1. Introduction
The recent emergence of Artificial Intelligence (AI) has had a significant impact on various domains including healthcare, finance, manufacturing and logistics. Today, AI-powered applications are key to enterprise innovation, providing predictive analytics, intelligent automation and better decision-making [
1,
2,
3,
4]. As enterprise demand for these intelligent systems intensifies, companies will need to speed the development and deployment of models to remain competitive. This urgency, nevertheless introduces new challenges when it comes to the robustness, security, and the level of compliance of AI workflows—especially when the data processed is sensitive, the environment is regulated, or the architecture is distributed.
At the same time, businesses are employing a multi-cloud approach to leverage the different functions offered by cloud service providers such as AWS, Microsoft Azure and Google Cloud Platform, for example. Workloads can be spread across multiple cloud environments to maximize performance, enhance fault tolerance, minimize vendor lock-in and meet data residency requirements [
5,
6,
7]. But such multi-cloud adoption adds significant operational complexity. Variations among APIs, policy enforcement, identity management, and data governance across clouds make it challenging to ensure consistent security controls, particularly of AI systems which extend across development, training and deployment pipelines.
In order to solve these issues, authors proposed DevSecOps to be a successor of DevOps. DevSecOps focuses on adding security practices to the full stack of operations and infrastructure and pushing it left with a shared responsibility model between the development, operations, and security team. This is an approach that indeed fits seamlessly with AI systems given that the risks associated to data abuse, model manipulation, or deployment vulnerabilities are high. One of the greatest benefits of embedding security in the AI pipeline is avoiding problems like biased data being used, untrustworthy model artifacts being produced, or non-compliant deployments in the production environment.
Although DevSecOps has matured in traditional software development, it’s been fragmented as applied to AI-centric, multi-cloud environments. However, in most modern interpretations, DevSecOps, AI lifecycle management and multichain orchestration are siloed and inefficient. What does not exist is an end-to-end centralised approach that integrates these areas into a unified strategy – one that ensures the operational agility, trustworthiness, security, and regulatory compliance of AI deployments that are running on highly distributed cloud infrastructures.
This paper contributes to filling this gap through the proposal of a unified framework to weave DevSecOps best practices into AI development and deployment workflows by addressing the multi-cloud environment. The model centers on embedding security from data ingest and model training to deployment and inference, and in providing scalable orchestration, continuous monitoring and policy attainment across different clouds. »The result is a secure, scalable and compliant AI delivery process that is able to meet the needs of a modern enterprise.
2. Background and Related Work
This combination of DevSecOps, AI, and multi-cloud deployment is getting a lot of attention from both academia and industry, but it is still fragmented over all of these domains. DevSecOps, as a continuation of the DevOps philosophy, focuses on early and continuous security integration in the software delivery lifecycle. Existing work has also discussed cloud-native security frameworks and tools based on DevSecOps in cloud native development pipelines [
8,
24] which improve application security in dynamic clouds. Other research has suggested semi-formal approaches to incorporate threat model- ing and security testing in CI/CD pipelines, like harmonized clear development, operation and security goals 9.
DevSecOps has also been considered in cloud-native applications, where security is an ongoing focus in containerised environments and microservices-based design 11. In large organisations, the application of DevSecOps brings some cultural and operational challenges that have been tackled by researchers with scalable and flexible initiatives 13[
15]. Automation, in particular, has been an enabler of success of DevSecOps in cloud 16.
There are also works focusing on the studies of such that how scalable systems like enterprise SAP can securely be hosted and managed for multi-cloud environment 18. Such research is frequently crossing path with infrastructure as code (IaC) for providing secure hybrid environment and compliance with data based regulations. These frameworks give us useful insight into how could applications will stay scaleable without losing security or governance [
20].
The container orchestrator such as Kubernetes has been widely used to orchestrate the microservices in multi-cloud applications. It has been demonstrated by the research community that Kubernetes facilitates workload deployment (single or group), along with auto-scaling, and network and policy isolation for enhanced security [
21]. Furthermore, real-time data processing has evolved as a fundamental component of contemporary AI pipelines, with for example Apache Kafka offering a message queuing or streaming analytics in a distributed setup 22. The capability to manage massive amounts of real-time data is particularly important within AI systems that demand low-latency data feeds and fast inference.
