Submitted:
02 September 2025
Posted:
03 September 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
- A novel construction method: We developed a systematic approach for building 8×8 S-Boxes from smaller component S-Boxes, which allows for a modular and efficient design.
- Optimal nonlinearity: The S-Boxes we constructed successfully achieve a nonlinearity of 116, reaching the theoretical maximum for 8-variable balanced Boolean functions.
- Comprehensive security analysis: Our analysis confirms that these new S-Boxes meet other critical security criteria, including the Strict Avalanche Criterion (SAC), Bit Independence Criterion (BIC), Differential Avalanche Probability (DAP), and Linear Avalanche Probability (LAP).
- Practical robustness: Side-channel attack experiments show that our S-Boxes offer resistance comparable to the Advanced Encryption Standard (AES) S-Box, proving their real-world applicability.
- Efficient hardware implementation: Our S-Boxes are designed for efficient hardware resource utilization, making them ideal for systems with limited resources.
2. Related Works
3. Background
3.1. Boolean Functions and Nonlinearity
3.2. Properties of Cryptographically Strong S-Boxes
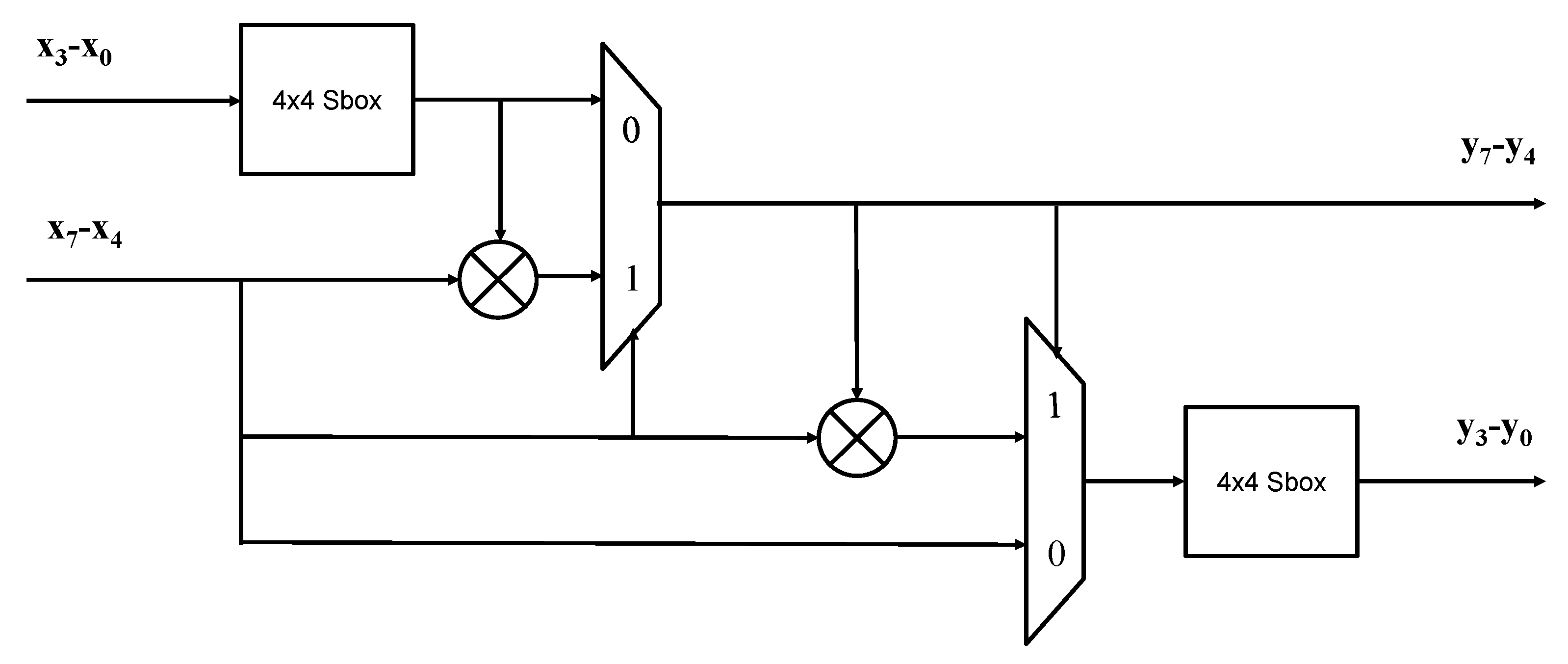
4. Proposed Method
4.1. Proposed Algorithm
4.2. Experimental
5. Security Analysis
5.1. Nonlinearity
5.2. Strict Avalanche Criterion
5.3. Bit Independence Criterion
5.4. Differential Approximation Probability
5.5. Linear Approximation Probability
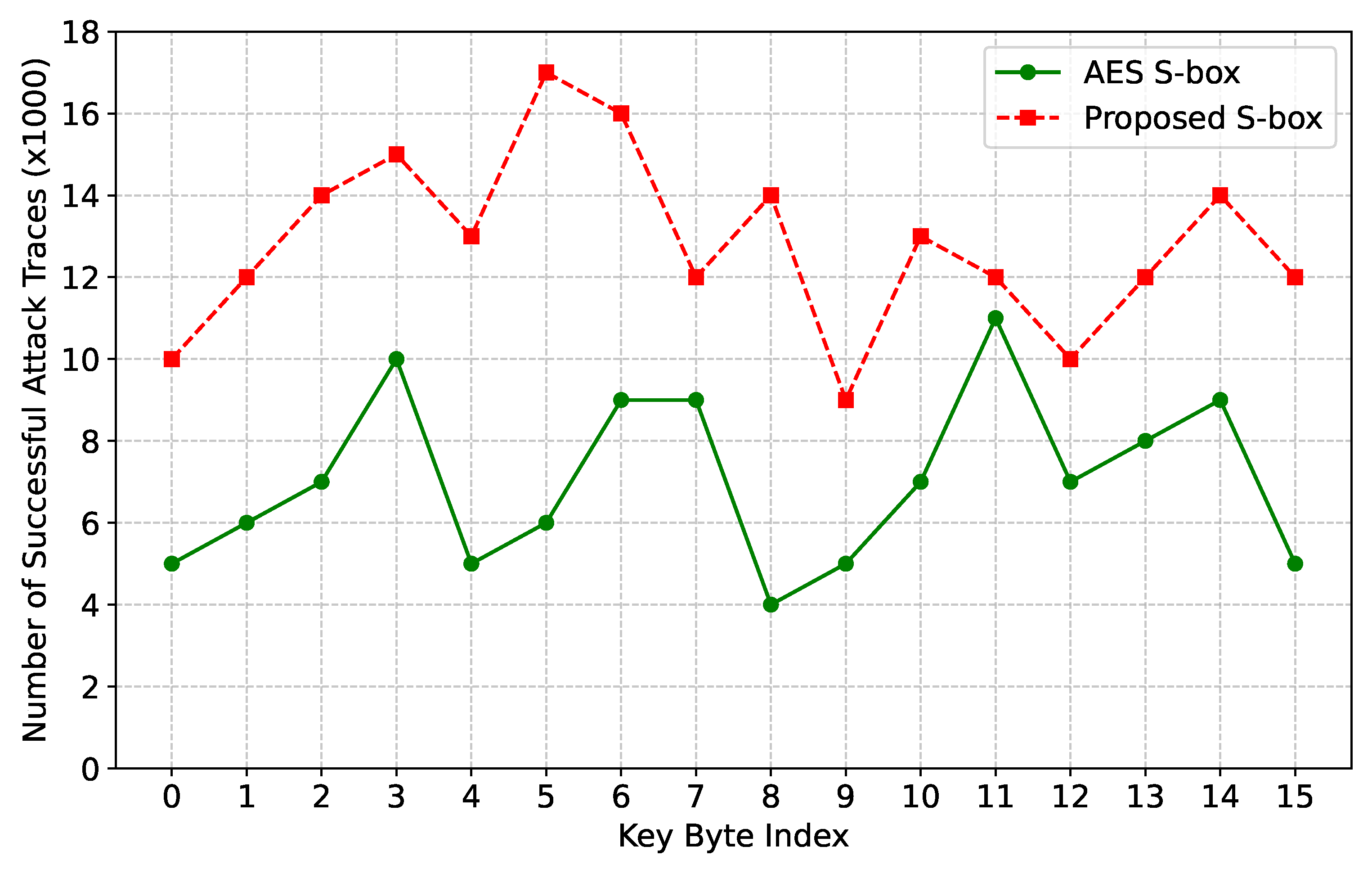
5.6. Side-Channel Attack Analysis
- With the AES S-Box, approximately 9,000 traces were sufficient to recover 14 out of 16 key bytes, with the most difficult byte requiring about 11,000 traces.
- With the proposed S-Box, around 12,000 traces were necessary to recover 12 out of 16 key bytes, and the hardest byte required up to 17,000 traces.
6. Implementation
7. Conclusion
- Optimal Nonlinearity: The S-Boxes developed using this new method achieve a nonlinearity of 116, which is the highest possible for balanced 8-variable Boolean functions. This breakthrough surpasses all previously reported results, setting a new benchmark in the field.
- Comprehensive Security: Beyond optimal nonlinearity, the S-Boxes also satisfy other key cryptographic criteria, including the Strict Avalanche Criterion (SAC), Bit Independence Criterion (BIC), Differential Avalanche Probability (DAP), and Linear Avalanche Probability (LAP), all at robust levels.
- Proven Robustness and Efficiency: Practical evaluations show that these S-Boxes are highly resilient. They offer side-channel attack resistance comparable to the AES S-Box and are designed for efficient hardware implementation, making them suitable for resource-constrained systems.
