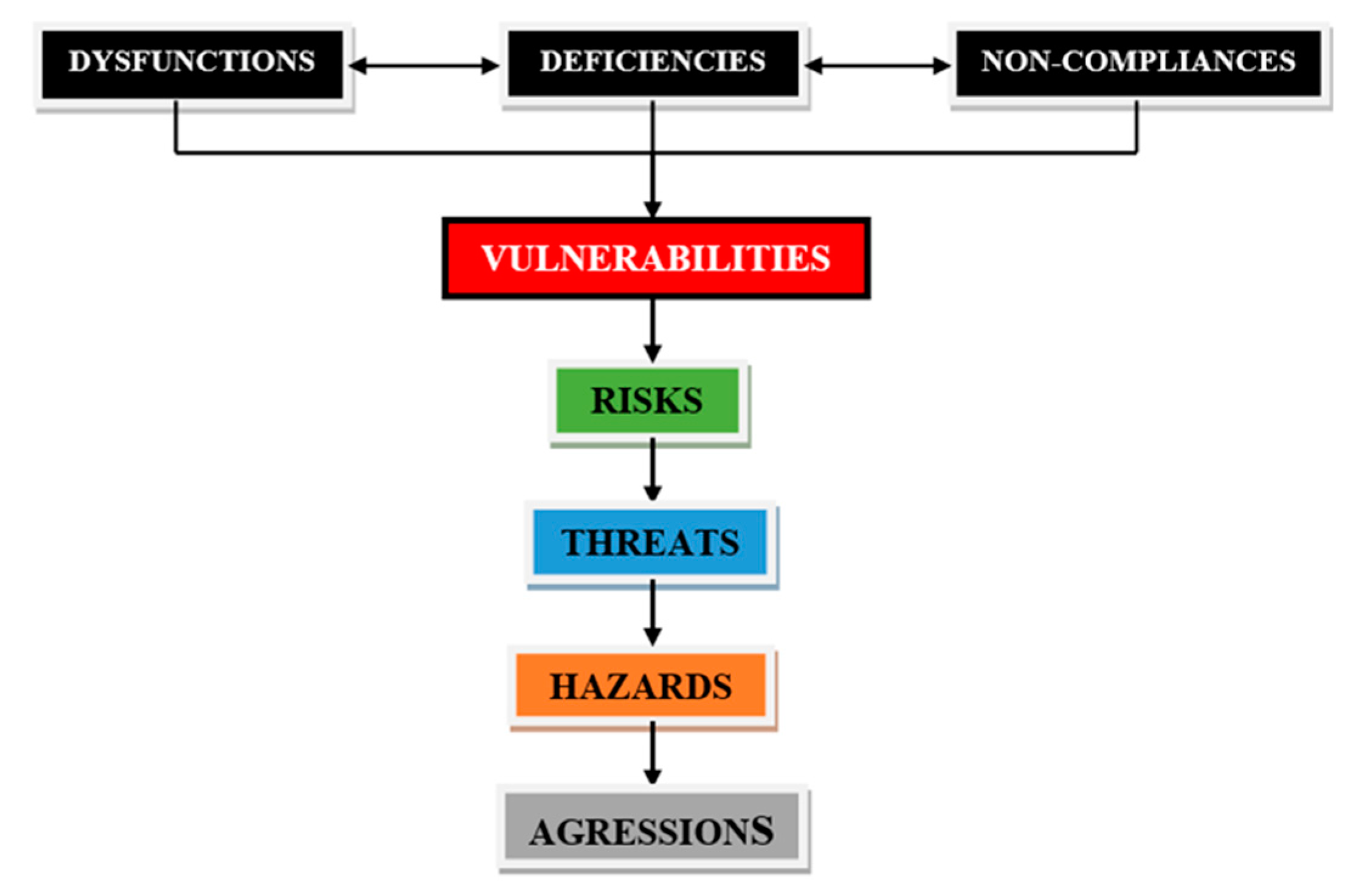
A. Systemic elements
a) Dysfunctions: The dysfunctions are those actions manifested by failures and/or disturbances of the functions of a system, with the effect of reducing, integrating or adapting of critical infrastructure, and the unidentification, superficial treatment or poor management of the dysfunctions automatically generates vulnerabilities, which can affect the smooth running of the critical infrastructure.
b) Deficiencies: The deficiencies represents the lack of physical attributes manifested by defects or gaps and are characterized by deficiency, and a critical infrastructure with deficiencies cannot operate at its normal parameters and urgent re-commissioning or resilience measures must be taken.
c) Non-compliances: The non-compliances represents the failure to meet the requirements of a critical infrastructure, manifested by the deviation of some characteristics from the requirements specified in the security plan or operating manual, and a critical infrastructure with non- compliances cannot operate at its normal parameters and urgent measures must be taken to eliminate non- compliances.
B. Vulnerabilities
The vulnerabilities generated by systemic dysfunctions, deficiencies or non-compliances are factual states, processes and phenomena that diminish the responsiveness of critical infrastructures to potential risks or threats or that favor their emergence and development, with consequences in terms of functionality and utility. Non-knowledge, non-management or poor and faulty management of vulnerabilities may result in risk factors, threats, dangers or aggression towards national objectives, values, interests and needs subsumed to critical infrastructures.
C. Risks
The risks generated by certain vulnerabilities, designate situations, circumstances, elements or internal or external conjuctions, sometimes doubled and operative, which determine or favor the materialization of a threat to critical infrastructure, generating insecurity effects.
D. Threats
The threats generated by risk factors are capacities, strategies, intentions, plans that potentiate a danger to critical infrastructures, materialized by attitudes, gestures, acts, facts that create states of imbalance or instability and generate states of hazard, with impact on security.
E. Hazards
The hazards arising from certain threats are situations, events that can endanger or threaten the existence or integrity of critical infrastructures.
F. Agressions
The aggressions arising from certain danger condtions are attacks, including armed attacks, which jeopardize the existence, balance or integrity of critical infrastructures.
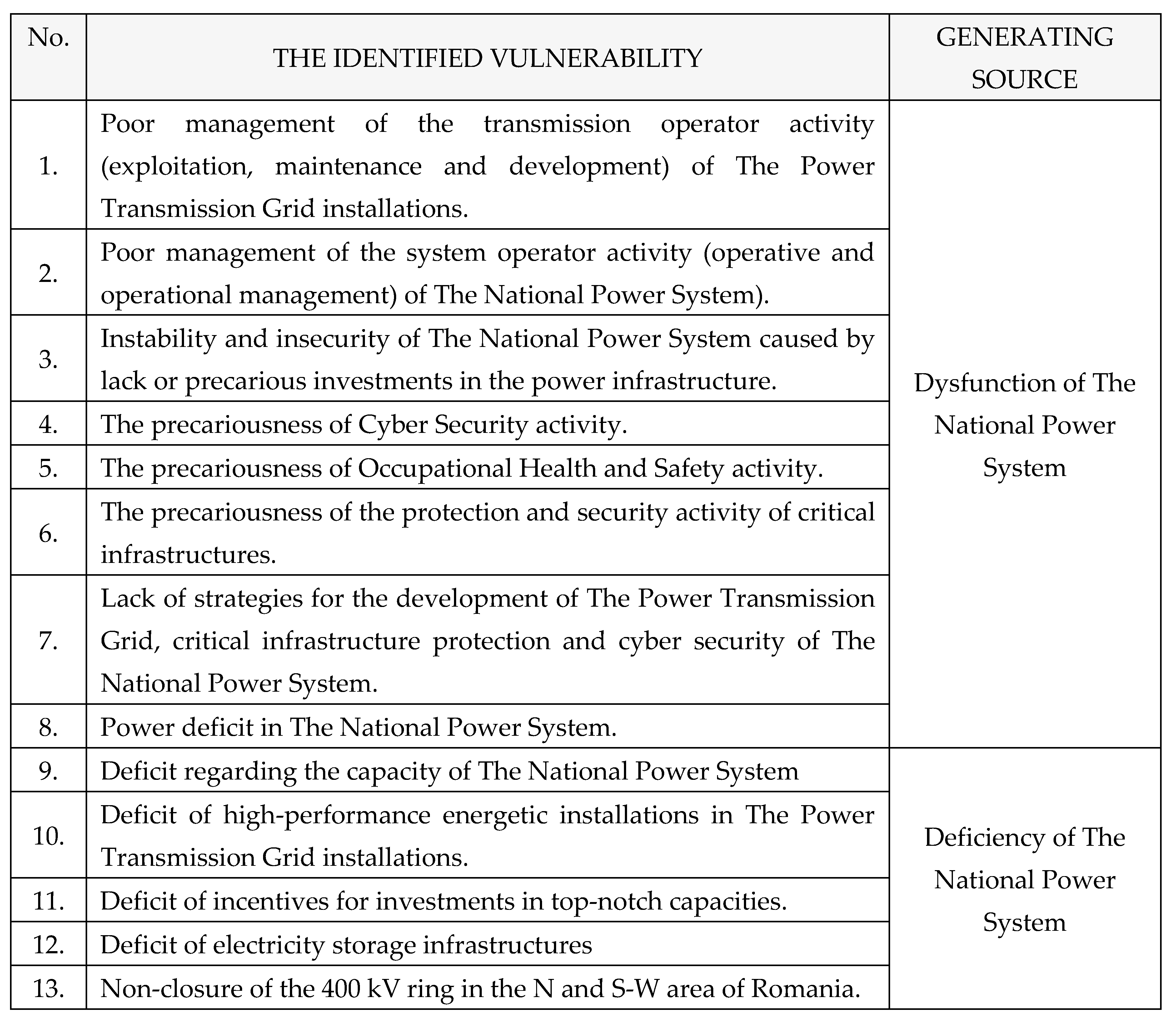
4. Types of the Instability and Insecurity Elements from Romanian Power System
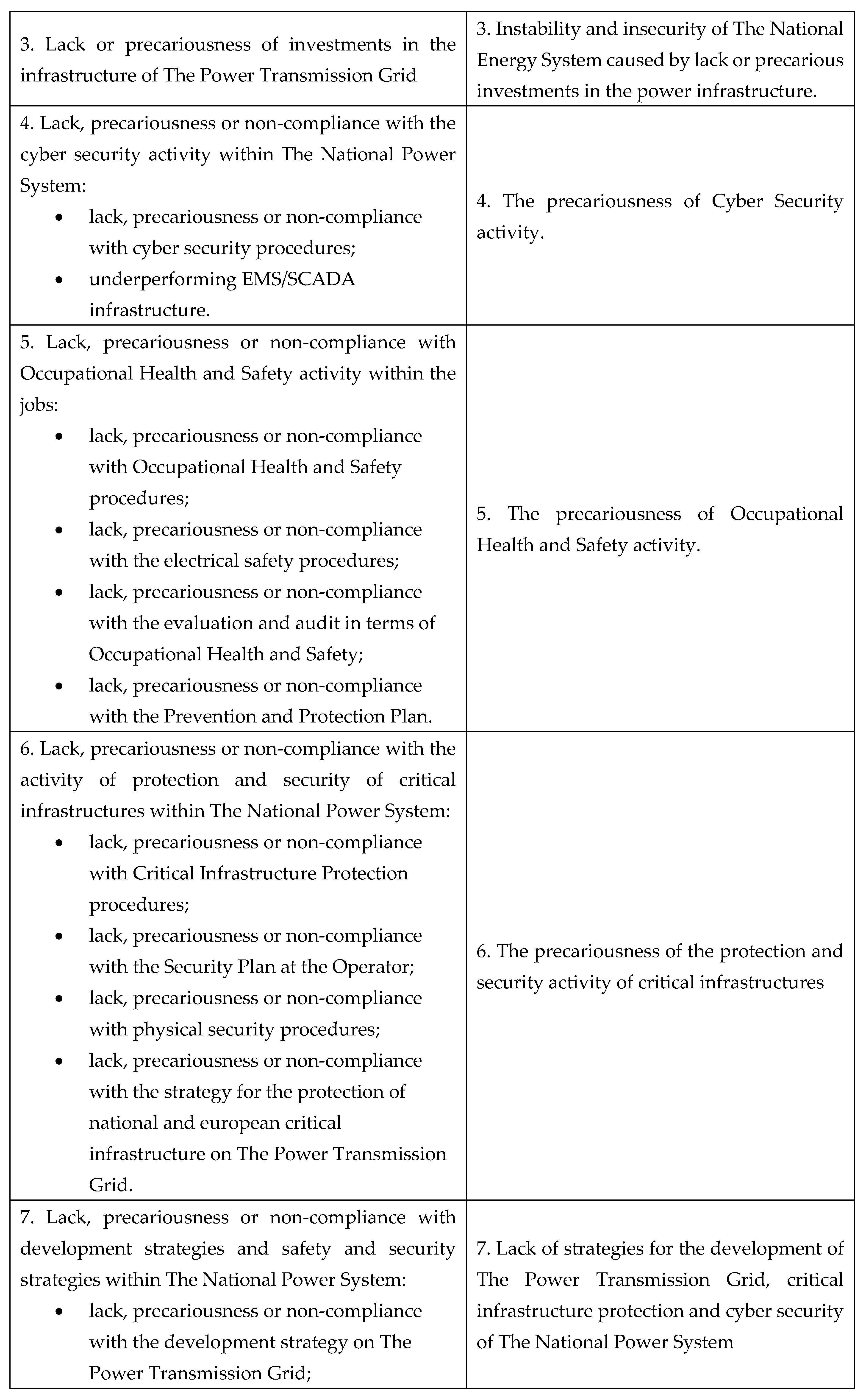
A. Types of systemic elements
a) Dysfunctions: dysfunctions identified within The National Power System, as shown in
Table 1: [
1,
2,
3,
4].
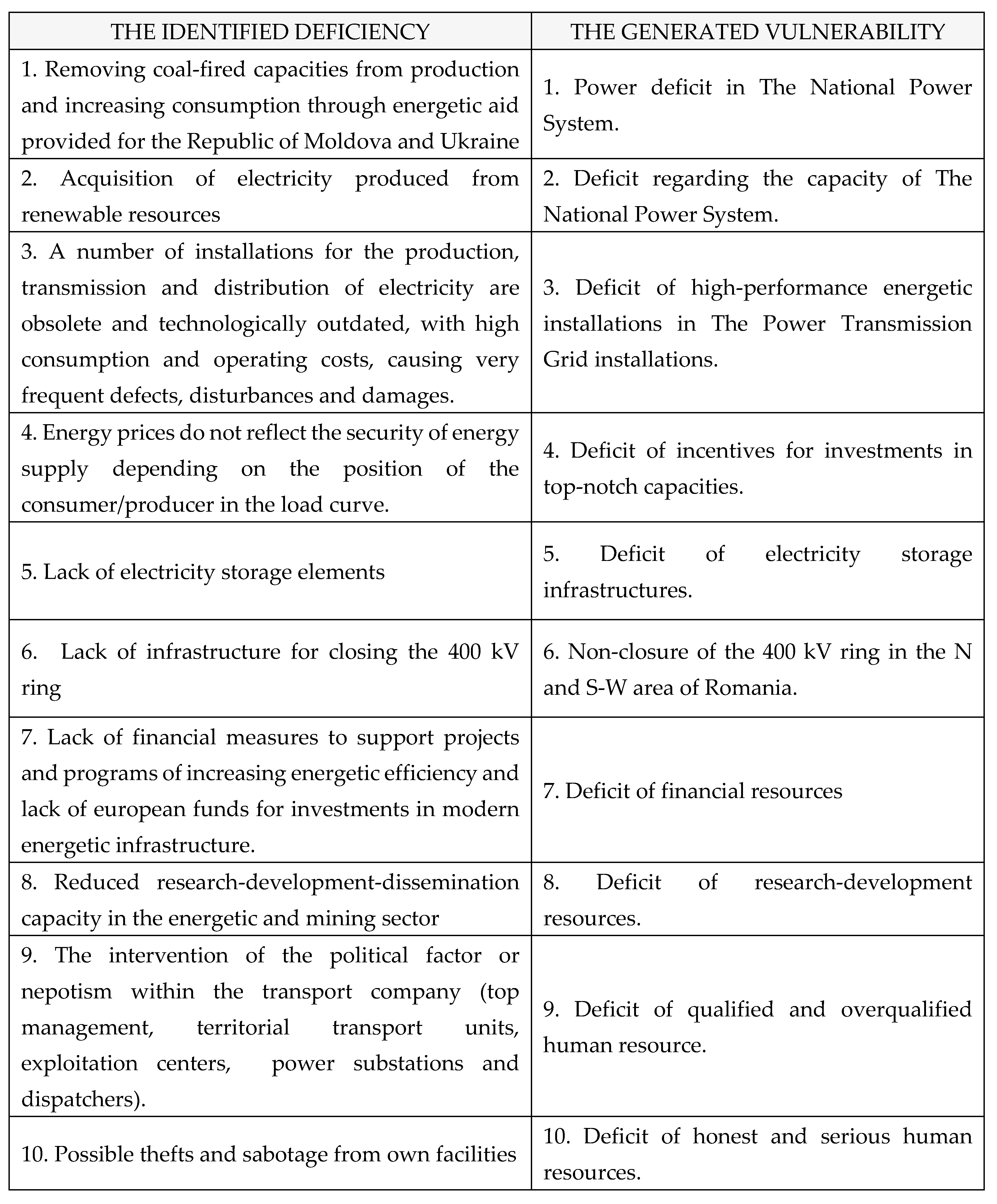
b) Deficiencies: deficiencies identified within The National Power System, as shown in
Table 2: [
1,
2,
3,
4].
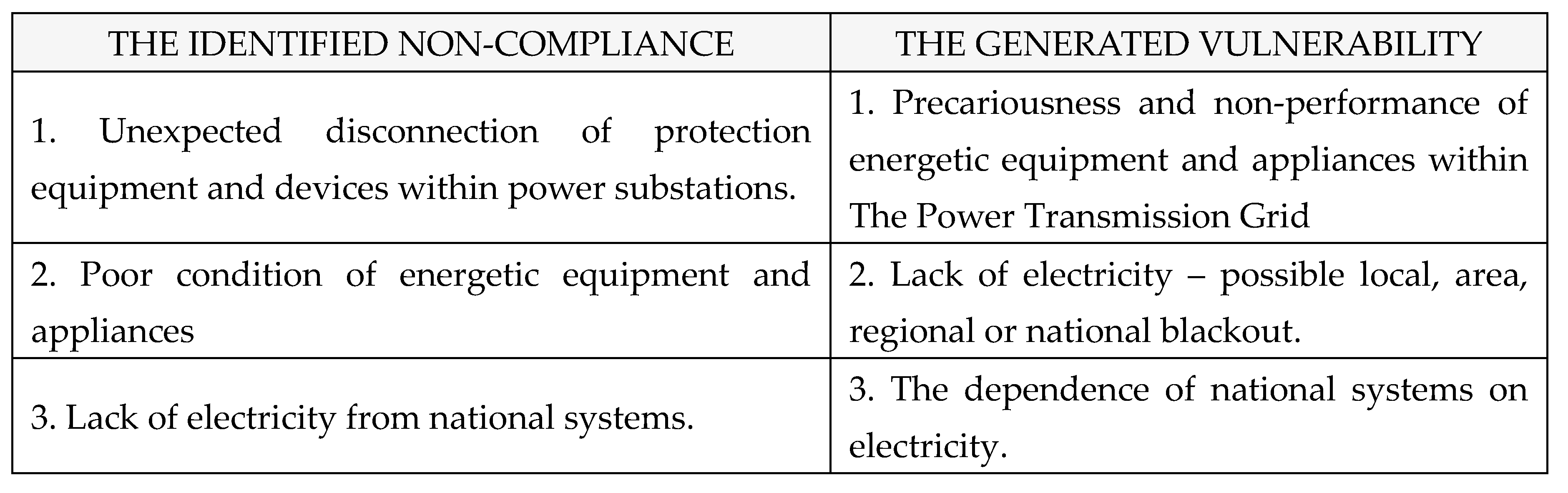
c) Non-compliances: non-compliances identified within The National Power System, as shown in
Table 3: [
1,
2,
3,
4].
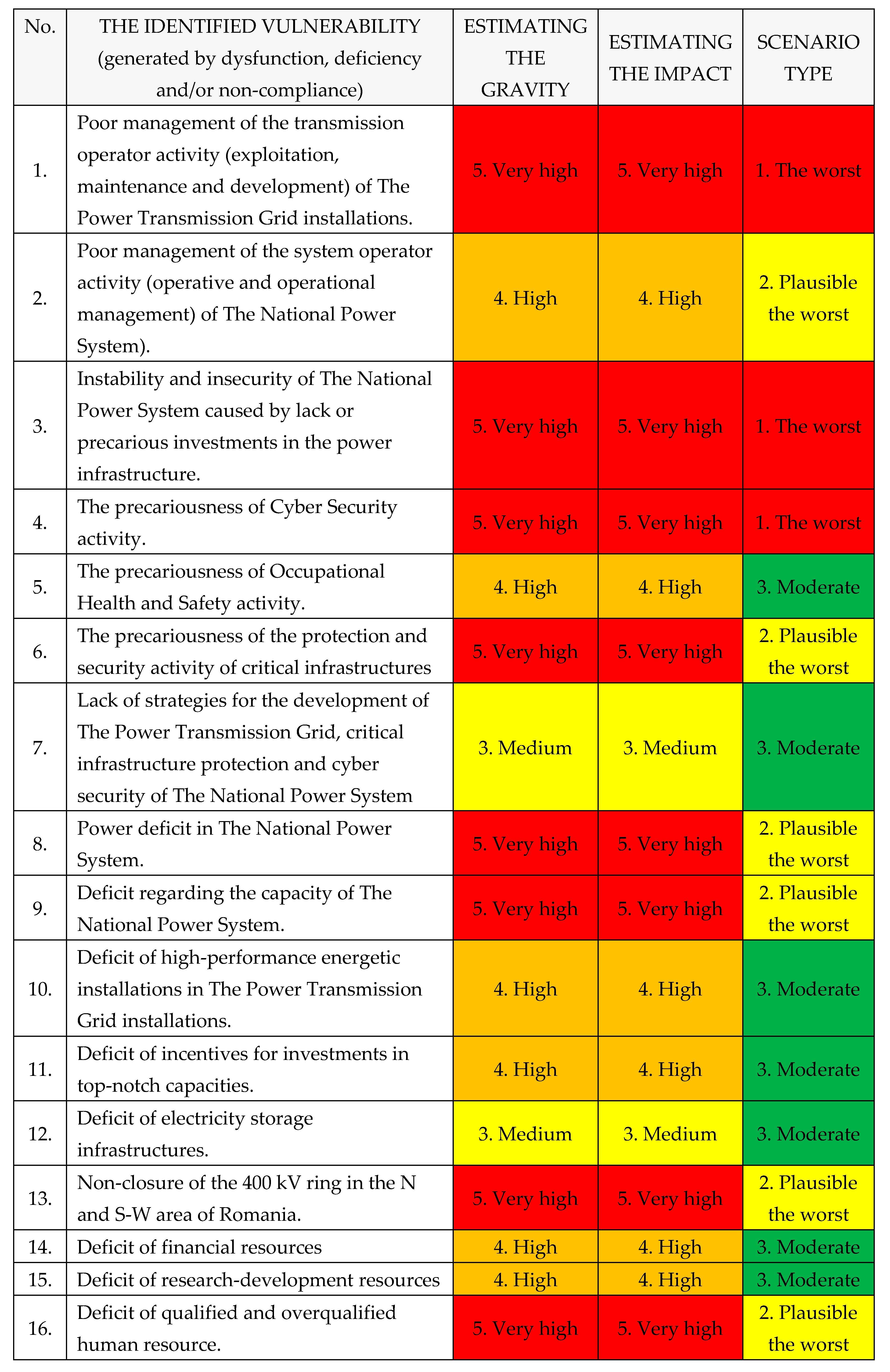
B. Types of vulnerabilities
The vulnerabilities identified caused by systemic elements (dysfunctions, deficiences and non-compliances) within The National Power System are the following, as shown in
Table 4: [
1,
2,
3,
4].
