Submitted:
25 May 2025
Posted:
27 May 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
- What are the attack demographics for the past 20 years of cybersecurity? What is the impact of emerging technology on cybersecurity?
- What is the motivation behind cyber crimes in the current technological era? What are the recent victim demographics of cyber crimes around the globe?
- What are some of the methods that can be used for mitigating these attacks? How cyber crimes are affecting governments and large organizations?
2. Literature Review
| AUTHORS | YEAR | CYBERCRIME TRENDS | GEOGRAPHICAL DISTRIBUTION | GENDER DISPARITY | PEAKS AND SCAMS | IMPLICATIONS |
|---|---|---|---|---|---|---|
| Hoar et. al. [9] | 2005 | × | × | |||
| Myriam et al. [10] | 2006 | × | × | × | ||
| Su et. al. [11] | 2007 | × | × | |||
| Alvaro et. al. [12] | 2008 | × | × | × | ||
| McCrohan at. el. [13] | 2009 | × | × | × | ||
| Chee-Wooi et. al. [14] | 2010 | × | × | |||
| Amir et. al. [15] | 2011 | × | × | × | ||
| Broadhurst et. al. [16] | 2012 | × | × | |||
| Sharjeel et. al. [17] | 2013 | × | × | × | ||
| Reddy et. al. [18] | 2014 | × | × | × | ||
| Bendovschi et al. [19] | 2015 | × | × | |||
| Pescatore et. al. [20] | 2016 | × | × | |||
| Osawa et al. [21] | 2017 | × | × | × | ||
| Cabaj .at. el. [22] | 2018 | × | × | × | ||
| Ali et al. [23] | 2019 | × | × | |||
| Rajasekharaiah et al. [24] | 2020 | × | × | × | × | |
| Dillon et al. [25] | 2021 | × | × | |||
| Kaur et al. [26] | 2022 | × | × | × | ||
| Stafiniak et al. [27] | 2022 | × | × | |||
| Durojaye et al. [28] | 2022 | × | × | × | ||
| Francis et al. [29] | 2023 | × | × | |||
| Fadziso et al. [30] | 2023 | × | × | × | ||
| This Paper | —- |
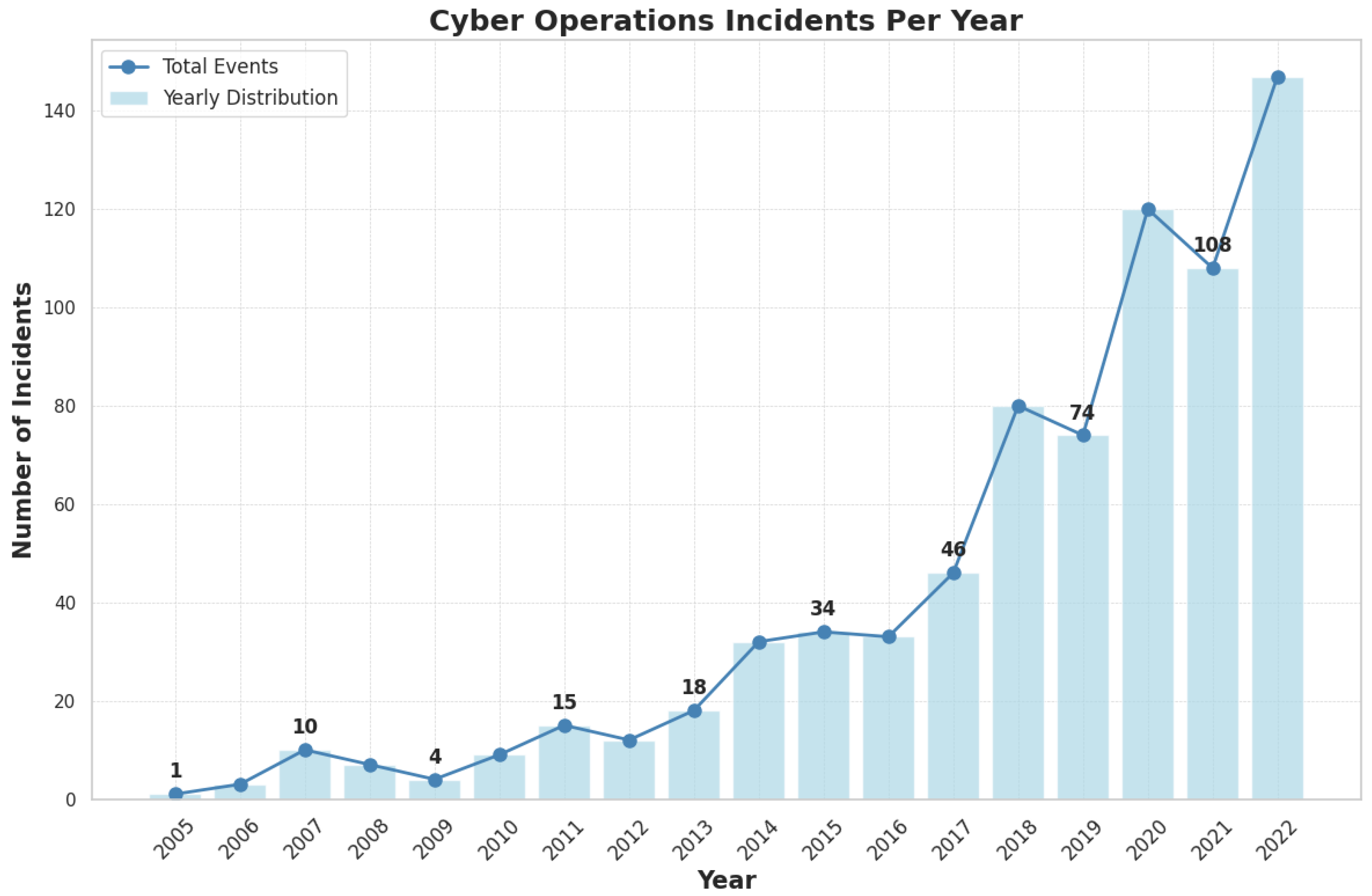
3. Evolution of Cybercrime Trends
3.1. Data Analysis Methods
- Data Collection: The data used in the research has been collected from various credible sources like the IC3 Report 2023 [1] and the data set that is used in this research is a well-organized and comprehensive collection of all of the data related to state-sponsored cyber attacks from the year 2005 to the present [6]. The data set tracks statistics like summary and description of the cyber operation, date of happening, and state affiliated with the respective operation. Following these statistics responses against these cyber operations, victims and their categories that were targeted, and finally, the sources that reported the operations are also tracked via this data set. With these statistics in mind, we can form a robust framework for understanding the patterns of state-sponsored cyber operations.
- Data Preprocessing: Before the data was used for analysis it went through a preprocessing cleaning phase. In this process, all the duplicate and redundant data was removed. Following this methods like data imputation were used to address any gaps in the data and lastly, the data was converted into a suitable format for data analysis.
- Analytical Techniques: For analysis we trained a machine learning algorithm using tools like Jupiter Notebook. We automated all the cleaning and visualization processes using this machine-learning algorithm.
- Data Visualization: Charts and graphs are used to show the demographics from the data analysis. They were made precise using the machine learning algorithm. Alongside these heatmaps were used to show the intensity and frequency of cyber threats across different regions or periods.
