Submitted:
16 January 2025
Posted:
17 January 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
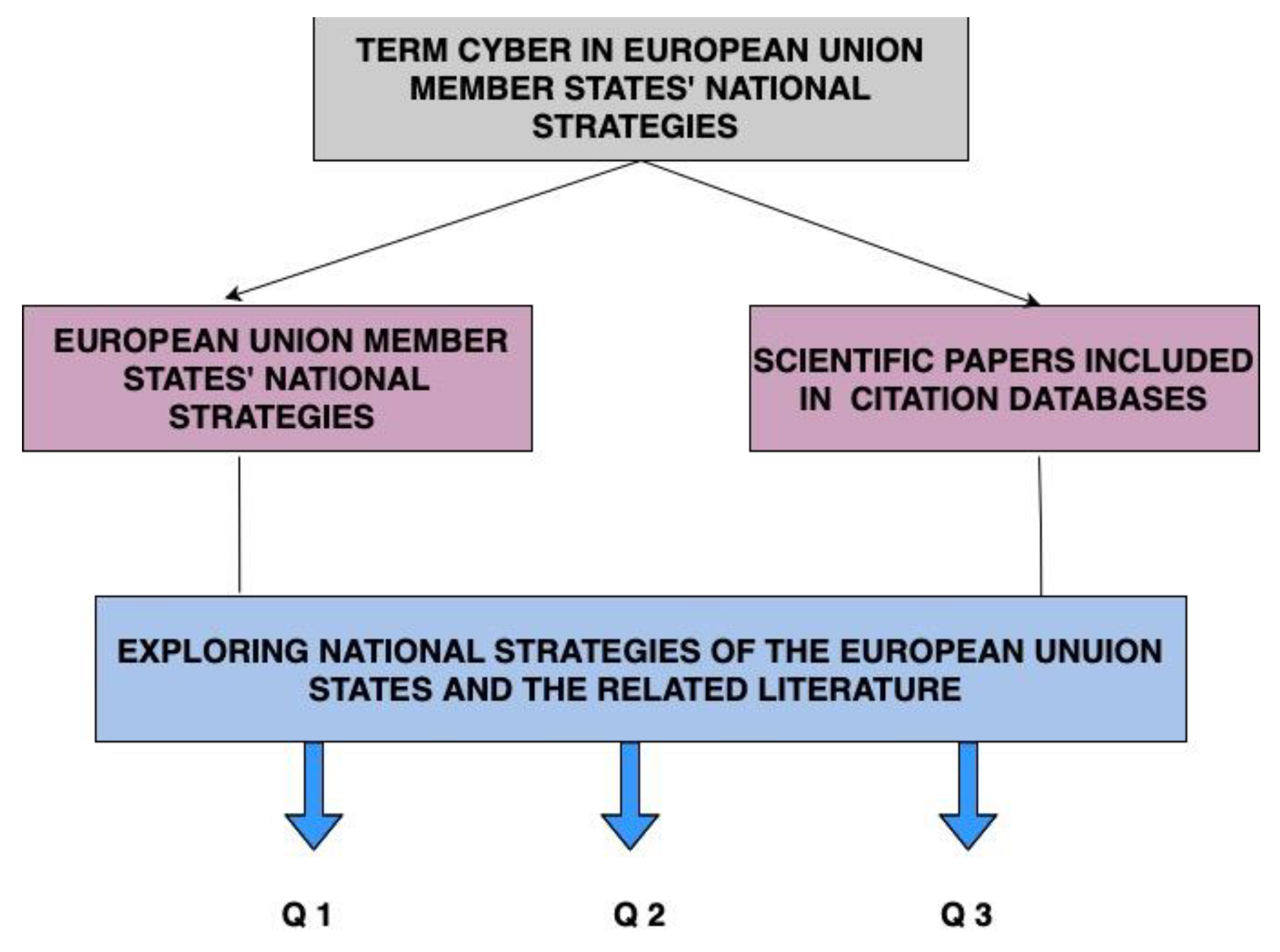
2. Research Methodology
3. Results
3.1. Statistical Analysis of the Occurrence of the Term Cyber in National Security Strategies
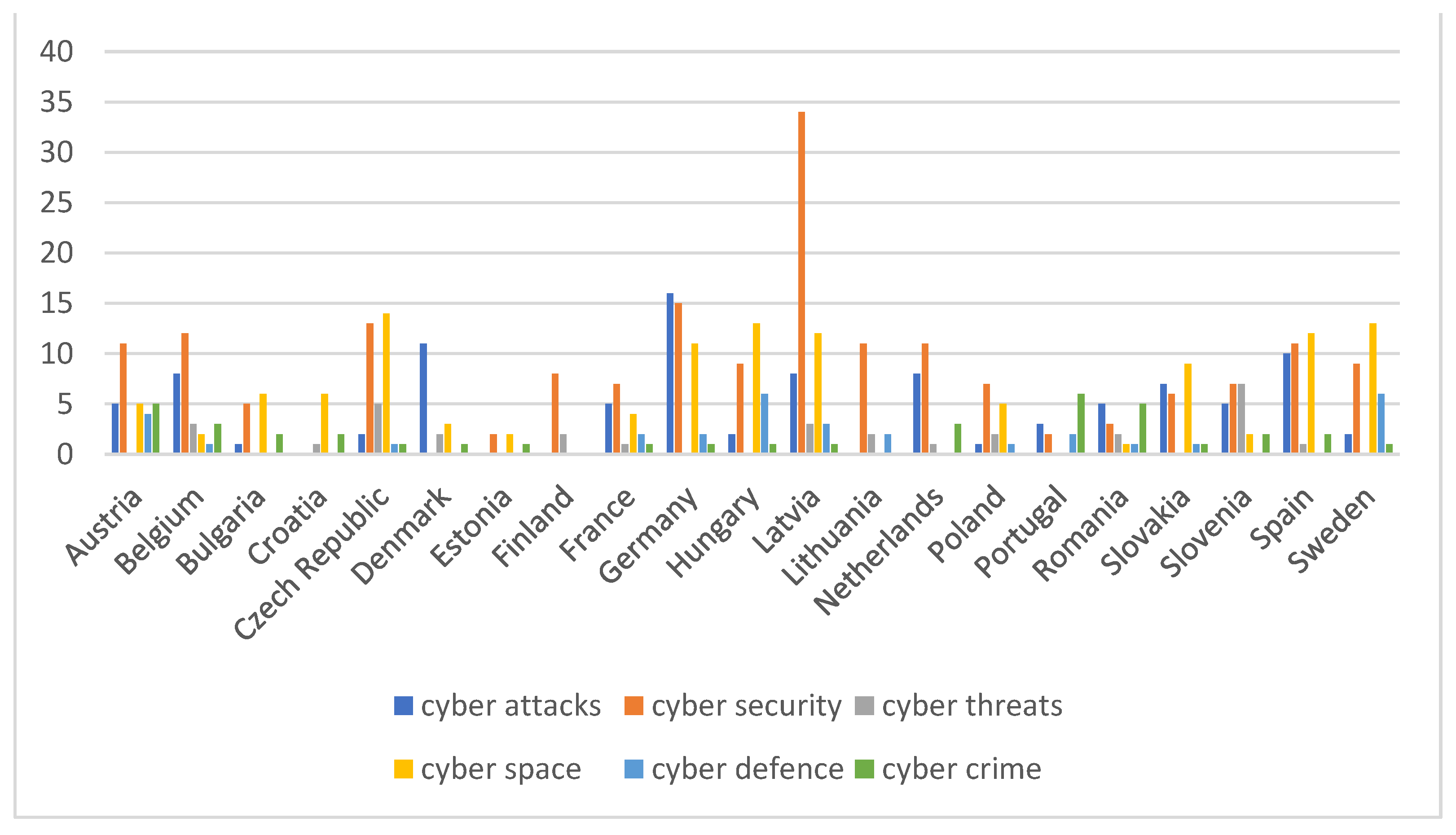
3.2. Statistical Analysis of the Most Mentioned Terms Containing the Term Cyber
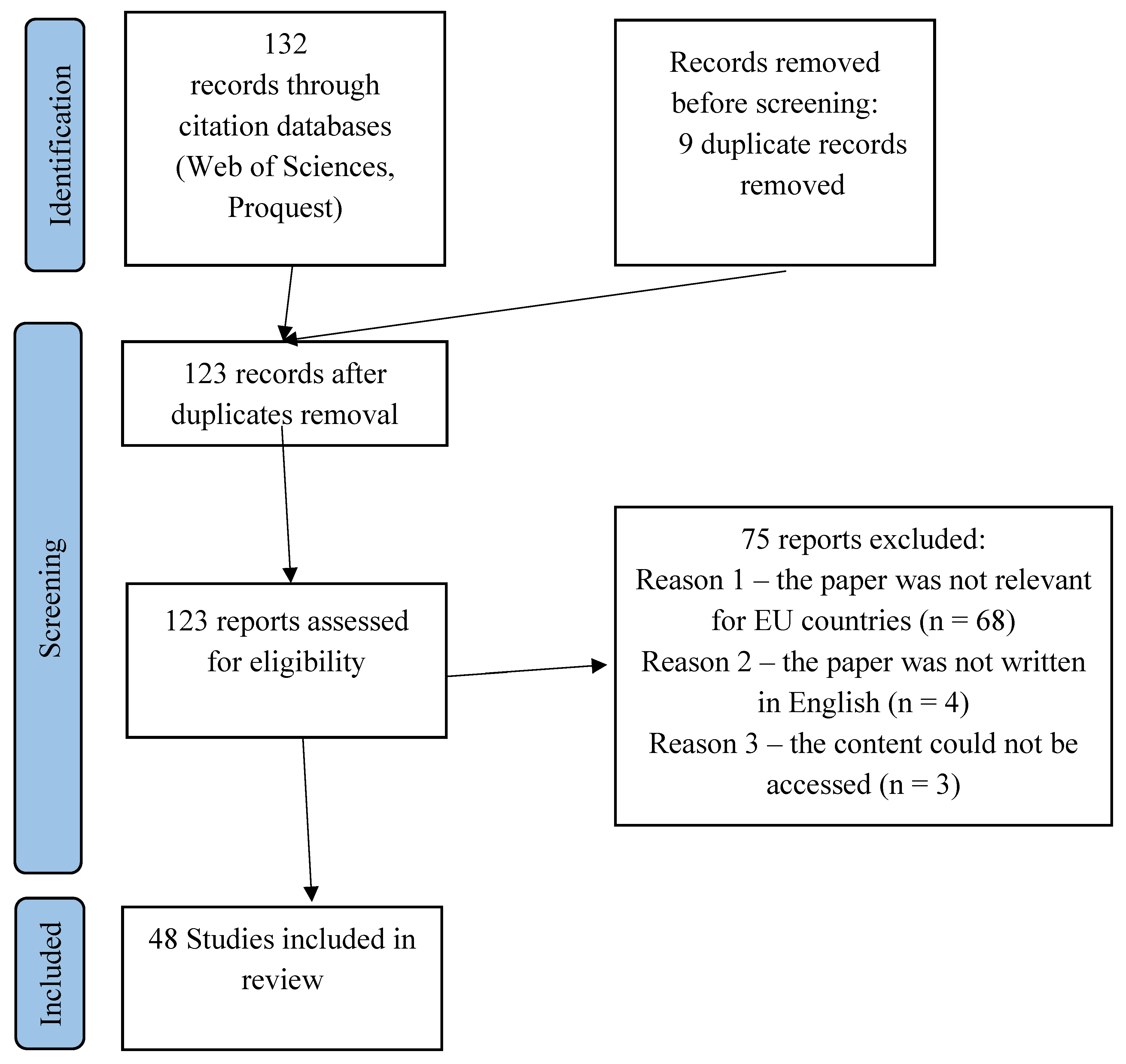
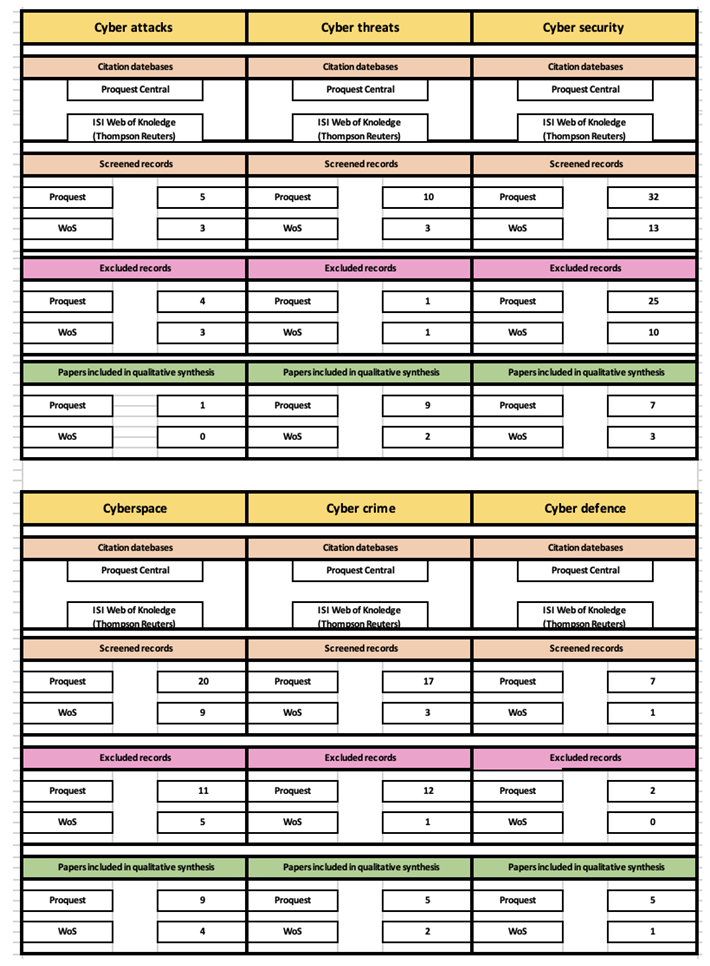
3.3. Systematic Review of Scientific Literature
- a.
- Establishing search criteria in relation to cyber issues
- ”cyber attack” AND ”national security”;
