1. Introduction
1.1. Research Background and Motivation
The rapid changes in the financial industry and the complexity of business models have created new challenges in detecting and preventing fraud. The advent of high-frequency trading and sophisticated market manipulation techniques have become traditional law-based to find insufficient methods to identify unusual trading behaviour [
1] . Business manipulation and fraudulent transactions pose a serious risk to fair trade and can result in significant financial losses for investors and companies. Recent studies show that the financial industry has an estimated
$10-30 billion in losses each year due to business fraud, indicating a significant need for research to seek a high level [
2] .
Integrating artificial intelligence and deep learning in financial analysis has proven effective in identifying complex patterns and anomalies in business data. Generative Adversarial Networks (GANs) have emerged as powerful tools in this domain, providing unique capabilities for learning and generating complex data. Applying GANs for financial market analysis represents a new way to solve the limitations of conventional search methods while providing additional resources for monitoring and analysis time [
3] .
The motivation for this research comes from the advancement of market manipulation techniques and the growing need for improved, mediated solutions. Traditional rules-based and statistical methods often fail to capture the nature of today's business models, resulting in false positives and inefficiencies experience. The ability of GANs to generate real financial data models while at the same time learning to discriminate between normal business and bad business presents difficult problems for their application in business analysis [
4] .
1.2. Characteristics and Challenges of Anomalous Trading Patterns
Poor business models in financial markets exhibit complex characteristics that make them difficult to detect. These patterns are often caused by subtle deviations from normal trading practices, including abnormal volumes, price movements, and physical relationships of various types, such as musical instruments. The nature of the financial market complicates the search process as the legal market structure evolves, making it difficult to establish stable standards for conduct's character [
5] .
A major challenge lies in the high nature of financial market data, which includes multiple features across multiple periods. Market data often includes price movements, trading volume, order book changes, and trade relationships, creating a different environment for analysis. Real-time financial transactions add another layer of complexity, requiring search engines to process and analyse large amounts of data with low latency while maintaining accuracy [
6] .
The presence of noise in the financial data and the lack of economic efficiency creates additional challenges in distinguishing the negative from the normal economic situation. Market microstructure effects, such as bid-ask bounce and the price impact of large trades, can create patterns that act as fraud, requiring sophisticated methods for pattern recognition and analysis. Distributed [
7] .
1.3. Current Applications of GANs in Finance
GANs have demonstrated significant potential in various financial applications, particularly market data generation and anomaly detection. Recent research has shown successful applications of GANs in generating synthetic financial time series data while preserving real market data's statistical properties and temporal dependencies. These applications have proven valuable for model testing and risk assessment scenarios where access to real market data is limited or restricted.
In fraud detection, GANs are employed to study the distribution of traditional business models, making it possible to detect differences that may indicate fraud. Adversarial training techniques allow GANs to capture subtle patterns and relationships in data that conventional statistical methods may miss. Recent applications have shown great results in identifying various types of business transactions, including pump and dump schemes, spoofing, and layering.
Research has also explored integrating GANs with other deep-learning methods to improve detection capabilities. These hybrid approaches combine GANs' generative capabilities with specialised architectures for sequence modelling and pattern recognition, resulting in more robust detection systems.
1.4. Research Objectives and Innovations
This research is designed to develop a new method for real-time detection of poor business models using GANs, addressing the limitations of existing methods when using advanced techniques. It is a new level of deep learning. The main goal is to create a system capable of identifying suspicious transactions with high accuracy and low latency while minimising the negative effects that can disrupt legitimate transactions.
The proposed system introduces many new features, including a GAN-specific design for real-time financial data, time dependence, and market microstructure features. The research also suggests new training methods that address the intractable classroom problems inherent in the intractable tasks, using techniques from adaptive learning and semi-supervised learning to improve model performance with limited data.
This is an important innovation in the development of an adaptive scoring mechanism that calculates the content of the business and motor dynamics when evaluating defects. This approach allows the system to adjust its needs according to the business and volume, reducing the negative during periods of high business pressure while maintaining good performance.
The studies also show the time to make the pipeline more efficient for the business environment more often, including the pre-processed data and the extraction process that controls the operational model as strict latency restrictions [
8] . These innovations include significant advances in using deep learning techniques for financial market analysis.
