Submitted:
06 February 2025
Posted:
06 February 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
- (1)
- We have contrived an innovative sharding architecture that can function in parallel and handle transactions within and across shards effectively.
- (2)
- We have, for the first time, proposed a sharding method based on the SSCFLP model. In contrast to the currently prevalent random sharding techniques, our FLPShard method is capable of rationally assigning nodes to each shard in accordance with multiple informational dimensions, including but not limited to node distance, latency between nodes, and node bandwidth. This not only heightens the consensus efficiency within the shard but also markedly augments the overall throughput of the system.
- (3)
- We have actualized the prototype algorithm of this sharding scheme and examined its feasibility via a simulator. Through in-depth analysis and experimental corroboration, we have ascertained that the FLPShard scheme exhibits significant advantages over the random sharding scheme with regard to transaction confirmation latency and system throughput.
2. Related Work
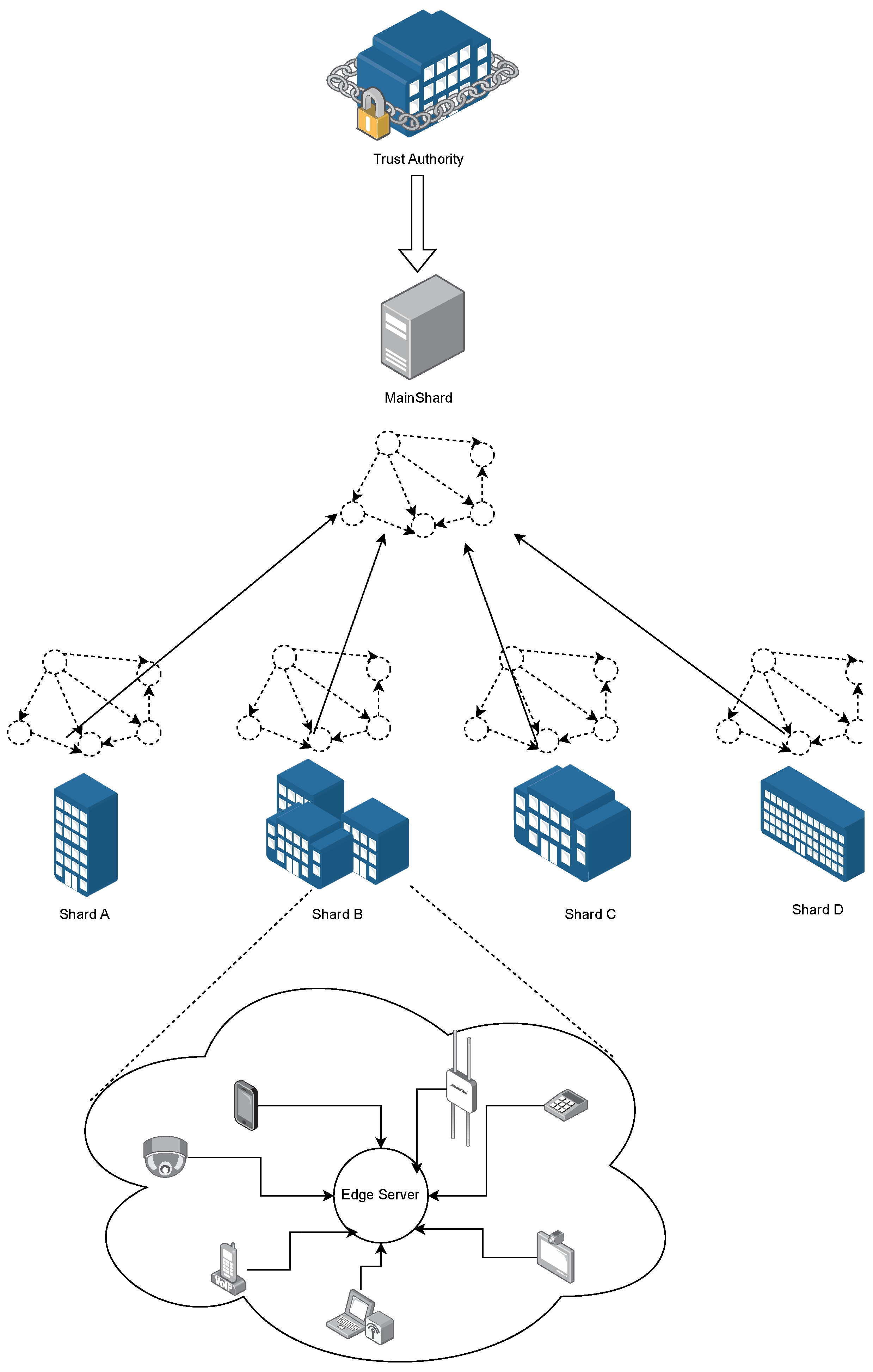
3. Overview of System Model
- (1)
- Industrial devices: The Industrial Internet encompasses a multitude of devices, including cameras, sensors, and computers. These devices typically exhibit limited storage capacity and relatively feeble computing power, rendering them incapable of undertaking the responsibilities of blockchain nodes. In our design, the primary function of industrial devices is to supply data to edge servers.