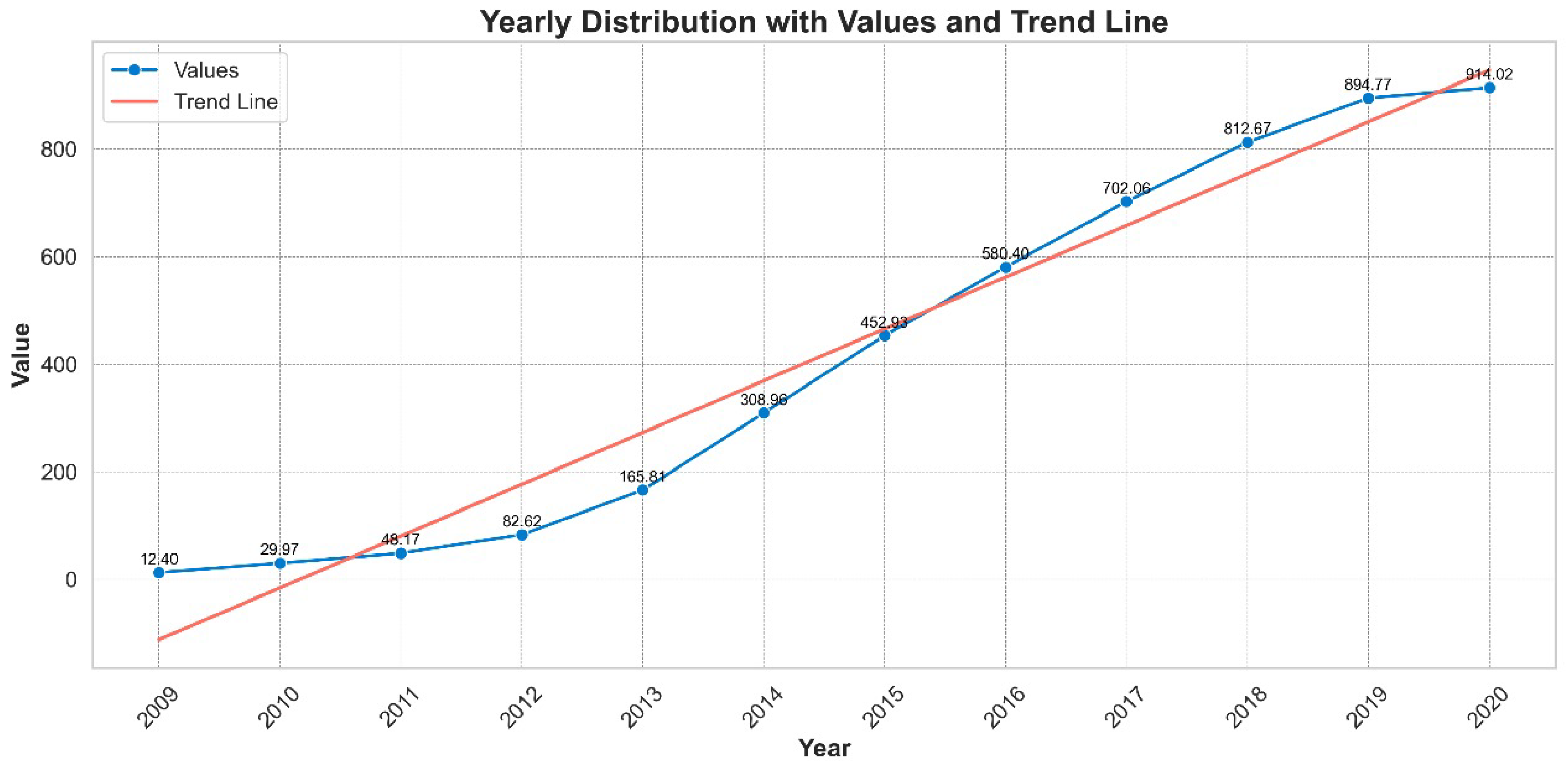
3.2. Evolution of Cybersecurity and Cybercrimes from 1960 to Present
3.2.1. 1960’s
3.2.2. 1970’s
3.2.3. 1980s
3.2.4. 1990s
3.2.5. 2000s
3.2.6. 2010s
3.2.7. The Present
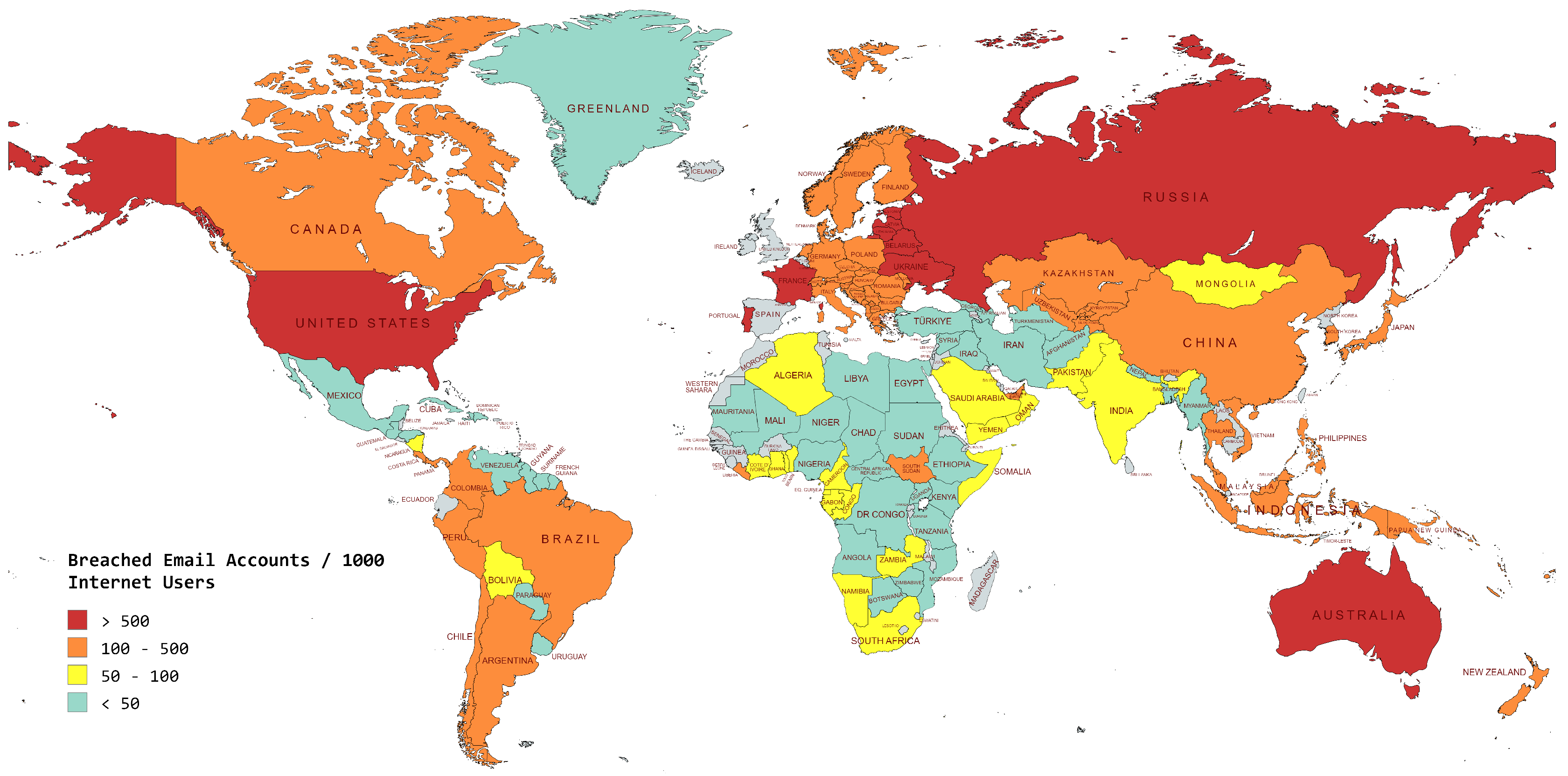
4. Geographical and Temporal Distribution
- Population: Population plays are very vital role when it comes to geographical and temporal distributions of cybercrime activities. Always the densely populated areas will be deeply affected by cybercrimes.
