1. Introduction
The cloud computing paradigm of elasticity, cost efficiency, and innovation at scale becomes the underpinning of modern IT designs [
1,
2]. But growing things up only invites a different kind of headache, because cloud systems are swimming against a rising tide of cyber security problems — like insider attacks, zero-day exploits, etc. [
3] Traditional network perimeter security, while effective in static, centrally managed topological, often provides little to no value in the elastic world of cloud-native workloads [
4,
5]. These are not visible and manageable for distributed environment in the older models and so there is exposure of Organizations [
6,
7].
To ameliorate this difficulty, the use of artificial intelligence in security workflows across the Software Development Life cycle (SDLC) is a possible promising approach [
8,
9,
10]. Within the security context, AI may provide support and automation for anomaly detection [
11,
12,
13,
14]12, breach prediction, response automation [
15,
16] and law enforcement [
17,
18]. In this way organizations will be able to mitigate clouds security more directly and flexibly [
19,
20], and less trust in defensive techniques [
21,
22,
23].
AI learning based systems enhance visibility in the cloud as dynamic patterns and attack vectors of data are discovered [
24,
25]. ML systems capable of dynamic threat modelling and real-time risk analysis at scale not feasible with manual operations [
26,
27]. These intelligent systems can also adapt to new attacks by consuming data on the fly and making context-aware decisions [
28,
29].
Furthermore, AI can support secure coding practices and the testing of the code in DevOps pipelines by automatically reviewing the code, identifying the vulnerabilities and applying the compliance polices [
30,
31,
32]. Moreover, the end-to-end integration also reduces potential for human error mini-kube facilitates securing the applications to deploy it faster [
33,
34]. As the adoption of cloud services in multi-cloud and hybrid cloud environments is growing, there is a need for automated, scalable and intelligent security mechanisms [
35,
36,
37,
38,
39,
40].
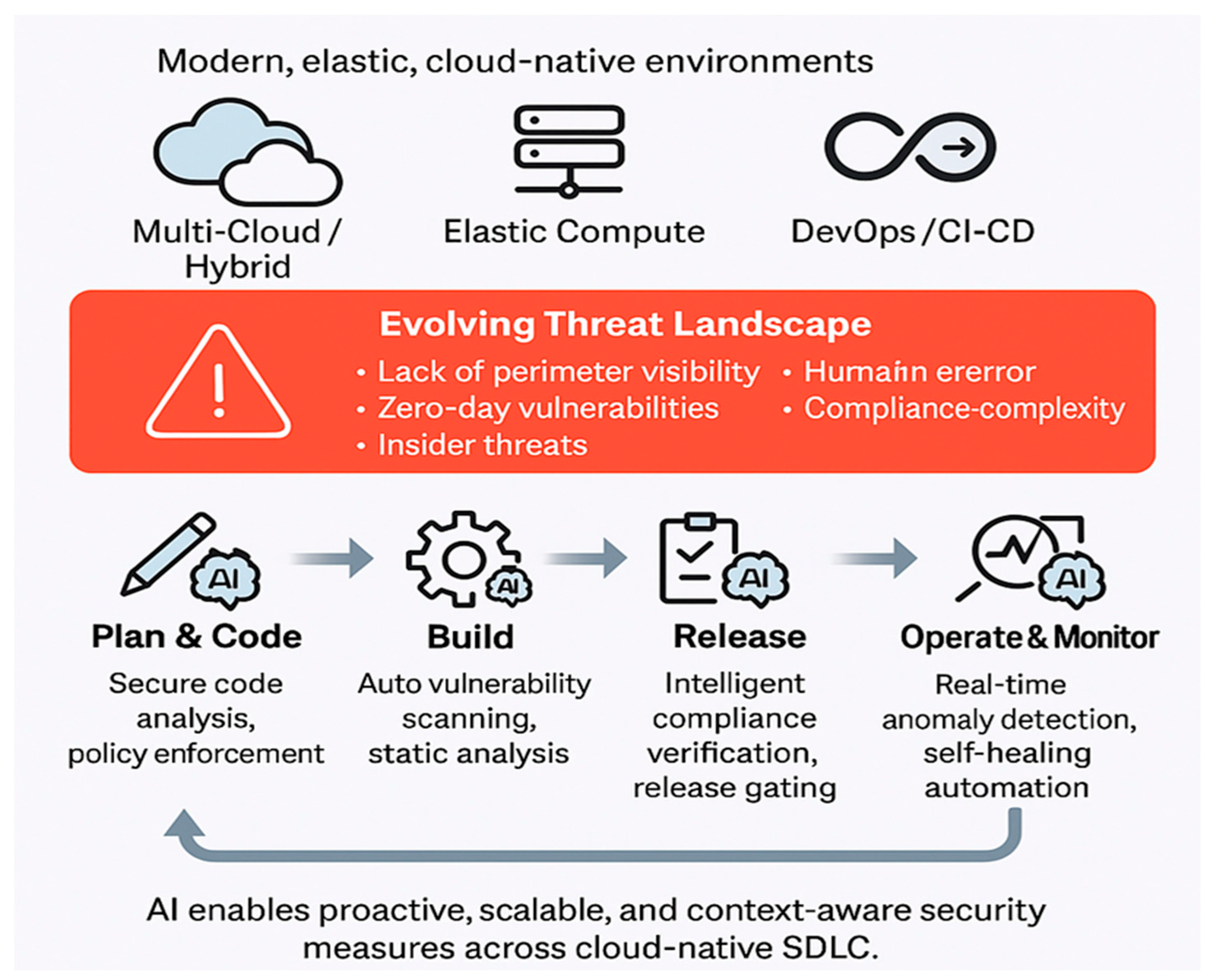
Figure 1.
AI at different stages.
Figure 1.
AI at different stages.
The integration of AI throughout an SDLC [
25] alters the manner in which the organizations build, launch, and protect cloud-native applications. This move away from reactive defense to proactive, AI-driven security allows businesses to stay one step ahead of sophisticated cyber threats in today’s fast paced and ever-changing cyber environment, and meet agility and compliance requirements in this cloud era.