- (2)
- Edge servers: In the context of FLPSHARD, there exist multiple edge servers, each denoted as . Edge servers are tasked with gathering data from industrial devices and collating it.
- (3)
- Main chain nodes: In FLPSHARD, the nodes of the main blockchain, known as main chain nodes, are assembled from the most potent servers. Their role is to maintain the global ledger as full nodes and store information such as the geographical location, network connectivity, number of shards, and shard number of each node. They also perform sharding on the business chain network and oversee cross-shard transactions and final consensus.
- (4)
- Business chain nodes: These nodes handle intra-shard transactions. The business blockchain is segmented into several shards by the main chain and dynamically adjusts the shard size and number when requisite.
4. Blockchain Sharding Scheme Based on the Improved SSCFLP Model
4.1. Modification of SSCFLP
| No | Symbols | Notations |
|---|---|---|
| 1 | S | All nodes set |
| 2 | Leader node candidates | |
| 3 | Set of ordinary node candidates | |
| 4 | c | Communication cost between nodes |
| 5 | d | Unit or node occupancy capacity |
| 6 | f | Cost for a new shard |
| 7 | s | Capacity of shard |
| 8 | H | Values exceeding the shard capacity limit |
| 9 | L | Value below the lower limit of shard capacity |
| 10 | Q | Number of shards affected in each iteration |
4.2. Sharding Construction
| Algorithm 1: Shards construction. |
| Require: member nodes and , nodes set S , max loop number: |
| Ensure: shards set D |
| 1: |
| 2: for 0 < l < do |
| 3: Take a neighborhood from the current set of nodes and construct a new set of nodes. |
| 4: Obtain the corresponding sharding scheme for the current set of nodes. |
| 5: if then |
| 6: |
| 7: end if |
| 8: end for |
| 9. return D |
4.3. Dynamic Expansion of the Network
| Algorithm 2: Dynamic Expansion of the Network. |
|
4.4. Dynamic Allocation Method
| Algorithm 3: Dynamic Allocation Method. |
|