- Economic Concentration: One of the root causes of increased cybercrimes in a region is economic concentration. Cybercriminals mostly target the areas where economic congregation is elevated.
- Technological Hubs: Technological hubs being the home of tech giants, are always are target for cybercrimes. The wealth of data that they produce is always vulnerable to many sophisticated cyber attacks
4.1. Geographical Spread of Cybercrimes
- Urban Areas and Technological Hub: States like New York, Los Angeles, San Francisco, and Chicago are targeted by cybercriminals more as compared to other states due to their technological density and high population.
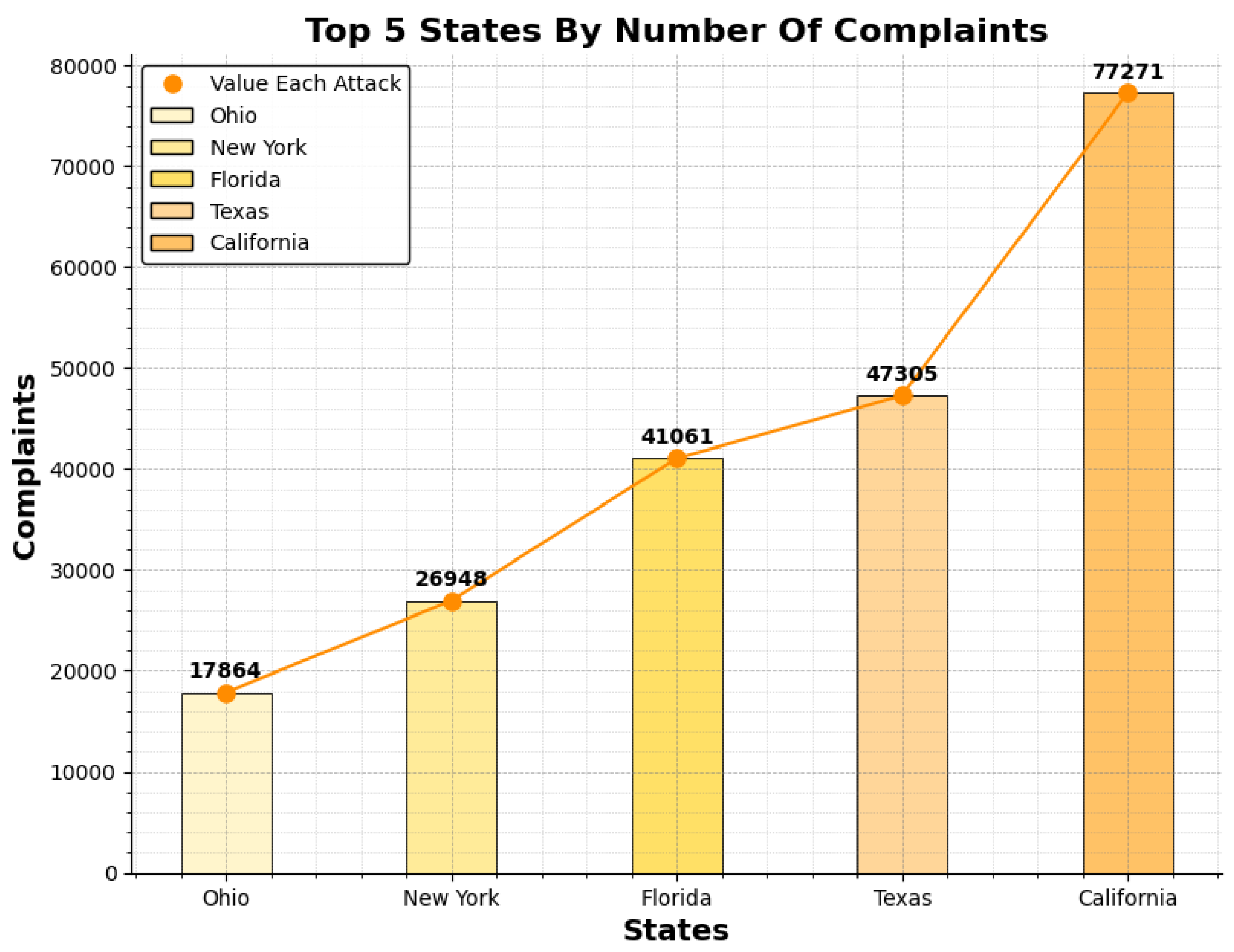
- State Trends: The US states like California, Florida, Texas, and New York are often struck by different cybercrime activities. This trend may be due to their dense population and large-scale technological hubs.
- Regional Distribution: In this rapidly evolving world of cybersecurity there is no area immune from digital threats. However, some regions like the east cost and the west cost exhibit higher cybercrimes due to all the factors discussed earlier.
4.2. Most Targeted States and Patterns
- States With The Most Complaints: States like California , Florida, New York, and Texas were the states with the most number of complaints in the year 2023. Some of these states are heavily populated and are considered as the technological centers due to which they often report high cybercrime rates.
- Emerging Trends: In the year 2023 small states like Ohio and Arizona have shown a relative increase as compared to previous records. This could be due to their significant financial sectors and proximity to larger urban centers.
- Industry-Specific Targeting: States with high industrial density like New York and California are the targets of financial frauds and data breaches.
