Submitted:
14 January 2025
Posted:
15 January 2025
You are already at the latest version
Abstract
Keywords:
MSC: 15A09; 15A24; 15B33
1. Introduction
2. Preliminaries
- (a)
- if and only if ;
- (b)
- ;
- (c)
- ;
- (d)
- .
- (a)
- if and only if ,
- (b)
- ,
- (c)
- .
3. Solution of System (1)
4. Numerical Exemplification
Algorithm 1 General Solution of System (1) |
|
(1) Input the factors: n.
(2) Input the tensors:
and .
(3) Calculate the marices and , where .
(5) If both the equation (11) and the equation (13) hold, then calculate the unique solution by the equation (14).
(7) Output: .
|
| Algorithm 2 General Solution of System (1) |
|
(1) Input the factors: n.
(2) Input the tensors:
and .
(3) Calculate the matrices and , where .
(5) If both the equation (18) and the equation (13) hold, then calculate the unique solution by the equation (21).
(7) Output: .
|
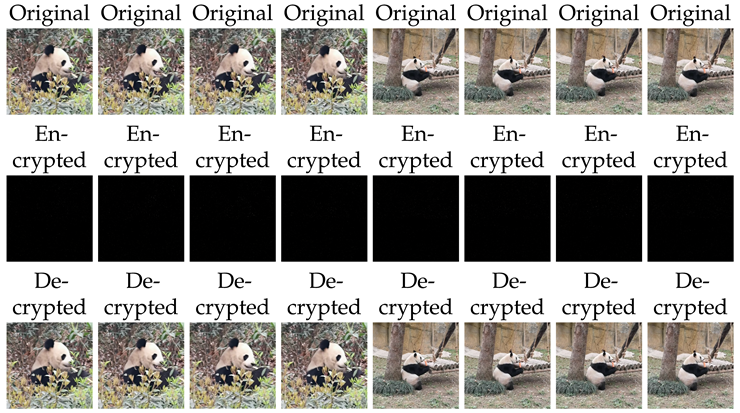
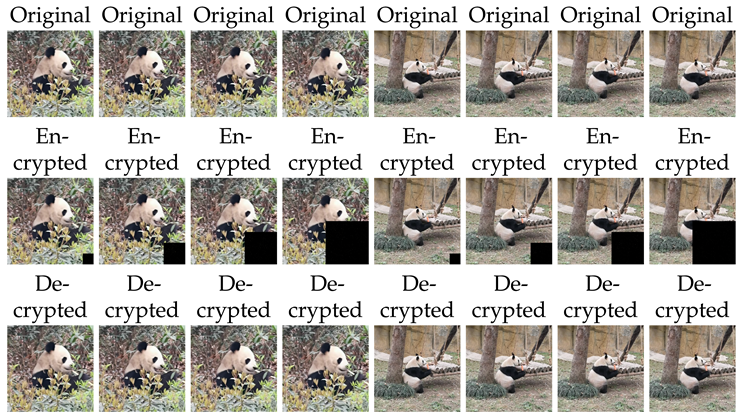
5. Color Videos Encryption and Decryption Based on (1)
| Algorithm 3 Encryption Process of Videos |
|
(1) Input: n original videos and system coefficients
and .
(2) Parse the videos: The represents i-th video where and represents j-th frame of i-th video.
(3) Calculate the tensors and by system (1).
(4) Encrypt i-th video by where . and is the key of i-th video.
(5) Output: Encrypted video.
|
| Algorithm 4 Decryption Process of Videos |
|
(1) Input: Encrypted videos , keys and system coefficients where .
(2) Calculate the numerical tensors by Algorithm 1.
(3) Recovered the videos: The represents i-th recovered video where and represents j-th recovered frame of i-th video.
(4) Calculate the error norm for and .
(5) Output: Decrypted video.
|
| Algorithm 5 Block Encryption Process of Frame |
|
(1) Input: one original frame and system coefficients
and .
(2) Parse the frames: The represents the frame and represents i-th sub-frame of the frame where .
(3) Calculate the matrices and by system (1).