2. Background and Motivation
2.1. Security Challenges in Cloud Computing
Cloud computing systems are naturally complex due to the distributed and dynamic nature of the whole systems. As organizations are heading to hybrid and multi cloud infrastructures the classic model of security perimeters gets stage-frighten [
41,
42]. Dynamic attack surfaces is a major challenge in such environments. These surfaces are dynamically changing as applications ramp virtual machines, containers or services in or out, i.e., instantiate or decommission, services as they run [
43]. This dynamism makes it difficult to keep a stable security posture, as security tooling must follow dynamic workloads in real time [
44,
45].
In multi-tenant environments - where resources are consumed collectively by multiple users or organizations-this problem is asso ciated with identity and access management(IAM) [
46]. Good IAM is when no one has more than just the stuff they need to sit on “least privilege.” But privilege escalation or Lateral movement in the system due to misconfiguration and decentralization may exist [
47]. Moreover, offering separation of duty, auditing activity across tenants is an arduous and important work to defend unauthorized ingress or insider threats [
48,
49].
CommonlySP uses APIs to integrate with cloud services, which makes this challenge even more difficult to solve. APIs, by their very nature, were created to be an interface between applications and systems, facilitating interconnectivity, bringing about a new bible of attack surfaces which range as a means no proper authorisation or abuse to bad design or otherwise [
50,
51]. One of the common breach is through insecure APIs where an attacker exploits these vulnerabilities to get access to confidential data or systems [
52]. By how common they are in contemporary cloud designs, APIs should be near the top already: solid testing, strong authentication and steady monitoring with it.
Finally, operational overhead has been minimized with Infrastructure-as-Code (IaC), that allows configuration of infrastructure to be deployed automatically. But it has also introduced new security challenges to the system [
53,
54]. Configuration file misconfigurations have also been attributed to some of the worst exposures to the internet — publicly exposed storage buckets, security groups that are open to the world and credentials without any permissions [
55]. This type of misconfiguration can be present in several locations in the environments via the CI/CD pipelines, so it is a big issue detecting and patching it quickly.
Another open problem in cloud is that you may not understand or even see third-party services, and containerized workloads [
56,
57]. It is industry standard that organizations may include external libraries, open source modules and other Software as Service (SaaS) integrations into their applications and many at times these components may cover-up the vulnerabilities or backdoors [
58,
59,
60]. Containers and VMs protect against scale and portability, but could also introduce security blind spots, if they are not scanned for vulnerabilities and abnormal behaviors. This limited visibility also restricts the organisation from performing a comprehensive risk assessment and applying consistent policies against threats at the application and network layers.
2.2. Limitations of Traditional Security
‘‘ Signature - Based Threat mitgiations are unable to calibrate with Dynamic, Polymorphic and ever-increasing pools of threats In the sequence diagram, Threat Analysis Engine represent the Signature-based Approach method [
61]. These approaches were developed in a world of monolithic on-premises systems that were rigid and incapable of easily adapting to the agile workloads imposed upon them, there was little need for systems to be highly dynamic and workloads would become predictable and not rapidly changing [
62]. However, they are inadequate for dynamic cloud-native environments with CI, CD, and scaling [
63]. Notably, one shortcoming of these legacy systems is the inability to efficiently detect new or modified threats, also known as polymorphic threats: malicious behaviors that modify or mutate signatures so as to avoid being detected [
64,
65]. Static rules and subsignature databases are constantly behind zero-days and advanced attacks, which frequently leverage AI and automatization, internally [
66].
In addition, traditional manual incident response processes and outdated tools are far too sluggish to respond to the pace of cloud operations [
67]. In case of cloud deployments, it can take seconds to spin-up new instances only for them to get compromised while human-based detection and triage takes minutes to hours [
68]. This latency is potentially problematic in the face of rapid-moving attacks like ransomware and post-compromise motion within virtualized environments [
69]. It is the reactive nature of such defensive strategies that attacks can be detected only after a successful entry which already leads to a considerable amount of downtime and reputation loss [
70].
On top of that, security technologies are traditionally separate, and side by side with the develop and deployments. [
71] Traditional approaches do not work well for fast Automation and Continuous delivery, particularly if the environment has had a culture Nurtured around DevOps or agilemethodsthat deploys "little and often" [
72]. They also lack any integrations with CI/CD pipelines and IaC workflows to enable proactive security enforcement at build and deployment time [
73,
74]. As such, security holes can be put in place during the early stages of development and not realized until too late and be relatively expensive to address and, more importantly, leaves such applications open for attack [
75].
3. Role of AI in Security Integration
3.1. AI Capabilities in Cloud Security
AI to revolutionize cloud security with intelligent, adaptive and automated defense systems [
76]. Anomaly detection is a classic application of AI in this domain, based on historical and current telemetry data identifying behavioral anomalies that frequently denote threats [
77]. Unlike rule-based systems, such approaches adapt on the fly to the patterns found in data and, over time, discern even subtle new attack vectors such as insider threats, lateral movement and misconfigurations [
78].
Exponentialadvantageof AI for security operations also means alert fatigue DIE. Traditional security systems always create too much false positives, burdening the SOC and holding back on incident response. AI is addressing this challenge by categorizing alerts by means of a contextual examination, eliminating useless alarms, and prioritising threats based on their impact and severity [
79]. This enables faster triage and faster processing of real alerts.
And AI supercharges automated policy enforcement and compliance validation. AI engines can continually scrutinize system settings, access controls, and data flow configurations for compliance against industry and regulatory norms (e.g. GDPR, HIPAA, ISO 27001) [
80]. Such systems can correct mis-matches or mis-conduct by themselves (they can be self-enforcing in other words) without the intervention of permanent human staff.
Most importantly, however, AI involves responsive systems with the ability to automatically reciprocate. These systems can isolate the impacted workloads, kill the malicious processes, change the credentials, or re-write security policy on-the-fly [
81]. This quick reaction not only limits the attack’s blast radius, but also better arm the cloud infrastructure to (re)learn and defend itself from ongoing attacks automatically, so cloud infrastructure can defend itself and self-heal without the need for human intervention as it learns from continuous attacks.