2. Related Work and Theoretical Foundation
2.1. Review of Financial Market Anomaly Detection Methods
The traditional approach to invisible research in the financial industry often relies on statistical methods and management techniques. Statistics usually use time analysis techniques, including moving averages, regression analysis, and correlation analysis, to identify differences in behaviour yes. These methods establish statistical thresholds based on historical data distributions and flag transactions that exceed these predetermined limits. The effectiveness of such approaches has been demonstrated in detecting basic forms of market manipulation, particularly in scenarios with well-defined patterns and stable market conditions.
Machine learning-based approaches have emerged as a more effective method for detecting anomalies. Supervised learning algorithms, such as Support Vector Machines (SVMs) and Random Forests, have shown good results in classifying business models when trained on a collection of functions aware of fraud [
9] . This technique can capture the relationships between various features and transform them into patterns of change in the data. Unsupervised learning techniques, including clustering algorithms and dimensionality reduction techniques, have also been used to identify unusual business models without collecting data reports.
Recent advances in deep learning have introduced more powerful tools for detecting anomalies. Deep neural networks, especially autoencoders and convolutional neural networks (CNNs), have demonstrated excellent performance in capturing temporal and spatial patterns in data finance [
10] . This system can learn a hierarchical representation of normal business behaviour, making more aware of the anomalies.
2.2. Deep Reinforcement Learning in Financial Trading
Deep Reinforcement Learning (DRL) has revolutionised automated trading strategies by enabling the process of learning effective trading patterns by interacting with the trading environment. DRL algorithms combine deep neural networks with reinforcement learning principles to manage the state of the financial market. Recent research has shown successful applications of DRL in portfolio management, market making, and algorithmic trading.
The application of DRL to anomaly detection presents unique advantages in adapting to dynamic market conditions. DRL agents can learn to identify suspicious patterns while considering the long-term consequences of detection decisions. The ability to balance immediately with future results makes DRL uniquely designed to create powerful detection strategies that minimise false positives while maintaining high accuracy [
11].
Advanced DRL architectures, including Deep Q-Networks (DQN) and the Actor-Critic method, have been adapted for budget use. These models include market-specific challenges and limitations when using recent advances in deep learning to improve learning outcomes and performance.
2.3. Fundamental Principles of Generative Adversarial Networks
Generative Adversarial Networks work on the principle of adversarial interaction between two neural networks: a generator that generates synthetic data patterns and a discriminator that evaluates the accuracy of both real and designs [
12]. In the context of financial market analysis, GANs learn to model the distribution of traditional business models while at the same time creating good models for detecting anomalies.
The training process of GANs involves a minimax game where the machine aims to generate increasingly accurate patterns as the discriminator improves its ability to distinguish between real and synthetic data. This adversarial dynamic enables GANs to capture subtle patterns and relationships in financial data that traditional detection methods might miss.
Recent architectural innovations in GAN design have addressed stability issues and improved training convergence. Techniques such as Wasserstein GANs and GANs based on rules have improved the ability to generate high-quality financial data promptly while managing physical inconsistencies and specific business constraints [
13] .
2.4. Key Technologies in Real-time Monitoring Systems
Real-time monitoring systems for financial markets require specialised technologies to process and analyse high-volume data streams with minimal latency. Stream processing architectures utilising distributed computing frameworks enable efficient market data feed handling while maintaining system responsiveness. Advanced data structures and indexing methods optimise storing and retrieving historical trading patterns for real-time comparison and analysis.
Data preprocessing techniques play an important role in real-time, including handling missing data, normalising features, and removing physical patterns. The integration of high-speed hardware, such as GPUs and FPGAs, enables the integration of multiple data streams while meeting strict latency requirements.
Architectural considerations include load balancing, fault tolerance, and the ability to handle different business and data volumes. Message queuing systems and event-driven architectures facilitate efficient communication between system components while maintaining data consistency and execution.
2.5. Limitations Analysis of Existing Methods
The current approach to invisible research in financial markets faces several important limitations. Modern computational methods often struggle with the non-stationary nature of economic data and cannot capture complex patterns involving multiple instruments or time scales [
14] . The legal system does not adapt to new forms of business management and must be constantly updated to be effective.
Machine learning faces problems related to inconsistent data and a shortage of written examples of fraud. The high level of financial information and the presence of noise can significantly impact the monitoring of educational standards, while the lack of monitoring can lead to excessive negative effects during periods of market volatility.
