1. Introduction
The European Union has historically prioritized cybersecurity concerns, with the objective of safeguarding its member states and extending this protection beyond its borders. This commitment is evidenced by the issuance of directives such as NIS 1 [
1] and NIS 2 [
2], and the establishment of a specialized agency, the European Union Agency for Cybersecurity (ENISA [
3]), which was created to address cybersecurity concerns within the European Union.
In December 2024, the Cybersecurity Agency published the inaugural report [
4] assessing the state of cybersecurity in the different member states. This report was intended to provide reliable information for policy making by the competent bodies of each member state. It is evident that reliable sources of information capable of contributing to their further protection are scarce.
The availability of public datasets that comprehensively document cyberattacks experienced over time remains constrained. Notable exceptions are represented by the datasets from the Center for International and Security Studies at Maryland [
5] and the European Repository of Cyber Incidents (EuRepoC [
6]).
This research utilizes research hypotheses to examine the existence of relationships between the collected data and the conclusions that can be drawn from it, with the objective of further contributing to the formulation of security policies in the future.
The utilization of the chi-square test [
7] is deemed appropriate, as it is a widely used statistical method for examining the relationships between categorical variables.
The objective of the present research study is to examine the existence, or absence, of relationships between the type of actors and the type of cyber incidents, as well as between industry sectors and type of cyber incidents.
2. Materials and Methods
2.1. Basic Terms
The ENISA Directive [
8] (2019/881) delineates its objectives, tasks, and organizational arrangements. The NIS1 Directive (2016/1148) and the NIS2 Directive (2022/2555) further elaborate various definitions. Among these directives, the following definitions merit particular attention:
Cybersecurity: “means the activities necessary to protect network and information systems, the users of such systems, and other persons affected by cyber threats”.
Incident: “means an event compromising the availability, authenticity, integrity or confidentiality of stored, transmitted or processed data or of the services offered by, or accessible via, network and information systems”.
Cyber threat: “means any potential circumstance, event or action that could damage, disrupt or otherwise adversely impact network and information systems, the users of such systems and other persons”.
2.2. NIS360 [9]
In March of 2025, the European Union’s (EU) Agency for Cybersecurity (ENISA) published a report that detailed the findings of the NIS360 methodology. This methodology employs data from National Authorities, companies (in accordance with the NIS2 Directive), and EUROSTAT. The report’s primary objective is to enhance cybersecurity resilience within the following sectors:
Energy
Transport
Finance
Health
Drinking and waste water
Digital infrastructure
ICT service management
Public administrations
Space
The NIS360 methodology is a systematic approach to evaluating the maturity and criticality of various sectors and their sub-sectors. According to the data assessment, the following sectors and sub-sectors fall within the critical risk zone:
ICT Service Management
Space
Public Administration
Maritime
Health
Gas
2.3. NIS2
The NIS2 Directive, a cybersecurity framework, aims to ensure a high level of cybersecurity for Member States. A central tenet of the directive is the facilitation of optimal functionality in networks and information systems. In comparison to its predecessor, the directive has expanded the scope to encompass a more extensive array of sectors.
The directive establishes the following key objectives:
The manage cybersecurity-related risks.
The reporting of cyber incidents.
The minimum compliance with cybersecurity standards.
In the event of noncompliance by the implicated parties, the directive empowers national cybersecurity authorities to proceed with the imposition of sanctions.
A distinguishing feature of the directive is its comprehensive approach to addressing diverse cyber risks, with a primary objective being the uninterrupted delivery of services to citizens of the European Union.
2.4. Cyber Events Database—European Repository of Cyber Incidents (EuRepoC) [10]
The European Repository of Cyber Incidents (EuRepoC) is a comprehensive database designed to document and analyze security incidents affecting entities across various sectors in Europe. The objective of this study is to provide a comprehensive overview of the database’s structure, the types of data it encompasses, and its significance within the broader context of cybersecurity in Europe.