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Sarkar, P.; Maitra, S. Nonlinearity Bounds and Constructions of Resilient Boolean Functions. In Proceedings of the Advances in Cryptology — CRYPTO 2000. Springer Berlin Heidelberg; 2000; pp. 515–532. [Google Scholar]
- Carlet, C.; Djurasevic, M.; Jakobovic, D.; Mariot, L.; Picek, S. Evolving constructions for balanced, highly nonlinear boolean functions. In Proceedings of the Proceedings of the Genetic and Evolutionary Computation Conference, 2022; pp. 1147–1155. [CrossRef]
- Gini, A.; Méaux, P. Weightwise perfectly balanced functions and nonlinearity. Cryptology ePrint Archive, Paper 2022/1777, 2022.
- Duong, P.P.; Dang, T.K.; Hoang, T.T.; Pham, C.K. Compact 8-Bit S-Boxes Based on Multiplication in a Galois Field GF(24). Cryptography 2025, 9. [Google Scholar] [CrossRef]
- Kuznetsov, O.; Poluyanenko, N.; Frontoni, E.; Kandiy, S. Enhancing Smart Communication Security: A Novel Cost Function for Efficient S-Box Generation in Symmetric Key Cryptography. Cryptography 2024, 8. [Google Scholar] [CrossRef]
- Baowidan, S.A.; Alamer, A.; Hassan, M.; Yousaf, A. Group-Action-Based S-box Generation Technique for Enhanced Block Cipher Security and Robust Image Encryption Scheme. Symmetry 2024, 16. [Google Scholar] [CrossRef]
- Alali, A.S.; Ali, R.; Jamil, M.K.; Ali, J.; Gulraiz. Dynamic S-Box Construction Using Mordell Elliptic Curves over Galois Field and Its Applications in Image Encryption. Mathematics 2024, 12. [Google Scholar] [CrossRef]
- Aribilola, I.; Lee, B.; Naveed Asghar, M. Möbius Transformation and Permutation Based S-Box to Enhance IoT Multimedia Security. IEEE Access 2024, 12, 140792–140808. [Google Scholar] [CrossRef]
- Asif, M.; Wajiha, S.; Askar, S.; Ahmad, H. A Novel Scheme for Construction of S-Box Using Action of Power Associative Loop and Its Applications in Text Encryption. IEEE Access 2024, 12, 90853–90861. [Google Scholar] [CrossRef]
- Ali, R.; Jamil, M.K.; Alali, A.S.; Ali, J.; Afzal, G. A Robust S Box Design Using Cyclic Groups and Image Encryption. IEEE Access 2023, 11, 135880–135890. [Google Scholar] [CrossRef]
- Zahid, A.H.; Rashid, H.; Shaban, M.M.U.; Ahmad, S.; Ahmed, E.; Amjad, M.T.; Baig, M.A.T.; Arshad, M.J.; Tariq, M.N.; Tariq, M.W.; et al. Dynamic S-Box Design Using a Novel Square Polynomial Transformation and Permutation. IEEE Access 2021, 9, 82390–82401. [Google Scholar] [CrossRef]
- Kuznetsov, A.; Frontoni, E.; Romeo, L.; Poluyanenko, N.; Kandiy, S.; Kuznetsova, K.; Beňová, E. Optimizing Hill Climbing Algorithm for S-Boxes Generation. Electronics 2023, 12. [Google Scholar] [CrossRef]
- A. Mahboob, M. Asif, I. Siddique, A. Saleem, M. Nadeem, D. Grzelczyk, and J. Awrejcewicz. A Novel Construction of Substitution Box Based on Polynomial Mapped and Finite Field With Image Encryption Application. IEEE Access Nov. 2022, 10, 119244–119258.