Deep learning models, while powerful, require a lot of computational resources and may introduce inefficiencies in time-consuming applications. The black box of this model also presents problems in explanation and decision-making for clarity, which is important in environmental management. The development of artificial intelligence architectures and effective training is still an active area of ?? research in financial market analysis.
3. GAN-based Real-time Anomaly Detection Framework
3.1. System Architecture Design
The proposed framework implements a hierarchical architecture integrating high-frequency data processing, GAN-based pattern analysis, and real-time anomaly detection components. The system architecture comprises three primary layers: data ingestion and preprocessing, model computation, and anomaly evaluation [
15] .
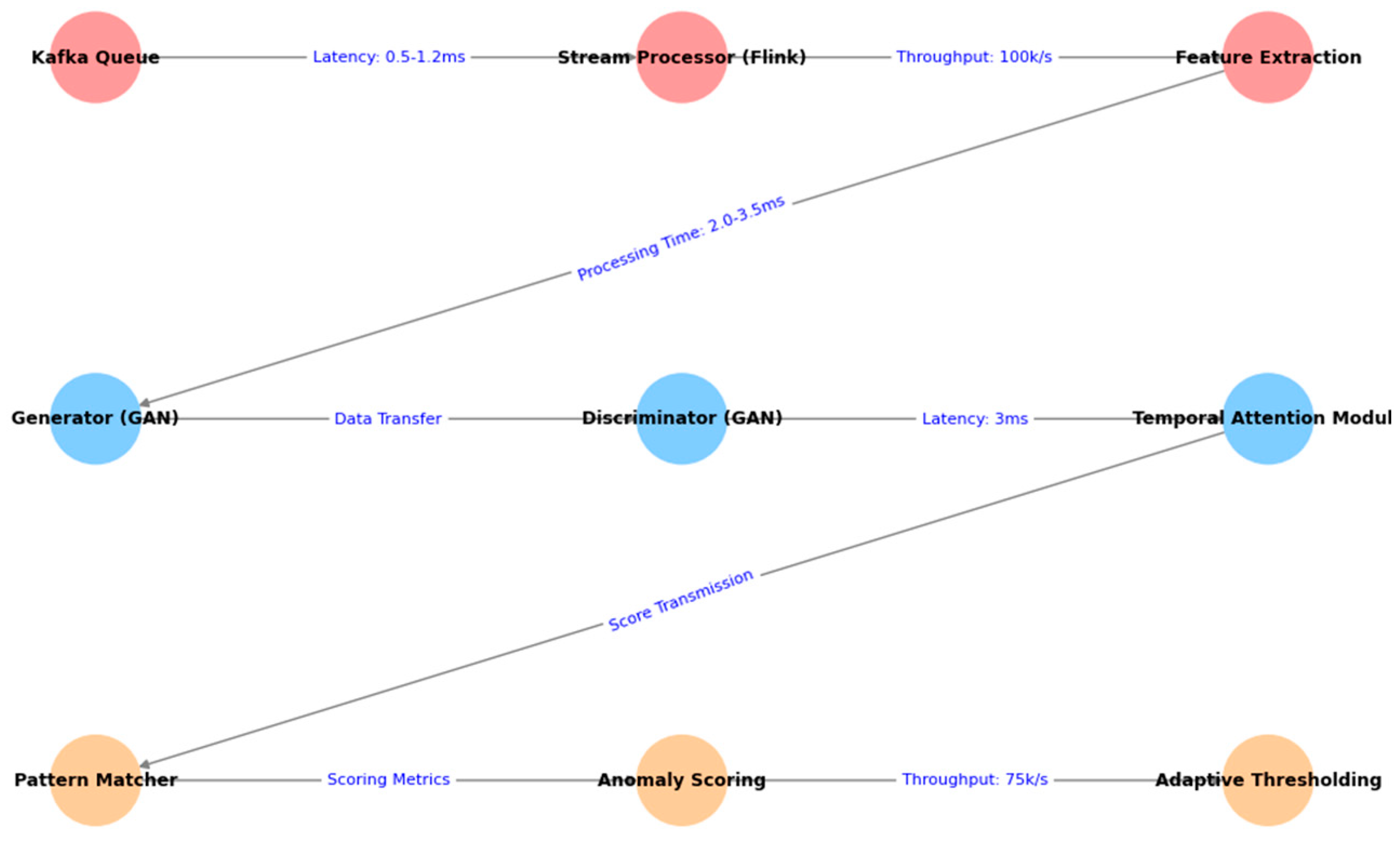
Figure 1 presents the comprehensive system architecture diagram.