The increasing frequency and sophistication of cyber incidents necessitate meticulous tracking for informed decision-making and policy formation. EuRepoC is an initiative that aims to catalog cyber events to support research and enhance the collective cyber resilience of European nations. The repository’s objective is to compile data encompassing a diversity of attacks, their impact, and the responses instituted.
The database is structured to facilitate efficient data retrieval and analysis through relational processes. The system incorporates numerous fields intended to provide a thorough synopsis of incidents, encompassing, but not limited to, the following:
Incident Description: The text provides a detailed account of the event, offering a comprehensive narrative that captures the essence of the occurrence.
Type of Incident: These threats are classified into various subtypes, including data breaches, ransomware, denial-of-service attacks, and phishing attempts.
Sector Affected: The following sectors have been identified as being impacted by the incident: public, healthcare, finance, and information technology.
Geographical Location: The region or country in which the incident was registered is specified, thereby enabling geographically focused analysis of cyber threats.
Date and Time of Incident: The documentation of the incident is imperative for conducting a trend analysis.
Impact Assessment: The evaluation process is intended to ascertain the consequences of the incident on affected entities. Such consequences may include financial losses and operational disruption.
Mitigation Efforts: The following information is provided for the purpose of elucidating the responses to the incident: updates to security measures, public disclosures, and alterations to policy.
EuRepoC encompasses a wide array of incidents, structured to reflect the evolving threat landscape. The following categories of incidents have been documented:
Malware Attacks: This encompasses a range of malicious software, including viruses, worms, and Trojan horses, which are designed to compromise the integrity of the system.
Phishing Attacks: In the realm of cybersecurity, incidents involving the masquerade of attackers as legitimate entities to obtain sensitive information are of particular concern.
Data Breaches: The phenomenon of events involving unauthorized access to confidential data, which frequently encompasses sensitive personal data, is of particular concern.
Denial-of-Service: The phenomenon of service unavailability, often characterized by an excessive influx of requests directed towards a particular system, is a salient example of this phenomenon.
Insider Threats: Incidents stemming from actions taken by individuals within the organization, whether intentionally or not, that result in harm.
The repository fulfills several pivotal functions, including:
Data-Driven Insights: EuRepoC plays a pivotal role in this endeavor by aggregating diverse incident data, thereby facilitating research into patterns and trends within the cybersecurity landscape in Europe.
Policy Formulation: is the process of establishing guidelines and regulations for the governance of an organization, institution, or system. It is evident that policymakers have the capacity to employ the findings from EuRepoC in order to formulate regulations that are intended to fortify cyber defenses on a sector-wide basis.
Security Awareness: Organizations can utilize this database to assess their vulnerability to prevalent cyber threats, facilitating the implementation of proactive rather than reactive strategies.
International Collaboration: EuRepoC, a European-centered initiative, fosters collaboration and information sharing among member states, ultimately enhancing collective cybersecurity measures.
The European Repository of Cyber Incidents signifies a substantial advancement in the realm of understanding and responding to cyber threats within the European continent. EuRepoC facilitates this process by consolidating extensive data on incidents across various sectors and countries. This consolidation enables individual organizations to enhance their cybersecurity postures and contributes to the development of strategies at the national and European levels. The continued evolution of this repository is imperative, as it must align with the rapidly changing cybersecurity landscape and emerging technologies.
2.5. Cyber Events Database—University of Maryland [11,12,13]
The Cyber Events Database, which is hosted on the Critical Infrastructure Security and Resilience (CISR) website operated by the University of Maryland, functions as a comprehensive repository of notable cyber incidents. This database has been developed for the use of researchers, policymakers, and cybersecurity professionals, providing detailed information on major cyber events and attacks that have occurred on a global scale. The subsequent discussion will elucidate the salient features and insights derived from this database.
