1. Introduction
The Internet of Things (IoT) is a comprehensive network of interconnected physical devices equipped with sensors, software, and various communication technologies, enabling them to communicate and share data over the Internet. Powered by smart devices, edge computing (EC), and big data analytics, IoT is transforming both business operations and the interactions between service providers and customers [
1]. The number of IoT devices is estimated to nearly double, rising from 15.9 billion in 2023 to over 32.1 billion by 2030. IoT devices find applications across various industry sectors and consumer markets, such as healthcare, industrial automation, automotive, smart cities, logistics, and agriculture [
2,
3]. The adoption of IoT has been further fuelled by the integration of advanced technologies such as 5G, AI, Blockchain, and EC [
4,
5]. In a typical IoT application architecture shown in
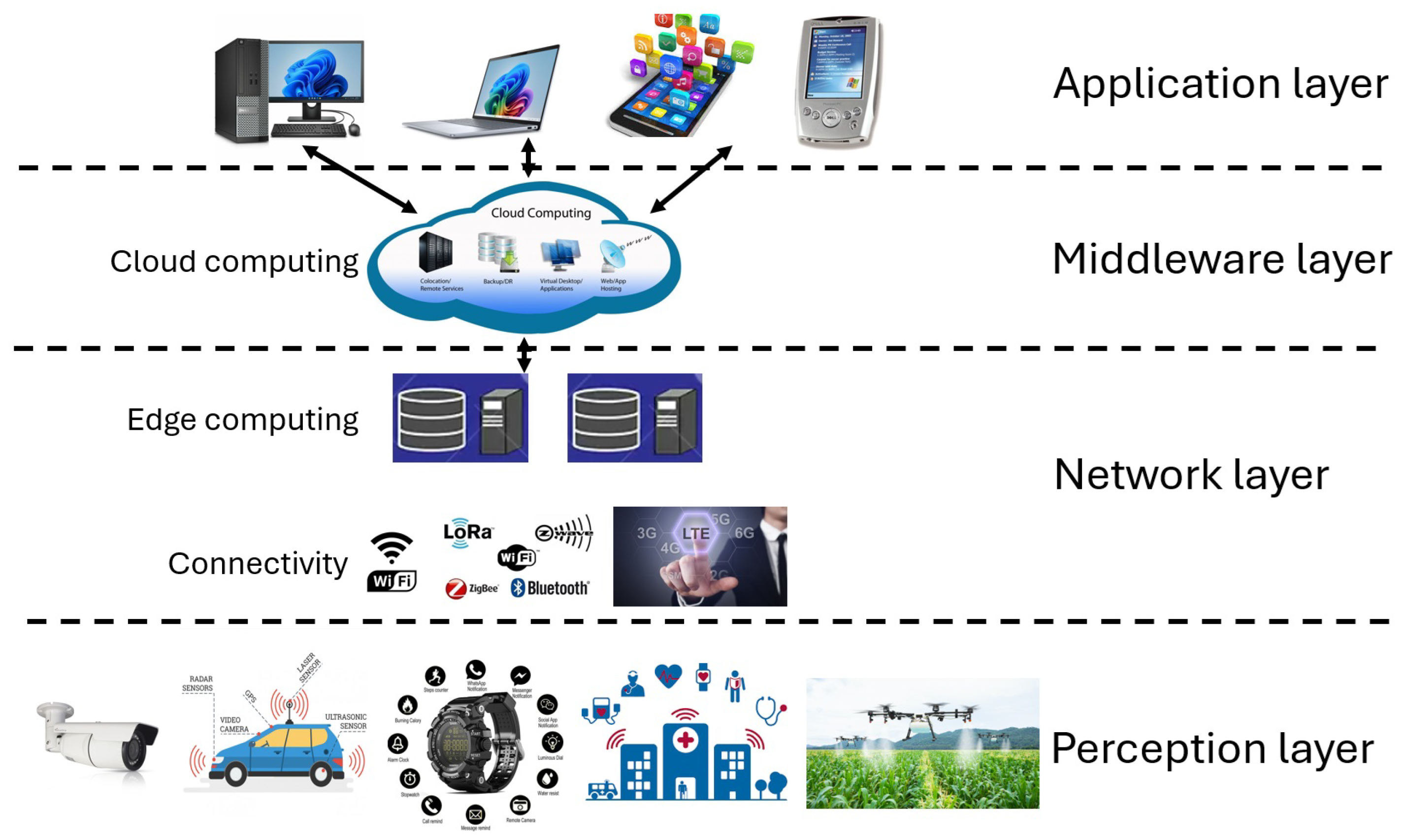
Figure 1, sensing nodes generate a huge amount of data requiring further processing to enable intelligence for service providers and end users. Cloud computing technology requires sensed data to be uploaded to centralized servers called data centers for further processing and results get transmitted back to the device layer. Such a centralized processing approach puts enormous pressure on the communication network regarding bandwidth, latency, and the vulnerability of data security [
6].
Centrally located servers at data centers offer poor quality of service (QoS) in addition to the burden imposed on the communication networks as,
Additional costs are involved due to inefficient utilization of bandwidth and network resources,
Large-sized data drastically degrades network performance,
Billions of connected devices on IoT network make it difficult to manage data traffic, and
Time-sensitive IoT applications are bound to get affected due to network-introduced latency [
7,
8].
For example, a camera installed on an autonomous vehicle captures a large amount of data from its surroundings, to make decisions in real-time. In a cloud computing environment, the time spent in transmitting sensed data from the vehicle to the cloud and receiving processed data back from the cloud is crucial. Further, a large number of such vehicles may cripple the network bandwidth and its reliability. Hence, processing the raw data closer to its source would reduce response times and reduce the burden on the network [
9].
The concept of “Edge Computing (EC)” was introduced to reduce communication latency and bandwidth requirements, offer real-time data analysis, lower operational cost, higher scalability, and improve the quality of services [
10,
11,
12,
13]. Earlier, the data had to be transmitted to the cloud over long distances, with the results then being sent back to the user through an extended path. EC, being closer to the data source, reduces transmission delays, packet loss, and high energy consumption [
9,
14,
15]. Additionally, EC offers location-aware services and enhances resource allocation by shifting tasks from IoT devices with limited resources to more powerful edge servers [
16]. EC is characterized by its heterogeneous distributed network architecture, large-scale data processing, parallel computing capabilities, and support for mobility services, including location tracking. Whether data is stored at edge nodes or in the cloud, the risk of a security breach or hacking remains present. However, EC heightens vulnerability to cyber-attacks and threats because sensitive data is stored and processed in a distributed environment with limited resources, making it challenging to implement complex security algorithms [
7,
17].
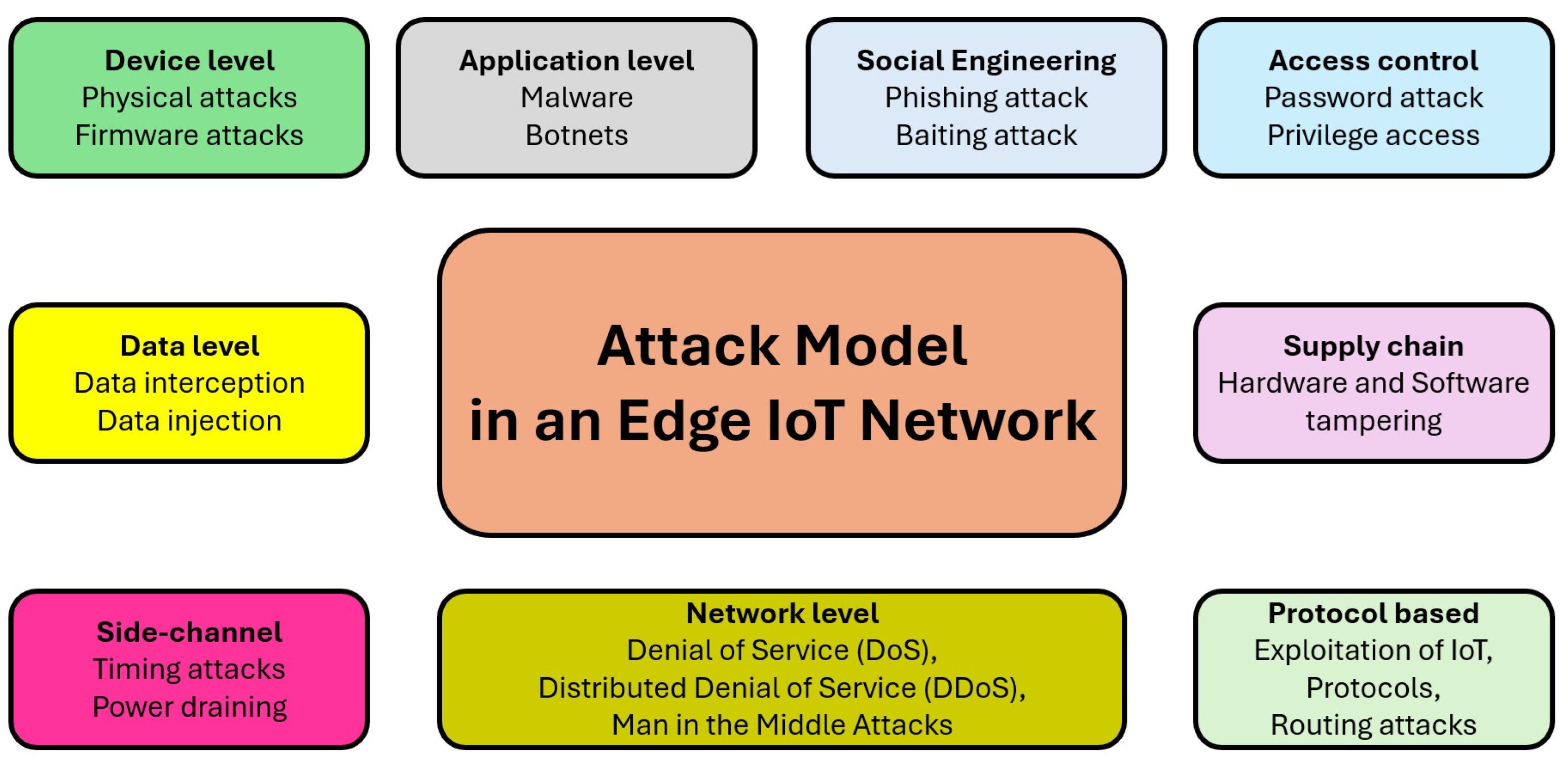
Figure 2 shows an edge-based IoT attack model outlining various threats and vulnerabilities specific to the edge computing environment in the Internet of Things (IoT) context [
18].
Also, the dynamic environment at the edge of the IoT network makes it vulnerable to security attacks and challenging to protect. Most of the attacks on edge computing architecture can be placed into four different classes i.e., distributed denial-of-service (DDoS) attacks, side-channel attacks, malware injection attacks, and authentication and authorization attacks [
19].
Current research areas in edge computing security and privacy mainly focus on techniques like data privacy, lightweight security protocols, Artificial Intelligence (AI) integration, trust management, and collaborative security. Differential privacy (DP) adds noise to data to protect individual privacy while allowing aggregate data analysis in five critical areas: data transmission, data processing, data model training, data publishing, and location privacy [
20,
21,
22]. Authors from [
23], introduce a hybrid differential privacy model combined with adaptive gradient compression, providing stronger protection against inference attacks while transmitting gradient parameters. Implementing secured lightweight encryption and authentication techniques secures data from side-channel and hardware attacks [
24]. Samad et. al., proposed an anonymous authentication protocol that utilizes elliptic curve cryptography (ECC) and signcryption techniques [
25]. Several encryption models have been developed over the years, using or combining various techniques, like authenticated encryption (AE) with associated data (AEAD) schemes [
26].
AI-driven techniques can improve edge environments’ intrusion detection, data confidentiality, and access control. Researchers have developed various strategies for securing edge computing, including machine learning (ML) algorithms and innovative approaches like hybrid feature analysis. ML is particularly effective for detecting anomalies and potential breaches in real-time, providing strong protection against advanced attacks [
27,
28]. The shift from cloud computing to edge computing has brought intelligence closer to edge devices such as mobile phones, smart speakers, sensors, wearable devices, and sensor networks, enabling faster data processing tasks like inference, pattern matching, and more [
29]. AI chips with computational accelerators like Field Programmable Gate Arrays (FPGAs), Graphics Processing Units (GPUs), Tensor Processing Units (TPUs), and Neural Processing Units (NPUs) are integrated into intelligent mobile devices [
30]. Trust management is a critical component of EC, involving the processing and storage of data at the network’s edge. Blockchain and distributed ledger technologies (DLTs) enable decentralized, secure, and transparent trust management. Wang et. al., introduced a Blockchain-based secure data aggregation strategy (BSDA) integrating a security label into the block header, which includes the task’s security level (SL) and completion requirement (CR) [
31]. Blockchain-based protocol introduced by [
32], supports conditional anonymity and efficient key management, overcoming the limitations of traditional cryptographic protocols. Authors of [
33], propose multiple edge blockchains that interact through a cloudlet chain operating independently.
Collaborative edge computing selectively shares data or insights among nodes or with the cloud, reducing the overall exposure of private information. Techniques like federated learning (FL) enable multiple devices to train machine learning models locally on their data, without sharing the actual data with others. This approach helps organizations adhere to data residency and privacy laws by ensuring data remains within specific geographic boundaries. Li et. al. have developed algorithms based on Multi-Armed Bandit (MAB) frameworks by sharing information about server security risks [
34] while proposes an SDN-based framework [
35]. Data disturbance and adversarial training methods are adopted in [
36] for generating adversarial samples using the Firefly Algorithm (FA).
Xiao et. al., provide a classification of security attacks in an edge environment under six categories i.e., DDoS attacks, side-channel attacks, malware injection attacks, authentication & authorization attacks, man-in-the-middle attacks, and bad-data injection attacks [
19]. A threat intelligence report from “Netscout” reports an upsurge in DDoS attacks during the second half of 2021. About 9.7 million attacks were identified in 2021, which is 14% higher than in 2019 [
37]. The number of malware attacks on IoT devices has grown from 813 million to 2.9 billion from 2018 to 2020 [
38]. Field programmable gate arrays (FPGAs) are suitable for implementing customized hardware logic and real-time image processing for high-performance edge computation [
39]. They possess characteristics that suit edge computing requirements like (i) processing of data streams at lower latency, (ii) adaptability to any algorithm due to their reconfigurable architecture exploiting both spatial and temporal parallelism at a finer granularity, and (iii) thermal stability reduces cooling cost [
40]. FPGA-based edge devices have proven their resilience to physical and side-channel attacks. FPGA’s inherent ability to process tasks in parallel and flexibility in handling diverse workloads can match AI and ML algorithms’ computational and processing needs. FPGAs allow greater flexibility in what the processor does, they are very useful in building AI accelerators [
41]. The FPGA-based edge reduces the response time by 1.62x for the object application and 1.14x for the face application as compared to CPU-based edge offloading in general [
42]. Zhao et. al., presented a novel approach to secure FPGA-based edge devices, using lightweight hardware-assisted chaos-based stream cipher for protecting FPGA bitstreams [
43]. Regarding security, IP protection techniques implemented on FPGA have better flexibility and require no extra resource overhead compared to those implemented on the traditional custom circuit. Ngo et. al., implemented a hierarchical decision-making approach combined with an ANN model as a hardware-accelerated framework on the FPGA for real-time detection of network intrusions [
44]. An Oscillator Collapse (OC-PUF) designed to utilize manufacturing variations in FPGAs that generate unique responses to input challenges was tested on Altera DE2-115 FPGA boards, achieving an inter-chip Hamming distance of 46.7% [
45]. FPGAs can run several lightweight cryptographic protocols simultaneously in addition to advantages like optimal chip area, speed, and power consumption [
46]. Silicon physically unclonable functions (PUFs) implemented on FPGA platforms are flexible, secure, cost-effective, and offer a quick turnaround. FPGA-based PUFs are diverse and effective in IP protection [
47], RFIDs [
48], secured key generation [
49], and remote activation [
50].
The remainder of this paper is placed under the following sections. Section II discusses the basic edge IoT architecture and key components of the edge ecosystem across three distinct layers of cloud, edge, and devices. Section III comprehensively discusses security, privacy challenges, associated countermeasures, and defense mechanisms deployed in an edge paradigm. Section IV digs into reasons responsible for authentication and trust challenges, access control, and root causes of edge computing security threats, and also proposes future research directions. Finally, we conclude this paper in Section V.