- Ramzan, M.; Shah, T.; Hazzazi, M.M.; Aljaedi, A.; Alharbi, A.R. Construction of S-Boxes Using Different Maps Over Elliptic Curves for Image Encryption. IEEE Access 2021, 9, 157106–157123. [Google Scholar] [CrossRef]
- Zahid, A.H.; Arshad, M.J.; Ahmad, M. A Novel Construction of Efficient Substitution-Boxes Using Cubic Fractional Transformation. Entropy 2019, 21. [Google Scholar] [CrossRef]
- Zahid, A.H.; Arshad, M.J. An Innovative Design of Substitution-Boxes Using Cubic Polynomial Mapping. Symmetry 2019, 11. [Google Scholar] [CrossRef]
- Song, R.; Zhao, H. Security-Enhanced Image Encryption: Combination of S-Boxes and Hyperchaotic Integrated Systems. IEEE Access 2025, 13, 105151–105164. [Google Scholar] [CrossRef]
- Boobalan, S.; Gurunathan Arthanari, S.K. Lorenz and Chua Chaotic Key-Based Dynamic Substitution Box for Efficient Image Encryption. Symmetry 2025, 17. [Google Scholar] [CrossRef]
- Dutra e Silva Junior, É.C.; Cruz, C.A.d.M.; Saraiva, I.A.L.; Santos, F.G.; dos Santos Junior, C.R.P.; Indrusiak, L.S.; Finamore, W.A.; Glesner, M. Chaos-Based S-Boxes as a Source of Confusion in Cryptographic Primitives. Electronics 2025, 14. [Google Scholar] [CrossRef]
- Alabduallah, B.; Banga, A.; Iqbal, N.; Ikram, A.; Diab, H. Advancing Cryptographic Security With a New Delannoy-Derived Chaotic S-Box. IEEE Access 2024, 12, 82926–82937. [Google Scholar] [CrossRef]
- Aydın, Y.; Özkaynak, F. Automated Chaos-Driven S-Box Generation and Analysis Tool for Enhanced Cryptographic Resilience. IEEE Access 2023, 12, 312–328. [Google Scholar] [CrossRef]
- Malik, A.W.; Zahid, A.H.; Bhatti, D.S.; Kim, H.J.; Kim, K.-I. Designing S-Box Using Tent-Sine Chaotic System While Combining the Traits of Tent and Sine Map. IEEE Access Jul. 2023, 11, 79265–79274. [Google Scholar] [CrossRef]
- Alharbi, A.R.; Jamal, S.S.; Khan, M.F.; Gondal, M.A.; Abbasi, A.A. Construction and Optimization of Dynamic S-Boxes Based on Gaussian Distribution. IEEE Access 2023, 11, 35818–35829. [Google Scholar] [CrossRef]
- Haque, A.; Abdulhussein, T.A.; Ahmad, M.; Waheed Falah, M.; Abd El-Latif, A.A. A Strong Hybrid S-Box Scheme Based on Chaos, 2D Cellular Automata and Algebraic Structure. IEEE Access 2022, 10, 116167–116181. [Google Scholar] [CrossRef]
- Corona-Bermúdez, E.; Chimal-Eguía, J.C.; Corona-Bermúdez, U.; Rivero-Ángeles, M.E. Chaos Meets Cryptography: Developing an S-Box Design with the Rössler Attractor. Mathematics 2023, 11. [Google Scholar] [CrossRef]
- Shafique, A.; Khan, K.H.; Hazzazi, M.M.; Bahkali, I.; Bassfar, Z.; Rehman, M.U. Chaos and Cellular Automata-Based Substitution Box and Its Application in Cryptography. Mathematics 2023, 11. [Google Scholar] [CrossRef]
- C. Yang, X. Wei, and C. Wang. S-Box Design Based on 2D Multiple Collapse Chaotic Map and Their Application in Image Encryption. Entropy Oct. 2021, 23. [CrossRef]
- Yogi, B.; Roy, S.; Rawat, U.; Redkar, S. Advanced Image Ciphering: 1-D Group Cellular Automata and S-Box Strategies. In Proceedings of the 2025 International Conference on Next Generation Communication & Information Processing (INCIP); 2025; pp. 15–19. [Google Scholar] [CrossRef]
- Waheed, A.; Subhan, F.; Mohd Su’ud, M.; Mansoor Alam, M. Molding robust S-box design based on linear fractional transformation and multilayer Perceptron: Applications to multimedia security. Egyptian Informatics Journal 2024, 26, 100480. [Google Scholar] [CrossRef]
- Zhang, N.; Zhao, Q.; Zhang, H. Construction of Rotation Symmetric S-Boxes Based on a Hybrid Heuristic Algorithm. In Proceedings of the 2024 6th International Conference on Natural Language Processing (ICNLP); 2024; pp. 295–299. [Google Scholar] [CrossRef]
- Kuznetsov, O.; Poluyanenko, N.; Kuznetsova, K.; Frontoni, E.; Arnesano, M. Hybrid Population-Based Hill Climbing Algorithm for Generating Highly Nonlinear S-boxes. Computers 2024, 13. [Google Scholar] [CrossRef]
- Hazzazi, M.M.; Baowidan, S.A.; Yousaf, A.; Adeel, M. An Innovative Algorithm Based on Chaotic Maps Amalgamated with Bit-Level Permutations for Robust S-Box Construction and Its Application in Medical Image Privacy. Symmetry 2024, 16. [Google Scholar] [CrossRef]
- Malik, D.S.; Shah, T.; Tehsin, S.; Nasir, I.M.; Fitriyani, N.L.; Syafrudin, M. Block Cipher Nonlinear Component Generation via Hybrid Pseudo-Random Binary Sequence for Image Encryption. Mathematics 2024, 12. [Google Scholar] [CrossRef]
- Ahmad, M.; Alkanhel, R.; El-Shafai, W.; Algarni, A.D.; El-Samie, F.E.A.; Soliman, N.F. Multi-Objective Evolution of Strong S-Boxes Using Non-Dominated Sorting Genetic Algorithm-II and Chaos for Secure Telemedicine. IEEE Access 2022, 10, 112757–112775. [Google Scholar] [CrossRef]
- Artuğer, F.; Özkaynak, F. SBOX-CGA: substitution box generator based on chaos and genetic algorithm. Neural Computing and Applications 2022, 34, 20203–20211. [Google Scholar] [CrossRef]
- A. I. Lawah, A. A. Ibrahim, S. Q. Salih, H. S. Alhadawi, and P. S. JosephNg. Grey Wolf Optimizer and Discrete Chaotic Map for Substitution Boxes Design and Optimization. IEEE Access Apr. 2023, 11, 42416–42430.