This dataset provides a detailed account of a structured framework for logging incidents of cybersecurity breaches, employing a consistent categorical format. The employment of variables that delineate event dates, actors, organization types, tactics, motives, and the impacts of such breaches engenders a robust reporting mechanism to track these incidents comprehensively.
In an era of increasing digitalization, cybersecurity breaches have the potential to have far-reaching consequences. A comprehensive understanding of the nature of these incidents, the actors involved, and their motives is imperative for the development of effective strategies for prevention and response. This dataset delineates the specific variables indispensable for reporting and analyzing cybersecurity events, emphasizing the significance of standardization in data collection.
The structure of the dataset can be described as follows:
Event Date and Year
Event Date (event_date): This variable captures the specific date of the event occurrence in the DD-MM-YYYY format. For estimated dates, the first day of the month is recorded.
Year (year): This captures the year the event occurred in the YYYY format.
Actors Involved
Actor (actor): An identification string representing the individual or organization responsible for the event. If unknown, the entry shall be noted as “undetermined”.
Actor Type (actor_type): This variable indicates the nature of the actor:
Criminal: Organizations engaging in illicit activities for financial profit.
Nation-State: Entities affiliated with government bodies or militaries.
Terrorist: Non-state actors employing violence or intimidation for political objectives.
Hacktivist: Groups or individuals conducting cyber-attacks for political or social causes.
Hobbyist: Individuals acting out of curiosity or interest rather than for financial gain.
Target Organization Details
Organization (organization): This string variable specifies the name of the organization affected by the breach.
North American Industry Classification System (NAICS) Code (industry_code): A two-digit code categorizing the industry of the impacted organization.
Industry Name (industry): This field presents the name correlating to the NAICS category.
Motives of the Actors
Motive (motive): This categorical variable defines the objectives of the attacking agent:
Protest: Activities aimed at causing service disruptions to convey political messages.
Sabotage: Actions leading to the irreversible destruction of information or networks.
Espionage: The act of improperly accessing networks to acquire intelligence.
Financial: The exfiltration of sensitive data for economic gain.
Event Type Classification
Event Type (event_type): Indicating the primary end effects of the incident, this can be:
Disruptive: Events that disrupt normal operations.
Exploitive: Events that entail stealing sensitive information.
Mixed: Uniting both disruptive and exploitative elements, exemplified by ransomware attacks.
Event Sub-Types
The classification of events can be further detailed into specific sub-types, categorized as either disruptive or exploitive incidents:
Disruptive Events:
Message Manipulation: Tampering with organizational messages, affecting communication accuracy.
External Denial of Services: Attacks executed from external networks to halt communication.
Internal Denial of Services: Disruptions instigated from within the organization’s infrastructure.
Data Attack: Actions aimed at damaging, encrypting, or manipulating data.
Physical Attack: Direct manipulation of IT components affecting physical systems.
Exploitive Events:
Exploitation of Sensors: Data theft from peripheral devices.
Exploitation of End Host: Information theft from individual user devices.
Exploitation of Network Infrastructure: Theft accomplished via direct access to network devices.
Exploitation of Application Server: Gaining access to data through application vulnerabilities.
Exploitation of Data in Transit: Theft of information while in transit between devices.
2.6. Methodology
As previously stated, the present research study investigates the presence or absence of relationships between:
Research Questions:
RQ1 A correlation has been observed between the type of actor and the type of cyber incident.
RQ2 The industry sector has been found to be correlated with the type of cyber incident.