5. Gender Disparity and Vulnerable Age Groups in Cybercrimes
5.1. Male and Female Cybercriminal Ratio
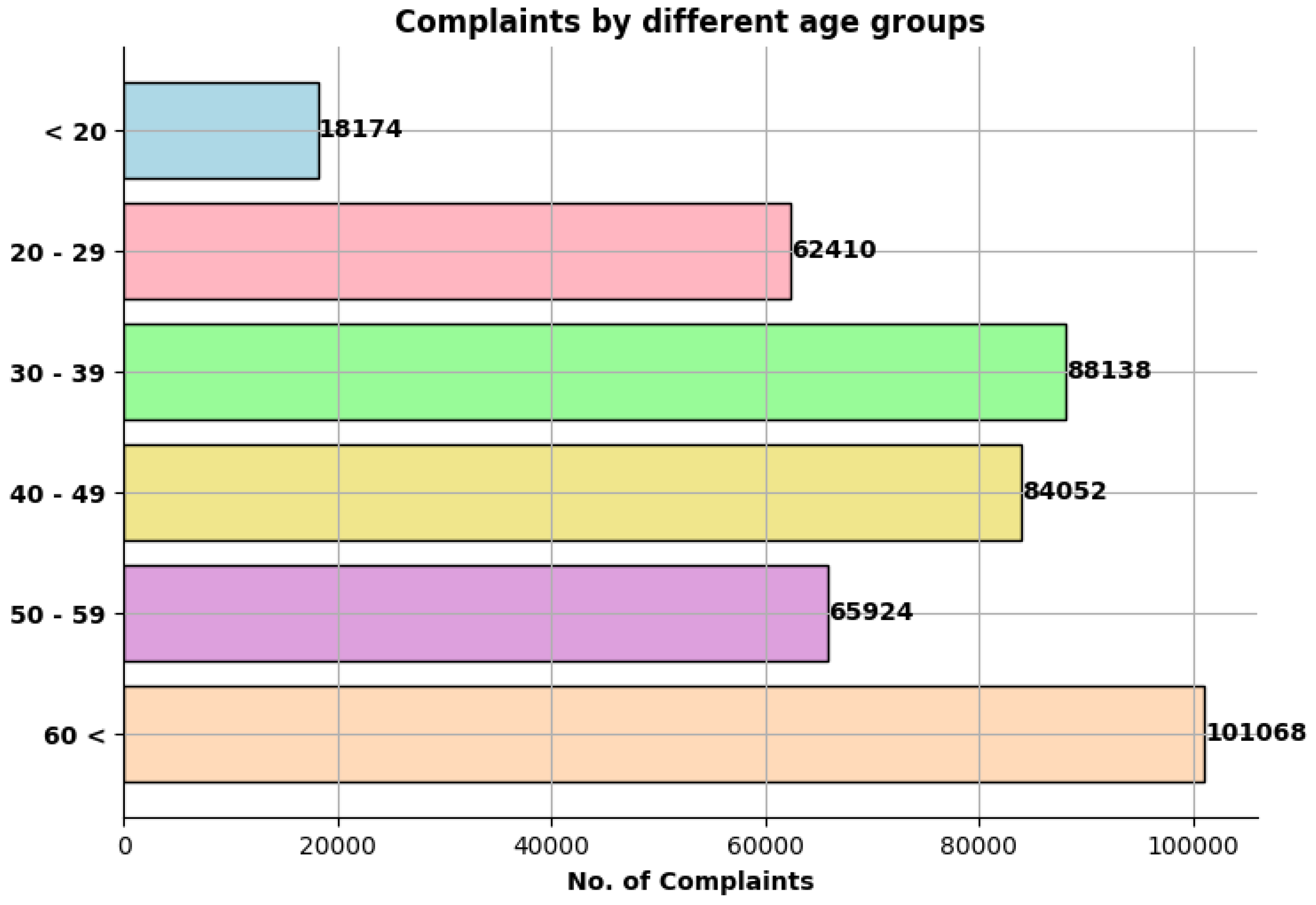
5.2. Victim Age Distribution
6. Temporal Peaks and Scams
6.1. Notable Scam Peaks
6.1.1. Phishing
6.1.2. Personal Data Breach
6.1.3. Non-Payment/ Non-Delivery
6.1.4. Tech Support Scams
6.2. Modus Operandi Patterns and Trends
| Attacks | Modus Operandi |
|---|---|
| Phishing | Emails, messages, |
| and malicious Links | |
| Personal data | Hacking or Malware |
| Breaches | |
| Extortion | Ransomware or threats |
| to reveal personal information | |
| Tech Support | Social engineering |
| Ransomware | Encrypting user data |
| Malware | software designed |
| to cause harm | |
| DDoS | Overwhelming the target |
| to make it slow | |
| MitM | Intercepting Communication |
| XSS | Injecting malicious scripts |
| Creds. spoofing | Using combinations of passwords |
| to gain unauthorized access | |
| Zero-Day | Exploiting unknown vulnerabilities |
| Insider attacks | Malicious attraction taken |
| by someone within the organization | |
| DNS spoofing | Redirecting website to |
| a malicious website |
6.3. Scams and Sponsors
6.3.1. Scams
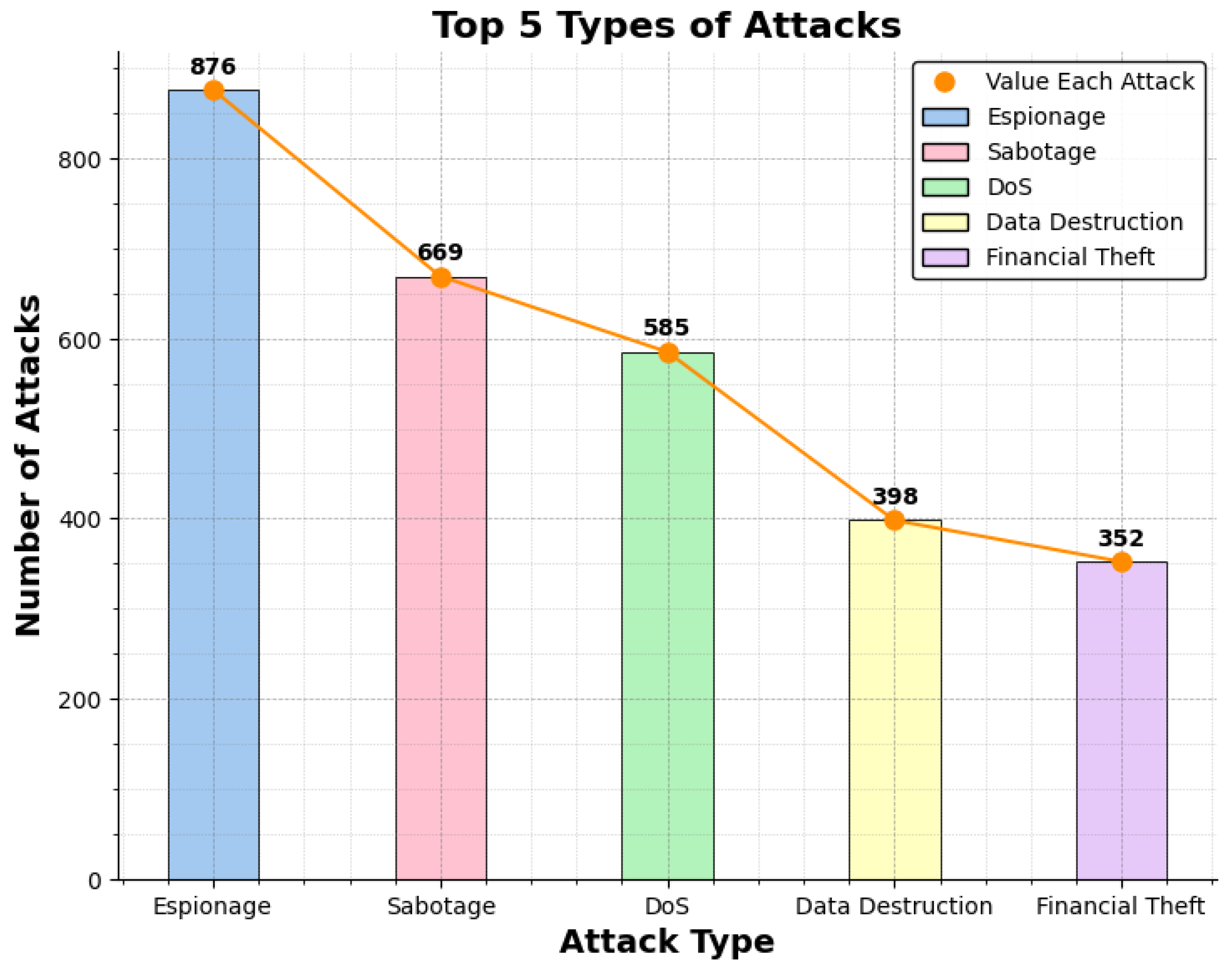
- Espionage: According to the data espionage is at the top of state-sponsored attacks. These attacks involve stealing sensitive pieces of information and intellectual property.
- Sabotage: After espionage attacks in the list is sabotage. In such crimes, governments or states target critical infrastructures.
- Distributed Denial of Service (DDoS): Third in the list is DDoS or Distributed Denial of Service. Such attacks are used to disturb different services.
- Data Destruction: Succeeding to DDoS in the list Data Destructions. Governments use these attacks to destroy financial data, country databases, and all.
