Submitted:
19 October 2023
Posted:
20 October 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Smart Cities and Information Security
3. Materials and Method
4. Findings and Discussion
4.1. Identifying the information security applications in smart cities clusters of research through bibliographic
4.2. Top authors with the highest number of publications and citations
4.3. Most active and cited journals
4.4. Country co-citation analysis
4.5. Keyword co-occurrence analysis
4.6. Methods in Cybersecurity
5. Discussion
5.1. Theoretical and Practical Implications
6. Conclusion
6.1. Limitations and Future Works
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Alfouzan, F.A.; Kim, K.; Alzahrani, N.M. An Efficient Framework for Securing the Smart City Communication Networks. Sensors 2022, 22, 3053. [Google Scholar] [CrossRef] [PubMed]
- Belgaum, M.R.; Alansari, Z.; Jain, R.; Alshaer, J. A Framework for Evaluation of Cyber Security Challenges in Smart Cities. In Proceedings of the Smart Cities Symposium 2018; Institution of Engineering and Technology, 2018; pp. 4 (6 pp.)–4 (6 pp.).
- Sharma, G.; Kalra, S. A Secure Remote User Authentication Scheme for Smart Cities E-Governance Applications. J. Reliab. Intell. Environ. 2017, 3, 177–188. [Google Scholar] [CrossRef]
- Naqvi, N.; Ur Rehman, S.; Islam, Z. A Hyperconnected Smart City Framework. Australas. J. Inf. Syst. 2020, 24. [Google Scholar] [CrossRef]
- Arasteh, H.; Hosseinnezhad, V.; Loia, V.; Tommasetti, A.; Troisi, O.; Shafie-khah, M.; Siano, P. Iot-Based Smart Cities: A Survey. In Proceedings of the 2016 IEEE 16th International Conference on Environment and Electrical Engineering (EEEIC); IEEE, June 2016; pp. 1–6.
- Mohamed, N.; Al-Jaroodi, J.; Jawhar, I.; Idries, A.; Mohammed, F. Unmanned Aerial Vehicles Applications in Future Smart Cities. Technol. Forecast. Soc. Change 2020, 153, 119293. [Google Scholar] [CrossRef]
- Braun, T.; Fung, B.C.M.; Iqbal, F.; Shah, B. Security and Privacy Challenges in Smart Cities. Sustain. Cities Soc. 2018, 39, 499–507. [Google Scholar] [CrossRef]
- Gourisetti, S.N.G.; Mylrea, M.; Patangia, H. Cybersecurity Vulnerability Mitigation Framework through Empirical Paradigm: Enhanced Prioritized Gap Analysis. Futur. Gener. Comput. Syst. 2020, 105, 410–431. [Google Scholar] [CrossRef]
- Nieto, A.; Acien, A.; Fernandez, G. Crowdsourcing Analysis in 5G IoT: Cybersecurity Threats and Mitigation. Mob. Networks Appl. 2019, 24, 881–889. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A Vision, Architectural Elements, and Future Directions. Futur. Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Ma, C. Smart City and Cyber-Security; Technologies Used, Leading Challenges and Future Recommendations. Energy Reports 2021, 7, 7999–8012. [Google Scholar] [CrossRef]
- Habib, M.Y.; Qureshi, H.A.; Khan, S.A.; Mansoor, Z.; Chishti, A.R. Cybersecurity and Smart Cities: Current Status and Future. In Proceedings of the 2023 IEEE International Conference on Emerging Trends in Engineering, Sciences and Technology (ICES&T); IEEE, January 9 2023; pp. 1–7.
- Behnam, A.; Azad, S.; Daneshvar, M.; Anvari-Moghaddam, A.; Marzband, M. Artificial Intelligence–Enabled Internet of Things Technologies in Modern Energy Grids. In IoT Enabled Multi-Energy Systems; Elsevier, 2023; pp. 69–86.
- Kim, K.; Alshenaifi, I.M.; Ramachandran, S.; Kim, J.; Zia, T.; Almorjan, A. Cybersecurity and Cyber Forensics for Smart Cities: A Comprehensive Literature Review and Survey. Sensors 2023, 23, 3681. [Google Scholar] [CrossRef]
- Elmaghraby, A.S.; Losavio, M.M. Cyber Security Challenges in Smart Cities: Safety, Security and Privacy. J. Adv. Res. 2014, 5, 491–497. [Google Scholar] [CrossRef]
- Xia, L.; Semirumi, D.T.; Rezaei, R. A Thorough Examination of Smart City Applications: Exploring Challenges and Solutions throughout the Life Cycle with Emphasis on Safeguarding Citizen Privacy. Sustain. Cities Soc. 2023, 98, 104771. [Google Scholar] [CrossRef]
- Anisetti, M.; Ardagna, C.; Bellandi, V.; Cremonini, M.; Frati, F.; Damiani, E. Privacy-Aware Big Data Analytics as a Service for Public Health Policies in Smart Cities. Sustain. Cities Soc. 2018, 39, 68–77. [Google Scholar] [CrossRef]
- Baig, Z.A.; Szewczyk, P.; Valli, C.; Rabadia, P.; Hannay, P.; Chernyshev, M.; Johnstone, M.; Kerai, P.; Ibrahim, A.; Sansurooah, K.; et al. Future Challenges for Smart Cities: Cyber-Security and Digital Forensics. Digit. Investig. 2017, 22, 3–13. [Google Scholar] [CrossRef]
- Caragliu, A.; Del Bo, C.F. Smart Innovative Cities: The Impact of Smart City Policies on Urban Innovation. Technol. Forecast. Soc. Change 2019, 142, 373–383. [Google Scholar] [CrossRef]
- Kitchin, R.; Dodge, M. The (In)Security of Smart Cities: Vulnerabilities, Risks, Mitigation, and Prevention. J. Urban Technol. 2019, 26, 47–65. [Google Scholar] [CrossRef]
- Sharma, K.; Mukhopadhyay, A. Sarima-Based Cyber-Risk Assessment and Mitigation Model for A Smart City’s Traffic Management Systems (Scram). J. Organ. Comput. Electron. Commer. 2022, 32, 1–20. [Google Scholar] [CrossRef]
- Rao, P.M.; Deebak, B.D. Security and Privacy Issues in Smart Cities/Industries: Technologies, Applications, and Challenges. J. Ambient Intell. Humaniz. Comput. 2023, 14, 10517–10553. [Google Scholar] [CrossRef]
- Lai, C.S.; Jia, Y.; Dong, Z.; Wang, D.; Tao, Y.; Lai, Q.H.; Wong, R.T.K.; Zobaa, A.F.; Wu, R.; Lai, L.L. A Review of Technical Standards for Smart Cities. Clean Technol. 2020, 2, 290–310. [Google Scholar] [CrossRef]
- Yigitcanlar, T.; Kankanamge, N.; Vella, K. How Are Smart City Concepts and Technologies Perceived and Utilized? A Systematic Geo-Twitter Analysis of Smart Cities in Australia. J. Urban Technol. 2021, 28, 135–154. [Google Scholar] [CrossRef]
- Verhulsdonck, G.; Weible, J.L.; Helser, S.; Hajduk, N. Smart Cities, Playable Cities, and Cybersecurity: A Systematic Review. Int. J. Human–Computer Interact. 2023, 39, 378–390. [Google Scholar] [CrossRef]
- Boni, A.; López-Fogués, A.; Fernández-Baldor, Á.; Millan, G.; Belda-Miquel, S. Initiatives towards a Participatory Smart City. The Role of Digital Grassroots Innovations. J. Glob. Ethics 2019, 15, 168–182. [Google Scholar] [CrossRef]
- Xu, N.; Ding, Y.; Guo, J. Do Smart City Policies Make Cities More Innovative: Evidence from China. J. Asian Public Policy 2022, 15, 1–17. [Google Scholar] [CrossRef]
- Habib, A.; Alsmadi, D.; Prybutok, V.R. Factors That Determine Residents’ Acceptance of Smart City Technologies. Behav. Inf. Technol. 2020, 39, 610–623. [Google Scholar] [CrossRef]
- Langer, L.; Skopik, F.; Smith, P.; Kammerstetter, M. From Old to New: Assessing Cybersecurity Risks for an Evolving Smart Grid. Comput. Secur. 2016, 62, 165–176. [Google Scholar] [CrossRef]
- Silva, M.M.; Costa, A.P.C.S.; Gusmão, A.P.H. de Continuous Cooperation: A Proposal Using a Fuzzy Multicriteria Sorting Method. Internenational J. Prod. Econ. 2014, 151, 67–75. [Google Scholar] [CrossRef]
- De Gusmão, A.P.H.; E Silva, L.C.; Silva, M.M.; Poleto, T.; Costa, A.P.C.S. Information Security Risk Analysis Model Using Fuzzy Decision Theory. Int. J. Inf. Manage. 2016, 36, 25–34. [Google Scholar] [CrossRef]
- Poleto, T.; Silva, M.M.; Clemente, T.R.N.; de Gusmão, A.P.H.; Araújo, A.P. de B.; Costa, A.P.C.S. A Risk Assessment Framework Proposal Based on Bow-Tie Analysis for Medical Image Diagnosis Sharing within Telemedicine. Sensors 2021, 21, 2426. [Google Scholar] [CrossRef]
- Rodgers, W.; Alhendi, E.; Xie, F. The Impact of Foreignness on the Compliance with Cybersecurity Controls. J. World Bus. 2019, 54, 101012. [Google Scholar] [CrossRef]
- De Gusmão, A.P.H.; Silva, M.M.; Poleto, T.; Silva, L.C.; Costa, A.P.C.S. Cybersecurity Risk Analysis Model Using Fault Tree Analysis and Fuzzy Decision Theory. Int. J. Inf. Manage. 2018, 43, 248–260. [Google Scholar] [CrossRef]
- Makhdoom, I.; Abolhasan, M.; Lipman, J.; Liu, R.P.; Ni, W. Anatomy of Threats to the Internet of Things. IEEE Commun. Surv. Tutorials 2019. [Google Scholar] [CrossRef]
- Kruse, C.S.; Frederick, B.; Jacobson, T.; Monticone, D.K. Cybersecurity in Healthcare: A Systematic Review of Modern Threats and Trends. Technol. Heal. Care 2017, 25, 1–10. [Google Scholar] [CrossRef] [PubMed]
- Stamatellis, C.; Papadopoulos, P.; Pitropakis, N.; Katsikas, S.; Buchanan, W.J. A Privacy-Preserving Healthcare Framework Using Hyperledger Fabric. Sensors 2020, 20, 6587. [Google Scholar] [CrossRef] [PubMed]
- Cabaj, K.; Domingos, D.; Kotulski, Z.; Respício, A. Cybersecurity Education: Evolution of the Discipline and Analysis of Master Programs. Comput. Secur. 2018, 75, 24–35. [Google Scholar] [CrossRef]
- Li, X.; Shan, Z.; Liu, F.; Chen, Y.; Hou, Y. A Consistently-Executing Graph-Based Approach for Malware Packer Identification. IEEE Access 2019, 7, 51620–51629. [Google Scholar] [CrossRef]
- Habibzadeh, H.; Nussbaum, B.H.; Anjomshoa, F.; Kantarci, B.; Soyata, T. A Survey on Cybersecurity, Data Privacy, and Policy Issues in Cyber-Physical System Deployments in Smart Cities. Sustain. Cities Soc. 2019, 50, 101660. [Google Scholar] [CrossRef]
- Shin, S.; Lee, S.; Burian, S.J.; Judi, D.R.; McPherson, T. Evaluating Resilience of Water Distribution Networks to Operational Failures from Cyber-Physical Attacks. J. Environ. Eng. 2020, 146, 1–11. [Google Scholar] [CrossRef]
- Collier, Z.A.; Dimase, D.; Walters, S.; Tehranipoor, M.M.; Lambert, J.H.; Linkov, I. Cybersecurity Standards: Managing Risk and Creating Resilience. Computer 2014, 47, 70–76. [Google Scholar] [CrossRef]
- National Institute of Standards and Technology Framework for Improving Critical Infrastructure Cybersecurity. Proc. Annu. ISA Anal. Div. Symp. 2018, 535, 9–25.
- Ben-Asher, N.; Gonzalez, C. Effects of Cyber Security Knowledge on Attack Detection. Comput. Human Behav. 2015, 48, 51–61. [Google Scholar] [CrossRef]
- Boyson, S. Cyber Supply Chain Risk Management: Revolutionizing the Strategic Control of Critical IT Systems. Technovation 2014, 34, 342–353. [Google Scholar] [CrossRef]
- Kawaguchi, H.; Tone, K.; Tsutsui, M. Estimation of the Efficiency of Japanese Hospitals Using a Dynamic and Network Data Envelopment Analysis Model. Health Care Manag. Sci. 2014, 17, 101–112. [Google Scholar] [CrossRef] [PubMed]
- Kim, Y.S.; Tague, P.; Lee, H.; Kim, H. A Jamming Approach to Enhance Enterprise Wi-Fi Secrecy through Spatial Access Control. Wirel. Networks 2015. [Google Scholar] [CrossRef]
- Kritzinger, E.; Von Solms, S.H. Cyber Security for Home Users: A New Way of Protection through Awareness Enforcement. Comput. Secur. 2010, 29, 840–847. [Google Scholar] [CrossRef]
- Pfleeger, S.L.; Caputo, D.D. Leveraging Behavioral Science to Mitigate Cyber Security Risk. Comput. Secur. 2012, 31, 597–611. [Google Scholar] [CrossRef]
- Razzaq, A.; Sharif, A.; Ozturk, I.; Skare, M. Asymmetric Influence of Digital Finance, and Renewable Energy Technology Innovation on Green Growth in China. Renew. Energy 2023, 202, 310–319. [Google Scholar] [CrossRef]
- Asif, M.; Aziz, Z.; Bin Ahmad, M.; Khalid, A.; Waris, H.A.; Gilani, A. Blockchain-Based Authentication and Trust Management Mechanism for Smart Cities. Sensors 2022, 22, 2604. [Google Scholar] [CrossRef]
- Anomah, S.; Ayeboafo, B.; Aguabeng, O. A Conceptual Model for Comprehensive Assurance Review Engagements for Less Developed Regulatory Environments. Edpacs 2023, 67, 1–29. [Google Scholar] [CrossRef]
- Nandan, M.; Singh, A.; Mandayam, G. Social Value Creation and Social Innovation by Human Service Professionals: Evidence from Missouri, USA. Adm. Sci. 2019, 9, 86. [Google Scholar] [CrossRef]
- Rathore, M.M.; Ahmad, A.; Paul, A.; Rho, S. Urban Planning and Building Smart Cities Based on the Internet of Things Using Big Data Analytics. Comput. Networks 2016, 101, 63–80. [Google Scholar] [CrossRef]
- Pohls, H.C.; Angelakis, V.; Suppan, S.; Fischer, K.; Oikonomou, G.; Tragos, E.Z.; Rodrigo Diaz Rodriguez; Mouroutis, T. RERUM: Building a Reliable IoT upon Privacy- and Security- Enabled Smart Objects. In Proceedings of the 2014 IEEE Wireless Communications and Networking Conference Workshops (WCNCW); IEEE, April 2014; pp. 122–127.