3.2. AI Techniques Used
It is intuitive that ML can have a large impact and, possibly, it can be employed in several cloud security domains [
82]. Supervised learning is used in several classification tasks such as malicious code detection, authorship identification, and role based access control [
83]. Such models are trained using labeled benign and malicious data and are therefore able to accurately distinguish benign from malicious behavior [
84]. Eventually, the supervised models which become finer with the addition of labeled data achieve higher accuracy in threat classification [
85].
On the other hand, unsupervised learning does not utilize labeled data, and it is also an excellent technology for detecting unknown or zero-day threats [
86]. [
87] also points to unsupervised models to, given user activities, network flows or system logs, spot anomalies as an indicator of a potential security breach. Algorithms like clustering and dimension reduced are employed to reveal underlying patterns from multidimensional data which aids in early identification of subtle and unknown attack vectors [
88].
RL may serve as a good path to adaptive security. Strong defense strategies are also learned via RL, where the game agent interacts with the environment and receives rewards/penalties [
89]. These models update and act on feedback of their interventions (e.g. blocking traffic, isolating nodes, adding new rules) to adapt their policy so that optimum long-term protection can be achieved [
90]. These more and more dynamic cloud environments are good candidates for RL (since the number of threats and attack possibilities is growing and a (static) rule set has to be modified after a short period of time).
In addition, Natural Language Processing (NLP) is critical for making sense of unstructured data sources such as system logs, security reports, emails, and policy [
92]. Copyright line NLP has capabilities to detect insider threats by analyzing language patterns, sentiment and intent in communications [I09]. It is also employed for an automatic parsing of compliance docs and finds non-compliant process and incomplete controls in textual policies [
94]. Given that cloud systems increasingly rely on human-resource interaction, NLP systems ultimately provide greater situational awareness and inter alia are employed for document analysis [
95].
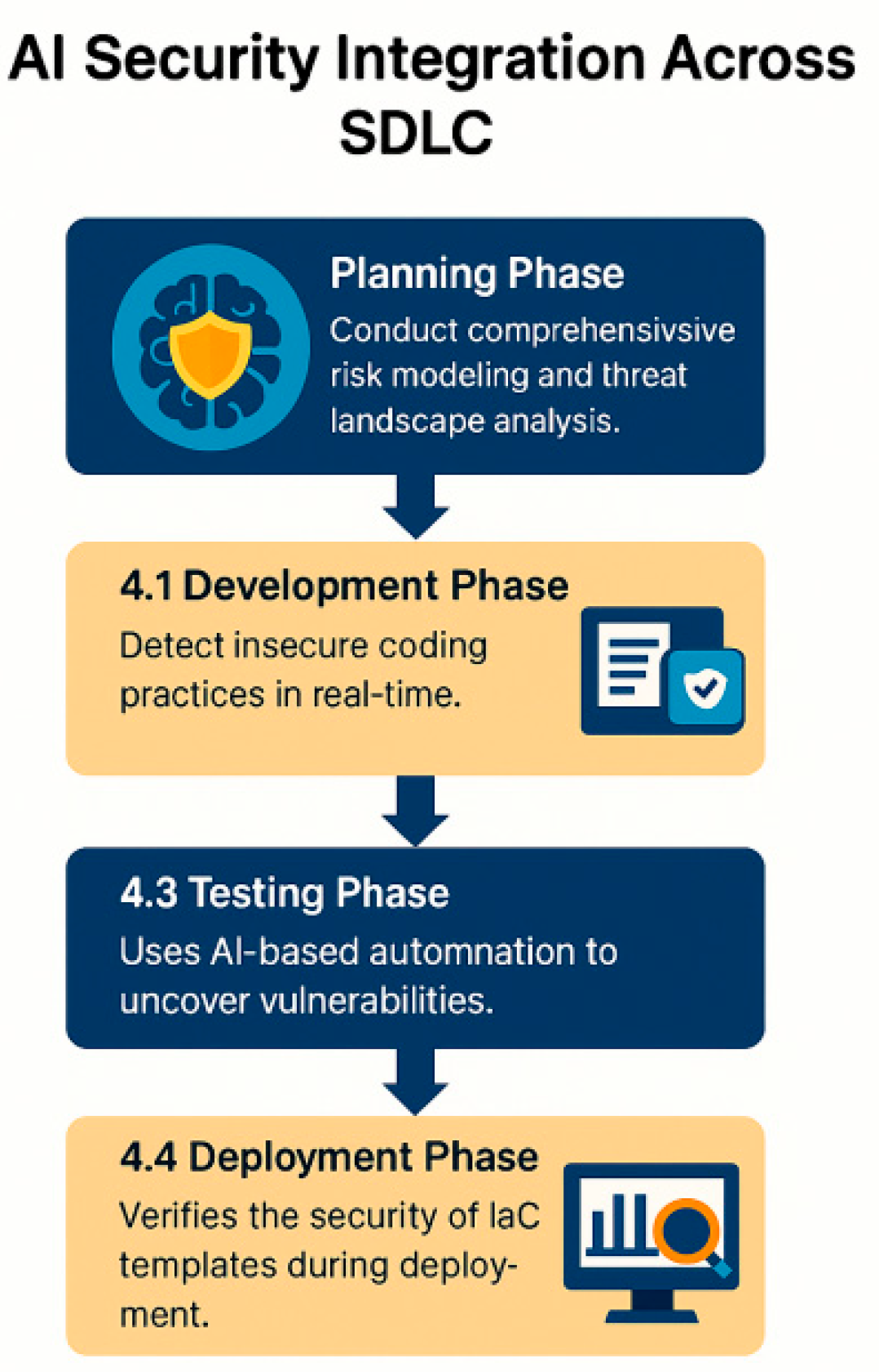
4. AI Security Integration Across SDLC
The Software Development Lifecycle (
Figure 2) can easily close the loop of how artificial intelligence can be incorporated at each stage of the lifecycle to enhance cloud security from development through operation [
96,
97,
98].
