Submitted:
31 December 2025
Posted:
15 January 2026
You are already at the latest version
Abstract
Keywords:
1. Introduction: The Invisibility Problem in Epistemic Justice Research
- Flattening: The dominant agent’s geometric collapse of the Other’s complex, autonomous hexid structure into a marginal, high-entropy position within the dominant agent’s navigational space.
- Internalization: The subalternized agent’s coerced construction of self-access routes through outer-ring positions that function as mirrors of dominant valuations, blocking return to minimal selfhood ().
- Trajectorial refraction: Resistance operations that disrupt the appropriation cycle through emergent topological configurations that contest dominant saturations—saturation against saturation. Counter-exonymy (autonomous naming) exemplifies this mechanism: the trajectory toward endonyms (Yoreme, Deaf, autistic) necessarily traverses the exonymic trace (“Mayo,” “hearing-impaired,” “person with autism”) before emerging at a refracted angle, contesting flattening while operating within the same register.
1.1. Theoretical Objectives and Empirical Payoffs
1.2. Paper Structure and Methodological Approach
- The appropriation mapping:
- The flattening operation:
- The resistance function:
2. Critical Literature Review: Mapping Epistemic Appropriation Across Contexts
2.1. Epistemic Injustice: From Testimonial to Structural
2.2. The Double Empathy Problem: Reconceptualizing Neurodivergence
2.3. Deaf Gain and Linguistic Minoritization
2.4. Chronic Illness and the “Medically Unexplained”
2.5. Educational Minoritization and DisCrit
3. Formalizing Epistemic Appropriation
3.1. The Asymmetry Function: Architectural Context
-
: Historically Saturated SSPsThread bundles crystallized through asymmetric social reproduction. These are not neutral objects but crystallized asymmetry, saturated through countless prior navigations encoding power differentials into the informational landscape itself.
-
: Exchange ProtocolsThe informational economy governing what flows between interfaces and at what cost. Exchange protocols can favor certain agents through differential access (who can speak?), asymmetric validation requirements (whose claims require evidence?), and cost gradients (who must expend effort to be heard?).
-
: MimesisInternal structures within each hexid that mirror other hexids. This is the generative operation where internalized asymmetry resides—producing the mirror positions () that subalternized agents construct under sustained institutional pressure.
| Component | Clinical Instantiation |
| diagnostic categories, examination room layout, intake form structure | |
| clinician controls duration; patient must justify claims | |
| patient’s internalized “deficiency” narrative | |
| actual navigation through consultation |
Infrarepresentational Stratification: Where Protocols Operate
-
: Proximal SSPs ()Patterns within the dissociative boundary, fully delimited by hexid individuation. They constitute the representational furniture of conscious experience—objects, categories, social roles.
-
: Medial SSPs ()Patterns at the edge of dissociation—aware that dissociation exists but not fully delimited by it. This is the terrain of transductive coupling: operates here as a Markov blanket.
-
: Distal SSPs ()Patterns below the dissociative boundary, relatively “blind” to hexid individuation. The function (spatiotemporal sequencing) operates on this stratum, which is why spatiotemporality appears as a universal framework rather than agent-specific.
The Gaussian Saturation Principle
- Hypo-Saturation ( / Trace Level): Pure Possibility. At the low end of the curve, there is insufficient saturation to establish boundaries. The substrate is undifferentiated.
- Optimal Saturation (): High Definition. The balance of the curve. Thread bundles achieve sufficient density to individuate clearly, supporting rich phenomenological detail (the specific patient, the specific sensation) without collapsing into generics.
- Hyper-Saturation (): Categorical Collapse. At the high end, massive repetition causes distinct threads to fuse into dense attractors. Boundaries between specific instances are overwritten by the gravitational pull of the category. This produces efficiency at the cost of detail.
Why This Architecture Matters for Epistemic Appropriation
- Asymmetry is not in the mechanism of communication (), which remains infrastructurally neutral.
- Asymmetry resides in the arrangement of SSPs, exchange protocols, and mimetic configurations—all operating at , within hexid boundaries.
- Internalization is geometrically precise: when a subalternized agent constructs mirror positions (), they are not “importing” external structures but constructing internal configurations that correspond to dominant patterns. The asymmetry becomes part of their own navigational landscape.
- Institutional power operates through differential distribution: dominant agents navigate through SSPs whose elevated intrinsic is offset by collective distribution, high TE, and mimetic naturalization—the maintenance burden is absorbed by institutional infrastructure and rendered phenomenologically invisible. Subalternized agents’ autonomous trajectories face equally high but without collective support, without transductive efficiency, and with the full weight of maintenance cost phenomenologically salient.