- Aloqaily, M.; Otoum, S.; Ridhawi, I.Al.; Jararweh, Y. An Intrusion Detection System for Connected Vehicles in Smart Cities. Ad Hoc Networks 2019, 90, 101842. [Google Scholar] [CrossRef]
- Chen, H.C.; You, I.; Weng, C.E.; Cheng, C.H.; Huang, Y.F. A Security Gateway Application for End-to-End M2M Communications. Comput. Stand. Interfaces 2016, 44, 85–93. [Google Scholar] [CrossRef]
- Cowley, J.A.; Greitzer, F.L.; Woods, B. Effect of Network Infrastructure Factors on Information System Risk Judgments. Comput. Secur. 2015, 52, 142–158. [Google Scholar] [CrossRef]
- Asri, S.; Pranggono, B. Impact of Distributed Denial-of-Service Attack on Advanced Metering Infrastructure. Wirel. Pers. Commun. 2015. [Google Scholar] [CrossRef]
- Ismagilova, E.; Hughes, L.; Rana, N.P.; Dwivedi, Y.K. Security, Privacy and Risks Within Smart Cities: Literature Review and Development of a Smart City Interaction Framework. Inf. Syst. Front. 2022, 24, 393–414. [Google Scholar] [CrossRef] [PubMed]
- Zhou, J. Artificial Intelligence-Based Recommendation and Application of Public Services in Smart Cities. Comput. Intell. Neurosci. 2022, 2022, 1–10. [Google Scholar] [CrossRef]
- Mora, L.; Gerli, P.; Ardito, L.; Messeni Petruzzelli, A. Smart City Governance from an Innovation Management Perspective: Theoretical Framing, Review of Current Practices, and Future Research Agenda. Technovation 2023, 123, 102717. [Google Scholar] [CrossRef]
- Azzaoui, A.El.; Singh, S.K.; Pan, Y.; Park, J.H. Block5GIntell: Blockchain for AI-Enabled 5G Networks. IEEE Access 2020, 8, 145918–145935. [Google Scholar] [CrossRef]
- He, Y.; Zhang, M.; Yang, X.; Luo, J.; Chen, Y. A Survey of Privacy Protection and Network Security in User On-Demand Anonymous Communication. IEEE Access 2020, 8, 54856–54871. [Google Scholar] [CrossRef]
- Lin, H.; Chen, C.; Wang, J.; Qi, J.; Jin, D.; Kalbarczyk, Z.T.; Iyer, R.K. Self-Healing Attack-Resilient PMU Network for Power System Operation. IEEE Trans. Smart Grid 2018, 9, 1551–1565. [Google Scholar] [CrossRef]
- Shin, J.; Son, H.; Khalil ur, R.; Heo, G. Development of a Cyber Security Risk Model Using Bayesian Networks. Reliab. Eng. Syst. Saf. 2015, 134, 208–217. [Google Scholar] [CrossRef]
- Verma, V.K.; Singh, S.; Pathak, N.P. Impact of Malicious Servers over Trust and Reputation Models in Wireless Sensor Networks. Int. J. Electron. 2016, 103, 530–540. [Google Scholar] [CrossRef]
- Gartner Gartner Forecasts Worldwide Public Cloud End-User Spending to Reach Nearly $600 Billion in 2023 Available online: www.gartner.com/en/industries/high-tech.
- Luo, Y.; Xu, M.; Huang, K.; Wang, D.; Fu, S. Efficient Auditing for Shared Data in the Cloud with Secure User Revocation and Computations Outsourcing. Comput. Secur. 2018, 73, 492–506. [Google Scholar] [CrossRef]
- Butpheng, C.; Yeh, K.-H.; Xiong, H. Security and Privacy in IoT-Cloud-Based e-Health Systems—A Comprehensive Review. Symmetry 2020, 12, 1191. [Google Scholar] [CrossRef]
- Dinh, T.; Kim, Y. A Novel Location-Centric IoT-Cloud Based On-Street Car Parking Violation Management System in Smart Cities. Sensors 2016, 16, 810. [Google Scholar] [CrossRef] [PubMed]
- Marwan, M.; Kartit, A.; Ouahmane, H. Security Enhancement in Healthcare Cloud Using Machine Learning. Procedia Comput. Sci. 2018, 127, 388–397. [Google Scholar] [CrossRef]
- National Institute of Standards and Technology - NIST Gaithersburg, MD October 2015, p. 75. 20 October.
- Bojanc, R.; Jerman-Blažič, B.; Tekavčič, M. Managing the Investment in Information Security Technology by Use of a Quantitative Modeling. Inf. Process. Manag. 2012, 48, 1031–1052. [Google Scholar] [CrossRef]
- Tweneboah-Koduah, S.; Skouby, K.E.; Tadayoni, R. Cyber Security Threats to IoT Applications and Service Domains. Wirel. Pers. Commun. 2017, 95, 169–185. [Google Scholar] [CrossRef]
- Aceto, G.; Persico, V.; Pescapé, A. The Role of Information and Communication Technologies in Healthcare: Taxonomies, Perspectives, and Challenges. J. Netw. Comput. Appl. 2018, 107, 125–154. [Google Scholar] [CrossRef]
- Whitley, E.a. Informational Privacy, Consent and the “Control” of Personal Data. Inf. Secur. Tech. Rep. 2009, 14, 154–159. [Google Scholar] [CrossRef]
- Wang, W.; Lu, Z. Cyber Security in the Smart Grid: Survey and Challenges. Comput. Networks 2013, 57, 1344–1371. [Google Scholar] [CrossRef]
- El-Gayar, O.F.; Fritz, B.D. A Web-Based Multi-Perspective Decision Support System for Information Security Planning. Decis. Support Syst. 2010, 50, 43–54. [Google Scholar] [CrossRef]
- Chen, R.-M.; Hsieh, K.-T. Effective Allied Network Security System Based on Designed Scheme with Conditional Legitimate Probability against Distributed Network Attacks and Intrusions. Int. J. Commun. Syst. 2012, 25, 672–688. [Google Scholar] [CrossRef]
- Varadharajan, V.; Tupakula, U. Counteracting Security Attacks in Virtual Machines in the Cloud Using Property Based Attestation. J. Netw. Comput. Appl. 2014, 40, 31–45. [Google Scholar] [CrossRef]
- Jolly, P.K.; Batra, S. Security against Attacks and Malicious Code Execution in Mobile Agent Using IBF-CPABE Protocol. Wirel. Pers. Commun. 2019, 107, 1155–1169. [Google Scholar] [CrossRef]
- Chuang, Y.-H.; Lei, C.-L.; Shiu, H.-J. How to Design a Secure Anonymous Authentication and Key Agreement Protocol for Multi-Server Environments and Prove Its Security. Symmetry (Basel). 2021, 13, 1629. [Google Scholar] [CrossRef]
- Bojanc, R.; Jerman-Blažič, B. Standard Approach for Quantification of the ICT Security Investment for Cybercrime Prevention. Proc. - 2nd Int. Conf. Digit. Soc. ICDS 2008 2008, 30, 7–14. [Google Scholar] [CrossRef]
- Saber, O.; Mazri, T. SMART CITY SECURITY ISSUES: THE MAIN ATTACKS AND COUNTERMEASURES. Int. Arch. Photogramm. Remote Sens. Spat. Inf. Sci. 2021, XLVI-4/W5-, 465–472. [Google Scholar] [CrossRef]
- Andriole, K.P. Security of Electronic Medical Information and Patient Privacy: What You Need to Know. J. Am. Coll. Radiol. 2014, 11, 1212–1216. [Google Scholar] [CrossRef]
- Ullah, F.; Ali Babar, M. Architectural Tactics for Big Data Cybersecurity Analytics Systems: A Review. J. Syst. Softw. 2019, 151, 81–118. [Google Scholar] [CrossRef]
- Kshetri, N. Blockchain’s Roles in Strengthening Cybersecurity and Protecting Privacy. Telecomm. Policy 2017, 41, 1027–1038. [Google Scholar] [CrossRef]
- Daoudagh, S.; Marchetti, E.; Savarino, V.; Bernabe, J.B.; García-Rodríguez, J.; Moreno, R.T.; Martinez, J.A.; Skarmeta, A.F. Data Protection by Design in the Context of Smart Cities: A Consent and Access Control Proposal. Sensors 2021, 21, 7154. [Google Scholar] [CrossRef] [PubMed]
- Zhou, L.; Thieret, R.; Watzlaf, V.; Dealmeida, D.; Parmanto, B. A Telehealth Privacy and Security Self-Assessment Questionnaire for Telehealth Providers: Development and Validation. Int. J. Telerehabilitation 2019, 11, 3–14. [Google Scholar] [CrossRef]
- Rehman, A.; Haseeb, K.; Saba, T.; Lloret, J.; Ahmed, Z. Mobility Support 5G Architecture with Real-Time Routing for Sustainable Smart Cities. Sustainability 2021, 13, 9092. [Google Scholar] [CrossRef]
- Nabi, F. Designing a Framework Method for Secure Business Application Logic Integrity in E-Commerce Systems. Int. J. Netw. Secur. 2011, 12, 29–41. [Google Scholar] [CrossRef]
- Ikrissi, G.; Mazri, T. IOT-BASED SMART ENVIRONMENTS: STATE OF THE ART, SECURITY THREATS AND SOLUTIONS. Int. Arch. Photogramm. Remote Sens. Spat. Inf. Sci. 2021, XLVI-4/W5-, 279–286. [Google Scholar] [CrossRef]
- Awan, K.A.; Ud Din, I.; Almogren, A.; Almajed, H. AgriTrust—A Trust Management Approach for Smart Agriculture in Cloud-Based Internet of Agriculture Things. Sensors 2020, 20, 6174. [Google Scholar] [CrossRef]
- Raoof, A.; Matrawy, A. The Effect of Buffer Management Strategies on 6LoWPAN’s Response to Buffer Reservation Attacks. IEEE Int. Conf. Commun. 2017, 1–7. [Google Scholar] [CrossRef]
- Sohal, A.S.; Sandhu, R.; Sood, S.K.; Chang, V. A Cybersecurity Framework to Identify Malicious Edge Device in Fog Computing and Cloud-of-Things Environments. Comput. Secur. 2018, 74, 340–354. [Google Scholar] [CrossRef]
- Sasaki, T.; Morita, Y.; Jada, A. Access Control Architecture for Smart City IoT Platform. In Proceedings of the 2019 18th IEEE International Conference On Trust, Security And Privacy In Computing And Communications/13th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE); IEEE, August 2019; pp. 717–722.
- Wang, F.; Luo, W. Assessing Spatial and Nonspatial Factors for Healthcare Access: Towards an Integrated Approach to Defining Health Professional Shortage Areas. Heal. Place 2005, 11, 131–146. [Google Scholar] [CrossRef]
- Banerjee, S.; Roy, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Rodrigues, J.J.P.C.; Park, Y. Multi-Authority CP-ABE-Based User Access Control Scheme with Constant-Size Key and Ciphertext for IoT Deployment. J. Inf. Secur. Appl. 2020, 53, 102503. [Google Scholar] [CrossRef]
- Di Francesco Maesa, D.; Mori, P.; Ricci, L. A Blockchain Based Approach for the Definition of Auditable Access Control Systems. Comput. Secur. 2019, 84, 93–119. [Google Scholar] [CrossRef]
- Dagher, G.G.; Mohler, J.; Milojkovic, M.; Marella, P.B. Ancile: Privacy-Preserving Framework for Access Control and Interoperability of Electronic Health Records Using Blockchain Technology. Sustain. Cities Soc. 2018, 39, 283–297. [Google Scholar] [CrossRef]
- Ferreira, D.C.; Marques, R.C. Do Quality and Access to Hospital Services Impact on Their Technical Efficiency? Omega 2019, 86, 218–236. [Google Scholar] [CrossRef]
- Kang, M.; Robards, F.; Luscombe, G.; Sanci, L.A.; Hawke, C.I.; Steinbeck, K.S.; Jan, S.; Kong, M.J.; Usherwood, T.P. Understanding Access and Equity: Associations between Barriers to Health Care and Social Marginalisation. J. Adolesc. Heal. 2018, 62, S28–S29. [Google Scholar] [CrossRef]
- Shi, M.; Jiang, R.; Hu, X.; Shang, J. A Privacy Protection Method for Health Care Big Data Management Based on Risk Access Control. Health Care Manag. Sci. 2019. [Google Scholar] [CrossRef] [PubMed]
- Hsu, C.; Zeng, B.; Zhang, M. A Novel Group Key Transfer for Big Data Security Q. Appl. Math. Comput. 2014, 249, 436–443. [Google Scholar] [CrossRef]
- Moreno-Sanchez, R.; Hayden, M.; Janes, C.; Anderson, G. A Web-Based Multimedia Spatial Information System to Document Aedes Aegypti Breeding Sites and Dengue Fever Risk along the US-Mexico Border. Heal. Place 2006, 12, 715–727. [Google Scholar] [CrossRef]
- Mendonça Silva, M.; Poleto, T.; Silva, L.C.E.; Henriques De Gusmao, A.P.; Cabral Seixas Costa, A.P. A Grey Theory Based Approach to Big Data Risk Management Using FMEA. Math. Probl. Eng. 2016, 2016. [Google Scholar] [CrossRef]
- Wang, J.; Paschalidis, I.C. Botnet Detection Based on Anomaly and Community Detection. IEEE Trans. Control Netw. Syst. 2017, 4, 392–404. [Google Scholar] [CrossRef]
- Singh, K.; Guntuku, S.C.; Thakur, A.; Hota, C. Big Data Analytics Framework for Peer-to-Peer Botnet Detection Using Random Forests. Inf. Sci. 2014, 278, 488–497. [Google Scholar] [CrossRef]
- Kim, D.W.; Yan, P.; Zhang, J. Detecting Fake Anti-Virus Software Distribution Webpages. Comput. Secur. 2015, 49, 95–106. [Google Scholar] [CrossRef]
- Alotaibi, S.S. Registration Center Based User Authentication Scheme for Smart E-Governance Applications in Smart Cities. IEEE Access 2019, 7, 5819–5833. [Google Scholar] [CrossRef]
- Deypir, M.; Horri, A. Instance Based Security Risk Value Estimation for Android Applications. J. Inf. Secur. Appl. 2018, 40, 20–30. [Google Scholar] [CrossRef]
- Pérez-González, D.; Preciado, S.T.; Solana-Gonzalez, P. Organizational Practices as Antecedents of the Information Security Management Performance. Inf. Technol. People 2019, 32, 1262–1275. [Google Scholar] [CrossRef]
- Rebollo, O.; Mellado, D.; Fernández-Medina, E. A Systematic Review of Information Security Governance Frameworks in the Cloud Computing Environment. J. Univers. Comput. Sci. 2012, 18, 798–815. [Google Scholar] [CrossRef]
- Arslan, O.; Çepni, M.S.; Etiler, N. Spatial Analysis of Perinatal Mortality Rates with Geographic Information Systems in Kocaeli, Turkey. Public Health 2013, 127, 369–379. [Google Scholar] [CrossRef]
- Wu, D.; Wu, D.D. Risk-Based Robust Evaluation of Hospital Efficiency. IEEE Syst. J. 2019, 13, 1906–1914. [Google Scholar] [CrossRef]
- Wu, D.X.; Wu, D.D. Risk-Based Robust Evaluation of Hospital Efficiency. IEEE Syst. J. 2019, 13, 1906–1914. [Google Scholar] [CrossRef]
- Ben-Arieh, D.; Gullipalli, D.K. Data Envelopment Analysis of Clinics with Sparse Data: Fuzzy Clustering Approach. Comput. Ind. Eng. 2012, 63, 13–21. [Google Scholar] [CrossRef]
- Verri Lucca, A.; Augusto Silva, L.; Luchtenberg, R.; Garcez, L.; Mao, X.; García Ovejero, R.; Miguel Pires, I.; Luis Victória Barbosa, J.; Reis Quietinho Leithardt, V. A Case Study on the Development of a Data Privacy Management Solution Based on Patient Information. Sensors 2020, 20, 6030. [Google Scholar] [CrossRef] [PubMed]
- Golmohammadi, D.; Mellat-Parast, M. Developing a Grey-Based Decision-Making Model for Supplier Selection. Int. J. Prod. Econ. 2012, 137, 191–200. [Google Scholar] [CrossRef]
- Ferdous, R.; Khan, F.; Sadiq, R.; Amyotte, P.; Veitch, B. Handling Data Uncertainties in Event Tree Analysis. Process Saf. Environ. Prot. 2009, 87, 283–292. [Google Scholar] [CrossRef]