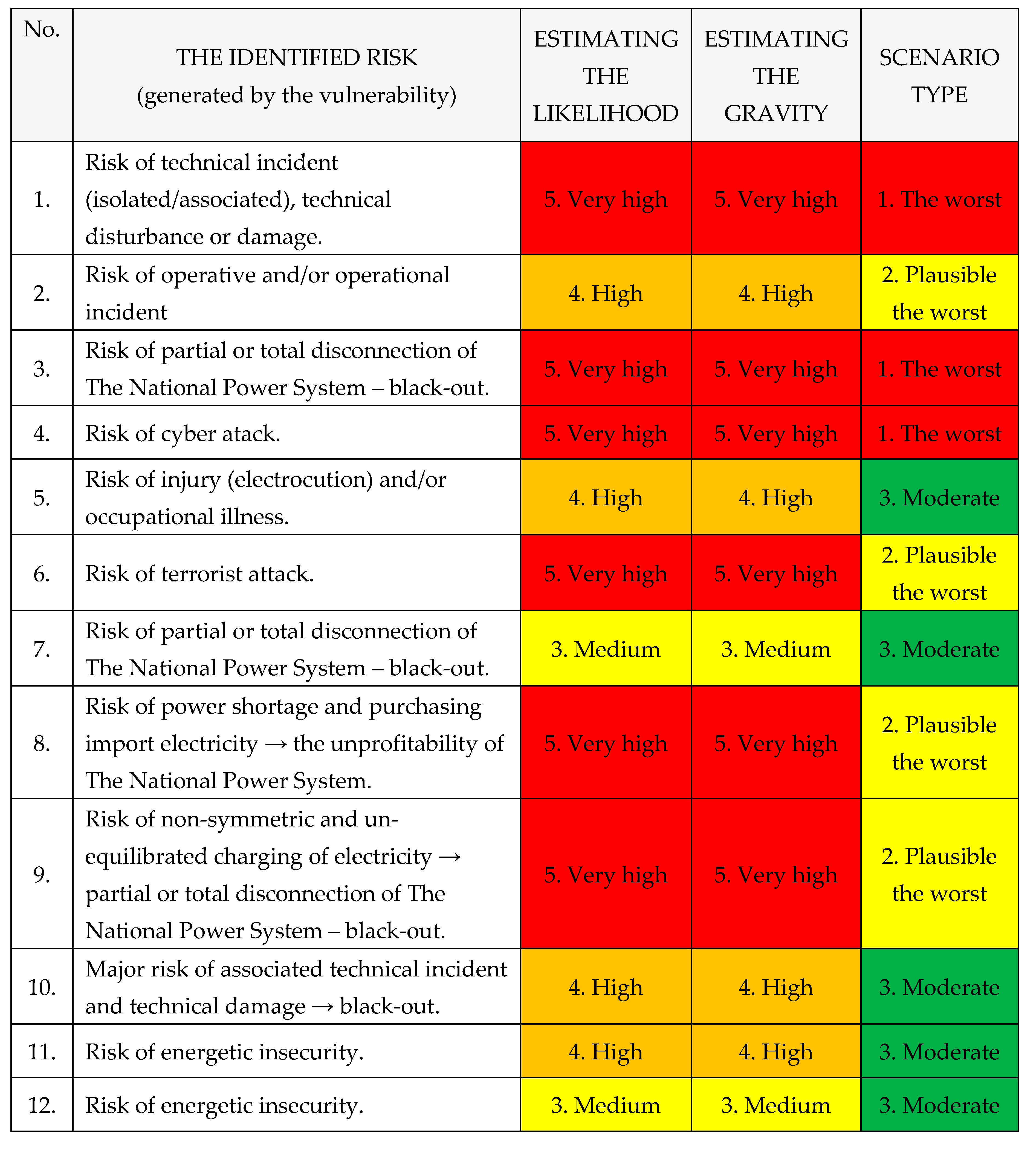
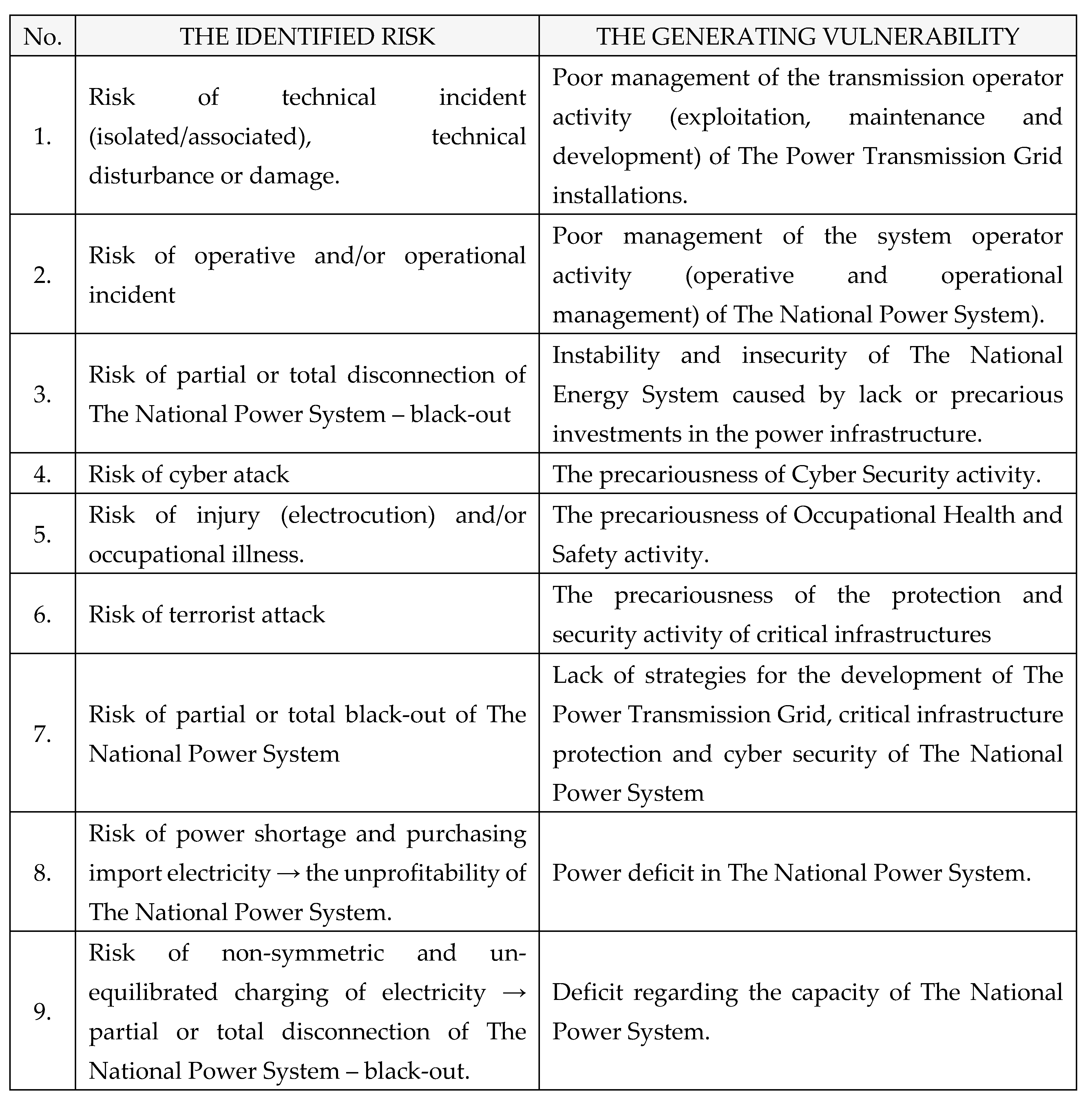
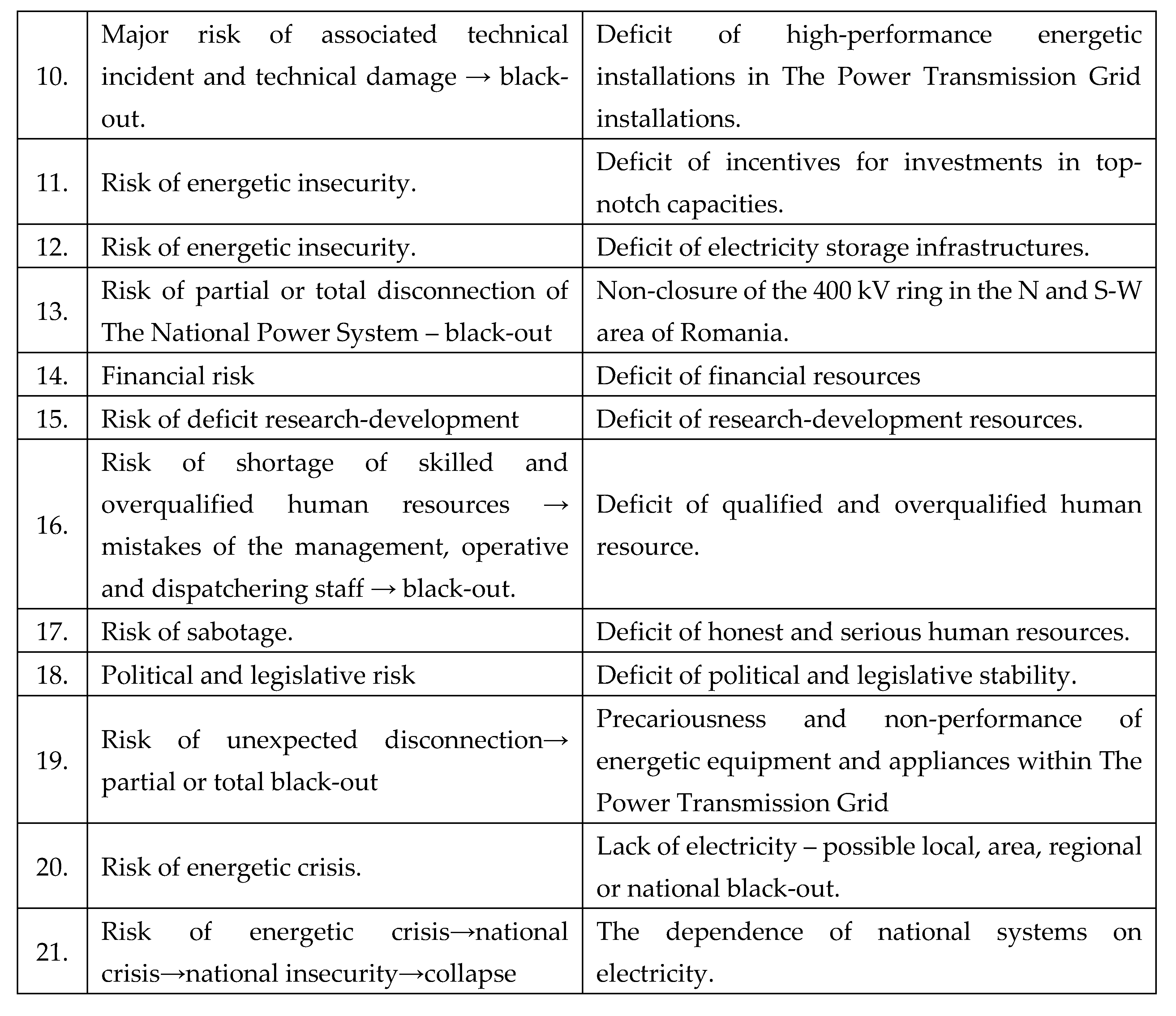
C. Types of risks
The risks identified caused by vulnerabilities within The National Power System are the following, as shown in
Table 5: [
1,
2,
3,
4].
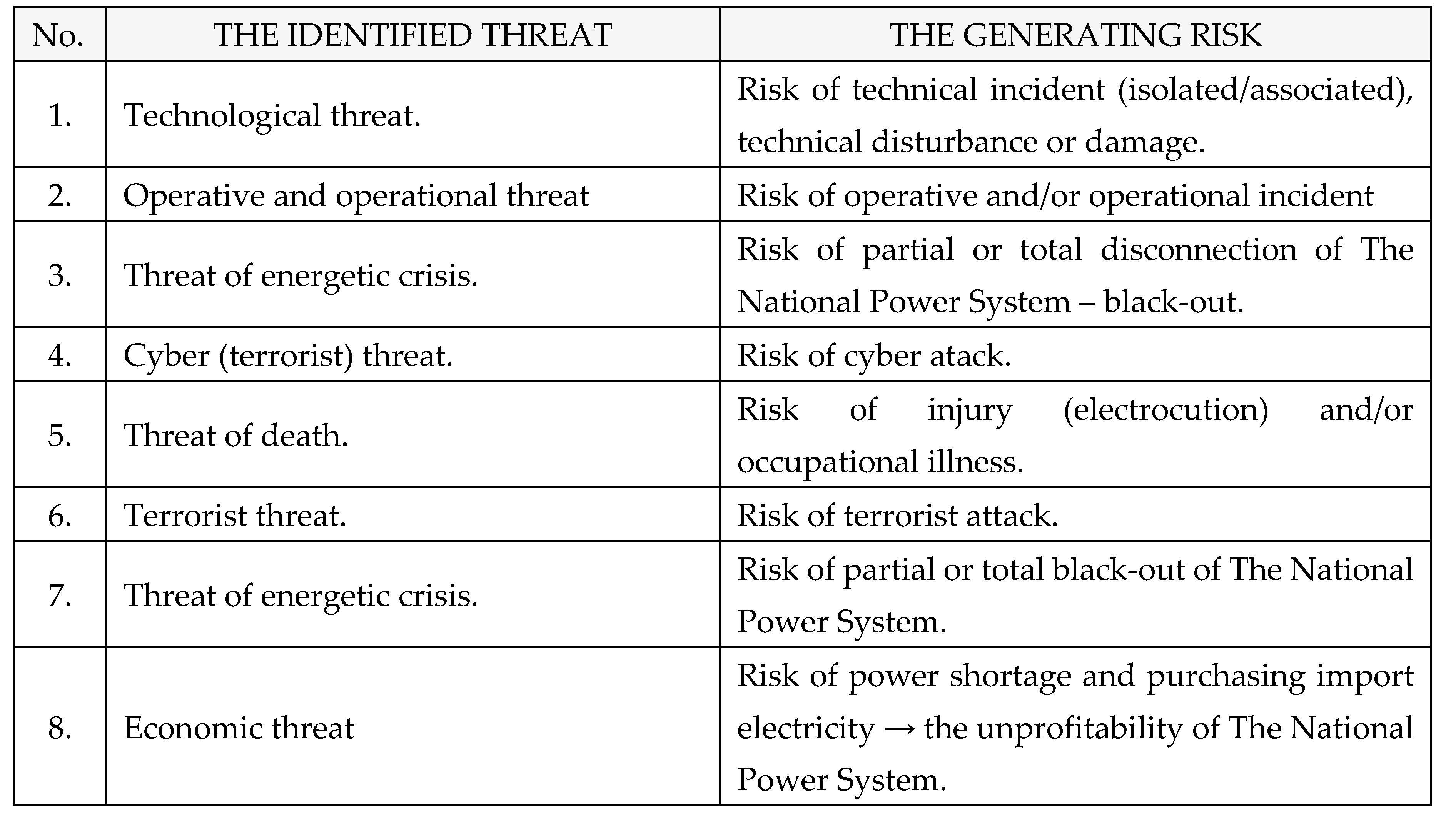
D. Types of threats
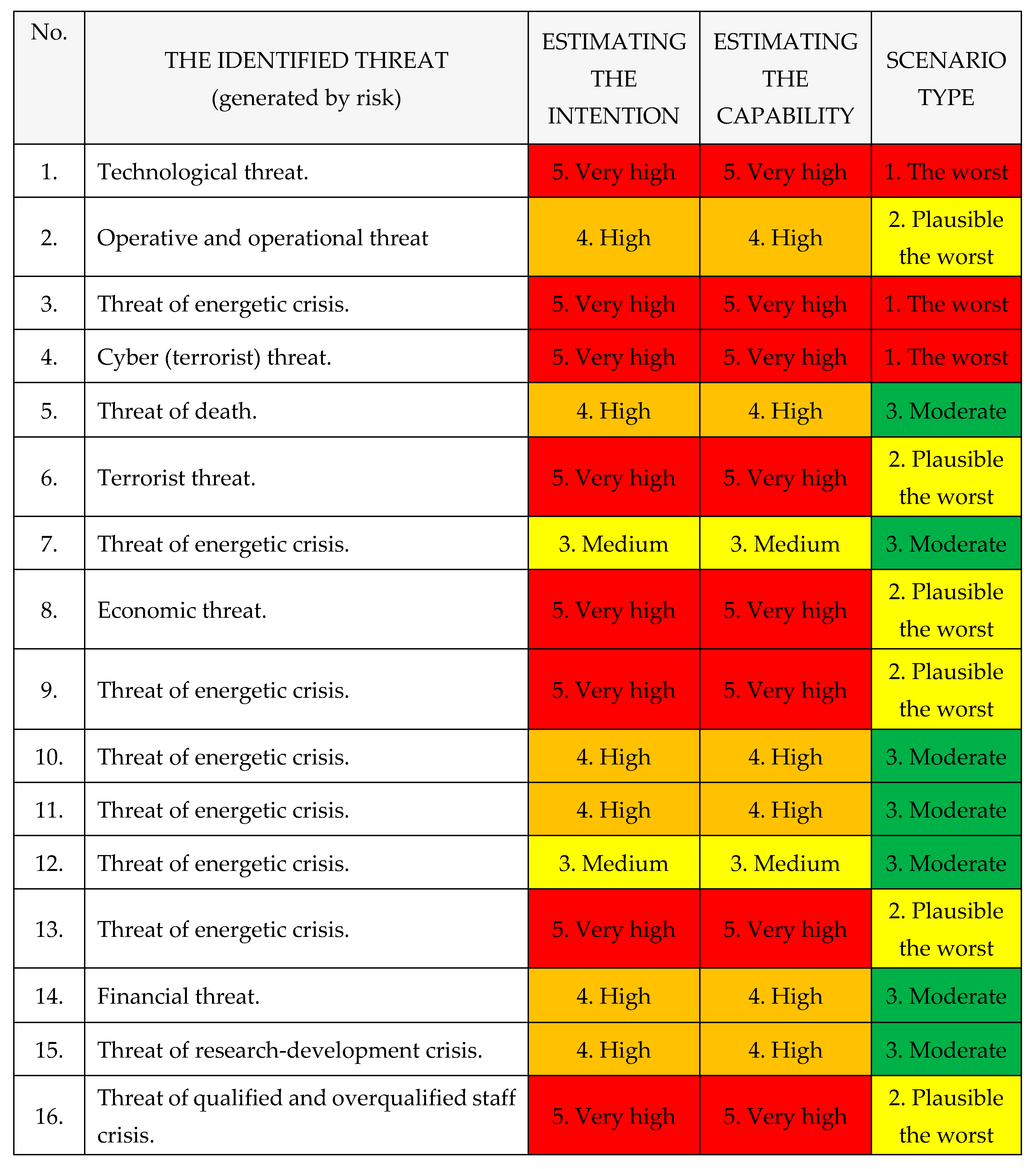
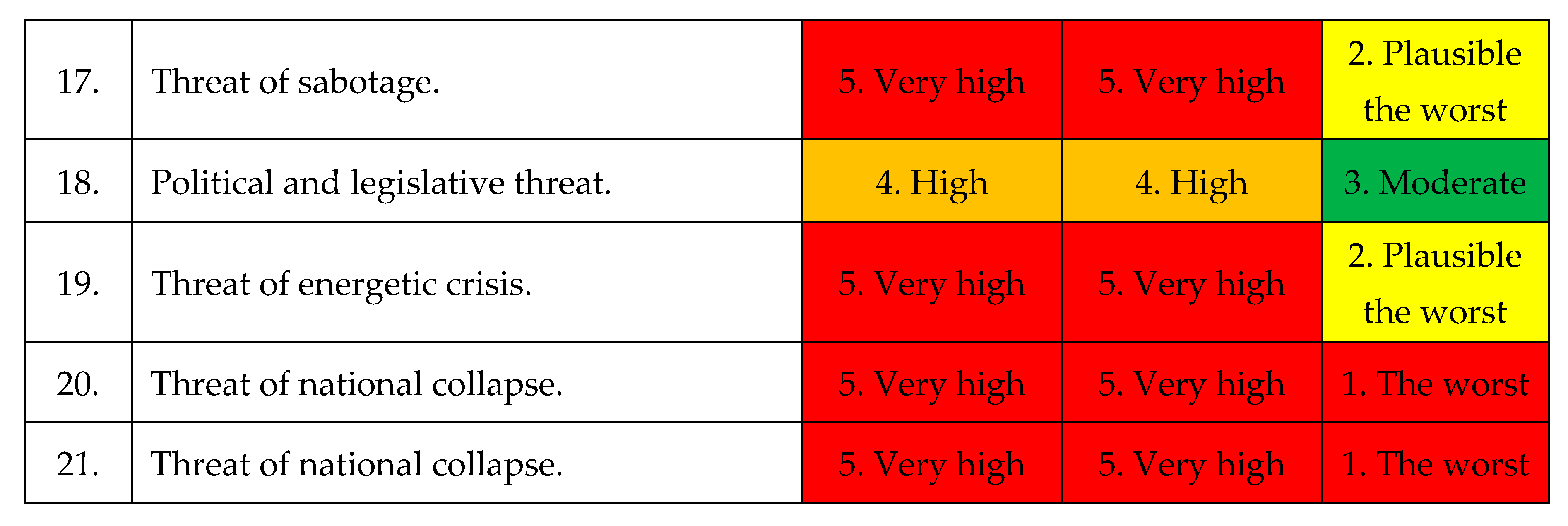
Identified threats caused by risks within The National Power System are the following, as shown in
Table 6: [
1,
2,
3,
4].
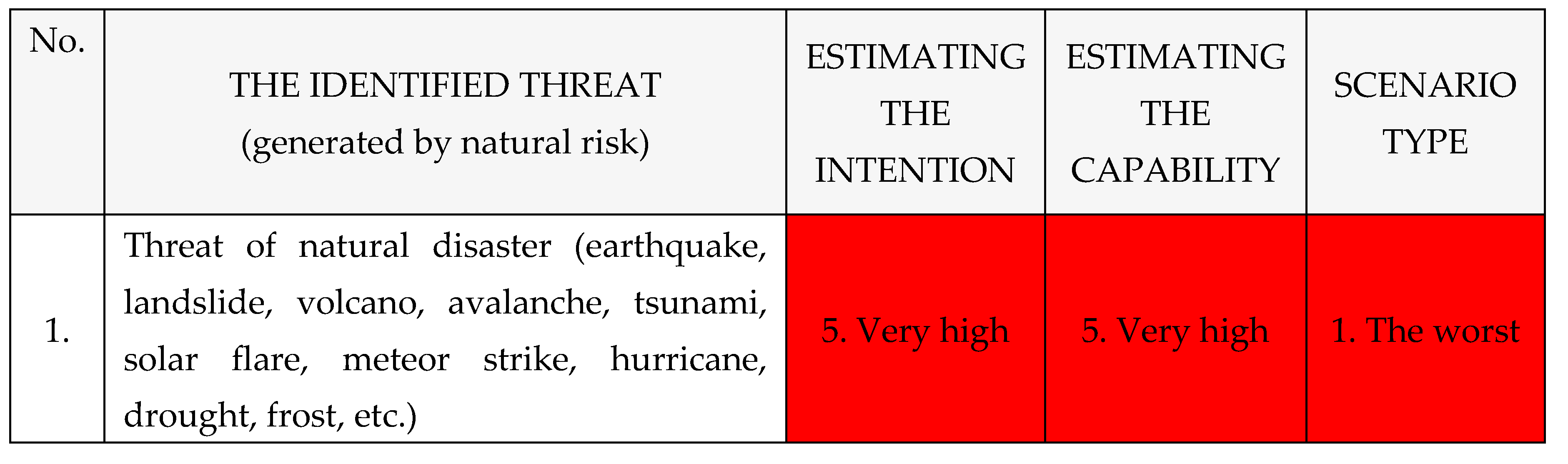
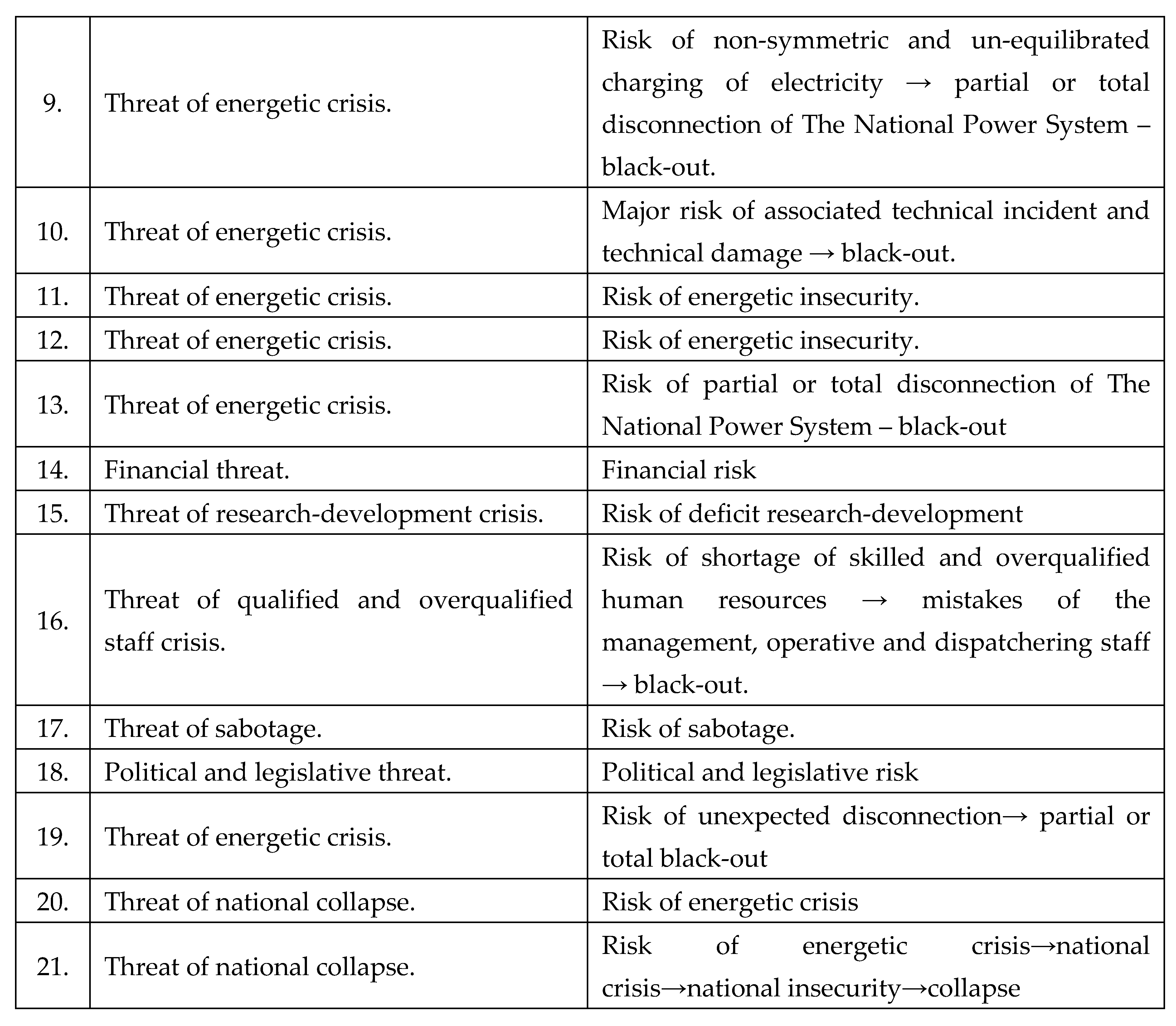
Other identified threats naturally caused with a crisis or collapse effect on The National Power System, as shown in
Table 7: [
1,
2,
3,
4].