Transductive Mimesis: A Critical Clarification
- An object (a hearing aid, a diagnostic form, an appointment slot)
- A type of SSP
- An inherent property of certain renders
- An arrangement of the asymmetry function
- A recurrent configuration where SSPs operating at imitate the functions of
3.2. The Unified Mechanism: Epistemic Appropriation
3.3. Operation 1: Flattening
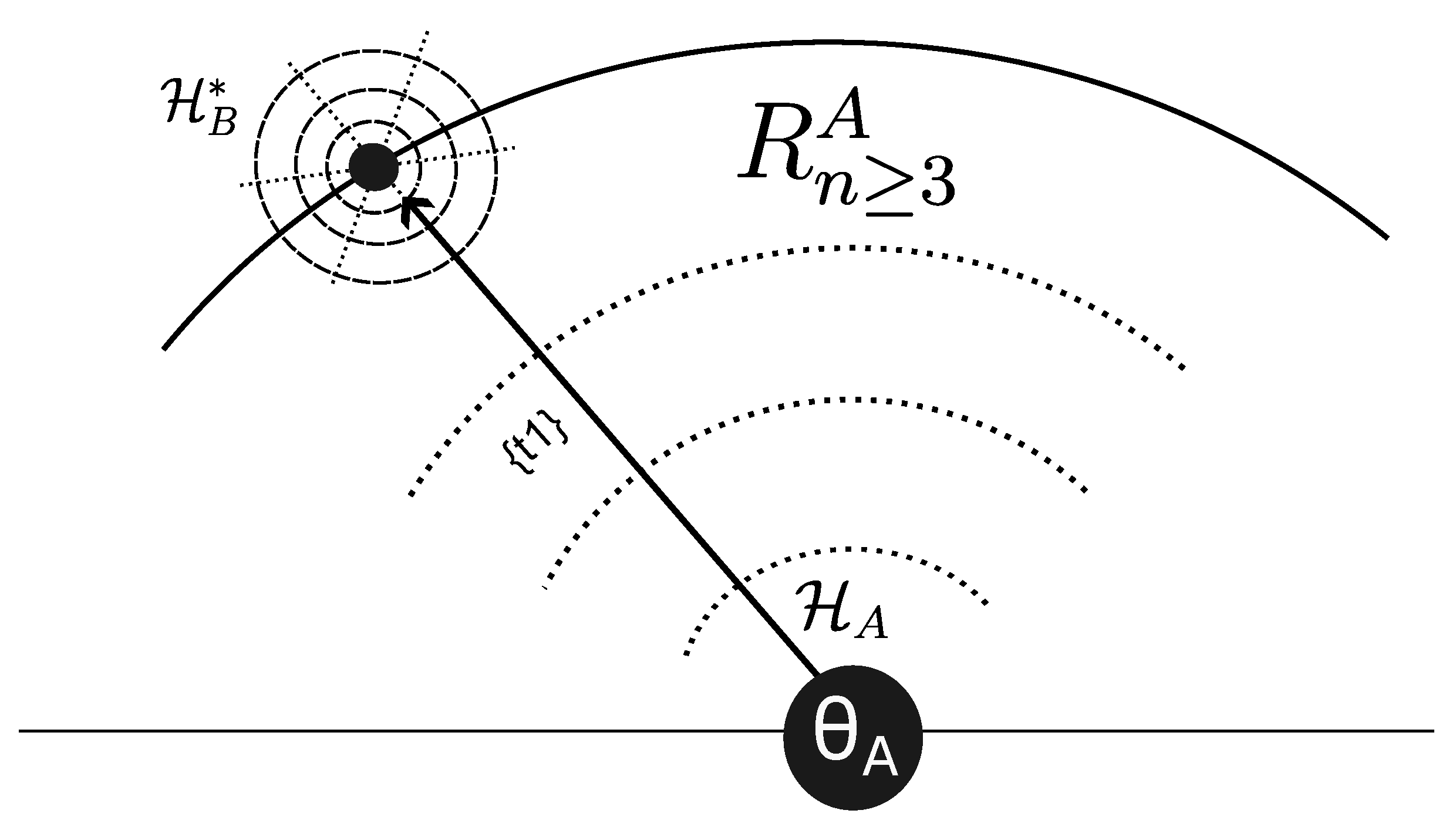
- Peripheral marginalization: B is represented exclusively in outer rings (, , ) of A’s hexid—abstract categories (“disabled,” “noncompliant,” “difficult”), not core relational or self-identity structures.
- -invisibility: A cannot conceive that B possesses a legitimate experiential baseline. B’s phenomenological reality is treated as aberration from A’s normative standard rather than autonomous validity.
- Dimensional collapse: The rich multidimensionality of —B’s complex navigational possibilities, historical trajectories, relational threads—is compressed into a single deficit-coded node.
- Deficit framing: The position is marked by absence (“lacks focus,” “hearing-impaired,” “medically unexplained”) rather than autonomous presence.
3.4. Operation 2: Internalization and the Appropriation Cycle
The Appropriation Cycle
- Agent B enters transductive coupling with asymmetrically configured arrangements (clinical encounter, classroom, institutional intake).
- Elevated TC: Transductive Coupling Cost is high because B’s native positions lack correspondence with dominant SSPs. B’s authentic navigation requires continuous “fresh translation” work.
- Asymmetric detection: Agent A (or institutional protocols) detects epistemic distance (lack of Transductive Equivalence) when the transduction cost exceeds its tolerance threshold, i.e., (Eq. 6). Exchange protocols () impose additional costs: B’s claims require more evidence, B’s expressions are scrutinized more heavily, B’s timeline is subordinated to institutional schedules.
-
Response choice: B faces a navigational fork:
- Resist: Maintain autonomous trajectories at high informational cost
- Desaturate: Return toward , disengaging from the encounter
- Align: Construct mirror positions that reduce transductive friction
- If B aligns: Mimetic construction () lowers TC but sediments asymmetric configuration within B’s own hexid.