- Cao, Z.; Lumineau, F. Revisiting the Interplay between Contractual and Relational Governance: A Qualitative and Meta-Analytic Investigation. J. Oper. Manag. 2015, 33–34, 15–42. [Google Scholar] [CrossRef]
- Liu, Q.; Zhou, T.; Cai, Z.; Yuan, Y.; Xu, M.; Qin, J.; Ma, W. Turning Backdoors for Efficient Privacy Protection against Image Retrieval Violations. Inf. Process. Manag. 2023, 60, 103471. [Google Scholar] [CrossRef]
- Martin, K. The Penalty for Privacy Violations: How Privacy Violations Impact Trust Online. J. Bus. Res. 2018, 82, 103–116. [Google Scholar] [CrossRef]
- Bansal, G.; Zahedi, F.M. Trust Violation and Repair: The Information Privacy Perspective. Decis. Support Syst. 2015, 71, 62–77. [Google Scholar] [CrossRef]
- Melnik, T. Avoiding Violations of Patient Privacy With Social Media. J. Nurs. Regul. 2013, 3, 39–46. [Google Scholar] [CrossRef]
- Liu, M.; Luo, Y.; Yang, C.; Pang, S.; Puthal, D.; Ren, K.; Zhang, X. Privacy-Preserving Matrix Product Based Static Mutual Exclusive Roles Constraints Violation Detection in Interoperable Role-Based Access Control. Futur. Gener. Comput. Syst. 2020, 109, 457–468. [Google Scholar] [CrossRef]
- Tamjidyamcholo, A.; Bin Baba, M.S.; Shuib, N.L.M.; Rohani, V.A. Evaluation Model for Knowledge Sharing in Information Security Professional Virtual Community. Comput. Secur. 2014, 43, 19–34. [Google Scholar] [CrossRef]
- Anwar, M.; He, W.; Ash, I.; Yuan, X.; Li, L.; Xu, L. Gender Difference and Employees’ Cybersecurity Behaviors. Comput. Human Behav. 2017, 69, 437–443. [Google Scholar] [CrossRef]
- Jalali, M.S.; Razak, S.; Gordon, W.; Perakslis, E.; Madnick, S. Health Care and Cybersecurity: Bibliometric Analysis of the Literature. J. Med. Internet Res. 2019, 21. [Google Scholar] [CrossRef] [PubMed]
- Huber, T.L.; Fischer, T.a.; Dibbern, J.; Hirschheim, R. A Process Model of Complementarity and Substitution of Contractual and Relational Governance in IS Outsourcing. J. Manag. Inf. Syst. 2013, 30, 81–114. [Google Scholar] [CrossRef]
- Manimaran, S.; Sastry, V.N.; Gopalan, N.P. SBTDDL: A Novel Framework for Sensor-Based Threats Detection on Android Smartphones Using Deep Learning. Comput. Secur. 2022, 118, 102729. [Google Scholar] [CrossRef]
- Cano Bejar, A.H.; Ray, S.; Huang, Y.H. Fighting for the Status Quo: Threat to Tech Self-Esteem and Opposition to Competing Smartphones. Inf. Manag. 2023, 60, 103748. [Google Scholar] [CrossRef]
- Tams, S.; Legoux, R.; Léger, P.-M. Smartphone Withdrawal Creates Stress: A Moderated Mediation Model of Nomophobia, Social Threat, and Phone Withdrawal Context. Comput. Human Behav. 2018, 81, 1–9. [Google Scholar] [CrossRef]
- Pang, H.; Ruan, Y. Can Information and Communication Overload Influence Smartphone App Users’ Social Network Exhaustion, Privacy Invasion and Discontinuance Intention? A Cognition-Affect-Conation Approach. J. Retail. Consum. Serv. 2023, 73, 103378. [Google Scholar] [CrossRef]
- De Prisco, R.; De Santis, A.; Malandrino, D.; Zaccagnino, R. An Improved Privacy Attack on Smartphones Exploiting the Accelerometer. J. Inf. Secur. Appl. 2023, 75, 103479. [Google Scholar] [CrossRef]
- van Eck, N.J.; Waltman, L.; Dekker, R.; van den Berg, J. A Comparison of Two Techniques for Bibliometric Mapping: Multidimensional Scaling and VOS. J. Am. Soc. Inf. Sci. Technol. 2010, 61, 2405–2416. [Google Scholar] [CrossRef]
- Chou, D.; Yen, D.; Lin, B.; Hong-Lam Cheng, P. Cyberspace Security Management. Ind. Manag. Data Syst. 1999, 99, 353–361. [Google Scholar] [CrossRef]
- Ahmad, F.; Adnane, A.; Franqueira, V.; Kurugollu, F.; Liu, L. Man-In-The-Middle Attacks in Vehicular Ad-Hoc Networks: Evaluating the Impact of Attackers’ Strategies. Sensors 2018, 18, 4040. [Google Scholar] [CrossRef] [PubMed]
- Abi Sen, A.A.; Eassa, F.A.; Jambi, K.; Yamin, M. Preserving Privacy in Internet of Things: A Survey. Int. J. Inf. Technol. 2018, 10, 189–200. [Google Scholar] [CrossRef]
- Ahmad, F.; Franqueira, V.N.L.; Adnane, A. TEAM: A Trust Evaluation and Management Framework in Context-Enabled Vehicular Ad-Hoc Networks. IEEE Access 2018, 6, 28643–28660. [Google Scholar] [CrossRef]
- Ahmad, F.; Kurugollu, F.; Adnane, A.; Hussain, R.; Hussain, F. MARINE: Man-in-the-Middle Attack Resistant Trust Model in Connected Vehicles. IEEE Internet Things J. 2020, 7, 3310–3322. [Google Scholar] [CrossRef]
- Ahmad, F.; Kurugollu, F.; Kerrache, C.A.; Sezer, S.; Liu, L. NOTRINO: A NOvel Hybrid TRust Management Scheme for INternet-of-Vehicles. IEEE Trans. Veh. Technol. 2021, 70, 9244–9257. [Google Scholar] [CrossRef]
- Farahani, B.; Firouzi, F.; Chang, V.; Badaroglu, M.; Constant, N.; Mankodiya, K. Towards Fog-Driven IoT EHealth: Promises and Challenges of IoT in Medicine and Healthcare. Futur. Gener. Comput. Syst. 2018, 78, 659–676. [Google Scholar] [CrossRef]
- Gaba, G.S.; Hedabou, M.; Kumar, P.; Braeken, A.; Liyanage, M.; Alazab, M. Zero Knowledge Proofs Based Authenticated Key Agreement Protocol for Sustainable Healthcare. Sustain. Cities Soc. 2022, 80, 103766. [Google Scholar] [CrossRef]
- Javed, M.; Ben Hamida, E.; Znaidi, W. Security in Intelligent Transport Systems for Smart Cities: From Theory to Practice. Sensors 2016, 16, 879. [Google Scholar] [CrossRef]
- Garcia-Font, V.; Garrigues, C.; Rifà-Pous, H. A Comparative Study of Anomaly Detection Techniques for Smart City Wireless Sensor Networks. Sensors 2016, 16, 868. [Google Scholar] [CrossRef]
- Garcia-Font, V.; Garrigues, C.; Rifà-Pous, H. Attack Classification Schema for Smart City WSNs. Sensors 2017, 17, 771. [Google Scholar] [CrossRef]
- Beltran, V.; Skarmeta, A.F.; Ruiz, P.M. An ARM-Compliant Architecture for User Privacy in Smart Cities: SMARTIE—Quality by Design in the IoT. Wirel. Commun. Mob. Comput. 2017, 2017, 1–13. [Google Scholar] [CrossRef]
- Chatzigiannakis, I.; Vitaletti, A.; Pyrgelis, A. A Privacy-Preserving Smart Parking System Using an IoT Elliptic Curve Based Security Platform. Comput. Commun. 2016, 89–90, 165–177. [Google Scholar] [CrossRef]
- Chen, C.-T.; Lee, C.-C.; Lin, I.-C. Efficient and Secure Three-Party Mutual Authentication Key Agreement Protocol for WSNs in IoT Environments. PLoS ONE 2020, 15, e0232277. [Google Scholar] [CrossRef]
- Das, A.K.; Bera, B.; Wazid, M.; Jamal, S.S.; Park, Y. On the Security of a Secure and Lightweight Authentication Scheme for Next Generation IoT Infrastructure. IEEE Access 2021, 9, 71856–71867. [Google Scholar] [CrossRef]
- Jain, S.K.; Kesswani, N.; Agarwal, B. Security, Privacy and Trust: Privacy Preserving Model for Internet of Things. Int. J. Intell. Inf. Database Syst. 2020, 13, 249. [Google Scholar] [CrossRef]
- Kamil, I.A.; Ogundoyin, S.O. A Big Data Anonymous Batch Verification Scheme with Conditional Privacy Preservation for Power Injection over Vehicular Network and 5G Smart Grid Slice. Sustain. Energy, Grids Networks 2019, 20, 100260. [Google Scholar] [CrossRef]
- Singh, S.; Pise, A.; Alfarraj, O.; Tolba, A.; Yoon, B. A Cryptographic Approach to Prevent Network Incursion for Enhancement of QoS in Sustainable Smart City Using MANET. Sustain. Cities Soc. 2022, 79, 103483. [Google Scholar] [CrossRef]
- Khan, Z.A. Using Energy-Efficient Trust Management to Protect IoT Networks for Smart Cities. Sustain. Cities Soc. 2018, 40, 1–15. [Google Scholar] [CrossRef]
- Li, X.; Shen, X. Blockchain Technology-Based Electronic Payment Strategy for City Mobile Pass Cards. Mob. Inf. Syst. 2022, 2022, 1–13. [Google Scholar] [CrossRef]
- Garcia-Font, V. SocialBlock: An Architecture for Decentralized User-Centric Data Management Applications for Communications in Smart Cities. J. Parallel Distrib. Comput. 2020, 145, 13–23. [Google Scholar] [CrossRef]
- Gong, B.; Liu, J.; Guo, S. A Trusted Attestation Scheme for Data Source of Internet of Things in Smart City Based on Dynamic Trust Classification. IEEE Internet Things J. 2021, 8, 16121–16141. [Google Scholar] [CrossRef]
- Ghahramani, M.; Javidan, R.; Shojafar, M. A Secure Biometric-Based Authentication Protocol for Global Mobility Networks in Smart Cities. J. Supercomput. 2020, 76, 8729–8755. [Google Scholar] [CrossRef]
- Gaur, M.S.; Kumar, S.; Gaur, N.K.; Sharma, P.S. Persuasive Factors and Weakness for Security Vulnerabilities in BIG IOT Data in Healthcare Solution. J. Phys. Conf. Ser. 2021, 2007, 012046. [Google Scholar] [CrossRef]
- Gope, P.; Amin, R.; Hafizul Islam, S.K.; Kumar, N.; Bhalla, V.K. Lightweight and Privacy-Preserving RFID Authentication Scheme for Distributed IoT Infrastructure with Secure Localization Services for Smart City Environment. Futur. Gener. Comput. Syst. 2018, 83, 629–637. [Google Scholar] [CrossRef]
- Islam, S.H.; Obaidat, M.S.; Vijayakumar, P.; Abdulhay, E.; Li, F.; Reddy, M.K.C. A Robust and Efficient Password-Based Conditional Privacy Preserving Authentication and Group-Key Agreement Protocol for VANETs. Futur. Gener. Comput. Syst. 2018, 84, 216–227. [Google Scholar] [CrossRef]
- Hassan, A.M.; Awad, A.I. Urban Transition in the Era of the Internet of Things: Social Implications and Privacy Challenges. IEEE Access 2018, 6, 36428–36440. [Google Scholar] [CrossRef]
- Kumar, A.; Abhishek, K.; Liu, X.; Haldorai, A. An Efficient Privacy-Preserving ID Centric Authentication in IoT Based Cloud Servers for Sustainable Smart Cities. Wirel. Pers. Commun. 2021, 117, 3229–3253. [Google Scholar] [CrossRef]
- Lee, J.; Kim, G.; Das, A.K.; Park, Y. Secure and Efficient Honey List-Based Authentication Protocol for Vehicular Ad Hoc Networks. IEEE Trans. Netw. Sci. Eng. 2021, 8, 2412–2425. [Google Scholar] [CrossRef]
- Li, X.; Liu, T.; Obaidat, M.S.; Wu, F.; Vijayakumar, P.; Kumar, N. A Lightweight Privacy-Preserving Authentication Protocol for VANETs. IEEE Syst. J. 2020, 14, 3547–3557. [Google Scholar] [CrossRef]
- Li, X.; Sangaiah, A.K.; Kumari, S.; Wu, F.; Shen, J.; Khan, M.K. An Efficient Authentication and Key Agreement Scheme with User Anonymity for Roaming Service in Smart City. Pers. Ubiquitous Comput. 2017, 21, 791–805. [Google Scholar] [CrossRef]
- Liu, W.; Wang, X.; Peng, W. Secure Remote Multi-Factor Authentication Scheme Based on Chaotic Map Zero-Knowledge Proof for Crowdsourcing Internet of Things. IEEE Access 2020, 8, 8754–8767. [Google Scholar] [CrossRef]
- Malik, V.; Singh, S. Security Risk Management in IoT Environment. J. Discret. Math. Sci. Cryptogr. 2019, 22, 697–709. [Google Scholar] [CrossRef]
- Khattak, H.A.; Farman, H.; Jan, B.; Din, I.U. Toward Integrating Vehicular Clouds with IoT for Smart City Services. IEEE Netw. 2019, 33, 65–71. [Google Scholar] [CrossRef]
- Rauf, A.; Wang, Z.; Sajid, H.; Ali Tahir, M. Secure Route-Obfuscation Mechanism with Information-Theoretic Security for Internet of Things. Sensors 2020, 20, 4221. [Google Scholar] [CrossRef] [PubMed]
- Qureshi, K.N.; Qayyum, S.; Ul Islam, M.N.; Jeon, G. A Secure Data Parallel Processing Based Embedded System for Internet of Things Computer Vision Using Field Programmable Gate Array Devices. Int. J. Circuit Theory Appl. 2021, 49, 1450–1469. [Google Scholar] [CrossRef]
- Salameh, H.B.; Almajali, S.; Ayyash, M.; Elgala, H. Security-Aware Channel Assignment in IoT-Based Cognitive Radio Networks for Time-Critical Applications. In Proceedings of the 2017 Fourth International Conference on Software Defined Systems (SDS); IEEE, May 2017; pp. 43–47.
- Reddy, A.G.; Suresh, D.; Phaneendra, K.; Shin, J.S.; Odelu, V. Provably Secure Pseudo-Identity Based Device Authentication for Smart Cities Environment. Sustain. Cities Soc. 2018, 41, 878–885. [Google Scholar] [CrossRef]
- Liu, X.; Wang, J.; Yang, Y.; Cao, Z.; Xiong, G.; Xia, W. Inferring Behaviors via Encrypted Video Surveillance Traffic by Machine Learning. In Proceedings of the 2019 IEEE 21st International Conference on High Performance Computing and Communications; IEEE 17th International Conference on Smart City; IEEE 5th International Conference on Data Science and Systems (HPCC/SmartCity/DSS); IEEE, August 2019; pp. 273–280.
- Memos, V.A.; Psannis, K.E.; Ishibashi, Y.; Kim, B.-G.; Gupta, B.B. An Efficient Algorithm for Media-Based Surveillance System (EAMSuS) in IoT Smart City Framework. Futur. Gener. Comput. Syst. 2018, 83, 619–628. [Google Scholar] [CrossRef]
- Mohanta, B.K.; Jena, D.; Satapathy, U.; Ramasubbareddy, S. Collaborative Decision Making System in Intelligent Transportation System Using Distributed Blockchain Technology. Int. J. Veh. Inf. Commun. Syst. 2022, 7, 64. [Google Scholar] [CrossRef]
- Meshram, C.; Ibrahim, R.W.; Deng, L.; Shende, S.W.; Meshram, S.G.; Barve, S.K. A Robust Smart Card and Remote User Password-Based Authentication Protocol Using Extended Chaotic Maps under Smart Cities Environment. Soft Comput. 2021, 25, 10037–10051. [Google Scholar] [CrossRef]
- Zakaria, H.; Abu Bakar, N.A.; Hassan, N.H.; Yaacob, S. IoT Security Risk Management Model for Secured Practice in Healthcare Environment. Procedia Comput. Sci. 2019, 161, 1241–1248. [Google Scholar] [CrossRef]
- Pangestuti, D.D.; Susanto, T.D.; Trisunarno, L. Measuring Smart Cities: Identification of Smart Society Indicators in Indonesia. In Proceedings of the 2021 IEEE International Conference on Industrial Engineering and Engineering Management (IEEM); IEEE, December 13 2021; pp. 1245–1249.