1.1. Methodology
Systematic Literature Reviews (SLR) [
51], as well as Preferred Reporting Items for Systematic reviews and Meta-Analyses (PRISMA) [
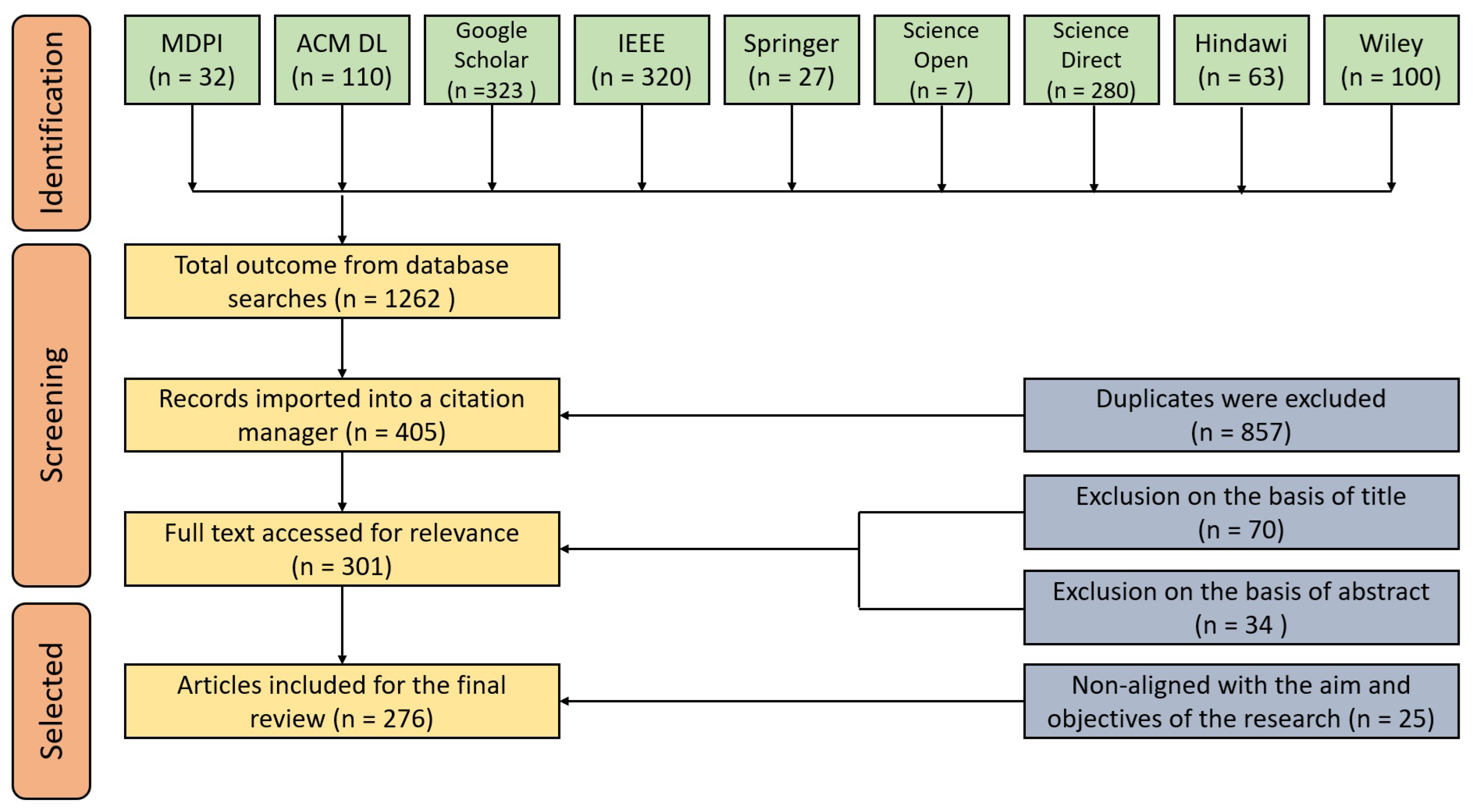
52] guidelines were followed while conducting this review work. PRISMA statements shown in
Figure 3 help to improve the reporting of systematic reviews and meta-analyses [
52].
SLR is a technique of classifying, picking, and critically evaluating research to propose solutions to a framed question by analyzing, and evaluating available literature. In October 2023, all recently published review papers were chosen from relevant and reliable academic repositories such as Google Scholar, IEEE, ACM, Science Open, Science Direct, Springer, Hindawi, Wiley Online Library, and MDPI.
1.2. Motivation
The primary strength of EC in IoT network security lies in its decentralized architecture. EC reduces the need for data to travel, thus reducing the potential attack surface. Hence, due to its precise control over data processing locations and methods, the EC can uphold data privacy regulations like the General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA). Therefore, EC enables the implementation of security protocols and analytics directly at the device level, facilitating real-time threat detection and response. EC is expected to possess flexible, lightweight, secure, and self-adaptive data analytic mechanisms based on user data sensitivity. However, the decentralized architecture of EC poses significant trust management challenges due to the issues related to collecting and managing evidence information from edge devices [
53]. ML-enabled EC can make data-driven inferences, predictions, and decisions based on acquired knowledge from past data. Also, ML is a preferred choice for IoT services’ privacy and data security due to its analytical capability. However, ML-based security schemes possess serious limitations due to the need for huge training datasets and privacy issues. So, there is an urgent need to devise an ML-based security scheme with low computation and communication costs [
54]. ML-based modeling through anomaly detection techniques offers more generic and robust security solutions against unknown attacks. However, ML-based security solutions may be vulnerable to ever-evolving attacks like adversarial ML [
55]. With a large amount of data generated by edge devices, there is a need for ML models that can run on resource-constrained edge devices. Also, techniques should exist for compressing the ML models that can make these models lighter and faster while making them suitable for edge deployment. Traditional security solutions rely on cryptographic methods where a secret key is stored within the device. However, the entire security system can be breached if this key is compromised. In contrast, a Physical Unclonable Function (PUF) uses the hardware itself as the medium to generate a unique secret key. The core principle of PUFs is based on the unique, device-level variations introduced during the manufacturing process. PUFs can be applied in various security protocols, including unique identifiers, secret keys, device authentication, intellectual property protection, and pseudo-random bit generators (PRNGs) [
56].
1.3. Comparison with Existing Literature
Table 1 lists recently published research articles that comprehensively survey data security and privacy challenges and their mitigation techniques in the context of EC-based IoT services. Topics covered include comprehensive trust management frameworks, mechanisms orchestration, and standardization, software-defined networking (SDN), blockchain, ML techniques, and diverse versions of cryptosystems. PUFs enable the authentication of integrated circuit (IC) chips by exploiting inherent device variations. These features include random delay characteristics of wires and transistors, due to process variations during semiconductor manufacturing processes [
57]. PUF-enabled RFIDs and processors are under development that can generate cryptographic keys and make physical cloning of semiconductors difficult [
49]. Majzoobi et. al., published a survey on PUF-enabled security primitives for field programmable gate arrays (FPGA) that can mitigate IP theft and tampering at HDL, synthesis, and bitstream levels [
58]. Edge machine learning (ML) implementation models and architectures were surveyed by Merenda et. al [
59]. Edge ML effectively reduces data load on the IoT network while improving privacy. Also, various security aspects, effective countermeasures through Edge artificial intelligence (AI), and the potential to improve Edge AI through Blockchain and Deep Reinforcement Learning are highlighted in [
60,
61].
[
83] proposes a blockchain-enabled FL-based architecture, that integrates blockchain technology with FL for decentralized training and secure data exchanges in UAV networks. The authors of [
63] carried out cryptanalysis of blockchain-based decentralized security solution for EC i.e., DecChain architecture, using the AVISPA simulation tool. The authentication and transactions between users and service providers are verified through blockchain mechanisms. An overview of the integration between blockchain and EC systems, providing a tamper-proof transaction ledger is discussed in [
65,
84]. The survey Identifies the critical issues in areas such as scalability, self-organization, security, resource management, and combining blockchain’s consensus algorithms with EC dynamic nature. Zhao et. al. conducted a detailed study on the benefits of integrating EC with cloud computing, and performance issues related to resource management, virtualization, and networking in several sub-aspects [
73]. Authors of [
75,
78] review the integration of Intrusion Detection Systems (IDS) and ML techniques on known signatures for an adaptive and efficient performance. A Hybrid Intrusion Detection Framework (EHIDF) for addressing security threats in Mobile Edge Computing (MEC) is proposed proposed by [
77], utilizing modules like Signature Detection Module (SDM), Anomaly Detection Module (ADM), and Hybrid Detection Module (HDM). The framework was evaluated using the UNSW-NB15 dataset, which includes various attack types. The researchers in [
79] implemented a double PUF-based model on the Xilinx Virtex5 FPGA for authenticating edge devices and software (IP cores), achieving a 61.96% reduction in resource utilization along with a performance stability rate of 99.54%. In [
80], XORArbiter PUFs were used for authenticating Edge Data Centres (EDCs) and edge devices, with Raspberry Pi devices simulating EDCs. In [
81], a 10-transistor SRAM cell was utilized to perform both XOR encryption (PUF) and MAC operations within the same cell, allowing the processing and encryption of DNN model weights. A delay-based PUF, producing a 1-bit signature, was synthesized and configured on a 28nm FPGA using on-chip resources such as lookup tables (LUTs) and flip-flops, achieving an average uniqueness of 49.7% [
82]. A fast and effective data encryption application, called Selective Encryption and Component-Oriented Deduplication (SEACOD) [
85] is discussed in context to the EC security [
86]. A Blockchain-based mutual authentication scheme integrated into certificate-less cryptography, elliptic curve cryptography, and pseudonym-based cryptography that authenticates transactions between edge servers and IoT devices is presented in [
87]. Also, the key generation negotiation mechanism while considering IoT devices’ mobility is implemented on hyper ledger fabric. A review of the current research status in EC security on access control, key management, privacy protection, attack mitigation, and anomaly detection is carried out by [
88]. The authors advocate the need for innovative proposals in EC as already-matured cloud computing does not meet recent challenges and requirements. Access control and key management schemes in Information-centric networking (ICN) and non-ICN infrastructures are based on traditional schemes and there is a need for newer architectures with lighter encryption protocols. A secured searching scheme for desired data within own/ shared data on storage as well as a searching scheme for IoT smart devices at the edge of cloud-assisted IoT is proposed in [
89]. The researchers claim that their proposed data-sharing mechanism along with the secret and public key encryption improves data processing time as compared to existing cloud-based systems.
A comprehensive overview of blockchain technology and its application in the network control, storage, and computation at edge nodes offering network security, data integrity, and computation verification are presented in [
64,
65,
90]. Blockchain technology integrated into the communication layer of an edge network can manage the radio spectrum and authentication of edge devices, as well as network access control in the network layer [
90]. Liu et. al. proposed blockchain-based data, and energy coins on the distributed consensus principle for the secured data exchange in Electric vehicles cloud and edge (EVCE) computing [
62]. Blockchain-based decentralized framework named “DecChain” is proposed to eliminate the need for authentication to access third-party services or resources [
63]. Also, hardware-assisted blockchain implementation of a defense-in-depth strategy and proper network segmentation forms the basis for a secured and trusted environment for the unidirectional payment channels is investigated by [
66,
68]. Infrastructure for cloud access through the adoption of the Secure access service edge (SASE) framework, is used for developing strategies for threat and intrusion detection, network segmentation, and defense in depth (DiD) [
69,
70].
1.4. Novelty and Contribution
The geographical distribution of edge devices increases the chances of a security risk as well as physical interference or damage. In addition, remote accessibility of edge devices presents opportunities for data theft and sabotages corporate operations. There are numerous research works available in the literature that address the above-discussed issues. Some of the research publications are survey conclusions related to the security aspects of IoT networks without any specific consideration of EC-assisted network deployments. The contributions made in this survey are listed below:
We present a summary, as well as detailed scrutiny and analysis of security and privacy-related issues about EC-assisted IoT services. Also, security objectives and functions on EC-based IoT applications are discussed.
A classification of data security threats and attacks due to poor design approaches, miss configurations, and implementation flaws is discussed. Also, appropriate mitigation techniques for the detection and prevention of attacks are covered.
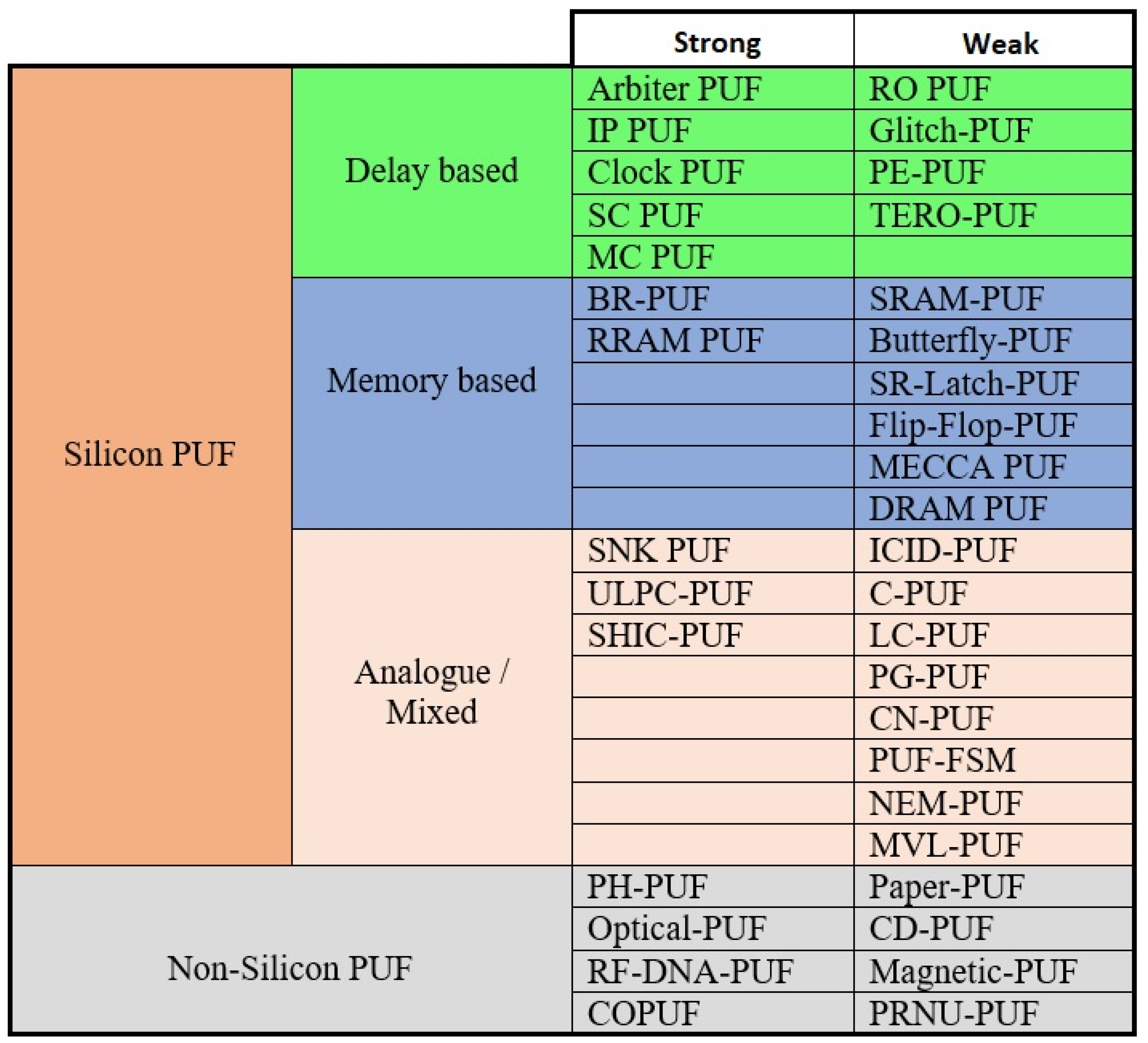
Detailed taxonomy of PUF classification based on silicon and non-silicon-based fabrication is presented, as well as significant performance and quality matrices are discussed.
A comprehensive summary of AI/ ML-based cryptography techniques for the mitigation of data security and privacy threats is presented. Also, the significance of reliable data sets and training data for the development of accurate ML algorithms is presented in this survey.
A discussion about future security research goals, privacy-related open challenges, and deeper insights into future research directions in the context of the EC-based IoT ecosystem.
2. Edge Computing
The enormous volume of data generated at IoT sensing nodes can overwhelm any commercial network, bringing all activities on the network to a halt. This leads to increased IT costs, dissatisfied customers causing financial and reputational losses, poor productivity in the industry, and most importantly health and safety concerns [
91]. EC is the real-time analysis, processing, and storage of data at a location near the source of data where it gets generated. Therefore, EC utilizes the available technology that moves computation nearer to the network edge. This involves handling downstream data for cloud services and upstream data for IoT services. [
92]. EC brings computational services, data storage, and retrieval as well as diverse enterprise applications near to the actual consumers of information. We can summarize the benefits of EC, as it eases the load on the network, cloud, and data center systems while mitigating latency concerns, offers quicker responses, and improves application performance, and customers’ experience. An edge computing platform provides its services by [
93]:
Processing the sensed data away from the central cloud or data center in real-time.
Caching, buffering, and optimization of the data close to edge nodes.
Transforms raw data from edge nodes into a format that can be processed for further deeper analysis.
There are numerous applications and services, such as industrial automation, virtual reality, real-time traffic management, data analytics, and home automation, that leverage the capabilities of EC. These capabilities include features like mobility support, situational awareness, minimal latency, and proximity to edge nodes or users. [
94]. Edge computing complements cloud computing services through improved user experience in the delay-sensitive application as well as offloading the cloud platform [
95]. Although there exist similarities between edge and cloud computing, certain distinct characteristics set them apart from each other. The location of EC and cloud computing layers in an IoT network is distinctive. Cloud is located significantly from the nodes/users’ location and induces high latency compared to EC. Location awareness and mobile support are possible in EC as it’s based on a distributed computing model as compared to a centralized model of cloud computing [
96]. An EC is a subset of cloud computing, that comprises hosting diverse services and applications in proximity to sensing nodes and users. As shown in
Table 2, there is a significant difference between cloud computing and EC. Also, an edge (location) is different from EC (action). Data collection at the edge (location) and forwarding it to a cloud with limited data processing is not considered to be EC. It is just a case of networking. However, if data collection and processing are carried out at the edge of EC.
2.1. Edge Architecture
Several architectures are proposed for the deployment of the EC layer but lack clear definitions and distinctions among nodes. Recent surveys conducted by researchers on EC architectures comprehend numerous outlooks, such as mobile edge cloud servers and networks, application specificity, and considerations regarding resource type, resource management objectives, resource location, and resource utilization. Also, architectural-related challenges like scalability and heterogeneity are elaborated. Premsankar et.al. classified all such edge architectures under three categories i.e., based on the location of resourceful servers from edge devices, resources from heterogeneous edge nodes, and classes of resources at edge & data centers [
14].
