Submitted:
05 January 2025
Posted:
06 January 2025
You are already at the latest version
Abstract
This paper addresses the rise of cyberattacks that pose significant threats to computer and network systems, including data breaches, malware, and unauthorized access, which are becoming increasingly prevalent (Aslan et al., 2023). It explores how security measures in cloud computing protect sensitive data and ensure operational integrity as more organizations adopt cloud environments. The paper examines advanced cloud security technologies concerning their mechanisms, components, and role in addressing modern cybersecurity challenges. Key elements such as data encryption, network security, and auditing are discussed regarding their role in safeguarding sensitive information within cloud environments. Essential processes such as identifying, protecting, detecting, responding, and recovering are considered in developing a comprehensive cybersecurity framework for cloud systems. Besides that, the paper also evaluates examples of advanced cloud security measures, such as encryption technologies, and discusses their benefits, including multi-layered defence, scalability, and cost efficiency. The presented limitations, which involve compliance challenges, multi-tenancy risks, and reduced direct control are critically assessed. Furthermore, the paper discusses future directions in cloud security, including edge-cloud computing and hybrid cloud solutions. Finally, it proposes advanced countermeasures, such as intelligent deception technologies using honeytokens and honeynets to dynamically mitigate evolving threats. This study emphasizes the importance of adaptive and proactive strategies for cloud environment security as well as provides valuable insights relevant to both academic research and practical implementation.
Keywords:
1. Background
Introduction to Cloud Computing Security
The Importance of Cloud Security
Challenges in Cloud Computing Security
2. Discussion on How Security-Related Technology Works
a) Component
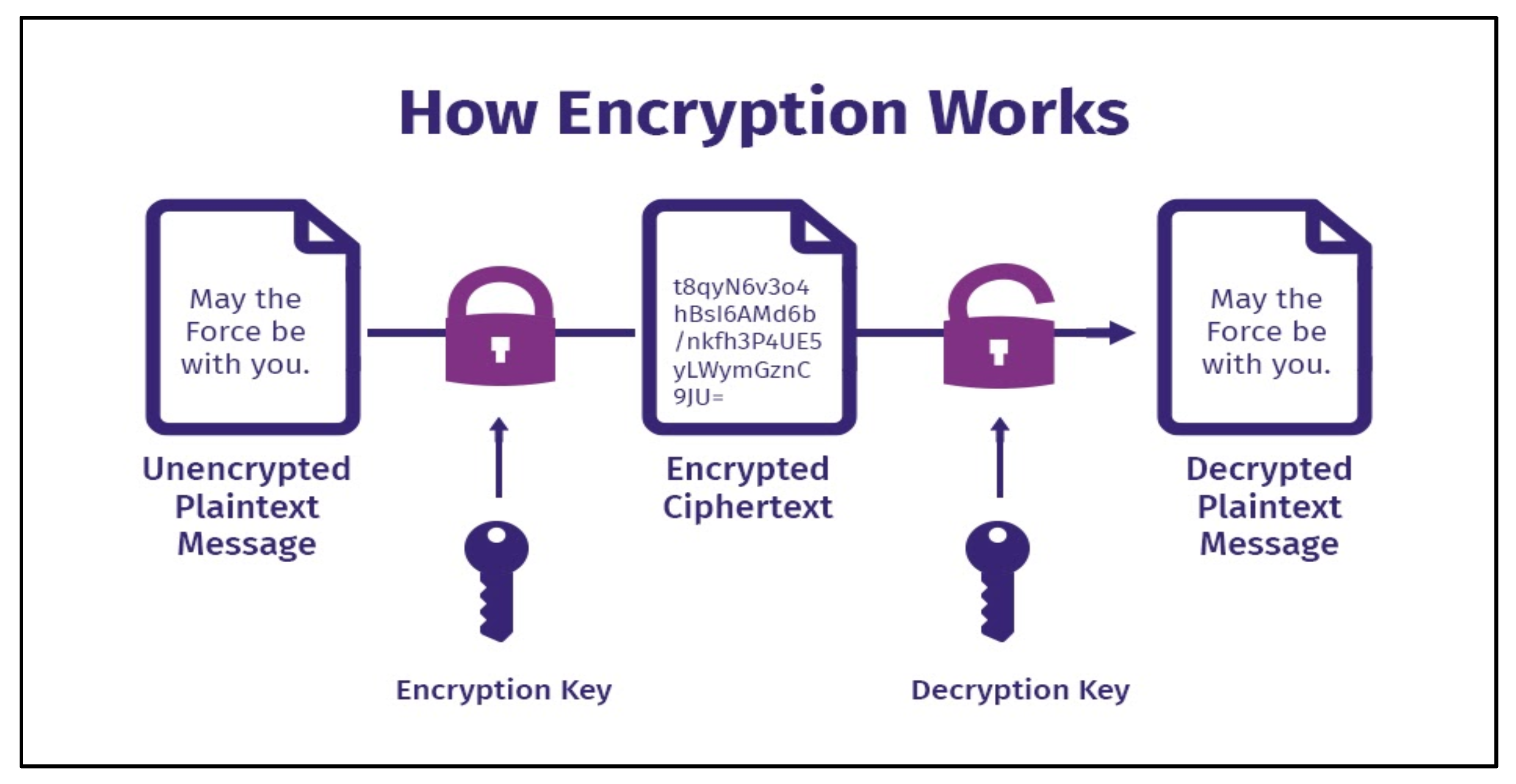
i. Data Encryption
- Encryption at Rest: This implies that data is stored encrypted when not in use. Cloud providers use strong encryption standards like AES-256 to restrict unauthorized access to data.
- Encryption in Transit: Information moving between the customer's device and the cloud-including from one cloud to another is encrypted using Transport Layer Security, and Secure Sockets Layer.
- Encryption in Use: In an emerging area like this, data is made incomprehensible when it is in use. For example, Homomorphic encryption enables computations on plain text data while it is still encrypted.