- Nikooghadam, M.; Amintoosi, H.; Islam, S.H.; Moghadam, M.F. A Provably Secure and Lightweight Authentication Scheme for Internet of Drones for Smart City Surveillance. J. Syst. Archit. 2021, 115, 101955. [Google Scholar] [CrossRef]
- Tanveer, M.; Khan, A.U.; Shah, H.; Chaudhry, S.A.; Naushad, A. PASKE-IoD: Privacy-Protecting Authenticated Key Establishment for Internet of Drones. IEEE Access 2021, 9, 145683–145698. [Google Scholar] [CrossRef]
- Tamizharasi, G.S.; Sultanah, H.P.; Balamurugan, B. IoT-Based E-Health System Security: A Vision Archictecture Elements and Future Directions. In Proceedings of the 2017 International conference of Electronics, Communication and Aerospace Technology (ICECA); IEEE, April 2017; pp. 655–661.
- Verde, L.; De Pietro, G.; Alrashoud, M.; Ghoneim, A.; Al-Mutib, K.N.; Sannino, G. Leveraging Artificial Intelligence to Improve Voice Disorder Identification Through the Use of a Reliable Mobile App. IEEE Access 2019, 7, 124048–124054. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Bhat K, V.; Vasilakos, A.V. LAM-CIoT: Lightweight Authentication Mechanism in Cloud-Based IoT Environment. J. Netw. Comput. Appl. 2020, 150, 102496. [Google Scholar] [CrossRef]
- Bagga, P.; Sutrala, A.K.; Das, A.K.; Vijayakumar, P. Blockchain-Based Batch Authentication Protocol for Internet of Vehicles. J. Syst. Archit. 2021, 113, 101877. [Google Scholar] [CrossRef]
- Umar, M.; Islam, S.H.; Mahmood, K.; Ahmed, S.; Ghaffar, Z.; Saleem, M.A. Provable Secure Identity-Based Anonymous and Privacy-Preserving Inter-Vehicular Authentication Protocol for VANETS Using PUF. IEEE Trans. Veh. Technol. 2021, 70, 12158–12167. [Google Scholar] [CrossRef]
- Wu, F.; Li, X.; Xu, L.; Kumari, S.; Lin, D.; Rodrigues, J.J.P.C. An Anonymous and Identity-Trackable Data Transmission Scheme for Smart Grid under Smart City Notion. Ann. Telecommun. 2020, 75, 307–317. [Google Scholar] [CrossRef]
- Vijayakumar, P.; Azees, M.; Chang, V.; Deborah, J.; Balusamy, B. Computationally Efficient Privacy Preserving Authentication and Key Distribution Techniques for Vehicular Ad Hoc Networks. Cluster Comput. 2017, 20, 2439–2450. [Google Scholar] [CrossRef]
- Wu, F.; Li, X.; Xu, L.; Kumari, S. A Privacy-Preserving Scheme with Identity Traceable Property for Smart Grid. Comput. Commun. 2020, 157, 38–44. [Google Scholar] [CrossRef]
- Sutrala, A.K.; Obaidat, M.S.; Saha, S.; Das, A.K.; Alazab, M.; Park, Y. Authenticated Key Agreement Scheme With User Anonymity and Untraceability for 5G-Enabled Softwarized Industrial Cyber-Physical Systems. IEEE Trans. Intell. Transp. Syst. 2022, 23, 2316–2330. [Google Scholar] [CrossRef]
- Sharma, G.; Kalra, S. Advanced Multi-Factor User Authentication Scheme for E-Governance Applications in Smart Cities. Int. J. Comput. Appl. 2019, 41, 312–327. [Google Scholar] [CrossRef]
- Simic, M.; Stankovic, M.; Orlic, V.D. Physical Layer Communication Security in Smart Cities: Challenges and Threats Identification. In Proceedings of the 2021 15th International Conference on Advanced Technologies, Systems and Services in Telecommunications (TELSIKS); IEEE, October 20 2021; pp. 209–218.
- Hamalainen, M.; Tyrvainen, P. A Framework for IoT Service Experiment Platforms in Smart-City Environments. In Proceedings of the 2016 IEEE International Smart Cities Conference (ISC2); IEEE, September 2016; pp. 1–8.
- Taher, B.H.; Liu, H.; Abedi, F.; Lu, H.; Yassin, A.A.; Mohammed, A.J. A Secure and Lightweight Three-Factor Remote User Authentication Protocol for Future IoT Applications. J. Sensors 2021, 2021, 1–18. [Google Scholar] [CrossRef]
- Sylla, T.; Chalouf, M.A.; Krief, F.; Samaké, K. SETUCOM: Secure and Trustworthy Context Management for Context-Aware Security and Privacy in the Internet of Things. Secur. Commun. Networks 2021, 2021, 1–24. [Google Scholar] [CrossRef]
- Sanober, S.; Aldawsari, M.; Karimovna, A.D.; Ofori, I. Blockchain Integrated with Principal Component Analysis: A Solution to Smart Security against Cyber-Attacks. Secur. Commun. Networks 2022, 2022, 1–9. [Google Scholar] [CrossRef]
- Xie, Q.; Hwang, L. Security Enhancement of an Anonymous Roaming Authentication Scheme with Two-Factor Security in Smart City. Neurocomputing 2019, 347, 131–138. [Google Scholar] [CrossRef]
- Wu, H.; Li, L.; Liu, Y.; Wu, X. Vehicle-Based Secure Location Clustering for IoT-Equipped Building and Facility Management in Smart City. Build. Environ. 2022, 214, 108937. [Google Scholar] [CrossRef]
- Zhang, J.; Zong, Y.; Yang, C.; Miao, Y.; Guo, J. LBOA: Location-Based Secure Outsourced Aggregation in IoT. IEEE Access 2019, 7, 43869–43883. [Google Scholar] [CrossRef]
- Zhang, H.; Babar, M.; Tariq, M.U.; Jan, M.A.; Menon, V.G.; Li, X. SafeCity: Toward Safe and Secured Data Management Design for IoT-Enabled Smart City Planning. IEEE Access 2020, 8, 145256–145267. [Google Scholar] [CrossRef]
- Wei, C. Copyright Protection and Data Reliability of AI-Written Literary Creations in Smart City. Secur. Commun. Networks 2022, 2022, 1–13. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, V.; Das, A.K.; Srinivas, J.; Kumar, N.; Chattopadhyay, S.; Choo, K.-K.R. A Provably Secure and Lightweight Anonymous User Authenticated Session Key Exchange Scheme for Internet of Things Deployment. IEEE Internet Things J. 2019, 6, 8739–8752. [Google Scholar] [CrossRef]
- Lever, K.E.; Kifayat, K. Identifying and Mitigating Security Risks for Secure and Robust NGI Networks. Sustain. Cities Soc. 2020, 59, 102098. [Google Scholar] [CrossRef]
- Mishra, A.K.; Puthal, D.; Tripathy, A.K. GraphCrypto: Next Generation Data Security Approach towards Sustainable Smart City Building. Sustain. Cities Soc. 2021, 72, 103056. [Google Scholar] [CrossRef]
- Wang, Z.; Jiang, D.; Wang, F.; Lv, Z.; Nowak, R. A Polymorphic Heterogeneous Security Architecture for Edge-Enabled Smart Grids. Sustain. Cities Soc. 2021, 67, 102661. [Google Scholar] [CrossRef]
- Duraisamy, A.; Subramaniam, M. Attack Detection on IoT Based Smart Cities Using IDS Based MANFIS Classifier and Secure Data Transmission Using IRSA Encryption. Wirel. Pers. Commun. 2021, 119, 1913–1934. [Google Scholar] [CrossRef]
- Deebak, B.D.; AL-Turjman, F. A Robust and Distributed Architecture for 5G-Enabled Networks in the Smart Blockchain Era. Comput. Commun. 2022, 181, 293–308. [Google Scholar] [CrossRef]
- Dwivedi, S.K.; Amin, R.; Vollala, S.; Chaudhry, R. Blockchain-Based Secured Event-Information Sharing Protocol in Internet of Vehicles for Smart Cities. Comput. Electr. Eng. 2020, 86, 106719. [Google Scholar] [CrossRef]
- Ferreira, C.M.S.; Garrocho, C.T.B.; Oliveira, R.A.R.; Silva, J.S.; Cavalcanti, C.F.M. da C. IoT Registration and Authentication in Smart City Applications with Blockchain. Sensors 2021, 21, 1323. [Google Scholar] [CrossRef]
- Guan, Z.; Si, G.; Zhang, X.; Wu, L.; Guizani, N.; Du, X.; Ma, Y. Privacy-Preserving and Efficient Aggregation Based on Blockchain for Power Grid Communications in Smart Communities. IEEE Commun. Mag. 2018, 56, 82–88. [Google Scholar] [CrossRef]
- Esposito, C.; Ficco, M.; Gupta, B.B. Blockchain-Based Authentication and Authorization for Smart City Applications. Inf. Process. Manag. 2021, 58, 102468. [Google Scholar] [CrossRef]
- Kumari, A.; Tanwar, S. Secure Data Analytics for Smart Grid Systems in a Sustainable Smart City: Challenges, Solutions, and Future Directions. Sustain. Comput. Informatics Syst. 2020, 28, 100427. [Google Scholar] [CrossRef]
- Kuppa, K.; Dayal, A.; Gupta, S.; Dua, A.; Chaudhary, P.; Rathore, S. ConvXSS: A Deep Learning-Based Smart ICT Framework against Code Injection Attacks for HTML5 Web Applications in Sustainable Smart City Infrastructure. Sustain. Cities Soc. 2022, 80, 103765. [Google Scholar] [CrossRef]
- Kumari, A.; Gupta, R.; Tanwar, S. Amalgamation of Blockchain and IoT for Smart Cities Underlying 6G Communication: A Comprehensive Review. Comput. Commun. 2021, 172, 102–118. [Google Scholar] [CrossRef]
- Ma, C.; Zeng, S.; Li, D. A New Algorithm for Backlight Image Enhancement. In Proceedings of the 2020 International Conference on Intelligent Transportation, Big Data & Smart City (ICITBS); IEEE, January 2020; pp. 840–844.
- Ma, R.; Lam, P.T.I.; Leung, C.K. Reliability Analysis of a Smart Parking Information System: The Case of Hong Kong. Wirel. Pers. Commun. 2021, 119, 1681–1701. [Google Scholar] [CrossRef]
- Gohari, S.; Ahlers, D.F.; Nielsen, B.; Junker, E. The Governance Approach of Smart City Initiatives. Evidence from Trondheim, Bergen, and Bodø. Infrastructures 2020, 5, 31. [Google Scholar] [CrossRef]
- Huang, C.-Y.; Chiang, Y.-H.; Tsai, F. An Ontology Integrating the Open Standards of City Models and Internet of Things for Smart-City Applications. IEEE Internet Things J. 2022, 1. [Google Scholar] [CrossRef]
- Huh, J.-H.; Kim, S.-K. The Blockchain Consensus Algorithm for Viable Management of New and Renewable Energies. Sustainability 2019, 11, 3184. [Google Scholar] [CrossRef]
- Jamil, F.; Cheikhrouhou, O.; Jamil, H.; Koubaa, A.; Derhab, A.; Ferrag, M.A. PetroBlock: A Blockchain-Based Payment Mechanism for Fueling Smart Vehicles. Appl. Sci. 2021, 11, 3055. [Google Scholar] [CrossRef]
- Kamal, R.; Hemdan, E.E.; El-Fishway, N. Forensics Chain for Evidence Preservation System: An Evidence Preservation Forensics Framework for Internet of Things-based Smart City Security Using Blockchain. Concurr. Comput. Pract. Exp. 2022. [Google Scholar] [CrossRef]
- Khan, Z.; Abbasi, A.G.; Pervez, Z. Blockchain and Edge Computing–Based Architecture for Participatory Smart City Applications. Concurr. Comput. Pract. Exp. 2020, 32. [Google Scholar] [CrossRef]
- Jan, A.; Parah, S.A.; Malik, B.A. IEFHAC: Image Encryption Framework Based on Hessenberg Transform and Chaotic Theory for Smart Health. Multimed. Tools Appl. 2022, 81, 18829–18853. [Google Scholar] [CrossRef]
- Roldán-Gómez, J.J.; Garcia-Aunon, P.; Mazariegos, P.; Barrientos, A. SwarmCity Project: Monitoring Traffic, Pedestrians, Climate, and Pollution with an Aerial Robotic Swarm. Pers. Ubiquitous Comput. 2022, 26, 1151–1167. [Google Scholar] [CrossRef]
- Salkuti, S.R. Smart Cities: Understanding Policies, Standards, Applications and Case Studies. Int. J. Electr. Comput. Eng. 2021, 11, 3137. [Google Scholar] [CrossRef]
- Sharma, P.K.; Ryu, J.H.; Park, K.Y.; Park, J.H.; Park, J.H. Li-Fi Based on Security Cloud Framework for Future IT Environment. Human-centric Comput. Inf. Sci. 2018, 8, 23. [Google Scholar] [CrossRef]
- Mukherjee, A.; Sahoo, S.; Halder, R. A Blockchain-Based Integrated and Interconnected Hybrid Platform for Smart City Ecosystem. Peer-to-Peer Netw. Appl. 2022, 15, 2116–2141. [Google Scholar] [CrossRef]
- Singh, S.K.; Rathore, S.; Park, J.H. BlockIoTIntelligence: A Blockchain-Enabled Intelligent IoT Architecture with Artificial Intelligence. Futur. Gener. Comput. Syst. 2020, 110, 721–743. [Google Scholar] [CrossRef]
- Otuoze, A.O.; Mustafa, M.W.; Mohammed, O.O.; Saeed, M.S.; Surajudeen-Bakinde, N.T.; Salisu, S. Electricity Theft Detection by Sources of Threats for Smart City Planning. IET Smart Cities 2019, 1, 52–60. [Google Scholar] [CrossRef]
- Omar, A.Al.; Jamil, A.K.; Khandakar, A.; Uzzal, A.R.; Bosri, R.; Mansoor, N.; Rahman, M.S. A Transparent and Privacy-Preserving Healthcare Platform With Novel Smart Contract for Smart Cities. IEEE Access 2021, 9, 90738–90749. [Google Scholar] [CrossRef]
- Joshi, S.; Dubey, D.M.; Kumar Mishra, D.D. An Approach Using Trust Management with Next-Generation IoT Networks for Healthcare, Agriculture and Sustainable Development Goals. J. Univ. Shanghai Sci. Technol. 2021, 23. [Google Scholar] [CrossRef]
- Pujol, F.A.; Mora, H.; Pertegal, M.L. A Soft Computing Approach to Violence Detection in Social Media for Smart Cities. Soft Comput. 2020, 24, 11007–11017. [Google Scholar] [CrossRef]
- Rehman, A.; Haseeb, K.; Saba, T.; Kolivand, H. M-SMDM: A Model of Security Measures Using Green Internet of Things with Cloud Integrated Data Management for Smart Cities. Environ. Technol. Innov. 2021, 24, 101802. [Google Scholar] [CrossRef]
- Pereira, J.; Batista, T.; Cavalcante, E.; Souza, A.; Lopes, F.; Cacho, N. A Platform for Integrating Heterogeneous Data and Developing Smart City Applications. Futur. Gener. Comput. Syst. 2022, 128, 552–566. [Google Scholar] [CrossRef]
- Rao, P.M.; Deebak, B.D. Security and Privacy Issues in Smart Cities/Industries: Technologies, Applications, and Challenges. J. Ambient Intell. Humaniz. Comput. 2022. [Google Scholar] [CrossRef]
- Alonso, Á.; Fernández, F.; Marco, L.; Salvachúa, J. IAACaaS: IoT Application-Scoped Access Control as a Service. Futur. Internet 2017, 9, 64. [Google Scholar] [CrossRef]
- Yuvaraj, N.; Praghash, K.; Raja, R.A.; Karthikeyan, T. An Investigation of Garbage Disposal Electric Vehicles (GDEVs) Integrated with Deep Neural Networking (DNN) and Intelligent Transportation System (ITS) in Smart City Management System (SCMS). Wirel. Pers. Commun. 2022, 123, 1733–1752. [Google Scholar] [CrossRef]
- Wang, D.; Bai, B.; Lei, K.; Zhao, W.; Yang, Y.; Han, Z. Enhancing Information Security via Physical Layer Approaches in Heterogeneous IoT With Multiple Access Mobile Edge Computing in Smart City. IEEE Access 2019, 7, 54508–54521. [Google Scholar] [CrossRef]
- Xie, J.; Tang, H.; Huang, T.; Yu, F.R.; Xie, R.; Liu, J.; Liu, Y. A Survey of Blockchain Technology Applied to Smart Cities: Research Issues and Challenges. IEEE Commun. Surv. Tutorials 2019, 21, 2794–2830. [Google Scholar] [CrossRef]
- Xu, Z.; Luo, M.; Vijayakumar, P.; Peng, C.; Wang, L. Efficient Certificateless Designated Verifier Proxy Signature Scheme Using UAV Network for Sustainable Smart City. Sustain. Cities Soc. 2022, 80, 103771. [Google Scholar] [CrossRef]
- Xu, R.; Chen, Y. Fed-DDM: A Federated Ledgers Based Framework for Hierarchical Decentralized Data Marketplaces. In Proceedings of the 2021 International Conference on Computer Communications and Networks (ICCCN); IEEE, July 2021; pp. 1–8.
