Submitted:
21 June 2023
Posted:
25 June 2023
You are already at the latest version
Abstract
Keywords:
1. Introduction
1.2. Blockchain features
- ◾
- Smart contracts: a controlled term using Blockchain technology used to describe program code in capable executing, and enforcing the negotiation and agreement& Regulations in automated process recorded in a computer language as an instruction of bank policy or central bank regulation’s. [3]
- ◾
- Hard Fork: Forcing method to update core software or business logic of Blockchain & to recover the Blockchain from any damage or cyber-attacks or transaction crimes a malicious user may illegally access private transaction data that significant attention because including transaction amount, account information, and balance due to public Blockchain is transparent and open [3]
1.3. Advantages of Blockchain
- ◾
- Group compliance can reduce fraud by strengthening its regulatory compliance example: after record stored in the ledger, it cannot only before a consensus.
- ◾
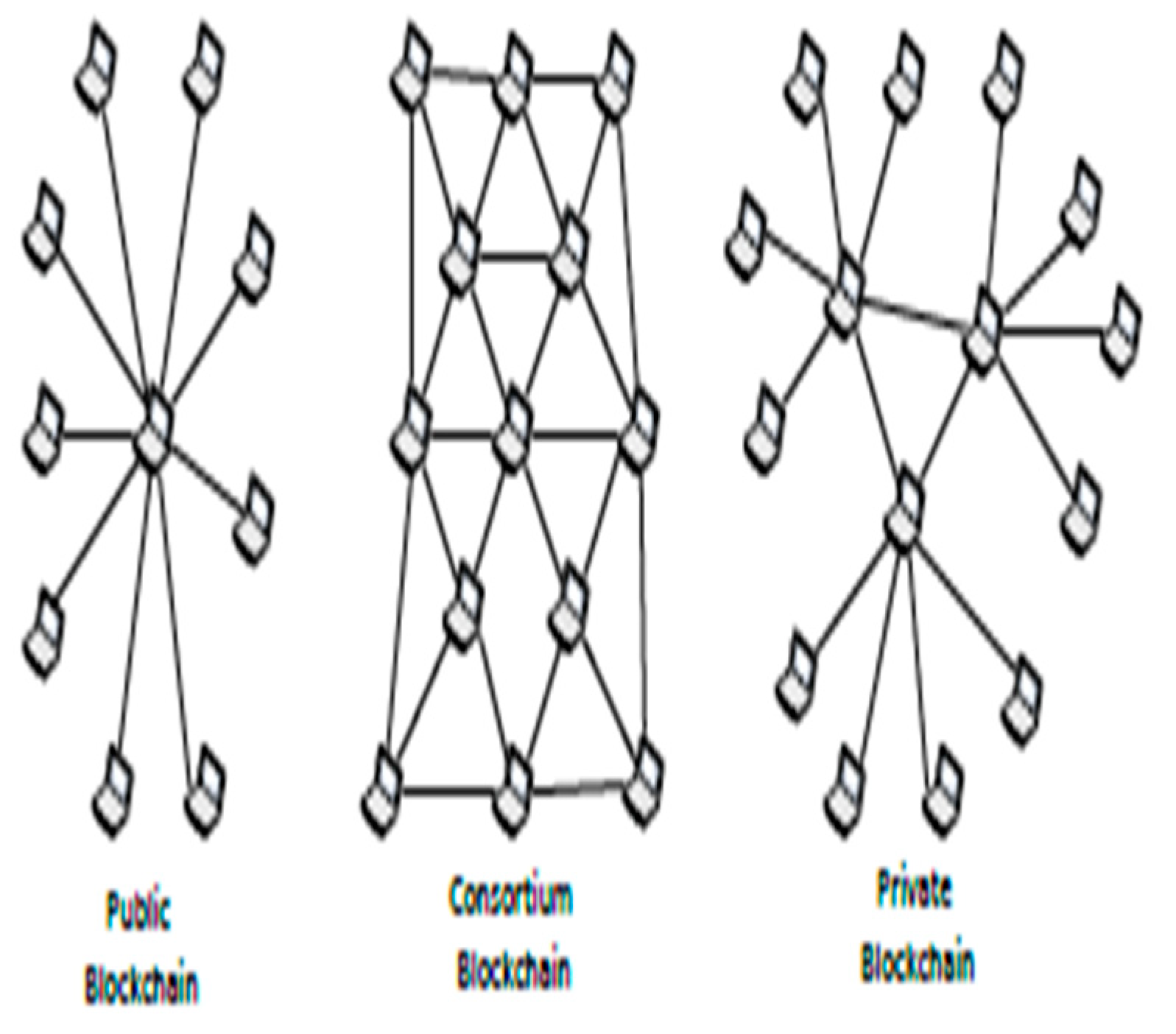
- Consortium Blockchain Build on decentralized networks, Blockchain Technology data would be complete accurate on time
- ◾
- All transactions will have timestamped using a cryptographic hash code, with unique signature 64-digit alpha-numeric it is recorded corresponding for every single transaction.