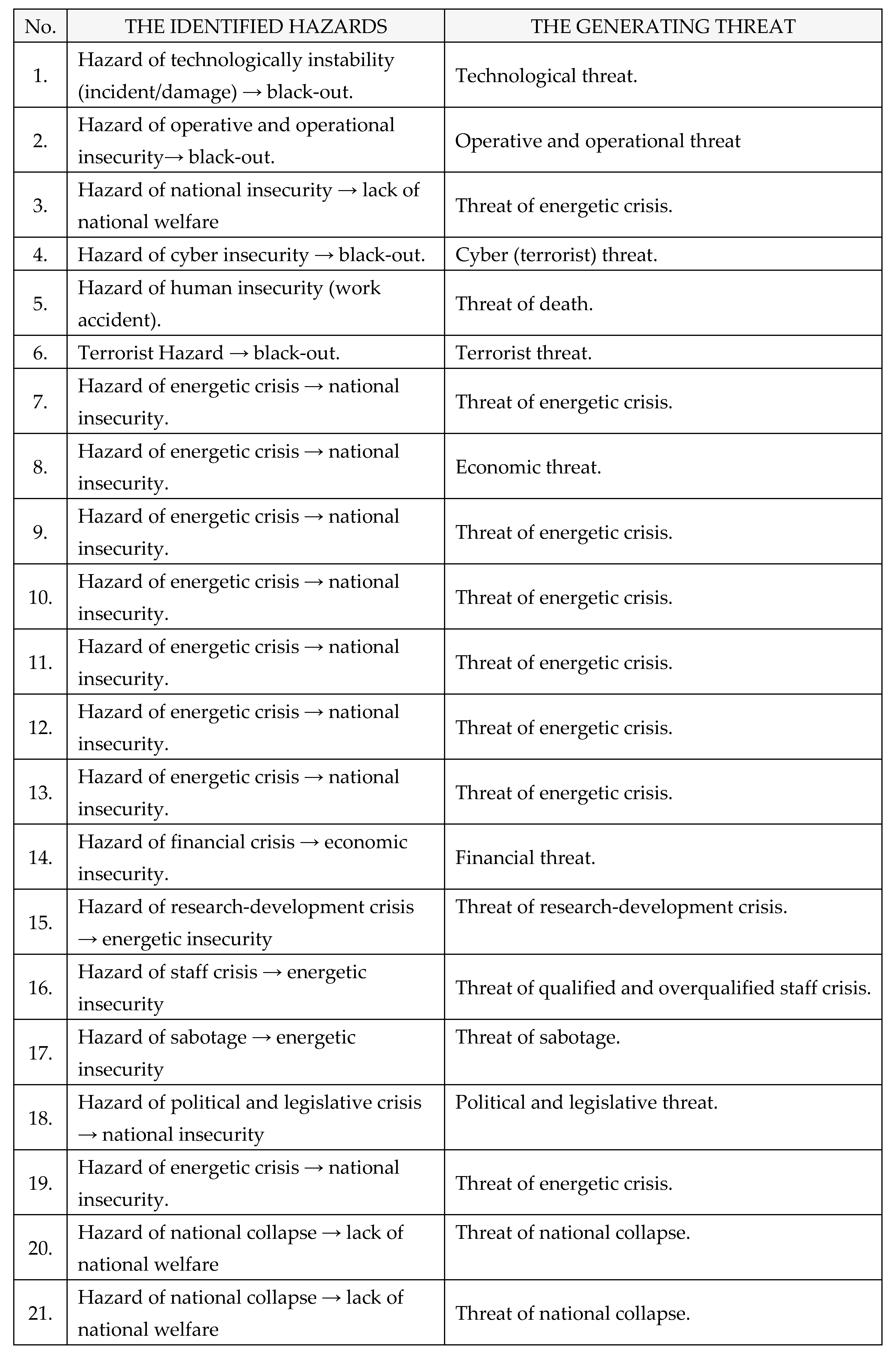
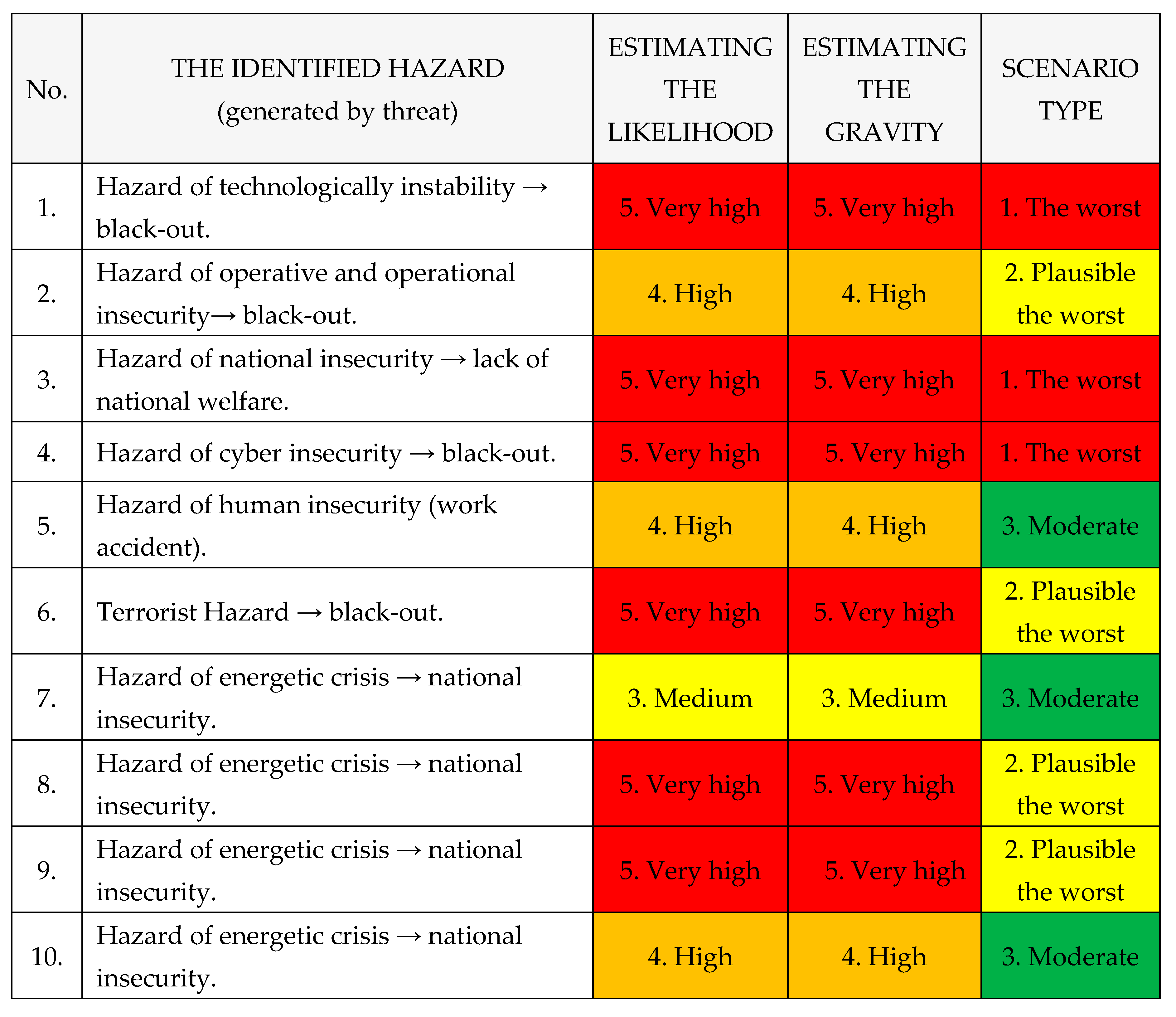
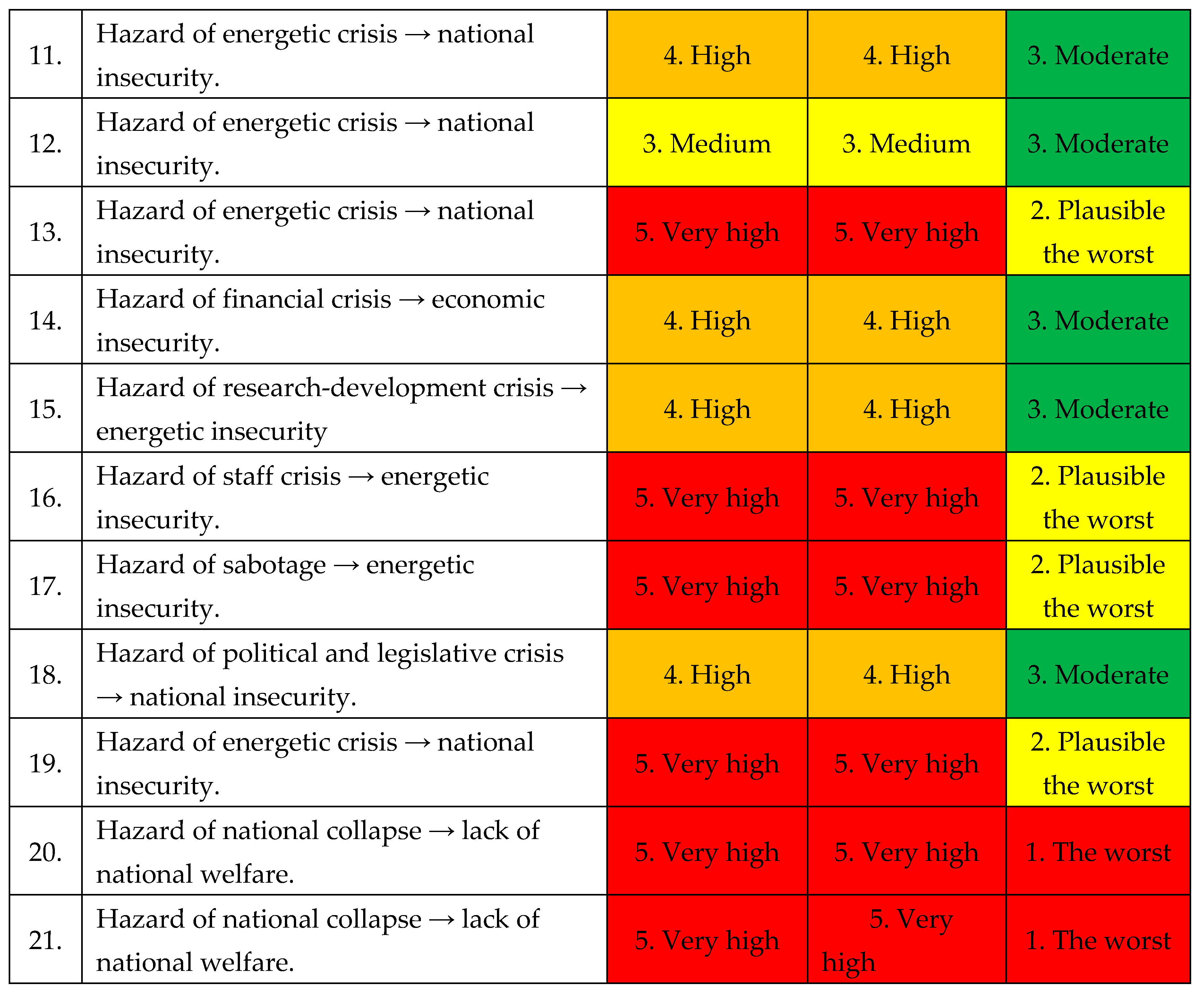
E. Types of hazards
Identified hazards caused by threats within The National Power System are the following, as shown in
Table 8: [
1,
2,
3,
4].
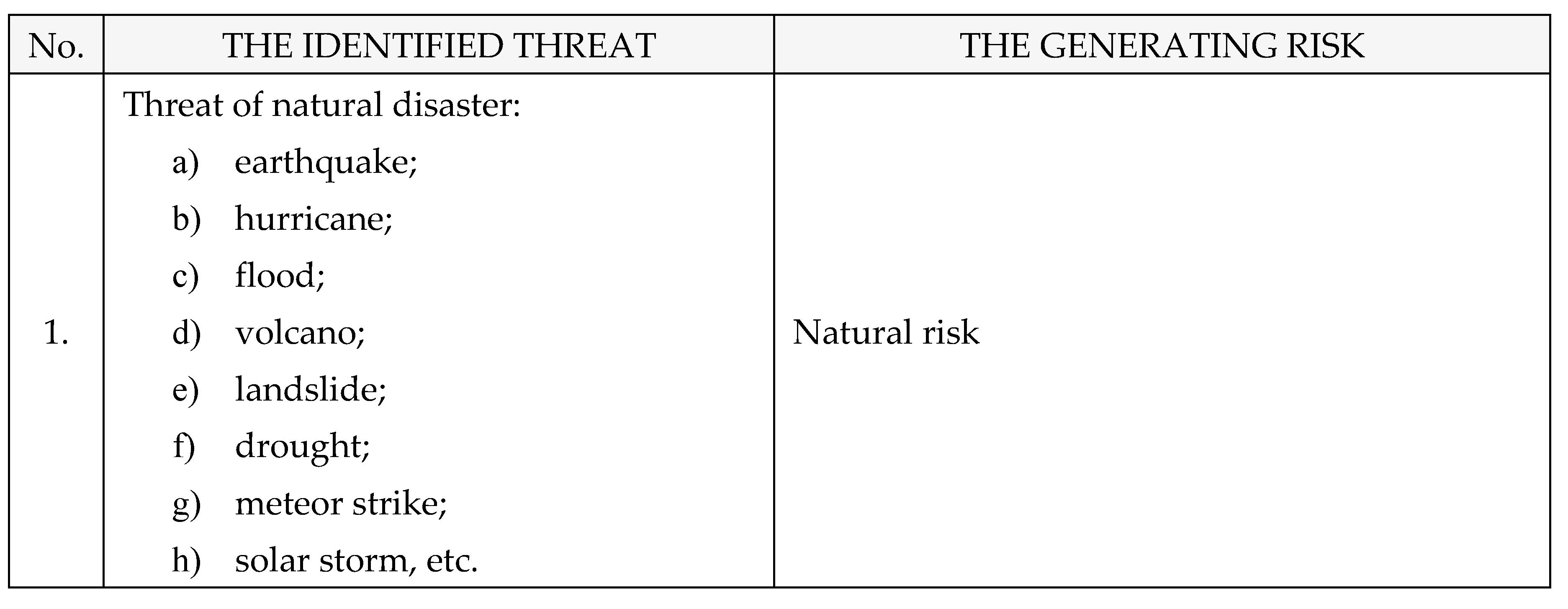
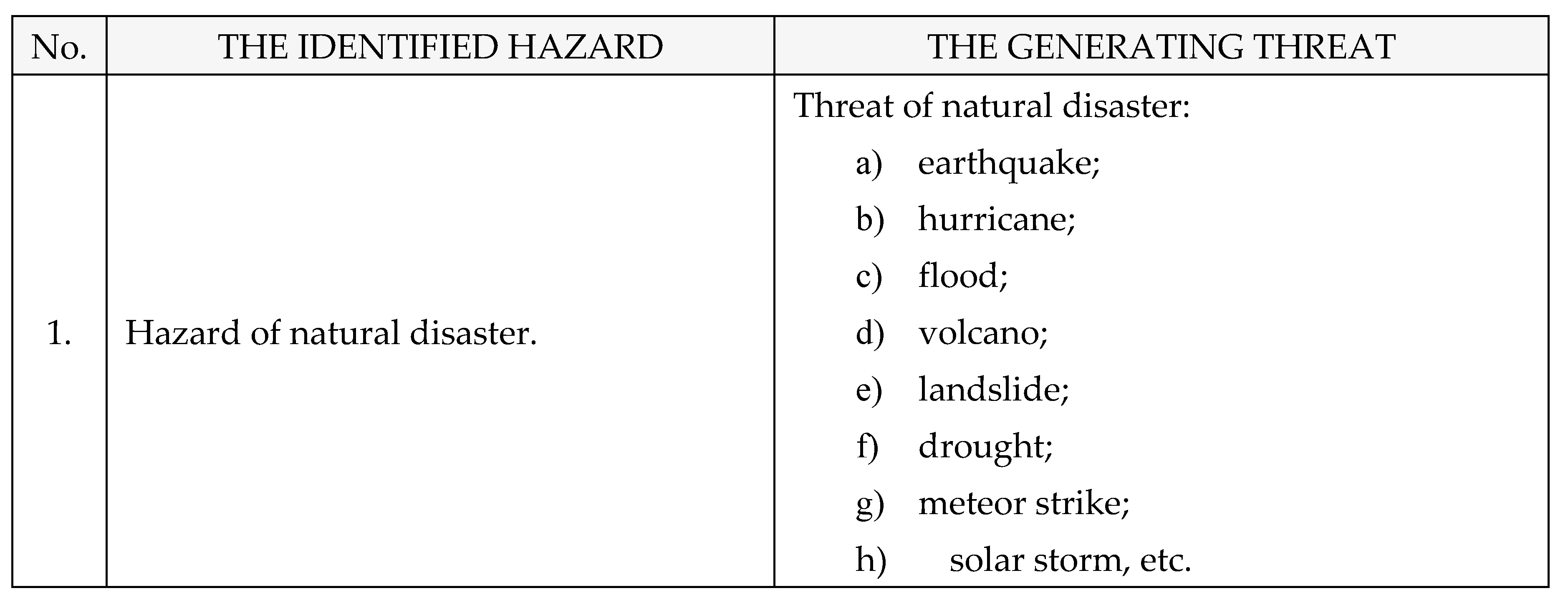
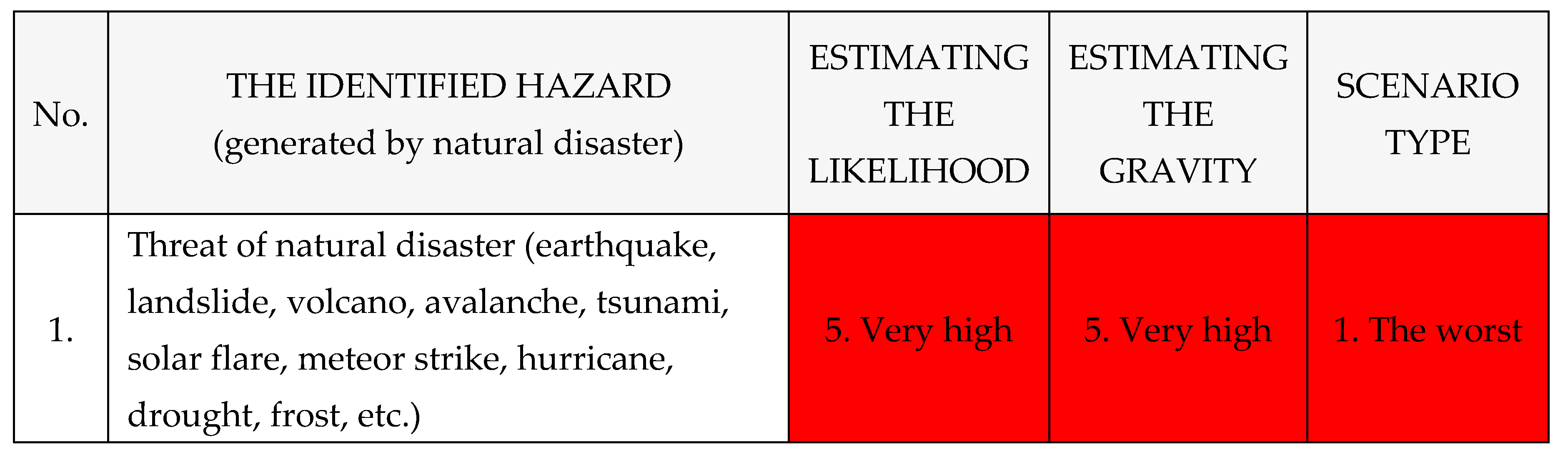
Other identified hazards naturally caused with a crisis or collapse effect on The National Power System, as shown in
Table 9: [
1,
2,
3,
4].
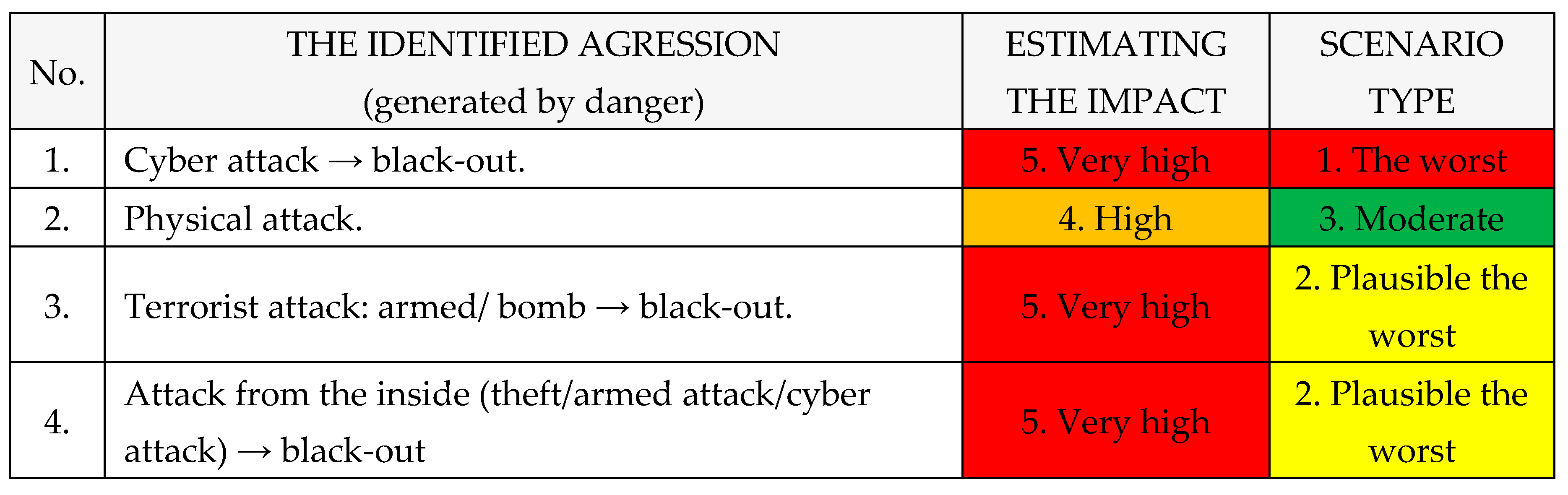
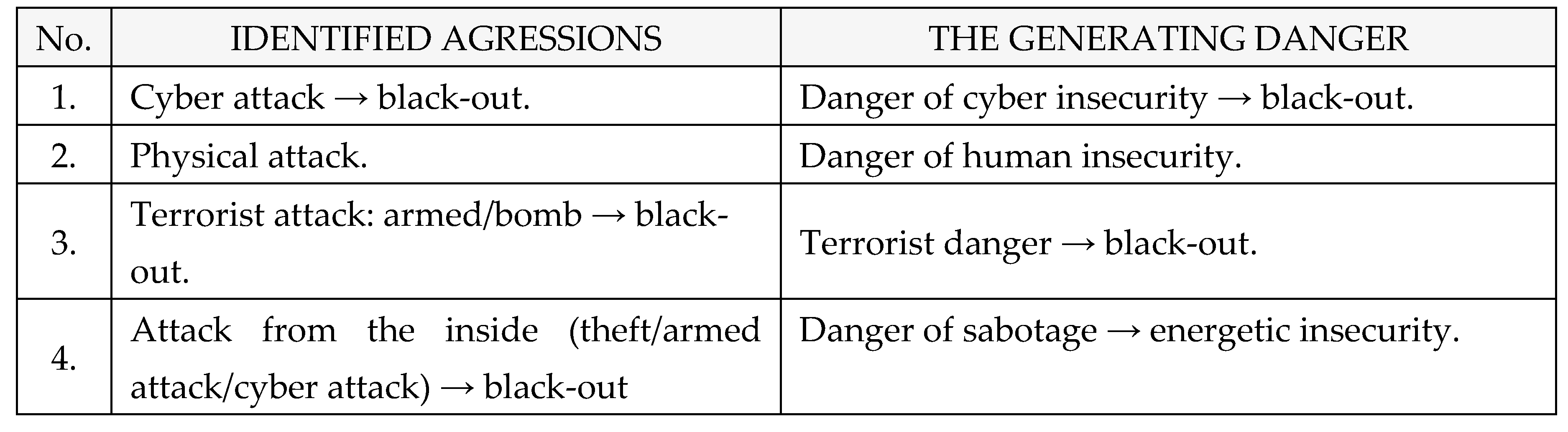
F. Types of agression
Identified aggression caused by dangers within The National Power System are the following, as shown in
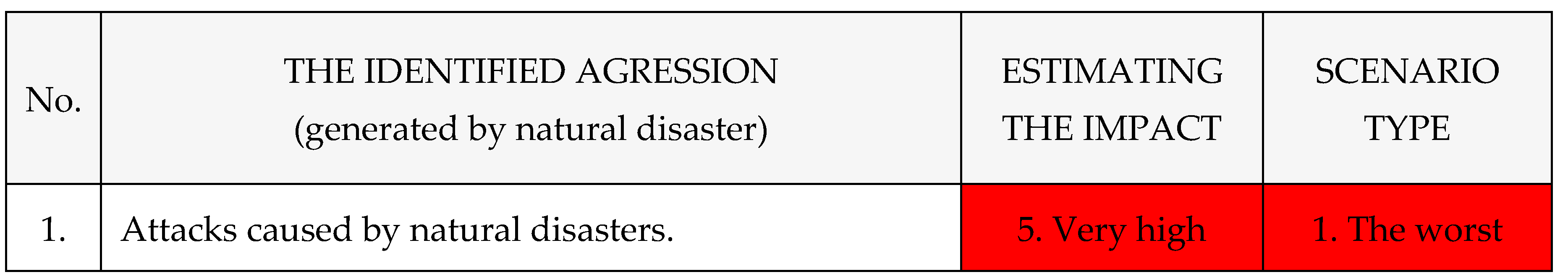
Table 10: [
1,
2,
3,
4].
Other identified aggressions naturally caused with a crisis or collapse effect on The National Power System, as shown in
Table 11: [
1,
2,
3,
4].
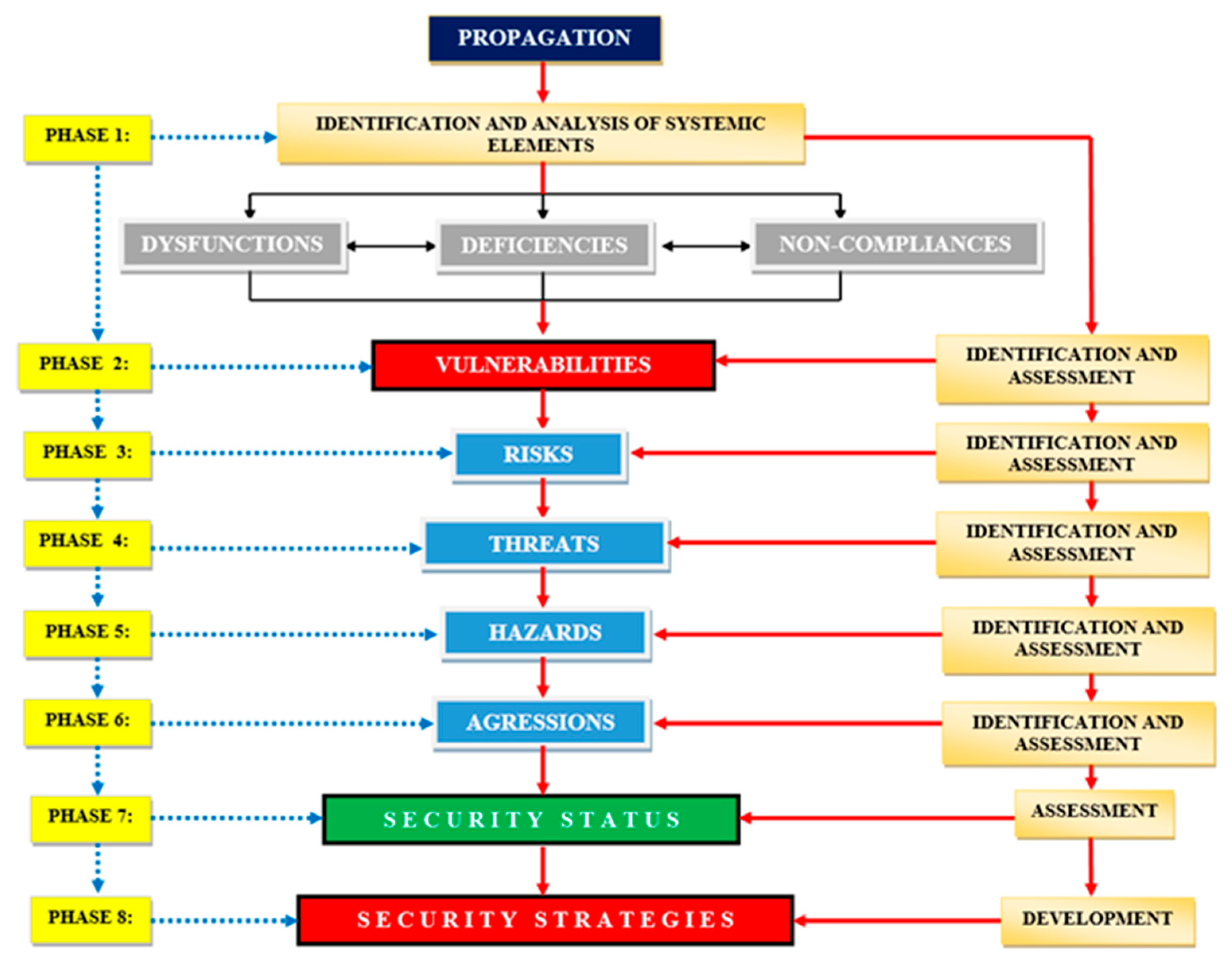
5. Propagation of the Instability and Insecurity Elements
Figure 4 shows the scheme of propagation of system, instability and insecurity elements, and figure 5 shows the sequence (phases) of propagation. [
1,
2,
3,
4].