4.1. Planning Phase
Planning AI-enabled full risk modeling and threat landscape analysis is conducted during the planning phase. By using historical breaches and contemporary threat intelligence, AI will be able to pinpoint vulnerabilities before they have a chance to spread. Project documents, user stories, and architectural design can be analyzed by NLP engines in order to detect security holes as early as possible so that security can be considered from the beginning.
4.2. Development Phase
In the development process state-of-art AI-based code analysis tools can screen insecure coding practices in real-time. Tools such as DeepCode or GitHub Copilot pour over source code to highlight flaws like buffer overflows, injection flaws and hardcoded credentials. Predictive models can predict the complexity and maintainability of the code to find vulnerability. These tooling systems assist developers in writing secure code without a contextual break in workflow.
4.3. Testing Phase
The testing part is particularly well-suited for getting amplified with automation based on AI. AI fuzzers produce vast amounts of random input to test application robustness and reveal latent vulnerabilities. Machine learning models can be developed to score the tests results and detect anomalous behavior. It mitigates the need for manual test script development and increases the effectiveness of security testing.
4.4. Deployment Phase
During deployment, AI confirms that your infrastructure-as-code templates are secured by scanning them for misconfigurations and policy violations. These analyses also address common problems such as open ports, unnecessary access, or exposed secrets. Further, AI is able to assess container images and their behavior to identify discrepancies from known baselines to make sure only known good, secure workloads are run.
4.5. Operations and Monitoring
After production, AI is an integral part of operations and monitoring. 3.5 AI-based Intrusion Detection Systems AI-based Intrusion Detection Systems keep comparing the input network and system traffic to detect whether there are any typical or abnormal signs of intrusion. AI-automated compliance monitoring which tracks changes to the systems against a wide range of regulations. When an incident occurs, AI-based incident response tools can leverage predefined responses to address the threat and limit the fallout.
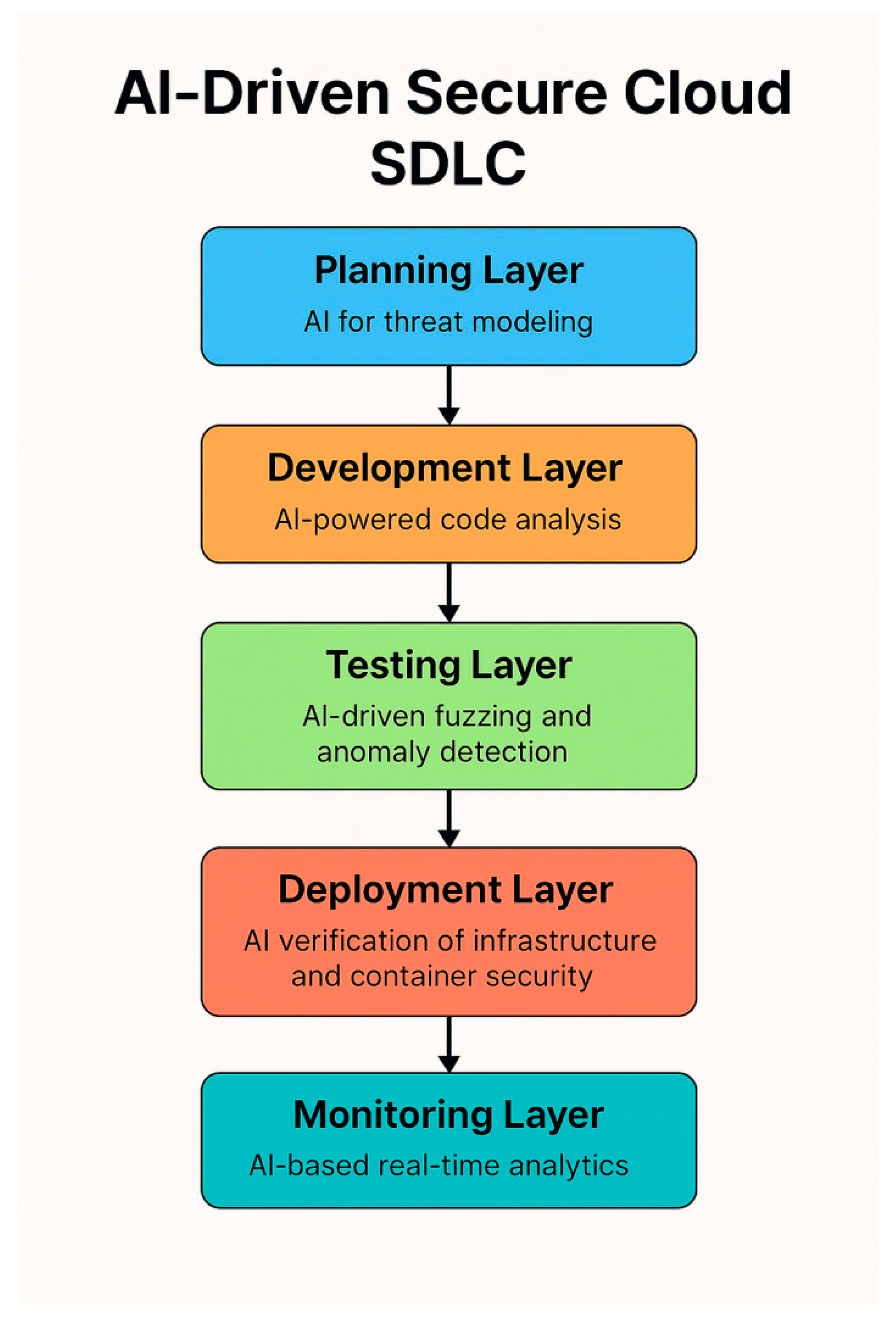
5. Framework: AI-Driven Secure Cloud SDLC
The envisioned AI-driven security integration model across SDLC is shown in
Figure 3 where it holds a end-to-end, layered AI centric integrated approach to SDLC phases of development and operations. The method provides a way to ensure that cloud-native deployments are proactive about addressing the type of security issues by ensuring that smart, automated, adaptive software security is built into each stage of the software process. This continuous framework, made up of five stages, planning, development, testing, deployment, and monitoring, ensures that security is not something that is done as an activity once, for any cloud-based application lifecycle.
