1. Introduction
The digitization of financial infrastructure in smart cities has intensified the frequency and complexity of transaction-based interactions across interconnected devices. Modern cities embed financial services into transportation, healthcare, utilities, and commerce using the Internet of Things (IoT) to create a seamless digital environment. However, this connectivity increases the surface area for financial crimes and requires intelligent, real-time anomaly detection systems. Conventional cloud-only architectures struggle to manage such volumes due to bottlenecks in centralized processing and real-time responsiveness demands [
1,
2,
3].
1.1. Problem Statement
Cloud-centric systems introduce several inherent weaknesses. First, they exhibit high latency due to dependence on remote data centers, rendering them unsuitable for time-sensitive applications like fraud detection [
4,
5,
6]. Second, they frequently produce high false positive (FP) or false negative (FN) rates, as anomalies are subtle and context-sensitive [
7,
8]. Third, transferring sensitive data from the edge to the cloud raises significant privacy and regulatory concerns [
9,
10]. Thus, centralized systems alone are inadequate for fraud prevention in modern smart city ecosystems [
11,
12].
1.2. Motivation
Recent studies have proposed edge and fog computing paradigms as promising solutions to address these shortcomings. Edge computing enables real-time decision-making by processing data at the source, while fog computing offers intermediary processing nodes that can perform lightweight aggregation and deeper analysis without sending data to the cloud [
13,
14,
15]. This shift allows cities to distribute intelligence across infrastructure while minimizing latency and ensuring localized privacy controls. Additionally, embedded machine learning—especially unsupervised anomaly detection and ensemble models—can be deployed across edge-fog layers to enhance detection accuracy [
16,
17,
18].
Collaborative learning among edge devices further strengthens this architecture by aggregating multiple context-aware insights, improving classification robustness and reducing detection blind spots [
19,
20,
21].
1.3. Summary of Contributions
In this paper, we propose a multi-layered financial anomaly detection architecture that leverages unsupervised and supervised ML models at the edge and fog layers, respectively. Our key contributions include:
A novel 1–7 anomaly scoring model that classifies financial transactions from high-normal to highly anomalous using autoencoders and Gaussian-scaled post-processing.
A collaborative filtering mechanism that allows edge devices to refine their local predictions by integrating feedback from peer devices.
An ensemble architecture using Autoencoder, LightGBM, and One-Class SVM (OC-SVM) for hybrid anomaly detection, reducing FN and FP rates.
A fog-enabled decision framework that aggregates edge reports and conducts deeper analysis for supervisory escalation.
1.4. Paper Structure
The major objective of this manuscript is to develop and evaluate a multi-tier collaborative edge–fog intelligence framework that enables accurate, low-latency detection of financial anomalies in smart city environments by leveraging hybrid learning models and distributed processing across edge and fog computing layers. The remainder of this manuscript is structured as follows:
Section 2 reviews related literature on fog-based anomaly detection, the application of machine learning in smart city financial systems, and collaborative intelligence frameworks.
Section 3 introduces the proposed multi-tier architecture and outlines the transaction classification methodology.
Section 4 describes the experimental setup and implementation details of the employed algorithms.
Section 5 presents and analyzes the results obtained from simulated financial transaction data. Finally,
Section 6 concludes the paper with a summary of key findings and potential avenues for future research.
2. Related Works
The increasing deployment of IoT devices in smart cities has introduced new challenges in monitoring financial anomalies and ensuring secure data transmission. Traditional centralized systems lack the real-time responsiveness required for fine-grained anomaly detection and are often limited in scalability and privacy enforcement [
4,
5,
9].
Several works have explored
fog and edge computing architectures for smart cities. Malik and Gupta [
1] presented a fog-based IoT architecture for sustainable urban services, highlighting the role of distributed nodes in handling real-time analytics. Similarly, Aburukba et al. [
2] demonstrated a fog-layered framework for shared electric mobility services, which enabled real-time decision-making with reduced latency.
Machine learning-based anomaly detection has been widely investigated in smart city contexts. Wali and Bulla [
3] reviewed both supervised and unsupervised ML techniques (e.g., Decision Trees, Autoencoders, SOM-PSO) and emphasized hybrid models for fog-assisted classification. John [
4] implemented a CNN–RNN hybrid deep learning model for detecting banking fraud in real time using a fog-based deployment, reporting significant reductions in false positive rates.
Despite these innovations,
false negative rates remain a critical issue. Tariq et al. [
5] addressed this by applying federated support vector machines in a fog-edge architecture for smart grid intrusion detection. Their work validated the effectiveness of using OC-SVM for post-hoc anomaly refinement in ambiguous transaction regions. To reduce
data transmission latency and privacy leakage, Williams et al. [
6] proposed edge-based forensic frameworks for anomaly capture, while Tukur et al. [
7] extended blockchain smart contracts to securely log and validate anomalous behaviors detected at the edge.
From a systems perspective, Peruzzi et al. [
8] emphasized the importance of
multi-layered distributed intelligence, wherein embedded machine learning, such as embedded federated learning and edge-optimized neural nets, is deployed across constrained devices.
However,
collaborative classification—where peer edge nodes share transaction feedback—remains underexplored. Songhorabadi et al. [
9] identified the need for cooperative models in distributed fog networks and recommended collaborative filtering approaches as a promising direction.
Finally, Ometov et al. [
10] provided a comprehensive taxonomy of fog/edge security models aligned with the OSI stack. They noted the growing role of anomaly scoring and behavior-based classification in preventing insider financial crimes.
In sum, the literature reveals strong support for a decentralized, collaborative, ML-driven anomaly detection paradigm across the edge and fog continuum. Yet, there remains a critical need to integrate hybrid scoring, ensemble learning, and collaborative refinement into a unified, low-latency smart city framework—precisely what this paper proposes.
Table 1 shows the comparative analysis of related work.