The University of Maryland’s Cyber Events database is a suitable dataset for this investigation, as it is capable of contributing to the study of our research questions. The database under consideration contains more than 14,000 cyberattack incidents, spanning the period from 2014 to 2024. Among the variables examined, three were identified as the most pertinent to the research interests under investigation. In the context of this study, the following variables are of particular relevance:
Actor Type (actor_type):
Criminal
Nation-State
Terrorist
Hacktivist
Hobbyist
Event Type (event_type):
Disruptive
Exploitive
Mixed
Industry Name (industry)
3. Results
Based on the above, the results are as follows:
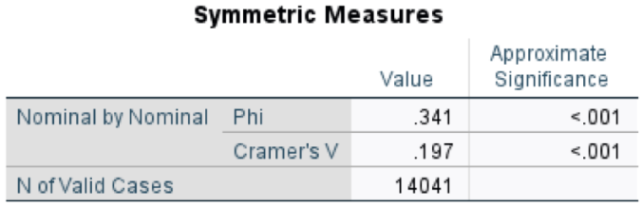
RQ1: A correlation has been observed between the type of actor and the type of cyber incident
The null hypothesis (H0) and the alternative hypothesis (H1) of the chi-square independence test are formulated as follows for the pair of variables (actor_type, event_type):
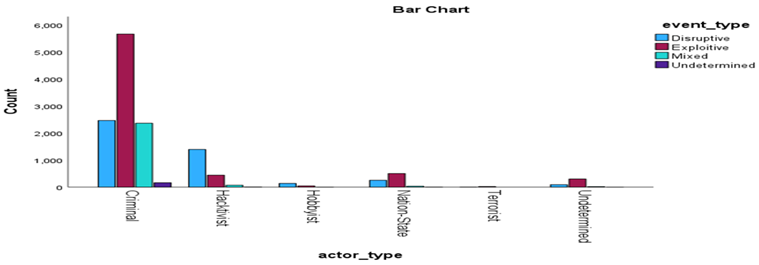
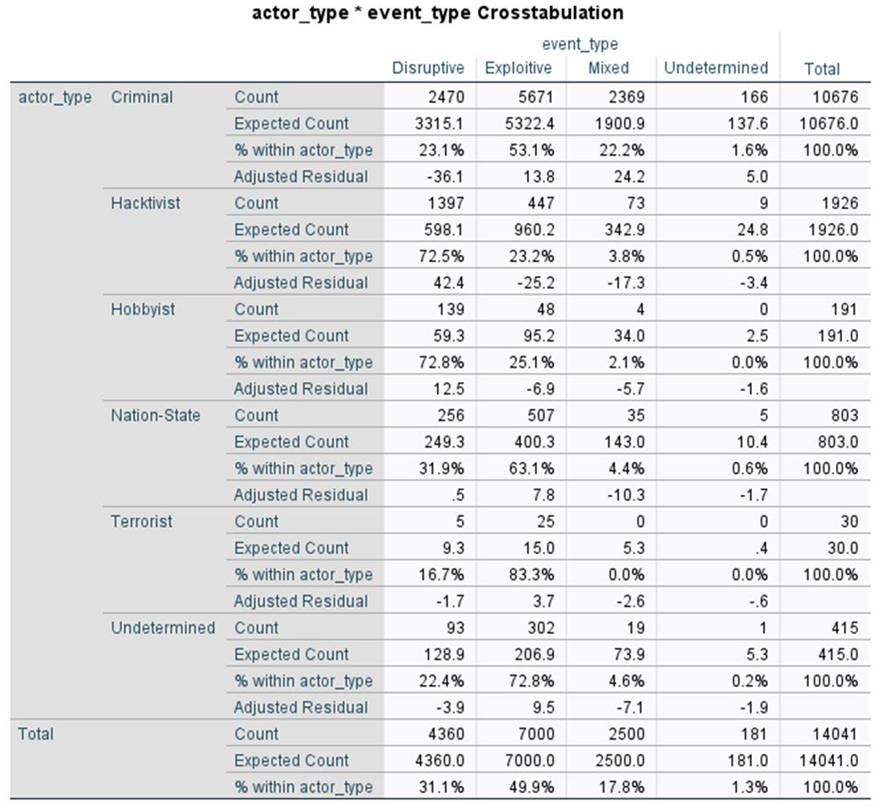
Our first research question was examined using the chi-square test. The categorical variables employed in this study included actor type and event type. Both are nominal variables and include the categories presented above. The following contingency table enumerates the observations that fall into each combination.