(4) Assemble the i-th sub-frame where back into the frame . Encrypt the frame X by .
(5) Output: Encrypted frame.
|
| Algorithm 6 Block Decryption Process of Frame |
|
(1) Input: Encrypted frame , keys and system coefficients where .
(2) Calculate the matrices by Algorithm 1.
(3) Recovered the frame: The represents i-th recovered sub-frame where and assemble the back into the frame .
(4) Calculate the error norm between X and .
(5) Output: Decrypted frame.
|
6. Conclusion
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Hamilton WR, Lectures on quaternions, Dublin, Hodges and Smith, 1853.
- Took CC and Mandic DP, Augmented second-order statistics of quaternion random signals, Signal Processing, 91(2): 214-224, 2011.
- Miao J and Kou KI, Color image recovery using low-rank quaternion matrix completion algorithm, IEEE Transactions on Image Processing, 31: 190-201, 2021.
- Chen JF, Wang QW, Song GJ and Li T, Quaternion matrix factorization for low-rank quaternion matrix completion, Mathematics, 11(9): 2144, 2023.
- Jia ZG, Ling ST and Zhao MX, Color two-dimensional principal component analysis for face recognition based on quaternion model, Liverpool, Intelligent Computing Theories and Application: 13th International Conference, Part I(13): 177-189, 2017.
- Cockle J, LII. On systems of algebra involving more than one imaginary; and on equations of the fifth degree., London, Edinburgh, and Dublin, Philosophical Magazine and Journal of Science 35(238): 434-437, 1849.
- Adler SL, Quaternionic Quantum Mechanics and Quantum Fields., Oxford University Press, USA, 1995.
- Shoemake K, Animating rotation with quaternion curves., ACM SIGGRAPH Computer Graphics, 19(3): 245-254, 1985.
- Antonelli G and Chiaverini S, Kinematic control of a platoon of autonomous vehicles with a virtual leader., IEEE Transactions on Intelligent Transportation Systems, 8(4): 666-671, 2007.
- Krizhevsky A, Sutskever I and Hinton GE, ImageNet Classification with Deep Convolutional Neural Networks., Communications of the ACM, 60(6): 84-90, 2017.
- Carroll SM, Spacetime and Geometry: An Introduction to General Relativity (2nd ed.)., Cambridge University Press, 2019.
- Griffiths DJ and Heald MA, Introduction to Electrodynamics (4th ed.)., Cambridge University Press, 2013.
- Abadi M, Barham P, Chen J, Chen Z, Davis A, Dean J and Zheng X, TensorFlow: A System for Large-Scale Machine Learning., 12th USENIX symposium on operating systems design and implementation, (OSDI 16): 265-283, 2016.
- Paszke A, Gross S, Massa F, Lerer A, Bradbury J, Chanan G and Chintala S, PyTorch: An Imperative Style, High-Performance Deep Learning Library., Advances in neural information processing systems, 2019.
- Zhang S, Yao L, Sun A and Tay Y, Deep Learning Based Recommender System: A Survey and New Perspectives., ACM Computing Surveys, 52(1): 1-38, 2019.
- Qi LQ and Luo ZY, Tensor analysis: spectral theory and special tensors., Society for Industrial and Applied Mathematics, 2017.
- Qi LQ, Tensor Eigenvalues and Their Applications., Springer Nature, 2018.
- Ding WY, Luo ZY and Qi LQ, P-Tensors, P0-Tensors, and Their Applications., Linear Algebra and Its Applications, 555: 336, 2018.
- Wang QW, Lv RY and Zhang Y, The least-squares solution with the least norm to a system of tensor equations over the quaternion algebra., Linear and Multilinear Algebra, 70(10): 1942-1962, 2022.
- Xie MY, Wang QW and Zhang Y, The minimum-norm least squares solutions to quaternion tensor systems., Symmetry 14(7): 1460, 2022.
- Qin J and Wang QW, Solving a system of two-sided Sylvester-like quaternion tensor equations., Computational and Applied Mathematics, 42(5): 232, 2023.