Comparative Insight from Annotated Radar Analysis
To contextualize the contribution of this study, we conducted a radar-based comparison of six representative works from the literature in
Figure 1, evaluated across three strategic dimensions: system focus (Fog, Edge, or both), use of machine learning (ML), and attention to false negative (FN) handling critical metric in fraud detection. The results reveal a clear maturity gradient in the evolution of financial anomaly detection frameworks. Early architectural or deployment-centric works, such as Malik (2021) and Pozzebon (2022), were fog-exclusive and lacked both machine learning and fraud-specific detection logic. Although foundational, these approaches do not scale well for real-time, context-sensitive decision-making in smart cities.
In contrast, John (2025) introduced ML capabilities (CNN–RNN) for fog-based banking fraud detection and made significant progress toward minimizing false negatives. However, it remained limited to centralized fog execution without edge adaptability. Tariq et al. (2024) demonstrated a hybrid fog–edge system leveraging federated SVMs, achieving strong performance and FN reduction. Yet, their model lacked collaborative scoring mechanisms and fine-grained anomaly grading.
The SmartC Compilation, while including multiple ML models, serves more as a reference dataset than a coherent framework for anomaly detection.
In comparison, this study presents a holistic edge–fog architecture integrating unsupervised and supervised learning (Autoencoder, LightGBM, OC-SVM), a graded anomaly scoring system (1–7), and collaborative filtering at the edge. It is one of the few works to comprehensively address false negative mitigation while maintaining low latency and high scalability, placing it at the forefront of next-generation smart city fraud detection systems.
3. System Architecture
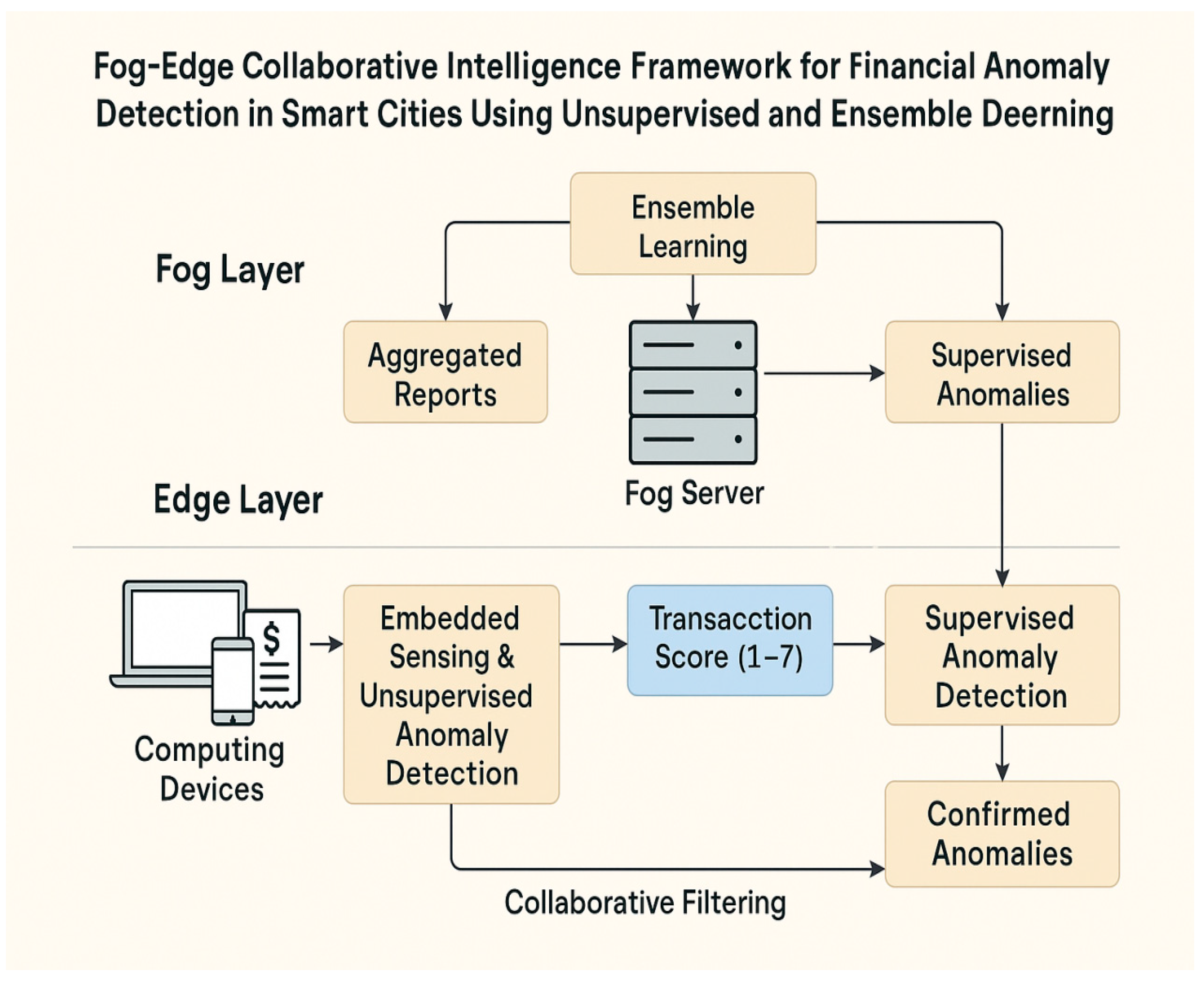
This section presents the architectural design of the proposed Fog–Edge Collaborative Framework for Financial Anomaly Detection in smart cities. The system is designed to detect financial anomalies by distributing computational intelligence across computing devices (edge) and localized servers (fog). The architecture follows a multi-layer hierarchy that supports distributed sensing, transaction scoring, anomaly classification, and intelligent aggregation.
3.1. Overview of Architecture
The proposed system is composed of two core layers:
➤ Edge Layer:
Consists of all financial transaction-generating computing devices in the smart city (e.g., mobile phones, ATMs, POS terminals, kiosks).