- Yazdinejad, A.; Srivastava, G.; Parizi, R.M.; Dehghantanha, A.; Choo, K.-K.R.; Aledhari, M. Decentralized Authentication of Distributed Patients in Hospital Networks Using Blockchain. IEEE J. Biomed. Heal. Informatics 2020, 24, 2146–2156. [Google Scholar] [CrossRef] [PubMed]
- Yahaya, A.S.; Javaid, N.; Javed, M.U.; Shafiq, M.; Khan, W.Z.; Aalsalem, M.Y. Blockchain-Based Energy Trading and Load Balancing Using Contract Theory and Reputation in a Smart Community. IEEE Access 2020, 8, 222168–222186. [Google Scholar] [CrossRef]
- Al-Aswad, H.; El-Medany, W.M.; Balakrishna, C.; Ababneh, N.; Curran, K. BZKP: Blockchain-Based Zero-Knowledge Proof Model for Enhancing Healthcare Security in Bahrain IoT Smart Cities and COVID-19 Risk Mitigation. Arab J. Basic Appl. Sci. 2021, 28, 154–171. [Google Scholar] [CrossRef]
- Al-Muhtadi, J.; Saleem, K.; Al-Rabiaah, S.; Imran, M.; Gawanmeh, A.; Rodrigues, J.J.P.C. A Lightweight Cyber Security Framework with Context-Awareness for Pervasive Computing Environments. Sustain. Cities Soc. 2021, 66, 102610. [Google Scholar] [CrossRef]
- Alasbali, N.; Bin Azzuhri, S.R.; Bin Salleh, R.; Kiah, M.L.M.; Shariffuddin, A.A.A.S.A.; Kamel, N.M.I. bin N.M.; Ismail, L. Rules of Smart IoT Networks within Smart Cities towards Blockchain Standardization. Mob. Inf. Syst. 2022, 2022, 1–11. [Google Scholar] [CrossRef]
- Alasbali, N.; Bin Azzuhri, S.R.; Salleh, R. Stakeholders’ Viewpoints toward Blockchain Integration within IoT-Based Smart Cities. J. Sensors 2021, 2021, 1–17. [Google Scholar] [CrossRef]
- Alharthi, A.; Ni, Q.; Jiang, R. A Privacy-Preservation Framework Based on Biometrics Blockchain (BBC) to Prevent Attacks in VANET. IEEE Access 2021, 9, 87299–87309. [Google Scholar] [CrossRef]
- Abishu, H.N.; Seid, A.M.; Yacob, Y.H.; Ayall, T.; Sun, G.; Liu, G. Consensus Mechanism for Blockchain-Enabled Vehicle-to-Vehicle Energy Trading in the Internet of Electric Vehicles. IEEE Trans. Veh. Technol. 2022, 71, 946–960. [Google Scholar] [CrossRef]
- Abbas, K.; Tawalbeh, L.A.; Rafiq, A.; Muthanna, A.; Elgendy, I.A.; Abd El-Latif, A.A. Convergence of Blockchain and IoT for Secure Transportation Systems in Smart Cities. Secur. Commun. Networks 2021, 2021, 1–13. [Google Scholar] [CrossRef]
- Abou-Nassar, E.M.; Iliyasu, A.M.; El-Kafrawy, P.M.; Song, O.-Y.; Bashir, A.K.; El-Latif, A.A.A. DITrust Chain: Towards Blockchain-Based Trust Models for Sustainable Healthcare IoT Systems. IEEE Access 2020, 8, 111223–111238. [Google Scholar] [CrossRef]
- Chaudhary, R.; Jindal, A.; Aujla, G.S.; Aggarwal, S.; Kumar, N.; Choo, K.-K.R. BEST: Blockchain-Based Secure Energy Trading in SDN-Enabled Intelligent Transportation System. Comput. Secur. 2019, 85, 288–299. [Google Scholar] [CrossRef]
- Cha, J.; Singh, S.K.; Kim, T.W.; Park, J.H. Blockchain-Empowered Cloud Architecture Based on Secret Sharing for Smart City. J. Inf. Secur. Appl. 2021, 57, 102686. [Google Scholar] [CrossRef]
- Botello, J.V.; Mesa, A.P.; Rodríguez, F.A.; Díaz-López, D.; Nespoli, P.; Mármol, F.G. BlockSIEM: Protecting Smart City Services through a Blockchain-Based and Distributed SIEM. Sensors 2020, 20, 4636. [Google Scholar] [CrossRef]
- Dar, M.A.; Askar, A.; Bhat, S.A. Blockchain Based Secure Data Exchange between Cloud Networks and Smart Hand-Held Devices for Use in Smart Cities. In Proceedings of the 2022 International Conference on Artificial Intelligence in Information and Communication (ICAIIC); IEEE, February 21 2022; pp. 457–460.
- Alsaffar, N.; El Medany, W.M.; Ali, H. Low Complexity Cybersecurity Architecture for the Development of ITS in Smart Cities. Int. J. Electron. Secur. Digit. Forensics 2021, 13, 571. [Google Scholar] [CrossRef]
- Alsammak, I.L.H.; Alomari, M.F.; Shakir Nasir, I.; Itwee, W.H. A Model for Blockchain-Based Privacy-Preserving for Big Data Users on the Internet of Thing. Indones. J. Electr. Eng. Comput. Sci. 2022, 26, 974. [Google Scholar] [CrossRef]
- Babiker Mohamed, M.; Matthew Alofe, O.; Ajmal Azad, M.; Singh Lallie, H.; Fatema, K.; Sharif, T. A Comprehensive Survey on Secure Software-defined Network for the Internet of Things. Trans. Emerg. Telecommun. Technol. 2022, 33. [Google Scholar] [CrossRef]
- Han, D.; Zhu, Y.; Li, D.; Liang, W.; Souri, A.; Li, K.-C. A Blockchain-Based Auditable Access Control System for Private Data in Service-Centric IoT Environments. IEEE Trans. Ind. Informatics 2022, 18, 3530–3540. [Google Scholar] [CrossRef]
- Haseeb, K.; Ud Din, I.; Almogren, A.; Ahmed, I.; Guizani, M. Intelligent and Secure Edge-Enabled Computing Model for Sustainable Cities Using Green Internet of Things. Sustain. Cities Soc. 2021, 68, 102779. [Google Scholar] [CrossRef]
- Moustaka, V.; Theodosiou, Z.; Vakali, A.; Kounoudes, A.; Anthopoulos, L.G. Εnhancing Social Networking in Smart Cities: Privacy and Security Borderlines. Technol. Forecast. Soc. Change 2019, 142, 285–300. [Google Scholar] [CrossRef]
- Mohanty, S.P.; Kougianos, E.; Guturu, P. SBPG: Secure Better Portable Graphics for Trustworthy Media Communications in the IoT. IEEE Access 2018, 6, 5939–5953. [Google Scholar] [CrossRef]
- Mugarza, I.; Amurrio, A.; Azketa, E.; Jacob, E. Dynamic Software Updates to Enhance Security and Privacy in High Availability Energy Management Applications in Smart Cities. IEEE Access 2019, 7, 42269–42279. [Google Scholar] [CrossRef]
- Safa, N.S.; Mitchell, F.; Maple, C.; Azad, M.A.; Dabbagh, M. Privacy Enhancing Technologies (<scp>PETs</Scp>) for Connected Vehicles in Smart Cities. Trans. Emerg. Telecommun. Technol. 2020. [Google Scholar] [CrossRef]
- Yang, W.; Lam, P.T.I. Evaluating Non-Market Costs of ICT Involving Data Transmission in Smart Cities. Build. Res. Inf. 2021, 49, 715–728. [Google Scholar] [CrossRef]
- Wang, Z.; Xu, J.; He, X.; Wang, Y. Analysis of Spatiotemporal Influence Patterns of Toxic Gas Monitoring Concentrations in an Urban Drainage Network Based on IoT and GIS. Pattern Recognit. Lett. 2020, 138, 237–246. [Google Scholar] [CrossRef]
- Wu, F.; Xu, T.; Guo, J.; Huang, B.; Xu, C.; Wang, J.; Li, X. Deep Siamese Cross-Residual Learning for Robust Visual Tracking. IEEE Internet Things J. 2021, 8, 15216–15227. [Google Scholar] [CrossRef]
- Vogiatzaki, M.; Zerefos, S.; Hoque Tania, M. Enhancing City Sustainability through Smart Technologies: A Framework for Automatic Pre-Emptive Action to Promote Safety and Security Using Lighting and ICT-Based Surveillance. Sustainability 2020, 12, 6142. [Google Scholar] [CrossRef]
- Zhang, Y.J.; Alazab, M.; Muthu, B. Machine Learning-Based Holistic Privacy Decentralized Framework for Big Data Security and Privacy in Smart City. Arab. J. Sci. Eng. 2021. [Google Scholar] [CrossRef]
- Zhang, M.; Wang, X.; Sathishkumar, V.E.; Sivakumar, V. Machine Learning Techniques Based on Security Management in Smart Cities Using Robots. Work 2021, 68, 891–902. [Google Scholar] [CrossRef] [PubMed]
- Lv, Y.; Su, D. Blockchain Security Technology Based on the Asynchronous Transmission Mode of IoT Technology in Smart Cities. Wirel. Pers. Commun. 2021. [Google Scholar] [CrossRef]
- Chaturvedi, K.; Matheus, A.; Nguyen, S.H.; Kolbe, T.H. Securing Spatial Data Infrastructures for Distributed Smart City Applications and Services. Futur. Gener. Comput. Syst. 2019, 101, 723–736. [Google Scholar] [CrossRef]
- Al-Turjman, F.; Zahmatkesh, H.; Shahroze, R. An Overview of Security and Privacy in Smart Cities’ IoT Communications. Trans. Emerg. Telecommun. Technol. 2022, 33. [Google Scholar] [CrossRef]
- Dahmane, W.M.; Ouchani, S.; Bouarfa, H. Towards a Reliable Smart City through Formal Verification and Network Analysis. Comput. Commun. 2021, 180, 171–187. [Google Scholar] [CrossRef]
- Miao, Y.; Ma, J.; Jiang, Q.; Li, X.; Sangaiah, A.K. Verifiable Keyword Search over Encrypted Cloud Data in Smart City. Comput. Electr. Eng. 2018, 65, 90–101. [Google Scholar] [CrossRef]
- Maltezos, E.; Lioupis, P.; Dadoukis, A.; Karagiannidis, L.; Ouzounoglou, E.; Krommyda, M.; Amditis, A. A Video Analytics System for Person Detection Combined with Edge Computing. Computation 2022, 10, 35. [Google Scholar] [CrossRef]
- Miraftabzadeh, S.A.; Rad, P.; Choo, K.-K.R.; Jamshidi, M. A Privacy-Aware Architecture at the Edge for Autonomous Real-Time Identity Reidentification in Crowds. IEEE Internet Things J. 2018, 5, 2936–2946. [Google Scholar] [CrossRef]
- Gopi, R.; Muthusamy, P.; Suresh, P.; G. Gabriel Santhosh Kumar, C.; V. Pustokhina, I.; A. Pustokhin, D.; Shankar, K. Optimal Confidential Mechanisms in Smart City Healthcare. Comput. Mater. Contin. 2022, 70, 4883–4896. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Kumari, S.; Wu, F.; Choo, K.-K.R. A Robust Biometrics Based Three-Factor Authentication Scheme for Global Mobility Networks in Smart City. Futur. Gener. Comput. Syst. 2018, 83, 607–618. [Google Scholar] [CrossRef]
- Sengan, S.; V, S.; Nair, S.K.; V., I.; J., M.; Ravi, L. Enhancing Cyber–Physical Systems with Hybrid Smart City Cyber Security Architecture for Secure Public Data-Smart Network. Futur. Gener. Comput. Syst. 2020, 112, 724–737. [Google Scholar] [CrossRef]
- Tanveer, M.; Khan, A.U.; Alkhayyat, A.; Chaudhry, S.A.; Bin Zikria, Y.; Kim, S.W. REAS-TMIS: Resource-Efficient Authentication Scheme for Telecare Medical Information System. IEEE Access 2022, 10, 23008–23021. [Google Scholar] [CrossRef]
- Manfreda, A.; Ljubi, K.; Groznik, A. Autonomous Vehicles in the Smart City Era: An Empirical Study of Adoption Factors Important for Millennials. Int. J. Inf. Manage. 2021, 58, 102050. [Google Scholar] [CrossRef]
- Makkar, A. SecureEngine: Spammer Classification in Cyber Defence for Leveraging Green Computing in Sustainable City. Sustain. Cities Soc. 2022, 79, 103658. [Google Scholar] [CrossRef]
- Rahouti, M.; Xiong, K.; Xin, Y. Secure Software-Defined Networking Communication Systems for Smart Cities: Current Status, Challenges, and Trends. IEEE Access 2021, 9, 12083–12113. [Google Scholar] [CrossRef]
- Sharma, R.; Arya, R. A Secure Authentication Technique for Connecting Different IoT Devices in the Smart City Infrastructure. Cluster Comput. 2022, 25, 2333–2349. [Google Scholar] [CrossRef]
- Shen, J.; Liu, D.; Sun, X.; Wei, F.; Xiang, Y. Efficient Cloud-Aided Verifiable Secret Sharing Scheme with Batch Verification for Smart Cities. Futur. Gener. Comput. Syst. 2020, 109, 450–456. [Google Scholar] [CrossRef]
- Li, D.; Deng, L.; Lee, M.; Wang, H. IoT Data Feature Extraction and Intrusion Detection System for Smart Cities Based on Deep Migration Learning. Int. J. Inf. Manage. 2019, 49, 533–545. [Google Scholar] [CrossRef]
- Li, D.; Deng, L.; Liu, W.; Su, Q. Improving Communication Precision of IoT through Behavior-Based Learning in Smart City Environment. Futur. Gener. Comput. Syst. 2020, 108, 512–520. [Google Scholar] [CrossRef]
- Lim, Y.; Edelenbos, J.; Gianoli, A. Smart Energy Transition: An Evaluation of Cities in South Korea. Informatics 2019, 6, 50. [Google Scholar] [CrossRef]
- Xu, C.; Lin, H.; Wu, Y.; Guo, X.; Lin, W. An SDNFV-Based DDoS Defense Technology for Smart Cities. IEEE Access 2019, 7, 137856–137874. [Google Scholar] [CrossRef]
- Subakti, P.; Putra, Y.H. Integration of TOGAF 9.1 ADM in Enterprise Architecture Smart City Design in the Tourism Domain with ISO 27001. IOP Conf. Ser. Mater. Sci. Eng. 2020, 879, 012029. [Google Scholar] [CrossRef]
- Bawany, N.Z.; Shamsi, J.A. SEAL: SDN Based Secure and Agile Framework for Protecting Smart City Applications from DDoS Attacks. J. Netw. Comput. Appl. 2019, 145, 102381. [Google Scholar] [CrossRef]
- Basmi, W.; Boulmakoul, A.; Karim, L.; Lbath, A. Modern Approach to Design a Distributed and Scalable Platform Architecture for Smart Cities Complex Events Data Collection. Procedia Comput. Sci. 2020, 170, 43–50. [Google Scholar] [CrossRef]
- Chatterjee, S.; Kar, A.K. Effects of Successful Adoption of Information Technology Enabled Services in Proposed Smart Cities of India. J. Sci. Technol. Policy Manag. 2018, 9, 189–209. [Google Scholar] [CrossRef]
- Chmielarz, W.; Zborowski, M.; Fandrejewska, A.; Atasever, M. The Contribution of Socio-Cultural Aspects of Smartphone Applications to Smart City Creation. Poland–Turkey Comparison. Energies 2021, 14, 2821. [Google Scholar] [CrossRef]
- Hassan, S.-U.; Shabbir, M.; Iqbal, S.; Said, A.; Kamiran, F.; Nawaz, R.; Saif, U. Leveraging Deep Learning and SNA Approaches for Smart City Policing in the Developing World. Int. J. Inf. Manage. 2021, 56, 102045. [Google Scholar] [CrossRef]
- Colla, M.; Santos, G.D. Public Safety Decision-Making in the Context of Smart and Sustainable Cities. Procedia Manuf. 2019, 39, 1937–1945. [Google Scholar] [CrossRef]
- Sinaeepourfard, A.; Garcia, J.; Masip-Bruin, X.; Marin-Tordera, E. Data Preservation through Fog-to-Cloud (F2C) Data Management in Smart Cities. In Proceedings of the 2018 IEEE 2nd International Conference on Fog and Edge Computing (ICFEC); IEEE, May 2018; pp. 1–9.