- ”cyberattack” AND ”national security”;
- ”cybers security” AND ”national security”;
- ”cybersecurity” AND ”national security”;
- ”cyber threats” AND ”national security”;
- ”cyberthreats” AND ”national security”;
- ”cyber space” AND ”national security”;
- ”cyberspace” AND ”national security”;
- ”cyber defence” AND ”national security”;
- ”cyberdefence” AND ”national security”;
- ”cyber crime” AND ”national security”;
- ”cybercrime” AND ”national security”.
- b.
- Establishing a preliminary documentation base using the search string
- c.
- Selecting scientific materials considered relevant for content analysis
- d.
- Extracting relevant information
- Cyber threats
- Cyber attacks
- Cyber security
- Cyberspace
- Cyber crime
- Cyber defense
4. Discussion and Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- A. Klimburg, National Cyber Security Framework Manual. în NATO CCDCOE Publication. Tallinn, 2012.
- H. Çifci, „Comparison of National-Level Cybersecurity and Cyber Power Indices: A Conceptual Framework”, 2022.
- Štitilis, D.; Rotomskis, I.; Laurinaitis, M.; Nadvynychnyy, S.; Khorunzhak, N. National cyber security strategies: management, unification and assessment. Indep. J. Manag. Prod. 2020, 11, 2341–2354. [Google Scholar] [CrossRef]
- K. Chałubińska-Jentkiewicz, F. Radoniewicz, și T. Zieliński, Cybersecurity in Poland Legal Aspects. în Warsaw. Springer, 2022.
- Štitilis, D.; Pakutinskas, P.; Laurinaitis, M.; de Castel, I.M.-V. A model for the national cyber security strategy. the lithuanian case. J. Secur. Sustain. Issues 2017, 6. [Google Scholar] [CrossRef] [PubMed]
- Carr, M.; Lesniewska, F. Internet of Things, cybersecurity and governing wicked problems: learning from climate change governance. Int. Relations 2020, 34, 391–412. [Google Scholar] [CrossRef]
- M. D. Cavelty și A. Wenger, Cyber Security Politics Socio-Technological Transformations and Political Fragmentation. Routledge, London, 2022.