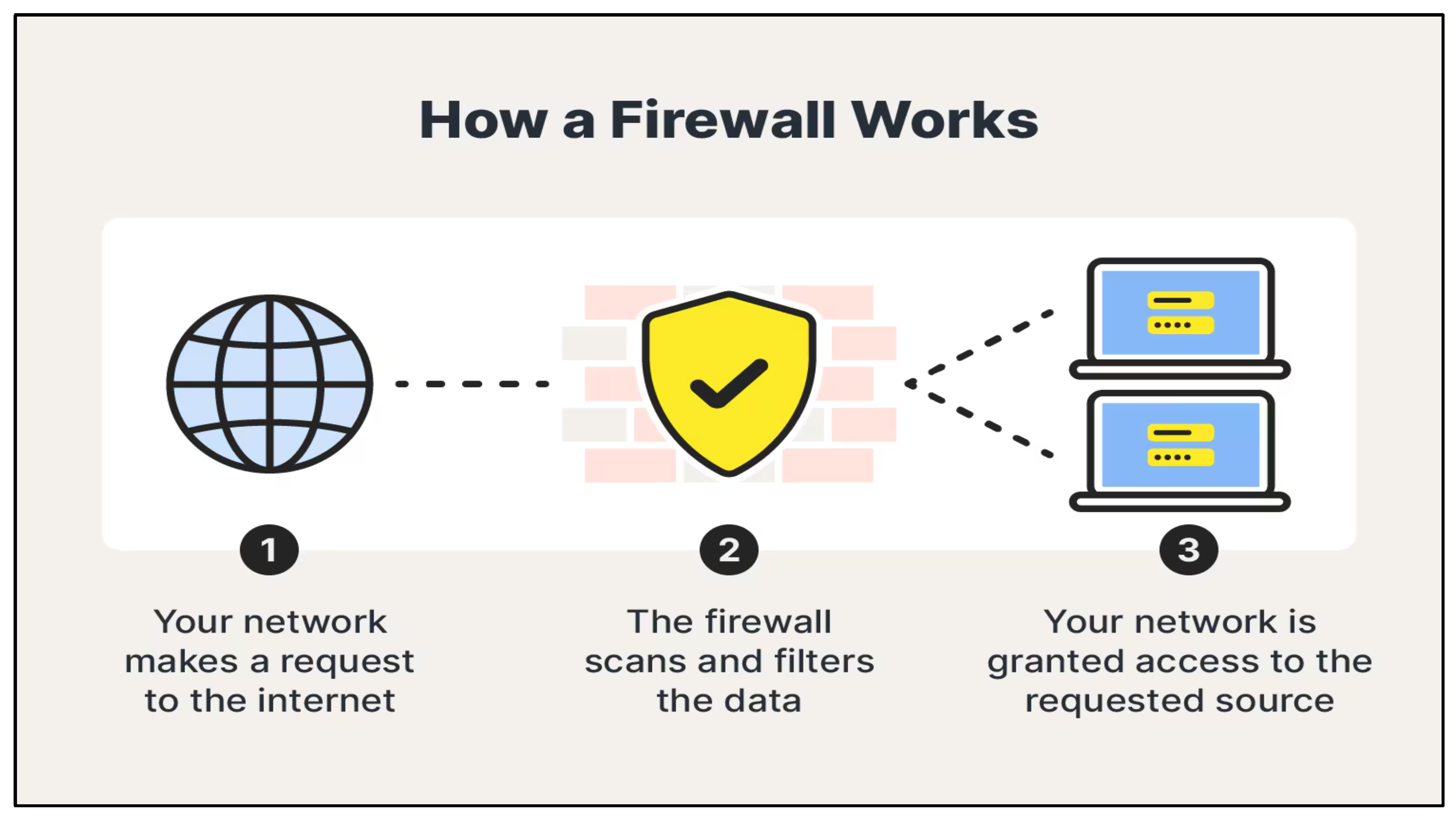
ii. Network Security
- Network-based Firewalls: Secure the perimeters of a cloud network by managing the flow of traffic based on certain IP addresses, ports or protocols. They apply the policies uniformly across the virtual private clouds (VPCs) and subnetworks. (Reddy, 2023)
- Web Application Firewalls (WAF): These firewalls are aimed at preventing attacks on web applications, which are the most common forms like SQL Injection and Distributed Denial of Service (DDoS) attacks by thorough checking of the HTTP requests.
- The way cloud firewalls work is by setting up security groups or by setting up network access control lists (ACLs). These include rules which state what traffic is permitted and what traffic is denied.
- Intrusion Detection/Prevention Systems (IDS/IPS): This is frequently done in combination with firewalls as a mechanism to inform and help the administrators of the network of the threat in real-time and even block any traffic that appears to be malicious traffic.
iii. Auditing
- Data Integrity and Compliance: Auditing acts to ensure that data is preserved without modifications and assists organizations in meeting laws such as GDPR and HIPAA. (Shanshan et al., 2023; Seng et al., 2024).
- Event Logging: Important activities such as data entry and retrieval, modification of settings, and user logins are documented in order to leave a clear trace of the activities performed.
- Authentication: It ensures the verification of a user in order to assert who he/she claims to be. In Cloud environments, this generally includes Passwords, Multi-factor authentication MFA, Biometric Verification (thumb impressions, facial recognition) and SSO - Single Sign-On. (Shanshan et al., 2023; Mbah, 2022)
- Authorization: This is what the user can do once they are authenticated. In most scenarios, this is done through roles and permissions. A good example is when admins have full permissions, whereas normal users will have very limited permissions.