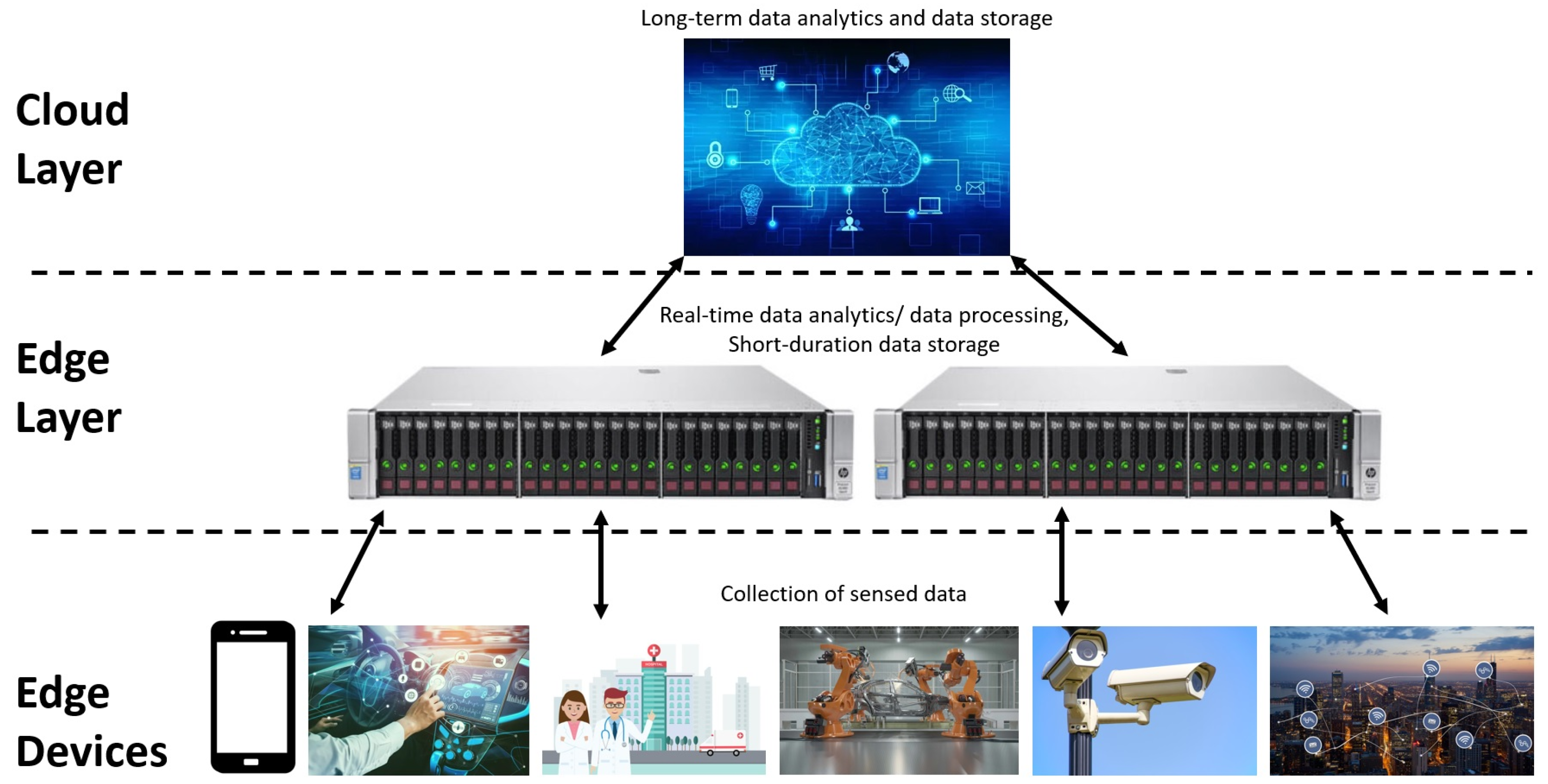
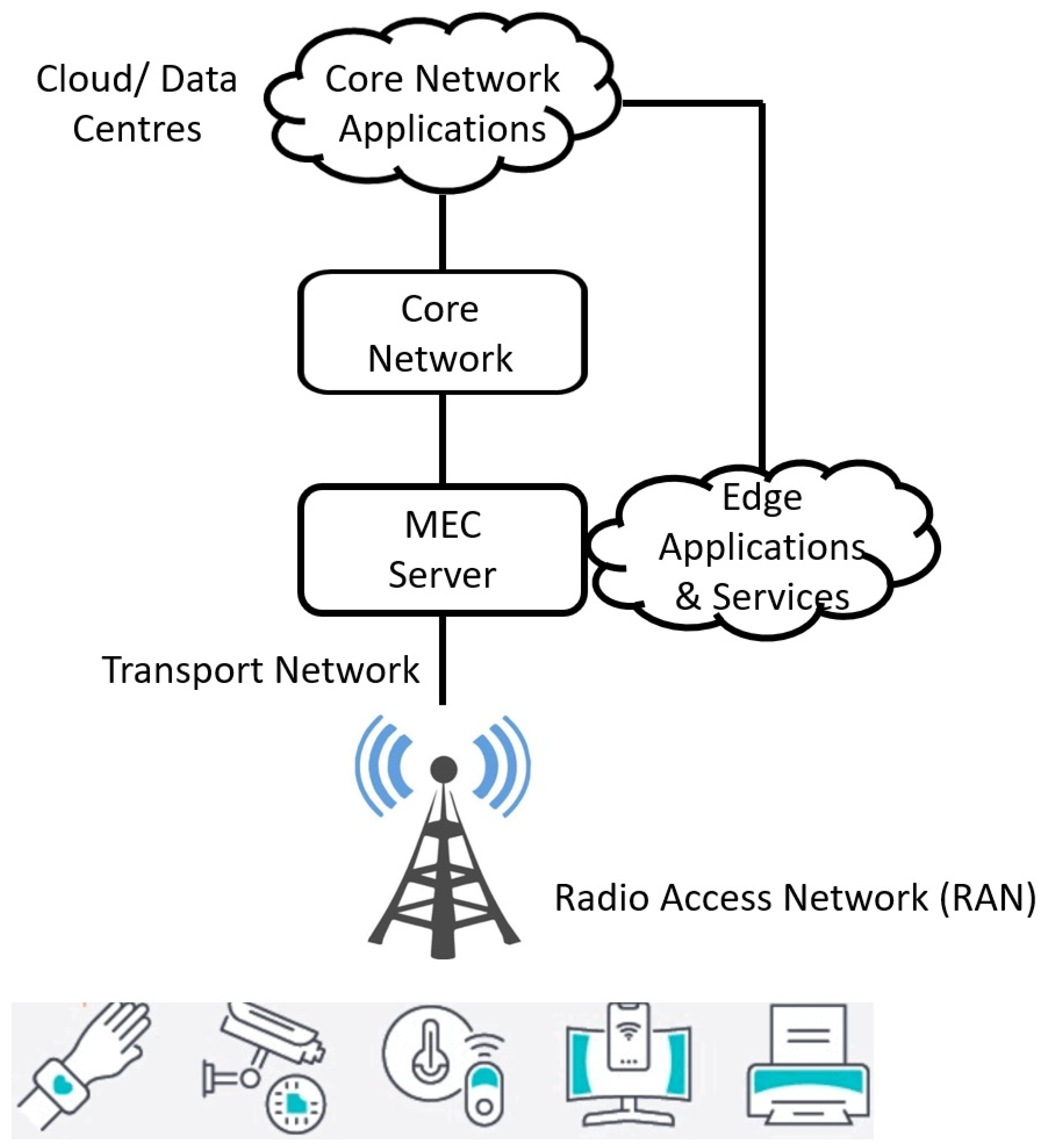
Figure 4 illustrates a fundamental three-layer architecture for EC. This structure establishes a connection from devices to an edge server, which in turn links to the entire network, encompassing both the cloud and data centers. Within this type of EC architecture, the edge server is situated in a fixed physical location and boasts significant computational capabilities, albeit less powerful than the conventional data centers employed in cloud computing. Furthermore, there is a discernible demarcation between the device level and the edge level, which includes the presence of edge servers. [
97,
98]. The lowest layer includes the IoT sensing nodes responsible for the ingestion of data and applications. It includes IoT devices like cameras, sensors, controllers, industrial machines, etc. The middle layer includes the edge computing infrastructure for data processing, routing, and computing operations. Data generated at the device layer undergo aggregation, analysis, and processing at the edge servers before being transmitted to the upper layer or returned to the device. Although edge computing servers have lower computational ability than cloud servers but offer better Quality of Service (QoS) and lower latency than cloud servers. At the topmost layer, there are cloud data centers involving a central data center and interconnected regional data centers. Even in an EC architecture, cloud data centers persist to serve a crucial role as storage places of information. This layer is accountable for tasks such as data analytics, artificial intelligence, machine learning, visualization, and more.
2.2. Edge Computing Challenges
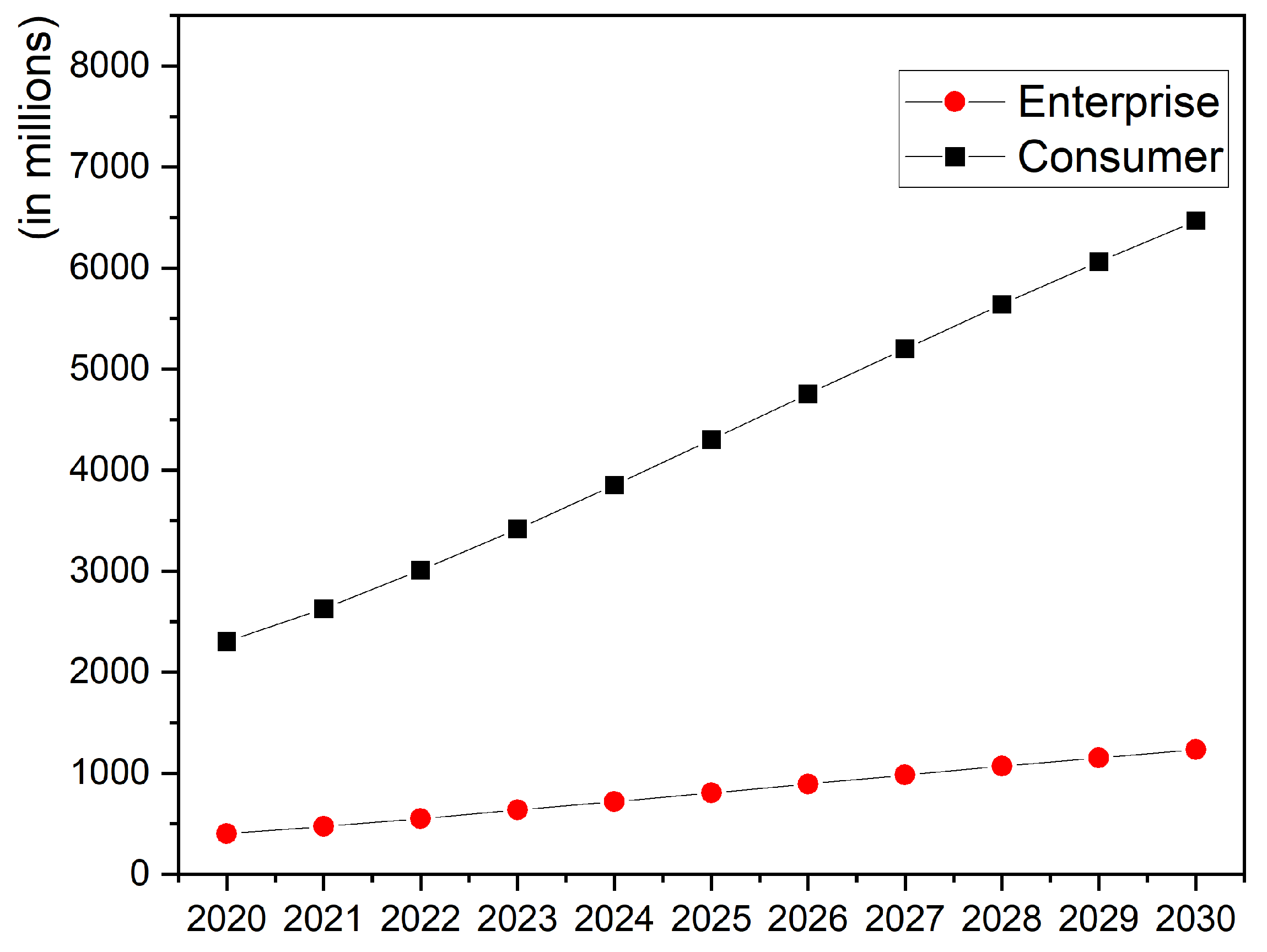
EC is characterized by higher bandwidth, lower latency, and real-time services, but it is still in the development stages and lacks a well-defined standard framework. As illustrated in
Figure 5, the number of edge devices is experiencing rapid growth, creating significant challenges for cloud servers in handling real-time data processing. Statista projects that by 2030, there will be approximately 6.5 billion consumer-focused edge devices, with their average processing speeds advancing exponentially. As a distributed computing technology, EC necessitates well-defined deployment strategies for application workloads on edge nodes. Deployment strategies should be able to answer key questions like, where to place a workload, connection policies, and heterogeneity of nodes [
99]. EC-driven IoT services create management challenges that organizations should overcome to ensure resilient and reliable operations. Equipment suppliers, service providers, and software vendors are required to work collaboratively to offer cohesive interoperability between various network functions and seamless integration from across edge-to-cloud infrastructure. These factors present challenges in deploying, scaling up, and managing the EC paradigm [
100].
Some of the challenges that must be addressed for the widespread adoption of edge computing are discussed below:
Heterogeneity Many hardware devices and communication standards of diverse natures are deployed at edge networks [
101]. EC exhibits heterogeneity across multiple dimensions, including hardware architecture, operating systems, programming languages, accessibility, and the nature of tasks [
102]. First, edge devices are diverse, generating data in various formats. Second, data is transmitted through various network access technologies, including 3G, 4G, 5G, WiFi, WiMAX, and LPWAN technologies like Sigfox [
103]. Third, the heterogeneous edge nodes providing services encompass a variety of devices such as end-user devices, access points, routers, and switches [
53,
96].
Coordination between communication and computing The integration of EC into IoT systems adds significant complexity due to the diverse resource constraints and operational requirements of edge servers and IoT devices [
101]. Mobile edge computing (MEC) is a computing model that extends cloud computing to the network’s edge [
104]. Researchers are exploring the integration of Low Earth Orbit (LEO) satellites with MEC’s for low latency computing offloading services by placing MEC servers on LEO satellites [
105] as well as collaborative MEC’s among connected entities [
106]. Network slicing divides a single physical network into multiple virtualized, independent, and tailored networks, aligning with the distributed models of EC. It is managed through the combined optimization of computing and communication resources in EC environments [
107].
Partitioning and Offloading Tasks The computational tasks are divided into smaller sub-tasks and routed these tasks for processing either locally on the edge device or offloaded to more powerful edge servers or the cloud. The overall system performance is enhanced by partitioning and offloading tasks while optimally balancing computing and communication resources [
108]. Task offloading is a comprehensive process involving application partitioning, decision-making regarding offloading, and executing tasks scattered across the system [
109]. The main challenges in designing partitioning and offloading algorithms involve determining the optimal granularity for partitioning, managing resource limitations, adapting to dynamic environments, and addressing the complexity of offloading within blockchain-enabled communication systems [
108]. In an MEC system with multiple edge nodes (EN) serving multiple users, user association is pivotal in shaping the task partitioning strategy, necessitating the joint optimization of task partitioning and user association [
110].
Security and privacy issues EC is vulnerable to access control, identity authentication, information security, and privacy protection-related threats [
111]. EC characteristics like geographic distribution, heterogeneity, lower latency, lack of standardized protocols, and operating software expand its attack surface [
53,
60,
101]. Conventional security mechanisms such as attribute or group-signature-based access control, homomorphic encryption, and public-key-based authentication require higher computational ability and storage [
112]. Securing edge environments is significantly different from traditional IT security. Implementing security measures on edge devices can potentially hinder their internal operations, impacting the real-time capabilities of edge computing. As a result, a key challenge in edge computing is finding the right balance between minimizing latency and meeting security requirements [
113]. Edge operations are typically time-sensitive, safety-critical, and autonomous. The security models implemented in EC networks must accommodate factors such as longer device lifespans and support for legacy infrastructure. Quick patching may not always be possible, particularly if updates require reboots, which could jeopardize safety [
114].
Monitoring, Accounting, and Billing It is important to continuously monitor the usage of EC resources, account keeping, and billing-related data for better QoS and charging for EC services. Traditional monitoring and accounting methods typically rely on monitoring interfaces on physical nodes, utilizing hardware probes, and correlating data with control plane and management plane information. However, these approaches often neglect the requirements of the distributed nature intrinsic in an edge environment. A sustainable business model for EC services is needed for monitoring, accounting, and billing purposes. Creating a robust business model proves to be quite challenging due to the mobile nature of users and the limited scope of services. The key focus for EC lies in enhancing resource utilization to its fullest extent and effectively monetizing these resources [
115,
116].
3. Security and Privacy Challenges
The first level of data processing is at the edge of EC, making them vulnerable to security attacks and data theft associated with end users. Security measures adopted in IoTs include advanced security algorithms like attribute-based access control, authentication based on group signatures, homomorphic encryption, and techniques based on public-key cryptography. Such algorithms demand sizable computational capabilities and memory availability on the devices where they are deployed [
112]. The cloud can host almost unlimited resources like memories, computing capabilities, power, etc., but lacks real-time user experience due to its physical distance from IoT end devices. Some research efforts have been made in developing and deploying edge-based security architecture designs like firewalls, Packet filters, intrusion detection systems, side-channel signal analysis, authentication and authorization protocols, privacy-preserving mechanisms, real-time traffic monitoring systems (RTMS), and cryptographic schemes. Adversaries use various hardware and software-based techniques to falsify, change, steal, or remove data within edge networks and infect and manipulate edge nodes, devices, or servers found at the edge [
117].