The chi-square test yielded a statistic of χ² = 2308.371 with 15 degrees of freedom (df = 15), p < 0.001. This finding suggests the presence of a statistically significant correlation between the variables under study.
| Symmetric Measures |
| |
Value |
Approximate Significance |
| Nominal by Nominal |
Phi |
.405 |
<.001 |
| Cramer’s V |
.234 |
<.001 |
| N of Valid Cases |
14041 |
|
Furthermore, all of the test criteria were met. Specifically, the following conditions were satisfied:
The expected cell frequencies all met the required conditions (80% of the cells are greater than or equal to 5).
The categories of the categorical variables are more than two.
The sample size is large.
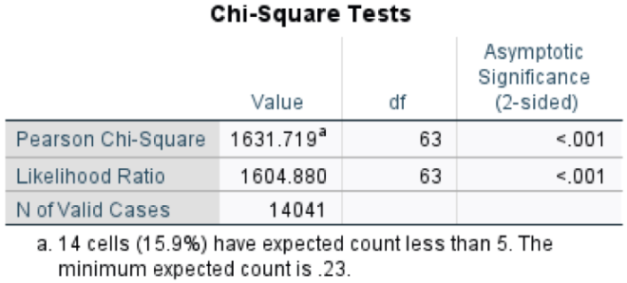
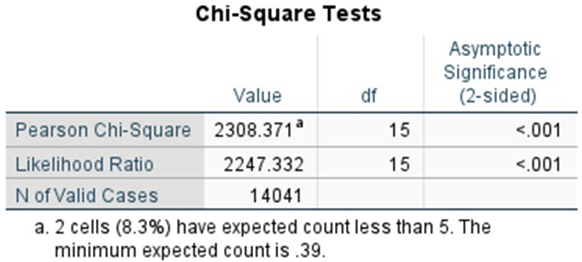
RQ2: The industry sector has been found to be correlated with the type of cyber incident
The null hypothesis (H0) and the alternative hypothesis (H1) of the chi-square independence test are formulated as follows for the pair of variables (industry, event_type):
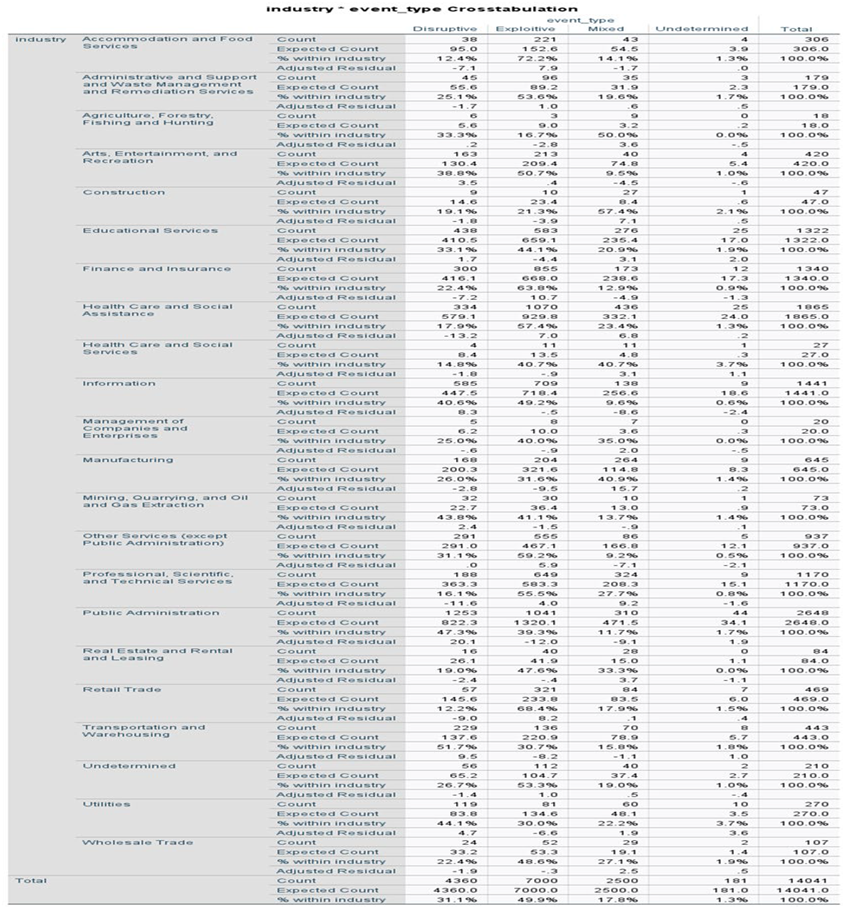
Our second research question was examined using the chi-square test. The categorical variables employed in this study included industry and event type. Both are nominal variables and include the categories presented above. The following contingency table enumerates the observations that fall into each combination.