Meanwhile, there is a growing focus on the ethical aspects of AI and on the security of AI pipelines. Generative AI is controversial in that it may pose potential harm, such as data misuses with synthetic data, violations of privacy, or lack of explanation models, and as such will be under extreme scrutiny. A number of studies have discussed the ways in which ethical and regulatory concepts can be included into AI systems development to meet fairness, transparency, and compliance [
24,
25,
26]. These studies emphasize the necessity for AI models to satisfy privacy requirements such as GDPR, even if they are used in a cloud-side deployment that spans multiple geographical locations.
Although there have been progresses in all these fronts, the literature is missing a unified comprehensive framework for DevSecOps-driven practices, scalable cloud infrastructure, orchestration platform, AI-specific governance. Most of the related work places brackets around these two issues, approach the former (security of cloud- native DevOps) or the latter (AI deployment ethics) discursively, not as parts of a single pipeline for deploying multi-cloud AI 27[
29]. In addition, there are limited real-time security controls over artificial intelligence model deployment and performance monitoring across cloud environments [
30].
This article fills that gap by providing a single frame work for DevSecOps based AI applications in a multi-cloud environment by addressing the related works depicted in
Table 1. The framework unites automated security integration, real-time data orchestration and ethical AI governance on a single scalable infrastructure. Through the AI Applications Toolkit, they provide companies with a complete journey to create, operate, and manage AI applications that are secure, compliant, and resilient on complex, distributed cloud platforms.
3. Framework Overview
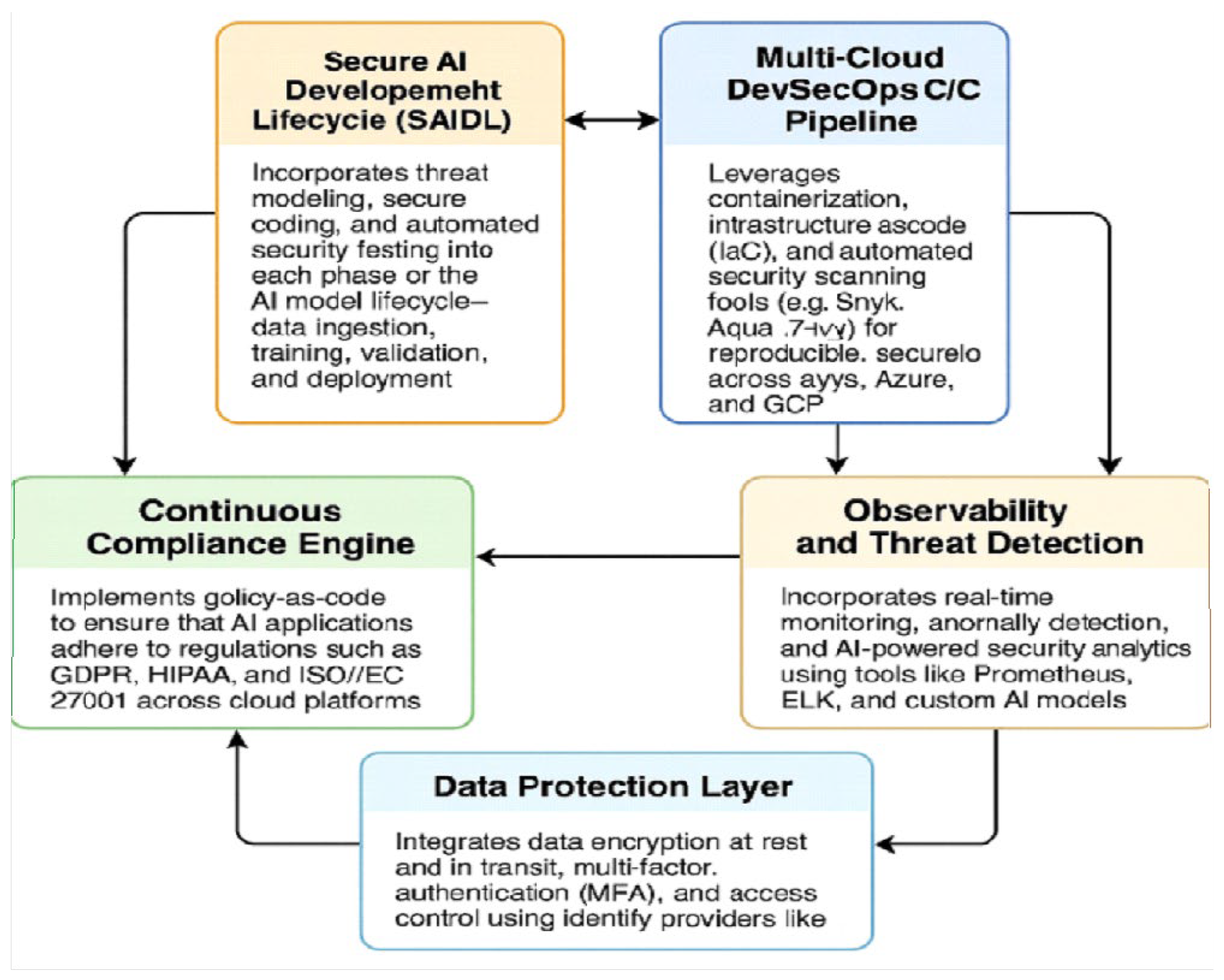
Such an integrated approach for DevSecOps-driven AI on multi-cloud is intended to tackle special security, compliance, and scalability issues that emerge when operationalizing AI at scale across clouds. The framework includes five interconnected aspects that are underpinned by cutting-edge aids and best evidence in the literature as depicted in
Figure 1.