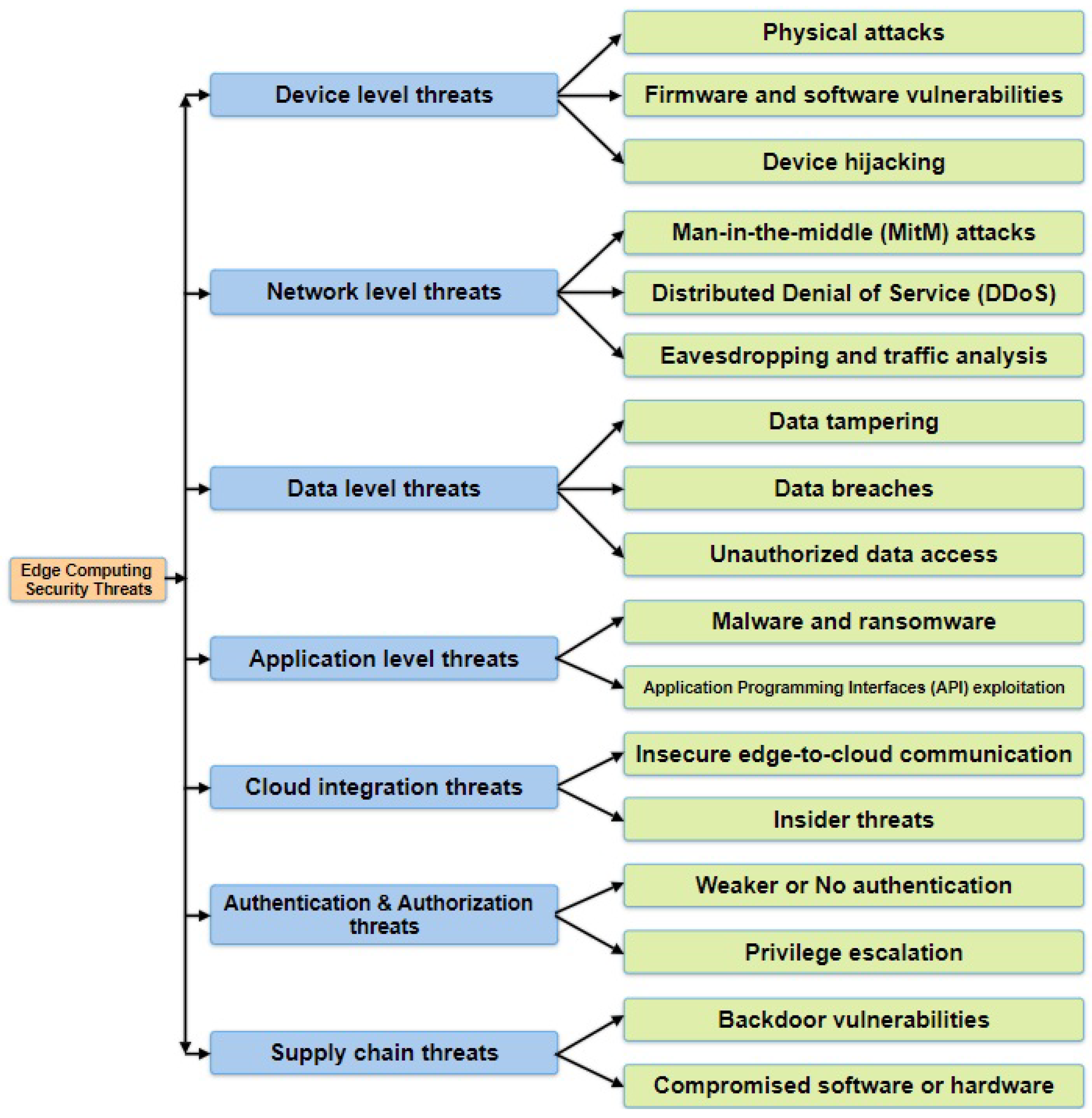
Numerous security threats that can compromise user privacy and data integrity or disrupt critical services exist in the edge device layer, communication layer, and edge computing layer in the EC paradigm of IoT network [
7,
17,
118,
119]. The commonly identified edge/ communication network attacks are eavesdropping, replay attacks, denial-of-service, and jamming [
10,
120]. The vulnerabilities associated with various edge peripherals within the computing layer are mostly DoS and DDoS attacks [
121], whereas [
19] has placed DDoS attacks, side-channel attacks, malware injection attacks, and authentication and authorization attacks under EC infrastructure layer.
However, the research outcomes for edge-based IoT security remain in the early stages of development. [
112,
122]. Initially, EC was assumed to be resilient against cyberattacks since user data no longer needed to travel to cloud servers. Nonetheless, the edge network layer’s dynamic nature makes it susceptible to data security threats, as unified security protocols cannot be uniformly applied. [
123]. Numerous factors contribute to data security and privacy concerns in EC. The vicinity of end users to edge nodes increases the risk of data interception by adversaries. Additionally, the constrained memory and processing capabilities of edge devices, when compared to cloud computing, impede the application of complex encryption techniques, and thus aggravate security challenges. [
124]. It is essential for all stakeholders within an EC ecosystem like service providers, system and application developers, and end users to appreciate data security’s ethical, legal, and financial implications. Another pressing concern is determining the ownership of sensitive data collected at edge nodes. [
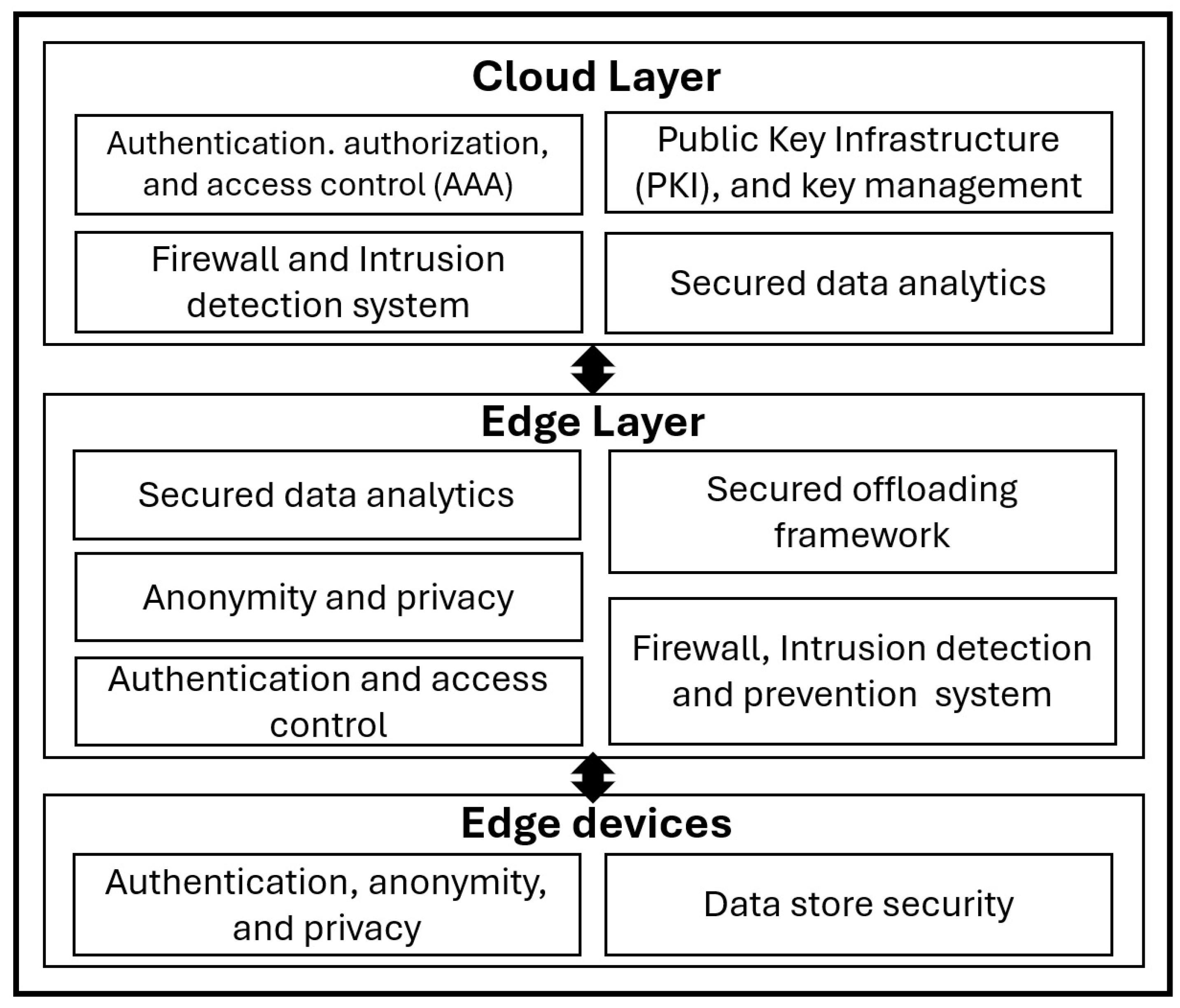
125]. Mukherjee et. al. proposed a layered security framework shown in
Figure 6 implemented on cloud-edge computing architecture. Common security components can exist across multiple layers due to network layer and device requirements, and their purpose and functionality might differ [
126]. Robust cryptographic techniques are needed in the cloud edge collaborative architecture, as a huge amount of data flow occurs through unsecured or least secured public channels with a higher probability of privacy leakage and unauthorized data access [
127].
Implementing a uniform security strategy across all edge nodes is extremely difficult due to their management by various users. Wei Yu et. al. proposed a problem space of EC-based IoT security defined over three distinct classes i.e., transmission, storage, and computation [
6],
Transmission: Jamming attacks, sniffing attacks, worm propagation, distributed denial-of-service (DDoS), and similar assaults can disrupt data links by choking the network or observing the data flow.
Storage: Innumerable sensors and devices produce a gigantic volume of data, which is then stored across various third-party locations. Such arrangement poses issues like, data integrity being seriously challenged due to the distribution of data into many fractions resulting in data packet losses as well as data corruption. Also, adversaries can modify or abuse stored data at third-party locations, leading to data leakage and other privacy issues.
Computation: The relocation of computational tasks from the cloud to edge nodes in EC demands an establishment of trust between edge servers and end devices.
3.1. Classification of Edge Computing Security Threats
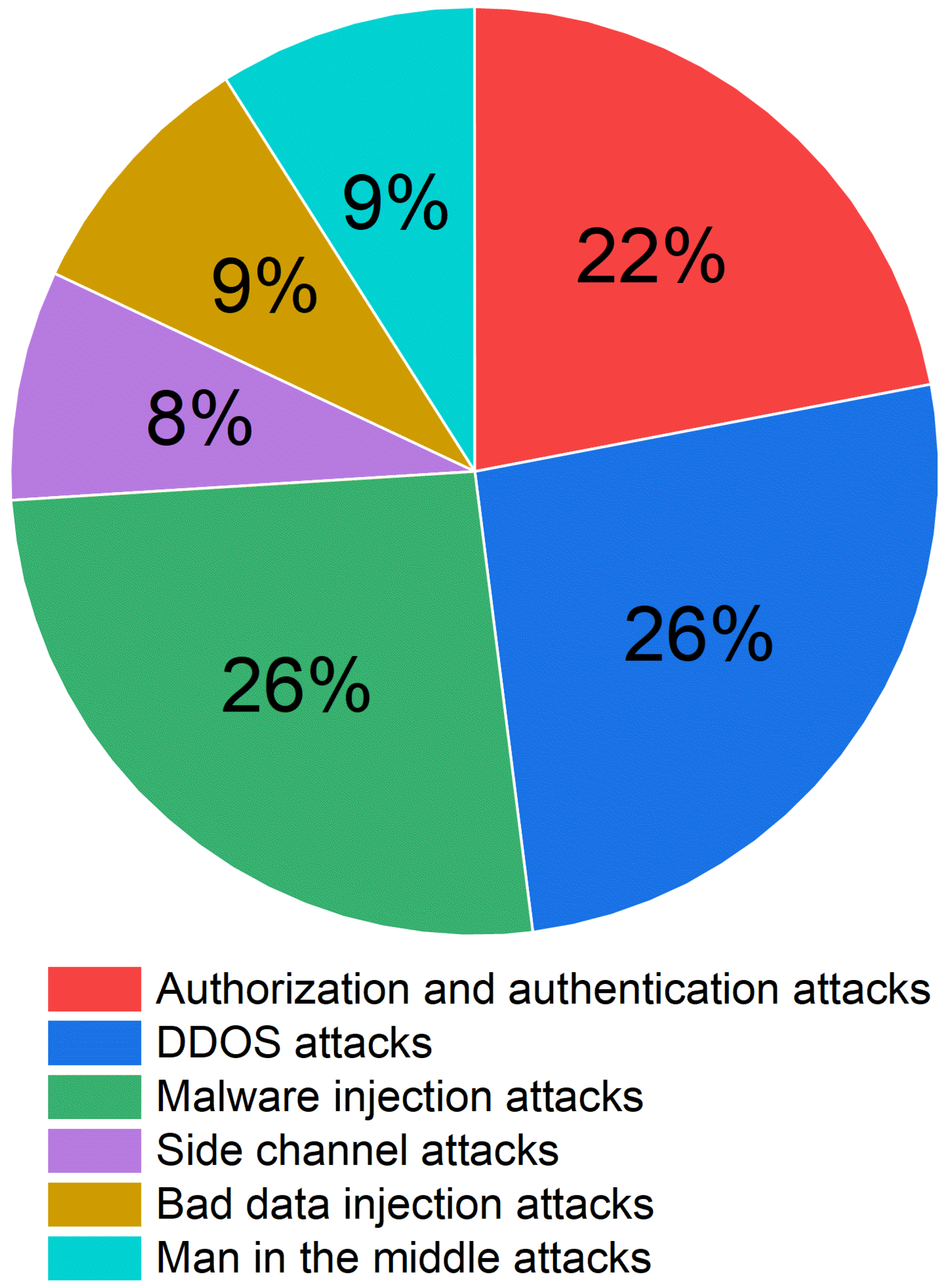
According to Statista’s 2017 report, approximately 159,700 cyber-attacks targeted edge networks and were grouped under six distinct groups: side-channel attacks, malware injection attacks, DDoS attacks, man-in-the-middle attacks, authentication and authorization attacks, and corrupt data injection attacks. The percentage share of each class of attacks is shown in
Figure 7. User privacy and data security are the most important factors from the service provider’s perspective. Sensing network data can extract a lot of private and vulnerable information. For example, access to the data from the electricity and water meters can provide information about the occupancy of a house. There are still open challenges that need to be answered by the EC service providers to protect user-sensitive data.
Figure 8 shows a classification of security and privacy threats, listing their types and origins across various levels and layers within EC networks. All stakeholders in EC, including service providers, system and application developers, and end users, must realize their responsibility against data security threats. Another essential data privacy and security issue is establishing the ownership of collected data at the network edge. A suggested solution is to collect and store data at the edge while leaving ownership to the user. Capable tools and technologies are needed to ensure data privacy and security while meeting EC requirements. Edge nodes are resource-constrained, making deploying advanced data security measures difficult due to their resource-intensive nature. Furthermore, the dynamic nature of the location at the network edge increases vulnerability to security attacks and illegal access to user data. Table ?? summarizes the security and privacy challenges as well as corresponding mitigation techniques against Jamming attacks, distributed denial of service (DDoS) attacks, eavesdropping or sniffing, routing information attacks, physical attacks, and privacy leakage.
Table 3 lists some possible countermeasures against security attacks on edge networks.
3.2. Mitigation Strategies Against EC Security Challenges
The countermeasures against security and privacy challenges in an EC Driven-IoT network are discussed in numerous works of literature and can be summarized and placed under classes as shown in
Table 4.
Table 4.
Strategies against EC security threats [
101].
Table 4.
Strategies against EC security threats [
101].
| Strategy |
Network layer |
Limitations |
| Cryptographic Schemes |
Communication Layer |
Power inefficient, computational ability, storage, etc. |
| Secured data aggregation, deduplication, analysis |
Data layer |
Consume power, render sensitive
data to intruders’ network bandwidth |
| Combined with Blockchain |
Architecture layer |
Complex system more computing capability |
| Intrusion Detection System (IDS) |
Communication Layer |
Resource consumption |
Table 5.
Classification of edge security threats.
Table 5.