Phase 1: The identification and analysis of the systemic elements:
dysfunctions;
deficiencies;
non-compliances;
Phase 2: The identification and assessment of vulnerabilities generated by systemic elements (dysfunctions, deficiencies and non-compliances);
Phase 3: The identification and assessment of risks generated by the identified vulnerabilities;
Phase 4: The dentification and assessment of threats generated by the identified risks;
Phase 5: The identification and assessment of hazards generated by the identified threats;
Phase 6: The identification and assessment of the aggressions generated by the identified dangers;
Phase 7: The assessment of the security state of The National Power System;
Phase 8: The development of The National Power System security strategies.
6. Prioritizing of the Instability and Insecurity Elements from Romanian Power System
6.1. Vulnerabilities
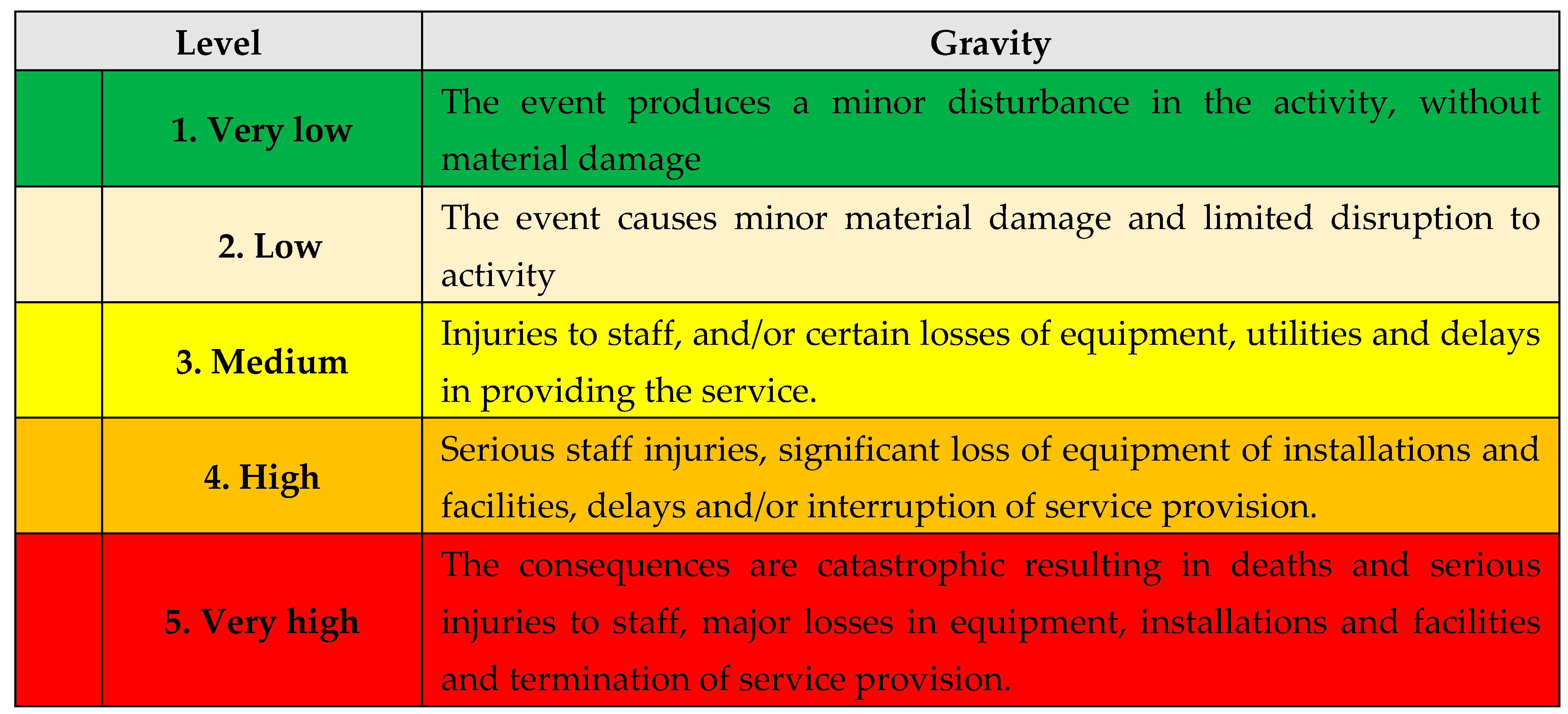
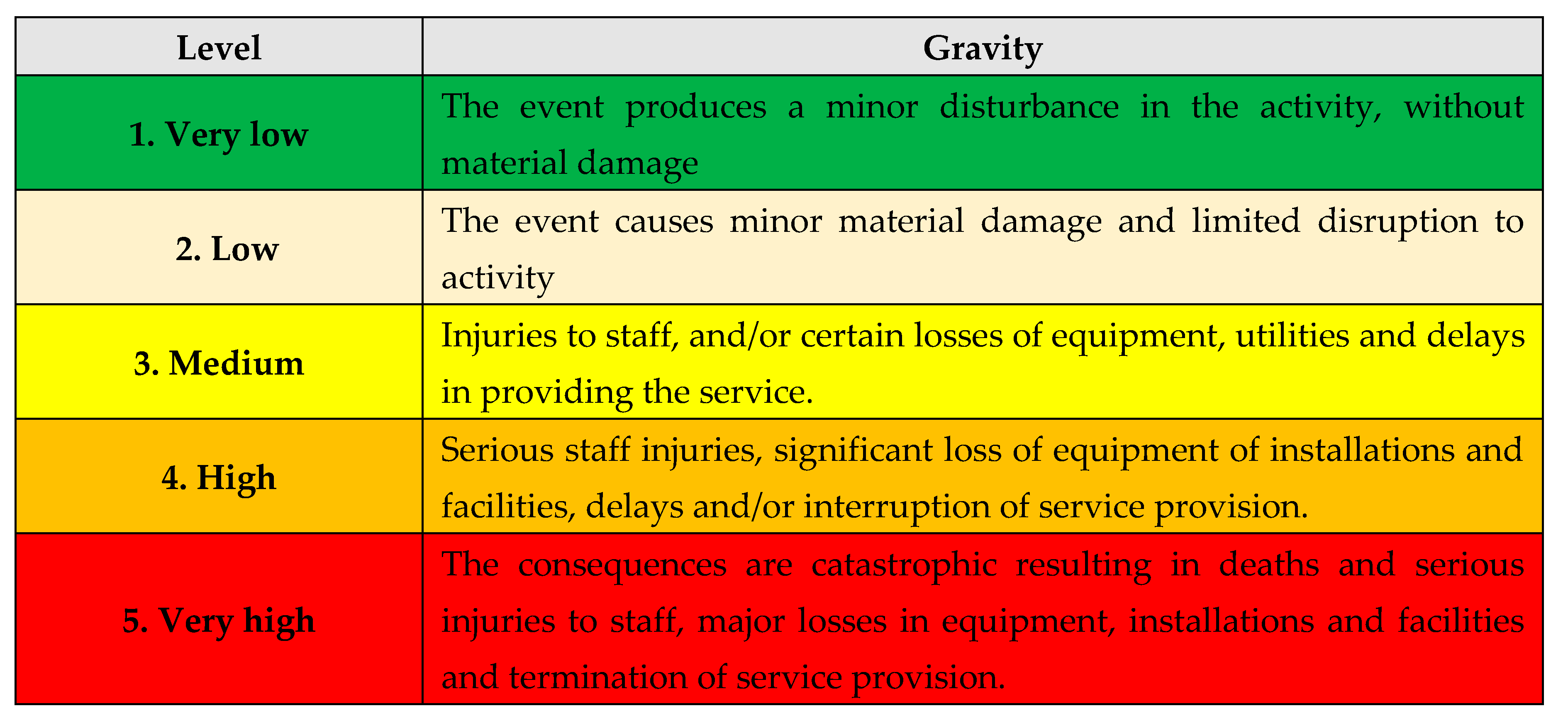
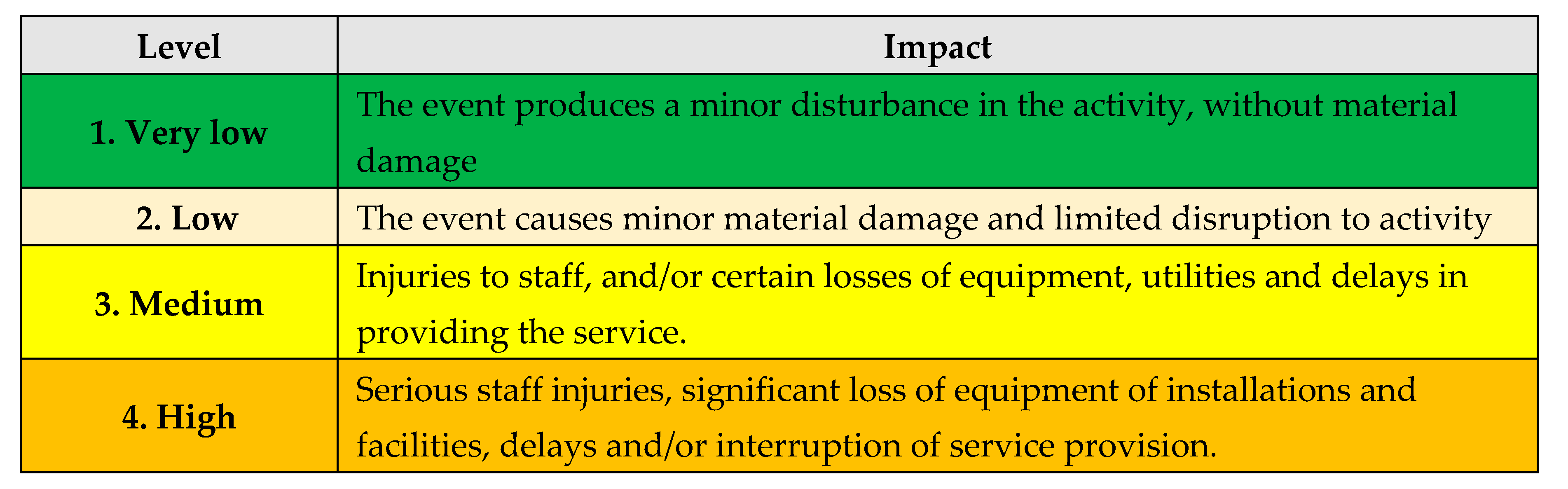
A. Estimating the Gravity: in this stage, the vulnerability gravity will be estimated:
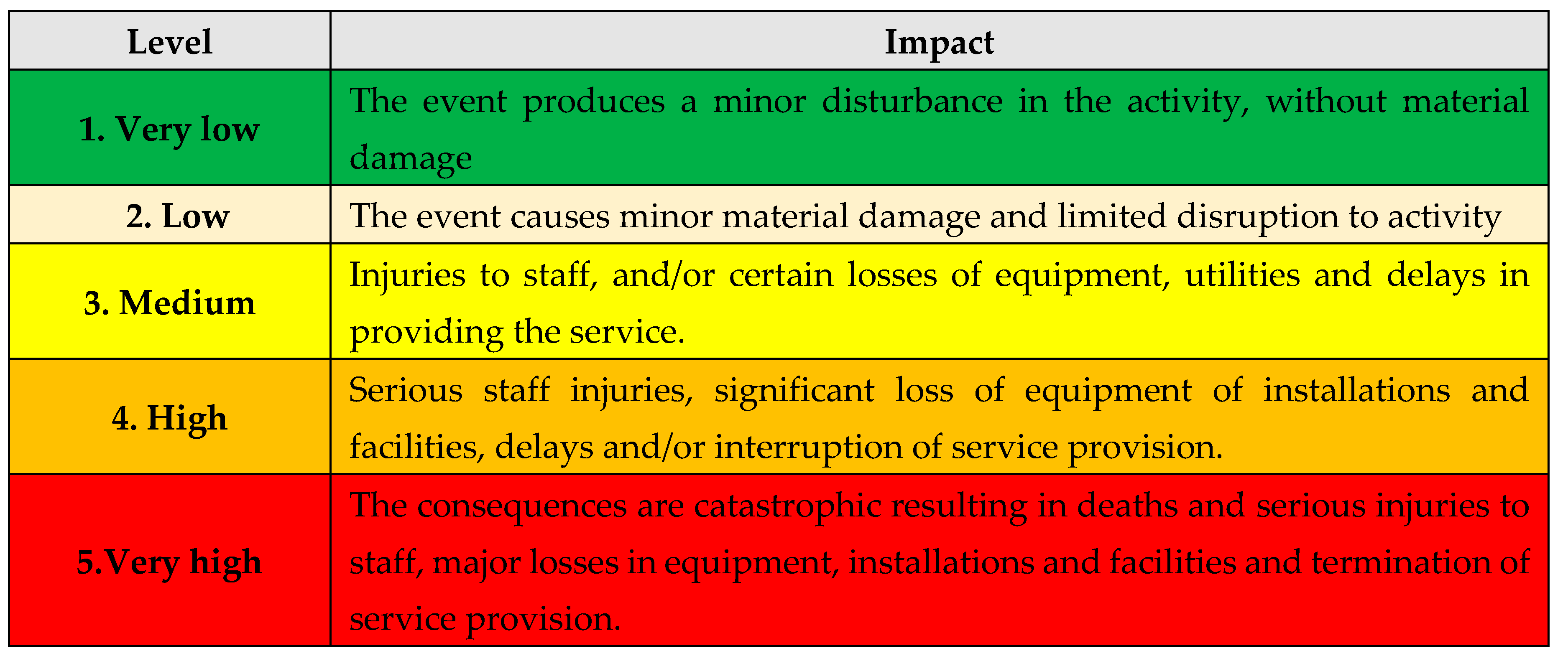
B. Estimating the Impact: in this stage, the vulnerability impact will be estimated:
C.
Scenario type: after estimating the vulnerability gravity and impact, the type of scenario will be decided, according with
Table 12:
1. The worst;
2. Plausible the worst;
3. Moderate.
6.2. Risks
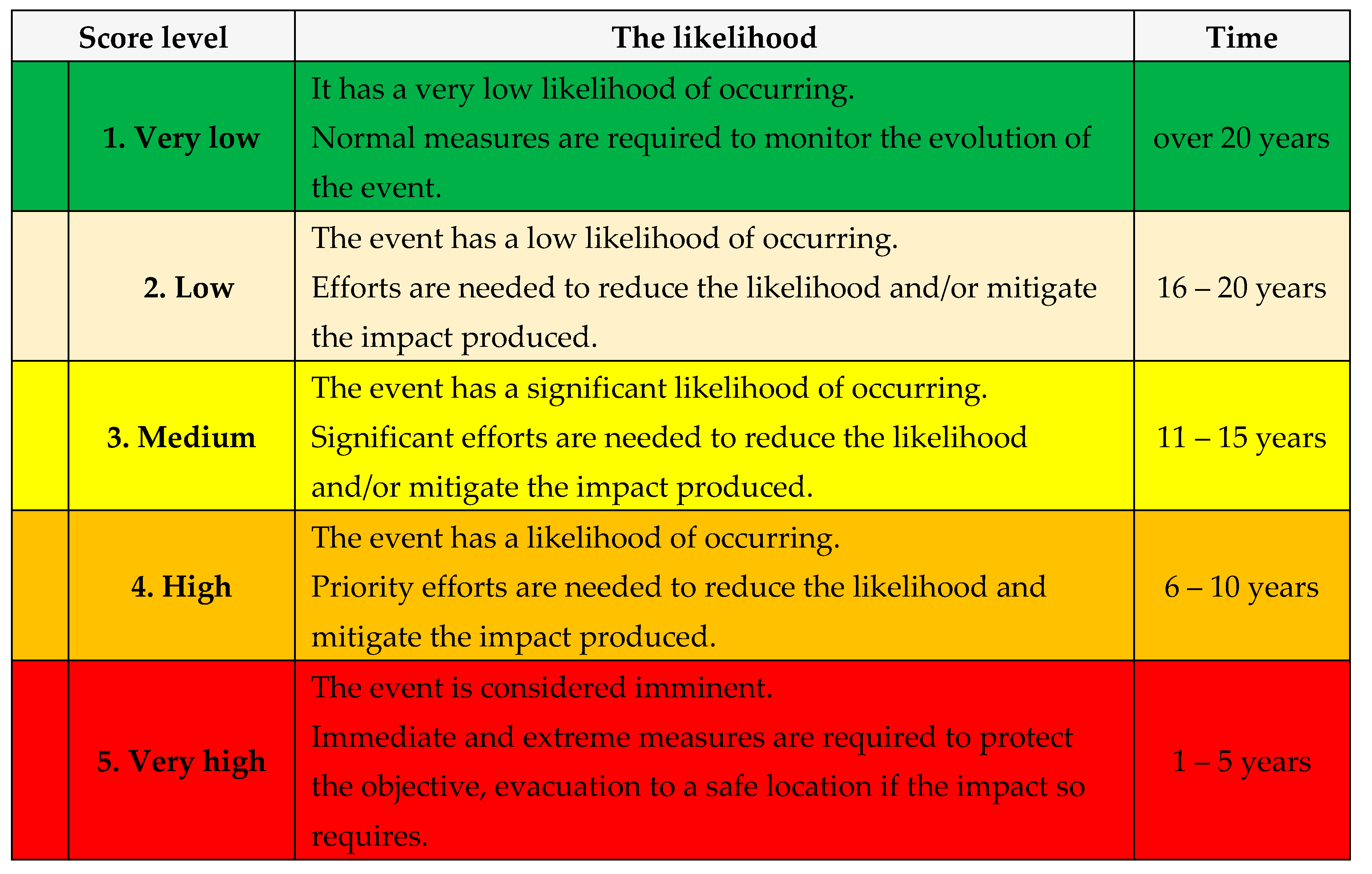
A. Estimating the Likelihood: in this stage, the risk likelihood will be estimated:
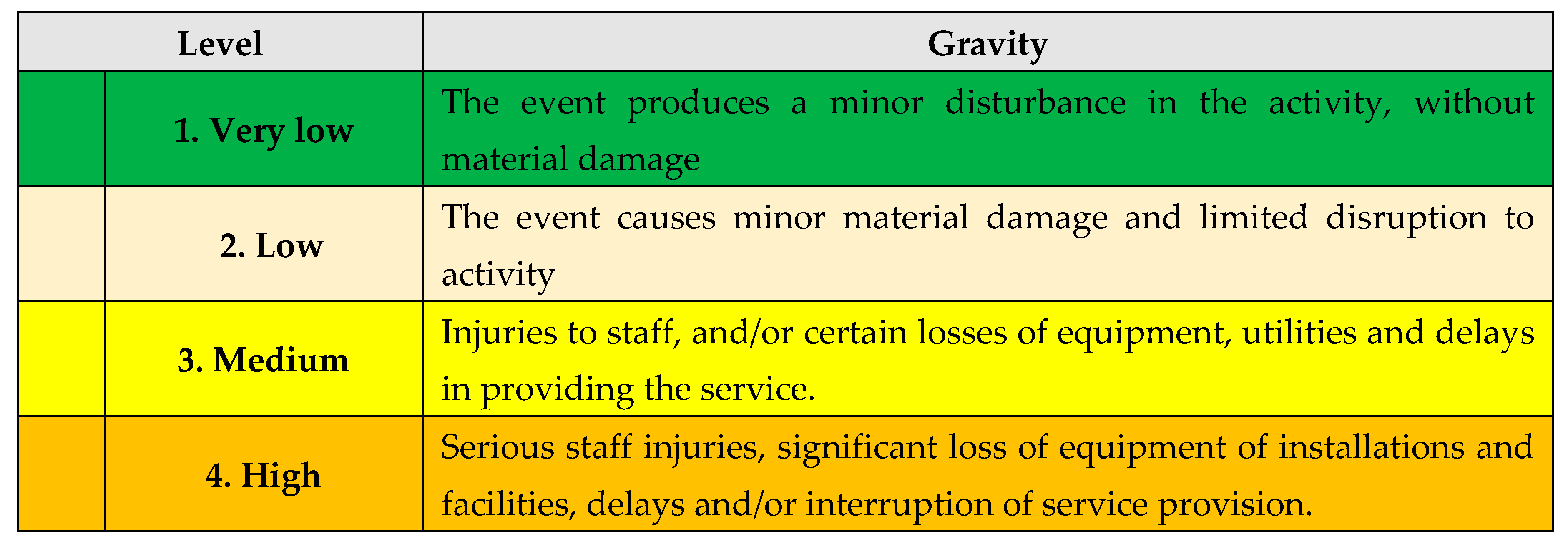
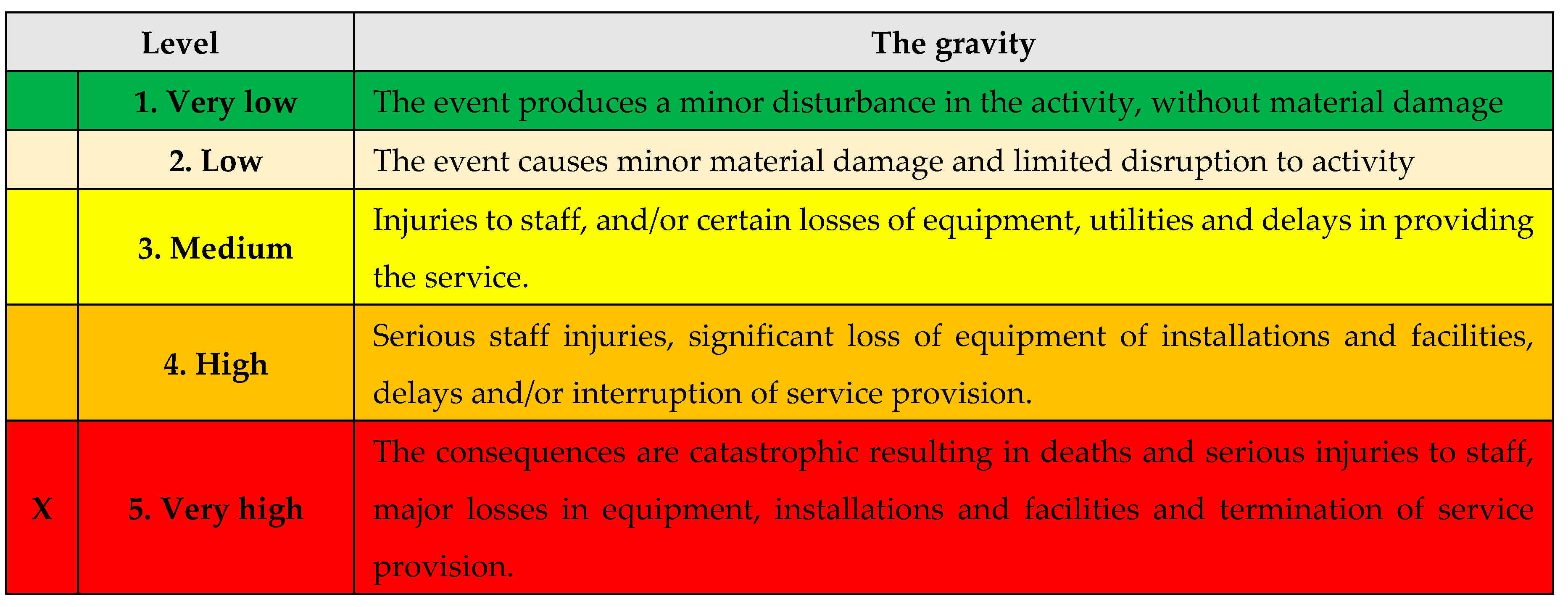
B. Estimating the Gravity: in this stage, the risk gravity will be estimated:
C.
Scenario type: after estimating the likelihood and gravity, the type of scenario will be decided, according with
Table 13:
1. The worst;
2. Plausible the worst;
3. Moderate.
6.3. Threats
A. Estimating the Intention: in this stage, the threats intention will be estimated:
B. Estimating the Capability: in this stage, the threats capability will be estimated:
C.
Scenario type: after estimating the intention and capability, the type of scenario will be decided, according with
Table 15 and
Table 16:
1. The worst;
2. Plausible the worst;
3. Moderate.
6.4. Hazards
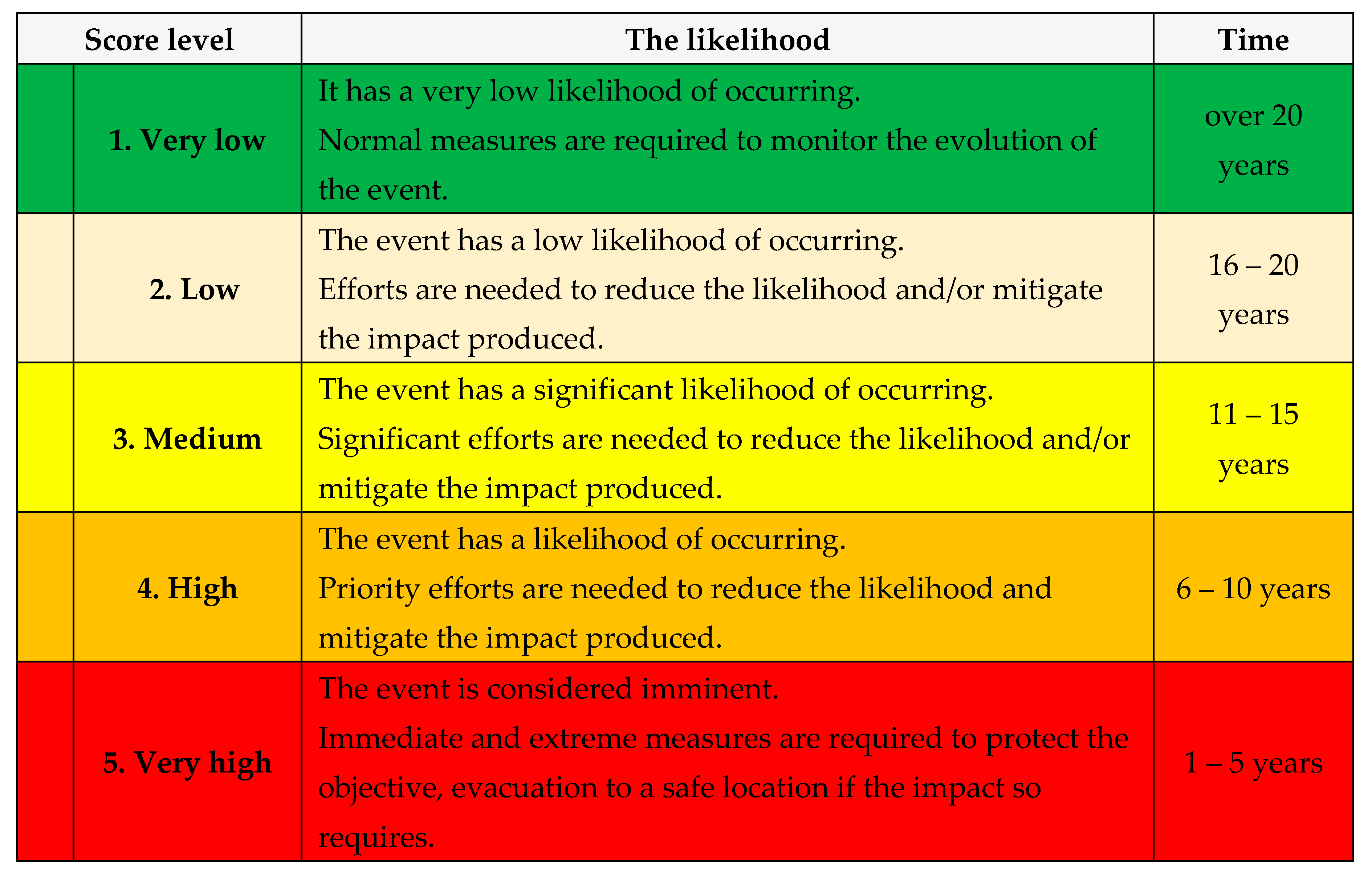
A. Estimating the Likelihood: in this stage, the danger likelihood will be estimated:
B. Estimating the Gravity: in this stage, the danger gravity will be estimated:
C.