- Alsaif, H.; Guesmi, R.; Kalghoum, A.; Alshammari, B.M.; Guesmi, T. A Novel Strong S-Box Design Using Quantum Crossover and Chaotic Boolean Functions for Symmetric Cryptosystems. Symmetry 2023, 15. [Google Scholar] [CrossRef]
- L. Li, J. Liu, Y. Guo, and B. Liu. A New S-box Construction Method Meeting Strict Avalanche Criterion. J. Inf. Secur. Appl. May 2022, 66, 103135.
- J. Abdurazzokov. Dynamic S-Box Generation Algorithm with Improved Strict Avalanche Criterion by Selection of Adjacency Matrix Parameters. In Proceedings of the Int. Conf. on Tech. Advancements in Comp. Sciences (ICTACS), Nov. 2023, pp. 393–398.
- Duong, P.P.; Nguyen, H.M.; Dao, B.A.; Tran, T.H.; Kieu-Do-Nguyen, B.; Pham, C.K.; Hoang, T.T. S-Boxes with Optimal Strict Avalanche Criterion using Chaotic Map. In Proceedings of the 2024 9th International Conference on Integrated Circuits, Design, and Verification (ICDV), 2024, pp. 85–90. [CrossRef]
- Sony, D.; Reddy, D.K. Dynamic Composite S-Boxes for High-Speed IoT Encryption with Enhanced Security. In Proceedings of the 2025 IEEE 14th International Conference on Communication Systems and Network Technologies (CSNT); 2025; pp. 371–375. [Google Scholar] [CrossRef]
- Kumar, S.; Kumar, D.; Lamkuche, H.; Sharma, V.S.; Alkahtani, H.K.; Elsadig, M.; Bivi, M.A. SHC: 8-bit Compact and Efficient S-Box Structure for Lightweight Cryptography. IEEE Access 2024, 12, 39430–39449. [Google Scholar] [CrossRef]
- Rashidi, B. Compact and efficient structure of 8-bit S-box for lightweight cryptography. Integration 2021, 76, 172–182. [Google Scholar] [CrossRef]
- Teng, Y.T.; Chin, W.L.; Chang, D.K.; Chen, P.Y.; Chen, P.W. VLSI Architecture of S-Box With High Area Efficiency Based on Composite Field Arithmetic. IEEE Access 2022, 10, 2721–2728. [Google Scholar] [CrossRef]
- Y. Li and M. Wang. Constructing S-boxes for Lightweight Cryptography with Feistel Structure. In Proceedings of the Crypto. Hardware and Embedded Syst. (CHES), Sep. 2014, Vol. 8731, pp. 127–146.
- E. Boss, V. Grosso, T. Guneysu, G. Leander, A. Moradi, and T. Schneider. Strong 8-bit Sboxes with Efficient Masking in Hardware. In Proceedings of the Crypto. Hardware and Embedded Syst. (CHES), Mar. 2017, Vol. 7, pp. 171–193.
- A. Canteaut, S. Duval, and G. Leurent. Construction of Lightweight S-Boxes Using Feistel and MISTY Structures. In Proceedings of the Selected Areas in Crypto. (SAC), Aug. 2015, pp. 373–393.
- Yan, L.; Li, L.; Song, Q. Lightweight 6-bit S-Boxes With DPA Resistance. IEEE Transactions on Network Science and Engineering 2025, 12, 3719–3730. [Google Scholar] [CrossRef]
- Duong, P.P.; Minh Nguyen, H.; Dao, B.A.; Kieu-Do-Nguyen, B.; Tran, T.H.; Hoang, T.T.; Pham, C.K. Construction of Robust Lightweight S-Boxes Using Enhanced Logistic and Enhanced Sine Maps. IEEE Access 2024, 12, 63976–63994. [Google Scholar] [CrossRef]
- Kang, M.; Wang, M. New Genetic Operators for Developing S-Boxes With Low Boomerang Uniformity. IEEE Access 2022, 10, 10898–10906. [Google Scholar] [CrossRef]
- H. Kim, Y. Jeon, G. Kim, J. Kim, B.-Y. Sim, D.-G. Han, H. Seo, S. Kim, S. Hong, J. Sung, and D. Hong. A New Method for Designing Lightweight S-Boxes With High Differential and Linear Branch Numbers, and its Application. IEEE Access Nov. 2021, 9, 150592–150607.
- Dimitrov, M.; Baicheva, T. On the Pentanomial Power Mapping Classification of 8-bit to 8-bit S-Boxes. Mathematics 2024, 12. [Google Scholar] [CrossRef]
- Zhang, L.; Ma, C.; Zhao, Y.; Zhao, W. A Novel Dynamic S-Box Generation Scheme Based on Quantum Random Walks Controlled by a Hyper-Chaotic Map. Mathematics 2024, 12. [Google Scholar] [CrossRef]
- Carlet, C. Boolean functions for cryptography and coding theory 2021.