- Bolbot, V.; Theotokatos, G.; Boulougouris, E.; Vassalos, D. A novel cyber-risk assessment method for ship systems. Saf. Sci. 2020, 131, 104908. [Google Scholar] [CrossRef]
- Aslan, Ö.; Aktuğ, S.S.; Ozkan-Okay, M.; Yilmaz, A.A.; Akin, E. A Comprehensive Review of Cyber Security Vulnerabilities, Threats, Attacks, and Solutions. Electronics 2023, 12, 1333. [Google Scholar] [CrossRef]
- Lipinsky, D.A.; Bolgova, V.V.; Musatkina, A.A.; Azarkhin, A.V.; Korobova, A.P. General Social Values in National Security Strategies of the Russian Federation and Germany. AD Alta: Journal of Interdisciplinary Research 2019.
- Caudle, S.L.; de Spiegeleire, S. A New Generation of National Security Strategies: Early Findings from the Netherlands and the United Kingdom. 2010, 7. [CrossRef]
- Vogler, A. Barking up the tree wrongly? How national security strategies frame climate and other environmental change as security issues. Political Geography 2023, 105, 102893. [Google Scholar] [CrossRef]
- Mara, D.; Nate, S.; Stavytskyy, A.; Kharlamova, G. The Place of Energy Security in the National Security Framework: An Assessment Approach. Energies 2022, 15. [Google Scholar] [CrossRef]
- Pătrașcu, P. National Security Strategies and Critical Infrastructure: An Analysis of the European Union Member States. Romanian Military Thinking 2022, 2022, 10–29. [Google Scholar] [CrossRef]
- Stefanescu, D.; Papoi, A. NEW threats to the national security of states ⇓ Cyber threat. Scientific Journal of Silesian University of Technology. Series Transport 2020, 107, 177–182. [Google Scholar] [CrossRef]
- Oxford Dictionary. Available online: https://en.oxforddictionaries.com/definition/cyberthreat.
- Jose de Arimateia da Cruz Cyber Mercenaries: A New Threat to National Security. International social science review 2020, 96.
- Manea, S.A. Implications of the evolution of cyber threats on the duties of actors in the field of security and national defense. International Scientific Conference “Strategies XXI”, suppl. Global Security and National Defence 2020, 213–217.
- Dinicu, A. Cyber threats to national security. Specific features and actors involved. Scientific Bulletin - Nicolae Balcescu Land Forces Academy 2014, 19, 109–113. [Google Scholar]
- Bobric, G.-D. Study Regarding the Cyber Threats to the National Security. Scientific Bulletin 2020, 25, 18–25. [Google Scholar] [CrossRef]
- Crossing the Line: The Law of War and Cyber Engagement - Crossing the Line: The Law of War and Cyber Engagement - Applying the Existing Body of Law to This New National Security Applying the Existing Body of Law to This New National Security Threat. The International Lawyer 2018, 51(3), 613–628.
- Grobman, S. Quantum Computing’s Cyber-Threat to National Security. Prism : a Journal of the Center for Complex Operations 2020, 9, 52–66. [Google Scholar]
- Osawa, J. The Escalation of State Sponsored Cyberattack and National Cyber Security Affairs: Is Strategic Cyber Deterrence the Key to Solving the Problem? ASIA-PACIFIC REVIEW 2017, 24, 113–131. [Google Scholar] [CrossRef]
- Haddad, C.; Binder, C. Governing through cybersecurity: national policy strategies, globalized (in-)security and sociotechnical visions of the digital society. Österreichische Zeitschrift für Soziologie 2019, 44, 115–134. [Google Scholar] [CrossRef]
- Peng, S. Digital economy and national security: contextualizing cubersecurity-related exceptions. AJIL UNBOUND 2023, 117, 122–127. [Google Scholar] [CrossRef]
- Petrov, V. Establishing a national cybersecurity system in the context of national security and defence sector reform. Information & Security 2014, 31, 73–77. [Google Scholar] [CrossRef]
- Ivanov, G.R. The cybersecurity of automated control systems as a key conponent of national security. Journal of Defense Resources Management 2016, 7, 91–96. [Google Scholar]
- Eviatar Matania; Yoffe, L.; Mashkautsan, M. A Three-Layer Framework for a Comprehensive National Cyber-security Strategy. Georgetown Journal of International Affairs 2016, 17, 77–84. 2016, 17, 77–84. [CrossRef]
- Štitilis, D.; Pakutinskas, P.; Malinauskaitė, I. EU and NATO cybersecurity strategies and national cyber security strategies: a comparative analysis. Security Journal 2017, 30, 1151–1168. [Google Scholar] [CrossRef]
- Dolzhenkova, E.; Mokhorov, D.; Baranova, T. National and International Issues of Cyber Security. IOP Conference Series: Materials Science and Engineering 2020. [CrossRef]
- R. Piotrowski; J. Sliwa Cyberspace situational awarness in national security system. In Proceedings of the 2015 International Conference on Military Communications and Information Systems (ICMCIS); 2015; pp. 1–6.