Scenario type: after estimating the likelihood and gravity, the type of scenario will be decided, according with
Table 17 and
Table 18:
1. The worst;
2. Plausible the worst;
3. Moderate.
6.5. Agression
A. Estimating the Impact: in this stage, the agression impact will be estimated:
B.
Scenario type: after estimating the agression impact, the type of scenario will be decided, according with
Table 19 and
20:
1. The worst;
2. Plausible the worst;
3. Moderate.
6.6. Prioritizing Scenarios
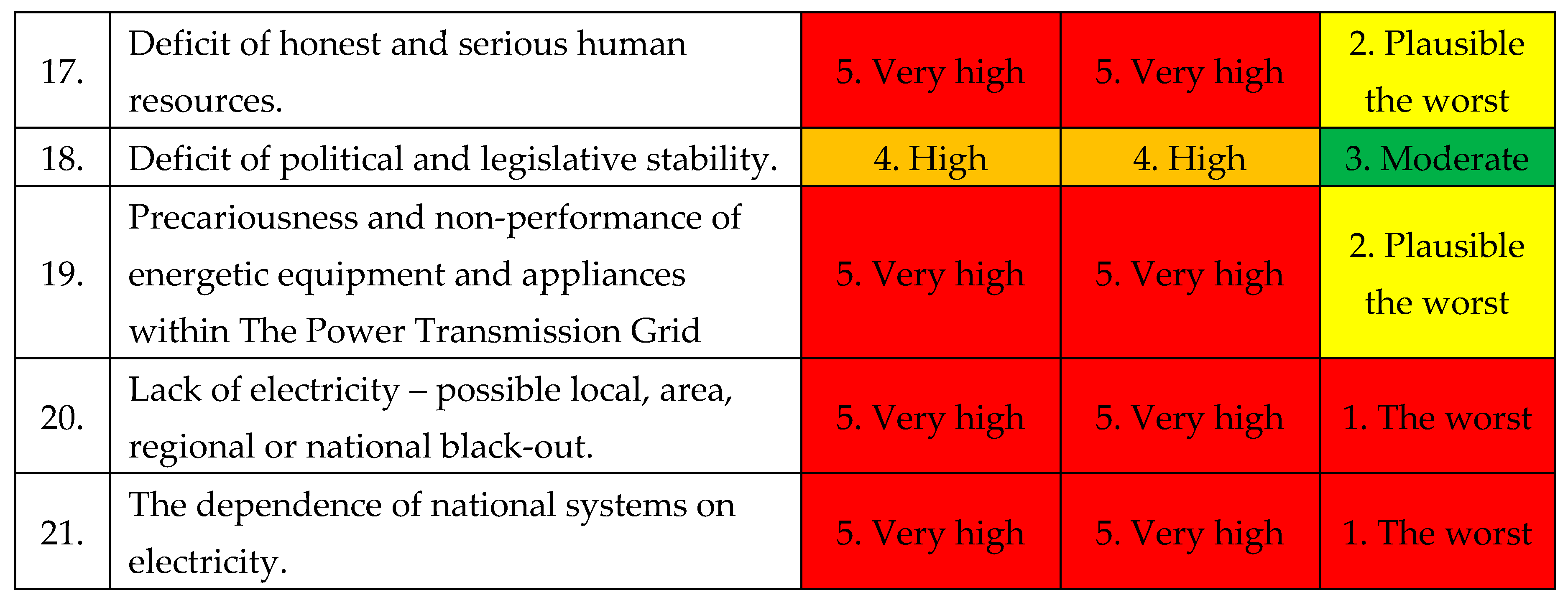
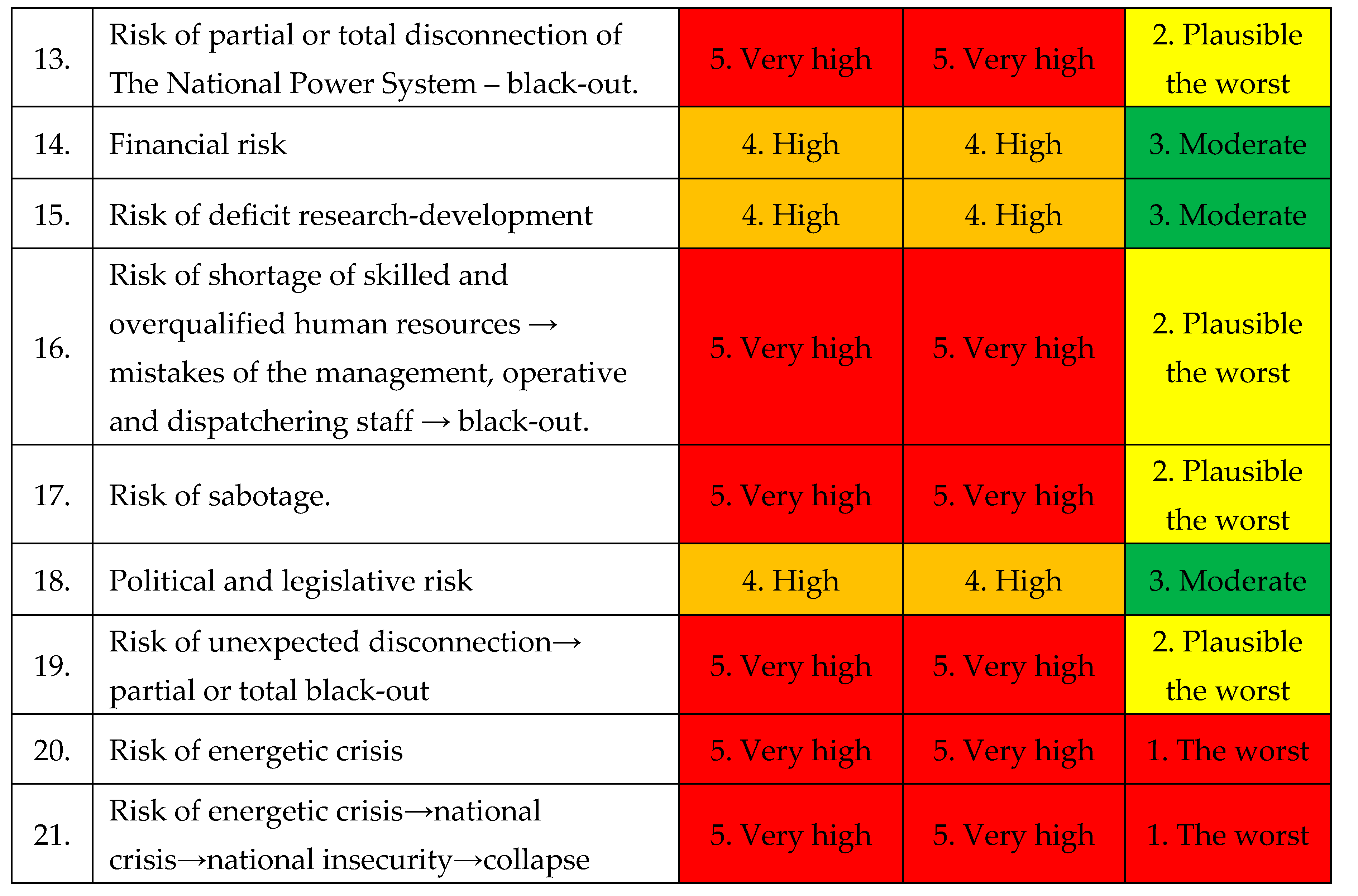
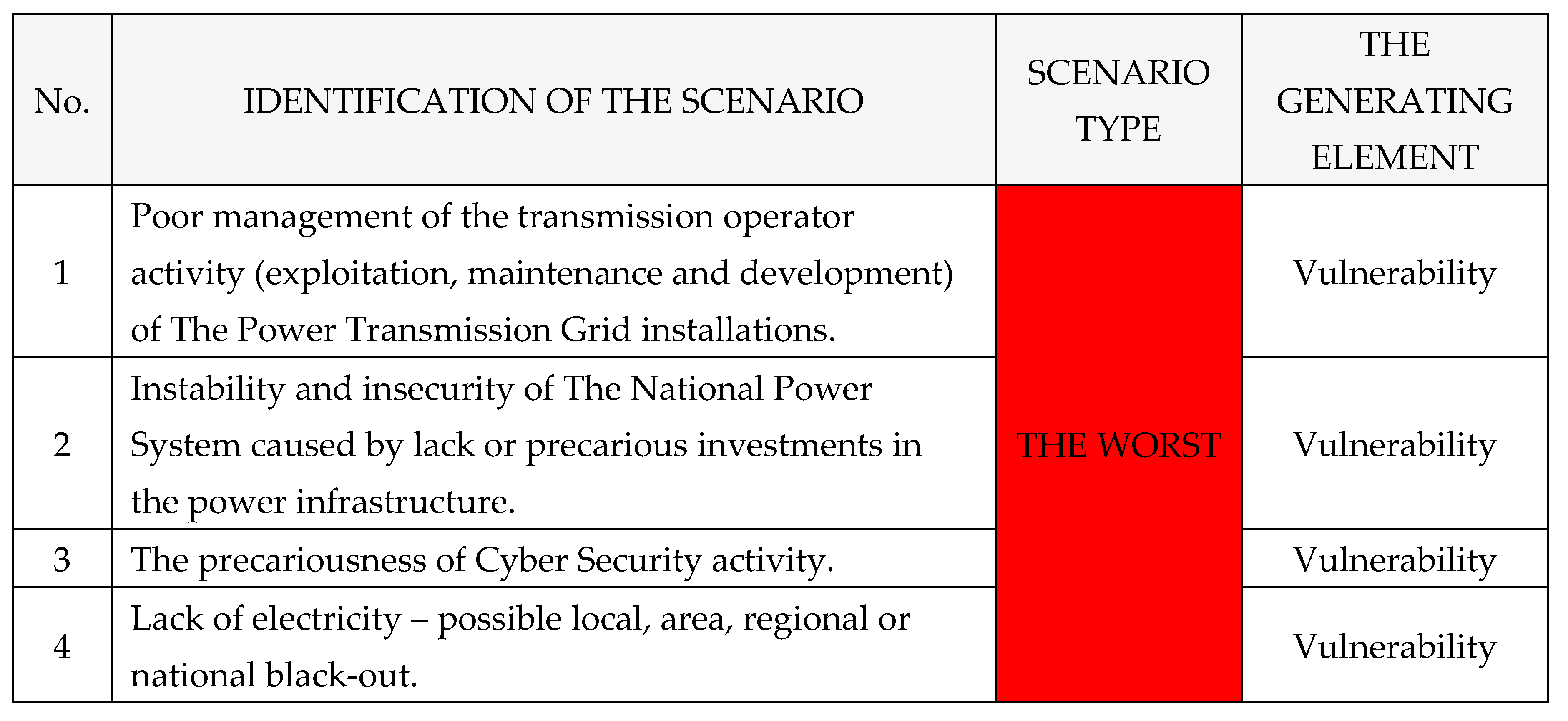
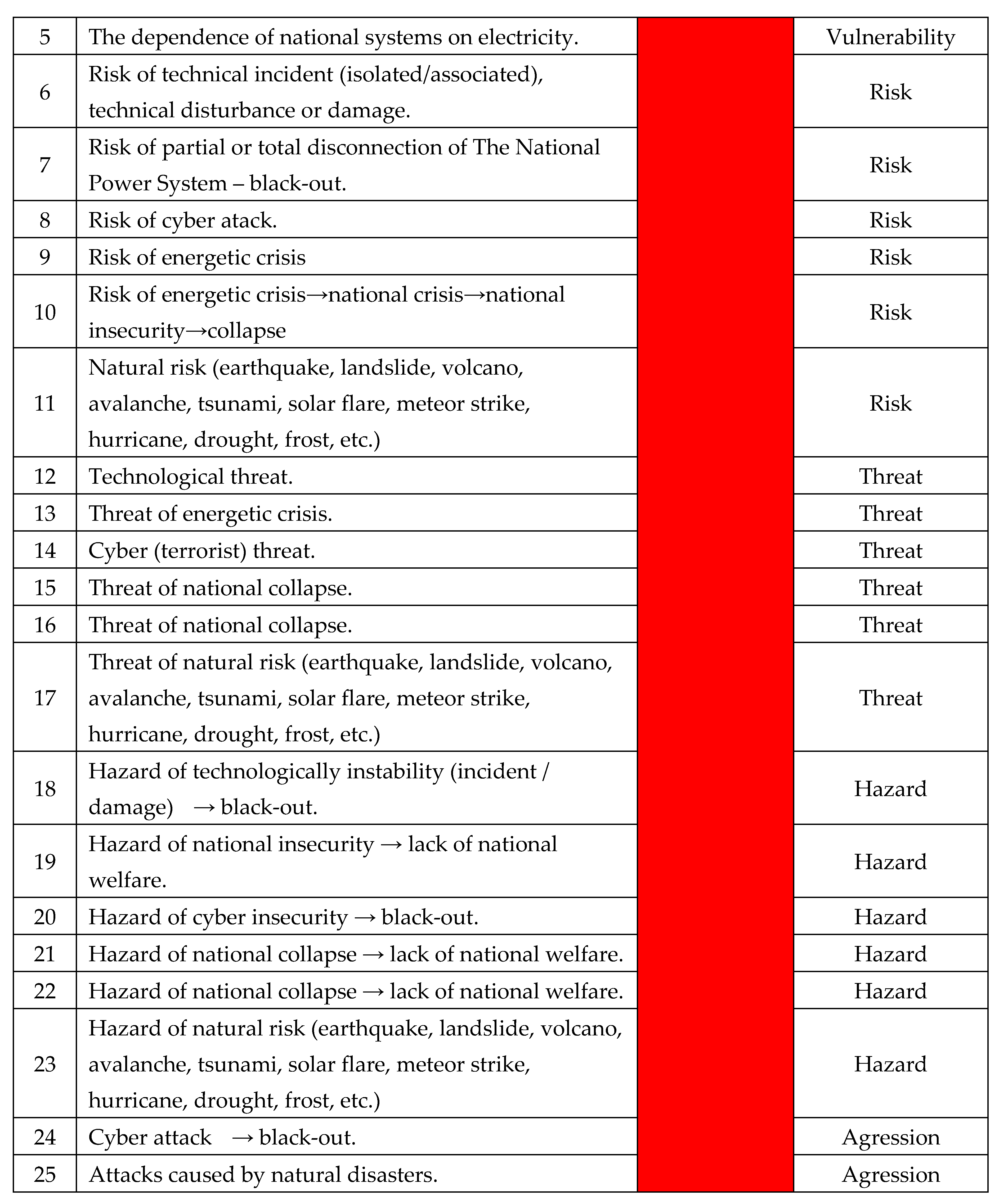
A.
The identification of the worst scenarios: according with
Table 21. [
1,
2,
3,
4]
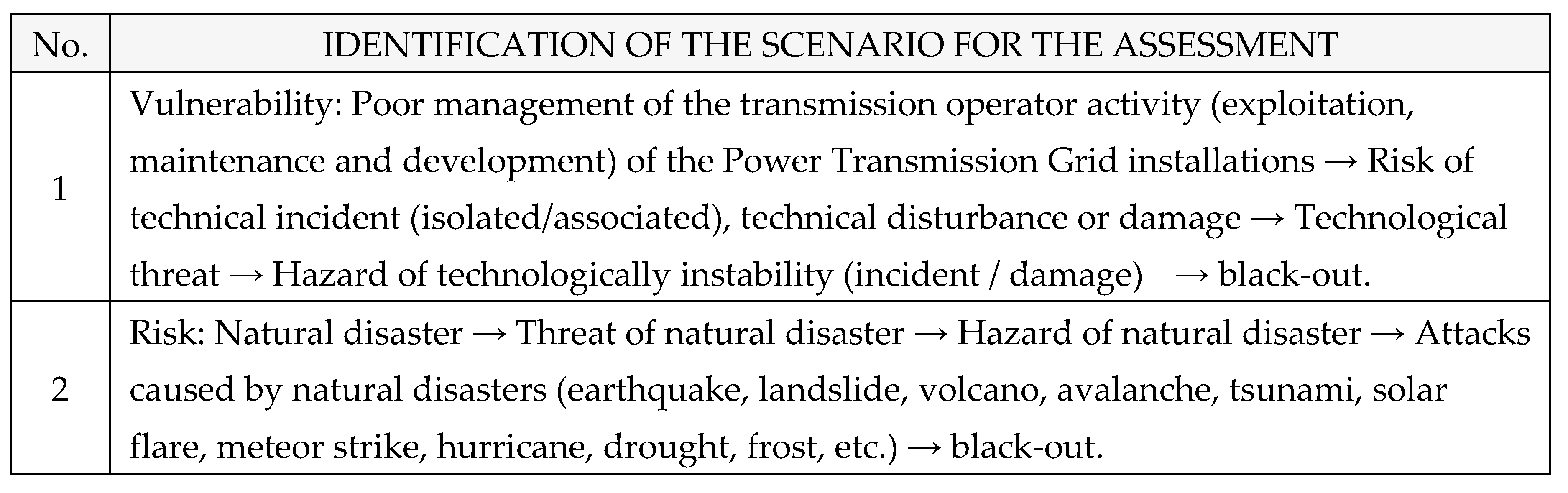
B.
Choosing the worst scenarios for the assessment: according with
Table 22. [
1,
2,
3,
4]
7. Assessment of Vulnerability and Risk Identifies from National Power System
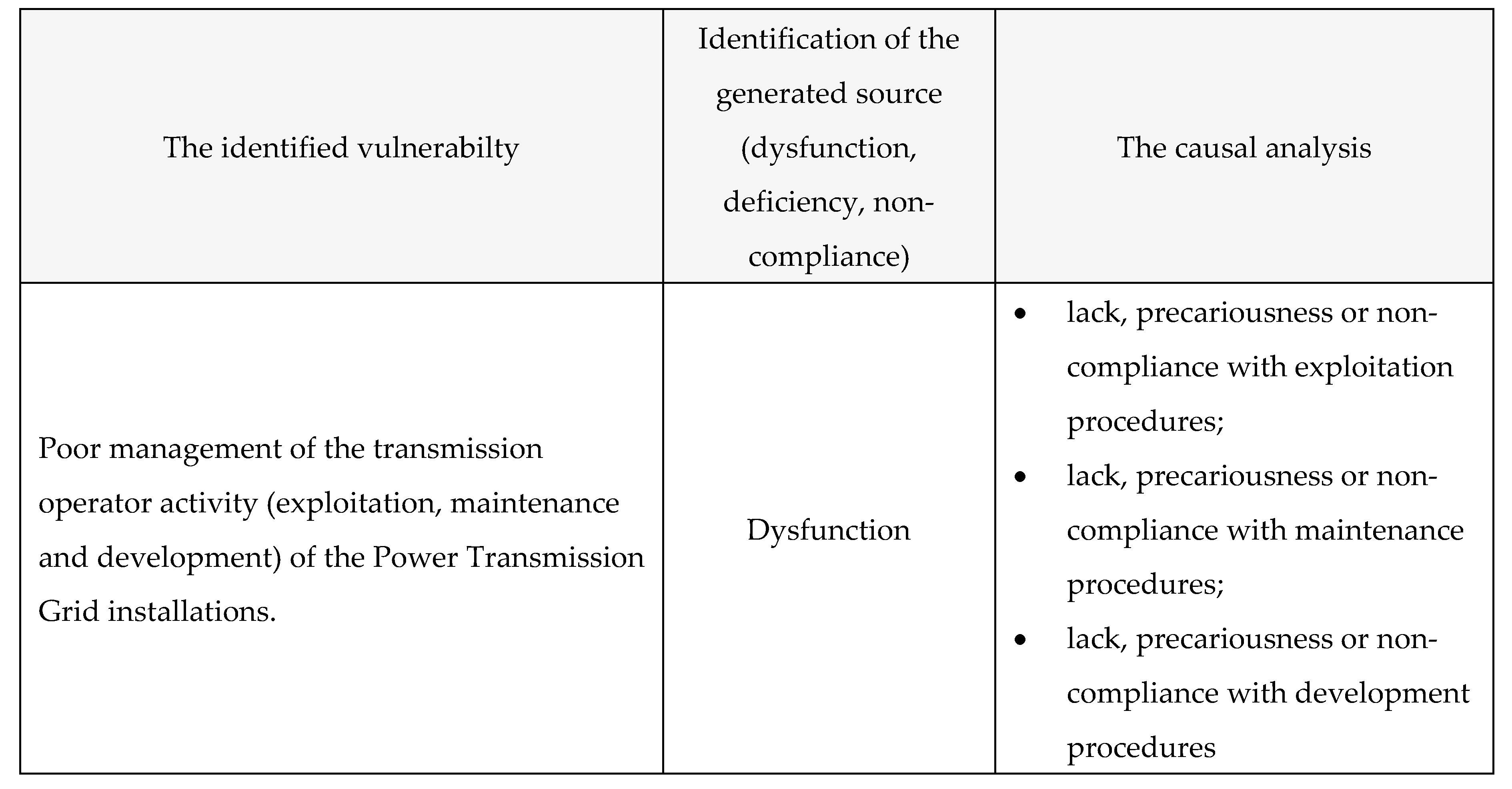
7.1. Vulnerability: Poor Management of the Transmission Operator Activity (Exploitation, Maintenance and Development) of the Power Transmission Grid Installations → Risk of Technical Incident (Isolated/Associated), Technical Disturbance or Damage → Technological Threat → Hazard of Technologically Instability (Incident / Damage) → Black-Out
Table 23.
The causal analysis.
Table 23.
The causal analysis.
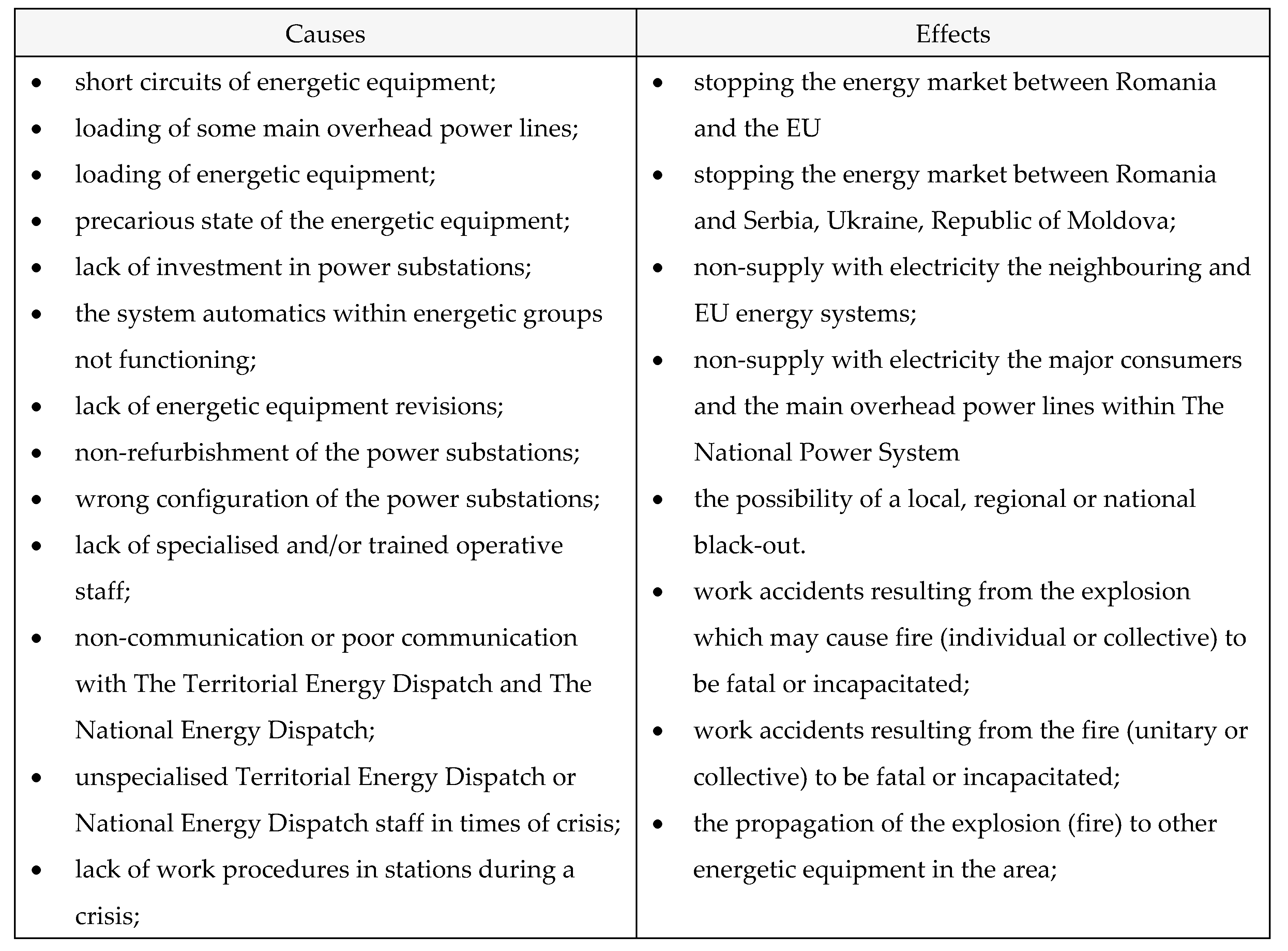
Table 24.