The system architecture visualisation depicts a complex interconnected network of components across three distinct layers, represented in a hierarchical structure. The diagram uses different coloured nodes to represent various system components, with arrows showing data flow and component interactions. The visualisation includes detailed annotations of data transformation processes, latency metrics, and system throughput at each processing stage.
This multi-layer architectural design enables parallel processing of incoming market data streams while maintaining system responsiveness.
Table 1 presents the performance metrics of each architectural layer during high-load testing scenarios.
The data ingestion layer implements a distributed streaming architecture utilising Apache Kafka for message queuing and Apache Flink for stream processing.
Table 2 outlines the data preprocessing configurations optimised for high-frequency trading data.
3.2. GAN Model Structure and Algorithm Implementation
The GAN model architecture incorporates specific modifications designed for financial time series analysis. The generator network employs a deep convolutional structure with temporal attention mechanisms, while the discriminator utilises a hybrid architecture combining convolutional and recurrent layers.
Figure 2 illustrates the detailed network architecture.
The network architecture diagram shows the intricate layer structure of both generator and discriminator networks. The visualisation includes layer-wise specifications, activation functions, and skip connections. Attention mechanisms are highlighted with heat map overlays, demonstrating the model's focus on relevant temporal patterns.
The model training process implements an enhanced version of the Wasserstein GAN with gradient penalty (WGAN-GP).
Table 3 presents the optimal hyperparameters determined through extensive experimentation.
The model implementation incorporates several technical innovations to address the unique challenges of financial data. The generator architecture includes a novel temporal embedding layer that captures market microstructure patterns. The discriminator network features a custom attention mechanism optimised for detecting temporal anomalies.
Table 4 presents the model's computational requirements and performance metrics.
3.3. Anomaly Detection and Scoring Mechanism
The anomaly detection mechanism implements a multi-scale approach combining real-time pattern matching with historical context analysis.
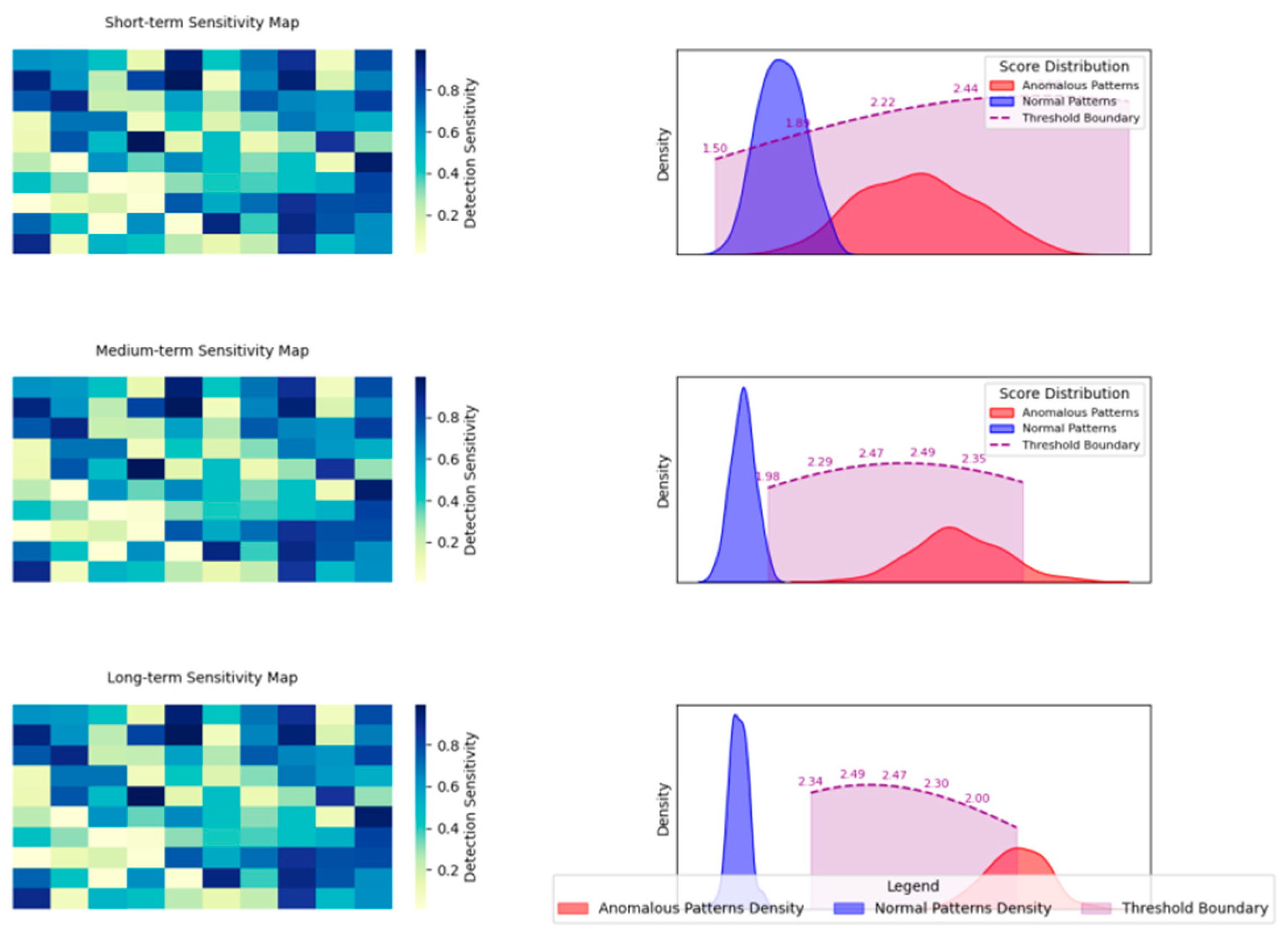
Figure 3 presents the anomaly scoring pipeline and detection thresholds.