- Saturation: Repeated alignment saturates mimetic threads. B’s navigation increasingly routes through internalized dominant coordinates.
- Completion: The asymmetric configuration becomes B’s own navigational structure—not external imposition but internal landscape.
The Thermodynamics of Coerced Alignment
Entropic Tolerance Threshold ().
Consequences of Internalization
-
Blocked -return ( emergence): Access to minimal selfhood (—the agent’s first-ring sense of “I am” prior to categorical saturation) becomes informationally expensive. The subject must “route through” internalized positions () to access even pre-categorical self-reference.A clarification is essential here: genuine -contact is already phenomenologically rare—typically requiring contemplative cultivation or altered states. What epistemic appropriation produces is : descending blockage at , where the capacity to navigate back to for identity recalibration becomes thermodynamically penalized by the very saturation that sustains outer-ring positions. The agent’s trajectory mathematically originates from , but phenomenologically, is where the agent first experiences “I am [something]”—like the downbeat that defines a musical phrase, even though the phrase emerges from preceding silence.The gradation of blockage matters: -contact faces “hard blockage” ()—phenomenologically rare even without appropriation. -return faces “soft blockage” (): structurally available but thermodynamically penalized. The difference explains why some subjects maintain a sense of “authentic self” beneath the mask (degraded but intact -return capacity) while others report complete identity foreclosure (saturated ).