- Doxing: At the end of the list are Doxing attacks where the personal information of an individual is used to harass or intimidate them.
6.3.2. Sponsors
-
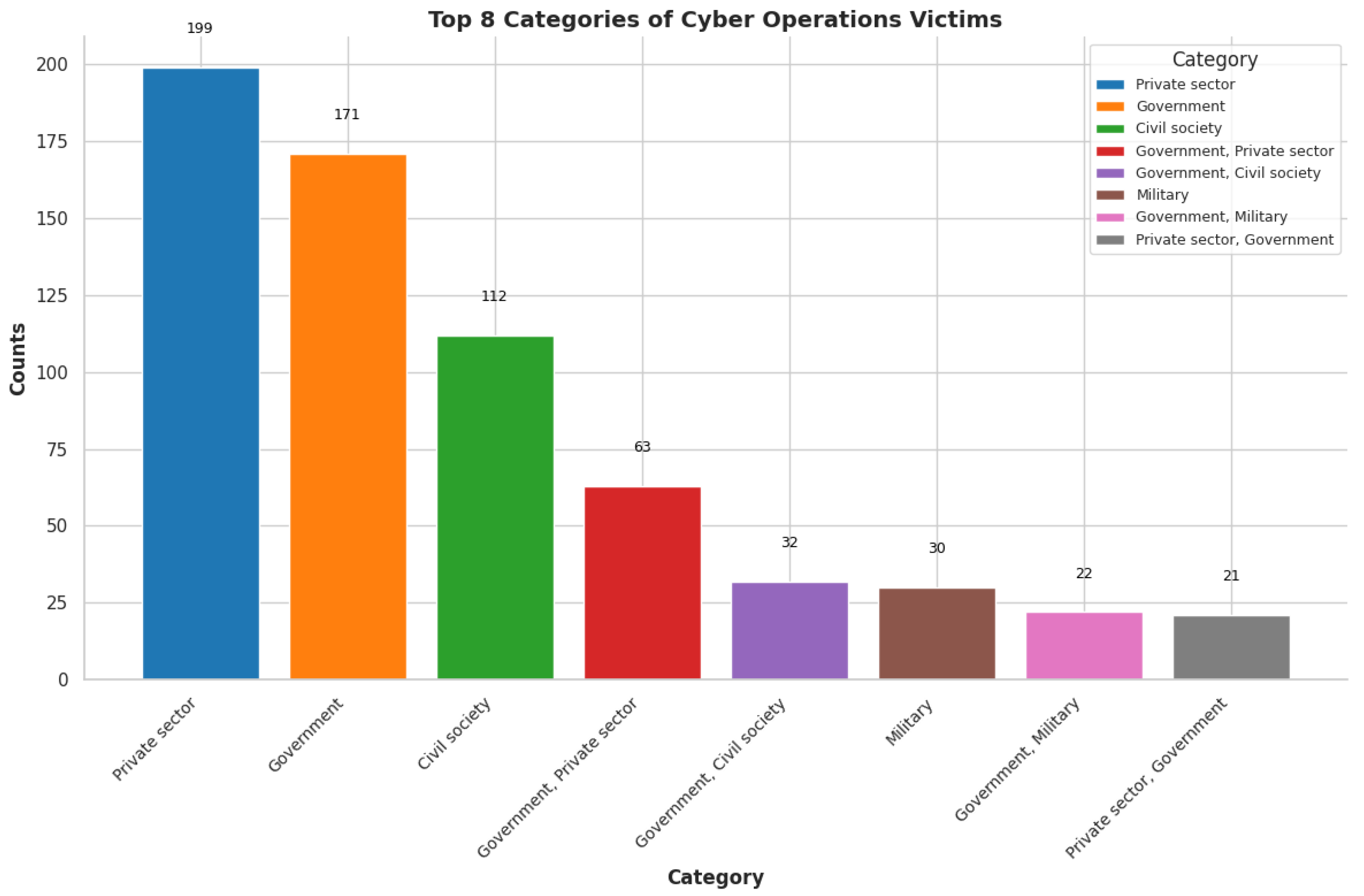
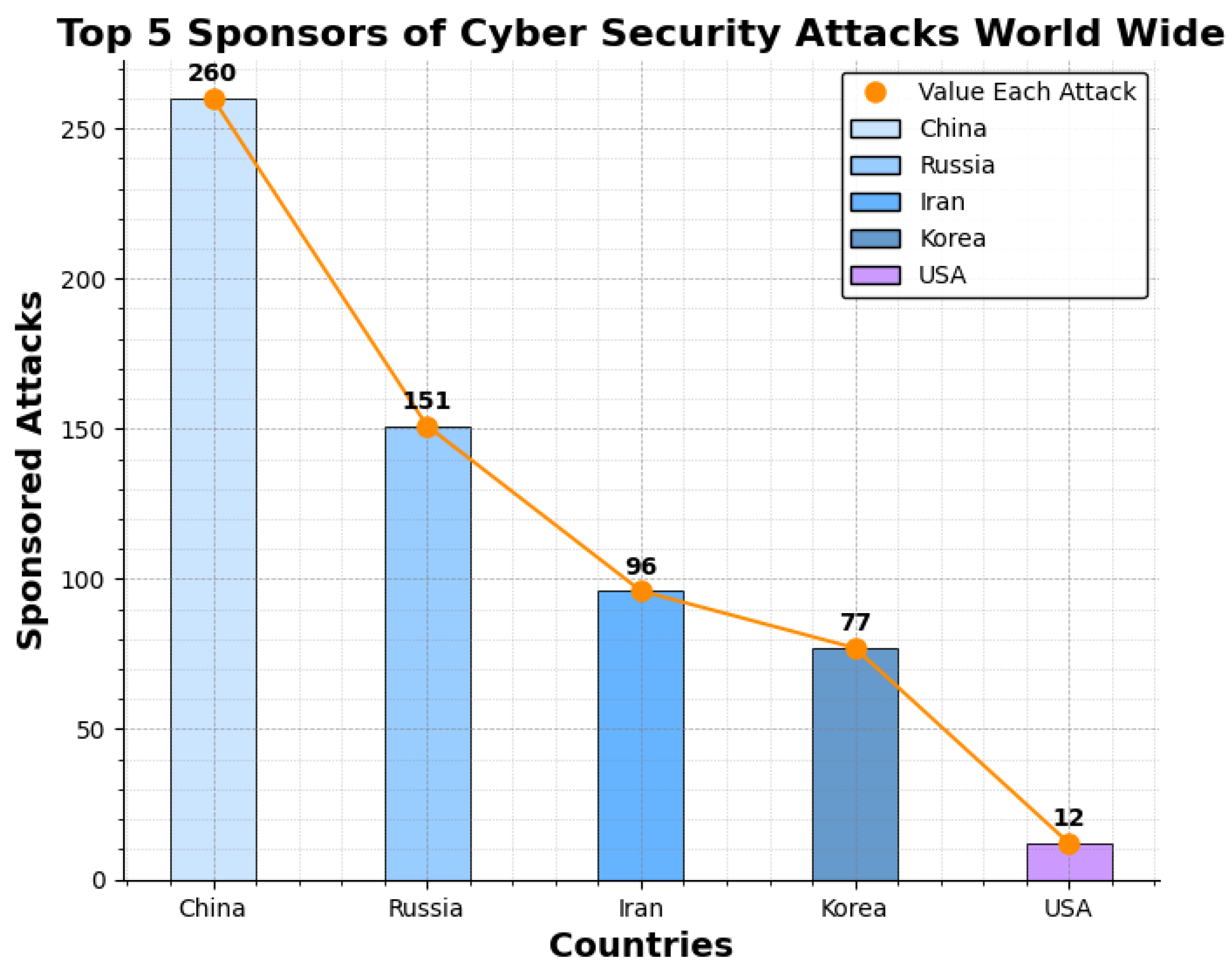
China has been recognized as the leading country in state-sponsored attacks in the last two decades with numbers crossing 250. China has recently been involved in cyber-espionage attacks targetting various states’ intellectualproperties, secrets, and digital infrastructure. The Chinese government is believed to sponsor a complex network of cyber units that engage in persistent threat activities. A Chinese Hacking group Double Dragon was associated with $20 million theft in COVID-19 relief aid in the US. [38]Figure shows elaborate the top Affiliated groups in global cyber crimes Figure 6
- Russians are one of the top contenders in cybercrimes after China. Russia is also accused of using cyber attacks and tools to support its geographical objectives and interference in foreign elections. This can also be proved by the NotPetya ransomware attack [39]. Many Russian hacking groups like the Nobelium and Midnight Blizzards have been accused multiple times for their cyber attacks on Western countries.