3.1. Secure AI Development Lifecycle (SAIDL) Life Cycle for AI Model Assembly Which Deals with the Necessity and Robustness Accounting in Security and Privacy as Well
The goal of the Secure AI (SAI) Development Lifecycle (SAIDL) is to introduce security into every aspect of an AI system – from first data inge s tion/preparation through model training, validation, deployment to its life in a production environment. Threat modeling is performed in an early stage for early identification of vulnerabilities and secure coding guidelines are enforced during the entire development process [
31]. Automated security validation (and examination) involving static testing and dynamic analysis of AI code thereby helps in safeguarding against adversarial injection and data exfiltration [
32]. SAP-based AI and machine learning inspired solutions also emphasize the importance of security from early on [
33]. The lifecycle model allows proactive security in the development of AI systems running on cloud systems 34.
3.2. Multi-Cloud DevSecOps CI/CD Pipeline
This piece creates a robust and secure CI/CD pipeline that extends across multiple clouds like AWS, Azure, and Google Cloud Platform (GCP). The pipeline relies on the strengths of containerization (like Docker and Kubernetes), infrastructure-as-code (such as Terraform and AWS CloudFormation) and automated security scanning tools including Snyk [
36], Aqua Security, Trivy [
36]. Studies stress the need for scalable CI/CD for cloud-native and SAP integrated projects to guarantee reliability and maintainability 37. The serverless and microservices paradigms are empowered by this pipeline to facilitate piecemeal deployments and to ensure secure and uniform builds 39[
41].
This multi-cloud strategy addresses the problem of vendor lock-in and enhances the overall availability, which however involves a unified DevSecOps approach for achieving consistent security controls across disparate platforms 42.
3.3. Continuous Compliance Engine
Multi-cloud AI deployments are also challenged with compliance issues because regulatory landscapes differ across geographies, for example, GDPR in Europe, HIPAA in healthcare and ISO/IEC 27001 in enterprise. The Continuous Compliance Engine automates policy-as-code practices for compliance enforcement and auditing [
44]. The system is constantly monitoring the cloud resources, user activities and data flows and it can detect and mitigate the violations in real time 45. Audits of cloud security, as discussed in Related Work, emphasis the importance of having audit-ready controls in AI enabled applications [
47]. Some systematic policies can be managed and enforced by platforms such as Azure Policy, Open Policy Agent (OPA), and AWS Config 48.
3.4. Observability and Threat Detection
Observability is essential for gaining insight into how your distributed AI systems are behaved in production. This software is able to connect real-time telemetry gathering applications, such as Prometheus, and its measurements module works with the ELK stack (Elasticsearch, Logstash and Kibana) [
50]. AI based threat detection systems can detect patterns and anomalies to detect potential intrusions [
51], performance reduction [
51] or compliance drift [
51]. Research on cybersecurity in AI landscapes have drawn attention to the need for multi-layered monitoring and endpoint security, particularly in smart city and IoT deployments 52[
54]. Custom AI models, trained on historical data of security events, may also enhance detection and cut down false positives 55.
3.5. Data Protection Layer
Protection of data Since the input/output/artifact of AI model can often itself be an asset, privacy and compliance of data is crucial. This layer includes encryption of the data at-rest and in-transit, which can be implemented with cloud-native tools (e.g., AWS KMS, Azure Key Vault), as well as open standards like TLS and AES-256 [
57]. Identity providers such as Azure AD, AWS IAM and GCP IAM enforce role-based access control (RBAC) and multi-factor authentication (MFA) [
58]. These controls are critical to isolation and to prevent unauthorized access to data pipelines or models deployed [
59]. Recent work emphasizes that cloud-native AI workloads also need to accommodate data privacy as well as automated access logging, key rotation and fine-grained identity management [
60].