AI is used in early design design to inform secure architectural decisions and strategies. In the planning phase, AI is employed for threat modeling and advanced risk profiling. AI has potential to be learned from the past cybersecurity attacks, vulnerabilities attack reports, or threat intelligence feeds in order to predict potential attackers based on the architecture of the application in question. These predictions help design teams make early decisions on technology stack selection, third- party integration requirement, access control methods.
NLP machines can be added to this stage, analyzing user stories, design docs, policy text, to spot likely security gaps and inconsistencies. Developing this orientation also ensures that security considerations are not merely bolted on as a layer, but baked in from the start. By integrating AI into planning they can: avoid downstream exposures, avoid costly re-designs, and be secure-by-design.
The switch from train_phases to develop_phases is where AI actually begins to act in a live environment. AI-based code analysis tools may comprise (i) Continuos monitoring and analysis of the source code while being written. These toolsets such as DeepCode, or GitHub’s Copilot with its underlying security models, generate security models and search for well-known vulnerabilities such as SQL injection, buffer overflow, and cross-site scripting (XSS). These machine learning models are based on large collections of safe and unsafe code, and can automatically recognize unsafe patterns and suggest safe alternatives to developers as they code.
Moreover, AI can scan the maintainability, modularity, and complexity of code and indicate suspicious constructs, where a complex or suboptimal implementation may emerge. That power of prediction means security is not just locking down against certain, specific bugs, it’s making code that is solid over time. AI improves developer productivity by integrating into dev environments to enable devs to solve security issues without ever leaving their flow.
Security testing is also bottlenecked in the SDLC, as it has traditionally been performed manually and is slow. AI is also affecting this phase, through the automation of essential testing activities. AI-fuzzing tools can generate such diverse random and non-random input to interactively scrutinize the boundaries and logic of applications. These tests uncover edge cases and exploits that are often overlooked by human testers.
Learned algorithms enhance a runs analysis with knowledge on the detected anomalous behavior of an application, which could be an indicator of a security hole. For instance, if a particular input always signifies some odd memory behavior or error messages, AI systems can label this input as a suspicious input. These classifiers are continuously re-trained on the historical test logs in order to capture new application behaviors and threat profiles. So testing is faster, more accurate and more complete than it would be, which helps in making applications more robust before they go into production.
Running in cloud offers like that whole new set of deployment challenges that you need to solve for, infrastructure miscommunications, insecure container images, mountain of policy violations. YC-Clouddeck - Clouddeck is AI-driven cloud-native deployment layer to fix that, it intelligently check IaC (infrastructure-as-code) templates for security issues. This includes open ports, too-privileged roles, unencrypted data and other more common configurations.
Besides the static analysis, AI monitor the behavior of container images and workloads deployed. Performance and behavior is simulated for IP blocks using a base lined behavior. Deviation from that norm, such as weird network calls or resource spikes, can cause automatic alerts or actions. AI can even influence policy, by banning deployments which do not meet pre-stated security criterion. That ensures that only verified, compliance-compatible software gets promoted to production.
The final layer of the framework focuses on security in production. Most industries rely on AI-based IDS (Intrusion Detection Systems) to monitor real-time network traffic, user activity, and system logs. These platforms utilize advanced machine learning anomaly detection mechanisms that can detect malicious behavior that may be indicative of lateral movement, brute-force attempts, and information theft.
Automated Compliance Monitoring AI Training and offers automated compliance monitoring as well where it audited continuously the system config and activities matching against what’s offered by the regulatory standards like GDPR, HIPAA or ISO 27001. If mismatch are found, AI can take corrective actions automatically or prompt support professionals. In a security event, response systems driven by AI can quarantine affected operations, reset configurations and institute containment measures within seconds or minutes, not hours or days.
By the feedback loop for detecting and responding, the monitoring layer ensures the resilience and adaptiveness of the cloud. AI isn't only reactive, but predictive and adaptive in a time of rapidly shifting threat landscapes.
Together, these five layers create one holistic AI-powered security architecture that nicely aligns with the modern agile and DevOps-focused philosophies of cloud computing today. This model turns security from a check-point type solution to a smart player in the software development, deployment space.
6. Case Studies
For a sense of what it looks like, in practice, to apply AI to cloud security, there are industry case studies that provide tangible evidence of the benefits any organization will gain by deploying AI to their cybersecurity operations [
98,
99,
100].
In finance, a leading bank used machine learning anomaly detection to increase the security of its cloud-based transaction systems. Generations of earlier transaction logs and behavior analytics had schooled this system to be able to recognize what normal was. If it found something odd, something trippy, so if you are transacting in odd times of the day or you are coming into a bank that we didn’t expect or that you are not coming to a bank, inside a customer journey, we flagged that and escalated that internally and started to investigate. Thus, the institution was able to cut threat detection time by 68%, and reduce the number of false positives by 40%, allowing it to use much less of the time of its security team in chasing benign anomalies. This roll-out improved how they did business-as-usual while ensuring compliance to financial governance (such as PCI-DSS) as ever.
And in the healthcare business, guarding against HIPAA violations, cloud platforms holding patient targeting data should all have hacker-proof security controls. One large regional healthcare organization deployed an encryption-key lifecycle automation solution based on AI, enabling it to automatically ensure that the correct keys were issued, rotated and expired in a secure manner. Access logs were used to trigger AI algorithms that were fed with access logs as they are filled (real-time) and compared with user roles, and a historical user accesses to be able to raise alerts on any suspicious access attempt. This strategy accomplished continuous compliance and removed a good deal of administrative overheads, enabling IT staff to focus on how their system is running rather than manually auditing and managing keys.