5. Performance Evaluation
5.1. Theoretical Analysis
5.2. Experimental Environment Design
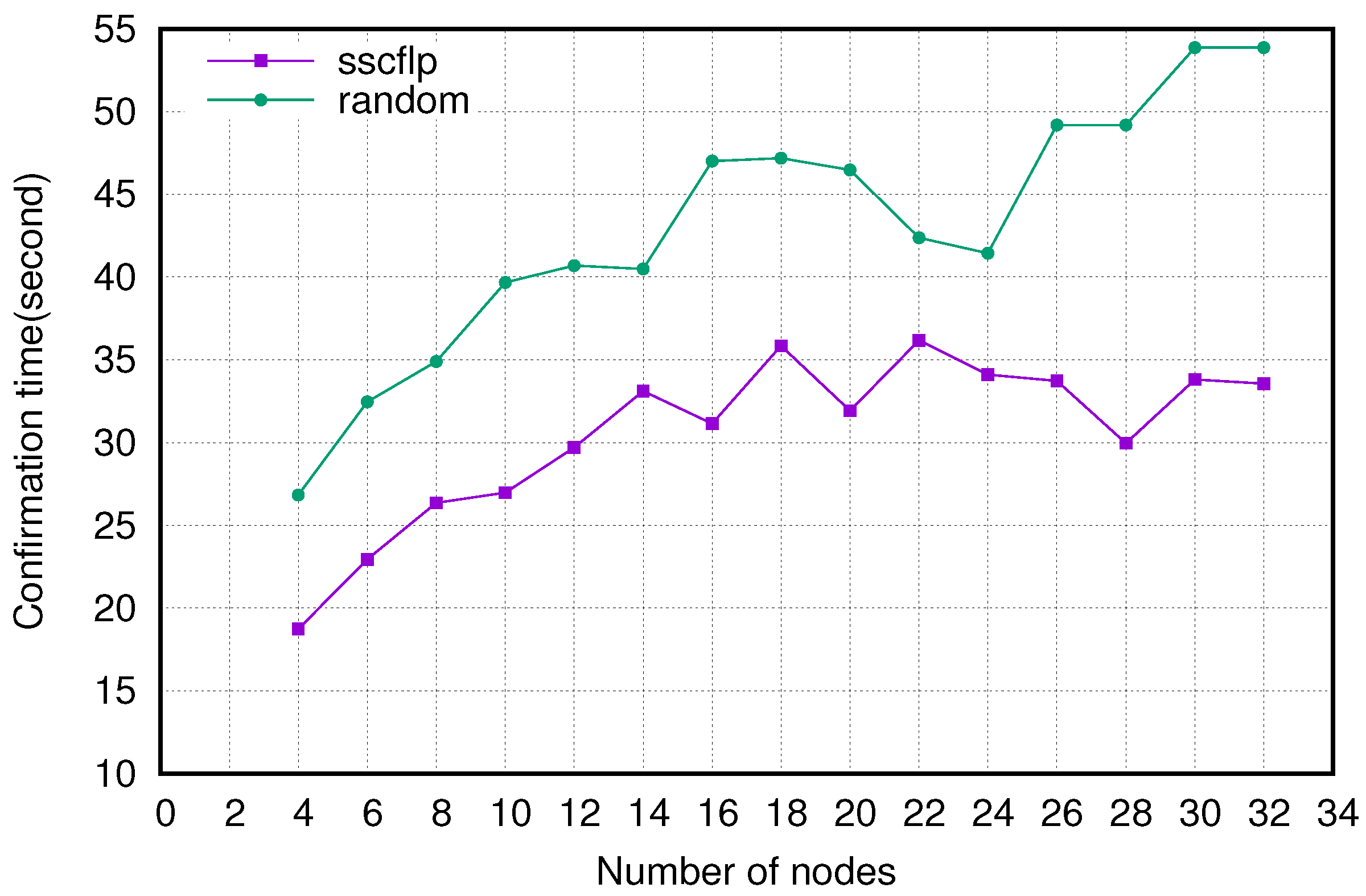
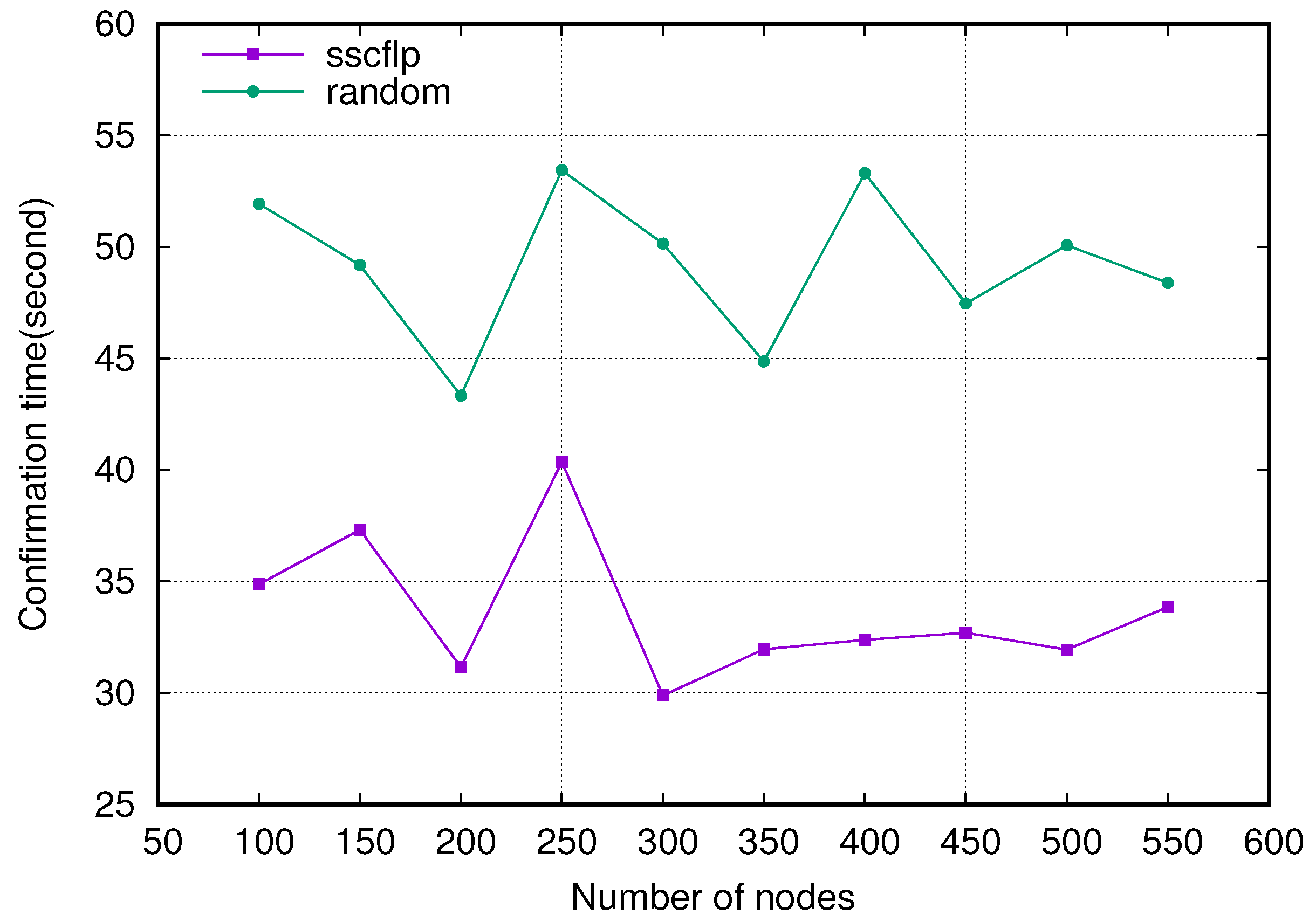
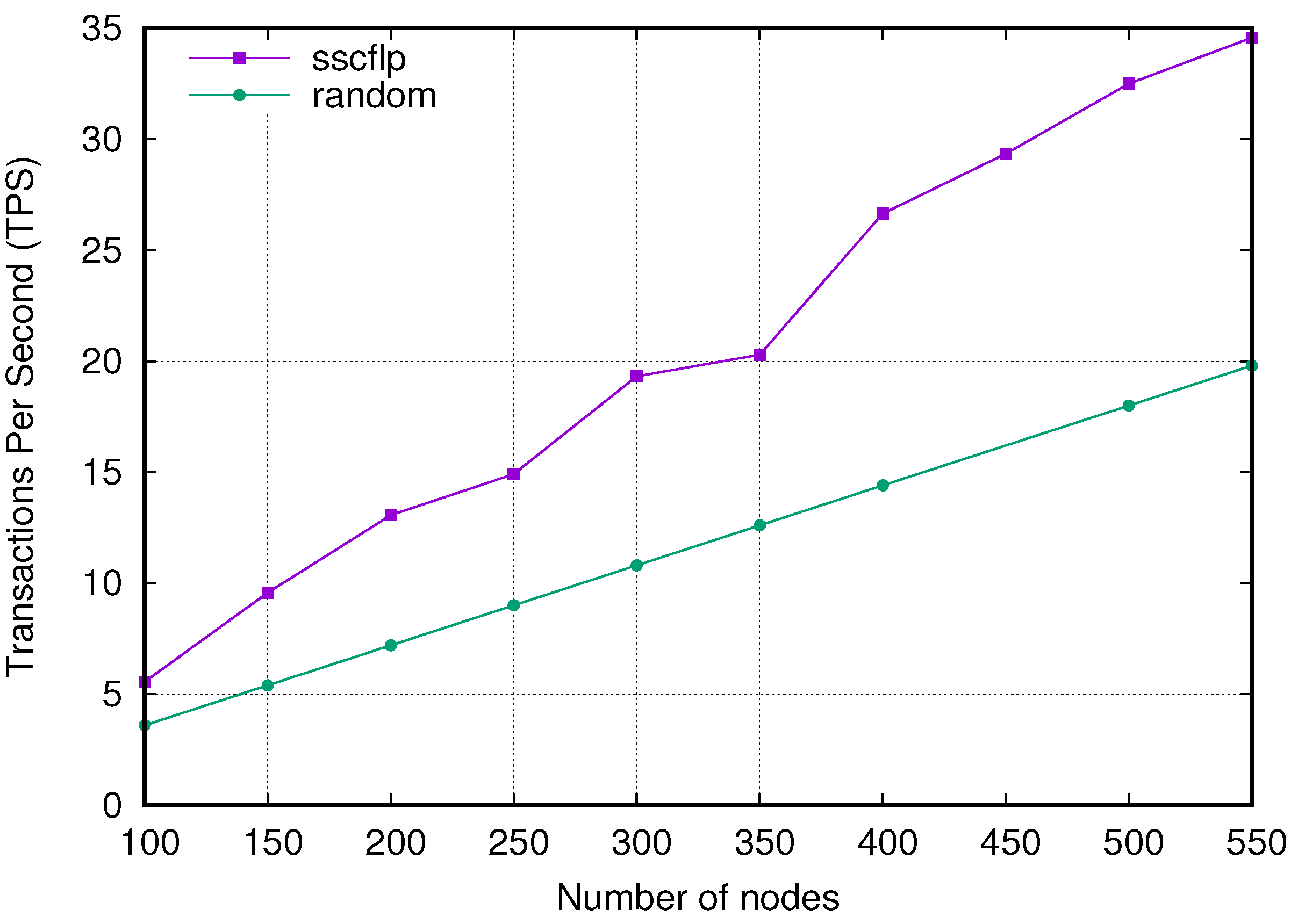
5.3. Experimental Results and Analysis
6. Conclusions
References
- Boyes, H.; Hallaq, B.; Cunningham, J.; Watson, T. The Industrial Internet of Things (IIoT): An Analysis Framework. Computers in Industry 2018, 101, 1–12. [Google Scholar] [CrossRef]
- Wright, C.S. Bitcoin: A Peer-to-Peer Electronic Cash System. SSRN Electronic Journal 2008. [Google Scholar] [CrossRef]
- King, S.; Nadal, S. PPCoin: Peer-to-Peer Crypto-Currency with Proof-of-Stake. 2012.