- ◾
- Blockchain Technology Not managed by only control center that not and there's no single point of failure regularly.
- ◾
- Blockchain is using technology peer-to-peer transaction which supports a decentralized concept.
- ◾
- Using Smart Contracts in Blockchain Technology gives it self-executed code commands which executed and stored on Blockchain.
- ◾
- All transactions are under shared ledger& Control of it by many control center that makes it transparent by any counterpart. [6]
1.4. Challenges and Barriers of Blockchain
- ◾
- Services costs are high and time critical is massive transaction it decrease by increasing number of miners /banks/ controls.
- ◾
- Blockchain have potential issue in the Blockchain and its ledger implementation the signatures that do not provide guarantee of the owner, hacker can modify and broadcasting a transaction again which can have broken the transaction confirmation.
- ◾
- Required amount of power resources.
- ◾
- Blockchain technology and its solutions require changes of existing legacy systems or reengineering it in order to incorporate.
- ◾
- It is new technology might lead to transformation or changes in organization structure, process, strategy, or culture. [7]
2. Background
3. Proposed approach
3.1. Outline This paper focuses on one aspect of This paper focuses on one aspect of banking.
- ◾
- Domain: are system boundary access permission or roles-scope.
- ◾
- Task: Tasks are activities or business banking processes.
- ◾
- Operation: there are many different banking operations like approve, reject, add, delete, modify…etc.
- ◾
- Authorization: like a Policies which are enforced by the system, sign not assigned to the same user.
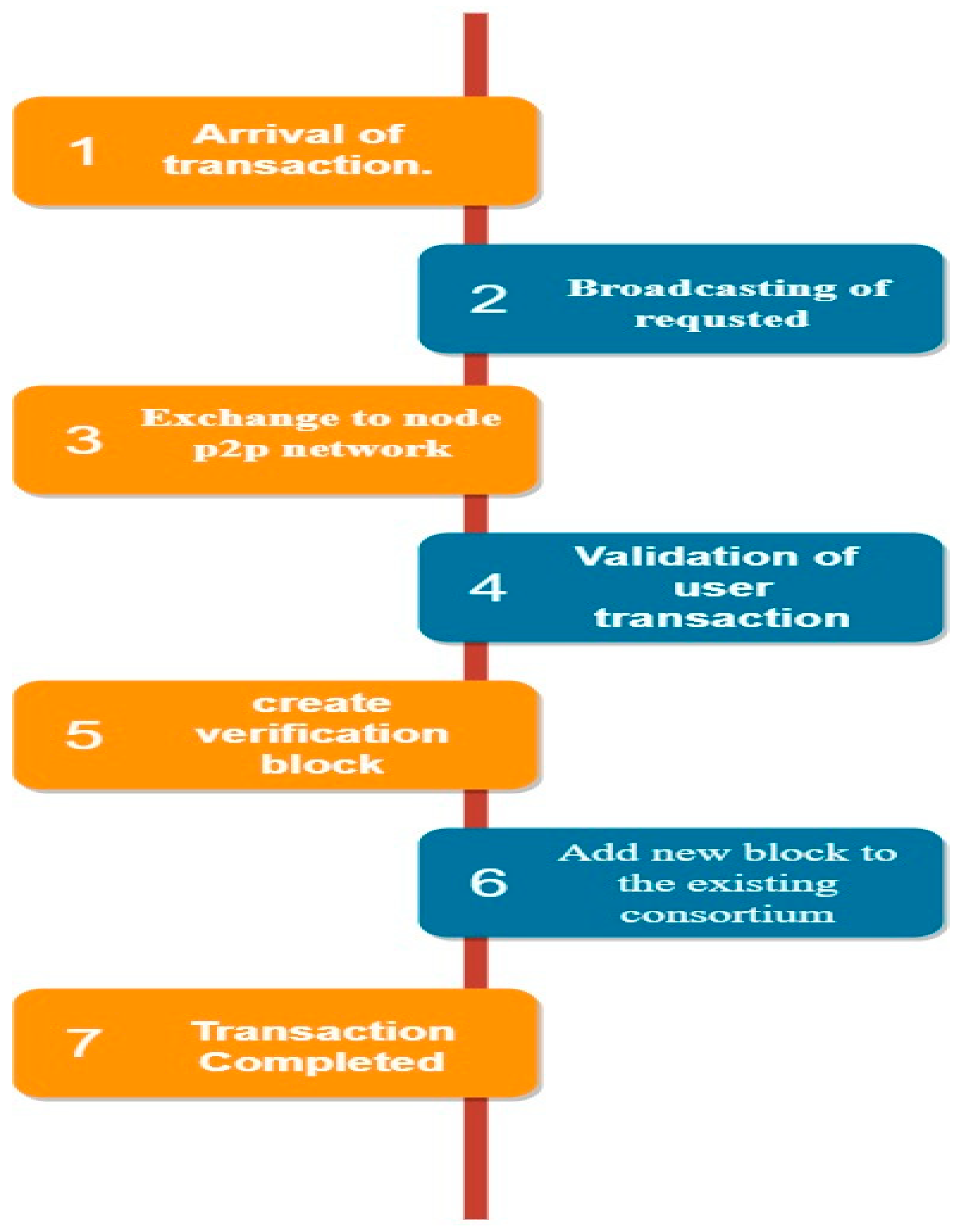
- The management layer: Issuers, verifiers, and agreement nodes are part of the administrative layer. When the clients first arrive to execute their registrations, the issuers authenticate them.
- The capacity layer:
| pseudocode |