- Yandri, E.; Hendroko Setyobudi, R.; Susanto, H.; Abdullah, K.; Adhi Nugroho, Y.; Krido Wahono, S.; Wijayanto, F.; Nurdiansyah, Y. Conceptualizing Indonesia’s ICT-Based Energy Security Tracking System with Detailed Indicators from Smart City Extension. E3S Web Conf. 2020, 188, 00007. [Google Scholar] [CrossRef]
- Kumar Gandhi, B.M. A Prototype for IoT Based Car Parking Management System for Smart Cities. Indian J. Sci. Technol. 2016, 9. [Google Scholar] [CrossRef]
- Patil, B. Novel NDN Based Routing Protocol for IoT Empowered Savvy City Applications. J. Adv. Res. Dyn. Control Syst. 2020, 12, 235–243. [Google Scholar] [CrossRef]
- Rodriguez-Hernandez, M.A.; Gomez-Sacristan, A.; Gomez-Cuadrado, D. SimulCity: Planning Communications in Smart Cities. IEEE Access 2019, 7, 46870–46884. [Google Scholar] [CrossRef]
- Schleicher, J.M.; Vögler, M.; Inzinger, C.; Dustdar, S. Modeling and Management of Usage-Aware Distributed Datasets for Global Smart City Application Ecosystems. PeerJ Comput. Sci. 2017, 3, e115. [Google Scholar] [CrossRef]
- Yang, Y.-S.; Lee, S.-H.; Chen, G.-S.; Yang, C.-S.; Huang, Y.-M.; Hou, T.-W. An Implementation of High Efficient Smart Street Light Management System for Smart City. IEEE Access 2020, 8, 38568–38585. [Google Scholar] [CrossRef]
- Denker, A. Protection of Privacy and Personal Data in the Big Data Environment of Smart Cities. Int. Arch. Photogramm. Remote Sens. Spat. Inf. Sci. 2021, XLVI-4/W5, 181–186. [Google Scholar] [CrossRef]
- Huang, Z.; Peng, Y.; Li, J.; Tong, F.; Zhu, K.; Peng, L. Secrecy Enhancing of SSK Systems for IoT Applications in Smart Cities. IEEE Internet Things J. 2021, 8, 6385–6392. [Google Scholar] [CrossRef]
- Guo, Y.; Zou, K.; Liu, C.; Sun, Y. Study on the Evolutionary Game of Information Security Supervision in Smart Cities under Different Reward and Punishment Mechanisms. Discret. Dyn. Nat. Soc. 2022, 2022, 1–14. [Google Scholar] [CrossRef]
- Gopinath, M.P.; Tamizharasi, G.S.; Kavisankar, L.; Sathyaraj, R.; Karthi, S.; Aarthy, S.L.; Balamurugan, B. A Secure Cloud-Based Solution for Real-Time Monitoring and Management of Internet of Underwater Things (IOUT). Neural Comput. Appl. 2019, 31, 293–308. [Google Scholar] [CrossRef]
- Ali, Z.; Alzahrani, B.A.; Barnawi, A.; Al-Barakati, A.; Vijayakumar, P.; Chaudhry, S.A. TC-PSLAP: Temporal Credential-Based Provably Secure and Lightweight Authentication Protocol for IoT-Enabled Drone Environments. Secur. Commun. Networks 2021, 2021, 1–10. [Google Scholar] [CrossRef]
- Alam, R.G.G.; Ibrahim, H. CYBERSECURITY STRATEGY FOR SMART CITY IMPLEMENTATION. Int. Arch. Photogramm. Remote Sens. Spat. Inf. Sci. 2019, XLII-4/W17, 3–6. [Google Scholar] [CrossRef]
- Ayala-Ruiz, D.; Castillo Atoche, A.; Ruiz-Ibarra, E.; Osorio de la Rosa, E.; Vázquez Castillo, J. A Self-Powered PMFC-Based Wireless Sensor Node for Smart City Applications. Wirel. Commun. Mob. Comput. 2019, 2019, 1–10. [Google Scholar] [CrossRef]
- Sharma, S.; Ghanshala, K.K.; Mohan, S. Blockchain-Based Internet of Vehicles (IoV): An Efficient Secure Ad Hoc Vehicular Networking Architecture. In Proceedings of the 2019 IEEE 2nd 5G World Forum (5GWF); IEEE, September 2019; pp. 452–457.
- Pacheco, J.; Benitez, V.H.; Pan, Z. Security Framework for IoT End Nodes with Neural Networks. Int. J. Mach. Learn. Comput. 2019, 9, 381–386. [Google Scholar] [CrossRef]
- Peixoto, J.P.J.; Costa, D.G. Wireless Visual Sensor Networks for Smart City Applications:A Relevance-Based Approach for Multiple Sinks Mobility. Futur. Gener. Comput. Syst. 2017, 76, 51–62. [Google Scholar] [CrossRef]
- Satamraju, K.P.; Malarkodi, B. A Secured and Authenticated Internet of Things Model Using Blockchain Architecture. In Proceedings of the 2019 TEQIP III Sponsored International Conference on Microwave Integrated Circuits, Photonics and Wireless Networks (IMICPW); IEEE, May 2019; pp. 19–23.
- Puliafito, A.; Tricomi, G.; Zafeiropoulos, A.; Papavassiliou, S. Smart Cities of the Future as Cyber Physical Systems: Challenges and Enabling Technologies. Sensors 2021, 21, 3349. [Google Scholar] [CrossRef]
- Turchet, L.; Fazekas, G.; Lagrange, M.; Ghadikolaei, H.S.; Fischione, C. The Internet of Audio Things: State of the Art, Vision, and Challenges. IEEE Internet Things J. 2020, 7, 10233–10249. [Google Scholar] [CrossRef]
- Gao, W.; Yu, W.; Liang, F.; Hatcher, W.G.; Lu, C. Privacy-Preserving Auction for Big Data Trading Using Homomorphic Encryption. IEEE Trans. Netw. Sci. Eng. 2020, 7, 776–791. [Google Scholar] [CrossRef]
- Hassan, M.; Jincai, C.; Iftekhar, A.; Cui, X. Future of the Internet of Things Emerging with Blockchain and Smart Contracts. Int. J. Adv. Comput. Sci. Appl. 2020, 11. [Google Scholar] [CrossRef]
- Kamaldeep; Dutta, M.; Granjal, J. Towards a Secure Internet of Things: A Comprehensive Study of Second Line Defense Mechanisms. IEEE Access 2020, 8, 127272–127312. [Google Scholar] [CrossRef]
- Jararweh, Y.; Al-Ayyoub, M.; Al-Zoubi, D.; Benkhelifa, E. An Experimental Framework for Future Smart Cities Using Data Fusion and Software Defined Systems: The Case of Environmental Monitoring for Smart Healthcare. Futur. Gener. Comput. Syst. 2020, 107, 883–897. [Google Scholar] [CrossRef]
- Karthick Raghunath, K.M.; Koti, M.S.; Sivakami, R.; Vinoth Kumar, V.; NagaJyothi, G.; Muthukumaran, V. Utilization of IoT-Assisted Computational Strategies in Wireless Sensor Networks for Smart Infrastructure Management. Int. J. Syst. Assur. Eng. Manag. 2022. [Google Scholar] [CrossRef]
- North American Electric Realiability Corporation-NERC Annual Report; 2019; Vol. 61.
- Poleto, T.; de Oliveira, R.C.P.; da Silva, A.L.B.; de Carvalho, V.D.H. Using Fuzzy Cognitive Map Approach for Assessing Cybersecurity for Telehealth Scenario. In; 2020; pp. 828–837.
- Rahim, N.H.A.; Hamid, S.; Kiah, L.M.; Shamshirband, S.; Furnell, S. A Systematic Review of Approaches to Assessing Cybersecurity Awareness. Kybernetes 2015, 44, 606–622. [Google Scholar] [CrossRef]
- Hao, S.; Wang, W.; Yan, Y.; Bruzzone, L. Class-Wise Dictionary Learning for Hyperspectral Image Classification. Neurocomputing 2017, 220, 121–129. [Google Scholar] [CrossRef]
- Molzahn, D.K.; Wang, J. Detection and Characterization of Intrusions to Network Parameter Data in Electric Power Systems. IEEE Trans. Smart Grid 2019, 10, 3919–3928. [Google Scholar] [CrossRef]
- Kott, A.; Alberts, D.S.; Wang, C. Will Cybersecurity Dictate the Outcome of Future Wars. Computer 2015, 48, 98–101. [Google Scholar] [CrossRef]
- Wang, X.; Luo, H.; Qin, X.; Feng, J.; Gao, H.; Feng, Q. Evaluation of Performance and Impacts of Maternal and Child Health Hospital Services Using Data Envelopment Analysis in Guangxi Zhuang Autonomous Region, China: A Comparison Study among Poverty and Non-Poverty County Level Hospitals. Int. J. Equity Health 2016, 15. [Google Scholar] [CrossRef]
- Liu, M.; Li, K.; Chen, T. Security Testing of Web Applications: A Search-Based Approach for Detecting SQL Injection Vulnerabilities. In Proceedings of the GECCO 2019 Companion - Proceedings of the 2019 Genetic and Evolutionary Computation Conference Companion; 2019; pp. 417–418.
- Liu, M.; Li, K.; Chen, T. Security Testing of Web Applications. In In Proceedings of the Proceedings of the Genetic and Evolutionary Computation Conference Companion on - GECCO ’19; ACM Press: New York, NY, USA, 2019; pp. 417–418. [Google Scholar]
- Liu, N.; Zhang, J.; Liu, W. A Security Mechanism of Web Services-Based Communication for Wind Power Plants. IEEE Trans. Power Deliv. 2008, 23, 1930–1938. [Google Scholar] [CrossRef]
- Feng, N.; Wang, H.J.; Li, M. A Security Risk Analysis Model for Information Systems: Causal Relationships of Risk Factors and Vulnerability Propagation Analysis. Inf. Sci. 2014, 256, 57–73. [Google Scholar] [CrossRef]
- Farley, R.; Wang, X. Exploiting VoIP Softphone Vulnerabilities to Disable Host Computers: Attacks and Mitigation. Int. J. Crit. Infrastruct. Prot. 2014, 7, 141–154. [Google Scholar] [CrossRef]
- Ten, C.W.; Liu, C.C.; Manimaran, G. Vulnerability Assessment of Cybersecurity for SCADA Systems. IEEE Trans. Power Syst. 2008, 23, 1836–1846. [Google Scholar] [CrossRef]
- Fournaris, A.P.; Fraile, L.P.; Koufopavlou, O. Exploiting Hardware Vulnerabilities to Attack Embedded System Devices: A Survey of Potent Microarchitectural Attacks. Electron. 2017, 6. [Google Scholar] [CrossRef]
- Kao, D.Y.; Wang, S.J.; Fu-Yuan Huang, F. SoTE: Strategy of Triple-E on Solving Trojan Defense in Cyber-Crime Cases. Comput. Law Secur. Rev. 2010, 26, 52–60. [Google Scholar] [CrossRef]
- Mimo, E.M.; McDaniel, T. 3D Privacy Framework: The Citizen Value Driven Privacy Framework. In Proceedings of the 2021 IEEE International Smart Cities Conference (ISC2); IEEE, September 7 2021; pp. 1–7.
- Hu, G.; Xiao, D.; Xiang, T.; Bai, S.; Zhang, Y. A Compressive Sensing Based Privacy Preserving Outsourcing of Image Storage and Identity Authentication Service in Cloud. Inf. Sci. 2017, 387, 132–145. [Google Scholar] [CrossRef]
- Foroutan, S.A.; Salmasi, F.R. Detection of False Data Injection Attacks against State Estimation in Smart Grids Based on a Mixture Gaussian Distribution Learning Method. IET Cyber-Physical Syst. Theory Appl. 2017, 2, 161–171. [Google Scholar] [CrossRef]
- Alami, H.; Gagnon, M.-P.; Ag Ahmed, M.A.; Fortin, J.-P. Digital Health: Cybersecurity Is a Value Creation Lever, Not Only a Source of Expenditure. Heal. Policy Technol. 2019, 8, 319–321. [Google Scholar] [CrossRef]
- Paul, J.A.; Wang, X. (Jocelyn) Socially Optimal IT Investment for Cybersecurity. Decis. Support Syst. 2019, 122, 113069. [Google Scholar] [CrossRef]
- Enoch, S.Y.; Ge, M.; Hong, J.B.; Alzaid, H.; Kim, D.S. A Systematic Evaluation of Cybersecurity Metrics for Dynamic Networks. Comput. Networks 2018, 144, 216–229. [Google Scholar] [CrossRef]
- Zhang, J.; Dong, Q. Efficient ID-Based Public Auditing for the Outsourced Data in Cloud Storage. Inf. Sci. 2016, 343–344, 1–14. [Google Scholar] [CrossRef]
- Xin, Y.; Kong, L.; Liu, Z.; Chen, Y.; Li, Y.; Zhu, H.; Gao, M.; Hou, H.; Wang, C. Machine Learning and Deep Learning Methods for Cybersecurity. IEEE Access 2018, 6, 35365–35381. [Google Scholar] [CrossRef]
- Montesdioca, G.P.Z.; Maçada, A.C.G. Measuring User Satisfaction with Information Security Practices. Comput. Secur. 2015, 48, 267–280. [Google Scholar] [CrossRef]
- Ten, C.W.; Ginter, A.; Bulbul, R. Cyber-Based Contingency Analysis. IEEE Trans. Power Syst. 2016, 31, 3040–3050. [Google Scholar] [CrossRef]
- Hong, J.; Liu, C.C.; Govindarasu, M. Integrated Anomaly Detection for Cyber Security of the Substations. IEEE Trans. Smart Grid 2014, 5, 1643–1653. [Google Scholar] [CrossRef]
- Hong, J.; Nuqui, R.F.; Kondabathini, A.; Ishchenko, D.; Martin, A. Cyber Attack Resilient Distance Protection and Circuit Breaker Control for Digital Substations. IEEE Trans. Ind. Informatics 2019, 15, 4332–4341. [Google Scholar] [CrossRef]
- Sterlini, P.; Massacci, F.; Kadenko, N.; Fiebig, T.; Van Eeten, M. Governance Challenges for European Cybersecurity Policies: Stakeholder Views. IEEE Secur. Priv. 2020, 18, 46–54. [Google Scholar] [CrossRef]
- Charlet, K.; King, H. The Future of Cybersecurity Policy. IEEE Secur. Priv. 2020, 18, 8–10. [Google Scholar] [CrossRef]
- Vattapparamban, E.; Güvenç, I.; Yurekli, A.I.; Akkaya, K.; Uluaǧaç, S. Drones for Smart Cities: Issues in Cybersecurity, Privacy, and Public Safety. 2016 Int. Wirel. Commun. Mob. Comput. Conf. IWCMC 2016 2016, 216–221. [Google Scholar] [CrossRef]
- Khatoun, R.; Zeadally, S. Cybersecurity and Privacy Solutions in Smart Cities. IEEE Commun. Mag. 2017, 55, 51–59. [Google Scholar] [CrossRef]
- Zimmermann, V.; Renaud, K. Moving from a ‘human-as-Problem” to a ‘human-as-Solution” Cybersecurity Mindset. Int. J. Hum. Comput. Stud. 2019, 131, 169–187. [Google Scholar] [CrossRef]
- Woods, D.W.; Moore, T. Does Insurance Have a Future in Governing Cybersecurity? IEEE Secur. Priv. 2020, 18, 21–27. [Google Scholar] [CrossRef]
- Maddux, J.E.; Rogers, R.W. Protection Motivation and Self-Efficacy: A Revised Theory of Fear Appeals and Attitude Change. J. Exp. Soc. Psychol. 1983, 19, 469–479. [Google Scholar] [CrossRef]
- Biswas, K.; Muthukkumarasamy, V. Securing Smart Cities Using Blockchain Technology. In Proceedings of the 2016 IEEE 18th International Conference on High Performance Computing and Communications; IEEE 14th International Conference on Smart City; IEEE 2nd International Conference on Data Science and Systems (HPCC/SmartCity/DSS); IEEE, December 2016; pp. 1392–1393.