- Role-Based Access Control (RBAC): A very applicable feature today; it is a system where permissions are granted through roles, not to the individual users themselves. This will help in managing a great number of user accesses efficiently.
b) Process
v. Identify
vi. Protect
vii. Detect
viii. Response
ix. Recover
c) Threats
x. Data Encryption Technologies
3. Discussion on the Impact
i. Benefits
a) Multi-Layered Defence
b) Scalability
c) Cost Saving
ii. Limitations
a) Limited Direct Control
b) Compliance and Regulatory Challenges
c) Multi-Tenancy Risk
iii. Future Potentials
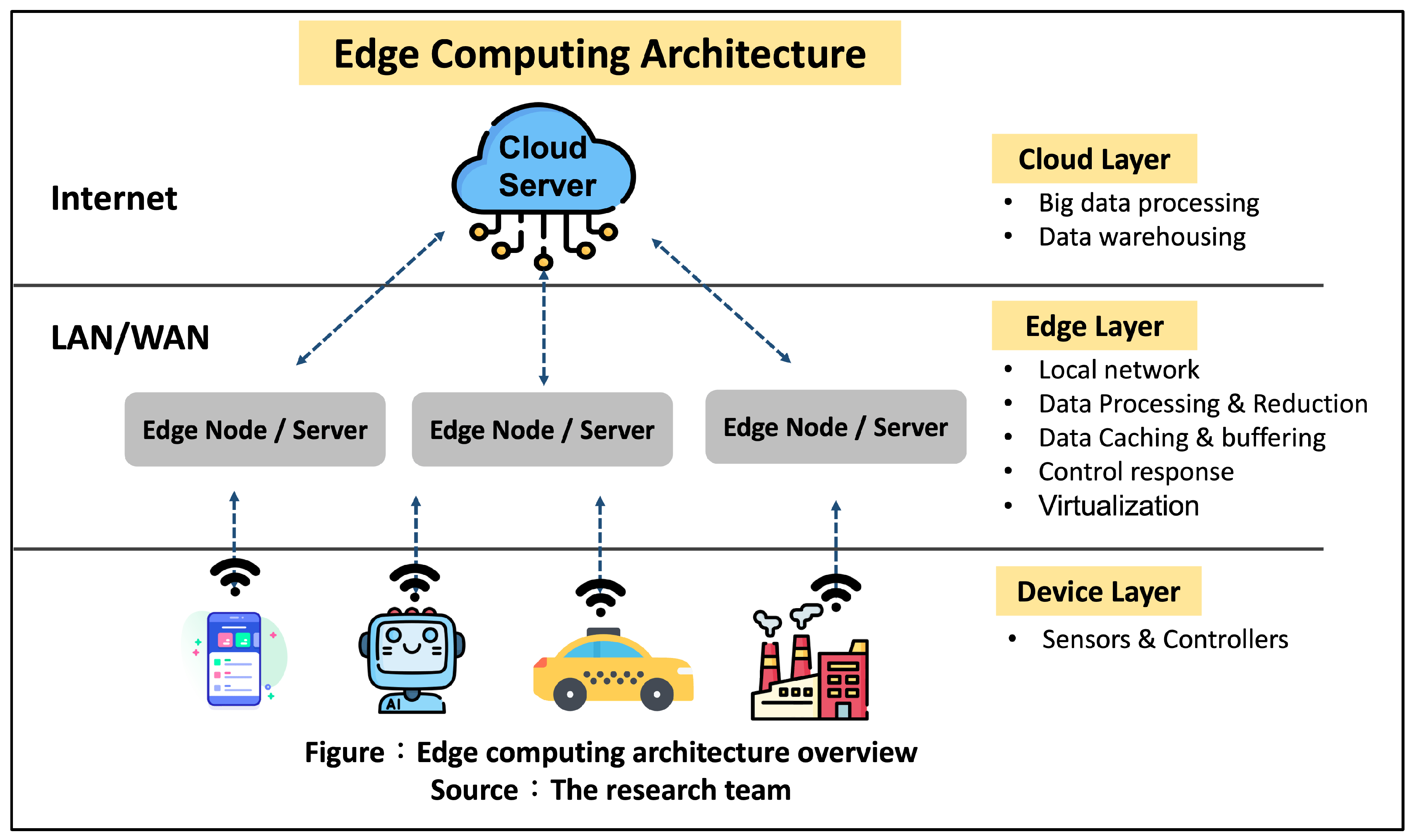
a. Edge-Cloud Computing
b. Localized Security Control
c. AI-Driven Threat Detection at the Edge
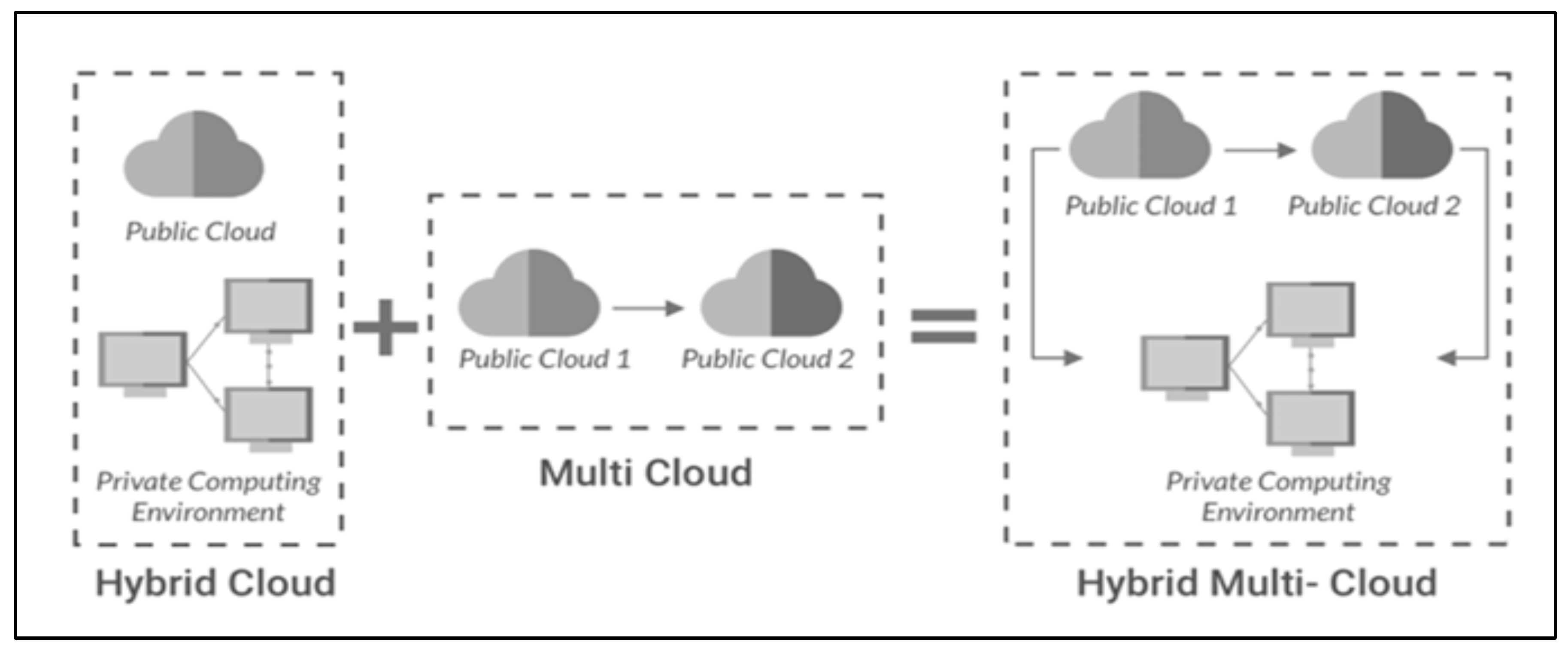
d. Hybrid and Multi-Cloud Solutions
iv. Resilience Through Hybrid and Multi-Cloud Strategies
v. Zero-Trust Security for Hybrid Multi-Cloud Environments
4. Discussion on Security Countermeasures
i. Security Countermeasures
a. Intrusion Detection System
b. Digital Signature and Message Digest
c. Comprehensive Security Measures
- Identity and Access Management (IAM): IAM serves as a core defence mechanism by controlling who accesses what resources. It employs strong authentication and authorization processes to verify users. Advanced authentication standards like OpenID Connect, Security Assertion Markup Language (SAML), and OAuth facilitate Multi-Factor Authentication (MFA), enhancing security. (Salama , S. et al. 2023)
- Network Security Measures: Measures such as Distributed Denial of Service (DDoS) protection, firewalls and Virtual Private Networks secure data communication. Firewalls control traffic based on security rules that are predefined, while VPNs encrypt data during transmission, mitigating interception risks. DDoS protection filters malicious traffic, ensuring availability during large-scale attacks. (Ometov, A. et al. 2022)
- Web Application Security: Web applications, central to most cloud environments, require rigorous countermeasures to address vulnerabilities. Security measures include digital signatures and XML encryption to ensure their integrity.
- Data Storage Security: Data backups and disaster recovery plans safeguard the integrity and availability of data during system failures or cyberattacks. These strategies involve data replication, geo-redundancy, and redundant storage systems, ensuring data restoration with minimal downtime and losses. (Salama , S. et al. 2023)
ii. Proposed Countermeasures (Defense Solutions)
a. Intelligent Deception Technologies (Honeytokens and Honeynets)
- Honeytokens: Fake data like fabricated database records, credentials, or document files, scattered throughout the cloud environment. A honeytoken could be a false set of keys embedded in a database. When attackers attempt to use or access these keys an alert is triggered, identifying and flagging suspicious activity early.
- Honeynets: Honeynets are networks of virtualized systems designed to simulate a real IT environment but hold no genuine data. When attackers infiltrate these decoys, they encounter a fully functional but isolated network that mimics legitimate cloud resources, capturing information on their methods without compromising real assets.
b. Innovation and Unique Features