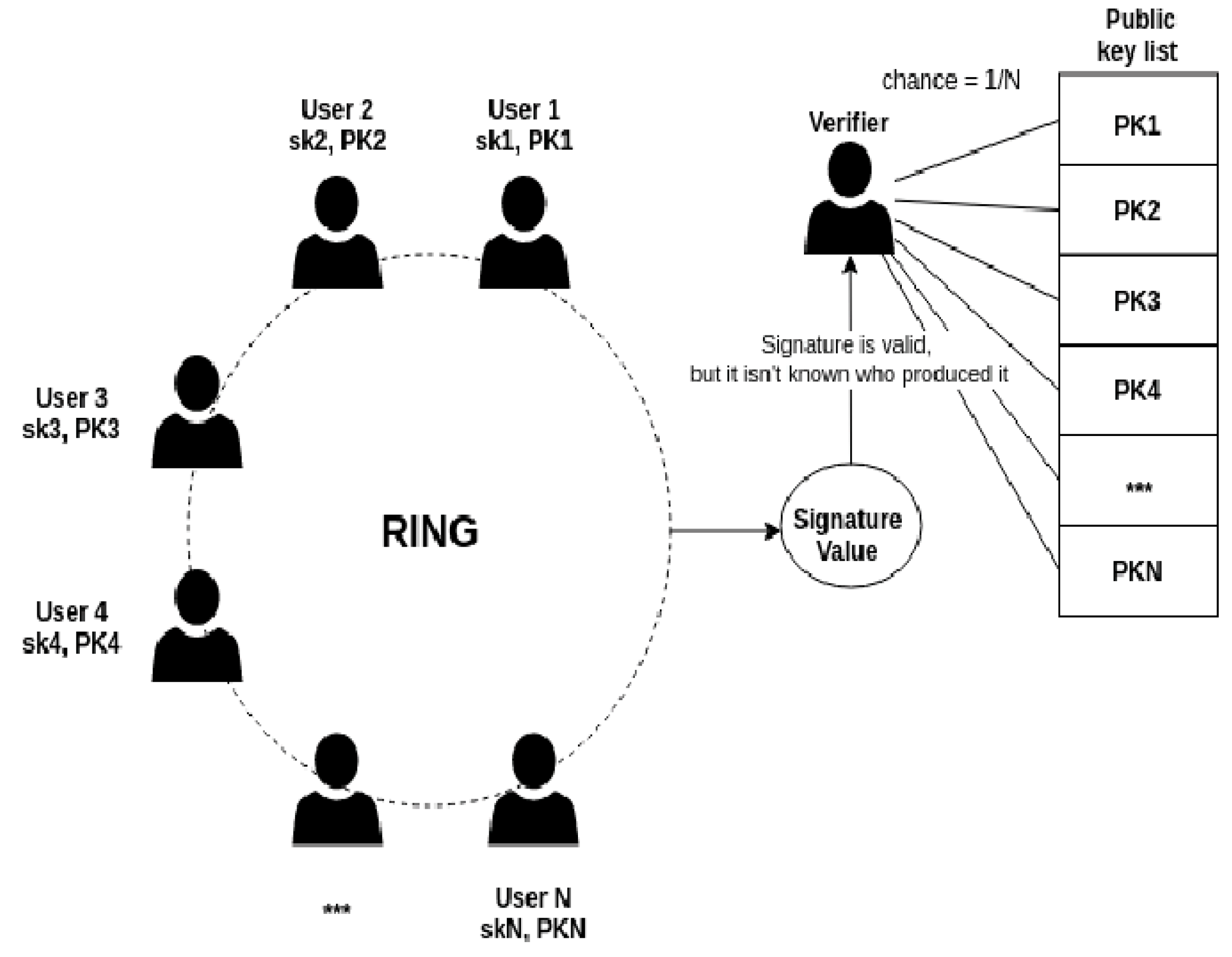
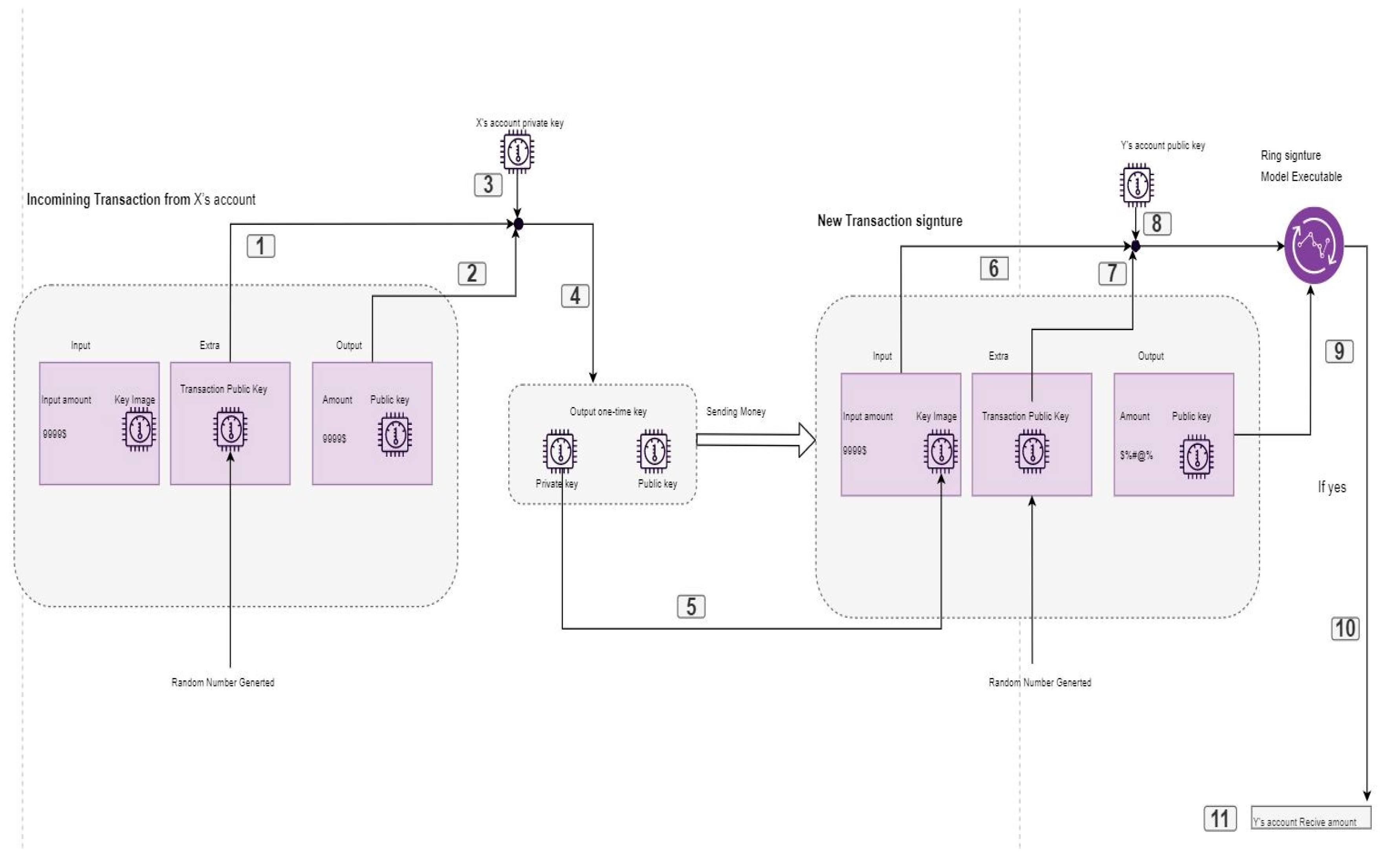
| m sign message R = {K1, K2, ..., Kn} kπ e private Kπ ∈ R. Hn and Hp, hash functions. RSBAC’Q’=1 verified else rejected 1. Compute K˜ = kπHp(R) 2. Create irrational values α ∈R Zq and r ∈R Zq for i ∈ {0, 1, ..., n} and i 6= π 3. Calculate cπ+1 = Hn(R, K, ˜ m, αG, αK˜ ) 4. For i = π + 1, π + 2, ..., n, 1, 2, ..., π − 1 c, n + 1 → 1 ci+1 = Hn(R, K, ˜ m, riG + ciKi , riHp(R) + ciK˜ ). 5. rπ = α − kπcπ (mod N) σ(m) = (c1, r1, ..., rn, K˜ ) -Signature confirmation For i = 1, 2, ..., n n + 1 → 1 z `i = riG + ciKi z ``i = riHp(R) + ciK˜ c `i+1 = Hn(R, K, ˜ m, zi `, zi `)Q==1 2. c`1 = c1 |
3.2. RSBACK group signature phase.
| Sign Equation |
| Ko = Hn(rKB1 , l)G + kB2G = (Hn(rKB1 , l) + kB2 )G ko = Hn(rKB1 , l) + kB2 |
Signature phase
- Proficiency and Flexibility: Since the majority of information privacy approaches rely on intricate cryptographic calculations, scaling them to accommodate big applications is inefficient and difficult. Later research aims to make these cryptographic systems less complicated and more productive.
- Effective Information Lifecycle Approach: To effectively describe the lifecycle of the information, a framework for data protection needs to be created. This system should be able to identify the phases, describe their security requirements, and accommodate modifications to the lifecycle. These phases may involve the gathering, the distribution, and the termination of the knowledge and resources contained in the framework.
4. Conclusion
- ◾
- Distributed Access Management.
- ◾
- more Information extracted conditionally assuring the same user privacy.
- ◾
- Dynamic and Active permission assignment.
- ◾
- authorization policies to support dynamic separation of duty.
- ◾
- Permission inheritance scope, eliminating the shortage of high management complexity.
- ◾
- Caused by inherited relationship in the traditional model that will save time.