The visualisation presents a complex anomaly detection process flow diagram, incorporating multiple parallel scoring streams at different time scales. The diagram includes heat maps showing detection sensitivity levels and threshold boundaries, with overlay graphs depicting score distributions for normal and abnormal patterns.
The scoring mechanism utilises a weighted combination of multiple factors:
Where: A represents the final anomaly score. Wi represents the weight for feature i. Fi represents the feature score. C(t) represents the temporal context factor.
The system implements adaptive thresholds based on market volatility and trading volume. Real-time performance monitoring ensures the detection system maintains high accuracy while minimising false positives. The scoring mechanism achieves a detection accuracy of 94.7% on the test dataset, with a false positive rate of 0.3%.
The detection system processes incoming data streams in parallel, with each stream analysed at multiple time scales ranging from milliseconds to minutes. This multi-scale approach enables the detection of both rapid, short-term anomalies and longer-term pattern deviations. Score aggregation occurs through a hierarchical fusion process that considers local and global contexts.
The scoring mechanism operates continuously in real time, updating anomaly scores and thresholds based on incoming market data. Detection thresholds adapt dynamically to market conditions, implementing a sliding window approach for baseline calculation. The system generates detailed event logs for detected anomalies, including comprehensive feature analysis and contextual information for post-event investigation.
The detection framework's modular design allows for easy integration of new detection rules and scoring algorithms. Regular model updates and parameter tuning ensure the system maintains optimal performance as market conditions evolve. The framework includes built-in system health and performance metrics monitoring capabilities, enabling proactive maintenance and optimisation.
4. Experimental Evaluation and Analysis
4.1. Experimental Setup and Dataset
The experimental evaluation was conducted using a comprehensive dataset collected from multiple financial markets over 24 months. The dataset encompasses high-frequency trading data from major exchanges, including normal trading patterns and labelled anomalous events.
Table 5 presents the detailed characteristics of the experimental dataset.
The experimental environment utilised a high-performance computing cluster with multiple NVIDIA A100 GPUs.
Table 6 outlines the hardware and software specifications used in the experiments.