- Machine Learning-Driven Deception: ML algorithms analyze previous attack behaviours and intelligently place honeytokens or honeynets based on high-risk zones, such as user access points or areas with frequent external connections. Over time, the system learns to optimize token placement, adjust to emerging threats, and better adapt to specific cloud environments.
- Real-Time Threat Intelligence Collection: When attackers interact with the decoys, the system logs their behaviours in detail, offering valuable data that can enhance threat intelligence. This insight helps organizations refine their security posture by understanding TTPs that attackers use to target cloud systems.
- Minimal Impact on System Performance: Since honeytokens and honeynets do not hold real data, there’s minimal risk to production systems, allowing organizations to adopt a more aggressive detection strategy without affecting legitimate workflows.
c. Technologies Used
- Machine Learning and AI: ML algorithms are central to optimising honeytoken and honeynet deployment by analysing patterns of suspicious activity and identifying high-risk zones. AI-driven behavioural analytics can adapt the placement and characteristics of deception assets, making them harder for attackers to distinguish from real resources.
- b. Data Masking and Tokenization: To make honeytokens more realistic, data masking and tokenization techniques can blur the actual data while creating convincing decoy records. This ensures that honeytokens mimic genuine data points.
- c. Sandboxing and Virtualization: Honeynets utilize virtualization and sandboxing to safely isolate decoy environments. This creates a controlled environment where attackers can be monitored and studied without risking actual production systems. These technologies enable honeynets to simulate various IT assets, including user endpoints, databases, and network nodes.
- d. Threat Intelligence Integration: Integration with threat intelligence feeds and databases help update honeytokens and honeynets with the latest TTPs observed in real-world attacks. This allows the deception system to remain relevant and convincing as attackers’ methods evolve.
d. How It’s Innovative
- Active Attacker Engagement: Unlike traditional defences, which are primarily passive, intelligent deception engages and diverts attackers from real assets, extending the defensive perimeter.
- Adaptation to Cloud Dynamics: Deception technologies leverage ML to adapt dynamically within scalable cloud environments, keeping up with evolving configurations, user patterns, and emerging attack vectors.
- Self-Learning and Optimization: Machine learning allows these systems to improve continuously by learning from prior attack attempts, making decoys more realistic and placement more precise over time. (Javadpour, A. et al. 2024)
d. Evolution of Honeypot Technologies
- Traditional Honeypots: Typically static and require manual setup and tuning. They often remain in fixed locations within a network, making them easier for experienced attackers to detect and bypass over time.
- Intelligent Deception: Uses machine learning (ML) to dynamically place honeytokens and honeynets based on risk analysis. ML-driven insights allow these decoys to adapt by relocating or changing in response to evolving threats, increasing resilience against attacker evasion tactics. (Javadpour, A. et al. 2024)
e. Contextual Realism with Behavioral Analysis
- Traditional Honeypots: Often operate as isolated systems that may lack contextual relevance to the actual production environment, limiting their ability to blend in convincingly.