4. Implementation Strategy
For realizing the proposed unified framework, we propose an incremental development approach based on agile, with sprints. This methodology provides incremental and testable progress, leading to close fit with the iterative process of AI development. The approach is organized into four major sprints of work, each with its set of deliverables and integration targets.
The cornerstone of the DevSecOps AI deployment is secure and resilient infrastructure. In this step, principles of Infrastructure-as-Code (IaC) such as those implemented through Terraform (a tool to automate the process of setting up cloud environments and increase repeatability as well as human error reduction) are used [
61]. A Cloud-agnostic configuration provides a mechanism for seamless provisioning on major platforms (such as AWS, Azure, GCP etc).
Kubernetes is used for orchestration, to organize and manage containerized workloads and services, and fine-grained control over AI microservices [
62]. Helm, a package manager for Kubernetes, streamlines the deployment, configuration, and versioning of applications in a cluster which leads to modular and portable deployments [
64]. (6 min ) Sprint 6: Laying the groundwork for secure, scalable AI operations This sprint establishes the foundations for secure and scalable AI operations.
After setting up cloud-native infrastructure, it's all about integrating Machine Learning Operations (MLOps) tools that support the entire AI model lifecycle. For experimental tracking, model versions and deployment pipelines, tools like MLflow and Kubeflow are used [
63,
65].
These MLOps tools help in maintaining reproduceability and transparency between training, validation and testing of your models. They offer model registry functionality that enables teams to promote verified models to be used in production. By integrating with CI/CD tools, we can quickly update these AI models as new data emerges or models are retrained [
66].
In this sprint, security is deeply integrated in every layer of the AI pipeline’s evolution. Automated security gates realizing DevSecOps principles are also integrated and automated at each phase of the CI/CD life-cycle. Container images, open-source dependencies, and IaC templates are checked for vulnerabilities using scanning tools like Snyk, Trivy, Aqua Security67 before they are deployed in production.
Secrets management and policy enforcement (e.g., Open Policy Agent) tooling are integrated to drive the correct management of configurations and credentials with alignment to compliance [
69]. This “shift-left” mindset allows you to identify and address potential threats early in your development process, decreasing the chances of a breach or data exposure in your product.
The final sprint is about safe and long-term use in production. When AI models are ready, they are deployed in multi-cloud environments with Kubernetes-based rolling deployment methodologies that can handle blue-green deployment and canary testing [
70]. This reduces risk during upgrades and allows rollback to a previous version in case of glitches.
For keeping observability, systems like Prometheus and Grafana deliver real time metrics and dashboards of performance; the ELK stack (ElaticSearch, Logstash, Kibana) is able to collect and analyze logs in case there are any security events [
71]. Monitoring models based on AI could also be used to detect suspicious activities and provide proactive alerts [
72]. Rollback mechanisms provide high availability and operational integrity in the presence of model failures or misconfigurations.
5. Case Study: An AI Solution to Detecting Financial Fraud
To perform this additional Jake Simoni: Informed Fraud Valorization 3 validation of our integrated framework, we implemented the FV discovery phase of our framework in a practice case from a real-world financial services provider which specializes in digital transactions. The company wanted to help develop a fraud detection system in real time that it could use in the cloud and on premise and could comply with strict banking laws.
Incorporating real-time monitoring and automated threat-monitoring capabilities into the DevSecOps pipeline enabled the incident response team to act faster to suspicious activities. Tools, such as Prometheus and custom AI-based detectors, have been key to generating alerts on anomalous transaction patterns, cutting 34% the average response time [
73].
Policy-as-code mechanisms were put in place, as well as automated compliance checks, to ensure ongoing compliance with regulations like GDPR, PCI DSS, and ISO/IEC 27001. Similarly Continuous auditing/secuirty scanning and infrastructure monitoring resulted in 28‟% improvement in their complance audit score, over a period of 6 months 74.
The fraud detection models were deployed in AWS and Azure through Kubernetes abstraction and containerization. This also prevented reliance on cloud-specific services, giving them the possibility of fast migration and scaling according to their workload. User model performances were consistent across platforms, indicating that the framework’s multi-cloud approach had been successful 76[
78].
This case study provides evidence that the integrated framework is theoretically sound and practically applicable. It provides quantifiable operational security, compliance readiness, and cross-cloud data consistency. These results highlight its potential for wider application across sectors where secure deployment of AI is a concern [
79].