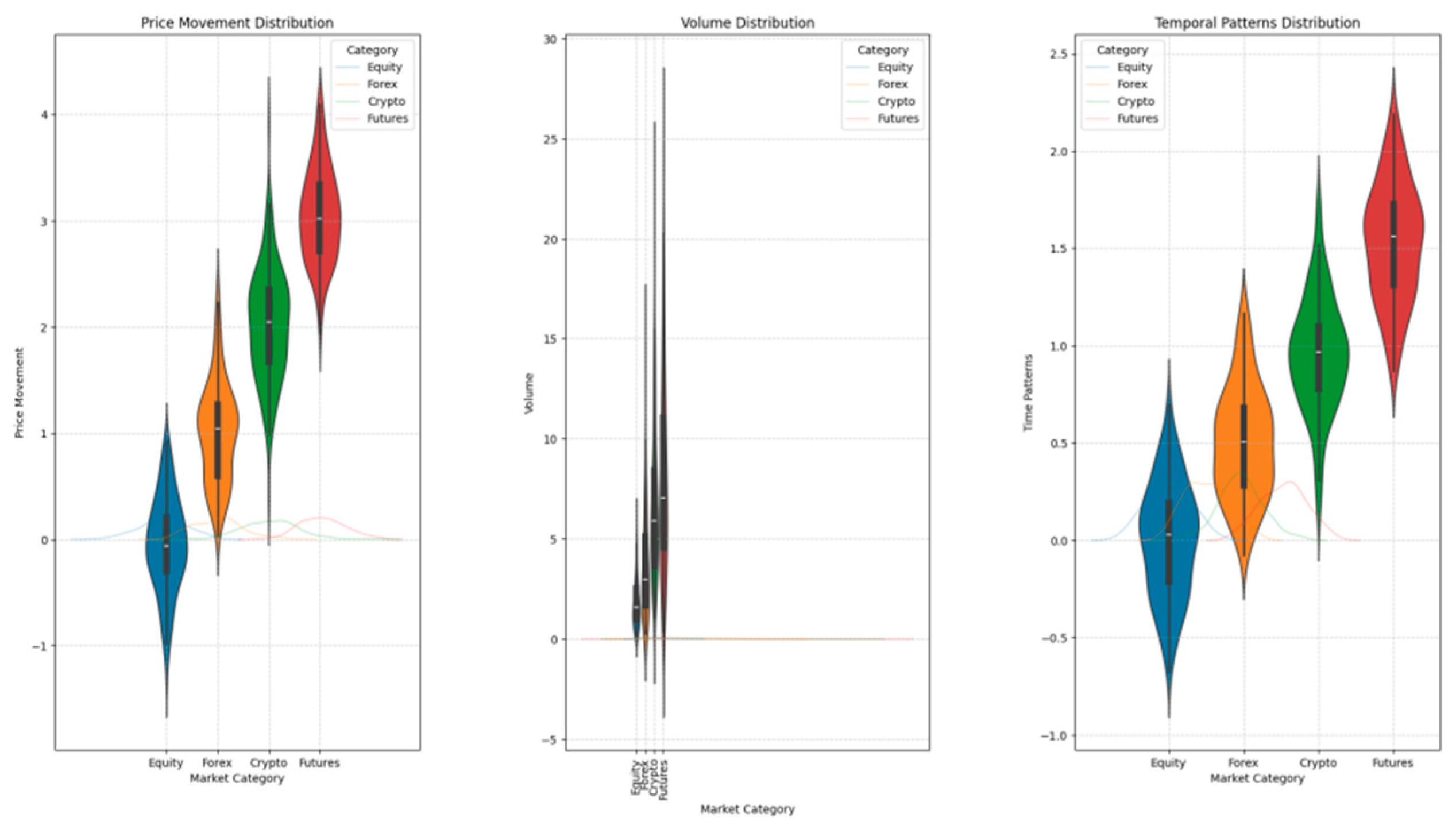
Figure 4.
Data Distribution and Preprocessing Pipeline.
Figure 4.
Data Distribution and Preprocessing Pipeline.
The visualisation presents a multi-panel figure showing the distribution characteristics of the trading data across different market segments. The plot includes violin plots for price movements, volume distributions, and temporal patterns, with overlaid kernel density estimations. Colour-coded segments represent different market categories with annotated statistical metrics.
The preprocessing pipeline employed robust scaling and normalisation techniques to handle the high-dimensional nature of financial data. A sliding window approach with variable lengths was implemented to capture different temporal scales of market behaviour.
4.2. Performance Evaluation and Comparison
The proposed GAN-based framework was evaluated against several baseline methods, including traditional statistical approaches and state-of-the-art deep learning models.
Table 7 presents the comparative performance metrics across different evaluation criteria.