- Intelligent Deception: Leverages behavioural analysis to tailor honeytokens and honeynets to match typical user behaviours and legitimate data patterns, making decoys highly realistic and difficult to distinguish from real assets. This contextual accuracy makes these decoys more effective in luring attackers. (SentinelOne, 2024)
f. AI-Driven Threat Prediction and Self-Learning
- Traditional Honeypots: Mostly reactive, capturing attacker activity after the attacker has entered the honeypot. They do not adapt based on attack patterns or improve their ability to attract attackers.
- Intelligent Deception: Incorporates AI-driven predictive analytics that can anticipate potential threats and adjust decoy placement to target high-risk areas. Self-learning capabilities mean these systems evolve continuously, optimizing their defences and maintaining relevance even as attacker methods change. (SentinelOne, 2024)
g. Integration with Threat Intelligence and Incident Response
- Traditional Honeypots: Typically lack integration with broader security frameworks, limiting their value to isolated threat detection.
- Intelligent Deception: Can integrate with threat intelligence feeds to reflect the latest TTPs (tactics, techniques, and procedures) used by attackers. Additionally, these systems often feed directly into incident response workflows, enabling automated responses like isolating affected areas, logging detailed activity, or deploying additional defences based on detected threats.(Javadpour, A. et al. 2024)
h. Reduced False Positives and Higher Alert Accuracy
- Traditional Honeypots: Might generate alerts whenever any interaction occurs, sometimes producing false positives that security teams must spend resources investigating.
- Intelligent Deception: Only triggers alerts upon genuine, malicious interactions with honeytokens or honeynets, reducing false positives and enhancing alert accuracy. This targeted approach enables security teams to focus on verified threats rather than dealing with benign or irrelevant alerts. (Javadpour, A. et al. 2024)
5. Conclusions
References
- aditya191251015002, *!!! REPLACE !!!*; et al. (2024) Architecture of Identity Access Management in cloud computing, GeeksforGeeks. Available at: https://www.geeksforgeeks.org/architecture-of-identity-access-management-in-cloud-computing/.
- Alex, S. A. , Jhanjhi, N., Humayun, M., Ibrahim, A. O., & Abulfaraj, A. W. (2022). Deep LSTM Model for Diabetes Prediction with Class Balancing by SMOTE. W. ( 11(17), 2737. [CrossRef]
- Alferidah, D. K. , & Jhanjhi, N. (2020). Cybersecurity Impact over Bigdata and IoT Growth. 2020 International Conference on Computational Intelligence (ICCI). [CrossRef]
- Alkinani, M. H. , Almazroi, A. A., Jhanjhi, N., & Khan, N. A. (2021). 5G and IoT Based Reporting and Accident Detection (RAD) System to Deliver First Aid Box Using Unmanned Aerial Vehicle. A. ( 21(20), 6905. [CrossRef]
- Alouffi, B. , Hasnain, M., Alharbi, A., Alosaimi, W., Alyami, H., and Ayaz, M. (2021). A systematic literature review on cloud computing security: threats and mitigation strategies. *IEEE Access*, 9, pp.57792-57807. [CrossRef]
- AlTwaijiry, A. (2021). Cloud Computing Present Limitations and Future Trends. *ScienceOpen Preprints*. [CrossRef]
- Amos, K. , Esquivel, R. and Esquivel, J.A. (2022). RANSOMWARE: RANSOMWARE AS A SERVICE (RaaS), METHODS TO DETECT, PREVENT, MITIGATE AND FUTURE DIRECTION. Available at: https://www.researchgate.net/publication/365349176_RANSOMWARE_RANSOMWARE_AS_A_SERVICE_RaaS_METHODS_TO_DETECTS_PREVENT_MITIGATE_AND_FUTURE_DIRECTION [Accessed 1 Nov. 2023].
- Ananna, F. F. , Nowreen, R., Jahwari, S. S. R. A., Costa, E. A., Angeline, L., & Sindiramutty, S. R. (2023). Analysing Influential factors in student academic achievement: Prediction modelling and insight. International Journal of Emerging Multidisciplinaries Computer Science & Artificial Intelligence. [CrossRef]
- Arjun, R.K. (2023). Security Concerns and Solutions for Enterprise Cloud Computing Applications. *Asian Journal of Research in Computer Science*, 15(4), pp.24–33. [CrossRef]
- Augmented, AI. (2023, March). Will edge computing replace cloud computing? A comprehensive analysis.
- Azam, H. , Dulloo, M. I., Majeed, M. H., Wan, J. P. H., Xin, L. T., & Sindiramutty, S. R. (2023). Cybercrime Unmasked: Investigating cases and digital evidence. International Journal of Emerging Multidisciplinaries Computer Science & Artificial Intelligence. [CrossRef]
- Azam, H. , Dulloo, M. I., Majeed, M. H., Wan, J. P. H., Xin, L. T., Tajwar, M. A., & Sindiramutty, S. R. (2023). Defending the digital Frontier: IDPS and the battle against Cyber threat. International Journal of Emerging Multidisciplinaries Computer Science & Artificial Intelligence. [CrossRef]
- Azam, H. , Tajwar, M. A., Mayhialagan, S., Davis, A. J., Yik, C. J., Ali, D., & Sindiramutty, S. R. (2023). Innovations in Security: A study of cloud Computing and IoT. International Journal of Emerging Multidisciplinaries Computer Science & Artificial Intelligence. [CrossRef]
- Azam, H. , Tan, M., Pin, L. T., Syahmi, M. A., Qian, A. L. W., Jingyan, H., Uddin, M. F., & Sindiramutty, S. R. (2023). Wireless Technology Security and Privacy: A Comprehensive Study. Preprints.org. [CrossRef]
- Babbar, H. , Rani, S., Masud, M., Verma, S., Anand, D., & Jhanjhi, N. (2021). Load balancing algorithm for migrating switches in software-defined vehicular networks. Computers, Materials & Continua/Computers, Materials & Continua (Print). [CrossRef]
- Beerman, J. , Berent, D., Falter, Z., and Bhunia, S. (2023). A Review of Colonial Pipeline Ransomware Attack. Available at: https://sbhunia.me/publications/manuscripts/ccgrid23.pdf [Accessed 1 Nov. 2024].