- ◾
- Suitable for workflow and non-workflow systems.
- ◾
- A framework for the data security ought to be built to efficiently define the lifecycle of the information.
- ◾
- distinguish the phases, characterize their privacy prerequisites, and allow flexibility within the lifecycle changes.
- ◾
- These stages can include the securing, the sharing and the erasure of the information and the assets included within the framework.
- ◾
- Be that as it may, a systematic approach is still lost in most of the proposed privacy techniques.
- ◾
- By restrain services cost is and time that the transaction diminish it by expanding
- ◾
- number of trusted get to list of mineworkers /banks/ controls without change or changes in organization structure.
5. Future Work
- Study possibilities of the improving proposed approach to be extended approach for Hyper ledger Projects.
- Study possibilities of the proposed approach to be extended over distributed systems or other Blockchain platforms through hard frogs.
- Study possibilities of the proposed approach to be extended over Blockchains environments. Also, during implementation the following extensions re discovered to be useful.
- De-centralized management of permission assignment.
- There will be many policies in enterprise environment, and as a result it is important to manage authorization policies and optimize policy description.
References
- Sam Mire. Blockchain-use-cases-banking. Published at [Online].
- Archana JoshiA.survey on security and privacy issues of Blockchain technology.
- Blockchain Council, Blockchain Ecosystem. Published at [Online].
- Adam Bender, Jonathan Katz, Ruggero Morsell. Ring Signatures: Stronger De_nitions, and Constructions without Random Oracles.
- Tara Salman, Maede Zolanvari, Aiman Erbad, RajJain, Mohammed Samaka. Security Services Using Blockchains: A State of the Art Survey.
- Dubai 2018 Fintech Conference. “ Blockchain's Implications on FinTech Ecosystem & Innovation ”.
- Fran CasinoThomas K. Dasaklis Constantinos PatsakisNakamoto. literature review of Blockchain-based applications: Current status, classification and open issues.
- Thomas kitsantas1 , Athanasios Vazakidis and Evangelos Chytis . Review of Blockchain Technology and Its Applications in the Business Environment.
- Shang GAO, Tianyu ZHENG, Yu GUO , Bin XIAO. Efficient and Post-Quantum Zero-Knowledge Proofs for Blockchain Confidential Transaction Protocols.
- Chia-Chen Lin, Chin-Chen Chang, Yao-Zhu Zheng 3. A Ring Signature Based Anonymity Authentication Scheme for Group Medical Consultation.
- Rubdos. Entity Ring signature, Published at [Online].
- O. Kurbatov, P. Kravchenko,,T. Kuznetsova . Using Ring Signatures For An Anonymous E-Voting System.
- Pierangela Samarati1, Sabrina De Capitani di Vimercati. Access Control, Policies, Models, and Mechanisms, lecture notes In Computer Science.
- Sunoo Park Adam Sealfon Reputability . .Unclaimability of Ring Signatures.
- E. Bresson, J. Stern, and M. Szydlo. Threshold Ring signatures and applications to ad-hocgroups.
| Features | PBFW | TRBAC | CPBAC | Proposed approach (RSBAC) |
| Task dependency | Exist | Exist | X | Exist |
| Dynamic permission management | Exist | Exist | X | Exist |
| Using data conditionally | X | X | Exist | Exist |
| Dynamic separation of duty | Exist | X | X | Exist |
| Scope inheritance | X | Exist | X | Exist |
| administrator protection | X | X | X | Exist |
| Protection when publishing | X | X | X | Exist |
| The usual tracing | Level of User Privacy/Traceability | ApplicationExample |
|---|---|---|
| Normal tracing |
|
|
| User dependent opening |
|
|
| Decentralized tracing |
|
|
| Message-dependent opening |
|
|
| Distributed tracing |
|
|
| Accountable tracing |
|
|
| Accountable Ring signature scheme | Clients post in any online gatherings without enrolling, and users can only be tracked by their tracer. |
|
| Linkable Ring signatures | Ring signatures that can be linked User confidentiality is secure |
|
| Traceable Ring signatures | Digital certificates used by malicious users are tracked |
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