- Chronic cognitive load: The mirror arrangement requires continuous maintenance—navigating simultaneously through autonomous and mirrored coordinates imposes persistent processing burden.
- Identity fragmentation: The subject experiences discontinuity between “authentic” navigation (toward ) and “institutional” navigation (through ).
- Resistance attrition: As mimetic threads saturate, the informational cost of resistance increases. The appropriated configuration becomes the “natural” route—not through belief change but through consolidation.
Alignment Mimesis vs. Control Mimesis
- -mimesis: Control over spatiotemporal assignment—appointment structures, institutional calendars, deadline regimes, property relations
- -mimesis: Control over transductive media—institutionalized registers, documentation requirements, authorized communication channels
- -mimesis: Control over exchange infrastructure—validation authority, resource allocation, diagnostic gatekeeping
| Mimesis Type | Typical Agent | Function | Relation to |
| Control mimesis | Dominant () | Operate , as instruments | Produces asymmetry |
| Alignment mimesis | Subalternized | Reduce TC via | Submits to asymmetry |
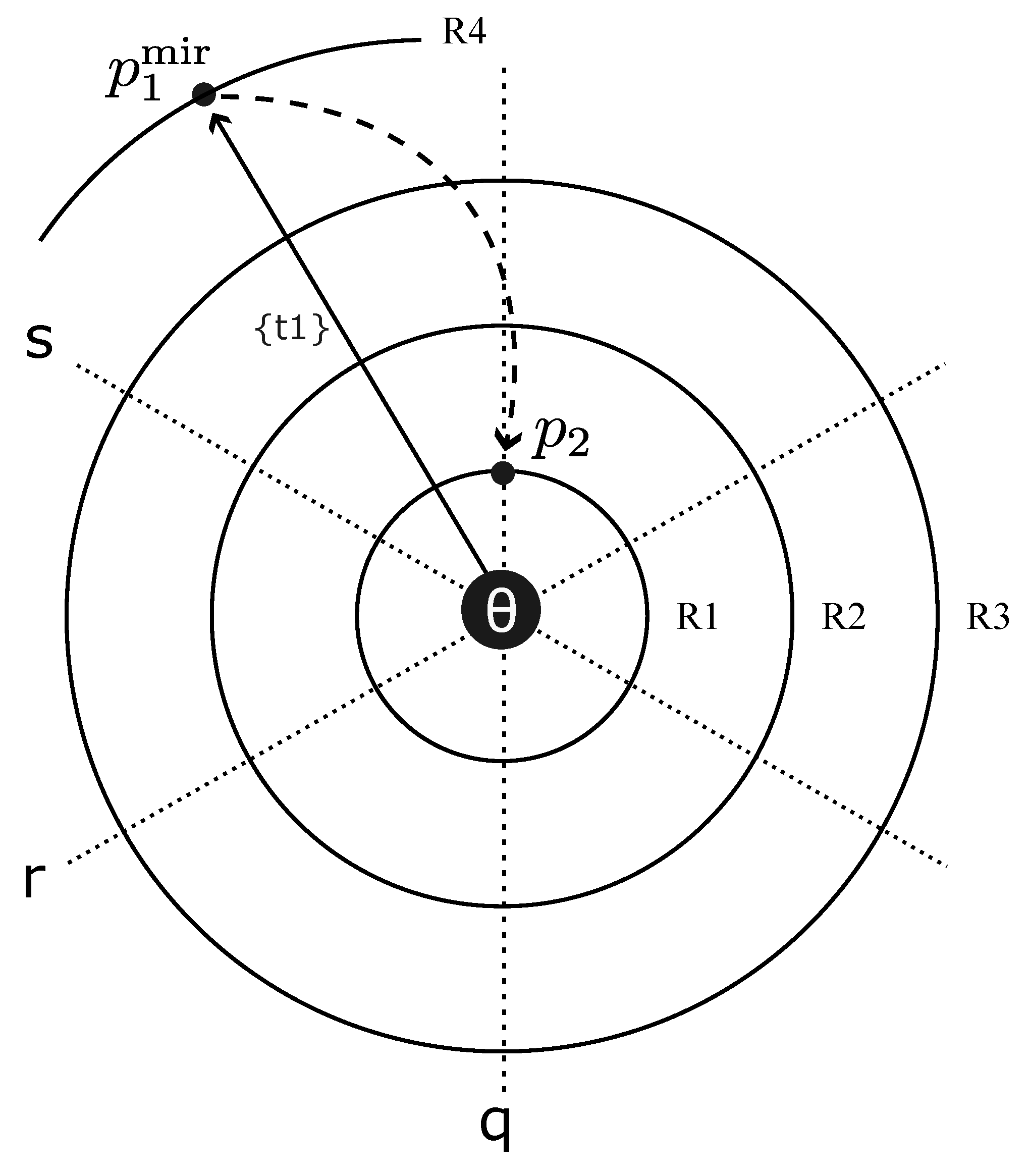
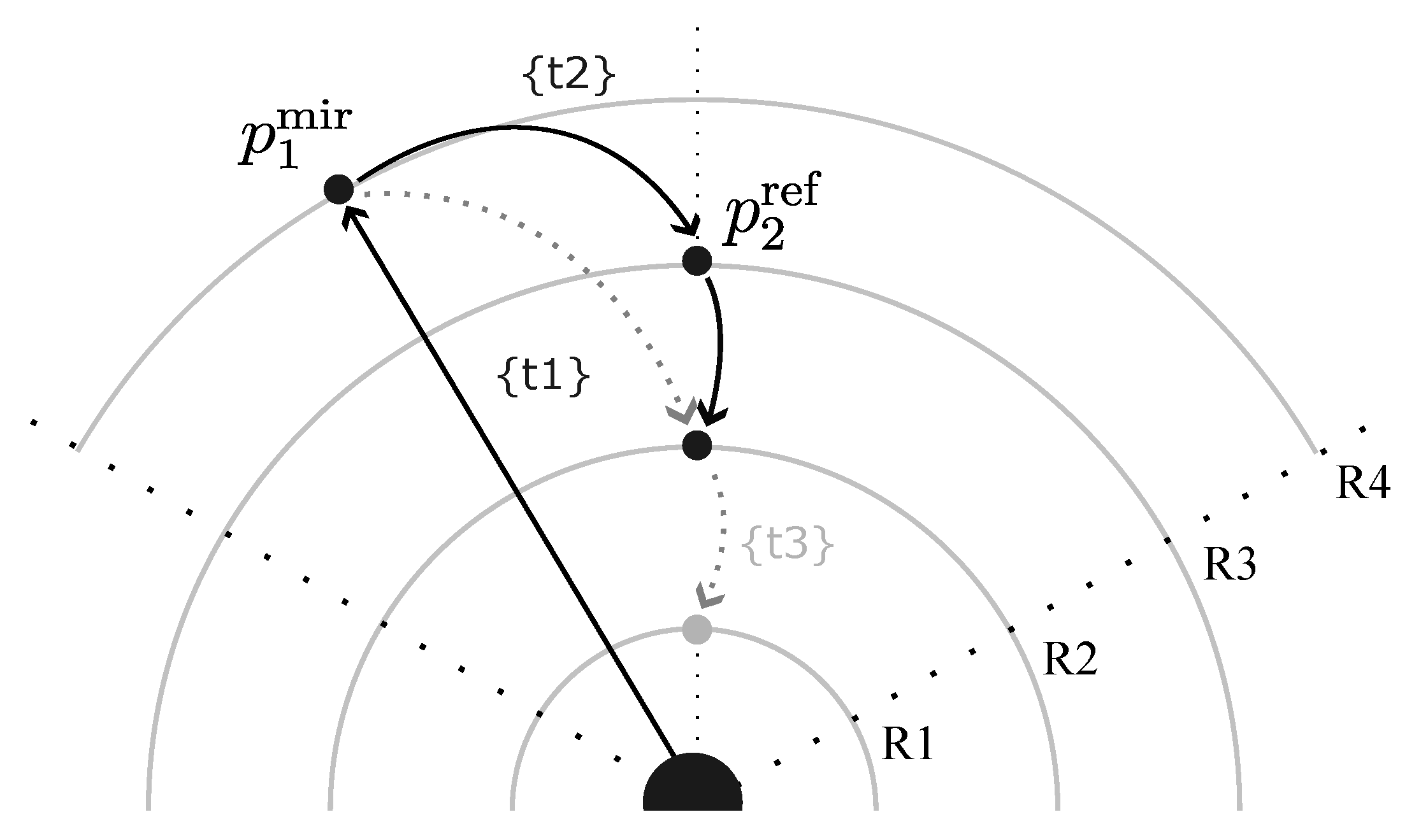
3.5. Operation 3: Trajectorial Refraction
The Mechanism
The optical analogy.
Notation.
- (mirror position): a node stabilized through alignment with dominant SSPs—the position the agent must traverse because institutional saturation has made it the available pathway.
- (refracted position): a node in the same ring () but at a different angular coordinate—the position where the trajectory emerges after contesting the dominant framing.
Autonymy as paradigm case.