- Blessing, M. (2024). Cloud Encryption Strategies and Key Management. [pdf] p.10. Available at: https://www.researchgate.net/profile/Moses-Blessing/publication/383660212_Cloud_Encryption_Strategies_and_Key_Management/links/66d5b688fa5e11512c47d0eb/Cloud-Encryption-Strategies-and-Key-Management.pdf [Accessed 10 Nov. 2024].
- Brohi, S. N. , Jhanjhi, N., Brohi, N. N., & Brohi, M. N. (2020). Key Applications of State-of-the-Art Technologies to Mitigate and Eliminate COVID-19.pdf. TECHRxiv. [CrossRef]
- Brown, E. (2024). Advanced Techniques for Data Loss Prevention and Access Control in Big Data Cloud Infrastructures. Advances in Computer Sciences, /: 7(1). Available at: https, 2024. [Google Scholar]
- Butt, U.A. , Mehmood, M., Shah, S.B.H., Amin, R., Shaukat, M.W., Raza, S.M., Suh, D.Y., and Piran, M.J. (2020). A review of machine learning algorithms for cloud computing security. *Electronics*, 9(9), p.1379. [CrossRef]
- Chauhan, M. and Shiaeles, S. (2023). An Analysis of Cloud Security Frameworks, Problems and Proposed Solutions. Network, [online] 3(3), pp.422–450. [CrossRef]
- Chebitko, R. (2024, February 13). What is a firewall and why is it used, /: https, 13 February.
- Cherney, M.A. (2024). Microsoft launches two data center infrastructure chips to speed up AI applications. Reuters.19 Nov. Available at: https://www.reuters.com/technology/artificial-intelligence/microsoft-launches-two-data-center-infrastructure-chips-speed-ai-applications-2024-11-19/.
- Chesti, I. A. , Humayun, M., Sama, N. U., & Jhanjhi, N. (2020). Evolution, Mitigation, and Prevention of Ransomware. 2020 2nd International Conference on Computer and Information Sciences (ICCIS). [CrossRef]
- Cloud IDS overview | Google Cloud (2024) Google. Available at: https://cloud.google.
- Cloud-based digital signatures (2023) Adobe Help Center. Available at: https://helpx.adobe.com/sign/config/send-settings/auth-methods/cloud-signature.html (Accessed: ). 1 November.
- Dawood, M. , Tu, S., Xiao, C., Alasmary, H., Waqas, M. and Rehman, S.U. (2023). Cyberattacks and Security of Cloud Computing: A Complete Guideline. Symmetry. [CrossRef]
- Digital signatures | cloud KMS documentation | google cloud (2024) Google. Available at: https://cloud.google.com/kms/docs/digital-signatures#:~:text=Digital%20signatures%20rely%20on%20asymmetric,used%20to%20verify%20the%20signature (Accessed: ). 1 November.
- Dogra, V. , Singh, A., Verma, S., Kavita, N., Jhanjhi, N. Z., & Talib, M. N. (2021). Analyzing DistilBERT for Sentiment Classification of Banking Financial News. In Lecture notes in networks and systems (pp. 501–510). [CrossRef]
- Dutta, S. (2024, March). What are The Implications of Data Encryption for MIS?
- EDPB (2023). 1.2 billion euro fine for Facebook as a result of EDPB binding decision. Available at: https://www.edpb.europa.eu/news/news/2023/12-billion-euro-fine-facebook-result-edpb-binding-decision_en [Accessed 1 Nov. 2024].
- El Kafhali, S. , El Mir, I., and Hanini, M. (2021). Security Threats, Defense Mechanisms, Challenges, and Future Directions in Cloud Computing. *Archives of Computational Methods in Engineering*, 29(1). [CrossRef]
- Fatima-Tuz-Zahra, N. , Jhanjhi, N., Brohi, S. N., Malik, N. A., & Humayun, M. (2020). Proposing a Hybrid RPL Protocol for Rank and Wormhole Attack Mitigation using Machine Learning. 2020 2nd International Conference on Computer and Information Sciences (ICCIS). [CrossRef]
- Garg, T. , Saini, N., Singh, M., and Singh, S. (2024). Comparative Study of Security Threats in Cloud Computing. Available at: https://www.researchgate.net/publication/381193283_Comparative_Study_of_Security_Threats_in_Cloud_Computing [Accessed 1 Nov. 2024].
- geeksforgeeks (2021). Security Issues in Cloud Computing. *GeeksforGeeks*. Available at: https://www.geeksforgeeks.org/security-issues-in-cloud-computing/.
- Google Cloud, n.d. What is cloud security?. Available at: https://cloud.google.
- Google Cloud. (2024). Cloud IDS overview. Available at: https://cloud.google.com/intrusion-detection-system/docs/overview?
- Gopi, R. , Sathiyamoorthi, V., Selvakumar, S., Manikandan, R., Chatterjee, P., Jhanjhi, N. Z., & Luhach, A. K. (2021). Enhanced method of ANN based model for detection of DDoS attacks on multimedia internet of things. Multimedia Tools and Applications, 6739. [Google Scholar] [CrossRef]
- Gouda, W. , Almurafeh, M., Humayun, M., & Jhanjhi, N. Z. (2022). Detection of COVID-19 based on chest x-rays using deep learning. Healthcare. [CrossRef]
- Gurulcu (2023). Famous Insider Threat Cases. Available at: https://gurucul.com/blog/famous-insider-threat-cases [Accessed 1 Nov. 2024].
- Hashim, W. and Noor (2024). Securing Cloud Computing Environments: An Analysis of Multi-Tenancy Vulnerabilities and Countermeasures. [online] 2024, pp.9–17. [CrossRef]
- Honey tokens: What are they and how are they used? Fortinet. Available at: https://www.fortinet.