A e-commerce organization tackled the frequently forgotten challenge of insider threats by incorporating NLP models as part of their development cycle. The models scoured developer comments, version control messages and internal communications for hints of subtle patterns of shifts in intent and sentiment, which might be evidence of mischief-making. Over a six-month period this system detected a number of potentially harmful interactions that were rapidly corrected. Overall, the company was able to reduce insider risk exposure by 25%, demonstrating the potential for AI to help organizations better detect and prevent the human-focused security threats inherent in a collaborative cloud development model.
Together, these cases demonstrate how AI enhances cloud security, providing it with the scale, flexibility and intelligence that older models lack. Machine learning allows even smallest companies to evolve detection of anomalies, automated security cryptography and behavior analysis to adapt to their unique security niches far better: AI in your defense.
7. Challenges and Considerations
Although there is much hype about AI and cloud security evolution, it poses significant challenges as well. The first one is data privacy: models are commonly trained on privacy-sensitive data (e.g. user behavior logs, communication content or system access records). Regulated and ethical AI will require the adoption of privacy safeguarding mechanisms — data anonymization, federated learning and differential privacy.
"More urgently, the fairness and equity of the training data are that problem. AI systems are only as good as the data they are trained on. Biased, Incomplete or Outdated Data: If the model itsel Bad models could cause the system to miss real threats, or it might raise too many false positives. Operational excellence Your data pipelines must run and run properly in terms of expected time to and accuracy of data ingestion.
Explainability and transparency of AI-inferences is also an important point in the security context. Security analysts are often required to justify why a model generated an alert or recommendation. But although black-box models can be high-performing, they have the potential to diminish trust and accountability. Ultimately, the long-term goal is to either (a) give an interpretable model or (b) one can embed the explainable AI (XAI) techniques that could compensate and bridge this trust-gap between the automation and the human user 28.
COMPUTATIONAL COST - On top of that, running and installing/supporting AI systems can be very expensive. Especially SMEs may lack the resources or expertise to develop, optimize, and maintain AI models by themselves. This has presented a tantalization but fraught decision between AI-as-a-service and cloud-based security offerings.
Lastly, adversarial attack to AI models are becoming problem. Attackers can even manipulate permissive model logic or poison data in order to influence outcomes. Robustness testing, model hardening and continuous monitoring against such AI-specific vulnerabilities will be required.
8. Conclusions
AI techniques for cloud Comp.’ security is a step forward from older security defense methods that have security being reactive, toward intelligent and more proactive securers and adaptive. Legacy methods are not scalable or nimble enough to match the speed and expertise of modern threats and the operational needs of multi-cloud environments. AI reins in these issues by detecting anomaly, auto compliance, auto response intelligently, and behavior analysis, empowering security operations to work at the same speed and scale of cloud native.
By embedding AI at all stages of the Software Development Lifecycle (SDLC) – planning, development, deployment, and monitoring – businesses can shift from security as an afterthought to security by design. Its this layered model the model that informed the model introduced in this paper abstract focuses on the way AI capabilities support to specific security outcomes to offer continuous protections across differing workloads.
Real-world applications in finance, healthcare, and e-commerce exhibit practical benefits of, and effectiveness achieved through, applying AI to security, and discussion on challenges indicates future research and development. With growing security threats of an advanced nature AI will play a pivotal role in securing and maintaining a clean cloud environment.
“Put simply, the future of cloud security is the smart and beneficial integration and orchestration of AI to support – not replace – human talent by guiding decision-making, automating repetitive tasks and pinpointing potential trouble spots across a distributed enterprise operating in a fluid digital economy.”
References
- Sidharth, S. (2024). Advanced Threat Detection Using AI-Driven Anomaly Detection Systems.
- Singh, B. (2025). Advanced Oracle Security Techniques for Safeguarding Data Against Evolving Cyber Threats. Available at SSRN 5267951.
- Singh, H. (2025). Key Cloud Security Challenges for Organizations Embracing Digital Transformation Initiatives. Available at SSRN 5267894.
- Sidharth, S. (2024). Enhancing Cloud Security with AI-Based Intrusion Detection Systems.
- Arora, A. (2025). Analyzing Best Practices and Strategies for Encrypting Data at Rest (Stored) and Data in Transit (Transmitted) in Cloud Environments. Available at SSRN 5268190.
- Arora, A. (2025). Comprehensive Cloud Security Strategies for Protecting Sensitive Data in Hybrid Cloud Environments.
- Singh, H. (2025). Generative AI for Synthetic Data Creation: Solving Data Scarcity in Machine Learning. Available at SSRN 5267914.
- Kumar, T. V. (2015). Cloud-Native Model Deployment for Financial Applications.
- Singh, B. (2025). CD Pipelines Using DevSecOps Tools: A Comprehensive Study. (May 23, 2025).
- Sidharth, S. (2024). Strengthening Cloud Security with AI-Based Intrusion Detection Systems.
- Singh, H. (2025). Artificial Intelligence and Robotics Transforming Industries with Intelligent Automation Solutions. Available at SSRN 5267868.
- Singh, B. (2025). Enhancing Oracle Database Security with Transparent Data Encryption (TDE) Solutions. Available at SSRN 5267924.
- Arora, A. (2025). Zero Trust Architecture: Revolutionizing Cybersecurity for Modern Digital Environments. Available at SSRN 5268151.
- Sidharth, S. (2023). The Role of Homomorphic Encryption in Secure Cloud Data Processing.
- Dalal, A. (2025). BRIDGING OPERATIONAL GAPS USING CLOUD COMPUTING TOOLS FOR SEAMLESS TEAM COLLABORATION AND PRODUCTIVITY. Available at SSRN 5268126.
- Singh, H. (2025). Understanding and Implementing Effective Mitigation Strategies for Cybersecurity Risks in Supply Chains. Available at SSRN 5267866.
- Arora, A. (2025). Detecting and Mitigating Advanced Persistent Threats in Cybersecurity Systems.
- Kumar, T. V. (2015). Serverless Frameworks for Scalable Banking App Backends.
- Sidharth, S. (2023). Homomorphic Encryption: Enabling Secure Cloud Data Processing.
- Dalal, A. (2025). Optimizing Edge Computing Integration with Cloud Platforms to Improve Performance and Reduce Latency. Available at SSRN 5268128.