- Gilad, A.; Pecht, E.; Tishler, A. Intelligence, Cyberspace, and National Security. Defence and Peace Economics 2021, 32, 18–45. [Google Scholar] [CrossRef]
- Ciekanowski, Z.; Gruchelski, M.; Nowicka, J.; Żurawski, S.; Pauliuchuk, Y. Cyberspace as a Source of New Threats to the Security of the European Union. European Research Studies Journal 2023, XXVI, 782–797. [Google Scholar] [CrossRef]
- Yannakogeorgos, P.; Lowther, A. Conflict and Cooperation in Cyberspace: The Challenge to National Security; 2013;
- Garibaldi, S.; Deane, F. Cyberspace as a fifth dimension of national security: trade measure exceptions. Journal of International Trade Law and Policy 2023, 22, 67–88. [Google Scholar] [CrossRef]
- Moore, M. Development and Implementation of Government Cybersecurity Policies and Practices for National Security and Cybercrime. 2014.
- Petrescu, E.P.; Giusca, F.L. Threats if cybercrime in the field of economic and financial security at national and regional level. International Scientific Conference “Strategies XXI”, suppl. Strategic Changes in Security and International Relations 2018, 3, 150–154. [Google Scholar]
- Apachiţei, I.; Ichim, C. The implications of cybercrime for national security. SHS Web of Conferences 2023, 177. [Google Scholar] [CrossRef]
- Tulvan, A.; Panfil, G. The importance of education related to cyber crimes in the traininf institution dedicated to public order and national secutiry - a case study focused on Romanian Ministry of Internal Affairs.; Roceanu, I., Dubois, D., Moldoveanu, F., Stanescu, I., Beligan, D., Dascalu, M., Barbieru, D., Eds.; 2016; pp. 481–484.
- E. M. Ngwana, „Emerging Paradigms of Cybercrimes, Supply Chain Attacks, and National Security Ramifications”, D.Sc., Marymount University, United States -- Virginia, US, 2022. [Online]. Disponibil la: https://www.proquest.com/dissertations-theses/emerging-paradigms-cybercrimes-supply-chain/docview/2817856379/se-2?accountid=15533.
- Varenia, N.; Avdoshyn, I.; Strelbytska, L.; Strelbytskyy, M.; Palchyk, M. Cybercrime as a threat to Ukreaine’s national security. International Journal of computer science and network security 2021, 21, 73–83. [Google Scholar] [CrossRef]
- Gudu, T. A logic model for the national cyber security / defence strategies? The case of French cuber defence pact. International Scientific Conference “Strategies XXI” 2016, 3, 156–161. [Google Scholar]
- Popa, E.-V. Aspects of national policy to ensure cyber security and defense in France and Germany. International Scientific Conference “Strategies XXI”, suppl. STRATEGIC CHANGES IN SECURITY AND INTERNATIONAL RELATIONS 2018, 3, 155–160. [Google Scholar]
- Kaponig, H. Austria’s National Cyber Security and Defense Policy: Challenges and the Way Forward. Connections : The Quarterly Journal 2020, 19, 21–37. [Google Scholar] [CrossRef]
- Dumitru, D.; Iuhas, G.C. Cyber security - a new dimension of national defense. International Scientific Conference “Strategies XXI”, suppl. Technologies - Military Applications, Simulations And Resources 2018, 1, 176–182. [Google Scholar]
| No | Criteria | Description |
|---|---|---|
| 1 | Database | Google Web Search |
| 2 | Keyword of search | The name of the country, followed by “national security strategy” AND “latest version” |
| 3 | Date of collection | From July 17 to September 30, 2024 |