Classification of edge security threats.
| Type of threat |
Description |
Mitigation strategies |
| Hardware or software malware |
Unauthorized hardware or software are injected into the edge network that attacks edge servers or devices. Such malware/ trojans interrupt network services and attackers gain control over edge devices and their data. |
Side-channel signal analysis, Trojan activation methods, and circuit modification or replacement are the techniques utilized in hardware security [144]. |
| Physical Tampering & Attacks |
Attackers may exploit physical access to EC nodes/ devices to extract significant and sensitive cryptographic data, manipulate circuits, and alter or corrupt the software and operating systems. |
Techniques such as system analysis and self-destruction are employed to inhibit or alleviate the destructive effects of physical altering and attacks. |
| Routing Information Attacks |
Data throughput, latency, and data paths over a network get affected due to routing attacks. Examples of routing information attacks include black holes, grey holes, wormholes, hello flood, etc. |
Monitoring malicious traffic and detecting policy violations can serve as effective countermeasures. |
| Distributed Denial of Service (DDoS) Attacks |
The continuous transmission of junk data packets toward the target node can exhaust all resources allocated for handling the malicious data packets. This may result in genuine requests getting dropped due to the overload of the target node’s resources. [60]. Three significant DDoS attacks on edge computing devices are outage attacks, sleep deprivation attacks, and battery-draining attacks. |
The Detect-and-filter technique is a tool against flooding attacks. Also, behavior control of devices and policy-based mechanisms within the network can mitigate DDoS attacks. |
| Privacy Leakage |
Privacy Leakage in EC mainly involves three separate classes of privacy concerns i.e., data privacy, location privacy, and identity privacy. Attackers might exploit the location awareness of EC nodes to detect and track device status or to get access to classified data, posing further risks to privacy. |
To address privacy concerns in EC, a privacy-preserving algorithm can be implemented between the cloud server and the edge server or between the end nodes and the edge server. [145]. |
| Eavesdropping or Sniffing |
An intruder listens over communication channels to gain access to private data, like the physical location of specific nodes, access or control information of the EC node like node identification or node configuration, message identities (IDs), timestamps, usernames, and passwords. |
Data encryption technique at edge nodes with asymmetric AES algorithm before the transmission on vulnerable channels, the realization of the connection between the edge nodes and edge server, and authentication service between the transmitting and receiving points could overcome eavesdropping attacks. [10]. |
| Jamming Attacks |
The attacker transmits a wide range of signals with a similar frequency, potentially disrupting network security. Also, it triggers unintentional interference in wireless networks due to induced noise and collisions. |
The significant transmission parameters like the signal strength of data packets at the physical layer and the packet loss ratio at the application layer serve as indicators of potential jamming attacks. [146]. |
| Integrity Attacks Against Machine Learning |
ML techniques utilized in EC-assisted Internet of Things (IoT) are susceptible to two different categories of data security attacks. Causative attacks involve manipulating and injecting misleading training datasets to compromise the training process of ML models and, Exploratory attacks where adversaries exploit vulnerabilities. |
Researchers propose the use of virtual machines (VMs) with boundaries for running ML processes, hence accelerating the testing and deployment of ML models, and systematic study of attacks in simulated environments, or sandboxes [147,148]. |
Cryptographic schemes: The edge layer which includes local data centers, as well as sensing devices, is vulnerable to security threats. These edge devices need cybersecurity solutions within limited storage and computation capabilities. A Zero-Trust approach is recommended for securing data in the EC paradigm with an assumption that all devices have been compromised and all access has to be strictly monitored and authenticated. The standard encryption/decryption methods are memory and computing exhaustive [
128]. ISO/IEC 29192, Lightweight cryptography is a cryptographic algorithm meant for implementation in constrained environments including RFID tags, sensors, contactless smart cards, healthcare devices, etc., for the protection of communication protocols.
-
Secured data aggregation, deduplication, analysis: Data aggregation is a method of clustering the data from various edge nodes by reducing the number of transfers and hence eliminating redundancy. Secure Data Aggregation (SDA) is a highly secure, privacy-preserving, and efficient data compression technique using homomorphic encryption against security attacks such as eavesdropping and forging. The secure deduplication technique removes matching copies of data while supporting data security. It employs Convergent Encryption (CE) for encrypting or decrypting data at the file level, along with a convergent key. [
129]. Load distribution is used in EC for even distribution of computational, network traffic, data storage, and security-related tasks across edge devices, edge servers, and the cloud. Thus, load distribution prevents edge devices or servers from getting overwhelmed by diverse tasks while ensuring key security measures like encryption, intrusion detection, and access control are in place. Neto et. al., estimated an optimal number of edge nodes that can be assigned to a particular edge server using equation
1 and further used it in estimating its security factor [
130].
represents the number of edge devices associated with a particular edge server. Thus, the percentage of devices assigned to edge server i is found by dividing by the total number of devices . is the min-max normalized security Key Performance Indicator (KPI) while regulates priority metrics.
-
Combined with Blockchain: The advantage of implementing blockchain with EC is that it can offer secure data transfer and processing without needing a centralized server by deploying distributed ledger technology. Blockchain governs protocols that collaboratively make judgments involving transaction execution, exercising mechanisms such as voting and consensus algorithms. [
7]. Blockchain is a distributed and secured ledger technology based on the zero-trust architecture, offering a strong shield against data privacy and security threats [
131]. Blockchains are integrated into EC that documents transactions in an increasing chain of blocks [
132,
133]. As shown in
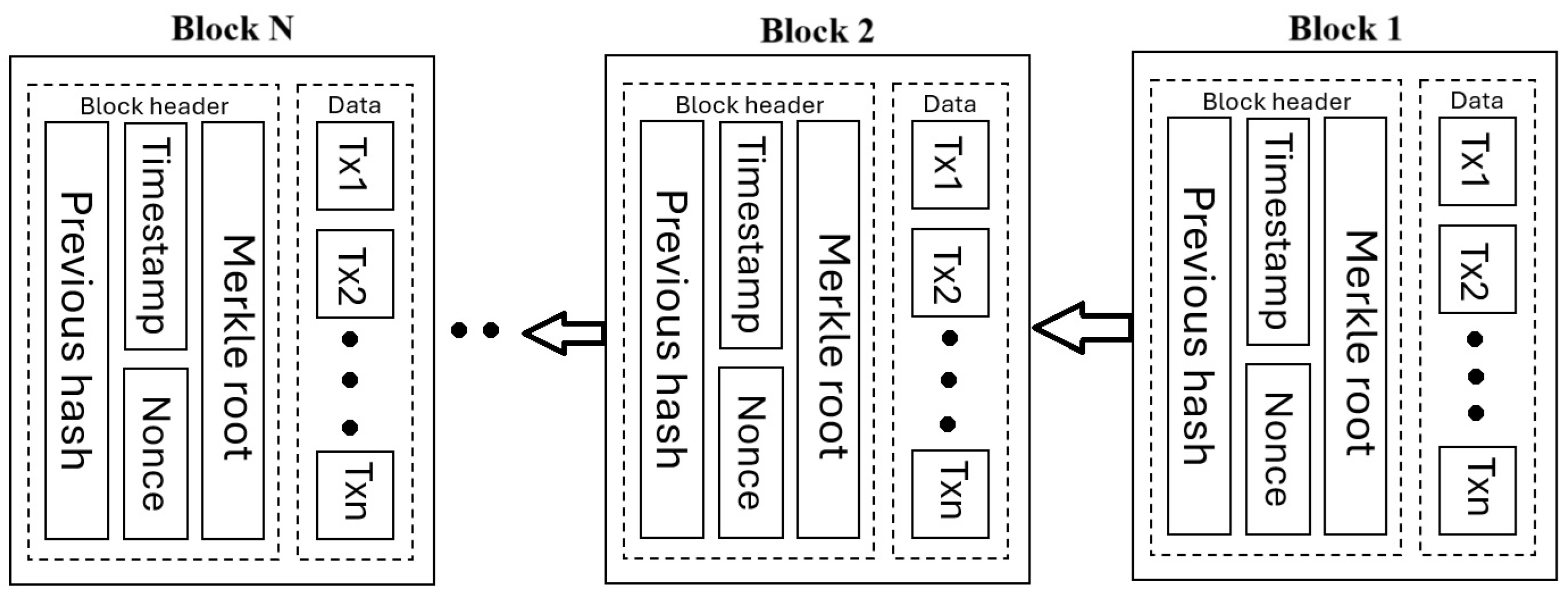
Figure 9, each block is connected to the previous one by referencing its cryptographic hash value, except the first block, the genesis block. Each block contains a significant piece of information like the previous hash, timestamp, counter-like mechanism for every hash estimation called a nonce, Merkle root representing hash of all the transaction hashes, and transactions (Tx) for a specific time [
134]. Consensus algorithms enthuse trust in the network through an agreement among the validated nodes while deciding to generate newer blocks into the blockchain [
33].
Medhane et. al. proposed a blockchain-enabled Platform-as-a-Service (PaaS) model that ensures data integrity and security of mobile users in an IoT environment [
135]. The behavior detection of blockchain nodes using a technique called T2A2vec is carried out by [
136] by extracting node account features, transaction time, transaction type, and transaction amount. T2A2vec technique counters tampering of transaction records and carries out authentication of blockchain nodes. BeCome is a blockchain-enabled computation offloading measure used by [
137] to ensure data integrity in EC. Also, a nondominated sorting genetic algorithm III (NSGA-III), additive weighting (SAW), and multicriteria decision-making (MCDM) are proposed for optimal resource allocation and offloading strategy. Jangirala et. al. have adopted Lightweight Blockchain-enabled RFID-based Authentication Protocol for Supply Chains (LBRAPS) offers secured and real-time authentication through the integration of blockchain, RFID techniques, and 5G MEC [
138]. A decentralized and tamper-proof system using Vickrey-Clarke-Groves (VCG) auction theory is proposed for inducing trust in a collaborative EC while optimizing resource allocation and load balancing [
139]. A blockchain-based secured data aggregation (BSDA) approach is used in mobile data collectors (MDCs) for task management and framing of block generation rules [
31]. Cheng et. al. integrated blockchain, certificateless cryptography, elliptic curve cryptography, and pseudonym-based cryptography methods in a mutual authentication scheme between the edge servers and devices citecheng2021blockchain. Electronic Health Record (EHR) security is ensured by integrating blockchains in EC while storing users’ data locally on edge devices [
140]. A blockchain user or miner estimates a hash value by solving a compute-intensive proof of work (PoW) linking any two immediate blocks after neighboring miners reach a consensus. However, roadblocks are met in resource-limited nodes of the EC network unable to undertake mining and consensus process [
141].
Intrusion Detection System (IDS): In EC networks, intrusion detection systems (IDS) can play a critical role in detecting malicious actions or attacks. IDS investigates data traffic and resource utilization, issues alerts when suspicious behavior is detected. IDS can be characterized into two groups based on their intrusion detection strategies: signature-based and anomaly-based. Signature-based IDS cross-checks monitored events with a database of known intrusion techniques to identify potential threats. In contrast, anomaly-based IDS learn the normal activities of the system and report any abnormalities or inconsistent events [
142]. Spadaccino et. al. and Gyamfi et. al. discuss supervised and unsupervised ML models for IDS, for the detection of anomalies in IoT networks, and deployment challenges of this ML on constrained edge devices [
75,
78]. A signature and anomaly-based Secured Edge Computing Intrusion Detection System (SEC-IDS) framework is proposed by [
77] for improved intrusion detection. A hybrid LDA-LR (Linear Discriminant Analysis-Logistic Regression) edge computing model is proposed in [
143], utilizing machine learning and an IDS.
3.3. AI Role in EC Security
Edge intelligence, or Edge AI, represents blending machine learning (ML) or artificial intelligence (AI) with EC. Edge AI enables both model training and inference directly at the edge through collaboration between edge devices or utilizing local edge servers near the devices [
149]. It is significant for adopting self-learning security solutions at the edges, thus fostering the development of adaptive and autonomous security mechanisms capable of addressing emerging threats in real-time [
150]. AI algorithms can handle highly unpredictable and complex data while ensuring data security against advanced and evolving threats [
151]. Edge intelligence implies a network of interconnected systems and devices conceived for data collection, storage, processing, and analysis near the physical location where the data gets generated. This methodology aims to enhance the quality and speed of data processing while improving data privacy and security by preserving sensitive information nearer to its source [
152]. The convergence of AI and EC is seen as a natural progression due to their clear intersection. EC is centered around coordinating numerous collaborative edge devices and servers, while AI aims to infuse devices with intelligent behavior by learning from data, thereby simulating human-like intelligence.
AI is important in ensuring data security through its advanced data processing and pattern recognition capabilities [
153]. The taxonomy of AI presents numerous techniques like Machine Learning (ML), Deep Learning (DL), Natural Language Processing (NLP), Computer Vision (CV), and Robotics [
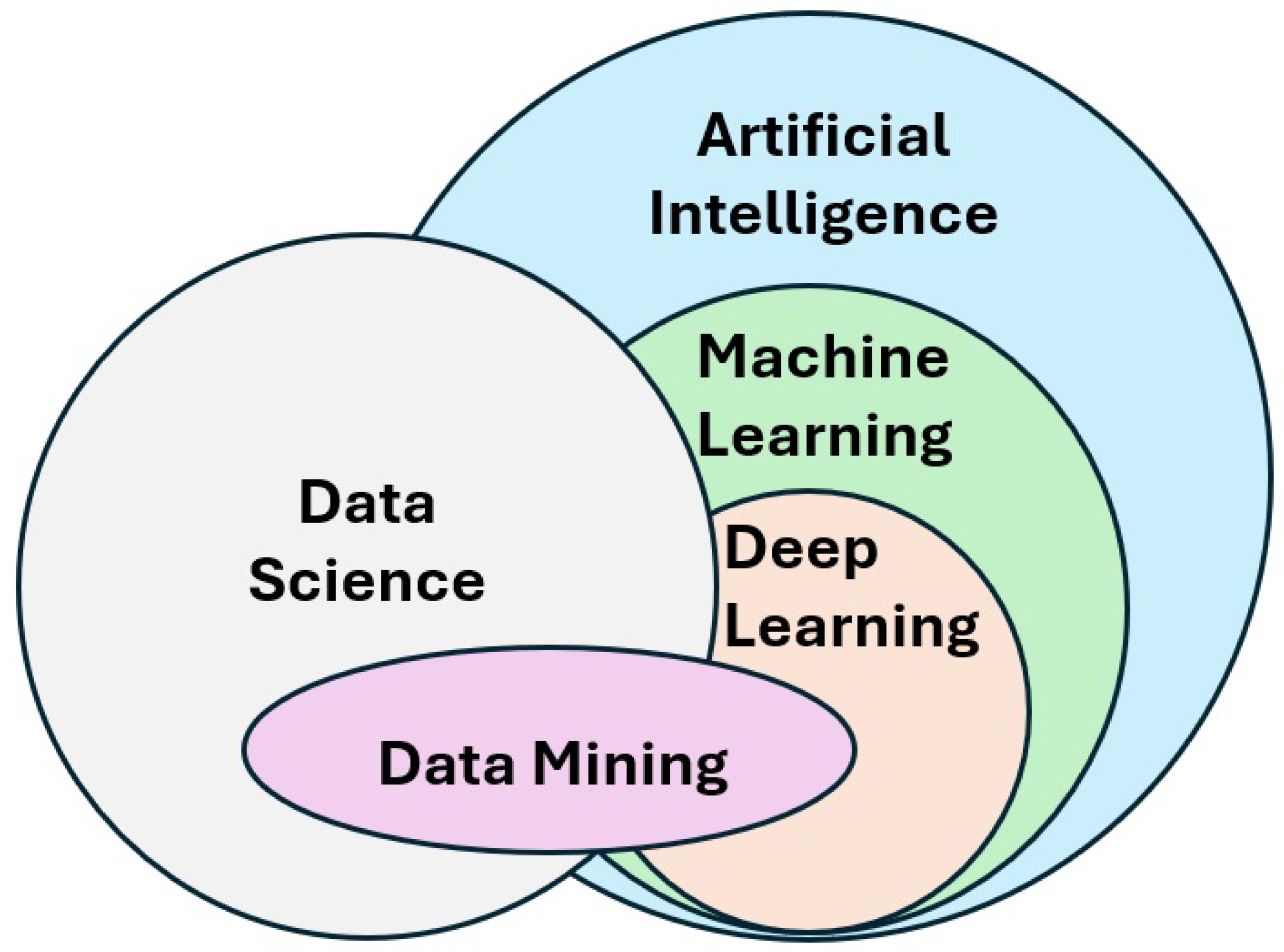
154]. A Venn diagram shown in
Figure 10, demonstrates the relation between artificial intelligence (AI), machine learning, deep learning (DL), data science, and data mining techniques [
155].
Machine learning (ML), a subset of AI, learns from past data, whereas deep learning (DL), a more specific area within ML, processes data using several non-linear transformations. DL, compared to traditional ML methods, has demonstrated a remarkable ability to extract and process data, but it also requires sizable computational resources [
156]. Decentralized deep learning (DDL), like federated learning (FL) and swarm learning, are promising tools in securing the data processing at edge devices [
157]. ML algorithms for data security can broadly be categorized into transaction algorithms and decision algorithms. Transaction algorithms handle data exploration and preprocessing tasks, while decision algorithms are used to manage business decisions [
158]. A major advantage of DL over traditional ML techniques is its ability to automatically extract complex, high-level features from data. DL uses hierarchical neural network models that automatically learn from unstructured data, such as images, sound, text and video [
28]. Wang et. al. have discussed numerous techniques which optimize DL models for EC, such as model pruning, quantization, early exit methods, and approaches in DL tasks distribution between cloud and edge nodes [
107]. Data science covers various aspects of data processing, including collection, storage, analysis, cleaning, visualization, interpretation, decision-making, value creation, and effectively reporting relevant insights. Data mining aims to uncover newer, hidden patterns and knowledge from data [
159].