Each device embeds an unsupervised anomaly detection module using autoencoders to evaluate the status of the transaction.
The output is converted into a transaction score (1–7), which is:
1–2: Highly normal (True Negative)
3–4: Borderline/Suspicious (Potential FN or FP)
5–7: Highly anomalous (True Positive)
- d.
Collaborative Filtering is applied across peer devices to strengthen prediction confidence, based on contextual patterns (e.g., device type, time of day, transaction type).
➤ Fog Layer:
- a.
Serves as the aggregation and refinement tier, hosting:
Supervised ML (OC-SVM) for evaluating borderline or suspicious transactions (scores 3–7).
Ensemble hybrid ensemblemodels combining LightGBM and score analytics to improve decision boundaries.
- b.
Reports are further classified and sent to:
Administrative dashboards
City-level fraud monitoring centers
3.2. Workflow Diagram
Table 2 below is the system architecture visualized in a flowchart:
Figure 2 presents a two-tier Fog–Edge Collaborative Intelligence Framework for detecting financial anomalies in smart cities. At the edge layer, financial computing devices (e.g., ATMs, POS systems) perform embedded sensing and unsupervised anomaly detection, assigning a transaction score (1–7) based on behavioral deviation. These scores undergo collaborative filtering among neighboring devices to refine context-aware inferences. Suspicious transactions (scores 3–7) are then forwarded to the fog layer, where a fog server aggregates reports and applies ensemble learning to combine predictions from multiple base models. Subsequently, supervised anomaly detection further scrutinizes the flagged data, isolating true anomalies from false positives/negatives. The process culminates in a confirmed anomaly report for managerial action, offering a scalable, real-time, and distributed solution for fraud detection across IoT-enabled smart city infrastructures.
4. Methodology and Algorithms
This section presents the core methodological components and machine learning algorithms implemented at the edge and fog layers for distributed financial anomaly detection. The system combines unsupervised anomaly detection, score scaling, collaborative filtering, and supervised refinement in a multi-tier pipeline.
4.1. Edge-Level Anomaly Detection Using Autoencoders
At the edge layer, every smart city device (e.g., mobile device, ATM, POS terminal) is equipped with a lightweight unsupervised anomaly detection model. We use an autoencoder neural network for this purpose due to its effectiveness in learning compact representations of normal transactional patterns.
Autoencoder Workflow:
Input: Transaction feature vector (amount, time, location, merchant, frequency, etc.)
Encoder: Compresses input into latent space representation
Decoder: Attempts to reconstruct original input
Loss: Mean squared reconstruction error (MSE) used as anomaly score
Scoring Mechanism:
Table 3 outlines how anomaly scores (ranging from 1 to 7) are interpreted and used for classification in a proposed financial anomaly detection model. Scores 1–2 indicate clearly normal transactions and are treated as True Negatives (TN). Score 3 represents near-normal cases that may be potential False Negatives (FN)—anomalies mistakenly classified as normal. Score 4 falls into a gray area where it is uncertain whether the case is a False Positive (FP) or False Negative, requiring further scrutiny. Score 5 flags transactions as suspicious, leaning toward False Positives. Finally, Scores 6–7 denote highly anomalous activity and are classified as True Positives (TP), meaning correctly identified threats. This graded scoring system allows nuanced decision-making and prioritization in real-time anomaly detection systems.
4.2. Post-Processing with LightGBM and Gaussian Scaling
The raw reconstruction scores are enhanced using:
This hybrid step improves sensitivity for borderline anomalies and ensures scores reflect contextual risks.
4.3. Collaborative Filtering for Peer-Aware Classification
To improve classification reliability, especially in ambiguous regions (scores 3–5), a collaborative filtering module is activated.
Steps:
Nearby or similar devices (same region, transaction type, or user segment) are used as references.
Similarity is calculated via:
Scores are refined via:
This context-aware approach helps reduce false positives and enhances decision confidence at the edge.
4.4. Fog-Based Supervised Refinement with OC-SVM
Transactions with scores between 3 to 7 are sent to the fog node for centralized refinement. A One-Class Support Vector Machine (OC-SVM) is used to:
Detect outliers using high-dimensional margin separation
Refine classification boundaries especially around borderline scores (3, 4, 5)
Why OC-SVM?
Effective in deep anomaly detection
Requires no labeled anomalies, well-suited for fraud scenarios
Learns from “normal” baseline behavior and flags deviations
4.5. Ensemble hybrid ensemblefor Unified Decision Making
A hybrid ensemble model is used at the fog layer to merge outputs from:
Autoencoder scores
LightGBM post-processing predictions
OC-SVM anomaly likelihood
Ensemble Stack Components:
Base learners: Autoencoder, LightGBM, OC-SVM
Meta learner: Logistic regression or decision tree classifier that learns optimal weights for combining predictions
This multi-model fusion improves overall system robustness, balances false positives/negatives, and provides a final binary decision (anomalous / normal) along with a confidence score.