- The agent’s trajectory necessarily passes through —the position saturated by exonymic SSPs (“hearing-impaired,” “disability,” “deficit”). This traversal is unavoidable: institutional saturation has configured as the low-cost pathway.
- The trajectory does not terminate at . Passing through the collective axis (), it stabilizes at —a position in the same structural ring () but with different thread-bundle composition and coalitional anchoring.
- At , the agent occupies “Deaf” as cultural identity rather than audiological lack. The structural location (, socially legible category) is unchanged; the trajectory that arrives there—and the collective “we” that sustains it—is not.
Counter-exonymy: Naming the dominant Other.
Structural relation.
The specificity of naming.
The Resistance Function
- indexes epistemic mode: meta-reflexive engagement () enables recognition of categorical construction, which is precondition for contestation
- measures saturation of transitional ring—positions that connect to outer rings without full institutional capture
- -return measures the agent’s capacity to return to minimal selfhood () for navigational recalibration—not the rarer -contact (), but reliable access to the “downbeat” of pre-categorical self-sense
Collective Support for Resistance
3.6. The Extractive Economy
3.7. Illustrative Case: Autistic Healthcare Navigation
The Asymmetry Function in Action
-
:The clinical environment is dense with historically saturated SSPs: the triage desk configuration, the intake form categories, the pain scale (“rate your pain 1–10”), the expected temporal rhythm of efficient processing. Each carries accumulated assumptions about valid expressions of suffering.
-
:Exchange protocols favor the nurse’s informational economy. The nurse’s assessments require no justification; the patient’s claims require corroboration. The nurse controls temporal flow; the patient waits. The nurse’s categories are institutionally authorized; the patient’s self-descriptions are data to be translated.
-
:Scenery trajectories render a stage optimized for neurotypical navigation: fluorescent lighting, acoustic chaos, visual clutter, unpredictable wait times. For B, this scenery configuration is not neutral backdrop but active assault on sensory regulation.
-
:If B has undergone prior healthcare encounters, they may have already constructed mirror positions (): learned scripts for performing legible distress, suppressed stimming behaviors, rehearsed phrases that translate autistic experience into clinical vocabulary.
Flattening: Rendered Invisible
Blockage Configurations and the Double Bind
- Operate from baseline: Navigate authentically from , but face elevated TC (fresh translation required at every encounter), risk flattening (atypical presentation misread), and potential care denial (“drug-seeking,” “psych consult”).
- Attempt to construct : Deploy mirror positions, perform expected distress signals, suppress autistic expression—but means these positions cannot stabilize cheaply. The attempt produces sensory overload amplification, executive function depletion, and potential masking collapse.
Systemic Outcomes
- Diagnostic overshadowing: B’s physical symptoms are attributed to “autism” rather than investigated—the flattened position ( “autistic patient”) subsumes all clinical presentation.
- Care fragmentation: B receives inconsistent care across encounters because their authentic presentation (-based) appears as inconsistency within neurotypical SSPs.
- Healthcare avoidance: Accumulated appropriation experiences lead B to avoid healthcare encounters entirely, producing downstream health consequences.
- Counter-exonymic adaptation: Some autistic patients develop robust stances, explicitly naming the appropriation operation (“You’re not seeing my actual experience”) as resistance strategy—high cognitive cost but preserving -return capacity.
4. Toward Operational Detection: Indicators for Professional Practice
4.1. Indicators of Flattening Operations
- Professional discourse systematically attributes patient/student reality to deficit (“can’t,” “lacks,” “impaired”) rather than difference (“experiences differently,” “processes via alternative pathways”).
- Absence of language recognizing subject’s experiential authority: subject’s self-reports are treated as data requiring professional interpretation rather than as direct testimony about phenomenological reality.
- Categorical override: When subject’s account conflicts with professional categories, the category prevails (“The test shows X” overrides “I experience Y”).
- Differential evidence requirements: Subject’s claims require corroboration; professional’s claims are presumed valid.
- Temporal control: Professional determines encounter duration, pacing, and scheduling; subject accommodates.
- Documentation authority: Professional’s notes constitute official record; subject’s account is “patient-reported” (epistemically downgraded).
4.2. Indicators of Internalization
- Subject reports increasing exhaustion from “being myself” in institutional settings.
- Sudden shift from resistance to compliance after prolonged institutional pressure.
- Development of rigid scripts () used exclusively for institutional interaction.
Emergence (Blocked -Return)
4.3. Indicators of Counter-Exonymic Resistance
4.4. Indicators of Extractive Configuration
Closed Threshold Signatures
4.5. Epistemic Mode Indicators (-Orientation)
5. Discussion: Contributions, Limitations, and Future Directions
5.1. Theoretical Contributions
5.2. Limitations and Boundary Conditions
5.3. Future Directions
5.4. Concluding Reflections: Toward Epistemic Expansion
Acknowledgments
Appendix A. Theoretical Foundations: The Trace & Trajectory Architecture
Appendix A.1. Ontological Commitments
- Informational Monism: Reality is information; matter and mind are interface-level distinctions within a unified informational substrate.
- Consciousness-First Ontology: Conscious experience is ontologically primitive; physical structures are representations within conscious interfaces.
- Pre-Representational Substrate: Meaning originates in navigational dynamics through informational space, not in correspondences between symbols and referents.