The chi-square test yielded a statistic of χ² = 1631.719 with 63 degrees of freedom (df = 63), p < 0.001. This finding suggests the presence of a statistically significant correlation between the variables under study.
Furthermore, all of the test criteria were met. Specifically, the following conditions were satisfied:
The expected cell frequencies all met the required conditions (80% of the cells are greater than or equal to 5).
The categories of the categorical variables are more than two.
The sample size is large.
4. Discussion
The cybersecurity landscape in the European Union is marked by a mounting cognizance of the perils engendered by cyber incidents, as substantiated by the establishment of comprehensive frameworks by directives such as NIS1 and NIS2, in conjunction with the inauguration of pivotal data repositories including the European Repository of Cyber Incidents (EuRepoC) and the Cyber Events Database from the University of Maryland. These frameworks and databases serve as pivotal tools for understanding the dynamics between the types of actors engaged in cyber activities and the nature of incidents they perpetrate, as noted through research findings. Specifically, the results of the chi-square tests indicated robust correlations between the types of actors and cyber incidents (RQ1) and between industry sectors and the incidents (RQ2). These findings served to validate the initial research hypotheses [
14].
The substantial correlation between actor types and incident types corroborates extant literature suggesting that particular actors are more prone to perpetrate specific types of cyber incidents. For instance, nation-state actors are typically attributed to sophisticated espionage-related cyber incidents, while criminal actors often exploit financial vulnerabilities [
15]. The aforementioned patterns underscore the considerable heterogeneity within the actor landscape. Consequently, it is imperative that tailored cybersecurity strategies be formulated that account for the motives and capabilities of these different actors [
16].
Furthermore, an analysis of the relationships between various industry sectors and their susceptibility to distinct types of cyber incidents reveals that critical sectors, such as healthcare and public administration, are especially vulnerable [
17,
18]. The implications of these findings are significant, as they underscore the necessity of conducting sector-specific risk assessments. Reports have emphasized the increasing sophistication of cyberattacks on healthcare infrastructures, necessitating a focused approach to the development of cybersecurity policy. Such an approach would need to incorporate lessons learned from the trends observed in the Cyber Events Database and other states’ cybersecurity strategies [
19,
20].
Data-driven insights from repositories such as EuRepoC play a significant role in identifying and analyzing trends within the cybersecurity landscape [
21,
22]. By facilitating the examination of incident contexts—including categorical classifications such as incident type, actor motivations, and operational impacts—these databases enable researchers and policymakers to tailor their responses more effectively. Evidently, data repositories are indispensable for the procurement of immediate operational insights. Moreover, they are integral to the broader formulation of preventive and reactive cybersecurity policies across European sectors.
5. Conclusions
The findings of this research underscore the critical importance of cultivating an informed understanding of the relationships between actor types, incident types, and industry sectors in the evolving realm of cybersecurity. The statistical evidence from the chi-square tests corroborates our hypotheses and supports the narrative that a nuanced understanding of actor motivations and sector vulnerabilities is essential for formulating effective cybersecurity governance mechanisms within the European Union.