5. Results, Discussions and Evaluation
Results at Edge:
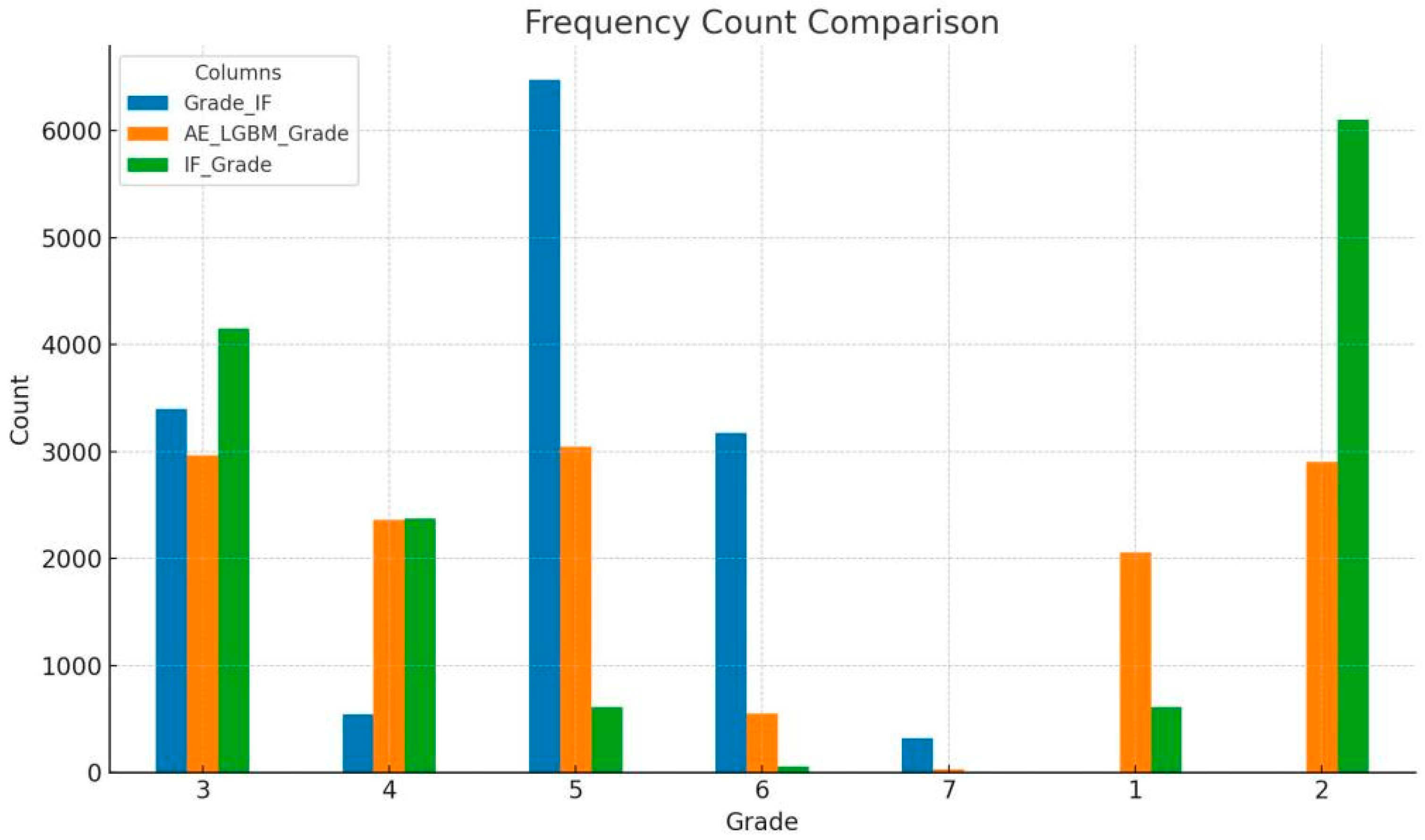
Table 4 shows the frequencies and percentages of all grades obtained by the algorithms used, IF in the initial stage (Grade_IF), AE-LGB and IF in the final stage (IF_Grade):
5.1. Interpretation of Grading Distributions:
1. Grade_IF
The Grade_IF, generated by an initial grading by IF, shows that the most frequent grade is 5 (6473 instances), followed by grade 3 (3397) and grade 6 (3172). This distribution suggests the model often classifies transactions as “suspicious” or “strongly anomalous,” potentially corresponding to true positives (TP) or false positives (FP). In contrast, the relatively low count of grade 4 (542) indicates fewer borderline or ambiguous cases, implying the system may be drawing a clear distinction between normal and anomalous behavior.
2. AE_LGBM_Grade
The AE_LGBM_Grade, generated by a hybrid LightGBM-autoencoder ensemble, displays a more balanced distribution across grades 1 to 5, with grades 5 (3046), 3 (2965), and 2 (2903) being the most frequent. Higher anomaly grades such as 6 (549) and 7 (27) are rare, indicating that this model is more conservative in flagging anomalies. This suggests an emphasis on reducing false positives and improving precision, potentially at the expense of missing some true anomalies (false negatives).
3. IF_Grade
The IF_Grade, derived from a final stage of Isolation Forest, shows a strong skew toward lower anomaly grades, with grade 2 (6102) and grade 3 (4147) being the most prevalent. In contrast, very few instances are assigned higher anomaly scores—only 55 for grade 6 and 5 for grade 7—indicating that the detector is highly conservative. This behavior suggests a bias toward high recall, minimizing false positives (FPs), but potentially at the cost of missing true anomalies, thus increasing the likelihood of false negatives.
Figure 3 below displays the comparism of all the frequencies obtained.
The Grade_IF model demonstrates higher sensitivity and aggressive detection by flagging more high-anomaly cases, indicating a tendency to capture a broader range of potential threats, including borderline ones. In contrast, the AE_LGBM_Grade model adopts a more balanced and cautious approach, distributing grades more evenly across the spectrum, which suggests an emphasis on precision and measured classification. Meanwhile, the IF_Grade model is the most conservative, predominantly labeling transactions as normal or near-normal, effectively minimizing false alarms but increasing the risk of overlooking true anomalies. This variability in grading behavior underscores the inherent trade-offs between sensitivity and specificity in anomaly detection, a crucial consideration in real-time, edge-based financial monitoring systems where detection accuracy and efficiency must be carefully balanced.