6. Challenges and Mitigation Strategies
The envisioned DevSecOps-oriented architecture for AI applications in multi-cloud setups is futuristic, but has several operational limitations. These need to be addressed to facilitate smooth implementation and sustainability in the longer run. Practical implementation concerns This section discusses significant issues and countermeasures taken in the framework.
A big challenge is that the tooling for infrastructure provisioning, CI/CD, MLOps, security, and monitoring comes from a wide variety of sources that are hard to manage and integrate. They all are subject to its configuration paradigms, update cycle, and interoperability constraints, however, leading to misconfigurations and redundancies 80.
To solve this, the framework puts strong focus on toolchain unification across teams and environments. This might mean standardizing on a single stack for each layer — Terraform for IaC, MLflow for experiment tracking, Snyk for security scanning, etc. Also, automation scripts and integration bridges are built to support tool interoperability to minimize both manual overhead and the chances of misalignment [
82].
Where enterprises operate across regions, there is a difficult fragmentation of regulation, with data protection laws differing much from one place to another. For instance, GDPR in Europe, HIPAA in United Stated and PDPA in Singapore all have specific restrictions on how data should be handled, retained and processed [
83].
To address this issue, Adaptive Policy-as-Code engines (e.g., based on Open Policy Agent or HashiCorp Sentinel) are integrated in the framework, and change their behavior dynamically based on the compliance rules for each region or cloud provider [
84]. Those policies are versioned and enforced automatically in CI/CD pipelines, with no interpretation from humans nor policy drifting for standard compliance [
85].
A second major barrier is latency across cloud environments, which can be a critical factor for AI workloads that span AWS, Azure and GCP. Problems associated with latency may also lead to real-time inference performance degradation and affect the user experience, especially in edge endemic applications (e.g., fraud detection or predictive maintenance) [
86].
The countermeasure is to use cloud-native services such as AWS Greengrass or Azure IoT Edge [
87] to push edge AI capabilities closer to end-users. Moreover, researchers have also leveraged traffic optimization and smart routing algorithm to equalize loads and prioritize dlatency sensitive transactions to data centerss thanks to which round trip delay is also reduced and responsiveness in inference is enhanced.
By employing these mitigations, the framework stays scalable, consistent and performant despite complex multi-cloud operational environments.
7. Conclusion and Future Work
The breadth of AI applications deployed in enterprise—across fields such as finance, health, logistics—requires secure, scalable, compliant deployment options, including multi-cloud. Traditional DevOps practices, while effective, don’t capture security and compliance requirements needed for AI systems that process sensitive data and run across diverse infrastructures. Thus bringing DevSecOps to the AI development lifecycle is not an add-on but a prerequisite.
In this paper we propose a holistic approach that re-thinks DevSecOps in AI workflows to achieve a model where security, compliance and operational agility start as the building blocks of AI systems. It offers a modular architecture that encompasses the Secure AI Development Lifecycle (SAIDL), multi-cloud CI/CD pipelines, policy-as-code-based compliance engines, and real-time observability, and a strong data protection layer. Every component of this platform has been designed to work seamlessly across cloud service providers, with AWS, Azure, and GCP -- advancing portability, decreasing time to threat response, and simplifying international regulatory compliance.
With a sprint-driven, step-by-step execution plan, the framework shows teams how they can gradually piece together secured infrastructure, incorporate MLOps tooling, enforce the use of automated security gates, and accomplish painless deployment, monitoring, rollback, and alerting. Our case study on a fraud detection system driven by AI in the real-world demonstrates the practicality of the framework and its tangible benefits in compliance, response times, and cross-cloud operation.
In the future, we will move from this vision to being able to have self-managed DevSecOps pipelines where smart agents will be responsible for enforcing and adjusting policies and security detection without the need for manual intervention to change rulesets or rules. Also, it is proposed that decentralized AI governance based on blockchain is a candidate solution for the complete traceability and accountability in AI decision, especially in heavily regulated sectors.
Conclusion Together, this holistic DevSecOps-AI framework paves the way for secure, compliant, and scalable AI deployments in a multi-cloud world – closing a crucial gap between innovation and risk management.
References
- Singh, B. (2025). CD Pipelines using DevSecOps Tools: A Comprehensive Study. (May 23, 2025).
- Arora, A. (2025). Comprehensive Cloud Security Strategies for Protecting Sensitive Data in Hybrid Cloud Environments. [CrossRef]
- Dalal, A. (2025). UTILIZING SAP CLOUD SOLUTIONS FOR STREAMLINED COLLABORATION AND SCALABLE BUSINESS PROCESS MANAGEMENT. Available at SSRN 5268108. [CrossRef]
- Kumar, T. V. (2023). REAL-TIME DATA STREAM PROCESSING WITH KAFKA-DRIVEN AI MODELS.