- Bentov, I.; Lee, C.; Mizrahi, A.; Rosenfeld, M. Proof of Activity: Extending Bitcoin’s Proof of Work via Proof of Stake [Extended Abstract]y. ACM SIGMETRICS Performance Evaluation Review 2014, 42, 34–37. [Google Scholar] [CrossRef]
- Castro, M.; Liskov, B. Practical Byzantine Fault Tolerance. In Proceedings of the 3rd Symposium on Operating Systems Design and Implementation (OSDI 99); 1999. [Google Scholar]
- Wood, G. ETHEREUM: A SECURE DECENTRALISED GENERALISED TRANSACTION LEDGER. 2019.
- Wu, K.; Ma, Y.; Huang, G.; Liu, X. A First Look at Blockchain-based Decentralized Applications. Software: Practice and Experience 2021, 51, 2033–2050. [Google Scholar] [CrossRef]
- Huo, R.; Zeng, S.; Wang, Z.; Shang, J.; Chen, W.; Huang, T.; Wang, S.; Yu, F.R.; Liu, Y. A Comprehensive Survey on Blockchain in Industrial Internet of Things: Motivations, Research Progresses, and Future Challenges. IEEE Communications Surveys & Tutorials 2022, 24, 88–122. [Google Scholar]
- Majeed, U.; Khan, L.U.; Yaqoob, I.; Kazmi, S.M.A.; Salah, K.; Hong, C.S. Blockchain for IoT-based Smart Cities: Recent Advances, Requirements, and Future Challenges. Journal of Network and Computer Applications 2021, 181, 103007. [Google Scholar] [CrossRef]
- Asheralieva, A.; Niyato, D. Reputation-Based Coalition Formation for Secure Self-Organized and Scalable Sharding in IoT Blockchains With Mobile-Edge Computing. IEEE Internet of Things Journal 2020, 7, 11830–11850. [Google Scholar] [CrossRef]
- Luu, L.; Narayanan, V.; Zheng, C.; Baweja, K.; Gilbert, S.; Saxena, P. A Secure Sharding Protocol For Open Blockchains. In Proceedings of the Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna Austria, 2016; pp. 17–30.
- Kokoris-Kogias, E.; Jovanovic, P.; Gasser, L.; Gailly, N.; Syta, E.; Ford, B. OmniLedger: A Secure, Scale-Out, Decentralized Ledger via Sharding. In Proceedings of the 2018 IEEE Symposium on Security and Privacy (SP), San Francisco, CA; 2018; pp. 583–598. [Google Scholar]
- Zamani, M.; Movahedi, M.; Raykova, M. RapidChain: Scaling Blockchain via Full Sharding. In Proceedings of the Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto Canada, 2018; pp. 931–948.
- Gao, N.; Huo, R.; Wang, S.; Huang, T.; Liu, Y. Sharding-Hashgraph: A High-Performance Blockchain-Based Framework for Industrial Internet of Things With Hashgraph Mechanism. IEEE Internet of Things Journal 2021, PP, 1–1. [Google Scholar] [CrossRef]
- Shahid, A.R.; Pissinou, N.; Staier, C.; Kwan, R. Sensor-Chain: A Lightweight Scalable Blockchain Framework for Internet of Things. In Proceedings of the 2019 International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Atlanta, GA, USA; 2019; pp. 1154–1161. [Google Scholar]
- Luo, C.; Hu, Y.; Zhang, S.; Zhang, Y.; Liu, Y.; Diao, X.; Huang, G. Fission: Autonomous, Scalable Sharding for IoT Blockchain. In Proceedings of the 2022 IEEE 46th Annual Computers, Software, and Applications Conference (COMPSAC), Los Alamitos, CA, USA, 2022; pp. 956–965. [Google Scholar]
- Santos, D.; Santos, C.; Santos, J.; Filho, A.; Saba, H. The Importance of the Facility Location Techniques to Assist Companies in Decision-Making for the Installation of Logistics Hub. Open Journal of Business and Management 2023, 12, 79–89. [Google Scholar] [CrossRef]
- Fajardo, J.; Lamata, M.; Pelta, D.; Porras Nodarse, C.; Rosete-Suárez, A.; Verdegay, J.L. Placing Wi-Fi Hotspots in Havana with Locations Availability Based on Fuzzy Constraints. 2018, pp. 1–6.