- Kumar, S.; Chaudhary, D.; Lakshmanan, S.A.; Lee, C.C. Novel Approach to Degree, Balancedness, and Affine Equivalence of Boolean Functions and Construction of a Special Class of Non-Quadratic Balanced Boolean Functions. Cryptography 2025, 9. [Google Scholar] [CrossRef]
- Tariq, O.; Dastagir, M.B.A.; Han, D. Compact Walsh–Hadamard Transform-Driven S-Box Design for ASIC Implementations. Electronics 2024, 13. [Google Scholar] [CrossRef]
- A. F. Webster and S. E. Tavares. On the Design of S-Boxes. In Proceedings of the Advances in Cryptology (CRYPTO), 1986, pp. 523–534. [CrossRef]
- H. M. Heys. A Tutorial on Linear and Differential Cryptanalysis. Cryptologia 2002, 26, 189–221. [CrossRef]
- Mishra, P.; Sarkar, S.; Gupta, I. Determining the Minimum Degree of an S-box 2017.
- Heuser, A.; Picek, S.; Guilley, S.; Mentens, N. Lightweight Ciphers and Their Side-Channel Resilience. IEEE Transactions on Computers 2020, 69, 1434–1448. [Google Scholar] [CrossRef]
- Li, H.; Zhou, Y.; Ming, J.; Yang, G.; Jin, C. The Notion of Transparency Order, Revisited. The Computer Journal 2020, 63, 1915–1938. [Google Scholar] [CrossRef]
- ZHOU, Y.; ZHAO, W.; Chen, Z.; WANG, W.; DU, X. On the Signal-to-Noise Ratio for Boolean Functions. IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences 2020, E103.A. [Google Scholar] [CrossRef]
- Li, H.; Yang, G.; Ming, J.; Zhou, Y.; Jin, C. Transparency order versus confusion coefficient: a case study of NIST lightweight cryptography S-Boxes. Cybersecurity 2021, 4, 35. [Google Scholar] [CrossRef]
- E. Biham and A. Shamir. Differential Cryptanalysis of DES-like Cryptosystems. Journal of Cryptology 1991, 4, 3–72. [CrossRef]
- C. Adams and S. Tavares. The Structured Design of Cryptographically Good S-Boxes. J. Cryptology Jan. 1990, 3, 27–41. [CrossRef]
- Alqahtani, J.; Akram, M.; Ali, G.A.; Iqbal, N.; Alqahtani, A.; Alroobaea, R. Elevating Network Security: A Novel S-Box Algorithm for Robust Data Encryption. IEEE Access 2024, 12, 2123–2134. [Google Scholar] [CrossRef]
- J. Daemen and V. Rijmen. The design of Rijndael; Vol. 2, Springer, 2002.
- H. Kim, Y. Jeon, G. Kim, J. Kim, B.-Y. Sim, D.-G. Han, H. Seo, S. Kim, S. Hong, J. Sung, and D. Hong. A New Method for Designing Lightweight S-Boxes With High Differential and Linear Branch Numbers, and its Application. IEEE Access Nov. 2021, 9, 150592–150607. [CrossRef]
- Brier, E.; Clavier, C.; Olivier, F. Correlation Power Analysis with a Leakage Model. In Proceedings of the Cryptographic Hardware and Embedded Systems - CHES 2004. Springer Berlin Heidelberg; 2004; pp. 16–29. [Google Scholar] [CrossRef]
- Mestiri, H.; Kahri, F.; Bouallegue, B.; Machhout, M. A CPA attack against cryptographic hardware implementation on SASEBO-GII. In Proceedings of the 2017 International Conference on Green Energy Conversion Systems (GECS); 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Canright, D. A Very Compact S-Box for AES. In Proceedings of the Cryptographic Hardware and Embedded Systems – CHES; 2005; 2005, p. pp. [Google Scholar] [CrossRef]
- Ueno, R.; Homma, N.; Sugawara, Y.; Nogami, Y.; Aoki, T. Highly Efficient GF(28) Inversion Circuit Based on Redundant GF Arithmetic and Its Application to AES Design. In Proceedings of the Cryptographic Hardware and Embedded Systems – CHES 2015. Springer, 2015, Vol. 9293; pp. 63–80. [CrossRef]
- Reyhani-Masoleh, A.; Taha, M.; Ashmawy, D. New Area Record for the AES Combined S-Box/Inverse S-Box. In Proceedings of the 2018 IEEE 25th Symposium on Computer Arithmetic (ARITH); 2018; pp. 145–152. [Google Scholar] [CrossRef]
- Rashidi, B. Compact and efficient structure of 8-bit S-box for lightweight cryptography. Integration 2021, 76, 172–182. [Google Scholar] [CrossRef]
- Zhang, X.; Parhi, K. High-speed VLSI architectures for the AES algorithm. IEEE Transactions on Very Large Scale Integration (VLSI) Systems 2004, 12, 957–967. [Google Scholar] [CrossRef]
- Maximov, A.; Ekdahl, P. New Circuit Minimization Techniques for Smaller and Faster AES SBoxes. IACR Transactions on Cryptographic Hardware and Embedded Systems 2019, 91–125. [Google Scholar] [CrossRef]