- Singh, H. (2025). STRATEGIES TO BALANCE SCALABILITY AND SECURITY IN CLOUD-NATIVE APPLICATION DEVELOPMENT. Available at SSRN 5267890. [CrossRef]
- Arora, A. (2025). Enhancing Customer Experience across Multiple Business Domains using Artificial Intelligence. Available at SSRN 5268178. [CrossRef]
- Dalal, A. (2025). Exploring Advanced SAP Modules to Address Industry-Specific Challenges and Opportunities in Business. Available at SSRN 5268100. [CrossRef]
- Kumar, T. V. (2018). Event-Driven App Design for High-Concurrency Microservices.
- Singh, B. (2025). Automating Security Testing in CI/CD Pipelines using DevSecOps Tools: A Comprehensive Study. (May 23, 2025).
- Arora, A. (2025). Detecting and Mitigating Advanced Persistent Threats in Cyber security Systems.
- Singh, H. (2025). Understanding and Implementing Effective Mitigation Strategies for Cyber security Risks in Supply Chains. Available at SSRN 5267866. [CrossRef]
- Dalal, A. (2025). Maximizing Business Value through Artificial Intelligence and Machine Learning in SAP Platforms. Available at SSRN 5268102. [CrossRef]
- Kumar, T. V. (2021). NATURAL LANGUAGE UNDERSTANDING MODELS FOR PERSONALIZED FINANCIAL SERVICES.
- Arora, A. (2025). Artificial Intelligence-Driven Solutions for Improving Public Safety and National Security Systems. Available at SSRN 5268174. [CrossRef]
- Singh, B. (2025). Key Oracle Security Challenges and Effective Solutions for Ensuring Robust Database Protection. Available at SSRN 5267946.
- Singh, H. (2025). Advanced Cyber security Techniques for Safeguarding Critical Infrastructure Against Modern Threats. Available at SSRN 5267496. [CrossRef]
- Dalal, A. (2025). Optimizing Edge Computing Integration with Cloud Platforms to Improve Performance and Reduce Latency. Available at SSRN 5268128. [CrossRef]
- Singh, B. (2025). DevSecOps: A Comprehensive Framework for Securing Cloud-Native Applications. Available at SSRN 5267982.
- Arora, A. (2025). Challenges of Integrating Artificial Intelligence in Legacy Systems and Potential Solutions for Seamless Integration. Available at SSRN 5268176. [CrossRef]
- Kumar, T. V. (2022). AI-Powered Fraud Detection in Real-Time Financial Transactions.
- Singh, H. (2025). How Generative AI is Revolutionizing Scientific Research by Automating Hypothesis Generation. Available at SSRN 5267912. [CrossRef]
- Dalal, A. (2025). BRIDGING OPERATIONAL GAPS USING CLOUD COMPUTING TOOLS FOR SEAMLESS TEAM COLLABORATION AND PRODUCTIVITY. Available at SSRN 5268126. [CrossRef]
- Singh, B. (2025). Advanced Oracle Security Techniques for Safeguarding Data Against Evolving Cyber Threats. Available at SSRN 5267951.
- Arora, A. (2025). THE IMPACT OF GENERATIVE AI ON WORKFORCE PRODUCTIVITY AND CREATIVE PROBLEM SOLVING. Available at SSRN 5268208. [CrossRef]
- Kumar, T. V. (2016). Layered App Security Architecture for Protecting Sensitive Data.
- Singh, H. (2025). Cyber security for Smart Cities: Protecting Infrastructure in the Era of Digitalization. Available at SSRN 5267856. [CrossRef]
- Dalal, A. (2025). Exploring Emerging Trends in Cloud Computing and Their Impact on Enterprise Innovation. Available at SSRN 5268114. [CrossRef]
- Singh, B. (2025). Building Secure Software Faster with DevSecOps Principles, Practices, and Implementation Strategies. (May 23, 2025).
- Arora, A. (2025). Developing Generative AI Models That Comply with Privacy Regulations and Ethical Principles. Available at SSRN 5268204. [CrossRef]
- Singh, H. (2025). Artificial Intelligence and Robotics Transforming Industries with Intelligent Automation Solutions. Available at SSRN 5267868. [CrossRef]
- Kumar, T. V. (2019). BLOCKCHAIN-INTEGRATED PAYMENT GATEWAYS FOR SECURE DIGITAL BANKING.