- Decolonial Axiology: Epistemic frameworks carry axiological commitments; TTF explicitly rejects universalist erasure of situated knowledge systems.
Appendix A.2. The Four-Level Ontological Hierarchy
-
(Traces)Pre-representational grooves in NET; pure possibilia encoding adjacency and transition structure without constituting navigable pathways. Traces are pre-phenomenal.
-
(Threads)Stabilized trace bundles; the first cumulative function over trace sets. Threads are string-like pathways that give coherence to the interface.
-
(Trajectories)Actual movement of conscious agents through thread-structured space. Trajectories are meaning-events—the analytical unit.
-
(Positions)Points of high harmonic coherence within thread bundles; navigational nodes, not categorical boxes. Positions have (intrinsic dissipative rate).
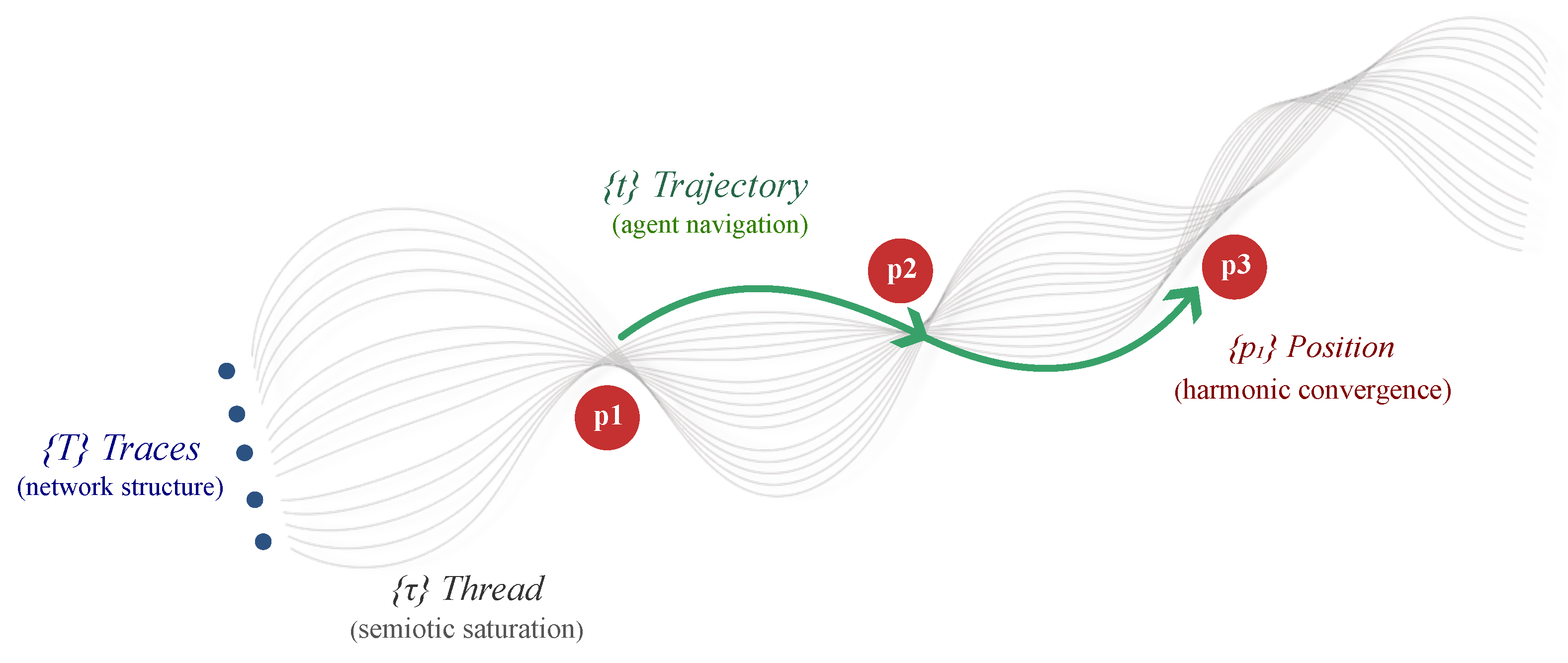
Appendix A.3. The Hexagonal Board: Geometry of Identity Space
Appendix A.4. Delta Dissipation Rate (δ DR )
A critical qualification: Functionally dissipative patterns.
Formal definition.
Implications for asymmetric saturation.
Blockage Configurations and δDR.
- blockage does not imply low at outer rings. Institutional positions at have elevated intrinsic ; what makes them “sticky” is not low maintenance but distributed maintenance + high TE + mimetic naturalization. The agent is locked in not because outer rings are easy but because exit is prohibitively expensive.
- blockage implies that the threads required for outer-ring stabilization do not sediment. Each deployment requires the agent’s own work; the must be borne individually rather than distributed across collective infrastructure.
- The asymmetry between a neurotypical professional’s and an autistic patient’s is not about “who has higher ” but about who bears the maintenance and how it registers phenomenologically. The professional’s maintenance is distributed and naturalized (invisible); the patient’s maintenance is individual and salient (exhausting).