- Avraamova, O.; Fomin, D.; Serov, V.; Smirnov, A.; Shokov, V. A compact bit-sliced representation of Kuznyechik S-box. Mатематические вoпрoсы криптoграфии 2021, 12, 21–38. [Google Scholar] [CrossRef]
| Criterion | Definition / Meaning | Optimal Value |
|---|---|---|
| Bijectivity | One-to-one mapping between input and output, ensuring uniform distribution and balance. | Must be satisfied |
| NL | Distance from affine functions; higher NL strengthens resistance against linear cryptanalysis. | High |
| AD | Maximum degree of output Boolean functions; higher AD makes algebraic attacks harder. | High |
| DAP | Probability that a specific input difference leads to a specific output difference. | Low |
| LAP | Correlation between linear combinations of input and output bits. | Low |
| SAC | Probability that a single input bit flip changes each output bit. | 0.5 |
| BIC | Measures independence among output bits when an input bit is flipped. | High |
| TO, MTO, RTO | Indicators of resistance against DPA; lower values reduce leakage correlation. | Low |
| CCV, MCC | Correlation between leakage and key-dependent intermediates. | Low |
| SNR | Ratio of exploitable leakage to noise in side-channel signals. | Low |
| Name | |||
|---|---|---|---|
| S1 | 10,11,12,13,14,15,16,17 18,19,10,11,12,13,14,15 |
10,11,12,13,14,15,16,17 18,19,10,11,12,13,14,15 |
10,11,12,13,14,15,16,17 18,19,10,11,12,13,14,15 |
| S2 | 10,11,14,15,13,12,17,16 12,13,18,19,15,14,11,10 |
10,11,14,15,19,18,13,12 15,14,11,10,16,17,12,13 |
10,11,14,15,15,14,11,10 12,13,16,17,13,12,19,18 |
| S3 | 10,11,13,12,15,14,16,17 15,14,12,13,10,11,19,18 |
10,11,19,18,14,15,17,16 13,12,10,11,13,12,14,15 |
10,11,15,14,18,19,17,16 14,15,11,10,12,13,13,12 |
| S4 | 10,11,11,13,19,14,16,17 12,15,18,13,15,12,14,10 |
10,11,17,15,12,18,12,19 15,16,10,11,14,14,13,13 |
10,11,14,17,15,10,13,14 12,11,19,15,12,13,16,18 |
| S5 | 10,11,15,14,12,13,17,16 10,11,15,14,18,19,13,12 |
10,11,14,15,12,13,12,13 15,14,11,10,17,16,19,18 |
10,11,18,19,12,13,10,11 15,14,17,16,13,12,15,14 |
| S6 | 10,11,14,19,11,13,17,16 18,13,10,14,12,15,12,15 |
10,11,13,13,17,15,14,14 18,12,11,10,19,12,16,15 |
10,11,12,11,14,17,19,15 18,16,14,13,13,12,10,15 |
| S7 | 10,11,13,11,14,19,16,17 10,14,15,12,18,13,15,12 |
10,11,16,15,13,13,19,12 15,17,10,11,14,14,12,18 |
10,11,18,16,12,11,14,13 15,10,15,19,12,13,17,14 |
| S8 | 10,11,19,14,13,11,17,16 15,12,12,15,10,14,13,18 |
10,11,12,18,16,15,14,14 13,13,11,10,12,19,17,15 |
10,11,15,10,18,16,15,19 14,17,13,14,13,12,11,12 |
| Average NL | Number of S-Boxes) |
|---|---|
| 108 | 768 |
| 110 | 1536 |
| 112 | 3072 |
| 114 | 4608 |
| 116 | 2304 |
| i/j | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | A | B | C | D | E | F |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0 | 01 | 11 | 91 | E1 | D1 | B1 | 71 | 61 | F1 | 21 | C1 | 51 | A1 | 41 | 31 | 81 |
| 1 | 00 | 10 | 93 | E2 | D5 | B4 | 77 | 66 | F9 | 28 | CB | 5A | AD | 4C | 3F | 8E |
| 2 | 08 | 2C | 18 | F5 | 90 | 5D | E9 | C4 | D3 | 4E | BA | A7 | 72 | 8F | 6B | 36 |
| 3 | 0F | 3A | 84 | 1F | 4B | E0 | 9E | A5 | 26 | 6D | 73 | F8 | DC | C7 | 59 | B2 |
| 4 | 0C | 4F | 2E | D0 | 1C | A2 | F3 | BD | 98 | 86 | 57 | 79 | E5 | 3B | CA | 64 |
| 5 | 0A | 58 | B0 | 39 | C3 | 1A | 82 | DB | 65 | AC | 94 | 2D | 47 | 7E | F6 | EF |
| 6 | 06 | 67 | 3D | 2B | 8A | FC | 16 | 70 | 44 | C2 | E8 | DE | 9F | B9 | A3 | 55 |
| 7 | 07 | 76 | AF | C8 | 5E | 49 | 60 | 17 | BC | EB | 22 | 85 | 33 | F4 | 9D | DA |
| 8 | 0E | 8B | 46 | 9C | 2F | 75 | D8 | 52 | 1E | 34 | A9 | E3 | F0 | 6A | B7 | CD |
| 9 | 03 | 95 | D9 | 7D | F2 | C6 | AA | 3E | E7 | 13 | 6F | BB | 54 | 20 | 8C | 48 |
| A | 0D | AE | 5C | 63 | B8 | 27 | 35 | 9A | C0 | 7F | 1D | 42 | 89 | E6 | D4 | FB |
| B | 04 | B3 | C5 | 87 | 69 | 9B | 4D | FF | 32 | 50 | D6 | 14 | 2A | A8 | EE | 7C |
| C | 0B | C9 | 62 | 4A | 37 | DF | 24 | EC | 8D | B5 | FE | 96 | 1B | 53 | 78 | A0 |
| D | 05 | D2 | F7 | A4 | ED | 6E | 5B | 88 | 7A | 99 | 3C | CF | B6 | 15 | 40 | 23 |