5.2. Results at Fog
Hybrid Ensemble:
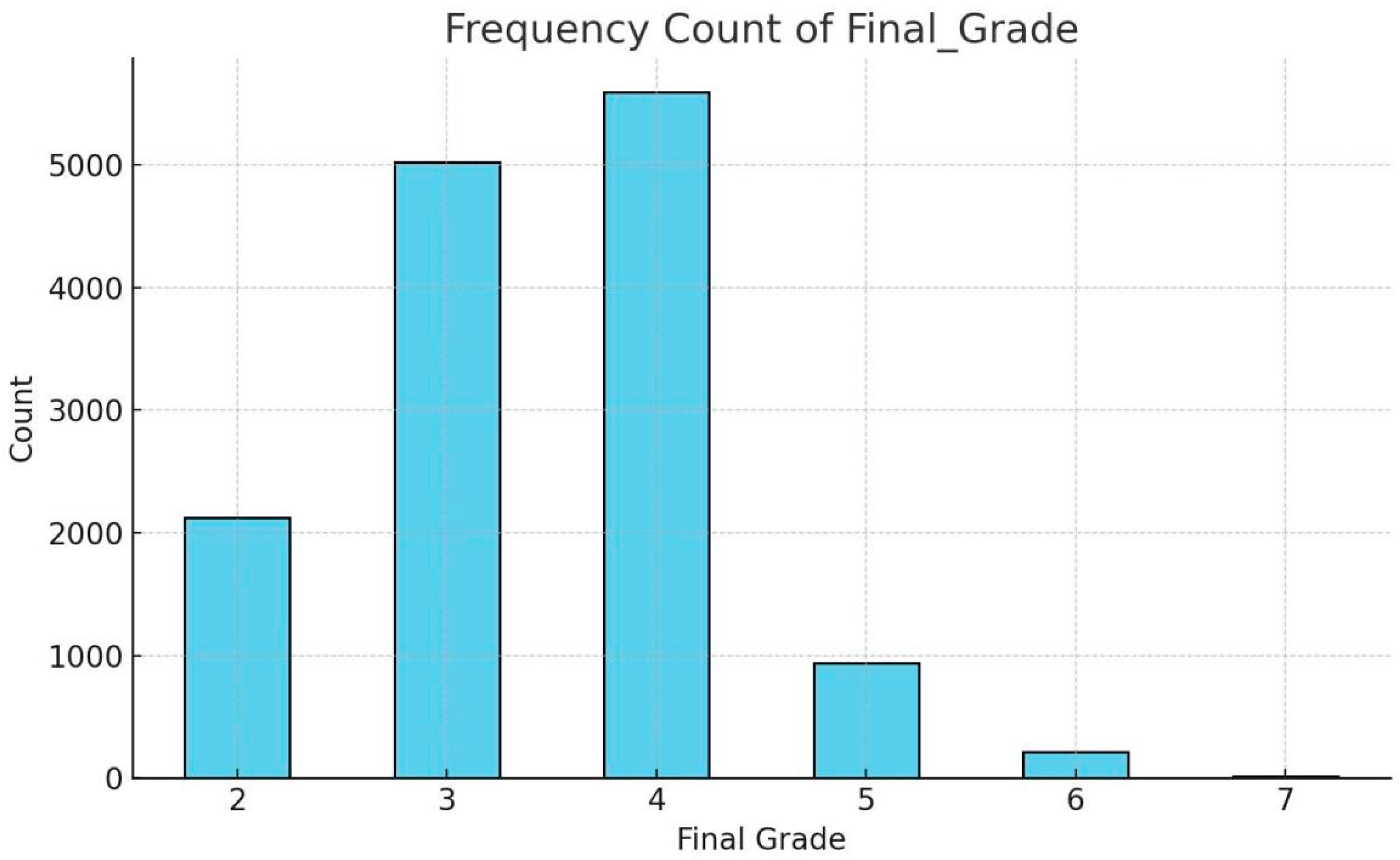
Figure 4 shows the frequency distribution of all final grades obtained from combining all the three (3) multiple grades by the hybrid ensemble:
With a mean of 3.44 (rounded from 3.436), it can be inferred that most data points fall within the "normal" to "borderline" anomaly range.
The distribution of the Final_Grade reveals a strong concentration in the mid-range scores, with grades 3 (5,019) and 4 (5,593) making up the majority, suggesting that most observations are either near normal or borderline anomalous. Grade 2 (2,123) also represents a sizable portion, indicating a significant share of highly normal behavior. In contrast, higher anomaly grades—5 (935), 6 (217), and especially 7 (19)—are much less frequent, implying that strongly suspicious or anomalous patterns are relatively rare. The overall mean of 3.44 further supports that the dataset skews toward normalcy with occasional suspicious behavior, aligning with a typical anomaly detection system designed to prioritize precision and minimize false positives.
5.3. Merged Result
SVM detected 1062 anomalies from the Full_Graded above. When merged with the 1171 confirmed anomalies (with grades from 5 to 7), the total anomalies detected will be:
Based on this, the performance metrics of the proposed model were computed in
Table 7.