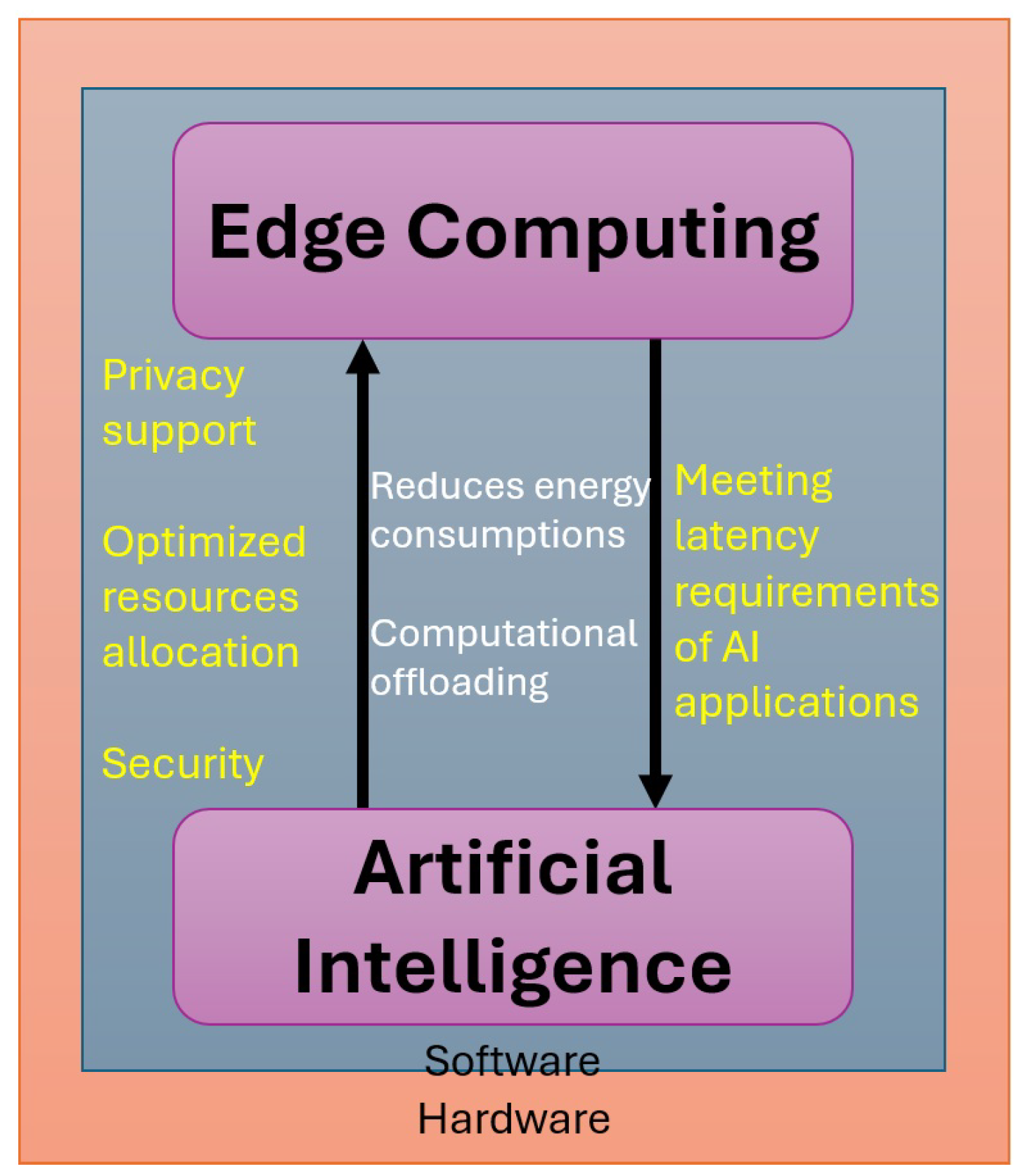
Integrating AI and EC are mutually beneficial to each other as they enable real-time dynamic adjusting and self-optimizing execution of IoT applications. The right-to-left arrow shown in
Figure 11 represents optimization and the development of EC that requires the assistance of AI algorithms (e.g., computation offloading optimization). Alternatively, the left-to-right arrow indicates the need for EC deployment closer to edge devices, hence meeting latency-sensitive requirements of AI applications [
160]. Deng et. al. have placed edge intelligence in two groups, the first group named “AI for Edge” or Intelligence enable EC utilizes AI technology in resource allocation whereas the second group “AI on Edge” or AI models at the Edge carries out training of the models and inference at the edge [
30]. A hierarchical framework proposed in [
161] distributes data fusion and AI processing across three levels i.e., edge nodes, edge servers, and the cloud. Data fusion eliminates data redundancy by combining data from multiple sources thus improving AI’s performance. The authors of [
162], had proposed a hybrid learning framework as current AI-based anomaly detection systems often report false detection. The proposed framework utilizes Stackelberg game model combined with expert-guided ML rules for higher detection accuracy and minimal false detections. Mitigation techniques against data security and privacy threats are grouped into software-based and hardware-based approaches. In software-based security mechanisms, authentication keys are stored in the non-volatile memories of devices. However, innovations in hardware designs and computational abilities have facilitated data adversaries to breach the security measures adopted under software approaches. Alternatively, hardware-based techniques utilize dedicated hardware-integrated circuits or processors to accomplish cryptographic functions and stored access keys. One of the principal challenges with hardware-based security techniques is their susceptibility to man-in-the-middle attacks. In such attacks, hackers can clone the device if the hardware security module gets compromised. To address these limitations, Gassend et al. proposed hardware-based physically unclonable functions (PUFs) as a security primitive [
163]. PUFs leverage intrinsic manufacturing alterations within devices to craft a unique fingerprint of the hardware, rendering it extremely challenging for hackers to reproduce these intrinsic characteristics. However, data acquired from PUFs are vulnerable to environmental factors and the physical conditions of the devices being tested. Subsequently, numerous versions of PUFs have been proposed in the literature to enable device identification and authentication, compliant with a tolerable margin of error [
164].
3.3.1. Machine Learning for Data Security and Privacy
Machine Learning (ML) indicates algorithms and statistical models for carrying out specific tasks without the need for explicit instructions. ML algorithm puts up a mathematical model of user data also known as a "training set" capable of making predictions or decisions. ML can be used to detect suspicious activity by analyzing user behavior to detect patterns that may indicate malicious activity and ensure data security and privacy requirements [
165]. Machine learning (ML) techniques have the potential for enhanced detection of data security and privacy threats while dealing with huge amounts of data coming out from IoT end devices. Rigaki et. al., mention that the training dataset utilized in the development of ML models is itself vulnerable to a possible data security threat [
166]. Usually, the data owners and end users are against the sharing of their sensitive data which becomes a bottleneck in the development of trusted ML models. To circumvent such issues, classification protocols utilize ML classifiers over encrypted data to protect the privacy of end users and service providers.
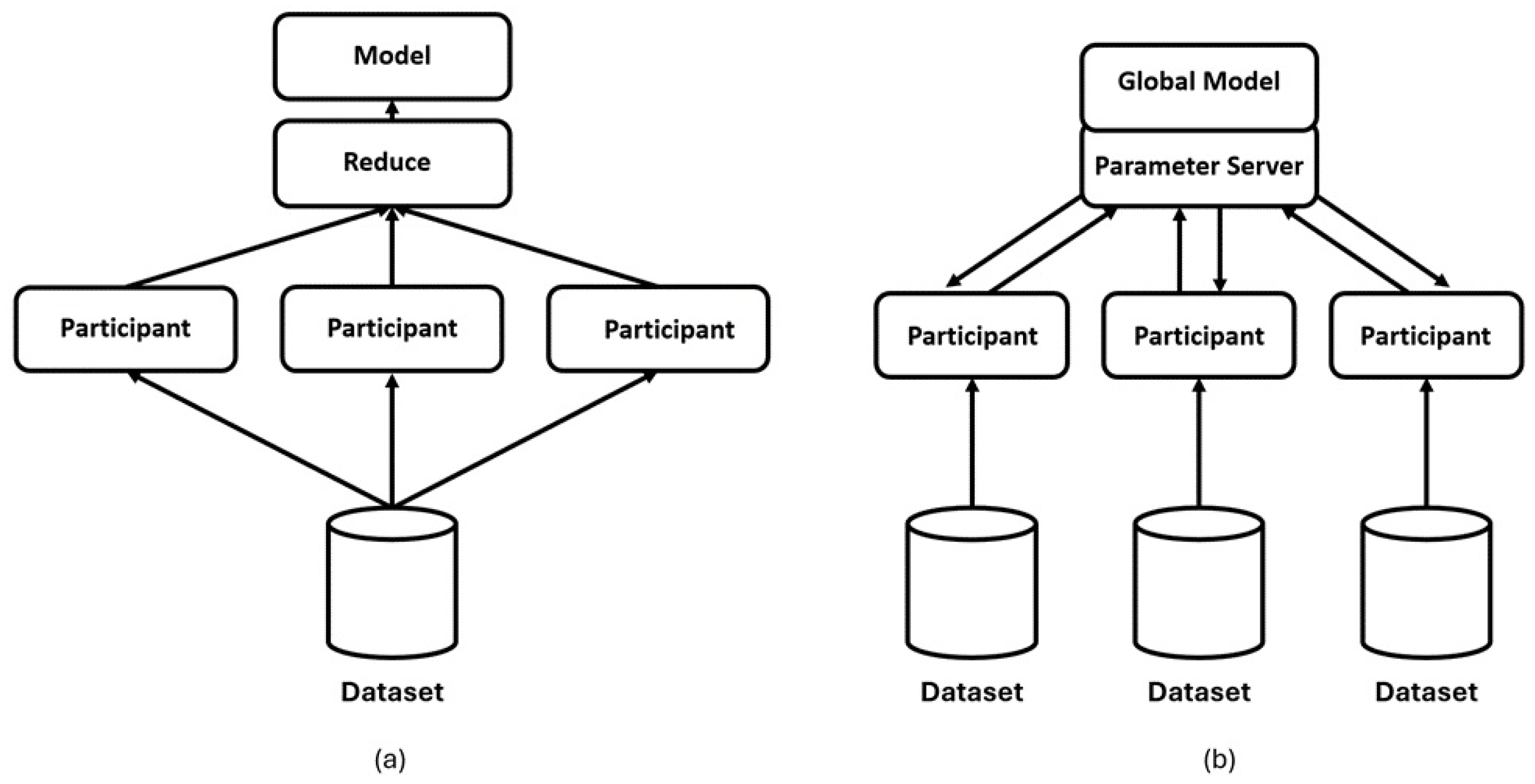
The training approach in centralized ML modeling involves collection as well as storage of data in a central location or server. Additionally, in a centralized approach, the intended model is trained using a complete dataset on a central server. This type of approach is practical when the training entity owns the data or has authorization to use it. As shown in
Figure 12 (a), each participant computes their part of the ML model, and subsequently, a reduced function finalizes the desired model. However, this technique has disadvantages including privacy issues due to the distribution of sensitive data with a central cluster of servers and the training process becoming bottleneck as the dataset grows. Various researchers have proposed an edge-based security system by combining ML with cryptography techniques which monitor and detect suspicious activities on the network and take appropriate countermeasures. The deployed ML models include Support Vector Machine (SVM), K-Nearest Neighbor (KNN), and Long Short-Term Memory (LSTM) [
167,
168].
A huge amount of data is required for the training of AI models and quite often user sensitive data gets exposed in the process. The integration of AI models with differential privacy ensures the accuracy of models with or without the inclusion of user-sensitive data. The traditional ML models might be robust against data attacks but lack feature extraction from the data and fail to detect attacks that have undergone minor modifications [
160]. The study in [
169] reviews ML frameworks like TensorFlow Lite, Apache MXNet, and Core ML, along with hardware platforms such as Nvidia Jetson and Google Edge TPU, focuses on their efficiency and accuracy in data processing within edge environments.
3.3.2. Federated Learning
Google proposed a distributed ML scheme called Federated Learning (FL), which required a local ML model at each data site and later trained a complex ML model on an aggregating centralized server [
170,
171]. FL allows the training of AI models without the need to transmit susceptible data to third-party servers. However, FL networks need a large number of heterogeneous distributed devices which reduces its communication efficiency. To circumvent the problem of channel efficiency, Feng et. al., have proposed a Hierarchical Federated Learning (HFL) framework, with an intermediate model aggregator [
172]. In a typical distributed learning environment shown in
Figure 12 (b), each participant has access to a local dataset, and the parameter server coordinates the participants. The parameter server in the role of an aggregator has no control or access over the data stored on participants. The aggregator server selects participants and aggregates the updated model parameters from the intended participants. Secured model transmission to the server is achieved using cryptographic techniques like Secure Multi-Party Computation (SMC), Differential Privacy (DP), Homomorphic Encryption (HE), etc. among multiple clients without revealing any classified data to each other. Hence, FL has reduced the communication overhead due to the processing of data locally and can offer data privacy and security. Integration of blockchain technology with the FL takes data security to the next higher levels [
173]. Blockchain prevents security and privacy threats with its decentralization, immutability, consensus, and transparency characteristics [
174]. Among the challenges that FL faces, resource constraints stand at the forefront due to limited power computing nodes and slower communication links. Hence, the FL process at the edge node may take longer time than expected as well as energy overheads. Each data source frequently communicates with the central server as the FL model needs to get updated repeatedly and continuously and there is a higher probability that some nodes upload wrong or old model parameters [
175]. A lightweight protocol using secret sharing and a weight masks-based framework is proposed in [
176] which protects gradients during FL against attacks like replay and gradient leakage attacks without compromising the model’s accuracy.
3.3.3. Multi-Access Edge Computing
Cloud computing capabilities are brought to the edge servers or nodes in a Multi-access Edge Computing (MEC) network shown in
Figure 13. MEC exists between the central cloud servers and edge nodes primarily for managing and processing huge amounts of raw data generated from IoT edge devices [
177]. MEC has the potential to improve the quality of service by reducing the end-to-end latency between the edge nodes and data processors as well as improvement in data security and privacy. MEC also fosters data encryption, authentication, and access control at the edge, thus ensuring authorized access and processing of the data. MEC is deployed either by Mobile Network Operators (MNO) or by private cloud service providers closer to end customers and has less latency and higher availability [
178]. Previous research works focused on resource allocation algorithms rather than ensuring the security of MEC servers and end devices. Of late, limitations of mobile devices and support for resource-intensive applications were introduced by Mobile Cloud Computing (MCC). MCC supports extended battery lifetime, unlimited storage on demand, improved processing capability, and self-service provisioning.
Due to the distributed, small-scale MEC infrastructure, there is less concentration of significant data, thus there is less chance of security and privacy-related attacks. Also, there is a possibility that MEC servers are owned privately, which eases the data privacy concerns. For example, the enterprise deployment of MEC skips uploading of users’ classified data to remotely located datacentres, as the enterprise administrator manages the authorization, access control, and classifies different levels of service requests at its discretion without involving external parties [
179]. MEC can introduce newer classes of services, but its unique characteristics open new types of security and privacy challenges. A huge amount of heterogeneous data generated at IoT edge nodes aggregated, stored, transmitted, and utilized in MEC networks may suffer data leakage incidents [
180].
3.3.4. Data Anonymisation Techniques
Data anonymization is a privacy-preserving technique that masks or removes personally identifiable information (PII) from a dataset to protect the privacy of the users. The user identifiers or PII fall under the direct and indirect identifiers type. The attributes that can directly identify a user, such as names, addresses, photos, etc. are direct identifiers, whereas indirect identifiers relate to the attributes that identify users by establishing a relation with other available datasets like age, salary, occupations, etc. The anonymization techniques have an edge over other privacy-enhancing techniques like encryption as they do not require key management and large computational resources. However, data anonymization techniques are an irreversible process that provides privacy but confidentiality or integrity remains unanswered [
181]. In recent times, numerous data anonymization techniques have been proposed, including privacy-preserving mechanisms implemented through data masking, pseudonymization, generalization, perturbation, synthetic, etc.
Data masking: Data masking is a technique of concealing data by creating faux versions of sensitive user data by modifying private information. The process involves modification techniques like shuffling, modest word or character substitution, encryption, or masking data. Common types of data masking are static, dynamic, and on-the-fly data masking.
Pseudonymization: Pseudonymization removes user identifiers from the data set and replaces them with pseudonyms which hides the data source identity. Pseudonymization is defined in the EU-General Data Protection Regulation (GDPR) as “the processing of personal data in such a manner that the personal data can no longer be attributed to a specific data subject without the use of additional information. Such additional information is kept separately and is subject to technical and organizational measures to ensure that the personal data are not attributed to an identified or identifiable natural person.” [
182].
Generalization: It’s a technique of eliminating identifiable aspects of data to fully remove or reduce its identifiability. Generalization picks up a distinguishable identifier and abstracts it into a more general, lesser distinguishable value. Multiple levels of generalization do exist based on the type of data. An example of a generalization technique is bucketing that group records into smaller buckets and minimizes the risk of data security challenges[
183].
Perturbation Methods: It involves mathematical techniques for the protection of user data privacy. A controlled noise or randomness is added to the data while still able to perform data analysis. These data privacy technique is used in various application domains, including ML, statistics, and cryptography. Another method called the differential privacy technique adds a random noise scaled by a privacy parameter to the original data values.
There are certain limitations and disadvantages of data anonymization techniques, as they reduce the granularity and the accuracy of the data. It may damage the relationships between the data points which is critical for artificial intelligence algorithms or any other data science process. Also, data anonymization techniques can be reverse-engineered by gaining access to external or pseudonym databases.
3.3.5. Intrusion Detection System
An Intrusion Detection System (IDS) is a software or hardware-based system, able to detect malicious activity in an IoT network [
184]. Also, IDS can track down any violations in the established network protocols or anomalies. Upon threat detection, IDS has two possible responses [
185],
Issue alerts: This class of responses comes from passive IDS systems that issue security alerts via email or text messages. Also, a notification is issued to the security information and event management (SIEM) system, which helps security teams detect user behavior anomalies and apply AI for threat detection and incident response.
Countermeasure: In this class, Active IDS not only sends alerts, but takes countermeasures like change in access control lists on firewalls to block the suspicious traffic, kill communication-related processes, and redirect traffic to a legitimate part of the network while assessing the threat.
IDS’s normally use one or both of two primary threat detection methods: signature-based or anomaly-based detection, [
186],
Signature Based: In this method, network packets are analyzed for attack signatures i.e., unique characteristics or behaviors linked to specific threats. The network traffic patterns are compared with attack signatures identified in the past and saved in an internal database. If a packet matches one of the stored signatures, the IDS alerts it. However, signature databases must be updated from time to time with new threat patterns to be effective against ever-evolving cyber threats.
Anomaly Based: In this method, the ML approach creates and regularly updates a baseline model of normal network activity. Further, the network activity is compared with the baseline model. It raises alerts if the process uses more bandwidth than usual, or if a device opens a port that is usually closed or has unusual conditions.
Specification Based: It’s a combination of the previous two methods which consumes more energy and resources to identify new attacks.
Physical Unclonable Function (PUF) is an alternative authentication scheme without any cryptographic assets burdening the resource-scarce IoT devices.