| E | 02 | E4 | 7B | BE | A6 | 83 | CC | 29 | 5F | FA | 45 | 30 | 68 | DD | 12 | 97 |
| F | 09 | FD | EA | 56 | 74 | 38 | BF | 43 | AB | D7 | 80 | 6C | CE | 92 | 25 | 19 |
| S-Box | Year | Avg. NL | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| [4] | 2025 | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112.00 |
| [6] | 2024 | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112.00 |
| [7] | 2024 | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112.00 |
| [8] | 2024 | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112.00 |
| [9] | 2024 | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112.00 |
| [10] | 2023 | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112.00 |
| [17] | 2025 | 109 | 106 | 108 | 110 | 109 | 108 | 108 | 108 | 108.25 |
| [20] | 2024 | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112.00 |
| [22] | 2023 | 106 | 104 | 106 | 110 | 106 | 108 | 108 | 106 | 106.75 |
| [25] | 2023 | 106 | 102 | 106 | 106 | 106 | 104 | 106 | 098 | 104.25 |
| [29] | 2024 | 116 | 114 | 116 | 114 | 114 | 114 | 114 | 114 | 114.50 |
| [32] | 2024 | 112 | 110 | 112 | 112 | 110 | 110 | 110 | 112 | 111.00 |
| [33] | 2024 | 112 | 112 | 112 | 110 | 112 | 112 | 112 | 112 | 111.75 |
| [36] | 2023 | 110 | 108 | 110 | 108 | 110 | 108 | 110 | 108 | 109.00 |
| [53] | 2024 | 104 | 106 | 106 | 104 | 110 | 106 | 112 | 104 | 106.50 |
| [66] | 2024 | 104 | 106 | 108 | 108 | 104 | 102 | 100 | 102 | 104.25 |
| [67] | 2001 | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112 | 112.00 |
| This work | 2025 | 116 | 116 | 116 | 116 | 116 | 116 | 116 | 116 | 116.00 |
| i/j | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 |
|---|---|---|---|---|---|---|---|---|
| 1 | 0.5000 | 0.5000 | 0.5000 | 0.5000 | 0.5469 | 0.5469 | 0.5313 | 0.5469 |
| 2 | 0.5000 | 0.5000 | 0.4375 | 0.5000 | 0.5313 | 0.5313 | 0.5313 | 0.5469 |
| 3 | 0.5000 | 0.4375 | 0.5000 | 0.5000 | 0.5313 | 0.5313 | 0.5469 | 0.5469 |
| 4 | 0.4375 | 0.5000 | 0.5000 | 0.5000 | 0.5313 | 0.5469 | 0.5469 | 0.5313 |
| 5 | 0.5469 | 0.5469 | 0.5313 | 0.5469 | 0.4375 | 0.5000 | 0.5000 | 0.5000 |
| 6 | 0.5313 | 0.5313 | 0.5313 | 0.5469 | 0.4375 | 0.5000 | 0.5000 | 0.5000 |
| 7 | 0.5313 | 0.5313 | 0.5469 | 0.5469 | 0.4375 | 0.5000 | 0.5000 | 0.5000 |
| 8 | 0.5313 | 0.5469 | 0.5469 | 0.5313 | 0.4375 | 0.5000 | 0.5000 | 0.5000 |
| i/j | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 |
|---|---|---|---|---|---|---|---|---|
| 1 | - | 116 | 116 | 116 | 110 | 108 | 108 | 108 |
| 2 | 116 | - | 116 | 116 | 108 | 108 | 108 | 108 |
| 3 | 116 | 116 | - | 116 | 108 | 110 | 108 | 108 |
| 4 | 116 | 116 | 116 | - | 110 | 108 | 108 | 108 |
| 5 | 110 | 108 | 108 | 110 | - | 116 | 116 | 116 |
| 6 | 108 | 108 | 110 | 108 | 116 | - | 116 | 116 |
| 7 | 108 | 108 | 108 | 108 | 116 | 116 | - | 116 |
| 8 | 108 | 108 | 108 | 108 | 116 | 116 | 116 | - |
| i/j | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 |
|---|---|---|---|---|---|---|---|---|
| 1 | - | 0.5176 | 0.5156 | 0.5078 | 0.4902 | 0.5117 | 0.5059 | 0.5020 |
| 2 | 0.5176 | - | 0.5137 | 0.5156 | 0.5039 | 0.5117 | 0.5332 | 0.5117 |
| 3 | 0.5156 | 0.5137 | - | 0.5156 | 0.5059 | 0.5176 | 0.5254 | 0.5039 |
| 4 | 0.5078 | 0.5156 | 0.5156 | - | 0.4941 | 0.5195 | 0.5078 | 0.5117 |
| 5 | 0.4902 | 0.5039 | 0.5059 | 0.4941 | - | 0.5098 | 0.5078 | 0.5078 |
| 6 | 0.5117 | 0.5117 | 0.5176 | 0.5195 | 0.5098 | - | 0.5059 | 0.5078 |
| 7 | 0.5059 | 0.5332 | 0.5254 | 0.5078 | 0.5078 | 0.5059 | - | 0.5078 |
| 8 | 0.5020 | 0.5117 | 0.5039 | 0.5117 | 0.5078 | 0.5078 | 0.5078 | - |
| 0 | 6 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 6 | 4 | 6 | 4 | 6 | 6 | 4 |
| 4 | 4 | 4 | 6 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 6 | 4 |
| 4 | 4 | 6 | 4 | 4 | 4 | 4 | 4 | 4 | 6 | 4 | 4 | 4 | 4 | 4 | 4 |
| 4 | 4 | 4 | 4 | 4 | 6 | 4 | 4 | 4 | 4 | 4 | 6 | 4 | 4 | 4 | 4 |
| 4 | 4 | 4 | 4 | 6 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 6 | 4 | 4 |
| 4 | 6 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 |
| 4 | 6 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 |