In the face of escalating cyber threats, both in terms of frequency and complexity, the importance of comprehensive data repositories such as EuRepoC and the Cyber Events Database cannot be overstated. These tools offer two primary benefits. First, they provide essential insight into the nature of cyber incidents. Second, they enable the creation of targeted, evidence-based policies that can enhance resilience against cyber threats. In the future, the incorporation of empirical data into policy discussions will be essential for ensuring a proactive and adaptable cybersecurity posture across the EU.
The cornerstone of a robust European cybersecurity environment is ultimately formed by continued collaboration among member states, leveraging insights from incident data, and fostering sector-specific security awareness. This will safeguard essential services and public trust across the continent.
References
-
https://eur-lex.europa.eu/eli/dir/2016/1148/oj/eng.
-
https://eur-lex.europa.eu/eli/dir/2022/2555/oj.
-
https://www.enisa.europa.eu/.
-
https://www.enisa.europa.eu/publications/2024-report-on-the-state-of-the-cybersecurity-in-the-union.
-
https://cissm.umd.edu/research-impact/publications/cyber-events-database-home.
-
https://eurepoc.eu/database/.
-
https://libguides.library.kent.edu/spss/chisquare.
-
https://eur-lex.europa.eu/eli/reg/2019/881/oj/eng.
-
https://www.enisa.europa.eu/publications/enisa-nis360-2024.
-
https://eurepoc.eu/.
-
https://cissm.umd.edu/cyber-events-database.
- Harry, C., & Gallagher, N. (2018). Classifying Cyber Events. Journal of Information Warfare, 17(3), 17-31 https://cissm.umd.edu/sites/default/files/2019-07/Cyber-Taxonomy-101918.pdf.
- . [CrossRef]
- Saalman, L., Su, F., & Dovgal, L. (2023). Cyber crossover and its escalatory risks for europe. [CrossRef]
- Stergiopoulos, G., Gritzalis, D., & Limnaios, E. (2020). Cyber-attacks on the oil & gas sector: a survey on incident assessment and attack patterns. Ieee Access, 8, 128440-128475. [CrossRef]
- Renaud, K. and Ophoff, J. (2021). A cyber situational awareness model to predict the implementation of cyber security controls and precautions by smes. Organizational Cybersecurity Journal Practice Process and People, 1(1), 24-46. [CrossRef]
- Raizada, N. and Biswal, M. (2024). An evidence-based investigation of cert-in’s reporting on cyber-threats in healthcare sector. Conhecimento & Diversidade, 16(42), 219-246. [CrossRef]
- Alade, O., Amusan, E., & Ojo, O. (2024). Strategic assessment of intricacies in healthcare cyber security: analyzing distinctive challenges, evaluating their ramifications on healthcare delivery, and proposing advanced mitigation strategies. Asian Journal of Research in Computer Science, 17(5), 238-248. [CrossRef]
- Nasser, M., Ahmad, R., Yassin, W., Hassan, A., Zainal, Z., Salih, N., … & Hameed, K. (2018). Cyber-security incidents: a review cases in cyber-physical systems. International Journal of Advanced Computer Science and Applications, 9(1). [CrossRef]
- Hugyik, A. (2020). Best practices in the application of the concept of resilience: building hybrid warfare and cybersecurity capabilities in the hungarian defense forces. Connections the Quarterly Journal, 19(4), 25-38. [CrossRef]
- Wang, K., Guo, X., & Yang, D. (2022). Research on the effectiveness of cyber security awareness in ics risk assessment frameworks. Electronics, 11(10), 1659. [CrossRef]
- Shevchenko, P., Jang, J., Malavasi, M., Peters, G., Sofronov, G., & Trück, S. (2022). The nature of losses from cyber-related events: risk categories and business sectors. [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).