4. Hardware Security
Edge devices are highly distributed and exposed to numerous threats, including physical tampering, data breaches, and remote cyberattacks. These devices lack standard security practices, deploy heterogeneous communication technologies, and have scalability issues [
187]. Thus, strong security measures are required at the hardware level to secure sensitive data and to restrict unauthorized access [
188]. Hardware security threats can infiltrate edge devices at any stage of the semiconductor lifecycle, from specification and fabrication to recycling. These threats may arise from unintended design flaws, system side effects, or deliberate malicious modifications during the design process [
189]. Both hardware and software-based mitigation techniques are used to reduce or randomize the vulnerable signal footprints [
190]. A widely used authentication technique for edge devices is challenge-response protocols, mostly based on cryptographic primitives and secret keys. However, implementing these protocols on resource-constrained IoT devices remains a challenge, and the probability of physical threats like direct probing and side-channel attacks is high. Subsequently, a new security primitive, known as PUFs, arrived that offers secured key storage and lightweight authentication [
191].
Hardware attacks can be placed into two distinct categories: non-invasive and invasive attacks, based on the level of physical impact on the device [
192]. Common hardware security protocols utilize encryption techniques like the Advanced Encryption Standard (AES) and Elliptic Curve Cryptography (ECC) that can be placed under private-key encryption, and public-key encryption. A Hardware Trojan (HT) is a malicious alteration during the chip fabrication stage, that might compromise its functionality or spy on encryption keys and forward sensitive chip data to unauthorized devices. HT detection techniques are placed under destructive or non-destructive approaches. Destructive detection includes reverse engineering techniques, such as dismantling IC architecture with Chemical Mechanical Polishing (CMP) and Scanning Electron Microscopy (SEM). However, non-destructive methods analyze IC during the pre-silicon or post-silicon stages. Pre-silicon analysis benchmarks the IC against a fully defined model, while post-silicon analysis includes logic testing and side-channel analysis [
193]. The IC supply chain faces security challenges in addition to HT at various stages, including IP piracy, IC cloning, hardware backdoors, and counterfeit chips. On-chip aging sensors can pick counterfeit chips while split manufacturing mitigates IC overproduction and IP piracy issues [
194].
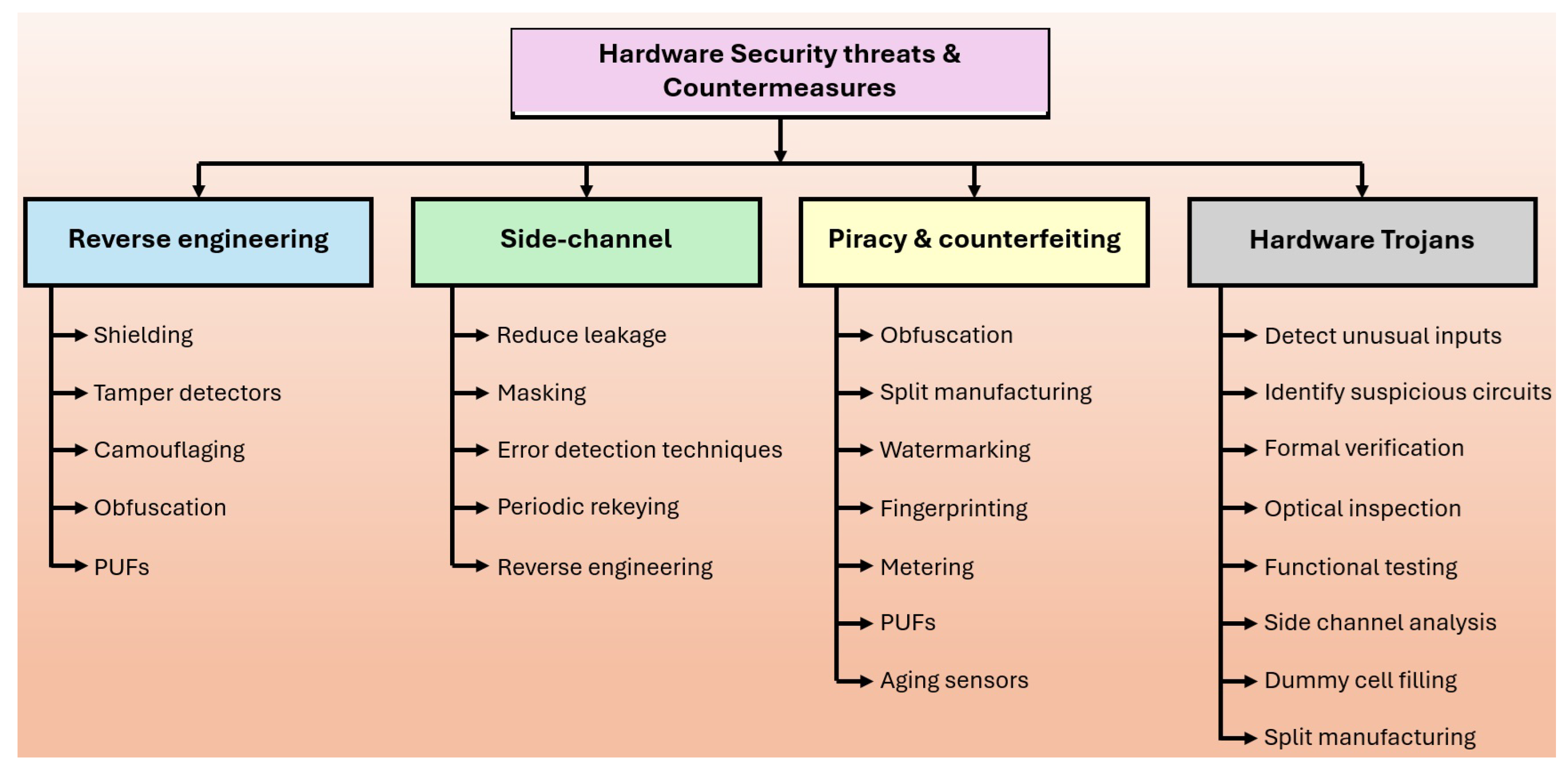
Figure 14 lists a broad classification of hardware security threats and corresponding countermeasures available. Reverse engineering (RE) is analyzing and decomposing edge devices’ design and behavior by extracting confidential data or intellectual property [
195]. RE is accomplished by examining various design formats, such as RTL, netlist, layout (GDS-II), mask, or fabricated ICs [
189]. It is viable to reverse-trace and refabricate the design, which can be further reused or enhanced [
196]. To restrict RE in IC design, hardware obfuscation is the preferred technique that conceals its functionality by placing the logic elements in a random fashion, irregular routing, varying doping concentrations, manipulating dielectric properties, and more [
197]. Camouflaging is another option that enables two functional modules to appear identical at the layout level [
198]. The adversaries do not physically damage the IoT devices in Side-Channel Attacks (SCA) nor intervene with or modify the system’s operation. SCAs passively monitor specific parameters from sensors or networks, like power consumption, the timing of cryptographic operations, electromagnetic emissions, or acoustic signals [
199]. The mitigation techniques against passive SCAs are classified into two groups: hiding and masking. Hiding methods are used for breaking the relation between the processed data and the side-channel leakage, while masking methods disconnect the actual data from the processed data [
200]. Counterfeiting is the duplication of hardware devices by cloning or altering with the designs without the approval from its creator. It may lead to functional failures in systems and processes but also negatively impacts sales and profits of the businesses involved. The broader consequences of piracy acts extend to public health, safety, and security [
201]. The detection of counterfeit devices is difficult as their response against test inputs remain undisputed even in extensive functional testing. However, these counterfeit devices might have hidden malicious characteristics with intentional malfunctions like "back door" for accessing sensitive data [
202]. Hardware metering and auditing is a key defense mechanism against hardware counterfeiting, involving tracking of devices. Certain properties of ICs, like negative temperature bias instability (NBTI), hot carrier injection, and electromigration can be monitored by sensors to identify counterfeit or previously used ICs [
203]. PUFs are becoming an integral part in security applications, including chip identification and authentication, secure key generation for lightweight encryption, prevention of hardware piracy and counterfeiting, hardware metering, and intellectual property protection [
197].
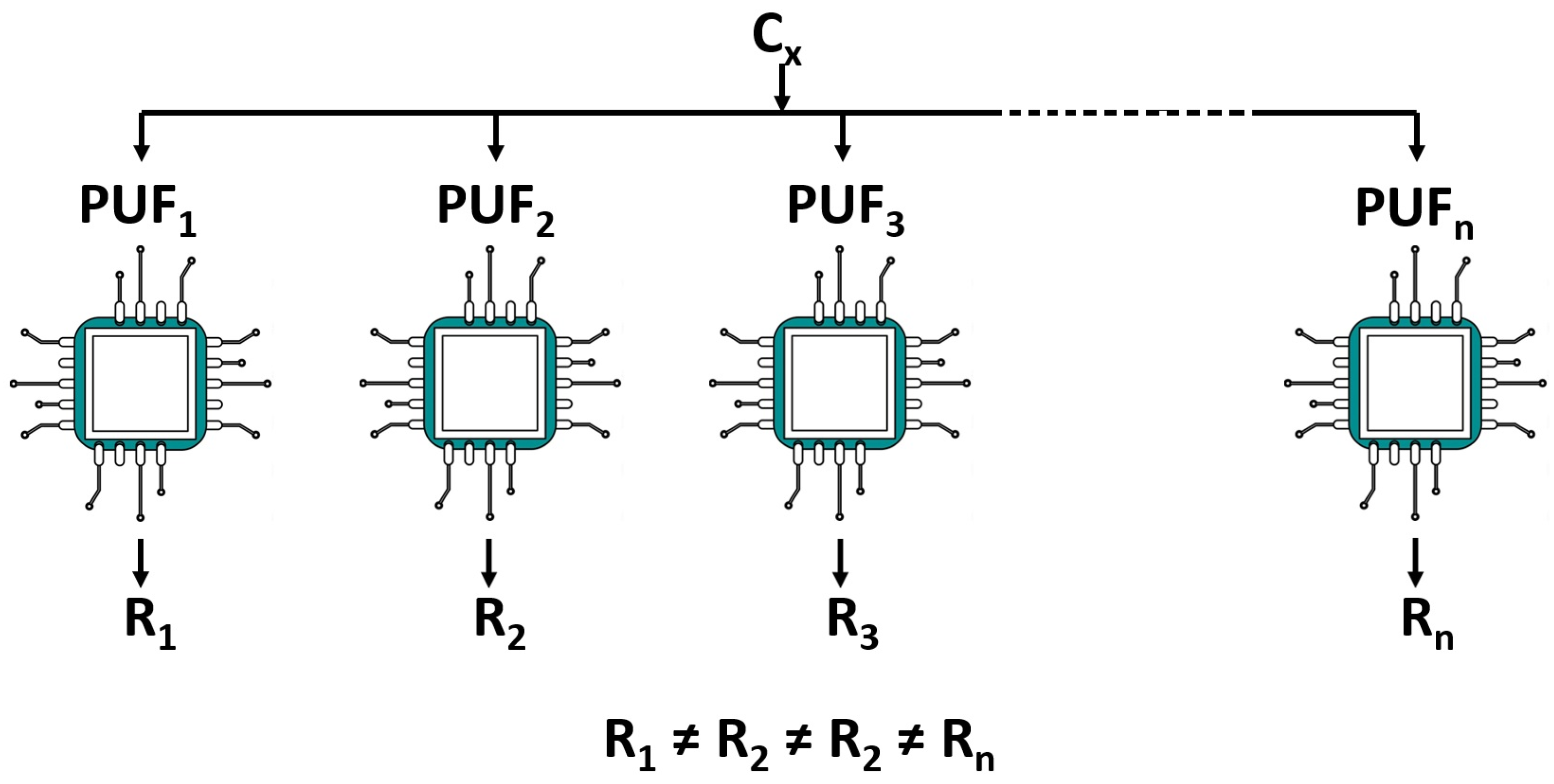
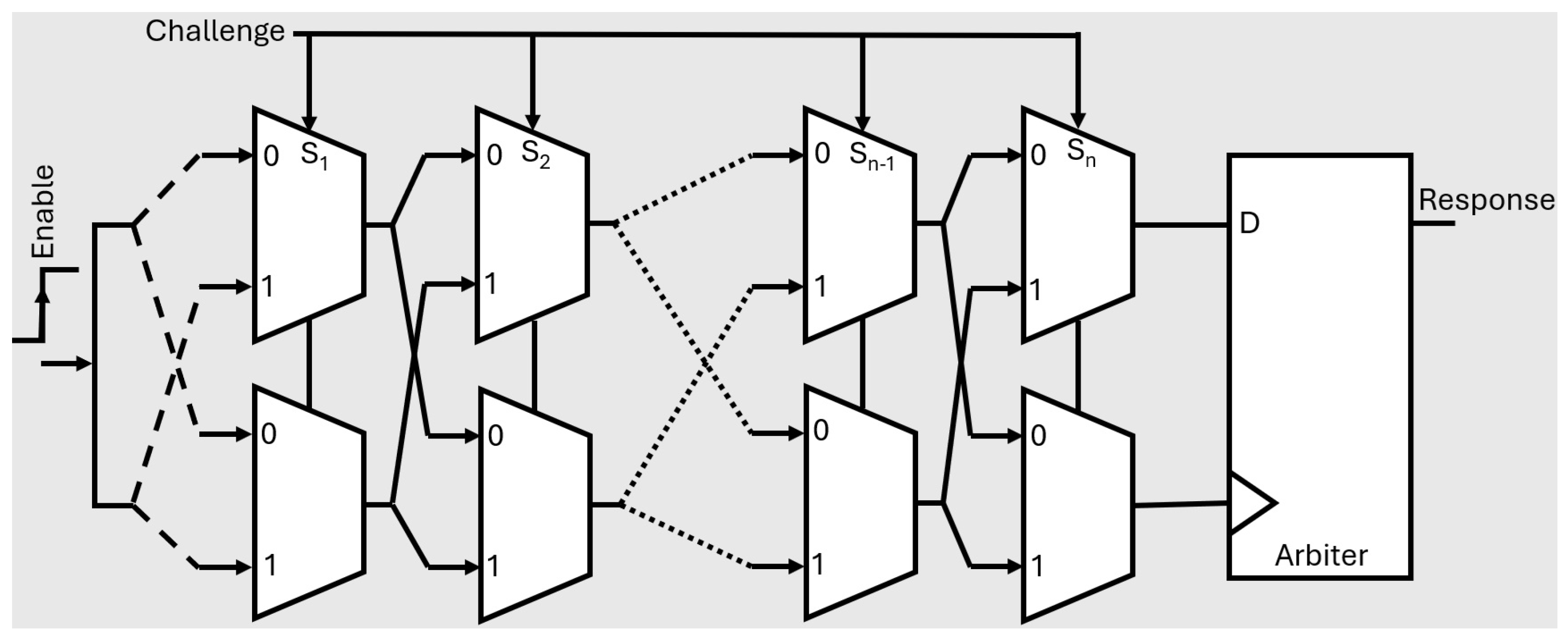
4.1. Physical Unclonable Functions (PUFs)
Authentication, authorization, and privacy are three essential requirements in an IoT network. Physical Unclonable Functions (PUFs) exploit the inherent randomness created during manufacturing to give a unique ‘digital fingerprint’ for authentication and secret key storage. Each chip has its fingerprint like those in humans, which is created during the fabrication processes. PUF circuits are triggered by a sequence of input bits known as challenges (
) and respond with a sequence of output bits called responses (
). No two chips generate identical responses for a common challenge. The combination of an input challenge and its corresponding response is known as a challenge response Pair (CRP) [
206]. The process variations during the manufacturing processes of the PUF circuit have a unique silicon fingerprint. Thus, even common input challenges as shown in
Figure 15 result in unique challenge-response pairs (CRPs) for the edge devices [
207].
PUF carries out an authentication process for an unknown device in two stages i.e., enrollment and verification stages. PUF module receives the challenge bits from the server and the corresponding response bits are stored back into the server by the PUF circuit during the authentication phase. During the verification stage, the server sends the previously stored challenge bits to the IoT device, and the PUF circuit embedded into the device generates response bits. The generated response bits are compared and matched with the CRP look-up table entries for the authentication of the IoT devices. Also, the response bits are used to extract the secret key to ensure confidentiality during data exchanges [
209].
PUFs are classified based on their security capabilities, fabrication methodology, physical characteristics, and delay characteristics. Many researchers have presented a taxonomy of PUF under categories like fabrication process and security as illustrated in
Figure 16. PUFs are categorized into two types, strong PUFs (SPUFs) and weak PUFs (WPUFs), depending on the number of CRPs. The number of CRPs in SPUFs scales exponentially and linearly in WPUFs with increasing PUF cells. WPUFs are used in storing secret keys or serve as a seed in a random sequence generator [
210], while SPUFs can be used for authentication, ID, or key generation [
211]. Arbiter PUFs fall under SPUFs whereas SRAM PUF and butterfly PUF are WPUFs [
212]. However, the responses of SPUFs are inherently correlated and highly susceptible to ML attacks, including modeling techniques like logistic regression (LR), support vector machines (SVM), artificial neural networks (ANN), and ANN-based approximation attacks [
213]. The variations in the manufacturing process result in silicon and non-silicon PUF types. The fundamental physical properties of silicon PUFs give rise to three types: analog electronic PUFs, memory-based PUFs, and delay-based PUFs [
214]. Non-silicon PUFs create unique characteristics by extracting keys from light beams or lasers as well as magnetic field strength and radio frequencies while avoiding the use of electronic signals [
215,
216].
An arbiter PUF is a delay-based strong PUF that belongs to Silicon PUFs.