| 4 | Year of publication | In the last 11 years (2013–2024) |
| 5 | Type of publication | Official document |
| 6 | Integrity | The latest official version |
| 7 | Title | Studies focus on the following criteria: national security strategies or similar documents |
| 8 | Language | The first option: English; The second option: the official language |
| 9 | Full-text analysis | A content analysis that highlights a statistical situation regarding the term “cyber” |
| Types of document | Countries | No. terms of Cyber | Year | Language |
|---|---|---|---|---|
| National Security Strategy NSC |
Austria | 37 | 2024 | English |
| Belgium | 36 | 2022 | English | |
| Bulgaria | 20 | 2018 | Bulgarian | |
| Croatia | 12 | 2017 | English | |
| Czech Republic | 43 | 2023 | English | |
| Finland | 13 | 2017 | English | |
| Germany | 62 | 2023 | English | |
| Hungary | 36 | 2020 | English | |
| Lithuania | 16 | 2021 | English | |
| Netherlands | 35 | 2023 | English | |
| Poland | 16 | 2020 | English | |
| Slovakia | 24 | 2021 | English | |
| Slovenia | 25 | 2020 | English | |
| Spain | 40 | 2021 | English | |
| Sweden | 13 | 2017 | English | |
| National Defence Strategy NDS |
Romania | 23 | 2020 | English |
| National Security Concept NSC |
Estonia | 5 | 2023 | English |
| Latvia | 76 | 2023 | English | |
| Strategic Concept of National Defence SCND |
Portugal | 14 | 2013 |
English |
| National Strategic Review NSR |
France | 49 | 2022 |
English |
| Foreign and Security Policy Strategy FSPS |
Denmark | 29 | 2023 |
English |
| Countries | Cyber attacks |
Cyber security |
Cyber threats |
Cyber space |
Cyber defence |
Cyber crime |
|---|---|---|---|---|---|---|
| Austria | 5 | 11 | 0 | 5 | 4 | 5 |
| Belgium | 8 | 12 | 3 | 2 | 1 | 3 |
| Bulgaria | 1 | 5 | 0 | 6 | 0 | 2 |
| Croatia | 0 | 0 | 1 | 6 | 0 | 2 |
| Czech Republic | 2 | 13 | 5 | 14 | 1 | 1 |
| Denmark | 11 | 0 | 2 | 3 | 0 | 1 |
| Estonia | 0 | 2 | 0 | 2 | 0 | 1 |
| Finland | 0 | 8 | 2 | 0 | 0 | 0 |
| France | 5 | 7 | 1 | 4 | 2 | 1 |
| Germany | 16 | 15 | 0 | 11 | 2 | 1 |
| Hungary | 2 | 9 | 0 | 13 | 6 | 1 |
| Latvia | 8 | 34 | 3 | 12 | 3 | 1 |
| Lithuania | 0 | 11 | 2 | 0 | 2 | 0 |
| Netherlands | 8 | 11 | 1 | 0 | 0 | 3 |
| Poland | 1 | 7 | 2 | 5 | 1 | 0 |
| Portugal | 3 | 2 | 0 | 0 | 2 | 6 |
| Romania | 5 | 3 | 2 | 1 | 1 | 5 |
| Slovakia | 7 | 6 | 0 | 9 | 1 | 1 |
| Slovenia | 5 | 7 | 7 | 2 | 0 | 2 |
| Spain | 10 | 11 | 1 | 12 | 0 | 2 |
| Sweden | 2 | 9 | 0 | 13 | 6 | 1 |
| Total | 99 | 183 | 32 | 120 | 32 | 39 |
| Criteria | Description | Details |
|---|---|---|
| Database | Web of Science, Proquest | Data |
| Keywords | Example: Cyber attack and national security | In the databases, both forms of the phrases specified in the search string must be identified. |
| Period of time | 2013 – September 2024 | The selection of this time period is justified by the emergence and development of strategic-level documents from European Union member states addressing the "cyber" domain. |
| Publication | Dissertations & Theses, Scholarly Journals, Trade Journals | These publications contain relevant articles and papers pertaining to the cybersecurity domain. |
| Language | English | The security strategies of the Member States of the European Union have English versions. |
 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