- Zhang, K.; Ni, J.; Yang, K.; Liang, X.; Ren, J.; Shen, X.S. Security and Privacy in Smart City Applications: Challenges and Solutions. IEEE Commun. Mag. 2017, 55, 122–129. [Google Scholar] [CrossRef]
- Sivanathan, A.; Gharakheili, H.H.; Loi, F.; Radford, A.; Wijenayake, C.; Vishwanath, A.; Sivaraman, V. Classifying IoT Devices in Smart Environments Using Network Traffic Characteristics. IEEE Trans. Mob. Comput. 2019, 18, 1745–1759. [Google Scholar] [CrossRef]
- Sharma, P.K.; Moon, S.Y.; Park, J.H. Block-VN: A Distributed Blockchain Based Vehicular Network Architecture in Smart City. J. Inf. Process. Syst. 2017, 13, 184–195. [Google Scholar] [CrossRef]
- Khatoun, R.; Zeadally, S. Smart Cities: Concepts, Architectures, Research Opportunities. Commun. ACM 2016, 59, 46–57. [Google Scholar] [CrossRef]
- Djahel, S.; Doolan, R.; Muntean, G.-M.; Murphy, J. A Communications-Oriented Perspective on Traffic Management Systems for Smart Cities: Challenges and Innovative Approaches. IEEE Commun. Surv. Tutorials 2015, 17, 125–151. [Google Scholar] [CrossRef]
- Sharma, P.K.; Park, J.H. Blockchain Based Hybrid Network Architecture for the Smart City. Futur. Gener. Comput. Syst. 2018, 86, 650–655. [Google Scholar] [CrossRef]
- Angelidou, M. The Role of Smart City Characteristics in the Plans of Fifteen Cities. J. Urban Technol. 2017, 24, 3–28. [Google Scholar] [CrossRef]
- Rathore, M.M.; Paul, A.; Hong, W.-H.; Seo, H.; Awan, I.; Saeed, S. Exploiting IoT and Big Data Analytics: Defining Smart Digital City Using Real-Time Urban Data. Sustain. Cities Soc. 2018, 40, 600–610. [Google Scholar] [CrossRef]
- Qiu, T.; Chen, N.; Li, K.; Qiao, D.; Fu, Z. Heterogeneous Ad Hoc Networks: Architectures, Advances and Challenges. Ad Hoc Networks 2017, 55, 143–152. [Google Scholar] [CrossRef]
- Petit, J.; Shladover, S.E. Potential Cyberattacks on Automated Vehicles. IEEE Trans. Intell. Transp. Syst. 2015, 16, 546–556. [Google Scholar] [CrossRef]
- Nepomuceno, T.C.C.; Silva, W.M.N.; Nepomuceno, K.T.C.; Barros, I.K.F. A DEA-Based Complexity of Needs Approach for Hospital Beds Evacuationduring the COVID-19 Outbreak. J. Healthc. Eng. 2020, 2020. [Google Scholar] [CrossRef]
- Daraio, C.; Kerstens, K.; Nepomuceno, T.; Sickles, R.C. Empirical Surveys of Frontier Applications: A Meta-Review. Int. Trans. Oper. Res. 2020, 27, 709–738. [Google Scholar] [CrossRef]
- Daraio, C.; Kerstens, K.H.J.; Nepomuceno, T.C.C.; Sickles, R. Productivity and Efficiency Analysis Software: An Exploratory Bibliographical Survey of the Options. J. Econ. Surv. 2019, 33, 85–100. [Google Scholar] [CrossRef]
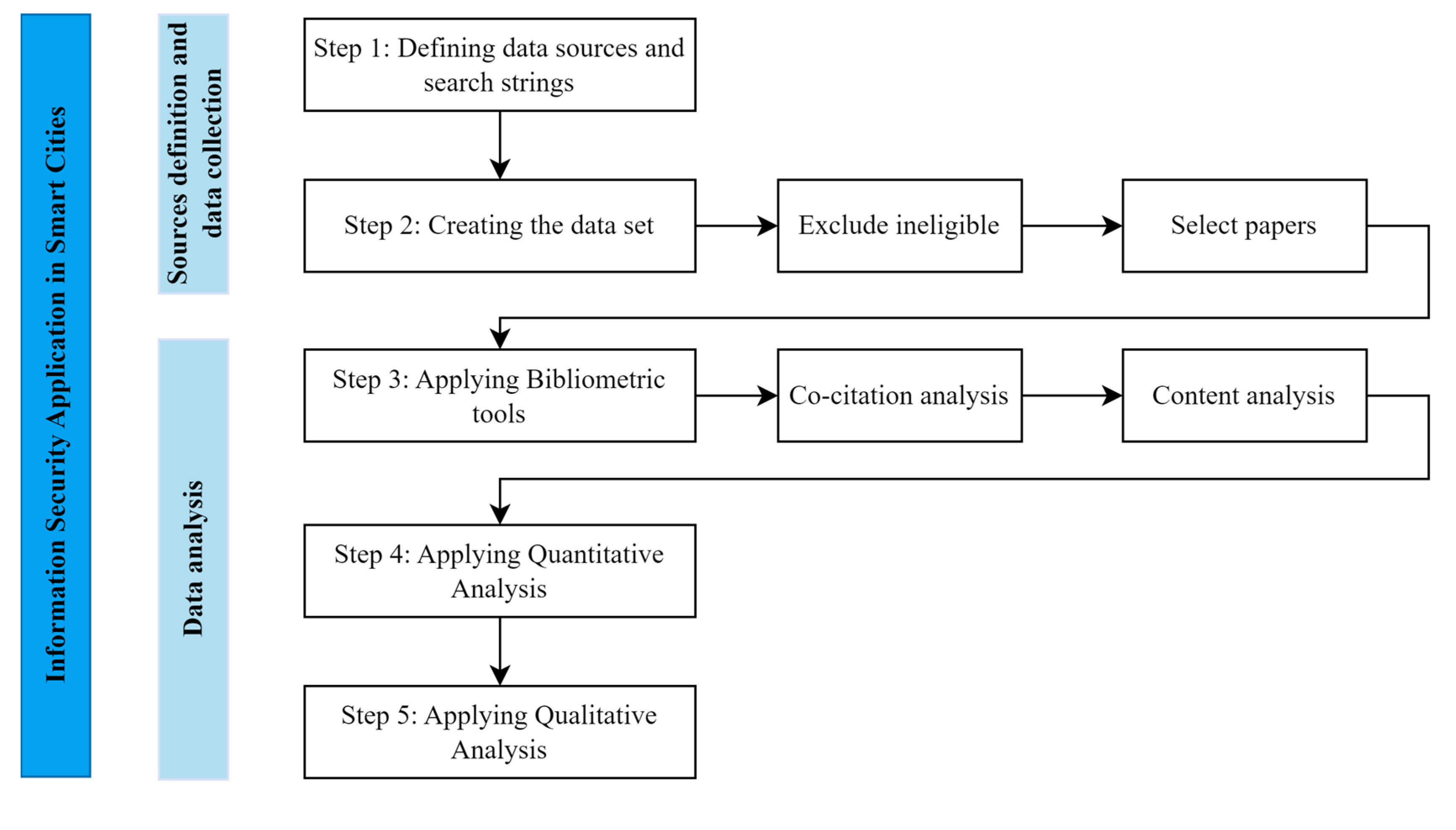
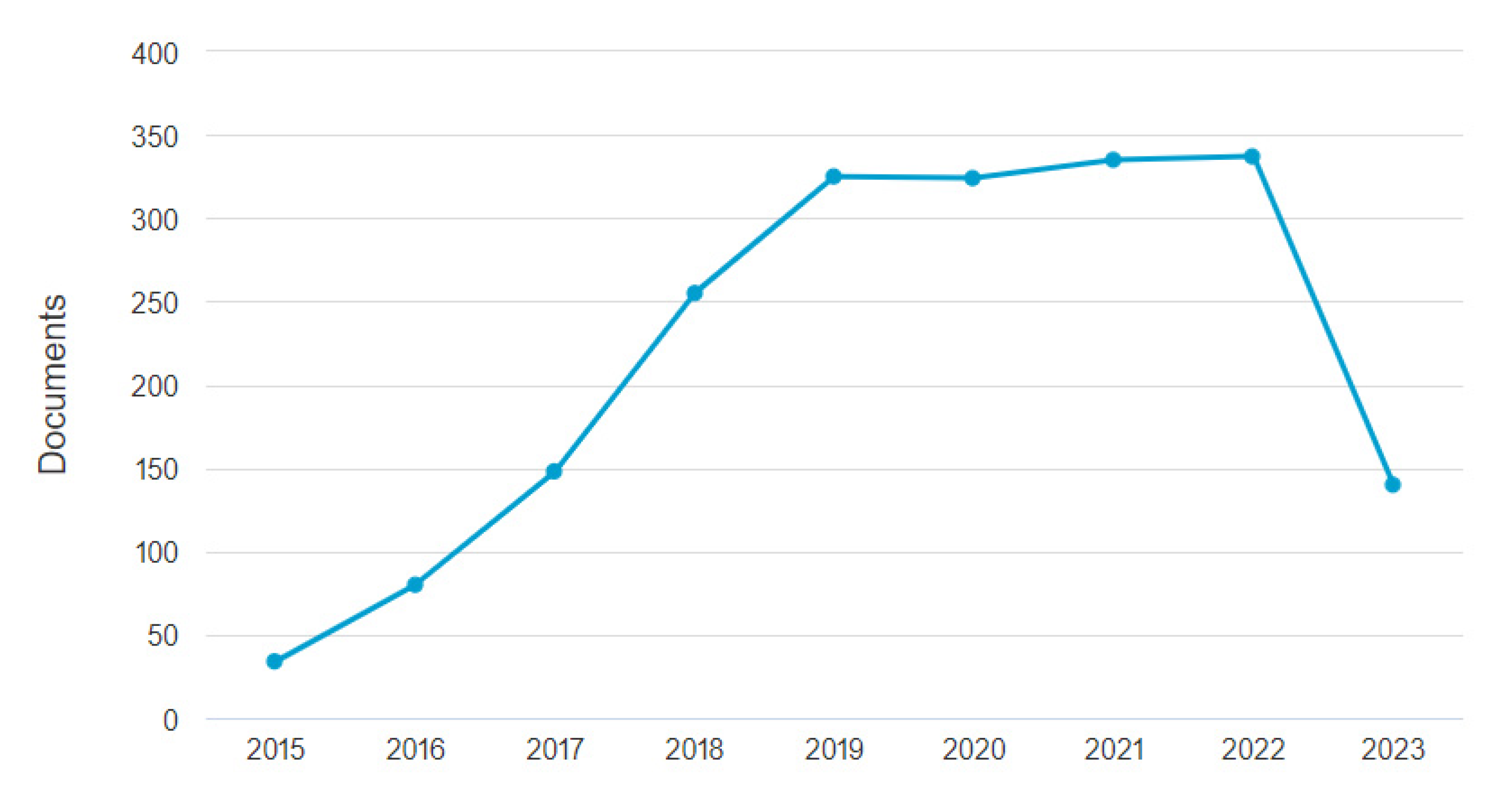
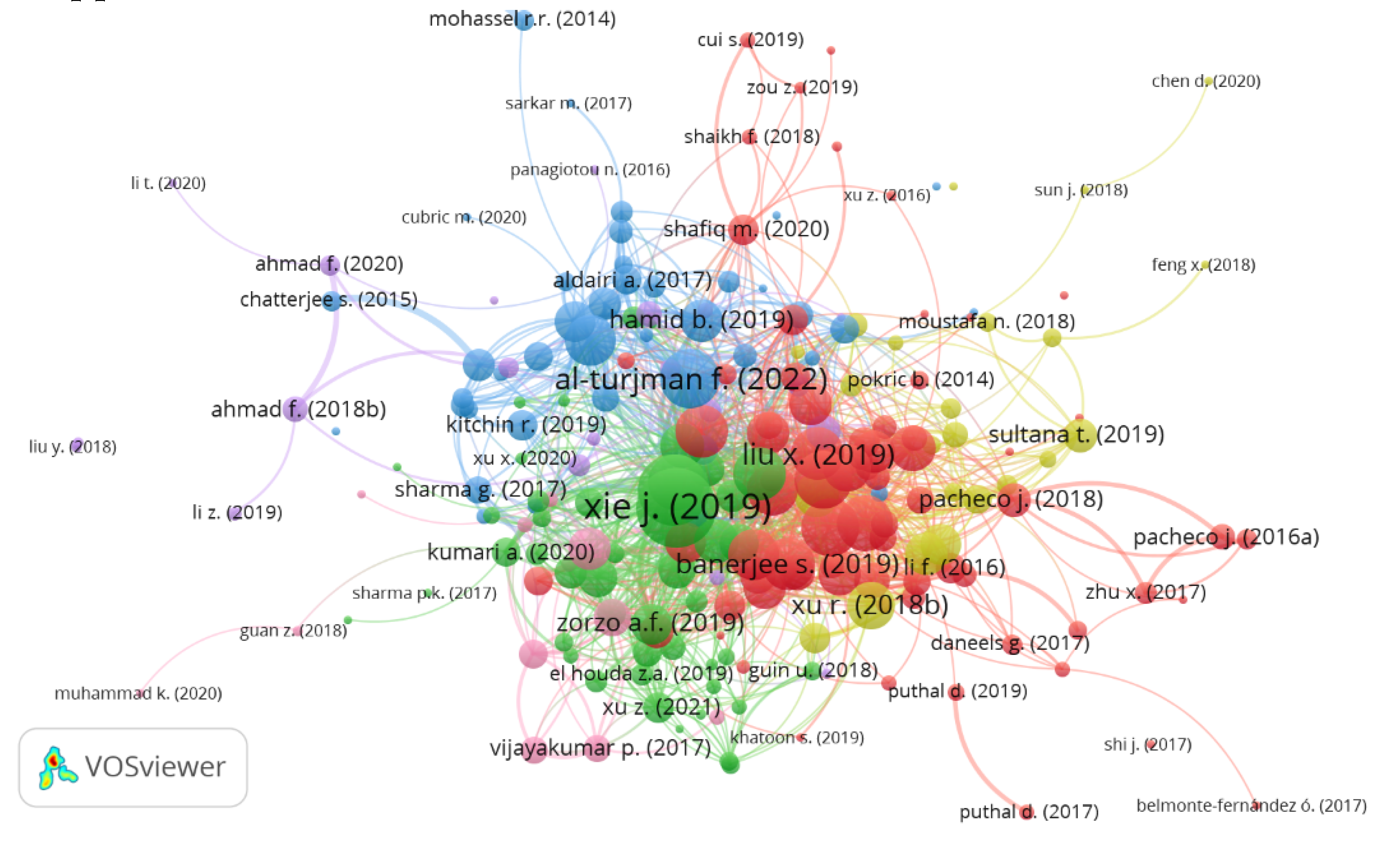
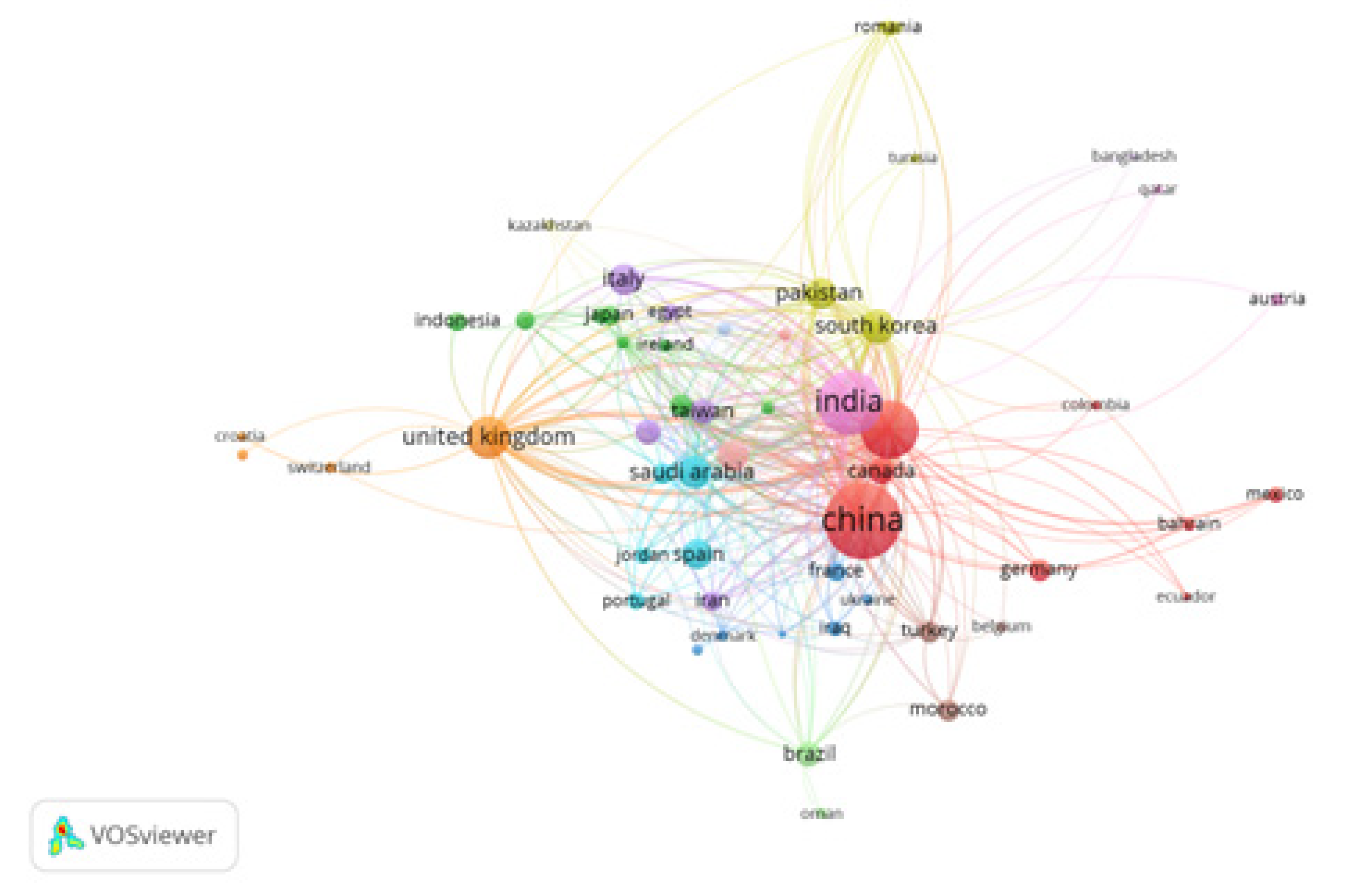
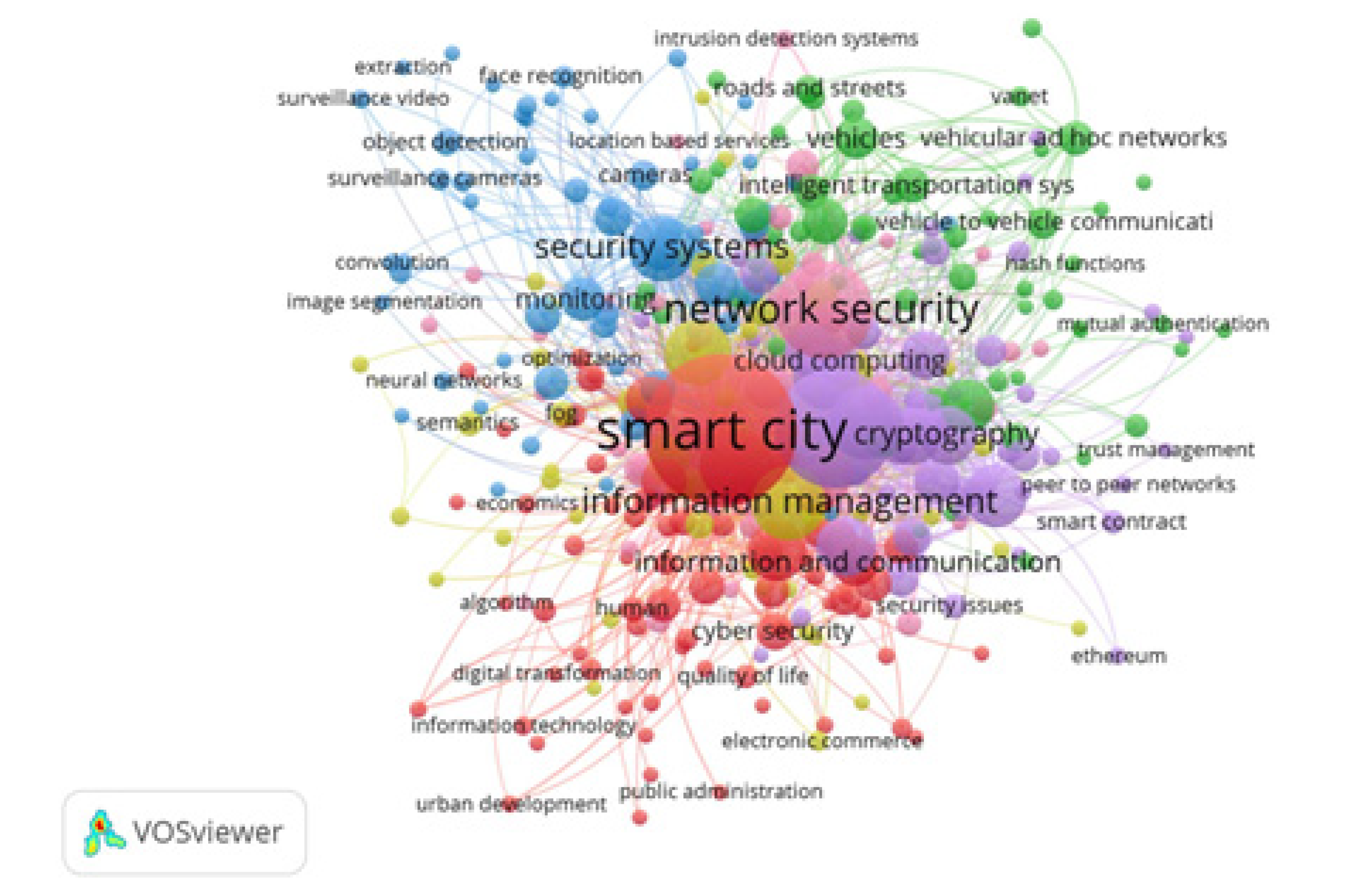
| Area | Risk Domain | References |
|---|---|---|
| Cloud computing (platform of services over the internet, accessible by people and business companies) | Cloud threats | [69,70,71,72] |
| Custodianship of keys | [73] | |
| Security of data | [60,74,75,76,77] | |
| Security attacks | [75,78,79,79,80,81,82,83,84,85] | |
| Lack of a data privacy policy | [73,77,86,87,88,89,90,91,92] | |
| Internet of Things (concerning devices to have an internet connection and that can communicate with the network independently of human action). | Attacks on IoT devices | [9,35,83,87,93,94,95,96] |
| Lack of effective access controls | [89,97,98,99,100,101,102,103,104] | |
| Protecting sensitive data | [32,105,106,107] | |
| Botnet activities | [35,108,109,110] | |
| Privileged user access | [89,99,111] | |
| Data interpretation (essentially the representation of complex data and understand trends and follow patterns) | Security reports | [112,113,114] |
| Discover sensitive data | [115,116,117,118,119] | |
| Errors and inconsistency Decision | [120,121,122] | |
| Privacy violations | [123,124,125,126,127] | |
| Smartphones (smart communication mobile devices) | Security of data | [128,129,130,131] |
| Smartphone threats | [132,133] | |
| Protecting sensitive data | [134] | |
| Lack of privacy of stakeholders | [135,136] |
| Cluster Number / Color | Cluster name | Size | Representative articles |
|---|---|---|---|
| Cluster 1 / Red | Smart Power Grid in Smart Cities | 324 | [3,55,71,83,99,111,139,140,141,142,143,144,145,146,147,148,149,150,151,152,153,154,155,156,157,158,159,160,161,162,163,164,165,166,167,168,169,169,170,170,171,172,173,174,175,176,177,178,179,180,181,182,183,184,185,186,187,188,189,190,191,192,193,194,195,196,197,198,199,200,201,202,203,204] |
| Cluster 2 / Green | Authentication Smart Cities | 241 | [51,63,85,91,93,94,155,205,206,207,208,209,210,211,212,213,214,215,216,217,218,219,220,221,222,223,224,225,226,227,228,229,230,231,232,233,234,235,236,237,238,239,240,241,242,243,244,245,246,247,248,249,250,251,252,253,254,255,256,257,258,259,260,261,262] |
| Cluster 3 / Blue | Cyber-attack in Smart Cities | 153 | [1,4,263,264,265,266,267,268,269,270,271,272,273,274,275,276,277,278,279,280,281,282,283] |