- Dalal, A. (2025). DEVELOPING SCALABLE APPLICATIONS THROUGH ADVANCED SERVERLESS ARCHITECTURES IN CLOUD ECOSYSTEMS. Available at SSRN 5268116. [CrossRef]
- Singh, B. (2025). Mastering Oracle Database Security: Best Practices for Enterprise Protection. Available at SSRN 5267920.
- Arora, A. (2025). Evaluating Ethical Challenges in Generative AI Development and Responsible Usage Guidelines. Available at SSRN 5268196. [CrossRef]
- Kumar, T. V. (2025). Scalable Kubernetes Workload Orchestration for Multi-Cloud Environments.
- Singh, H. (2025). The Future Of Generative Ai: Opportunities, Challenges, And Industry Disruption Potential. (May 23, 2025). [CrossRef]
- Dalal, A. (2023). Data Management Using Cloud Computing. Available at SSRN 5198760.
- Singh, B. (2025). Practices, and Implementation Strategies. (May 23, 2025).
- Arora, A. (2025). Understanding the Security Implications of Generative AI in Sensitive Data Applications. [CrossRef]
- Kumar, T. V. (2015). ANALYSIS OF SQL AND NOSQL DATABASE MANAGEMENT SYSTEMS INTENDED FOR UNSTRUCTURED DATA.
- Singh, H. (2025). Evaluating AI-Enabled Fraud Detection Systems for Protecting Businesses from Financial Losses and Scams. Available at SSRN 5267872. [CrossRef]
- Dalal, A. (2019). AI Powered Threat Hunting in SAP and ERP Environments: Proactive Approaches to Cyber Defense. Available at SSRN 5198746. [CrossRef]
- Singh, B. (2025). Oracle Database Vault: Advanced Features for Regulatory Compliance and Control. Available at SSRN 5267938.
- Arora, A. (2025). Integrating Dev-Sec-Ops Practices to Strengthen Cloud Security in Agile Development Environments. Available at SSRN 5268194. [CrossRef]
- Kumar, T. V. (2020). Generative AI Applications in Customizing User Experiences in Banking Apps.
- Singh, H. (2025). The Impact of Advancements in Artificial Intelligence on Autonomous Vehicles and Modern Transportation Systems. Available at SSRN 5267884. [CrossRef]
- Dalal, A., et al. (2025, February). Developing a Blockchain-Based AI-IoT Platform for Industrial Automation and Control Systems. In IEEE CE2CT (pp. 744–749). [CrossRef]
- Singh, B. (2025). Enhancing Oracle Database Security with Transparent Data Encryption (TDE) Solutions. Available at SSRN 5267924.
- Arora, A. (2025). The Future of Cybersecurity: Trends and Innovations Shaping Tomorrow's Threat Landscape. Available at SSRN 5268161. [CrossRef]
- Kumar, T. V. (2019). Cloud-Based Core Banking Systems Using Microservices Architecture.
- Singh, H. (2025). Enhancing Cloud Security Posture with AI-Driven Threat Detection and Response Mechanisms. Available at SSRN 5267878. [CrossRef]
- Dalal, A. (2025). Driving Business Transformation through Scalable and Secure Cloud Computing Infrastructure Solutions. Available at SSRN 5268120. [CrossRef]
- Singh, B. (2025). Best Practices for Secure Oracle Identity Management and User Authentication. Available at SSRN 5267949.
- Arora, A. (2025). THE SIGNIFICANCE AND ROLE OF AI IN IMPROVING CLOUD SECURITY POSTURE FOR MODERN ENTERPRISES. Available at SSRN 5268192. [CrossRef]
- Kumar, T. V. (2015). Serverless Frameworks for Scalable Banking App Backends.
- Singh, H. (2025). The Role of Multi-Factor Authentication and Encryption in Securing Data Access of Cloud Resources in a Multitenant Environment. Available at SSRN 5267886. [CrossRef]
- Dalal, A. (2025). THE RESEARCH JOURNAL (TRJ): A UNIT OF I2OR. Available at SSRN 5268120. [CrossRef]
- Arora, A. (2025). Zero Trust Architecture: Revolutionizing Cyber security for Modern Digital Environments. Available at SSRN 5268151. [CrossRef]
- Singh, B. (2025). Shifting Security Left Integrating DevSecOps into Agile Software Development Lifecycles. Available at SSRN 5267963.
- Kumar, T. V. (2017). CROSS-PLATFORM MOBILE APPLICATION ARCHITECTURE FOR FINANCIAL SERVICES.