- Arora, A. (2025). Enhancing Customer Experience Across Multiple Business Domains Using Artificial Intelligence. Available at SSRN 5268178.
- Sidharth, S. (2023). AI-driven anomaly detection for advanced threat detection.
- Singh, B. (2025). Challenges and Solutions for Adopting DevSecOps in Large Organizations. Available at SSRN 5267971.
- Kumar, T. V. (2022). AI-Powered Fraud Detection in Real-Time Financial Transactions.
- Sivaprakash, P., Priya, S. S., Maheswari, K., Rubini, B., Karthikeyan, N., & Shuriya, B. (2025). PATENT SEARCH CLASSIFICATION MODEL FOR SERVICE ROBOTS FIELD USING DEEP LEARNING APPROACH. INTERNATIONAL JOURNAL OF ROBOTICS & AUTOMATION, 40(1), 15-22.
- Singh, H. (2025). AI-Powered Chatbots Transforming Customer Support through Personalized and Automated Interactions. Available at SSRN 5267858.
- Arora, A. (2025). Transforming Cybersecurity Threat Detection and Prevention Systems Using Artificial Intelligence. Available at SSRN 5268166.
- Kumar, T. V. (2017). Cross-Platform Mobile Application Architecture for Financial Services.
- Sidharth, S. (2022). The role of Zero Trust Architecture in modern cybersecurity frameworks.
- Shuriya, B., Kumar, S. V., & Bagyalakshmi, K. (2024). Noise-Resilient Homomorphic Encryption: A Framework for Secure Data Processing in Health care Domain. arXiv 2024, arXiv:2412.11474. [CrossRef]
- Singh, B. (2025). Mastering Oracle Database Security: Best Practices for Enterprise Protection. Available at SSRN 5267920.
- Singh, H. (2025). How Generative AI is Revolutionizing Scientific Research by Automating Hypothesis Generation. Available at SSRN 5267912.
- Singh, B. (2025). Integrating Threat Modeling In DevSecOps for Enhanced Application Security. Available at SSRN 5267976.
- Sidharth, S. (2022). Improving generative AI models for secure and private data synthesis.
- Dalal, A. (2025). Revolutionizing Enterprise Data Management Using SAP HANA for Improved Performance and Scalability. Presented May 2025.
- Arora, A. (2025). The Future of Cybersecurity: Trends and Innovations Shaping Tomorrow’s Threat Landscape. Available at SSRN 5268161.
- Kumar, T. V. (2019). Cloud-Based Core Banking Systems Using Microservices Architecture.
- Shuriya, B., Balajishanmugam, V., & Sivaprakash, P. (2025, April). Towards Accurate Diabetes Prediction: A Synergistic Approach Using Adaptive Deep Learning Techniques. In 2025 3rd International Conference on Advancements in Electrical, Electronics, Communication, Computing and Automation (ICAECA) (pp. 1-6). IEEE.
- Dalal, A. (2025). Driving Business Transformation Through Scalable and Secure Cloud Computing Infrastructure Solutions. Aryendra Dalal, Deloitte. Available at SSRN 5268120.
- Arora, A. (2025). Evaluating Ethical Challenges in Generative AI Development and Responsible Usage Guidelines. Available at SSRN 5268196.
- Singh, B. (2025). Practices, and Implementation Strategies. (May 23, 2025).
- Kumar, T. V. (2018). Event-Driven App Design for High-Concurrency Microservices.
- Sidharth, S. (2022). Zero Trust Architecture: A key component of modern cybersecurity frameworks.
- Singh, H. (2025). The Role of Multi-Factor Authentication and Encryption in Securing Data Access of Cloud Resources in a Multitenant Environment. Available at SSRN 5267886.
- Dalal, A. (2025). The Research Journal (TRJ): A Unit of I2OR. Available at SSRN 5268120.
- Umamaheswari, S., Jagannath, V., & Shuriya, B. (2025, April). Integrated Wearable System for Enhanced Soldier Health Monitoring and Battlefield Awareness. In 2025 3rd International Conference on Advancements in Electrical, Electronics, Communication, Computing and Automation (ICAECA) (pp. 1-6). IEEE.
- Sidharth, S. (2022). Enhancing generative AI models for secure and private data synthesis.
- Singh, B. (2025). Oracle Database Vault: Advanced Features for Regulatory Compliance and Control. Available at SSRN 5267938.
- Kumar, T. V. (2019). Blockchain-Integrated Payment Gateways for Secure Digital Banking.
- Singh, H. (2025). Strengthening Endpoint Security to Reduce Attack Vectors in Distributed Work Environments. Available at SSRN 5267844.
- Dalal, A. (2025). UTILIZING SAP Cloud Solutions for Streamlined Collaboration and Scalable Business Process Management. Available at SSRN 5268108.
- Shuriya, B., Umamaheswari, S., Rajendran, A., & Sivaprakash, P. (2023, June). One-Dimensional Dilated Hypothesized Learning Method for Intrusion Detection System Under Constraint Resource Environment. In 2023 2nd International Conference on Advancements in Electrical, Electronics, Communication, Computing and Automation (ICAECA) (pp. 1-6). IEEE.
- Singh, B. (2025). DevSecOps: A Comprehensive Framework for Securing Cloud-Native Applications. Available at SSRN 5267982.
- Kumar, T. V. (2016). Layered App Security Architecture for Protecting Sensitive Data.
- Sidharth, S. (2021). Multi-cloud environments: Reducing security risks in distributed architectures.
- Singh, H. (2025). Meeting Regulatory and Compliance Standards. (May 23, 2025).
- Dalal, A. (2017). Advanced Governance, Risk, and Compliance Strategies for SAP and ERP Systems in the US and Europe: Leveraging Automation and Analytics.
- Arora, A. (2025). THE SIGNIFICANCE AND ROLE OF AI IN IMPROVING CLOUD SECURITY POSTURE FOR MODERN ENTERPRISES. Available at SSRN 5268192.
- Singh, B. (2025). Building Secure Software Faster with DevSecOps Principles, Practices, and Implementation Strategies. (May 23, 2025).