- Daskin, M.S.; Dean, L.K. Location of Health Care Facilities. In Operations Research and Health Care: A Handbook of Methods and Applications; Brandeau, M.L., Sainfort, F., Pierskalla, W.P., Eds.; Springer US: Boston, MA, USA, 2004; pp. 43–76. [Google Scholar]
- Yang, Z.; Chu, F.; Chen, H. A Cut-and-Solve Based Algorithm for the Single-Source Capacitated Facility Location Problem. European Journal of Operational Research 2012, 221, 521–532. [Google Scholar] [CrossRef]
- Basu, S.; Sharma, M.; Ghosh, P.S. Metaheuristic Applications on Discrete Facility Location Problems: A Survey. OPSEARCH 2015, 52, 530–561. [Google Scholar] [CrossRef]
- Xie, J.; Yu, F.R.; Huang, T.; Xie, R.; Liu, J.; Liu, Y. A Survey on the Scalability of Blockchain Systems. IEEE Network 2019, 33, 166–173. [Google Scholar] [CrossRef]
- Holmberg, K.; Rönnqvist, M.; Yuan, D. An Exact Algorithm for the Capacitated Facility Location Problems with Single Sourcing. European Journal of Operational Research 1999, 113, 544–559. [Google Scholar] [CrossRef]
- Contreras, I.A.; Díaz, J.A. Scatter Search for the Single Source Capacitated Facility Location Problem. Annals of Operations Research 2008, 157, 73–89. [Google Scholar] [CrossRef]
- Barceló, J.; Casanovas, J. A Heuristic Lagrangean Algorithm for the Capacitated Plant Location Problem. European Journal of Operational Research 1984, 15, 212–226. [Google Scholar] [CrossRef]
- Klincewicz, J.G.; Luss, H. A Lagrangian Relaxation Heuristic for Capacitated Facility Location with Single-Source Constraints. The Journal of the Operational Research Society 1986, 37, 495–500. [Google Scholar] [CrossRef]
- Cortinhal, M.J.; Captivo, M.E. Upper and Lower Bounds for the Single Source Capacitated Location Problem. European Journal of Operational Research 2003, 151, 333–351. [Google Scholar] [CrossRef]
- Ahuja, R.K.; Orlin, J.B.; Pallottino, S.; Scaparra, M.P.; Scutellà, M.G. A Multi-Exchange Heuristic for the Single-Source Capacitated Facility Location Problem. Management Science 2004, 50, 749–760. [Google Scholar] [CrossRef]
- Filho, V.J.M.F.; Galvão, R.D. A Tabu Search Heuristic for the Concentrator Location Problem. Location Science 1998, 6, 189–209. [Google Scholar] [CrossRef]
- Guastaroba, G.; Speranza, M.G. A Heuristic for BILP Problems: The Single Source Capacitated Facility Location Problem. European Journal of Operational Research 2014, 238, 438–450. [Google Scholar] [CrossRef]
- Jain, K.; Mahdian, M.; Markakis, E.; Saberi, A.; Vazirani, V.V. Greedy Facility Location Algorithms Analyzed Using Dual Fitting with Factor-Revealing LP, 2002, [cs/0207028].
| Solutions | Computing Complexity | Number of Shards | Sharding Way |
|---|---|---|---|
| Random | O(n) | Fixed | Random |
| FLPShard | O(c) | Dynamic | SSCFLP |
| Num of Nodes | Runtime(s) of Sharding | Num of Shards |
|---|---|---|
| 100 | 0.369857311 | 6 |
| 150 | 1.21786356 | 8 |
| 200 | 2.880915165 | 11 |
| 250 | 5.600496769 | 13 |
| 300 | 9.879560709 | 16 |
| 350 | 16.31054831 | 18 |
| 400 | 23.91638803 | 20 |
| 450 | 34.07220602 | 24 |
| 500 | 47.98072243 | 26 |
| 550 | 66.15946436 | 27 |
| 600 | 87.59393907 | 30 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