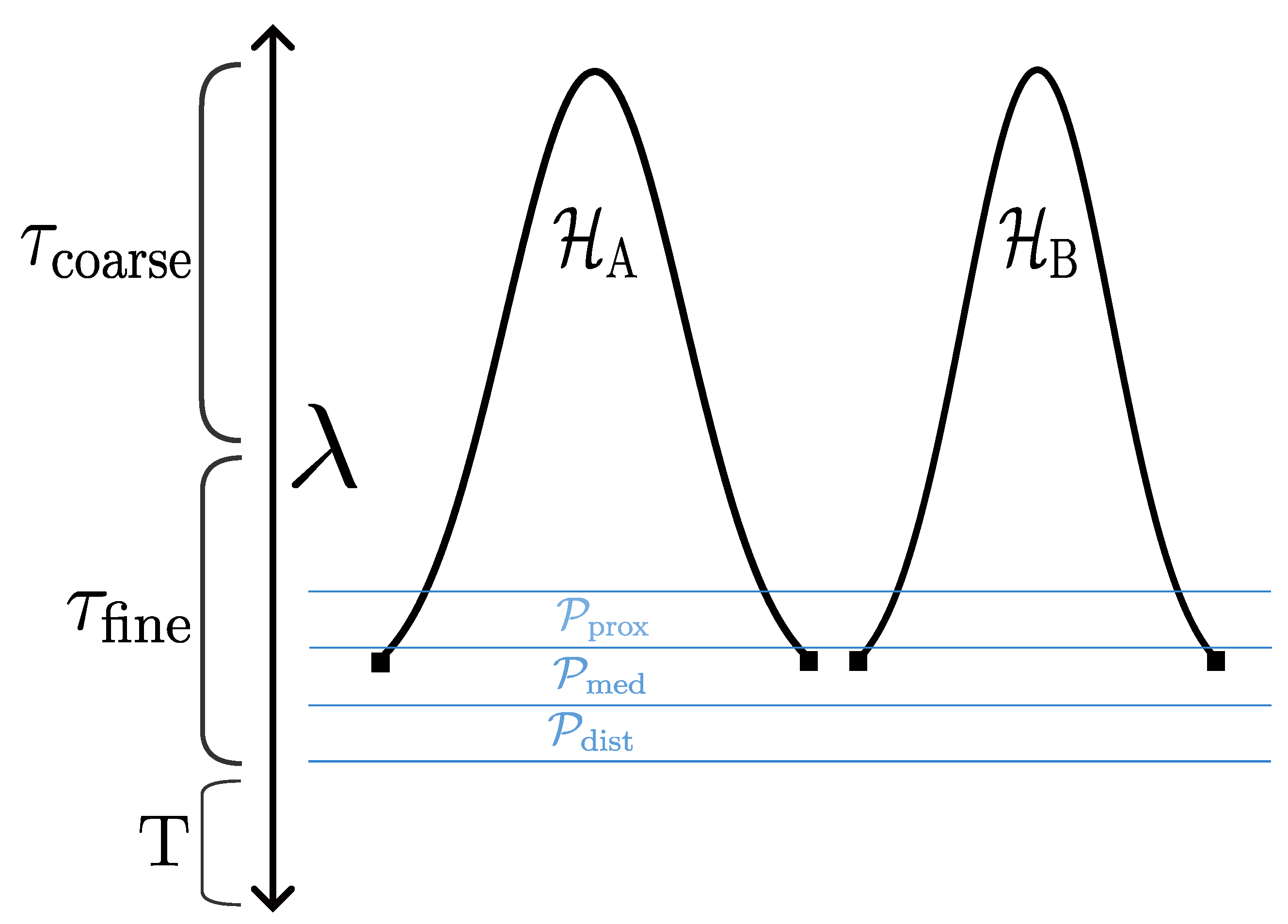
Appendix A.5. Orthogonal Parameters: λ and σ
-
(Trace level)Pre-stabilized substrate. Below the threshold of phenomenal access. Pure possibilia—the raw grooves in NET that have not yet been bundled into navigable pathways.
-
(Fine thread level)Fine-grained thread saturation. This is the level of phenomenal trajectories (): moment-to-moment experiential granularity, perceptual micro-regularities, gesture kinematics, sensory detail. The interface render operates here.
-
(Coarse thread level)Coarse-grained thread saturation. This is the level of meta trajectories (): categorical, social, and institutional navigation. Diagnostic labels, role structures, bureaucratic classifications, and the “science” of standardized assessment operate at this level. This is where asymmetric SSPs are most densely saturated—the terrain of epistemic appropriation.
-
(Compliant engagement)Agent treats categorical structures as transparent reality. Institutional positions are inhabited unreflectively; the constructed nature of categories does not register. High vulnerability to appropriation dynamics.
-
(Desaturating engagement)Agent moves toward , discharging representational saturation. This is the phenomenological stance of “letting go”—allowing accumulated categorical weight to dissipate rather than maintaining it. Moderate resistance capacity.
-
(Meta-reflexive engagement)Agent maintains critical distance, recognizing positions as constructed. The configuration becomes objectified, available for explicit analysis. The agent can name the operation being performed on them. Highest resistance capacity, but also highest cognitive load.