- Chen XY and Wang QW, The η-(anti-) Hermitian solution to a constrained Sylvester-type generalized commutative quaternion matrix equation., Banach Journal of Mathematical Analysis, 17(3): 40, 2023.
- Ren BY, Wang QW and Chen XY, The η-Anti-Hermitian solution to a system of constrained matrix equations over the generalized segre quaternion algebra., Symmetry, 15(3): 592, 2023.
- Wang QW, Gao ZH and Xie LM, The (anti-)η-Hermitian solution to a novel system of matrix equations over the split quaternion algebra., Mathematical Methods in the Applied Sciences, 2024.
- Xie MY, Wang QW and Zhang Y, The BiCG algorithm for solving the minimal frobenius norm solution of generalized Sylvester tensor equation over the quaternions., Symmetry, 16(9): 1167, 2024.
- Yang LQ, Wang QW and Kou Z, A System of Tensor Equations over the Dual Split Quaternion Algebra with an Application., Mathematics, 12(22): 3571, 2024.
- Sun LZ, Zheng BD, Bu CJ and Wei YM, Moore–Penrose inverse of tensors via Einstein product., Linear and Multilinear Algebra, 64(4): 686-698, 2016.
- Liu TT and Yu SW, Some Properties of Reduced Biquaternion Tensors, Symmetry, 16(10): 1260, 2024.
- Yuan SF, Wang QW, Yu YB and Tian Y, On Hermitian solutions of the split quaternion matrix equation AXB+ CXD= E AXB+ CXD= E[J]., Advances in Applied Clifford Algebras, 27: 3235-3252, 2017.
- Ben-Israel A and Greville TNE, Generalized inverses: theory and applications., Springer Science & Business Media, 2006.
- Magnus JR, L-structured matrices and linear matrix equations., Linear and Multilinear Algebra, 14(1): 67-88, 1983.
- Xie LM and Wang QW, A system of matrix equations over the commutative quaternion ring., Filomat, 37(1): 97-106, 2023.
- Sara U, Akter M and Uddin MS, Image quality assessment through FSIM, SSIM, MSE and PSNR—a comparative study., Journal of Computer and Communications, 7(3): 8-18, 2019.
| Video 1 | Error | Video 2 | Error |
|---|---|---|---|
| 1-frame | 1-frame | ||
| 10-frame | 10-frame | ||
| 16-frame | 16-frame | ||
| 25-frame | 25-frame |
| Video 1 | PSNR | SSIM | FSIM | Video 2 | PSNR | SSIM | FSIM | |
|---|---|---|---|---|---|---|---|---|
| 1-frame | 245.4833 | 1 | 1 | 1-frame | 244.6598 | 1 | 1 | |
| 10-frame | 246.1960 | 1 | 1 | 10-frame | 245.8679 | 1 | 1 | |
| 16-frame | 246.0469 | 1 | 1 | 16-frame | 245.6220 | 1 | 1 | |
| 25-frame | 246.0457 | 1 | 1 | 25-frame | 245.4920 | 1 | 1 | |
| (a) PSNR, SSIM and FSIM of the video 1 | (b) PSNR, SSIM and FSIM of the video 2 | |||||||
| Video 1 | Error | Video 2 | Error |
|---|---|---|---|
| 3-frame | 3-frame | ||
| 12-frame | 12-frame | ||
| 18-frame | 18-frame | ||
| 27-frame | 27-frame |
| Video 1 | PSNR | SSIM | FSIM | Video 2 | PSNR | SSIM | FSIM | |
|---|---|---|---|---|---|---|---|---|
| 3-frame | 245.0190 | 1 | 1 | 3-frame | 244.3713 | 1 | 1 | |
| 12-frame | 244.5530 | 1 | 1 | 12-frame | 244.8359 | 1 | 1 | |
| 18-frame | 244.6391 | 1 | 1 | 18-frame | 246.7069 | 1 | 1 | |
| 27-frame | 245.3403 | 1 | 1 | 27-frame | 246.3910 | 1 | 1 | |
| (a) PSNR, SSIM and FSIM of the video 1 | (b) PSNR, SSIM and FSIM of the video 2 | |||||||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