Figure 17 illustrates an N-stage arbiter PUF made up of n pairs of 2-to-1 multiplexers, with each pair in a stage controlled by identical challenge bits. The output, referred to as the "Response," is determined by the differences in path delays. In a standard N-stage arbiter PUF, a rising edge signal travels through one of the
possible paths, guided by the N-bit "Challenge" inputs. An arbiter generates the final response, typically implemented with a D-latch, which decides the output based on the first signal to arrive [
217,
218]. Optical PUFs have an edge over other PUF types as they are less noise-sensitive and leverage light diffraction complexity, making them stable and difficult to duplicate [
219]. Light acts as the challenge input and generates a unique random pattern as the response [
220]. Normally optical structures are not compatible with solid-state integration. However, a recently proposed CMOS imager PUF uses photodiode responsivity under uniform ambient light and dark current variations to generate unique identifiers for camera authentication [
221].
4.1.1. Application of PUFs
Physical unclonable functions (PUFs) are used for authentication and secret key storage without needing secure EEPROMs and other expensive hardware. Wang et. al. has proposed a Lattice PUF against ML attacks that leverage on Learning With Errors (LWE) cryptographic problem. The designers proposed to build a pseudo-random number generator that integrates a Physically Obfuscated Key (POK) with a LWE decryption function and a linear-feedback shift register (LFSR) [
222]. ML capabilities are utilized in the screening of stable challenges to strong PUFs. Initially, randomly generated challenges tested for stability are chosen as the input and output of the ML model, for extracting stable challenge dataset [
223]. Linjun et al. have proposed a lightweight feedback-based anti-ML-attack Physically Unclonable Function (FLAM-PUF) that integrates an arbiter PUF, a Galois LFSR, and basic logic gates. The design employs a 1-bit feedback mechanism to disrupt the training data, increasing complexity and randomness in the CRP set. This obfuscation reduces the CRP correlation and strengthens resistance to ML attacks by introducing non-linear relationships. The researchers reported a 50% prediction accuracy against various ML algorithms, including Support Vector Machines (SVMs), Logistic Regression, and Deep Neural Networks (DNNs) [
224]. A comparable design approach utilizing an LFSR and an Arbiter PUF (APUF) is introduced in [
225]. A delay difference quantization strategy for Arbiter PUF (DDQ-APUF) is proposed in [
226], which employs multiple configurable delay units (
) along two symmetrical signal transmission paths. The design measures and quantifies the delay difference between these two paths. A configurable delay is introduced along the signal path and gradually increases until the output response of the APUF flips. This quantified delay difference is then used as the PUF response, providing robustness against environmental variations. This design follows the Strict Avalanche Criterion (SAC), ensuring that even a minor alteration in the challenge inputs results in significant and random response changes. Wang et. al. have proposed a dynamically configured hybrid (DCH) PUF by combining the Self-XOR (SX) PUF with Modified Feed-Forward (MFF) PUF. A LFSR is used as a configuration generator, independent of the input challenge. DCH PUF has proven its resilience against diverse ML attacks, including deep neural networks (DNN), logistic regression (LR), and covariance matrix adaptation evolution strategy (CMA-ES) [
227]. Zhou et. al. propose to mitigate ML attacks by reducing linear correlation between the CRPs through a matrix encryption technique called Bagua matrices [
228]. This technique is implemented on numerous PUF architectures, including APUF, XOR-APUF, and Multiplexer PUF (MPUF). The prediction accuracy of ML attacks almost reduces to 50% through matrix encryptions, like random guessing, and subsequently improving data security and privacy [
229]. The method proposed in [
230] combines PUF with Paillier homomorphic encryption or ElGamal encryption to secure data exchanges. Encrypting CRPs during transmission ensures that adversaries cannot intercept or decode sensitive information. Homomorphic encryption enables data verification without decryption, further safeguarding against attacks [
230]. A CMOS-based PUF is proposed for device authentication integrated with Elliptic Curve Cryptography (ECC). Elliptic Curve Digital Signature Algorithm (ECDSA) is used in message signing, that enables devices to authenticate themselves without a need for error correction or storage of redundant data [
231]. Although APUFs are strong, lightweight, and capable of generating a large number of Challenge-Response Pairs (CRPs), they are susceptible to machine learning (ML) attacks. To counter this vulnerability, researchers in [
232] have developed a protocol that authenticates both devices and servers by incorporating an APUF in the device and a PUF model on the server. A zero-transistor interface between the device and server generates "ghost bits" that obscure the challenge bits, making it more difficult for attackers to model the PUF accurately. Another research on cryptography methods for improving Strong PUF security and functionality utilizes Erasable PUFs which delete specific Challenge-Response Pairs (CRPs) after their usage [
233]. A Configurable Dual State (CDS) PUF, featuring a Feedback Obfuscation Mechanism (FOM), is proposed to enhance hardware efficiency and defend against machine learning-based modeling attacks. The CDS PUF is configured as either a Ring Oscillator (RO) PUF or a Transient Effect Ring Oscillator (TERO) PUF based on the parity of the Hamming weight of the challenge bits. The feedback obfuscation mechanism leverages a stable count value from the RO as a dynamic mask to obscure the input challenge, effectively concealing the relationship between CRPs [
234]. A Cyclic Redundancy Check (CRC) PUF alters the seed challenges and transforms the response generation by changing the CRC generator polynomial to mitigate ML-based modeling attacks [
235].
A switched-capacitor PUF (SC-PUF) capable of generating stable cryptographic keys leverages metal blocks and capacitive sensing mechanisms. The proposed mechanism protects against invasive physical attacks like focused ion beam (FIB) and probing methods, with a much lower bit error rate (BER) of
[
236]. A low-cost resistor-capacitor (RC) PUF is proposed to sense voltage differences caused by the charging and discharging of RC circuits. The experimental results with RC-PUFs have shown 49% uniqueness while achieving over 98% reliability [
237]. Cross-PUF attacks exploit power intake measurements from one PUF instance to compromise another, assuming both PUFs originate from the same design file and manufacturing batch. To defend against these attacks, the DRILL method, introduced in [
238], integrates Dual-Rail Logic (DRL) with Random Initialization Logic (RIL). This combination reduces the signal-to-noise ratio (SNR) in the power rails and balances power consumption during the transmission of ‘0’ and ‘1’, making it more difficult for attackers to distinguish between the two states. A fuzzy extraction technique is proposed to authenticate biometric data within a lightweight authentication protocol that utilizes Blockchains and PUFs [
239]. This protocol addresses privacy and security risks, offering protection against threats such as man-in-the-middle attacks, replay attacks, and impersonation attempts. Similarly, a hybrid approach that integrates Blockchain and PUFs is used for device authentication and data integrity that uses PUFs to generate unique device fingerprints [
240].
Applications of PUFs include [
241,
242],
Identification is an act of claiming identity with a set of attributes, both physical and perceptual, that uniquely define a specific entity. Similar to a biometrical identification scheme, PUF response identification can be used to identify the ICs uniquely. A large range of CRPs is stored in the database along with the device ID implemented with the PUF during enrollment. The verifier chooses a CRP from the CRP database. The identification is considered successful if the obtained response and the CRP database output for a specific input are identical.
Authentication is an act of identity confirmation based on presented attributes. PUFs generate a secure key from intrinsic and inherent entropies created due to variations in the fabricating process. No standard non-volatile storage is needed as randomness is built-in inside a chip and assures extra protection against the side channel and probing attacks.
SRAM PUFs, RO PUFs, etc., can generate random numbers with slight modifications in their architecture and find their application in real, or cryptographically secure, random number generators.
Potential vulnerabilities like copying or reverse engineering can destroy devices’ intrinsic and inherent characteristics and thus modify their output. PUFs are suitable for the generation of secrets in cryptography as they are not kept on the hardware and get generated dynamically at device reset.
4.1.2. PUF Performance Indicators
The quality of a PUF is evaluated by metrics like uniqueness, reliability, randomness, correctness, strict avalanche condition (SAC), etc. that verify its applicability to a specific application. PUF metrics are measured by collecting response bits against a set of challenges to the PUF. A specific application has unique sets of requirements; hence all metrics are not equally important [
243,
244].
Uniqueness: It is a PUF characteristic representing its ability to generate a unique response against a similar set of challenges subjected to each die in a lot [
245]. Uniqueness is the average inter-chip Hamming Distance (HD) of the responses collected from a group of chips. The uniqueness value of an ideal PUF is about 50%, meaning half of the bits in the responses of the PUFs should be different [
243]. For example, in an FPGA-based k n-bit, PUF responses:
,
, · · ·,
, the average Hamming distance is given by Eqn. 3 [
82],
Reliability: The PUF, and CRP under noisy and variable environmental conditions are measured by their reliability i.e., the PUF outputs the same response under variable operating conditions. However, numerous environmental conditions like temperature, voltage, and aging of the devices, are responsible for variations in the PUF signatures. The ideal value for reliability is 100% and it can be estimated using eqn. 3.
where x represents the times of sampling; n is the number of bits of a signature generated by a PUF;
is the
sampling of
.
Randomness: It is a measure of the PUF’s ability to generate 0 or 1 in its response bits with equal probabilities. The randomness of a PUF should be 100% in an ideal case. PUF-based authentication protocols rely heavily on random physical imperfections that occur during the semiconductor manufacturing process, thus creating static randomness. However, the identification (ID) extraction from the PUF gets corrupted due to dynamic randomness sources like noise which reduces the PUF’s reliability [
246].
For
challenges, the probabilities to obtain an ID at 0 and 1 can be given as,
where
is the pdf of
For a variance of
, the randomness expression eqn.
8 is given by [
247],
Correctness, Bit Aliasing, Uniformity, and Steadiness are additional PUF performance metrics discussed in the literature [
82,
243,
245].
Table 6, presents a comparison of PUFs performance metrics mentioned in the previous section. It is inferred from the table that the Uniqueness and Uniformity performance metrics of Lattice PUF remain closer to ideal values whereas RC-PUF is the lowest performing one.
4.1.3. PUFs as a Root of Trust
A layered defense model as shown in
Figure 18, is preferred for a secure system with outermost layers managing the regular operations of the device and acting as protection barriers for inner layers. This design approach minimizes the attack surface area and makes inner layers easier to secure because they have fewer, highly controlled tasks. The trust-validation sequence continues moving towards inner layers up to the system core, known as the Root of Trust (RoT) [
248]. Edge devices leverage RoTs in establishing a protected environment for cryptographic processes needed for data encryption and authenticating devices connected to backend systems [
249]. RoT applies various code validation mechanisms before executing the codes on secured CPUs and shields against physical attacks to a certain extent. Thus, a Chain of Trust is established when each component in this chain trusts the codes it runs, as they get validated by the previous link, creating an unbroken line of trust back to the root of trust [
250,
251]. The hardware RoT secures EC operations, by providing the cryptographic keys in a booting process. Hardware-based RoT is typically a small, dedicated chip embedded within an IoT device leveraging upon intrinsic hardware characteristics [
252]. PUFs are ideal for hardware-based RoT that hosts cryptographic functions, such as private and public key encryption [
253]. The unique keys generated from the edge device’s PUF and the secure boot process ensure that only authorized firmware or updates are loaded, preventing trojan or malware attacks.
Rojas et al. proposed a hardware Root-of-Trust (RoT) architecture utilizing a Xilinx Zynq-7000 SoC FPGA and integrating various cryptographic components. These components include PUFs for device authentication, the Advanced Encryption Standard (AES) for data encryption, Secure Hash Algorithms (SHA-2 and SHA-3) for ensuring data integrity, and the Edwards-curve Digital Signature Algorithm (EdDSA) for digital signature verification [
254]. A hardware RoT is proposed in [
255] leveraging Quantum Tunneling PUFs for the digital identification of ICs. In contrast to SRAM PUFs, Quantum Tunneling PUFs operate without the need for error correction. The software-based PUF (SW-PUF) combines physical chip variations with delays in software instructions to generate unique IDs within a secure Root of Trust (RoT). This approach supports secure boot and remote attestation, ensuring that only authenticated, tamper-free software is executed [
256]. A secured IoT architecture proposed in [
257] combines PUF with Trusted Platform Module (TPM), and Tangle Distributed Ledger Technology (DLT acts as a RoT, establishing a unique digital identity for each device. The proposed architecture implements a Security-by-Design (SbD) approach at the hardware level strengthens attack resistance and defends device and data integrity. Quantum channels are vulnerable to diverse noise sources, which include environmental interactions and eavesdropping attempts. A key reconciliation protocol is proposed in [
258], allowing transmission of bits stream through insecure and noisy quantum channels. Also, the researchers claim that the proposed protocol can reconcile two PUF responses obtained from the same challenge but at a different time. Also, minor noise levels in the PUF responses are mitigated through the application of fuzzy extractor, designed to produce stable cryptographic keys from marginally erratic PUF responses [
259].
4.1.4. Integration of FPGAs Based PUFs with Edge AI
Artificial Intelligence (AI) assisted data analytics at the edge, allowing for improved interpretation of raw and unstructured data from the physical world. AI in the edge has the potential to automate complex and advanced tasks while preventing user-sensitive transmitted over the network and into data centers at the same time. Edge AI models human reasoning, thus enabling machines to sense, comprehend, perform intelligent detection, and transmit results to the cloud for long-term storage or big-data processing. It is capable of recognizing and fighting back against cyberattacks as well as other cyber threats based on the continuous input of data, identifying patterns, and backtracking the attacks. Data privacy and security breaches need to be seriously taken as they may cause business interruptions, revenue losses, and panic among the public [
260]. The human brain comprises nearly 100 billion neurons and over 100 trillion connections are established to form a network of neurons which in turn significantly influences the brain’s capabilities. The interconnectivity within an FPGA resembles the neural wiring of the human brain and its programmable-logic fabric offers the flexibility of the brain [
261].
The dynamically reconfigurable as well as customizable hardware architecture of Field Programmable Gate Arrays (FPGAs) has offered a promising solution in accelerating compute-intensive workloads [
39]. FPGA-based edge network accelerators offload intelligence, data processing, analytics, and communication capabilities from the cloud to where the data originates [
262]. Cloud computing provides the infrastructure needed for securing users’ data as well as maintaining their integrity and privacy. However, there is no foolproof technique yet that guarantees data protection nor a processor that can isolate the execution of users’ applications from data theft. FPGAs on the other are capable of providing stronger security guarantees as there is no need to involve vulnerable operating systems, drivers, or compilers, nor any other system software [
263].
The possibility of incorporating general-purpose processors such as soft cores on FPGAs makes these reconfigurable devices suitable for IoT applications as they can provide solutions with enhanced security, reduced size, energy consumption, and cost [
264]. Silicon chip fabricators and designers have integrated FPGA and ARM processor cores for efficient edge AI processing. Also, the benefits of shorter development time make an FPGA-based solution the ideal choice for an intelligent edge device [
265]. Integrated chip manufacturers mostly outsource their operations where intellectual property (IP) theft poses serious concerns. In contrast, FPGA designers do not configure them with sensitive IPs unless the delivery of the product is completed [
266]. Cybercriminals can replicate FPGA applications by intercepting their programming bitstream or reading the internal memory. Modern FPGAs have started using advanced encryption key standard (AES) with the battery-backed SRAM 256-bit or 384-bit security key, AES with the eFUSE key, on-chip bitstream keyed-Hash Message Authentication Code (HMAC) algorithm, bitstream authentication, etc. can mitigate the risks, protect intellectual property, and improve the overall safety of your FPGA devices.
FPGA-based edge devices exploit AI and ML capabilities for the processing of sensed data and subsequently reduce network bandwidth requirements and dependence on cloud processing. Also, vendors are providing IP cores like OpenVINO, Vitis-AI, etc., to leverage FPGA interfaces for the optimization and deployment of deep learning (DL) models [
267]. Open Visual Inference and Neural Network Optimization (OpenVINO) is an open-source toolkit from Intel, that facilitates quicker inference of deep learning models on hardware accelerators and easy heterogeneous execution across numerous hardware platforms. Deployment of the OpenVINO toolkit and the Intel FPGA AI Suite in the development of DL-enhanced embedded systems on multiple FPGA-accelerated servers is shown in
Figure 19. The OpenVINO toolkit comprises tools and libraries that utilize techniques like pruning, quantization, etc. for the optimization of neural networks. The basic workflow of Intel Distribution of the OpenVINO toolkit is:
Model Optimizer converts models from various frameworks like Caffe, TensorFlow, Open Neural Network Exchange (ONNX), and Kaldi to intermediate representation format for faster inference.
Inference Engine reads the IR format and supports heterogeneous execution across different hardware architectures such as CPU, GPU, Integrated GPU, etc.
Model Zoo is a common interface for heterogeneous hardware that contains examples to get started with OpenVINO quickly.
Xilinx Vitis is a unified software platform that includes optimized IP, tooling, and libraries to grant users access to AI inference acceleration through adaptable hardware. It consists of a rich set of AI models, optimized deep learning processor unit (DPU) cores, tools, libraries, and example designs for AI at the edge and in the data center. It provides a unified programming model for accelerating Edge, Cloud, and Hybrid computing applications. Vitis AI integrated development environment is presented in
Figure 20, with the target platform i.e., FPGAs as the base layer. The Xilinx runtime library in the second layer controls the data movement across domains. Also, compilers are used in the layer for mapping the AI model’s optimal instruction set and dataflow model as well as carrying out optimization tasks. There are more than 400 optimized and open-source applications across eight Vitis libraries that are defined in the third layer and offer out-of-the-box acceleration with minimal to zero code changes to your existing applications [
268].
Author Contributions
Conceptualization, A.M.S, M.R.I. and M.H.H; methodology, A.M.S., M.H.H, M.R.I., and A.K.; formal analysis, A.M.S, S.A.Z., and M.H.H; investigation, A.M.S, S.A.Z., and A.R.B.N; resources, A.M.S, M.R.I., and A.K.; data curation, A.M.S., and M.H.H.; writing—original draft preparation, A.M.S, and M.H.H.; writing—review and editing, A.M.S, M.R.I., M.H.H., A.K., S.A.Z., and A.R.B.N; visualization, A.M.S. and M.H.H; supervision, M.R.I. and M.H.H., and A.K.; project administration, A.M.S; funding acquisition, A.M.S., and A.K. All authors have read and agreed to the published version of the manuscript.