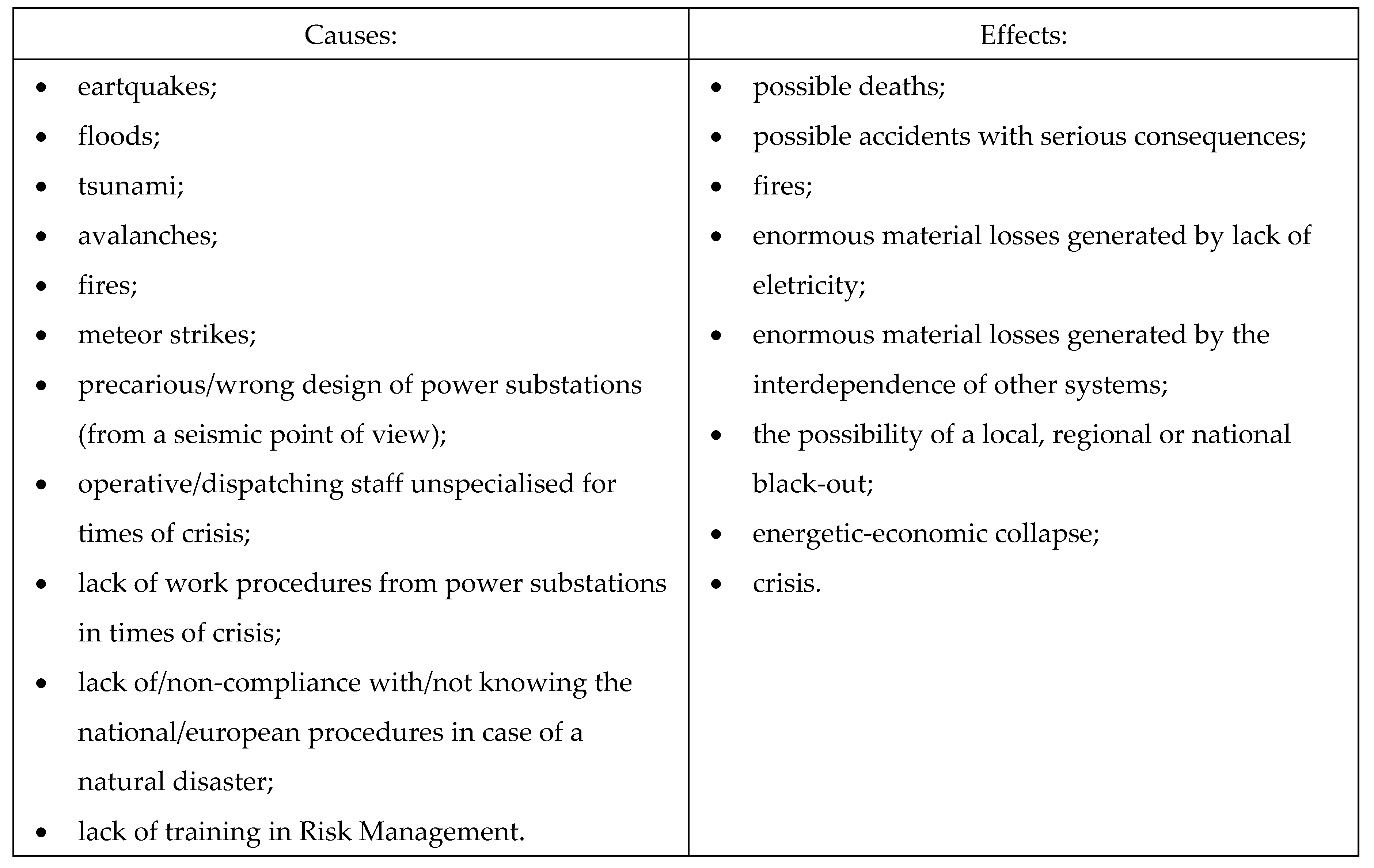
Causes and effects.
Table 24.
Causes and effects.
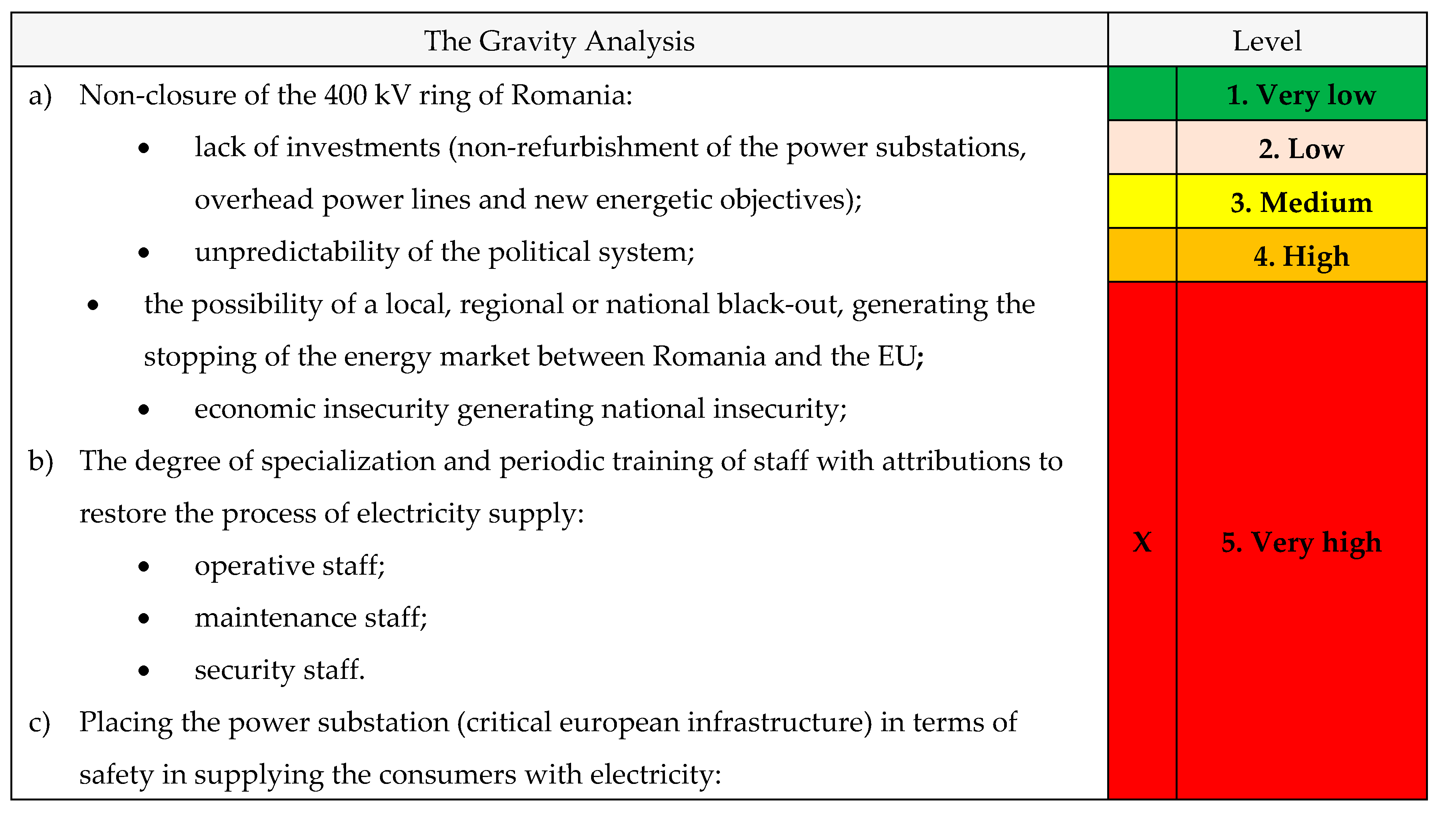
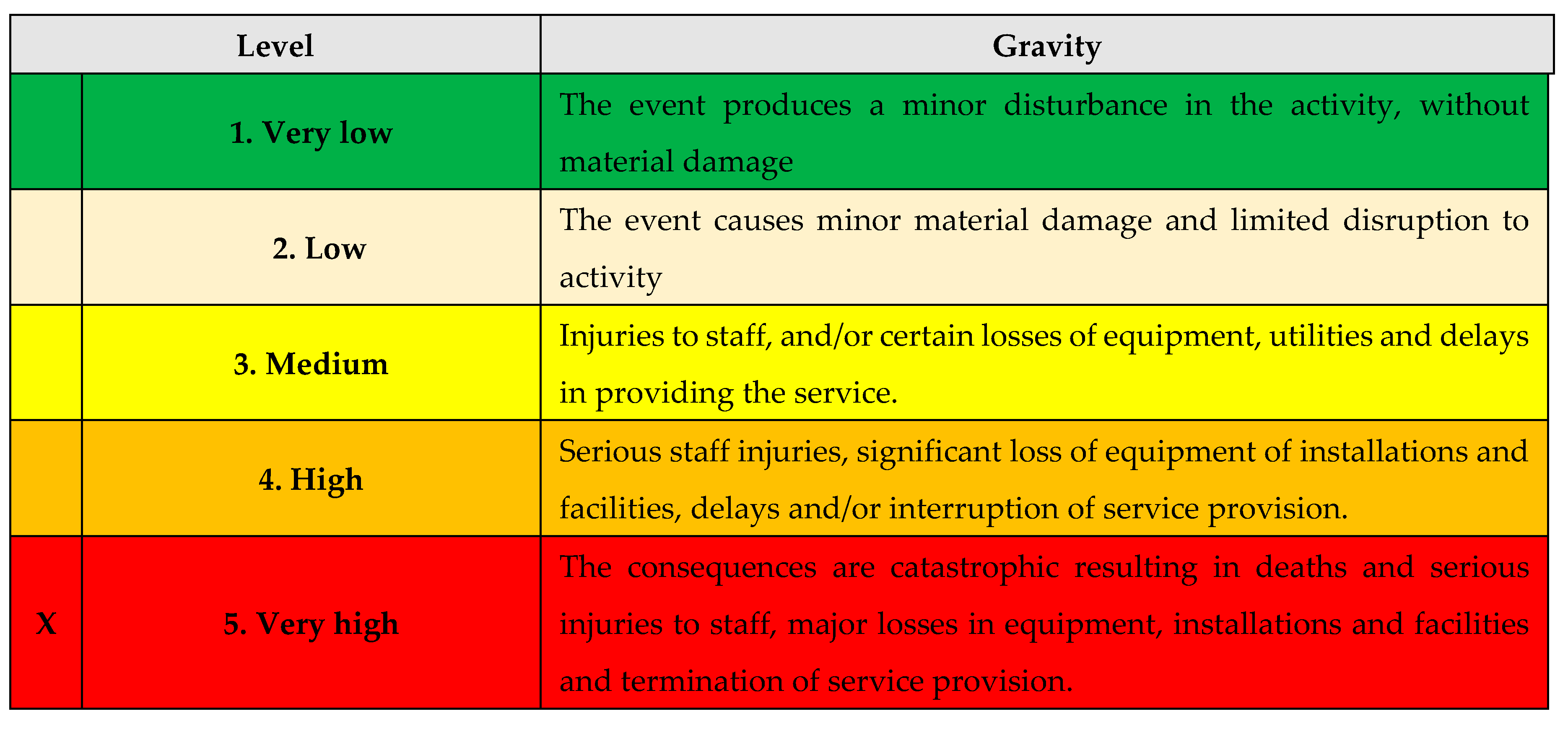
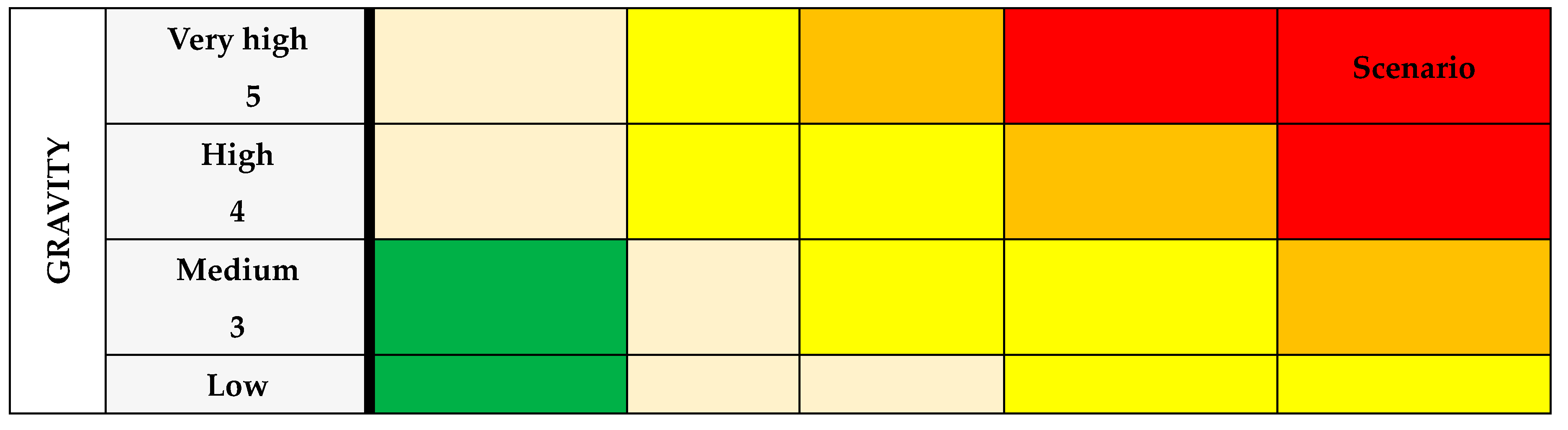
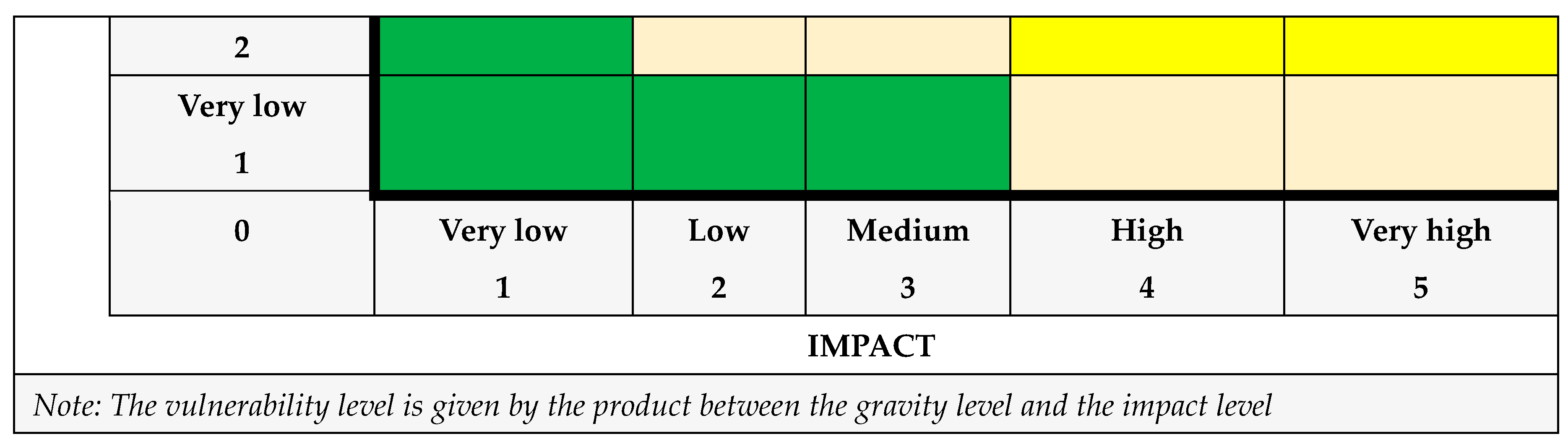
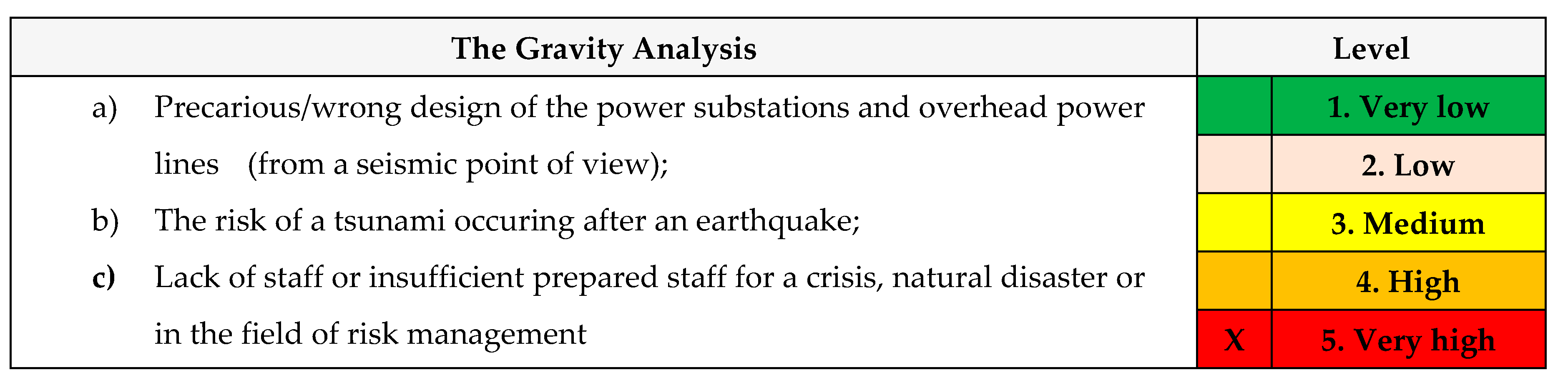
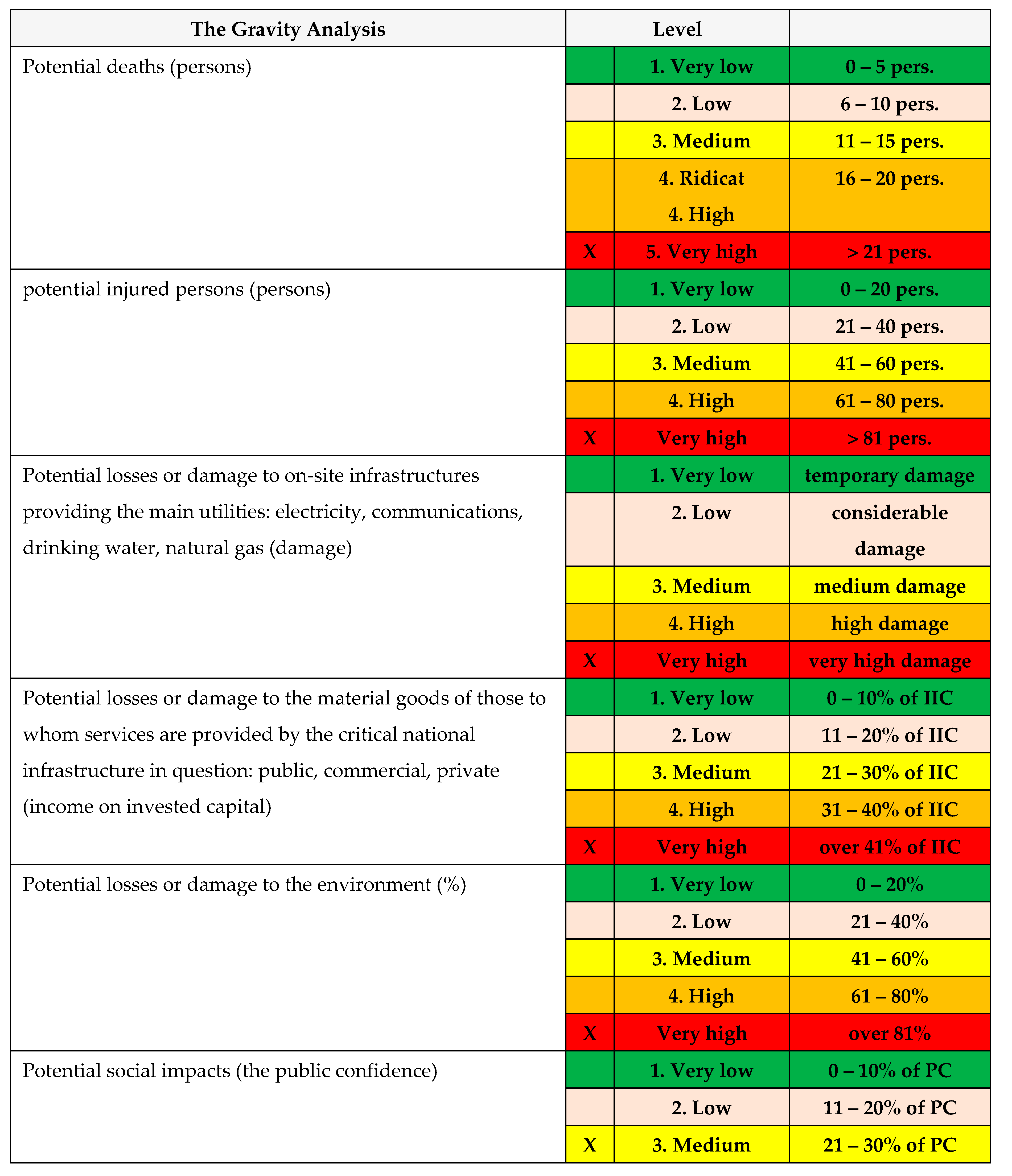
A. The gravity analysis
Table 25.
The gravitiy analysis.
Table 25.
The gravitiy analysis.
B. The gravity level
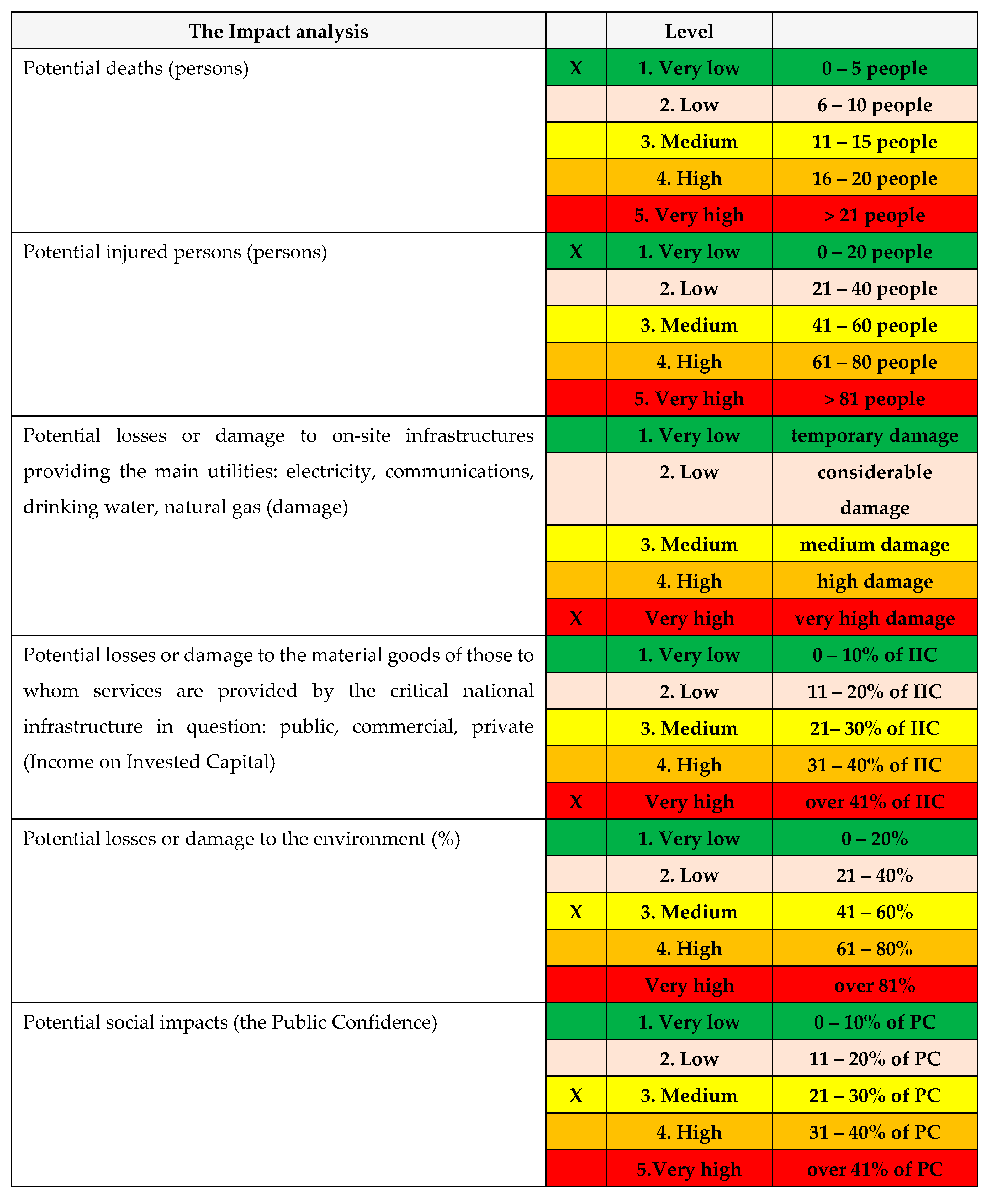
C. The impact analysis
Table 26.
The impact analysis.
Table 26.
The impact analysis.