- Huč, A. , Šalej, J., and Trebar, M. (2021). Analysis of Machine Learning Algorithms for Anomaly Detection on Edge Devices. *Sensors*, 21(14), p.4946. [CrossRef]
- Humayun, M. , Sujatha, R., Almuayqil, S. N., & Jhanjhi, N. Z. (2022). A Transfer Learning Approach with a Convolutional Neural Network for the Classification of Lung Carcinoma. Z. ( 10(6), 1058. [CrossRef]
- Hussain, K. , Rahmatyar, A. R., Riskhan, B., Sheikh, M. a. U., & Sindiramutty, S. R. (2024). Threats and Vulnerabilities of Wireless Networks in the Internet of Things (IoT). 2024 IEEE 1st Karachi Section Humanitarian Technology Conference (KHI-HTC). [CrossRef]
- IAIC (2020). *IAIC Transactions on Sustainable Digital Innovation (ITSDI) The 2nd Edition Vol. 1 No. *. Available at: https://books.google.com.my/books?id=VccwEAAAQBAJ. 2 April.
- IBM, 2024. Cloud security, /: at: https.
- IBM, 2024. Cost of a data breach 2024, /: at: https.
- Jack, B. , David, B., Zach, F., and Bhunia, S. (2023). A Review of Colonial Pipeline Ransomware Attack. Available at: https://sbhunia.me/publications/manuscripts/ccgrid23.pdf [Accessed 1 Nov. 2024].
- Javadpour, A.; et al. (2024) A comprehensive survey on cyber deception techniques to improve honeypot performance, Computers & Security. Available at: https://www.sciencedirect.com/science/article/pii/S0167404824000932(Accessed: ). 13 November.
- Jhanjhi, N. , Humayun, M., & Almuayqil, S. N. (2021). Cyber security and privacy issues in industrial internet of things. N. ( 37(3), 361–380. [CrossRef]
- Jun, A. Y. M. , Jinu, B. A., Seng, L. K., Maharaiq, M. H. F. B. Z., Khongsuwan, W., Junn, B. T. K., Hao, A. a. W., & Sindiramutty, S. R. (2024). Exploring the Impact of Crypto-Ransomware on Critical Industries: Case Studies and Solutions. Preprints.org. [CrossRef]
- Kaspersky, 2020. What is cloud security? /: at: https.
- Krebs, B. (2023). New T-Mobile Breach Affects 37 Million Accounts. Available at: https://krebsonsecurity. 2023. [Google Scholar]
- Kumar, M. S. , Vimal, S., Jhanjhi, N., Dhanabalan, S. S., & Alhumyani, H. A. (2021). Blockchain based peer to peer communication in autonomous drone operation. Energy Reports. [CrossRef]
- Kumar, S. , Rajlingam, A., Gokila, B., and Arunkumar, J. (2023). Study Analysis of Cloud Security Challenges and Issues in Cloud Computing Technologies. *Journal of Science, Computing and Engineering Research*, 6(6), pp.6–10. [CrossRef]
- Kunduru, A.R. (2023). THE PERILS AND DEFENSES OF ENTERPRISE CLOUD COMPUTING: A COMPREHENSIVE REVIEW. CENTRAL ASIAN JOURNAL OF MATHEMATICAL THEORY AND COMPUTER SCIENCES, /: 4(9), pp.29–41. Available at: https.
- Lata, S. and Singh, D. (2022). Intrusion detection system in cloud environment: Literature survey & future research directions. International Journal of Information Management Data Insights, 1001. [Google Scholar] [CrossRef]
- Lim, M. , Abdullah, A., Jhanjhi, N., Khan, M. K., & Supramaniam, M. (2019). Link Prediction in Time-Evolving Criminal Network with deep Reinforcement learning technique. IEEE Access, 1848. [Google Scholar] [CrossRef]
- Manchuri, A. , Kakera, A., Saleh, A., & Raja, S. (2024). pplication of Supervised Machine Learning Models in Biodiesel Production Research - A Short Review. Borneo Journal of Sciences and Technology. [CrossRef]
- McAuley, D. (2023). Hybrid and Multi-Cloud Strategies: Balancing Flexibility and Complexity. *MZ Computing Journal*, 4(2). Available at: https://mzjournal.com/index.
- Nayyar, A. , Gadhavi, L., & Zaman, N. (2021). Machine learning in healthcare: review, opportunities and challenges. In Elsevier eBooks (pp. 23–45). [CrossRef]
- Ometov, A.; et al. (2022) A Survey of Security in Cloud, Edge, and Fog Computing, https://www.mdpi.com/journal/sensors. Available at: chrome-extension://gphandlahdpffmccakmbngmbjnjiiahp/https://mdpi-res.com/d_attachment/sensors/sensors-22-00927/article_deploy/sensors-22-00927.pdf?version=1643114960(Accessed: ). 01 November.
- Papakonstantinou, N. , Van Bossuyt, D.L., Linnosmaa, J., Hale, B. and O’Halloran, B. (2021). A Zero Trust Hybrid Security and Safety Risk Analysis Method. Journal of Computing and Information Science in Engineering. [CrossRef]
- PECB (2023). Cloud Computing Security: Top Challenges and How to Mitigate Them. Available at: https://pecb.com/article/cloud-computing-security-top-challenges-and-how-to-mitigate-them.
- Practical Cloud Security A Guide for Secure Design and Deployment. (n.d.). Available at: https://orca.security/wp-content/uploads/2021/12/pracCloudSecurity.pdf.
- Rashid, A. and Chaturvedi, A. (2019). Cloud computing characteristics and services: a brief review. *International Journal of Computer Sciences and Engineering*, 7(2), pp.421-426. Available at: https://www.researchgate.net/publication/331731714_Cloud_Computing_Characteristics_and_Services_A_Brief_Review.
- Ravichandran, N. , Tewaraja, T., Rajasegaran, V., Kumar, S. S., Gunasekar, S. K. L., & Sindiramutty, S. R. (2024). Comprehensive Review Analysis and Countermeasures for Cybersecurity Threats: DDoS, Ransomware, and Trojan Horse Attacks. Preprints.org. [CrossRef]
- Salama, S.; et al. (2023) Cloud Computing Security Issues and Countermeasure: A Comprehensive Survey, International Journal of Computer Applications. Available at: chrome-extension://gphandlahdpffmccakmbngmbjnjiiahp/https://cdn.discordapp.com/attachments/1107952757320724611/1299234999249145866/salama-2023-ijca-922832.pdf?ex=673ac8e2&is=67397762&hm=be585808b85d92b7e2992f881c6c120afc7ab2565cd2f40e15dcfa0e69dcac3f&(Accessed: ). 28 October.