| Cluster 4 / Yellow | Security platform for vehicular Smart cities | 121 | [60,60,284,285,286,287,288,289,290,291,292,293,294,295,296,297,298,299] |
| Cluster 5 / Pink | Evaluation of threats to cybersecurity | 99 | [6,54,300,301,302,303,304,305,306,307,308,309,310,311,312,313,314] |
| Cluster 6 / Purple | Cybersecurity and society | 78 | [315,316,317,318,319,320,321,322,323,324] |
| Index | Author | Total of citations | Title | Reference |
|---|---|---|---|---|
| 1 | Farahani et. al | 1001 | Towards fog-driven IoT eHealth: Promises and challenges of IoT in medicine and healthcare | [144] |
| 2 | Rathore et. al | 996 | Urban planning and building smart cities based on the Internet of Things using Big Data analytics | [54] |
| 3 | Dagher et. al | 746 | Ancile: Privacy-preserving framework for access control and interoperability of electronic health records using blockchain technology | [101] |
| 4 | Biswas et. al | 746 | Securing Smart Cities Using Blockchain Technology | [359] |
| 5 | Elmaghraby et. al | 640 | Cyber security challenges in Smart Cities: Safety, security and privacy | [15] |
| 6 | Xie et. al | 630 | A Survey of Blockchain Technology Applied to Smart Cities: Research Issues and Challenges | [241] |
| 7 | Zhang et. al | 620 | Security and Privacy in Smart City Applications: Challenges and Solutions | [360] |
| 8 | Sivanathan et. al | 579 | Classifying IoT Devices in Smart Environments Using Network Traffic Characteristics | [361] |
| 9 | Sharma et.al | 500 | Block-VN: A Distributed Blockchain Based Vehicular Network Architecture in Smart City | [362] |
| 10 | Khatoun et. al | 473 | Smart cities: concepts, architectures, research opportunities | [363] |
| 11 | Djahel et. al | 436 | A Communications-Oriented Perspective on Traffic Management Systems for Smart Cities: Challenges and Innovative Approaches | [364] |
| 12 | Singh et. al | 429 | BlockIoTIntelligence: A Blockchain-enabled Intelligent IoT Architecture with Artificial Intelligence | [230] |
| 13 | Sharma et. al | 411 | Blockchain based hybrid network architecture for the smart city | [365] |
| 14 | Angelidou et. al | 390 | The Role of Smart City Characteristics in the Plans of Fifteen Cities | [366] |
| 15 | Rathore et. al | 330 | Exploiting IoT and big data analytics: Defining Smart Digital City using real-time urban data | [367] |
| 16 | Memos et. al | 352 | An Efficient Algorithm for Media-based Surveillance System (EAMSuS) in IoT Smart City Framework | [177] |
| 17 | Aloqaily et. al | 353 | An intrusion detection system for connected vehicles in smart cities | [56] |
| 18 | Braun et. al | 307 | Security and privacy challenges in smart cities | [7] |
| 19 | Esposito et. al | 297 | Blockchain-based authentication and authorization for smart city applications | [213] |
| 20 | Qiu et. al | 215 | Heterogeneous ad hoc networks: Architectures, advances and challenges | [368] |
| Subject areas | Source | Impact Factor 2022 | # of article |
|---|---|---|---|
| Computer Science | Computers & Security | 5.6 | 262 |
| Future Generation Computer Systems | 7.5 | 712 | |
| IEEE Access | 3.9 | 139 | |
| IET Information Security | 1.4 | 23 | |
| Computer Communications | 6 | 323 | |
| IEEE Security and Privacy | 1.9 | 54 | |
| Computers in Human Behavior | 9.9 | 60 | |
| Information Technology and People | 4.4 | 63 | |
| International Journal of Communication Systems | 2.1 | 256 | |
| International Journal of Software Engineering and Knowledge Engineering | 0.9 | 12 | |
| Social Sciences | Computer Law and Security Review | 2.9 | 164 |
| Technological Forecasting and Social Change | 12 | 346 | |
| Public Administration Review | 8.3 | 13 | |
| Technology in Society | 9.2 | 145 | |
| Journal of Intellectual Capital | 6 | 64 | |
| Behaviour and Information Technology | 3.7 | 88 | |
| International Journal of Human Computer Studies | 5.4 | 27 | |
| Business Horizons | 7.4 | 58 | |
| International Journal of Accounting Information Systems | 4.6 | 12 | |
| Business, Management and Accounting | International Journal of Information Management | 21 | 130 |
| Government Information Quarterly | 7.8 | 157 | |
| Information Technology for Development | 4.261 | 47 | |
| European Journal of Operational Research | 6.363 | 33 | |
| Information Sciences | 8.1 | 131 | |
| Energy | Energies | 3.2 | 195 |
| Sustainability | 3.9 | 76 | |
| Energy Research & Social Science | 6.7 | 151 | |
| Journal of Cleaner Production | 11.1 | 465 |
| Method | Computer Science | Engineering | Mathematics | Social Sciences | Business, Management and Accounting | Total |
|---|---|---|---|---|---|---|
| Risk Management | 57 | 32 | - | 19 | 21 | 129 |
| Machine Learning | 48 | 17 | 7 | 9 | 11 | 101 |
| Game Theory | 28 | 17 | 9 | 8 | 2 | 64 |
| Neural Network | 17 | 15 | 4 | - | 5 | 41 |
| Data Mining | 25 | 5 | 2 | - | 5 | 37 |
| Deep-Learning | 18 | 7 | 3 | 1 | 2 | 33 |
| Blockchain | 17 | 8 | 3 | 2 | 3 | 33 |
| Fuzzy Theory | 16 | 6 | 5 | - | 2 | 29 |
| Bayesian game | 6 | 3 | 2 | 2 | 2 | 15 |
| Software-Defined Networking | 6 | 2 | 2 | - | 1 | 11 |
| Natural Language Processing | 4 | 2 | - | - | 1 | 7 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