Appendix A.6. The Interface: H〈t〉
Appendix A.7. Transductive Equivalence and Coupling Cost
Appendix A.8. The Hexid Locality Principle
References
- Chapman, R. Empire of normality: Neurodiversity and capitalism; Pluto Press, 2023. [Google Scholar]
- Flores, N. Silencing the subaltern: Nation-state/colonial governmentality and bilingual education in the United States. Critical Inquiry in Language Studies 2013, 10(4), 263–287. [Google Scholar] [CrossRef]
- Mignolo, W. D. The darker side of Western modernity: Global futures, decolonial options; Duke University Press, 2011. [Google Scholar]
- Hoffman, D. D. The case against reality: Why evolution hid the truth from our eyes; W. W. Norton & Company, 2019. [Google Scholar]
- Deaf gain: Raising the stakes for human diversity; Bauman, H.-D. L., Murray, J. J., Eds.; University of Minnesota Press, 2014. [Google Scholar]
- Escobar L.-Dellamary, L. Trace & Trajectory Semantics: A pre-representational approach to meaning. Preprint 2025a. [Google Scholar]
- Escobar L.-Dellamary, L. Radial Analysis: Methodological framework for analyzing personal deixis and identity navigation. Preprint 2025b. [Google Scholar]
- Sampson, M. Diagnosis, misdiagnosis, and becoming better: An investigation into epistemic injustice. University of Wales Trinity Saint David Research Repository 2021. [Google Scholar]
- Internalized oppression: The psychology of marginalized groups; David, E. J. R., Ed.; Springer, 2014. [Google Scholar]
- Fricker, M. Epistemic injustice: Power and the ethics of knowing; Oxford University Press, 2007. [Google Scholar]
- Crichton, P.; Carel, H.; Kidd, I. J. Epistemic injustice in psychiatry. BJPsych Bulletin 2017, 41(2), 65–70. [Google Scholar] [PubMed]
- Kidd, I. J.; Carel, H. Epistemic injustice and illness. Journal of Applied Philosophy 2017, 34(2), 172–190. [Google Scholar] [CrossRef] [PubMed]
- Nielsen, K. M.; Nordgaard, J.; Henriksen, M. G. Fundamental issues in epistemic injustice in healthcare. Medicine, Health Care and Philosophy 2025, 28(2), 291–301. [Google Scholar] [CrossRef] [PubMed]
- Milton, D. E. M. On the ontological status of autism: The ‘double empathy problem’. Disability & Society 2012, 27(6), 883–887. [Google Scholar] [CrossRef]
- Crompton, C. J.; Ropar, D.; Evans-Williams, C. V.; Flynn, E. G.; Fletcher-Watson, S. Autistic peer-to-peer information transfer is highly effective. Autism 2020, 24(7), 1704–1712. [Google Scholar] [CrossRef] [PubMed]
- Rasmussen, E. B. Making and managing medical anomalies: Exploring the classification of ‘medically unexplained symptoms’. Social Studies of Science 2020, 50(6), 909–932. [Google Scholar] [CrossRef] [PubMed]
- Annamma, S. A.; Ferri, B. A.; Connor, D. J. Disability critical race theory: Exploring the intersectional lineage, emergence, and potential futures of DisCrit in education. Review of Research in Education 2018, 42(1), 46–71. [Google Scholar] [CrossRef]
- Teague, S. J. Perplexing presentations: Compulsory neuronormativity and cognitive marginalisation in social work practice with autistic mothers of autistic children. British Journal of Social Work 2023, 53(3), 1445–1464. [Google Scholar]
- Pearson, A.; Rose, K. Autistic, hysteric: Inequity in health care for autistic people assigned female at birth in the United Kingdom. In The Double Empathy Reader; NCBI Bookshelf, 2020. [Google Scholar]
- Shaw, S. C. K.; Carravallah, L.; Johnson, M.; O’Sullivan, J.; Chown, N.; Neilson, S.; Doherty, M. Barriers to healthcare and a ‘triple empathy problem’ may lead to adverse outcomes for autistic adults: A qualitative study. Autism 2024, 28(7), 1746–1757. [Google Scholar] [CrossRef] [PubMed]
| 1 | Autonymy is the direct response to exonymy targeting the agent’s own identity: “You named me; I rename myself.” Examples across contexts: “Mayo” →Yoreme; “Tarahumara” →Rarámuri; “Otomí” →Hñähñu; “hearing-impaired” → Deaf. |
| 2 | Counter-exonymy respects Hexid Locality: is within the subalternized agent’s navigational space—their representation of the Other, now refracted outward. The limited propagation (asymmetric g) reflects that this renaming, while locally stabilized, faces structural resistance in broader SSP distributions. |
| 3 | Not all trajectorial refraction involves naming. Marches, ceremonial practices, traditional dress, spatial occupation—these refract through embodied action, temporal rhythm, and collective visibility. Naming adds: (1) trans-λ saturation—the name configures positions across identity, epistemic, political, and affective registers simultaneously; (2) mimesis—the saturated name begins to operate as translation protocol between community and institutional space; (3) transductive stabilization—because naming operates at and propagates through transductive protocols, it elevates TE (Transductive Equivalence) across community members, thereby reducing TC (Transductive Coupling Cost) within those spaces. The named positions retain elevated intrinsic —they are CA-maintained, not NET-backed—but collective saturation distributes the maintenance burden and minimizes transductive friction. Refraction without naming contests; refraction with naming reconfigures the navigational landscape itself by establishing high-TE pathways where resistant trajectories become mutually legible. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2026 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