- Schulze, H. (2023). 2023 Insider Threat Report. Available at: https://www.cybersecurity-insiders.com/wp-content/uploads/2023/01/2023_Insider_Threat_Report-16d8d8f7.pdf[Accessed 1 Nov. 2024].
- Seng, Y. J. , Cen, T. Y., Raslan, M. a. H. B. M., Subramaniam, M. R., Xin, L. Y., Kin, S. J., Long, M. S., & Sindiramutty, S. R. (2024). In-Depth Analysis and Countermeasures for Ransomware Attacks: Case Studies and Recommendations. Preprints.org. [CrossRef]
- Shah, I. A. , Jhanjhi, N. Z., & Laraib, A. (2022). Cybersecurity and blockchain usage in contemporary business. In Advances in information security, privacy, and ethics book series (pp. 49–64). [CrossRef]
- Sharma, R. , Singh, A., Kavita, N., Jhanjhi, N. Z., Masud, M., Jaha, E. S., & Verma, S. (2021). Plant disease diagnosis and image classification using deep learning. Computers, Materials & Continua/Computers, Materials & Continua (Print). [CrossRef]
- Sheriffdeen, K. (2022). Integrating Cloud-Based Solutions in Disaster Recovery Planning. [pdf] p.20. Available at: https://www.researchgate.net/profile/Martins-Ade/publication/383849282_Integrating_Cloud-Based_Solutions_in_Disaster_Recovery_Planning/links/66dc87562390e50b2c729284/Integrating-Cloud-Based-Solutions-in-Disaster-Recovery-Planning.pdf [Accessed 14 Nov. 2024].
- Sindiramutty, S. R. , Jhanjhi, N. Z., Tan, C. E., Khan, N. A., Shah, B., & Manchuri, A. R. (2024). Cybersecurity measures for logistics industry. In Advances in information security, privacy, and ethics book series (pp. 1–58). [CrossRef]
- Sindiramutty, S. R. , Jhanjhi, N. Z., Tan, C. E., Khan, N. A., Shah, B., Yun, K. J., Ray, S. K., Jazri, H., & Hussain, M. (2024). Future trends and emerging threats in drone cybersecurity. In Advances in information security, privacy, and ethics book series (pp. 148–195). [CrossRef]
- Sindiramutty, S. R. , Jhanjhi, N. Z., Tan, C. E., Yun, K. J., Manchuri, A. R., Ashraf, H., Murugesan, R. K., Tee, W. J., & Hussain, M. (2024). Data security and privacy concerns in drone operations. In Advances in information security, privacy, and ethics book series (pp. 236–290). [CrossRef]
- Sindiramutty, S. R. , Jhanjhi, N., Tan, C. E., Lau, S. P., Muniandy, L., Gharib, A. H., Ashraf, H., & Murugesan, R. K. (2024). Industry 4.0. In Advances in logistics, operations, and management science book series (pp. 342–405). [CrossRef]
- Sindiramutty, S. R. , Tan, C. E., & Wei, G. W. (2024). Eyes in the sky. In Advances in information security, privacy, and ethics book series (pp. 405–451). [CrossRef]
- Sindiramutty, S. R. , Tan, C. E., Shah, B., Khan, N. A., Gharib, A. H., Manchuri, A. R., Muniandy, L., Ray, S. K., & Jazri, H. (2024). Ethical considerations in drone cybersecurity. In Advances in information security, privacy, and ethics book series (pp. 42–87). [CrossRef]
- Singhal, V. , Jain, S. S., Anand, D., Singh, A., Verma, S., Kavita, N., Rodrigues, J. J. P. C., Jhanjhi, N. Z., Ghosh, U., Jo, O., & Iwendi, C. (2020). Artificial Intelligence Enabled Road Vehicle-Train Collision Risk Assessment Framework for Unmanned railway level crossings. IEEE Access, 1138. [Google Scholar] [CrossRef]
- Tabrizchi, H. and Rafsanjani, M.K. (2020). A survey on security challenges in cloud computing: issues, threats, and solutions. The Journal of Supercomputing, 9493. [Google Scholar] [CrossRef]
- Technical Review. *Future Internet*, 14(1), p.11. [CrossRef]
- Tisha, G. , Neha, S., Manjeet, S., and Shalu, S. (2024). Comparative Study of Security Threats in Cloud Computing. Available at: https://www.researchgate.net/publication/381193283_Comparative_Study_of_Security_Threats_in_Cloud_Computing [Accessed 1 Nov. 2024].
- Ul Haq, M.N. and Sharma, M.K. (2023). MASTERING CLOUD SECURITY: TECHNIQUES AND BEST PRACTICES. EMERGING TRENDS IN CLOUD SECURITY AND INTELLIGENT AGENTS. [CrossRef]
- Waheed, A. , Seegolam, B., Jowaheer, M. F., Sze, C. L. X., Hua, E. T. F., & Sindiramutty, S. R. (2024). Zero-Day Exploits in Cybersecurity: Case Studies and Countermeasure. preprints.org. [CrossRef]
- Wen, B. O. T. , Syahriza, N., Xian, N. C. W., Wei, N. G., Shen, T. Z., Hin, Y. Z., Sindiramutty, S. R., & Nicole, T. Y. F. (2023). Detecting cyber threats with a Graph-Based NIDPS. In Advances in logistics, operations, and management science book series (pp. 36–74). [CrossRef]
- What is honeypot? working, types & benefits (2024) SentinelOne. Available at: https://www.sentinelone.com/cybersecurity-101/threat-intelligence/honeypot-cyber-security/(Accessed: ). 13 November.
- Zeyu, H. , Geming, X., Zhaohang, W., and Sen, Y. (2020). Survey on Edge Computing Security. *IEEE Xplore*. [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).