- Iran’s state-sponsored attacks are driven by geographical and ideological motives. Iran has been involved in state-backed attacks like espionage, sabotage, and cyber-terrorism. Iran has attacked many governmental networks and energy infrastructures in the past few years.
- United States has a more defensive approach when it comes to state-sponsored attacks. The US focuses on protecting its critical infrastructures and safeguarding its state from different cybersecurity threats. But the country has also been involved in many sophisticated cybercriminal activities like the Stuxnet.
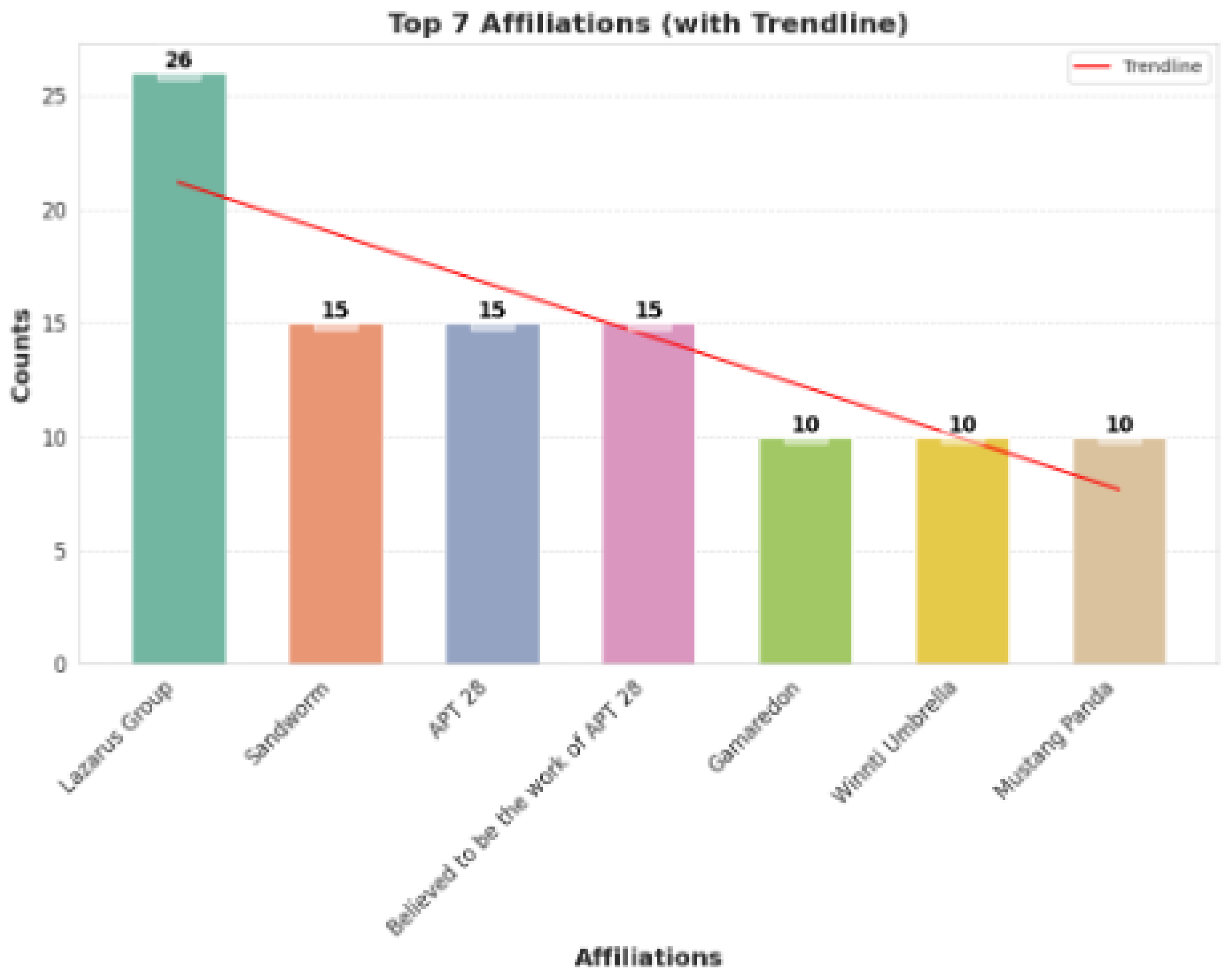
- Other developing countries like Vietnam and Pakistan are also emerging candidates in state-sponsored attacks.
6.4. Global Data Breach
7. Discussion and Implications
- Phishing attacks are one the most common cyberattacks in which criminals use techniques like social engineering by sending emails to the targeted individual to trick them into thinking that the email is from a legitimate source. If the attacker uses voice males in their phishing attack then such attacks are known as vishing and if it is done in the form of SMS then it is categorized as smishing.
- Another pervasive attack that is common nowadays is ransomware. In this attack, the adversary encrypts the files and folders of the victim and then demands a certain amount as ransom. If the user pays the desired ransom on time the attack releases their system or information. To put pressure on the affected users attackers sometimes use a technique known as Double extortion in which the attacker threatens to leak the information if ransom is not paid.
- Espionage attacks have been one of the most common and leading cyber-attacks in the past years. This attack damages the national security concern and the privacy of individuals. Normally attackers go against governments or businesses. It can be spread by the aid of malware and any other social engineering technique. The Intention behind these attacks can be money, power, or secret. There is a need to implement tough security measures and best practices to minimize these attacks.
- Supply chain attack mostly known as third-party risk exploitation is an attack that targets a system or a network via a third party. Normally victims are directly targeted by the attackers themselves but in a supply chain attack, the third party is exploited. The third party can be a vendor, a contractor, a dealer, or any other individual or network connected directly to an organization or a person. The motivation behind this attack is to gain access to the main system using the smallest and weakest link i.e. the external party in this case. Supply chain attacks can be then further classified into three categories i.e. software-based attacks where prebuilt software is either imported or manufactured with the collaboration of an external party. The next one is the hardware-based attack where hardware components are bought from an external entity. Last but not least is service service-based attacks where an individual or an organization is using a service provided by a service provider.
- Zero-day exploits are the exploitation of a new vulnerability in a system or a network that has never been exploited before. The technology and software landscape is constantly evolving. This evolution has worked as a catalyst for new and improved technological devices. The market for these devices is increasing rapidly alongside zero-day exploits.