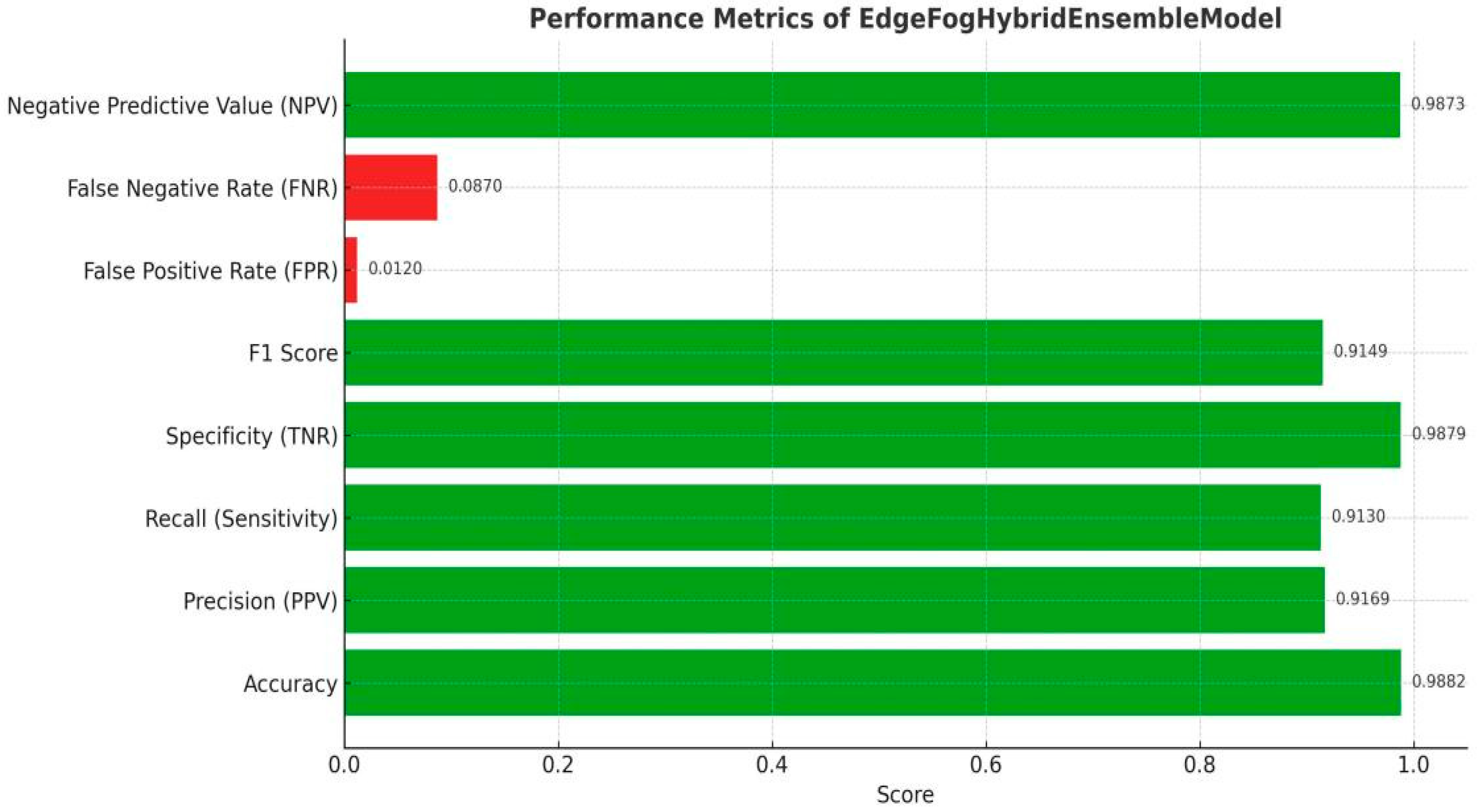
Table 7 and
Figure 5 illustrates the performance metrics of the proposed model. The EdgeFogHybridEnsembleModel (EPHEADMO) demonstrates exceptional performance across all critical classification metrics. With a high accuracy of 98.82%, it effectively distinguishes between normal and anomalous instances. Its precision (91.69%) and recall (91.30%) indicate a strong ability to both correctly identify anomalies and minimize false alarms. A F1 score of 91.49% confirms a robust balance between precision and recall. Notably, the specificity (98.79%) and negative predictive value (98.73%) affirm the model’s reliability in recognizing normal behavior. Furthermore, the low false positive rate (1.2%) and false negative rate (8.7%) underscore its efficiency in minimizing misclassifications. Overall, the model exhibits a well-rounded and dependable anomaly detection capability suitable for high-stakes environments.
5.4. Evaluation of Results
To rigorously assess the effectiveness of the proposed Edge–Fog collaborative anomaly detection framework, a comparative evaluation was conducted using the same financial transaction dataset. Multiple baseline models—namely Autoencoder, Isolation Forest (IF), One-Class SVM (SVM), and Local Outlier Factor (LOF)—were individually applied to detect anomalies, and their outputs were cross-analyzed against the results generated by the proposed hybrid architecture. The evaluation focused on key performance metrics commonly used in anomaly detection tasks: Specificity, Sensitivity, Accuracy, False Negative Rate (FNR), and False Positive Rate (FPR). This comparison provided a comprehensive understanding of each model’s strengths and limitations, particularly in terms of balancing precision and recall in high-volume, edge-generated financial transaction environments.
Metric Meaning
Specificity: Ability to correctly identify normal (non-anomalous) samples.
Sensitivity: Ability to correctly identify anomalies.
Accuracy: Overall correct predictions (anomalies + normals).
FNR: Proportion of actual anomalies incorrectly classified as normal.
FPR Proportion of normal data incorrectly classified as anomalies.