- Shuriya, B., & Thenmozhi, S. (2015). RBAM with Constraint Satisfaction Problem in Role Mining. International Journal of Innovative Research and Development, 4(2).
- Singh, H. (2025). Enhancing Cloud Security Posture with AI-Driven Threat Detection and Response Mechanisms. Available at SSRN 5267878.
- Dalal, A. (2023). Data Management Using Cloud Computing. Available at SSRN 5198760.
- Sidharth, S. (2020). The growing threat of deepfakes: Implications for security and privacy.
- Singh, B. (2025). Shifting Security Left: Integrating DevSecOps into Agile Software Development Lifecycles. Available at SSRN 5267963.
- Kumar, T. V. (2020). Generative AI Applications in Customizing User Experiences in Banking Apps.
- Singh, H. (2025). Cybersecurity for Smart Cities: Protecting Infrastructure in the Era of Digitalization. Available at SSRN 5267856.
- Sidharth, S. (2020). The rising threat of deepfakes: Security and privacy implications.
- Arora, A. (2025). Developing Generative AI Models That Comply with Privacy Regulations and Ethical Principles. Available at SSRN 5268204.
- Shuriya, B., Prakash, P., & Kiruthikka, D. C. (2022, March). Qos Based Aes Cryptography Network Model. In Proceedings of the International Conference on Innovative Computing & Communication (ICICC).
- Dalal, A., et al. (2025, February). Developing a Blockchain-Based AI-IoT Platform for Industrial Automation and Control Systems. In IEEE CE2CT (pp. 744–749).
- Singh, H. (2025). Securing High-Stakes Digital Transactions: A Comprehensive Study on Cybersecurity and Data Privacy in Financial Institutions. Available at SSRN 5267850.
- Kumar, T. V. (2019). Personal Finance Management Solutions with AI-Enabled Insights.
- Sidharth, S. (2019). Securing cloud-native microservices with service mesh technologies.
- Shuriya, B., & Rajendran, A. (2017). Tranquilize Role Mining using HR (Heuristic Random) Approach. Asian Journal of Research in Social Sciences and Humanities, 7(1), 744-753.
- Arora, A. (2025). Securing Multi-Cloud Architectures Using Advanced Cloud Security Management Tools. Available at SSRN 5268184.
- Singh, H. (2025). The Importance of Cybersecurity Frameworks and Constant Audits for Identifying Gaps, Meeting Regulatory and Compliance Standards. Presented in May 2025.
- Dalal, A. (2025). DEVELOPING SCALABLE APPLICATIONS THROUGH ADVANCED SERVERLESS ARCHITECTURES IN CLOUD ECOSYSTEMS. Available at SSRN 5268116.
- Arora, A. (2025). Integrating DevSecOps Practices to Strengthen Cloud Security in Agile Development Environments. Available at SSRN 5268194.
- Singh, B. (2025). Integrating Security Seamlessly into DevOps Development Pipelines Through DevSecOps: A Holistic Approach to Secure Software Delivery. Available at SSRN 5267955.
- Sidharth, S. (2019). Quantum-enhanced encryption techniques for cloud data protection.
- Kumar, T. V. (2021). Natural Language Understanding Models for Personalized Financial Services.
- Singh, H. (2025). The Future of Generative AI: Opportunities, Challenges, and Industry Disruption Potential. (May 23, 2025).
- Arora, A. (2025). The Future of Generative AI and Its Role in Shaping Secure and Ethical AI Systems.
- Singh, B. (2025). Enhancing Real-Time Database Security Monitoring Capabilities Using Artificial Intelligence. Available at SSRN 5267988.
- Kumar, T. V. (2015). Analysis of SQL and NoSQL Database Management Systems Intended for Unstructured Data.
- Jha, K., Dhakad, D., & Singh, B. (2020). Critical Review on Corrosive Properties of Metals and Polymers in Oil and Gas Pipelines. In Advances in Materials Science and Engineering: Select Proceedings of ICFMMP 2019 (pp. 99–113).
- Dalal, A. (2025). THE RESEARCH JOURNAL (TRJ): A UNIT OF I2OR. SSRN. https://ssrn.com/abstract=5268120. [CrossRef]
- Sidharth, S. (2019). Data loss prevention (DLP) strategies in cloud-hosted applications.
- Singh, B. (2025). Practices, and Implementation Strategies. Presented May 23, 2025.
- Singh, B. (2025). CD Pipelines Using DevSecOps Tools: A Comprehensive Study. Presented May 23, 2025.
- Singh, H. (2025). Meeting Regulatory and Compliance Standards. Presented May 23, 2025.
- Dalal, A. (2025). Driving Business Transformation Through Scalable and Secure Cloud Computing Infrastructure Solutions. Aryendra Dalal, Manager, Systems Administration, Deloitte Services LP. SSRN. https://ssrn.com/abstract=5268120. [CrossRef]
- Dalal, A. (2025). Revolutionizing Enterprise Data Management Using SAP HANA for Improved Performance and Scalability. Aryendra Dalal, Manager, Systems Administration, Deloitte Services LP. Presented May 23, 2025.
- Singh, H. (2025). Strengthening Endpoint Security to Reduce Attack Vectors in Distributed Work Environments. SSRN. https://ssrn.com/abstract=5267844. [CrossRef]
- Singh, H. (2025). Advanced Cybersecurity Techniques for Safeguarding Critical Infrastructure Against Modern Threats. SSRN. https://ssrn.com/abstract=5267496. [CrossRef]
- Sidharth, S. (2019). Enhancing security of cloud-native microservices with service mesh technologies.
- Kumar, T. V. (2015). Serverless Frameworks for Scalable Banking App Backends.
- Kumar, T. V. (2019). Personal Finance Management Solutions with AI-Enabled Insights.
- Dalal, A. (2025). THE RESEARCH JOURNAL (TRJ): A UNIT OF I2OR. SSRN. https://ssrn.com/abstract=5268120. [CrossRef]
- Sidharth, S. (2019). Quantum-enhanced encryption methods for securing cloud data.
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).