- Destributed Denial of Service (DDoS) is also one of some prevalent attacks that are common nowadays. In a DDoS attack, a particular system, server, or organization is overwhelmed by the excessive amount of requests from multiple locations. On the other hand when the requests are only coming from a single source then the attack is classified as a DoS attack. These two attacks are very common nowadays mostly at the state level where different countries are using such attacks to sabotage the critical digital infrastructure of fellow countries and states to gain technological advantage.
- Man-in-the-Middle (MitM) Attacks are the attacks in which the adversaries intercept the communication between two entities or nodes. Such attacks are also common nowadays. Some precautionary measures like strong Wifi passwords, secure communication protocols, and channels can be used to decrease the likelihood of such attacks.
- Advanced Persistent Threats (APTs) are very complex, sophisticated, and multilayered cyberattacks. These attacks are mostly state-sponsored and are used by governments to sabotage other countries and agencies. In some cases, the targets of such attacks are also large organizations and companies.
7.1. Future Cybersecurity Trends
- The main purpose of AI is to automate tasks to make our daily lives easy. Different machine learning algorithms are used for these purposes. The attackers nowadays also use AI to automate these exploits and malware development and to generate legit-looking emails and text messages that can further be used in social engineering campaigns. These algorithms are more efficient in bypassing security systems without being detected. Traditional cybersecurity measures are not enough to handle such attacks.
- The process of creating realistic-looking images of an individual using a deep learning algorithm is known as Deep Facks. Deep fakes have useful applications in different industries but cybercriminals are using this technology for negative purposes. As mentioned earlier it generates realistic images that can be used for many ethical purposes. Creating fake but real-looking images and videos using deep learning algorithms can be dangerous for exploiting human vulnerabilities.
- The motivation behind quantum computing is to have a computing system that works at a speed of exponent or we say exponentially faster computing. Quantum computing is also an emerging threat If it is used for negative purposes, as quantum computing contains bits known as qubits, these quantum bits have the property to be in multiple states at a time which causes parallel execution in a much faster way. Quantum computing uses algorithms like Shors and Grovers algorithms which are very effective in breaking cryptographic algorithms because of their efficiency for dividing data into half and factoring large composite numbers. The impact of this affects the confidentiality, integrity, and authenticity of sensitive information. Above is only one effect of quantum computing from a cybersecurity perspective. other can be technological inequality, data privacy regard, and cryptographic vulnerability.
- 5G network mobile communication is extremely fast and devices are connected more reliably. In a 5G network, the network is divided into slices. Each slice is for a specific use and purpose however these also introduce difficulties related to isolation and unauthorized access to sensitive information. 5G network introduces vide variety of security challenges that can be exploited, like its use of unique authentication and authorization mechanisms which also introduce issues like improper key management in protocol and security flaws irrespective of the fact that they aim to have an enhanced security measure.
- Iot-based attacks are also becoming a rising threat nowadays. As the technological world and interconnectivity of all devices are increasing all around the globe, the attacks and risks associated with it are also increasing rapidly. The prevention for such attacks suggested by researchers throughout the world is decentralization of technology or using blockchain.
- Slowly but surely the technology will use the cloud as its primary storage and data transmission source. This will increase the ratio of Cloud-Based Attacks. In such attacks, attackers exploit the cloud-based vulnerabilities. To gain unethical access to data or services.
- The trend of Ransomware-as-a-Service (RaaS) attacks has also increased in recent times. Some platforms are providing ransomware as a service nowadays. Due to such platforms less skilled hackers are now capable enough to launch their ransomware. These platforms also provide the facility of deployment as well which has drastically increased the sophistication of these attacks.
- Finally there are hybrid attacks where attackers or adversaries use a combination of two or more attacks. This makes the attack harder to detect and defend against.
7.2. Preventive Measures
- Training and awareness play an important role in minimizing security threats. This includes preparing employees by creating scenarios and training them how to behave in such scenarios. Most common attacks like social engineering and phishing attacks are due to less understanding of modern technology and also unawareness of trending techniques used for utilizing these attacks. One of the main reasons behind the large amount victims being 60 plus is less awareness of modern technology and attacks.
- Using machine learning algorithms and AI for defensive purposes can be done by training an AI model using a large dataset. The model would be able to effectively analyze the behavior of attacks and also create AI-based solutions that will play a pivotal role in preventing a system once an attack is detected. An example of an AI defense system is SentineIone, a tool based on a machine learning algorithm that provides end-point security and can stop end-point attacks like ransomware and other malware attacks.
- To minimize threats related to quantum computing there is a need for post-quantum cryptography which provides security by encryption that is not breakable by quantum computing algorithms. There is also a need for quantum key distribution which is based on the principle of quantum mechanics for generating a secure key that is again immune to quantum brute force. If someone tries to eavesdrop the state of quantum is disturbed and warns the individual or parties involved. Being aware of new vulnerabilities is important to minimize quantum attacks this is possible through security assessment and networking with researchers. To have a complete picture of protection there is a need for an effective mitigation plan and updating software and hardware components is also important.
- To have a secure 5G network there is a need for comprehensive security strategies from secure method of authentication and authorization to awareness of how to use and deal with the odd behavior of this technology. There is a need to communicate with various telecommunication provider and understand their point of view. For secure communication, there is a need to use protocols like transport layer security to ensure data security. To have a training and awareness program among all users is important to minimize threats like social engineering attacks as well.
7.3. Implications for Law Enforcement, Policy, and Public Awareness
8. Conclusion
Funding
Data Availability Statement
Abbreviations
| Abbreviation | Full Form |
| AI | Artificial Intelligence |
| APTs | Advanced Persistent Threats |
| CIIP | Critical Infrastructure Protection |
| DDoS | Distributed Denial of Service |
| FBI | Federal Bureau of Investigation |
| IC3 | Internet Crime Complaint Center |
| IoT | Internet of Things |
| NERC | North American Electric Reliability Corporation |
| PNN | Probabilistic Neural Network |
| ROI | Return on Investment |
| RaaS | Ransomware as a Service |
| SCADA | Supervisory Control and Data Acquisition |
| URL | Uniform Resource Locator |
| PII | Personally Identifiable Information |
| CFR | Council on Foreign Relations |
References
- of Investigation, F.B. Internet Crime Report 2023, 2023. Accessed from the Federal Bureau of Investigation website.