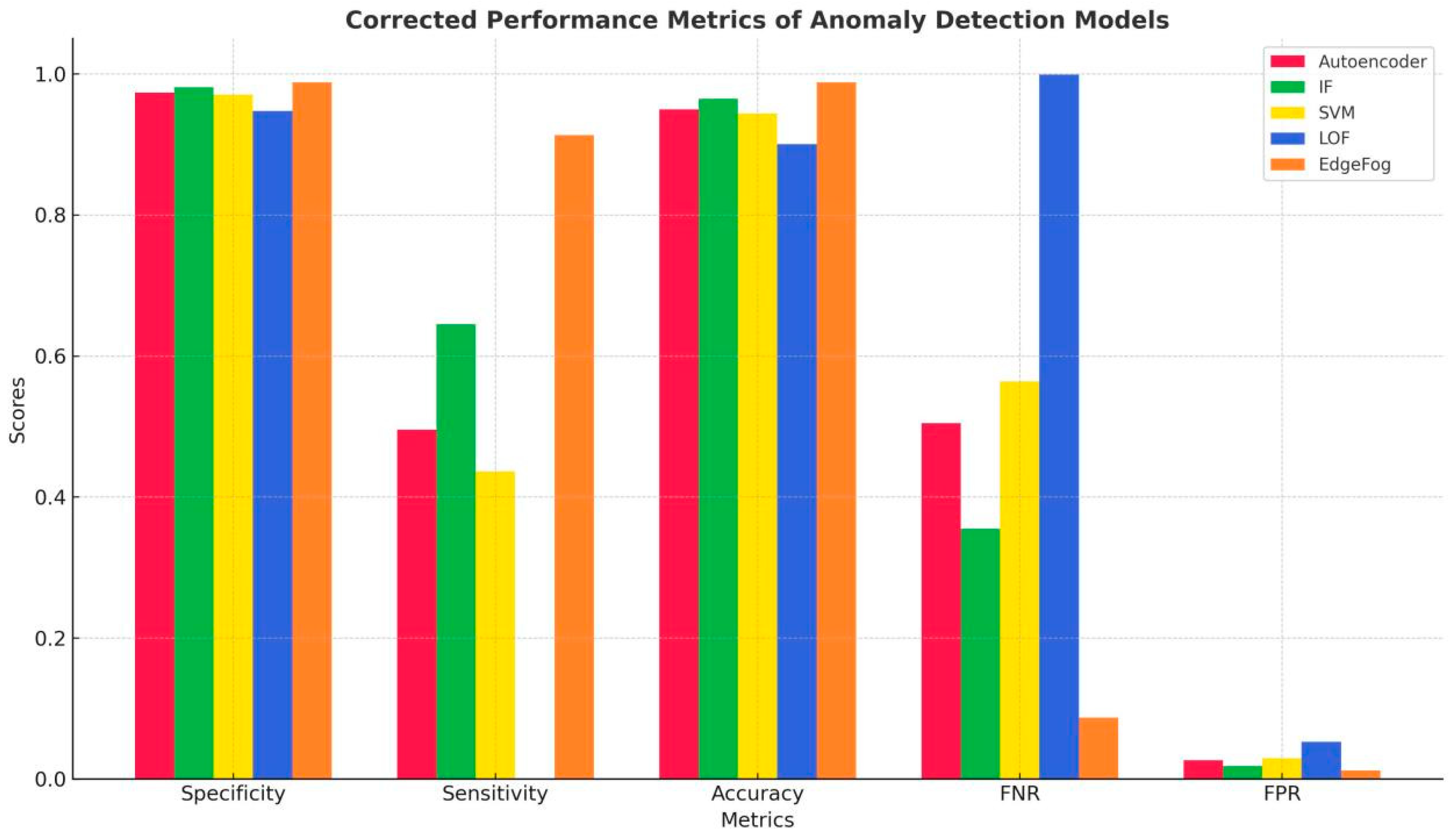
Table 8 below presents the computed result for each algorithm.
Figure 6 illustrates the comparative performance of five anomaly detection models—Autoencoder, Isolation Forest (IF), SVM, LOF, and Edge Fog Hybrid Ensemble Anomaly Detection Model (EPHEADMO)—across five key metrics: Specificity, Sensitivity, Accuracy, False Negative Rate (FNR), and False Positive Rate (FPR). EdgeFog emerges as the most effective anomaly detection model, outperforming all others across critical metrics. With a specificity of 98.79% and a sensitivity of 91.30%, it reliably detects true anomalies while minimizing false positives. Its high accuracy (98.82%) and low error rates—FNR (8.7%) and FPR (1.2%)—underline its robustness and consistency. Isolation Forest (IF) ranks second, offering a solid balance between detection power (sensitivity 64.5%) and precision (specificity 98.11%), making it a strong traditional alternative. In contrast, Autoencoder and SVM deliver reasonable accuracy and specificity but fall short in anomaly detection, with sensitivities below 50%, meaning they miss more than half of actual anomalies. LOF, with a sensitivity of just 0.12%, fails to detect outliers effectively, despite decent specificity. Overall, the chart reinforces EdgeFog's superiority in delivering both precision and recall, making it the most suitable for high-stakes anomaly detection scenarios where minimizing both missed detections and false alarms is critical.
6. Conclusions and Future Work
This study presented a robust, scalable, and real-time Edge–Fog Collaborative Intelligence Framework for financial anomaly detection in smart cities. The proposed architecture integrates unsupervised learning (Autoencoders, Isolation Forest), statistical post-processing (Gaussian scaling), and supervised refinement (One-Class SVM) across a multi-tiered infrastructure to identify suspicious financial activities with high accuracy. The edge layer enables localized, context-aware grading of transactions, while the fog layer performs confirmatory anomaly detection using device-level metadata, effectively reducing false negatives and ensuring prompt escalation of verified threats. Experimental evaluations demonstrated the superiority of the proposed hybrid model over traditional standalone algorithms. Compared to Autoencoder (FNR = 50.44%) and SVM (FNR = 56.38%), the edge–fog model significantly reduced the false negative rate to 8.70%, with an overall accuracy of 98.82%, sensitivity of 91.30%, and specificity of 98.79%. This confirms the utility of combining peer-aware classification at the edge with ensemble learning and supervised filtering at the fog layer to enhance anomaly detection in dynamic, high-volume transaction environments.
Future Work
Building on these promising results, several avenues remain open for further research:
Federated Learning Integration: Future iterations of the framework could integrate federated learning to ensure model privacy and compliance across geo-distributed smart cities without transferring raw data to central fog nodes.
Temporal and Sequential Modeling: Incorporating sequence-aware models such as LSTM or Transformer-based autoencoders can help detect temporal fraud patterns and layering activities over time.
Geospatial and Behavioral Enrichment: Adding geolocation, device mobility, and behavioral profiling features can enhance contextual accuracy, especially in detecting device impersonation or fraud rings.
Cross-Domain Adaptability: Testing and adapting the system in other anomaly-prone smart city domains such as energy, e-health, or transportation can validate the generalizability of the edge–fog hybrid framework.
Real-World Deployment: Future implementations will explore on-device deployment of lightweight autoencoders and real-time reporting in edge-optimized hardware such as Raspberry Pi or IoT microcontrollers.
In conclusion, this research contributes a novel, multi-layered, hybrid machine learning architecture that addresses critical challenges in smart city financial anomaly detection—balancing precision, responsiveness, and interpretability across a distributed computing paradigm.