D. The impact level
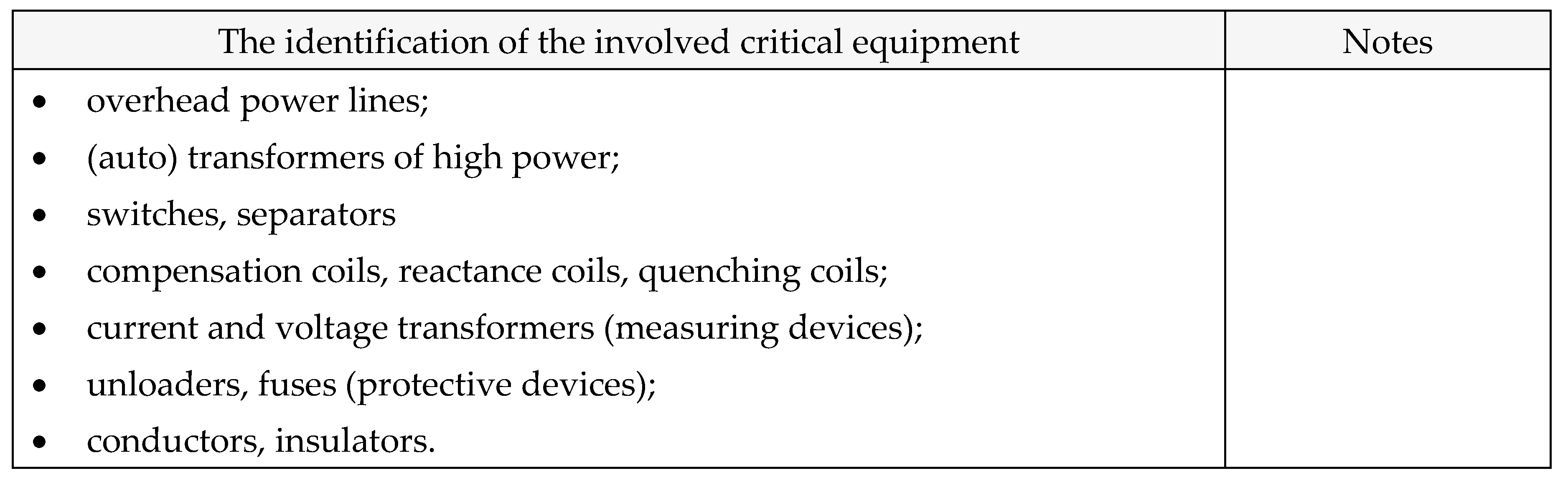
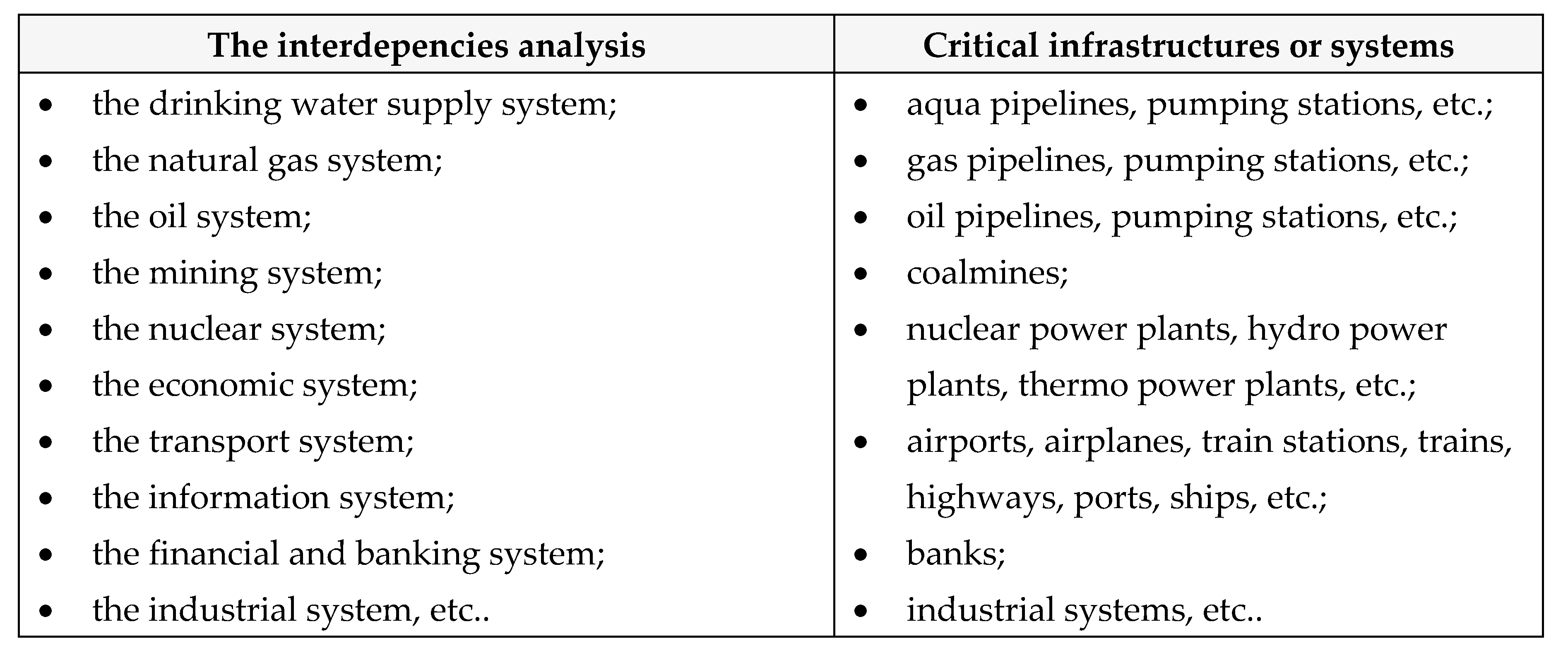
E. The identification of the involved infrastructures
Table 27.
Involved critical equipments.
Table 27.
Involved critical equipments.
F. The interdepepencies analysis
Table 28.
Interdepencies analysis / Critical infrastructures or system.
Table 28.
Interdepencies analysis / Critical infrastructures or system.
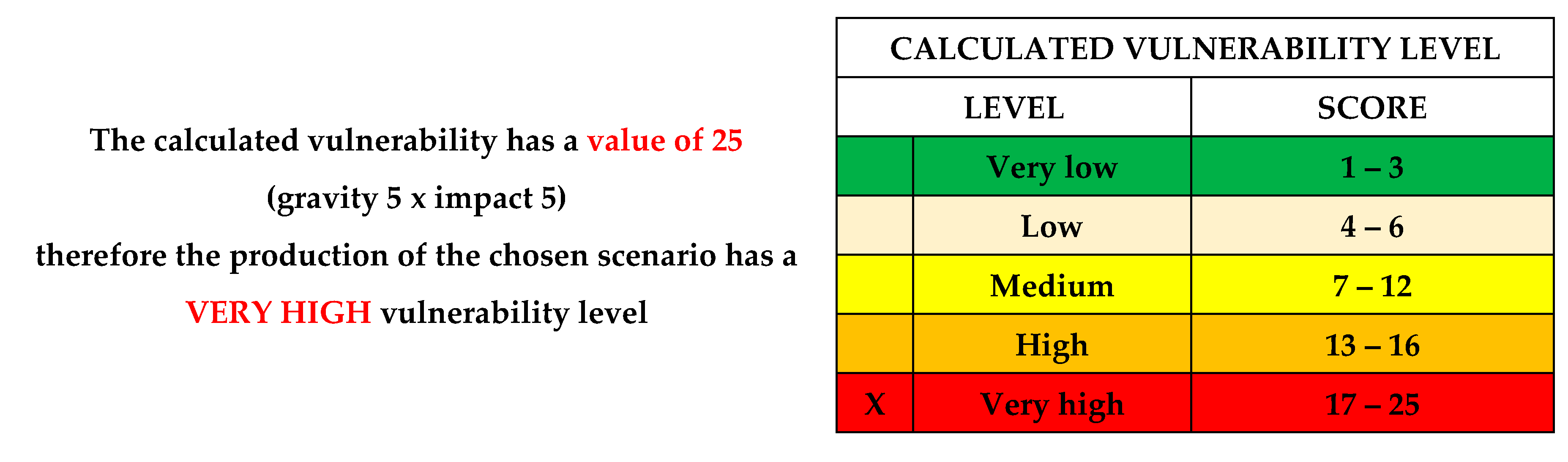
G. The calculation of the vulnerability level
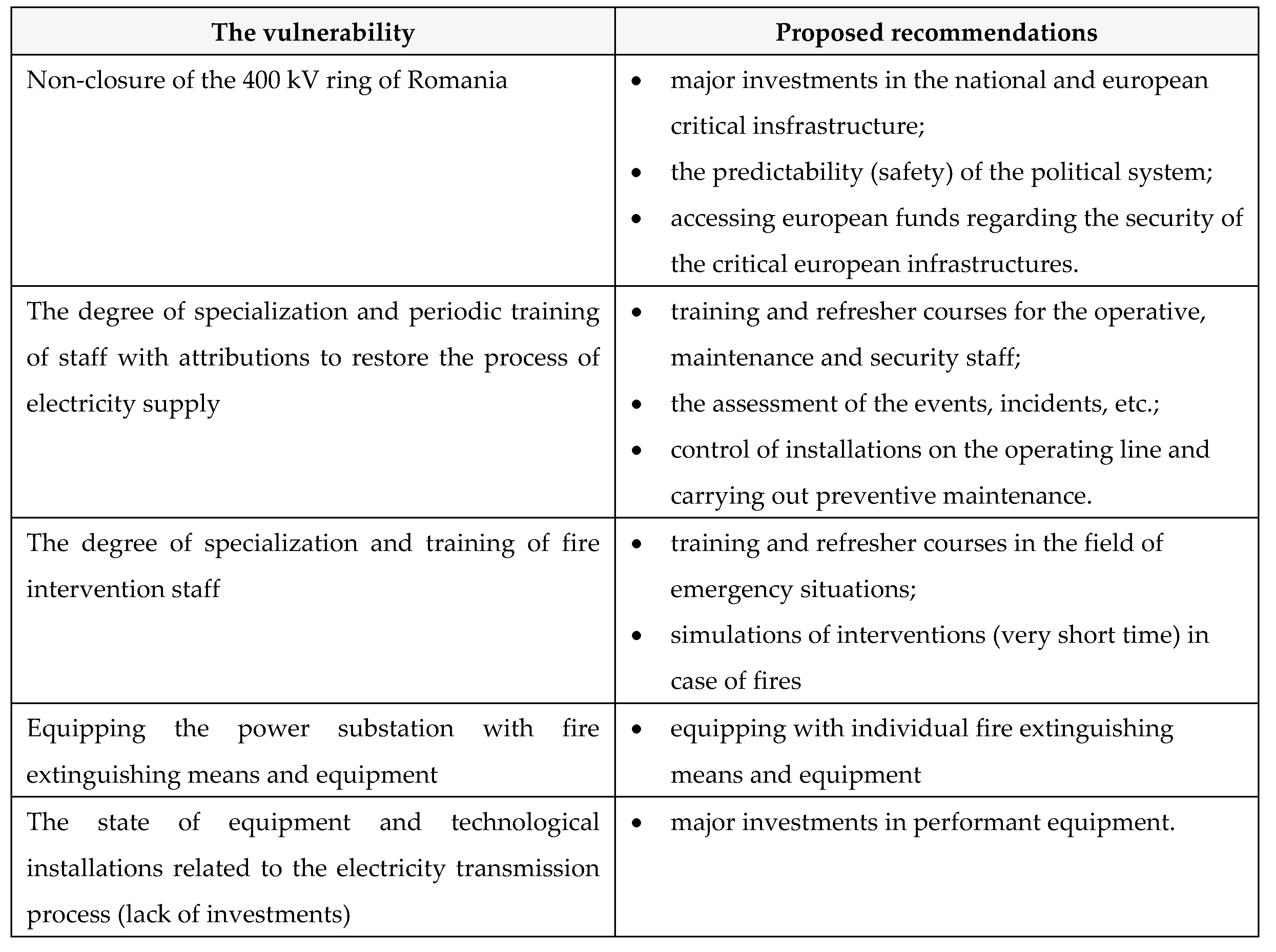
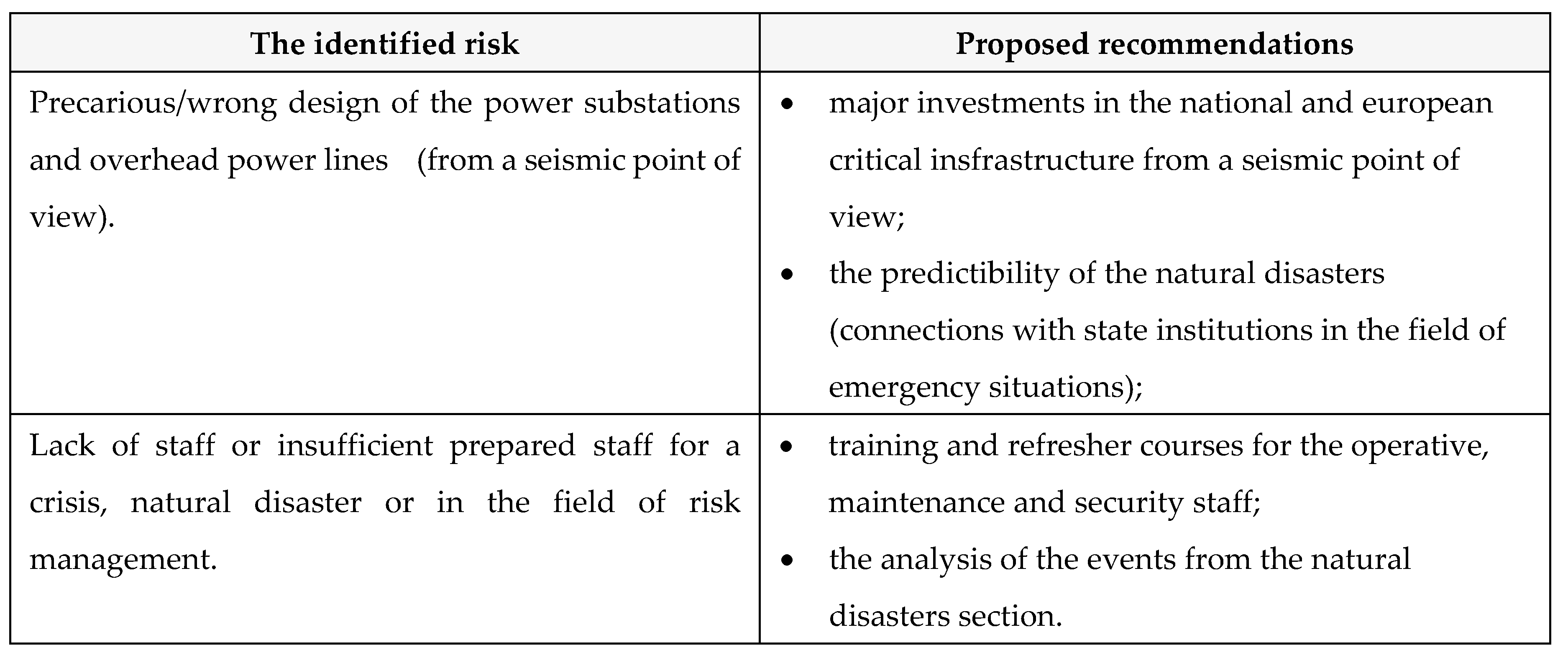
H. Proposed recommendations
Table 29.
Proposed recommedations.
Table 29.
Proposed recommedations.
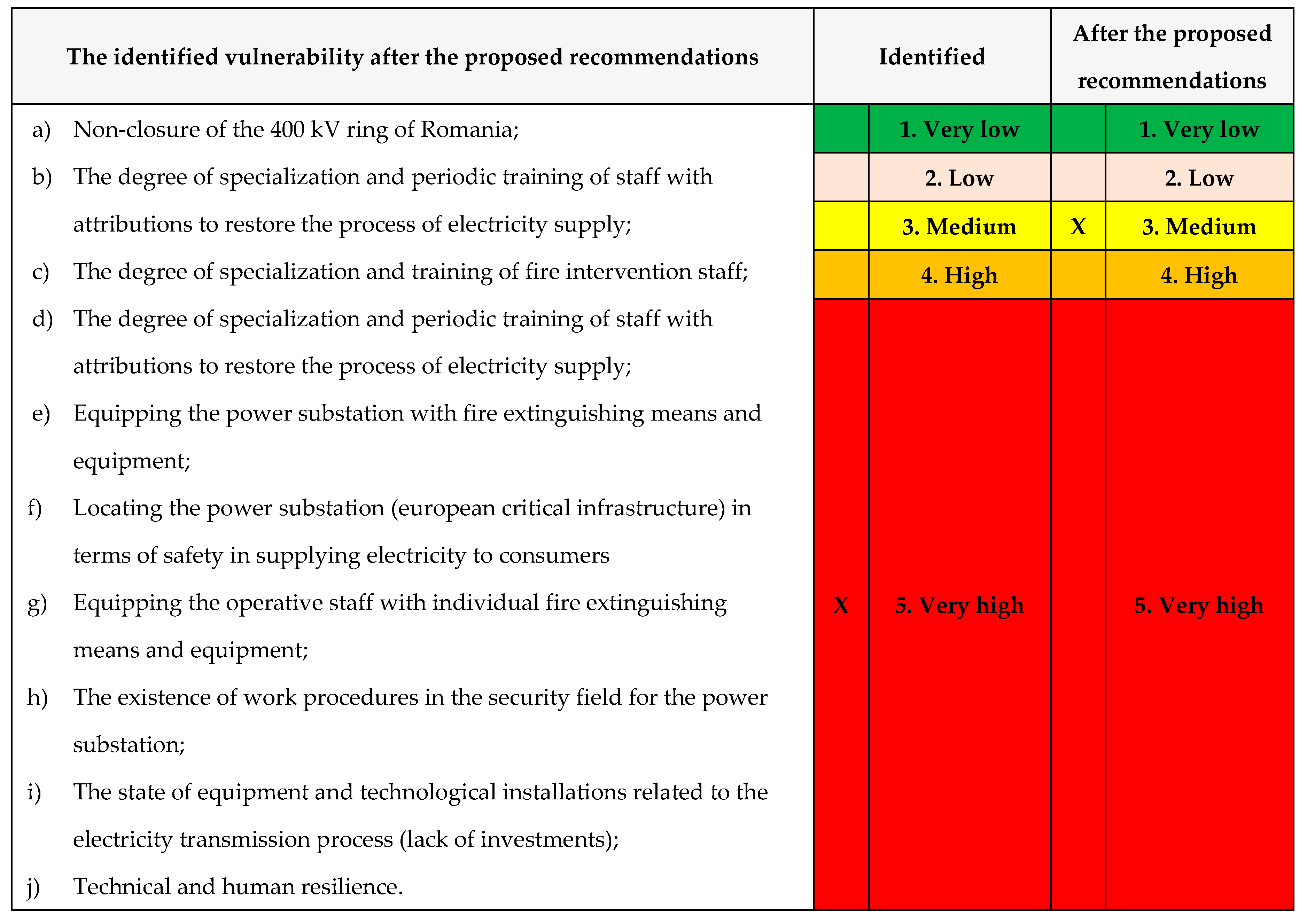
Table 29.
The identified vulnerability after the proposed recommendations.
Table 29.
The identified vulnerability after the proposed recommendations.
I. The recalculation of the vulnerability level
A. The causal analysis
Table 30.
The causal analysis.
Table 30.
The causal analysis.
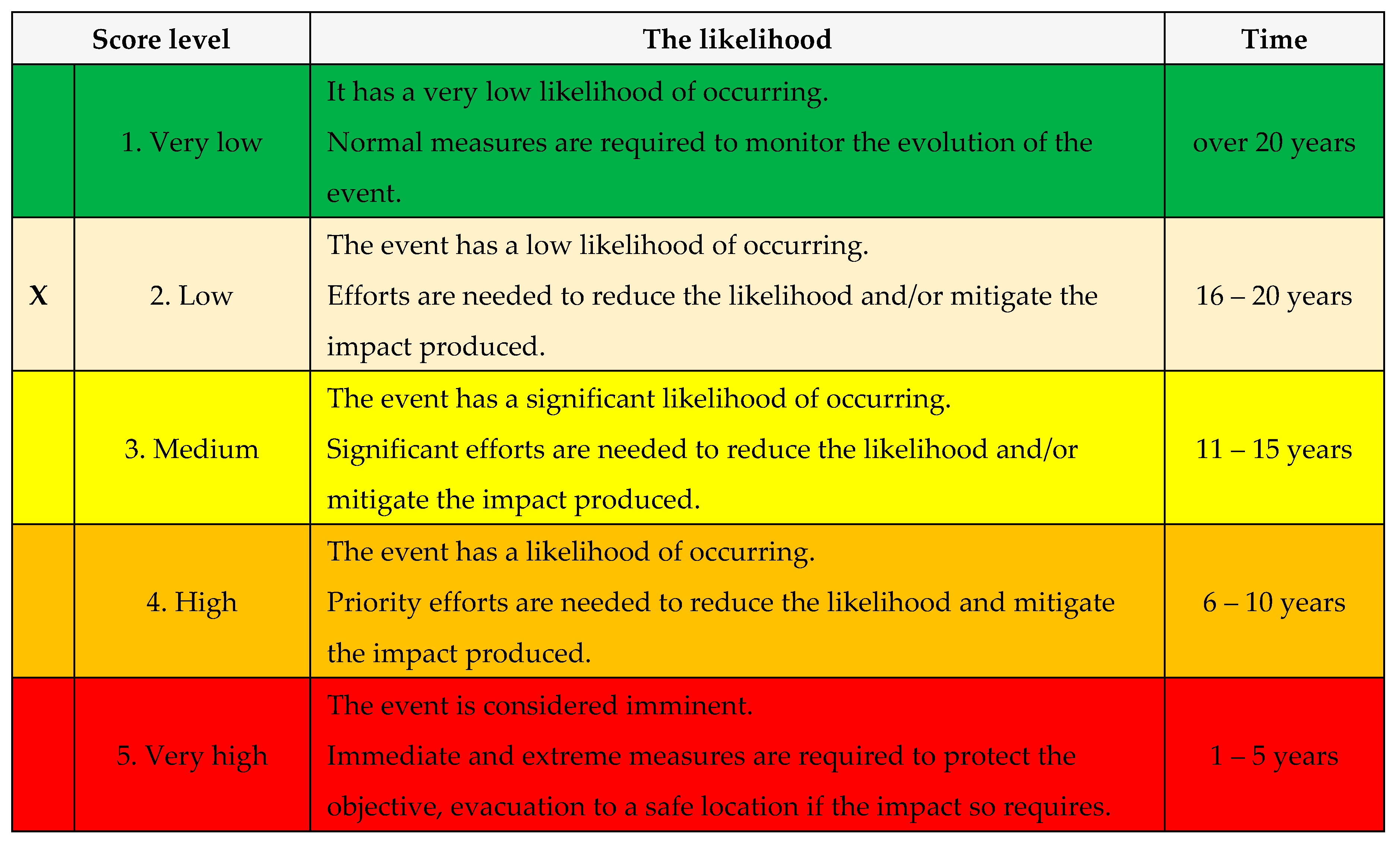
B. Estimating the likelihood
C. The gravity analysis
Table 31.
The Gravity Analysis.
Table 31.
The Gravity Analysis.
Table 32.
The Gravity and Level Analysis.
Table 32.
The Gravity and Level Analysis.
D. Estimating the gravity
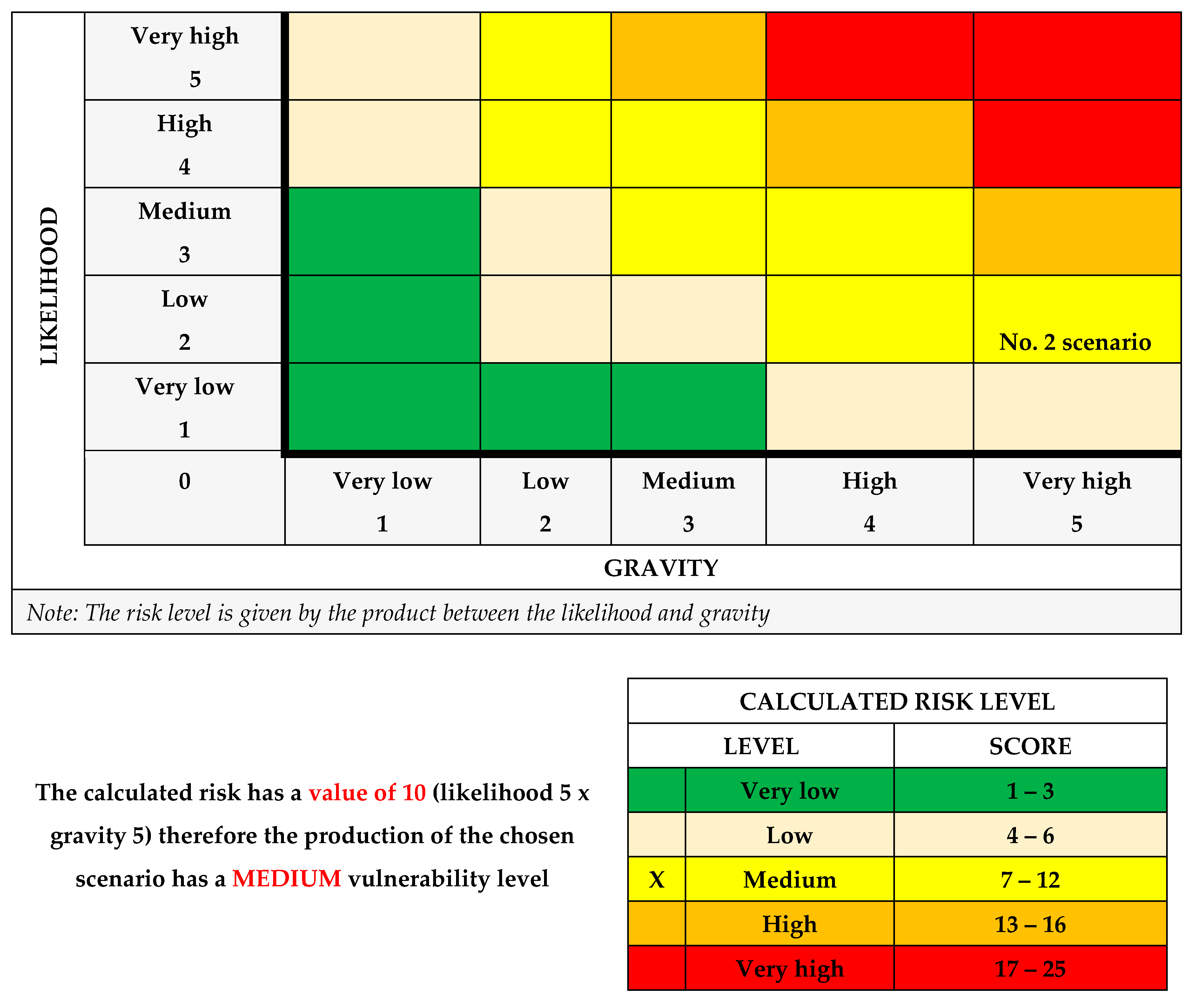
E. The calculation of the risk level
F. Treating the risk
Treating the risk is made through proposed recommendations that support the reduction of the risk level.
Table 33.
Proposed recommendations.
Table 33.
Proposed recommendations.
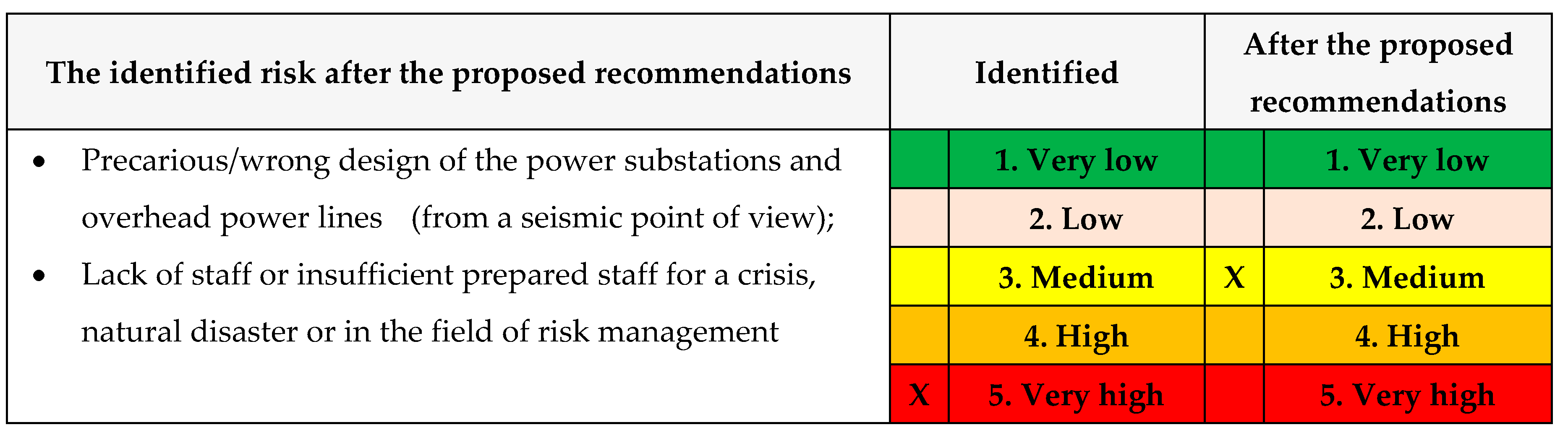
G. The recalculation of the risk
Table 34.