- Rajasekharaiah, K.; Dule, C.S.; Sudarshan, E. Cyber security challenges and its emerging trends on latest technologies. In Proceedings of the IOP Conference Series: Materials Science and Engineering; IOP Publishing, 2020; Vol. 981, p. 022062. [Google Scholar]
- Świątkowska, J. Tackling cybercrime to unleash developing countries’ digital potential. Pathways for Prosperity Commission Background Paper Series 2020, 33, 2020–01. [Google Scholar]
- Muhammad, Z.; Anwar, Z.; Saleem, B.; Shahid, J. Emerging cybersecurity and privacy threats to electric vehicles and their impact on human and environmental sustainability. Energies 2023, 16, 1113. [Google Scholar] [CrossRef]
- Fiaz, F.; Sajjad, S.M.; Iqbal, Z.; Yousaf, M.; Muhammad, Z. MetaSSI: A Framework for Personal Data Protection, Enhanced Cybersecurity and Privacy in Metaverse Virtual Reality Platforms. Future Internet 2024, 16, 176. [Google Scholar] [CrossRef]
- Oh, J. State-Sponsored Cyber Operations (2005-Present). 2023. [Google Scholar] [CrossRef]
- Irfan, M.; Ali, S.T.; Ijlal, H.S.; Muhammad, Z.; Raza, S. Exploring The Synergistic Effects of Blockchain Integration with IOT and AI for Enhanced Transparency and Security in Global Supply Chains. Int. J. Contemp. Issues Soc. Sci 2024, 3, 1326–1338. [Google Scholar]
- Muhammad, Z.; Anwar, Z.; Javed, A.R.; Saleem, B.; Abbas, S.; Gadekallu, T.R. Smartphone Security and Privacy: A Survey on APTs, Sensor-Based Attacks, Side-Channel Attacks, Google Play Attacks, and Defenses. Technologies 2023, 11, 76. [Google Scholar] [CrossRef]
- Hoar, S.B. Trends in cybercrime: The dark side of the Internet. Crim. Just. 2005, 20, 4. [Google Scholar]
- Dunn, M.; Mauer, V. Towards a Global Culture of Cyber-Security. The International CIIP Handbook 2006, 2, 189–206. [Google Scholar]
- Sheng, S.; Chan, W.L.; Li, K.; Xianzhong, D.; Xiangjun, Z. Context information-based cyber security defense of protection system. IEEE Transactions on Power Delivery 2007, 22, 1477–1481. [Google Scholar] [CrossRef]
- Cárdenas, A.A.; Roosta, T.; Taban, G.; Sastry, S. Cyber security basic defenses and attack trends. Homeland Security Technology Challenges 2008, 73–101. [Google Scholar]
- McCrohan, K.F.; Engel, K.; Harvey, J.W. Influence of awareness and training on cyber security. Journal of Internet Commerce 2010, 9, 23–41. [Google Scholar] [CrossRef]
- Ten, C.W.; Manimaran, G.; Liu, C.C. Cybersecurity for critical infrastructures: Attack and defense modeling. IEEE Transactions on Systems, Man, and Cybernetics-Part A: Systems and Humans 2010, 40, 853–865. [Google Scholar] [CrossRef]
- Lupovici, A. Cyber warfare and deterrence: Trends and challenges in research. Military and Strategic Affairs 2011, 3, 49–62. [Google Scholar]
- Broadhurst, R.; Chang, L.Y. Cybercrime in Asia: trends and challenges. In Handbook of Asian criminology; 2012; pp. 49–63. [Google Scholar]
- Zareen, M.S.; Akhlaq, M.; Tariq, M.; Khalid, U. Cyber security challenges and wayforward for developing countries. In Proceedings of the 2013 2nd National Conference on Information Assurance (NCIA). IEEE; 2013; pp. 7–14. [Google Scholar]
- Reddy, G.N.; Reddy, G. A study of cyber security challenges and its emerging trends on latest technologies. arXiv preprint 2014, arXiv:1402.1842. [Google Scholar]
- Bendovschi, A. Cyber-Attacks – Trends, Patterns and Security Countermeasures. Procedia Economics and Finance 2015, 28, 24–31, INTERNATIONAL CONFERENCE ON FINANCIAL CRIMINOLOGY 2015, 7th ICFC 2015, 13–14 April 2015,Wadham College, Oxford University, United Kingdom. [Google Scholar] [CrossRef]
- Pescatore, J. Cyber security trends: Aiming ahead of the target to increase security in 2017. SANS Institute InfoSec Reading Room 2017. [Google Scholar]
- Osawa, J. The Escalation of State Sponsored Cyberattack and National Cyber Security Affairs: Is Strategic Cyber Deterrence the Key to Solving the Problem? Asia-Pacific Review 2017, 24, 113–131. [Google Scholar] [CrossRef]
- Cabaj, K.; Kotulski, Z.; Księżopolski, B.; Mazurczyk, W. Cybersecurity: trends, issues, and challenges. 2018. [Google Scholar]
- Ali, M.L.; Thakur, K.; Atobatele, B. Challenges of Cyber Security and the Emerging Trends. In Proceedings of the Proceedings of the 2019 ACM International Symposium on Blockchain and Secure Critical Infrastructure, New York, NY, USA, 2019; BSCI’19, p. 107–112. [CrossRef]
- Rajasekharaiah, K.M.; Dule, C.S.; Sudarshan, E. Cyber Security Challenges and its Emerging Trends on Latest Technologies. IOP Conference Series: Materials Science and Engineering 2020, 981, 022062. [Google Scholar] [CrossRef]
- Dillon, R.; Lothian, P.; Grewal, S.; Pereira, D. Cyber Security: Evolving Threats in an Ever Changing World. In Digital Transformation in a Post-Covid World: Sustainable Innovation, Disruption and Change; Kuah, A., Dillon, R., Eds.; CRC Press, 2021; pp. 129–154. [Google Scholar]
- Kaur, J.; Ramkumar, K.R. The recent trends in cyber security: A review. Journal of King Saud University - Computer and Information Sciences 2022, 34, 5766–5781. [Google Scholar] [CrossRef]
- Stafiniak, M.; Wodo, W. State-sponsored Cybersecurity Attacks. In Proceedings of the 2022 63rd International Scientific Conference on Information Technology and Management Science of Riga Technical University (ITMS). IEEE; 2022; pp. 1–6. [Google Scholar]
- Durojaye, H.; Raji, O. Impact of State and State Sponsored Actors on the Cyber Environment and the Future of Critical Infrastructure. arXiv Submitted on 13 Dec 2022. 2022, arXiv:2212.08036. [Google Scholar]
- AZUBUIKE, C.F. Cyber Security and International Conflicts: An Analysis of State-Sponsored Cyber Attacks. Nnamdi Azikiwe Journal of Political Science 2023, 8, 101–114. [Google Scholar]
- Fadziso, T.; Thaduri, U.R.; Dekkati, S.; Ballamudi, V.; Desamsetti, H. Evolution of the Cyber Security Threat: An Overview of the Scale of Cyber Threat. 2023; Volume 3, pp. 1–12. [Google Scholar] [CrossRef]
- Wisnioski, M.H. Engineers for change: Competing visions of technology in 1960s America; Mit Press, 2012. [Google Scholar]
- Hauben, M. History of ARPANET. Site de l’Instituto Superior de Engenharia do Porto 2007, 17, 1–20. [Google Scholar]
- Saltzer, J.H.; Schroeder, M.D. The Protection of Information in Computer Systems. Proceedings of the IEEE 1975, 63, 1278–1308. [Google Scholar] [CrossRef]
- Zhang, L. A new architecture for packet switching network protocols. PhD thesis, Massachusetts Institute of Technology, 1989. [Google Scholar]
- de Jong, B. The KGB in Eastern Europe during the Cold War: on agents and confidential contacts. Journal of Intelligence History 2005, 5, 85–103. [Google Scholar] [CrossRef]
- Lemenager, T.; Neissner, M.; Koopmann, A.; Reinhard, I.; Georgiadou, E.; Müller, A.; Kiefer, F.; Hillemacher, T. COVID-19 lockdown restrictions and online media consumption in Germany. International journal of environmental research and public health 2021, 18, 14. [Google Scholar] [CrossRef] [PubMed]
- Arshad, J.; Talha, M.; Saleem, B.; Shah, Z.; Zaman, H.; Muhammad, Z. A Survey of Bug Bounty Programs in Strengthening Cybersecurity and Privacy in the Blockchain Industry. Blockchains 2024, 2, 195–216. [Google Scholar] [CrossRef]
- Fitzpatrick, S.; Ramgopal, K. Hackers linked to Chinese government stole millions in Covid benefits, Secret Service says. NBC News Archived from the original on 5 December 2022. Retrieved 5 December 2022. 2022.
- Fayi, S.Y.A. What Petya/NotPetya ransomware is and what its remidiations are. In Proceedings of the Information technology-new generations: 15th international conference on information technology; Springer, 2018; pp. 93–100. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