| 4 | 4 | 4 | 4 | 6 | 4 | 4 | 4 | 4 | 4 | 4 | 6 | 4 | 4 | 4 | 6 |
| 4 | 4 | 4 | 6 | 6 | 4 | 6 | 6 | 4 | 4 | 6 | 6 | 6 | 4 | 4 | 4 |
| 4 | 4 | 6 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 4 | 6 | 4 | 6 | 4 |
| 4 | 4 | 6 | 4 | 6 | 4 | 6 | 6 | 6 | 4 | 4 | 4 | 4 | 4 | 6 | 6 |
| 4 | 4 | 4 | 6 | 4 | 4 | 4 | 4 | 4 | 6 | 4 | 4 | 4 | 4 | 4 | 4 |
| 4 | 4 | 4 | 6 | 4 | 6 | 6 | 6 | 6 | 6 | 4 | 4 | 4 | 4 | 4 | 6 |
| 4 | 4 | 6 | 4 | 4 | 6 | 6 | 6 | 4 | 4 | 6 | 4 | 6 | 6 | 4 | 4 |
| 4 | 4 | 4 | 4 | 4 | 6 | 4 | 4 | 6 | 4 | 4 | 4 | 4 | 6 | 4 | 4 |
| S-Box | Year | NL | BIC-NL | SAC | BIC-SAC | DAP | LAP | FP | OFP |
|---|---|---|---|---|---|---|---|---|---|
| [4] | 2025 | 112.00 | 107.14 | 0.5009 | 0.4780 | 0.070 | 0.125 | 0 | 0 |
| [6] | 2024 | 112.00 | 112.00 | 0.5049 | 0.5046 | 0.016 | 0.063 | 2 | 1 |
| [7] | 2024 | 112.00 | 112.00 | 0.5032 | 0.5057 | 0.016 | 0.063 | 1 | 2 |
| [8] | 2024 | 112.00 | 112.00 | 0.5044 | 0.5047 | 0.016 | 0.063 | 1 | 1 |
| [9] | 2024 | 112.00 | 103.07 | 0.5014 | 0.4979 | 0.039 | 0.133 | 0 | 0 |
| [10] | 2023 | 112.00 | 112.00 | 0.4892 | 0.5017 | 0.016 | 0.063 | 0 | 1 |
| [17] | 2025 | 108.25 | 108.79 | 0.5063 | 0.5019 | 0.031 | 0.105 | 0 | 2 |
| [20] | 2024 | 112.00 | 112.00 | 0.5045 | 0.5042 | 0.016 | 0.063 | 0 | 0 |
| [22] | 2023 | 106.75 | 103.57 | 0.5026 | 0.5019 | 0.039 | 0.132 | 2 | 0 |
| [25] | 2023 | 104.25 | 104.00 | 0.5029 | 0.5026 | 0.047 | 0.125 | 0 | 0 |
| [29] | 2024 | 114.50 | 103.29 | 0.4976 | 0.5050 | 0.039 | 0.133 | 2 | 1 |
| [32] | 2024 | 111.00 | 111.43 | 0.5017 | 0.5034 | 0.023 | 0.070 | 2 | 0 |
| [33] | 2024 | 111.75 | 111.00 | 0.5034 | 0.5050 | 0.023 | 0.070 | 1 | 0 |
| [36] | 2023 | 109.00 | 103.86 | 0.4936 | 0.5057 | 0.039 | 0.156 | 0 | 1 |
| [53] | 2024 | 106.50 | 103.21 | 0.5034 | 0.5040 | 0.039 | 0.148 | 1 | 0 |
| [66] | 2024 | 104.25 | 104.23 | 0.5056 | 0.5001 | 0.055 | 0.133 | 1 | 2 |
| [67] | 2001 | 112.00 | 112.00 | 0.5048 | 0.5046 | 0.016 | 0.063 | 0 | 0 |
| This work | 2025 | 116.00 | 111.64 | 0.5126 | 0.5103 | 0.023 | 0.078 | 0 | 0 |
| Ideal value | – | High | High | 0.5000 | 0.5000 | Low | Low | 0 | 0 |
| S-Box | Year | MCC | CCV | SNR | |||
|---|---|---|---|---|---|---|---|
| [4] | 2025 | 7.852 | 6.872 | 7.432 | 0.800 | 0.116 | 14.950 |
| [6] | 2024 | 7.860 | 6.870 | 7.458 | 0.820 | 0.111 | 14.470 |
| [7] | 2024 | 7.851 | 6.905 | 7.541 | 0.844 | 0.080 | 12.219 |
| [8] | 2024 | 7.852 | 6.853 | 7.450 | 0.770 | 0.122 | 15.565 |
| [9] | 2024 | 7.833 | 6.833 | 7.373 | 0.738 | 0.148 | 19.973 |
| [10] | 2023 | 7.853 | 6.888 | 7.468 | 0.808 | 0.109 | 14.219 |
| [17] | 2025 | 7.844 | 6.843 | 7.467 | 0.855 | 0.111 | 15.162 |
| [20] | 2024 | 7.804 | 6.815 | 7.431 | 0.805 | 0.125 | 15.951 |
| [22] | 2023 | 7.820 | 6.850 | 7.440 | 0.820 | 0.117 | 15.088 |
| [25] | 2023 | 7.797 | 6.810 | 7.409 | 0.820 | 0.129 | 16.500 |
| [29] | 2024 | 7.854 | 6.903 | 7.441 | 0.804 | 0.115 | 14.877 |
| [32] | 2024 | 7.852 | 6.853 | 7.439 | 0.820 | 0.120 | 15.353 |
| [33] | 2024 | 7.858 | 6.865 | 7.463 | 0.820 | 0.109 | 14.276 |
| [36] | 2023 | 7.812 | 6.820 | 7.466 | 0.750 | 0.113 | 14.594 |
| [53] | 2024 | 7.807 | 6.794 | 7.401 | 0.785 | 0.143 | 18.837 |
| [66] | 2024 | 7.846 | 6.866 | 7.418 | 0.787 | 0.121 | 15.180 |
| [67] | 2001 | 7.860 | 6.869 | 7.458 | 0.820 | 0.111 | 14.473 |
| This work | 2025 | 7.908 | 6.967 | 7.511 | 0.801 | 0.092 | 12.991 |
| Ideal value | – | Low | Low | Low | Low | Low | Low |
| Studies | XOR/ XNOR |
NAND/ NOR |
AND | OR | NOT | MUX21 | GE (*) |
|---|---|---|---|---|---|---|---|
| [43] | 76 | 56 | 0 | 0 | 0 | 0 | 208.00 |
| [44] | 107 | 10 | 38 | 7 | 5 | 8 | 301.75 |
| [71] | 91 | 36 | 0 | 0 | 0 | 0 | 218.00 |
| [72] | 87 | 0 | 54 | 0 | 0 | 0 | 241.50 |
| [73] | 79 | 41 | 0 | 0 | 0 | 0 | 199.00 |
| [74] | 57 | 80 | 0 | 0 | 0 | 0 | 194.00 |
| [75] | 154 | 0 | 36 | 0 | 0 | 8 | 369.00 |
| [76] | 64 | 23 | 4 | 0 | 0 | 6 | 168.00 |
| [77] | 90 | 0 | 79 | 28 | 29 | 0 | 342.25 |
| Proposed S-Box | 43 | 0 | 39 | 6 | 0 | 8 | 159.75 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