The identified risk after the proposed recommendations.
Table 34.
The identified risk after the proposed recommendations.
H. The recalculation of the risk level
8. Conclusions
Following the analysis of the instability and insecurity elements within the National Power System, the following were identified: 7 dysfunctions, 11 deficiencies, 3 non-compliances, 21 vulnerabilities, 21 risks, 1 risk from outside, 21 threats, 1 threat from outside, 21 hazards, 1 hazard from outside, 4 aggressions and 1 aggression from outside.
Following the prioritization of the identified instability and insecurity elements within the National Power System (7 dysfunctions, 11 deficiencies, 3 non-compliances, 21 vulnerabilities, 21 risks, 21 threats, 1 threat from outside, 21 hazards, 1 hazards from outside, 4 aggressions and 1 aggression from outside), the following types of risk scenarios have been highlighted:
Vulnerabilities: 5 the worst scenarios; 8 the plausible the worst; 8 moderate scenarios;
Risks: 6 the worst scenarios; 8 the plausible the worst; 8 moderate scenarios;
Threats: 6 the worst scenarios; 8 the plausible the worst; 8 moderate scenarios;
Dangers: 6 the worst scenarios; 8 the plausible the worst; 8 moderate scenarios;
Aggression: 2 the worst scenarios; 2 the plausible the worst; 1 moderate scenarios.
In total is 25 the worst scenarios, 34 plausible the worst and 33 moderate scenarios.
Following the highlighting of the 25 the worst scenarios, the authors propose that only 2 risk scenarios with very high probability and severity, may endanger the malfunctioning of the National Power System (black-out), to be evaluated in this paper:
Poor management of the transmission operator activity (exploitation, maintenance and development) of the Power Transmission Grid installations → Risk of technical incident (isolated/associated), technical disturbance or damage → Technological threat → Hazard of technologically instability (incident / damage) → black-out;
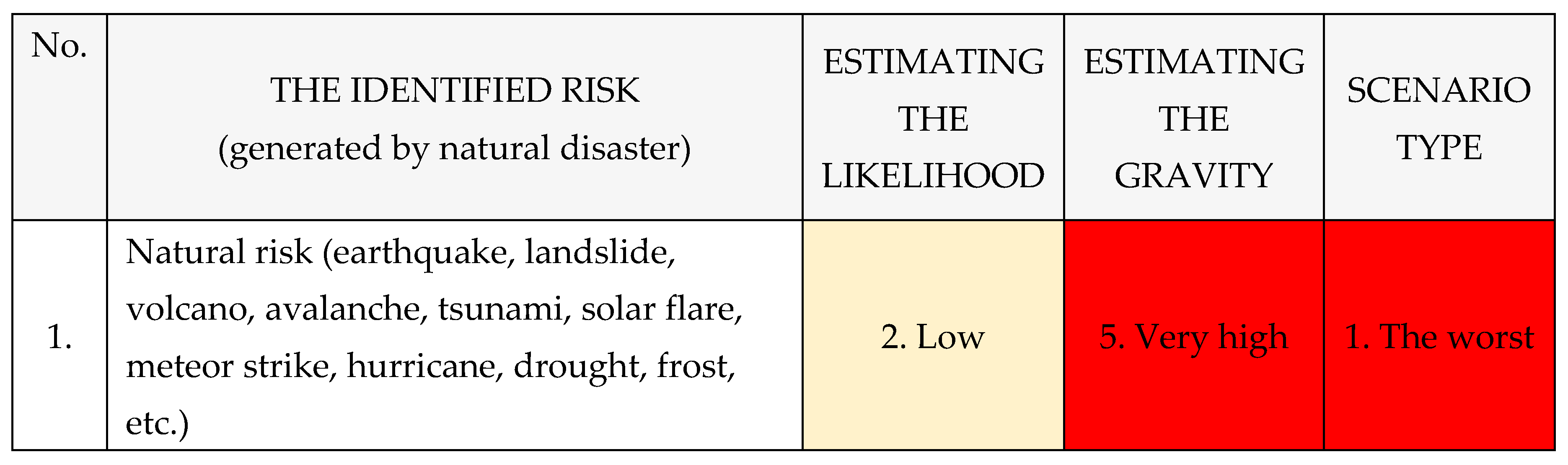
Risk of natural disaster → Threat of natural disaster → Hazard of natural disaster → Attacks caused by natural disasters (earthquake, landslide, volcano, avalanche, tsunami, solar flare, meteor strike, hurricane, drought, frost, etc.).
After assessment of Vulnerability: Poor management of the transmission operator activity (exploitation, maintenance and development) of the Power Transmission Grid installations → Risk of technical incident (isolated/associated), technical disturbance or damage → Technological threat → Hazard of technologically instability (incident / damage) → black-out, result is next:
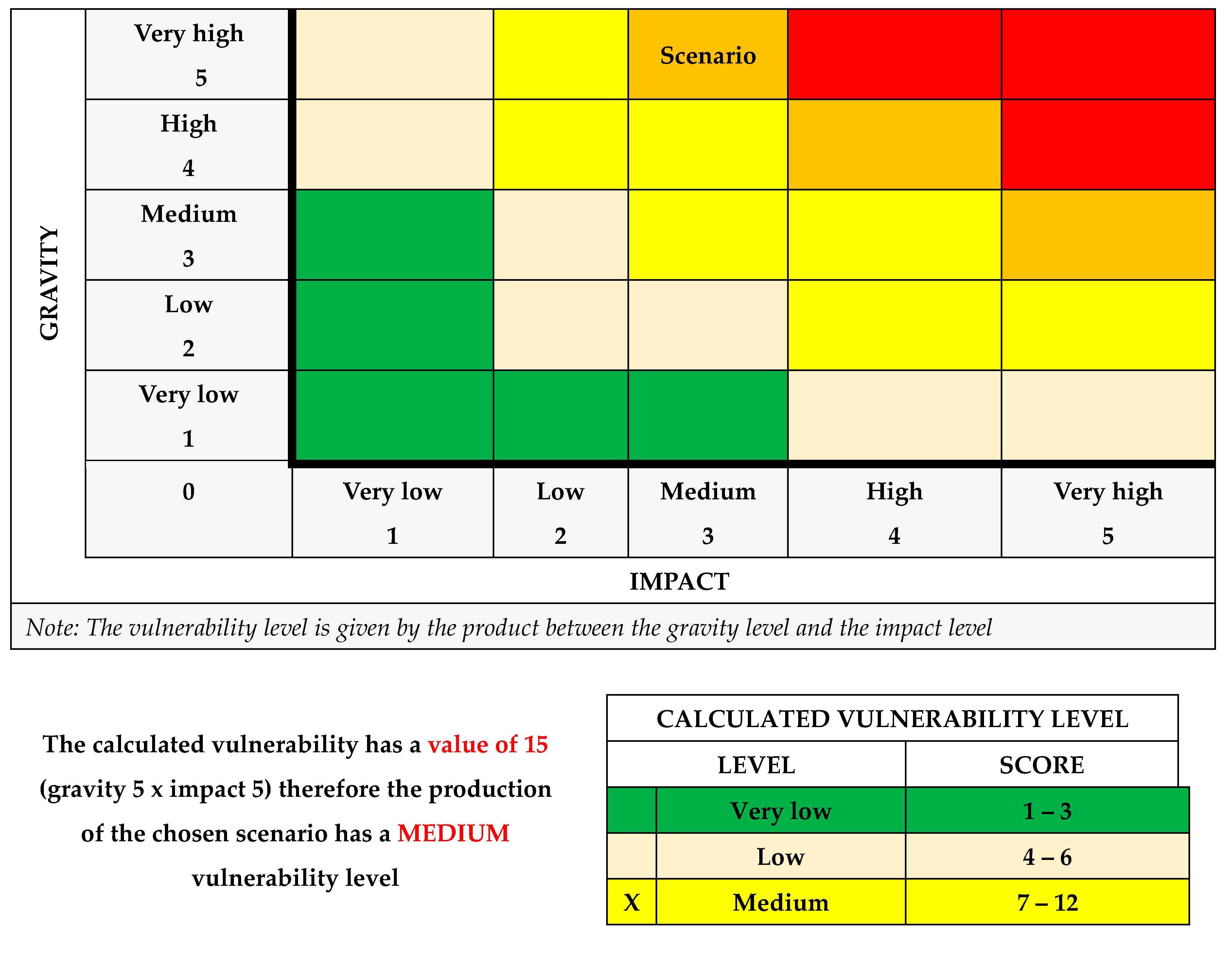
The calculated vulnerability has a value of 25 (gravity 5 x impact 5), therefore the production of the chosen scenario has a VERY HIGH vulnerability level;
After proposed recommendations: The calculated vulnerability has a value of 15 (gravity 5 x impact 5) therefore the production of the chosen scenario has a MEDIUM vulnerability level.
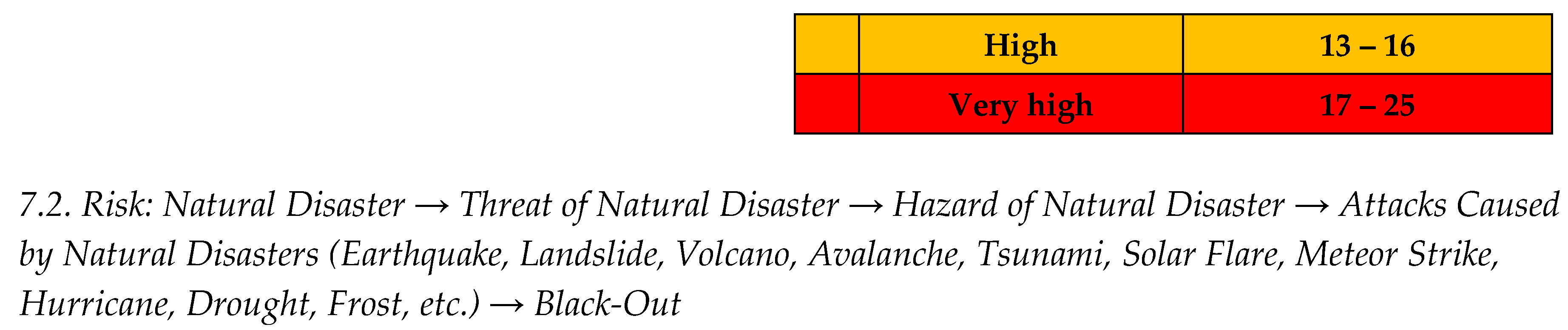
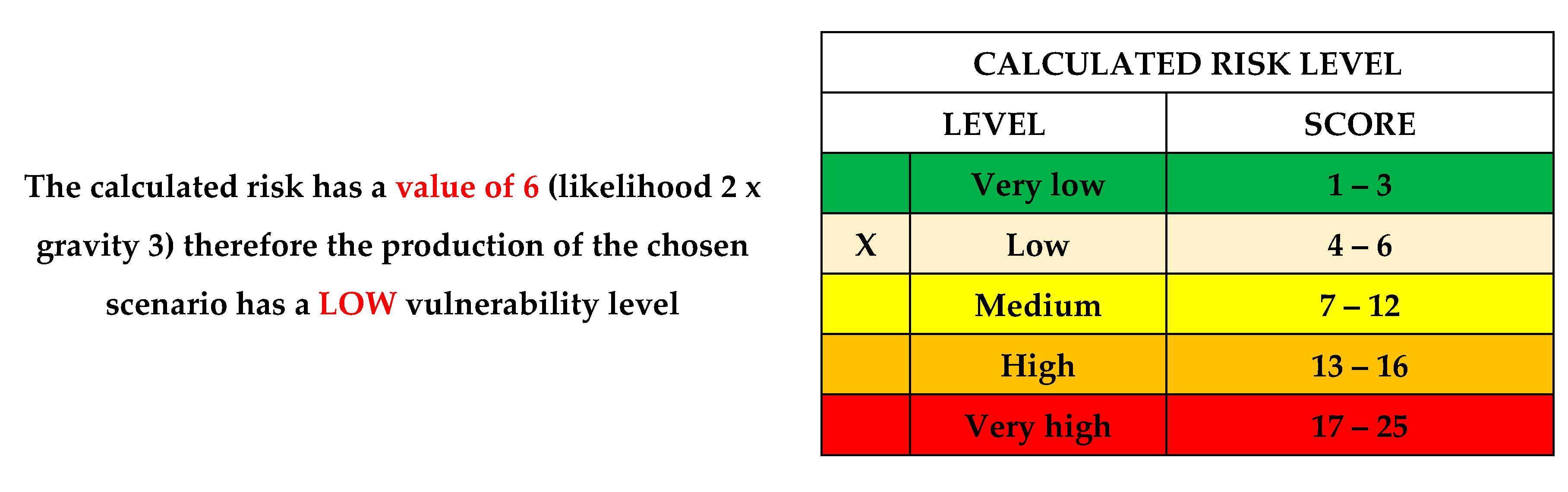
After assessment of the Risk: Natural disaster → Threat of natural disaster → Hazard of natural disaster → Attacks caused by natural disasters (earthquake, landslide, volcano, avalanche, tsunami, solar flare, meteor strike, hurricane, drought, frost, etc.) → black-out, rrsults is next:
The calculated risk has a value of 10 (likelihood 5 x gravity 5) therefore the production of the chosen scenario has a MEDIUM vulnerability level;
After proposed recommendations: The calculated risk has a value of 6 (likelihood 2 x gravity 3) therefore the production of the chosen scenario has a LOW vulnerability level.
References
- Nicolae Daniel Fîță, Mila Ilieva Obretenova, Florin G. Popescu, Romanian Power System – European energy security generator, LAP – Lambert Academic Publishing, ISBN: 978-620-7-46269-8, 2024.
- Nicolae Daniel Fîță, Dan Codrut Petrilean, Ioan Lucian Diodiu, Andrei Cristian Rada, Adrian Mihai Schiopu, Florin Muresan-Grecu, Analysis of the causes of power crises and theit impacts on energy security, Proceedings of International Conference on Electrical, Computer ad Energy Technologies – ICECET 2204, July 2024, Sydney, Australia, Publisher IEEE, Date added to IEEE Explore: 08 October 2024, www.icecet.com. [CrossRef]
- Nicolae Daniel Fîță, Adina Tătar, Mila Ilieva Obretenova, Security risk assessment of critical energy infrastructures, LAP – Lambert Academic Publishing, ISBN: 978-620-7-45824-0, 2024.
- Nicolae Daniel Fîță, Mila Ilieva Obretenova, Adrian Mihai Șchiopu, National Security – Elements regarding the optimisation of Energy Sector, LAP – Lambert Academic Publishing, ISBN: 978-620-7-45693-2, 2024.
- ISO 31000:2018 - Risk management — Guidelines.
- Kezunovic, M.; Dobson, I.; Dong, Y. Impact of extreme weather on power system blackouts and forced outages: New challenges. In Proceedings of the 7th Balkan Power Conference, Šibenik, Croatia, 10–12 September 2008; pp. 1–5.
- Panteli, M.; Mancarella, P. Influence of extreme weather and climate change on the resilience of power systems: Impacts and possible mitigation strategies. Electr. Power Syst. Res. 2015, 127, 259–270.
- Li, T.; Luo, B.; Liu, L.; Wu, T. Wind accident analysis of transmission line in China Southern Power Grid’s Coastal Regions. In Proceedings of the 5th International Conference on Electric Utility Deregulation and Restructuring and Power Technologies (DRPT), Changsha, China, 26–29 November 2015; pp. 1700–1704.
- Panteli, M.; Mancarella, P. Modeling and Evaluating the Resilience of Critical Electrical Power Infrastructure to Extreme Weather Events. IEEE Syst. J. 2015, 11, 1733–1742.
- Cadini, F.; Agliardi, G.L.; Zio, E. A modeling and simulation framework for the reliability/availability assessment of a power transmission grid subject to cascading failures under extreme weather conditions. Appl. Energy 2017, 185, 267–279.
- Liu, Y. Short-term operational reliability evaluation for power systems under extreme weather conditions. In Proceedings of the 2015 IEEE Eindhoven PowerTech, Eindhoven, The Netherlands, 29 June–2 July 2015; pp. 1–5.
- Anvari, M.; Lohmann, G.M.; Wächter, M.; Milan, P.; Lorenz, E.; Heinemann, D.; Tabar, M.R.R.; Peinke, J. Short term fluctuations of wind and solar power systems. New J. Phys. 2016, 18, 063027.
- Pahwa, S.; Scoglio, C.M.; Scala, A. Abruptness of Cascade Failures in Power Grids. Sci. Rep. 2014, 4, 3694.
- Gan, Y.; Hu, Y.; Ruan, J.; Du, Z.; Liu, C.; Du, W. Analysis and Prevention of Main Natural Disasters of 500kV Transmission Lines in Central China Power Grid. Electr. Power Constr. 2012, 6, 37–42.
- Kiel, E.S.; Kjølle, G.H. The impact of protection system failures and weather exposure on power system reliability. In Proceedings of the International Conference on Environment and Electrical Engineering and 2019 IEEE Industrial and Commercial Power Systems Europe (EEEIC/I&CPS Europe), Genova, Italy, 10–14 June 2019; pp. 1–6.
- Jufri, F.H.; Widiputra, V.; Jung, J. State-of-the-art review on power grid resilience to extreme weather events: Definitions, frameworks, quantitative assessment methodologies, and enhancement strategies. Appl. Energy 2019, 239, 1049–1065.
- Matko, M.; Golobič, M.; Kontić, B. Reducing risks to electric power infrastructure due to extreme weather events by means of spatial planning: Case studies from Slovenia. Utilities Policy 2017, 44, 12–24.
- Chen, X.; Sun, K.; Cao, Y.; Wang, S. Identification of Vulnerable Lines in Power Grid Based on Complex Network Theory. In Proceedings of the 2007 IEEE Power Engineering Society General Meeting, Tampa, FL, USA, 23 July 2007; pp. 1–6.
- Arianos, S.; Bompard, E.; Carbone, A.; Xue, F. Power grid vulnerability: A complex network approach. Chaos: Interdiscip. J. Nonlinear Sci. 2009, 19, 013119.
- Pagani, G.A.; Aiello, M. The Power Grid as a complex network: A survey. Phys. A Stat. Mech. Its Appl. 2013, 392, 2688–2700.
- Cuadra, L.; Salcedo-Sanz, S.; Del Ser, J.; Jiménez-Fernández, S.; Geem, Z.W.; Cuadra, L.; Salcedo-Sanz, S.; Del Ser, J.; Jiménez-Fernández, S.; Geem, Z.W. A Critical Review of Robustness in Power Grids Using Complex Networks Concepts. Energies 2015, 8, 9211–9265.
- Li, Q.; Li, H.Q.; Huang, Z.M.; Li, Y.Q. Power system vulnerability assessment based on transient energy hybrid method. Power Syst. Protect. Control. 2013, 41, 1–6.
- Li, X.; Qi, Z. Impact of cascading failure based on line vulnerability index on power grids. Energy Syst. 2021, 1–26.
- Abedi, A.; Gaudard, L.; Romerio, F. Review of major approaches to analyze vulnerability in power system. Reliab. Eng. Syst. Saf. 2019, 183, 153–172.
- Johansson, J.; Hassel, H.; Zio, E. Reliability and vulnerability analyses of critical infrastructures: Comparing two approaches in the context of power systems. Reliab. Eng. Syst. Saf. 2013, 120, 27–38.
- Ouyang, M. Comparisons of purely topological model, betweenness based model and direct current power flow model to analyze power grid vulnerability. Chaos Interdiscip. J. Nonlinear Sci. 2013, 23, 023114.
- Wei, X.; Gao, S.; Huang, T.; Bompard, E.; Pi, R.; Wang, T. Complex Network-Based Cascading Faults Graph for the Analysis of Transmission Network Vulnerability. IEEE Trans. Ind. Inform. 2018, 15, 1265–1276.
- Wang, W.; Song, Y.; Li, Y.; Jia, Y. Research on Cascading Failures Model of Power Grid Based on Complex Network. In Proceedings of the 2020 Chinese Control and Decision Conference (CCDC), Hefei, China, 22–24 August 2020; pp. 1367–1372.
- Alin E. Cruceru, Florin G. Popescu, Daniel N. Fita, Marius D. Marcu, Razvan C. Olteanu, Adrian M. Schiopu, Gabriela Popescu, Current Approaches in Engineering Research and Technology, Vol. 10, Chapter 4: Exploring the Dimensions of Energy Security in Relation to the National Power Grid, Book Publisher International, India ISBN 978-81-983173-4-6 (Print), ISBN 978-81-983173-0-8 (eBook). [CrossRef]
- Moraru, R.I., Păun, A.P., Dura, C.C., Dinulescu, R., Potcovaru, A-M. Analysis of the drivers of Occupational Health and Safety performance disclosures by Romanian companies, Economic Computation and Economic Cybernetics Studies and Research, Issue 3, 2020, pp. 197 – 214. [CrossRef]
- Darabont, D.C., Moraru, R.I., Antonov, A.E., Bejinariu, C. (2017), Managing new and emerging risks in the context of ISO 45001 standard, Quality - Access to Success, Volume 18, Supplement 1, pp. 11-14.
Figure 1.
National Power System map.
Figure 1.
National Power System map.
Figure 2.
The dependence of state systems, economy and national industry on electricity.
Figure 2.
The dependence of state systems, economy and national industry on electricity.
Figure 3.
The identification of instability and insecurity elements.
Figure 3.
The identification of instability and insecurity elements.
Figure 4.
The scheme of propagation of system, instability and insecurity elements.
Figure 4.
The scheme of propagation of system, instability and insecurity elements.
Figure 5.
The sequence (phases) of propagation of system, instability and insecurity elements.
Figure 5.
The sequence (phases) of propagation of system, instability and insecurity elements.
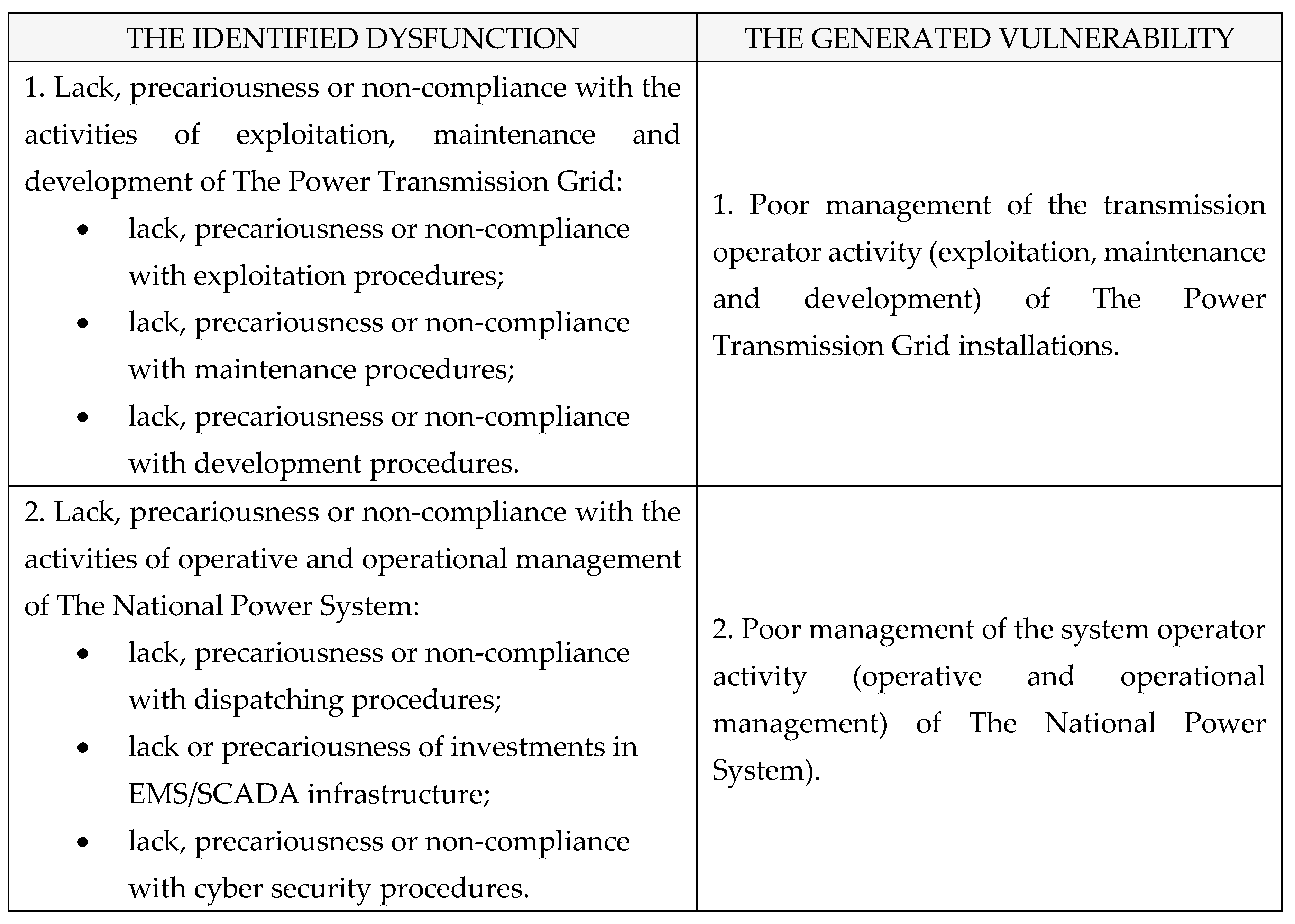
Table 1.
Dysfunctions identified within The National Power System.
Table 1.
Dysfunctions identified within The National Power System.
Table 2.
Deficiencies identified within The National Power System.
Table 2.
Deficiencies identified within The National Power System.
Table 3.
Non-compliances identified within The National Power System.
Table 3.
Non-compliances identified within The National Power System.
Table 4.
Vulnerabilities identified within The National Power System.
Table 4.
Vulnerabilities identified within The National Power System.
Table 5.
Identified risks within The National Power System.
Table 5.
Identified risks within The National Power System.
Table 6.
Identified threats within The National Power System.
Table 6.
Identified threats within The National Power System.
Table 7.
Identified threats from the outside with effect on The National Power System.
Table 7.
Identified threats from the outside with effect on The National Power System.
Table 8.
Identified dangers within The National Power System.
Table 8.
Identified dangers within The National Power System.
Table 9.
Identified dangers from the outside with effect on The National Power System.
Table 9.
Identified dangers from the outside with effect on The National Power System.
Table 10.
Identified agressions within The National Power System.
Table 10.
Identified agressions within The National Power System.
Table 11.
Other identified aggressions with effect on The National Power System.
Table 11.
Other identified aggressions with effect on The National Power System.
Table 21.
The identification of the worst scenarios.
Table 21.
The identification of the worst scenarios.
Table 22.
Choosing the worst scenarios for assessment.
Table 22.
Choosing the worst scenarios for assessment.
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).