References
- Park, S.; Sankaran, R.; Beckman, P.; Shahkarami, S.; Kim, Y.; Ferrier, N. Goal-driven scheduling model in edge computing for smart city applications. J. Parallel Distrib. Comput. 2022, 167, 97–108. [Google Scholar] [CrossRef]
- Chi, X.; Meng, S.; Ding, S.; Yan, C.; Yang, Y.; Liu, Y.; Ma, R. Fast wireless sensor for anomaly detection based on data stream in an edge-computing-enabled smart greenhouse. Digit. Commun. Networks 2022, 8, 498–507. [Google Scholar] [CrossRef]
- Rahim, M.S.M.; Suaib, N.M.; Waheed, S.R.; Adnan, M.M.; Salim, A.A.; A Kadhim, K.; Sakran, A.A.; Najjar, F.H. Design a Crime Detection System based Fog Computing and IoT. Malays. J. Fundam. Appl. Sci. 2023, 19, 345–354. [Google Scholar] [CrossRef]
- Wali, G.; Bulla, C. Anomaly Detection in Fog Computing: State-of-the-Art Techniques, Applications, Challenges, and Future Directions. Library Progress International 2024, 44, 13967–13993. [Google Scholar]
- Akbar, A.; Ibrar, M.; Wang, L.; Shah, N.; Muntean, G.-M.; Rottenstreich, O. Reliability-Aware Flow Distribution Algorithm in SDN-Enabled Fog Computing for Smart Cities. IEEE Trans. Veh. Technol. 2022, 72, 573–588. [Google Scholar] [CrossRef]
- Vo, T.; Dave, P.; Bajpai, G.; Kashef, R. Edge, Fog, and Cloud Computing: An Overview on Challenges and Applications. arXiv 2022, arXiv:2211.01863v1. [Google Scholar]
- Farooqi, A.M.; Alam, M.A.; Hassan, S.I.; Idrees, S.M. A Fog Computing Model for VANET to Reduce Latency and Delay Using 5G Network in Smart City Transportation. Appl. Sci. 2022, 12, 2083. [Google Scholar] [CrossRef]
- Jain, S.; Sreelakshmi, K.K.; Gupta, S.; Rodrigues, J.J.P.C. Fog computing in enabling 5G-driven emerging technologies for development of sustainable smart city infrastructures. Clust. Comput. 2022, 25, 1111–1154. [Google Scholar] [CrossRef]
- John, B. (2025). Deep Learning-Based Model for Detecting Suspicious Bank Transactions Leveraging Fog Computing Infrastructure. ResearchGate.
- Chen, J.I.Z.; Lai, K.-L. Development of Smart Cities with Fog Computing and Internet of Things. J. Ubiquitous Comput. Commun. Technol. 2021, 3, 52–60. [Google Scholar] [CrossRef]
- Bawa, S.; Prakash, V.; Garg, L.; Savaglio, C.; Williams, A. Cloud and Edge Computing-Based Computer Forensics: Challenges and Open Problems. Electronics 2021, 10, 1229. [Google Scholar] [CrossRef]
- Al Smadi, A.; Alsmadi, M.K.; Alshabanah, M.; Alrajhi, D.; Aloglah, R.M.A.; Abu-Darwish, N.J.S.; Alkhaldi, H.; Alsmadi, A.M. Fog computing scheduling algorithm for smart city. Int. J. Electr. Comput. Eng. (IJECE) 2021, 11, 2219–2228. [Google Scholar] [CrossRef]
- Adeyeye, O.J.; Williams, M.; Emeteveke, I.; Emehin, O. Enhancing Data Forensics through Edge Computing in IoT Environments. Int. J. Res. Publ. Rev. 2024, 5, 2970–2985. [Google Scholar] [CrossRef]
- Rahimi, M.; Songhorabadi, M.; Kashani, M.H.; MoghadamFarid, A. Fog computing approaches in IoT-enabled smart cities. J. Netw. Comput. Appl. 2022, 211. [Google Scholar] [CrossRef]
- Delicato, F.C.; Batista, T.; Pires, P.F.; Lopes, F.; Da Rocha, A.R.; Neto, A.R.; Da Silva, T.P. Fog Computing Platforms for Smart City Applications: A Survey. ACM Trans. Internet Technol. 2021, 22, 1–32. [Google Scholar] [CrossRef]
- Riaz, A.H.; Khan, D.; Khan, S.; Amer, M.; Aburukba, R.; Al-Ali, A.R.; Al Nabulsi, A. Fog Computing Approach for Shared Mobility in Smart Cities. Energies 2021, 14, 8174. [Google Scholar] [CrossRef]
- John, B. (2025). Intelligent Suspicious Activity Detection in Banking Transactions Utilizing Fog Computing and Deep Learning. ResearchGate.
- Alserhani, F.; Shaheen, M.; Alsirhani, A.; Humayun, M.; Tariq, N. A fog-edge-enabled intrusion detection system for smart grids. J. Cloud Comput. 2024, 13, 1–34. [Google Scholar] [CrossRef]
- Malik, S.; Gupta, K. Smart City: A new phase of sustainable development using fog computing and IoT. IOP Conference Series: Materials Science and Engineering 2021, 1022, 012093. [Google Scholar] [CrossRef]
- Ometov, A.; Nurmi, J.; Molua, O.L.; Komarov, M. A Survey of Security in Cloud, Edge, and Fog Computing. Sensors 2022, 22, 927. [Google Scholar] [CrossRef] [PubMed]
- Thakker, D.; Awan, I.; Tukur, Y.M. Edge-based blockchain enabled anomaly detection for insider attack prevention in Internet of Things. Trans. Emerg. Telecommun. Technol. 2020, 32. [Google Scholar] [CrossRef]
- Trigka, M.; Dritsas, E. Edge and Cloud Computing in Smart Cities. Futur. Internet 2025, 17, 118. [Google Scholar] [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).