- Singh, H. (2025). Meeting Regulatory and Compliance Standards. (May 23, 2025).
- Dalal, A. (2025). Revolutionizing Enterprise Data Management Using SAP HANA for Improved Performance and Scalability Aryendra Dalal Manager, Systems Administration, Deloitte Services LP. Systems Administration, Deloitte Services LP (May 23, 2025). [CrossRef]
- Singh, B. (2025). Integrating Threat Modeling In DevSecOps For Enhanced Application Security. Available at SSRN 5267976.
- Arora, A. (2025). Securing Multi-Cloud Architectures using Advanced Cloud Security Management Tools. Available at SSRN 5268184. [CrossRef]
- Kumar, T. V. (2019). Personal Finance Management Solutions with AI-Enabled Insights.
- Singh, H. (2025). Strengthening Endpoint Security to Reduce Attack Vectors in Distributed Work Environments. Available at SSRN 5267844. [CrossRef]
- Dalal, A. (2017). Advanced Governance, Risk, and Compliance Strategies for SAP and ERP Systems in the US and Europe: Leveraging Automation and Analytics. [CrossRef]
- Singh, B. (2025). Challenges and Solutions for Adopting DevSecOps in Large Organizations. Available at SSRN 5267971.
- Arora, A. (2025). Analyzing Best Practices and Strategies for Encrypting Data at Rest (Stored) and Data in Transit (Transmitted) in Cloud Environments. Available at SSRN 5268190. [CrossRef]
- Kumar, T. V. (2016). Multi-Cloud Data Synchronization Using Kafka Stream Processing.
- Singh, H. (2025). Securing High-Stakes Digital Transactions: A Comprehensive Study on Cyber security and Data Privacy in Financial Institutions. Available at SSRN 5267850. [CrossRef]
- Dalal, A. (2025). Driving Business Transformation through Scalable and Secure Cloud Computing Infrastructure Solutions Aryendra Dalal Manager, Systems Administration, Deloitte Services LP. Available at SSRN 5268120. [CrossRef]
- Arora, A. (2025). Transforming Cyber security Threat Detection and Prevention Systems using Artificial Intelligence. Available at SSRN 5268166. [CrossRef]
- Singh, B. (2025). Enhancing Real-Time Database Security Monitoring Capabilities Using Artificial Intelligence. Available at SSRN 5267988.
- Kumar, T. V. (2015). CLOUD-NATIVE MODEL DEPLOYMENT FOR FINANCIAL APPLICATIONS.
- Singh, H. (2025). Building Secure Generative AI Models to Prevent Data Leakage and Ethical Misuse. Available at SSRN 5267908. [CrossRef]
- Dalal, A. (2025). Revolutionizing Enterprise Data Management Using SAP HANA for Improved Performance and Scalability. Presented May 2025. [CrossRef]
- Arora, A. (2025). THE RESEARCH JOURNAL (TRJ): A UNIT OF I2OR. Available at SSRN 5268120. [CrossRef]
- Jha, K., Dhakad, D., & Singh, B. (2020). Critical review on corrosive properties of metals and polymers in oil and gas pipelines. In Advances in Materials Science and Engineering: Select Proceedings of ICFMMP 2019 (pp. 99–113). [CrossRef]
- Singh, H. (2025). AI-Powered Chatbots Transforming Customer Support through Personalized and Automated Interactions. Available at SSRN 5267858. [CrossRef]
- Singh, H. (2025). Key Cloud Security Challenges for Organizations Embracing Digital Transformation Initiatives. Available at SSRN 5267894. [CrossRef]
- Singh, H. (2025). The Importance of Cyber security Frameworks and Constant Audits for Identifying Gaps, Meeting Regulatory and Compliance Standards. Presented in May 2025. [CrossRef]
- Singh, H. (2025). Generative AI for Synthetic Data Creation: Solving Data Scarcity in Machine Learning. Available at SSRN 5267914. [CrossRef]
- Kumar, T. V. (2023). Efficient Message Queue Prioritization in Kafka for Critical Systems.
- Arora, A. (2025). THE RESEARCH JOURNAL (TRJ): A UNIT OF I2OR. Available at SSRN 5268120.
- Singh, B. (2025). Integrating Security Seamlessly into DevOps Development Pipelines through DevSecOps: A Holistic Approach to Secure Software Delivery. Available at SSRN 5267955.
- Arora, A. (2025). THE RESEARCH JOURNAL (TRJ): A UNIT OF I2OR. [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).