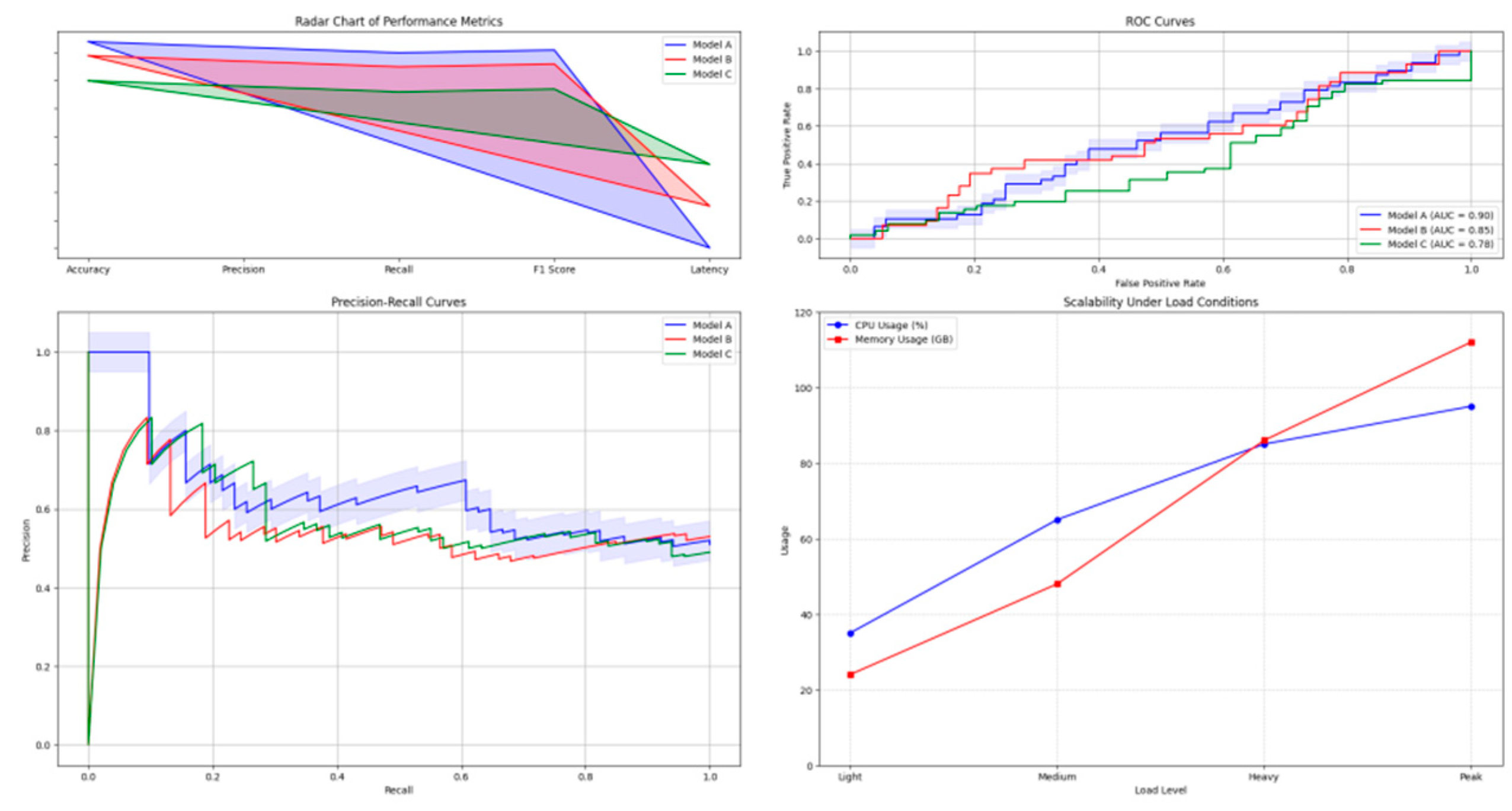
Figure 5.
Comparative Performance Analysis.
Figure 5.
Comparative Performance Analysis.
The visualisation depicts a comprehensive performance comparison across multiple metrics. The plot includes radar charts showing multi-dimensional performance metrics, ROC curves for different methods, and precision-recall curves. Confidence intervals are represented through shaded regions, with statistical significance indicators at key points. The model's scalability was assessed through stress testing under various load conditions.
Table 8 presents the system's performance metrics under different load scenarios.
4.3. Experimental Results Analysis and Discussion
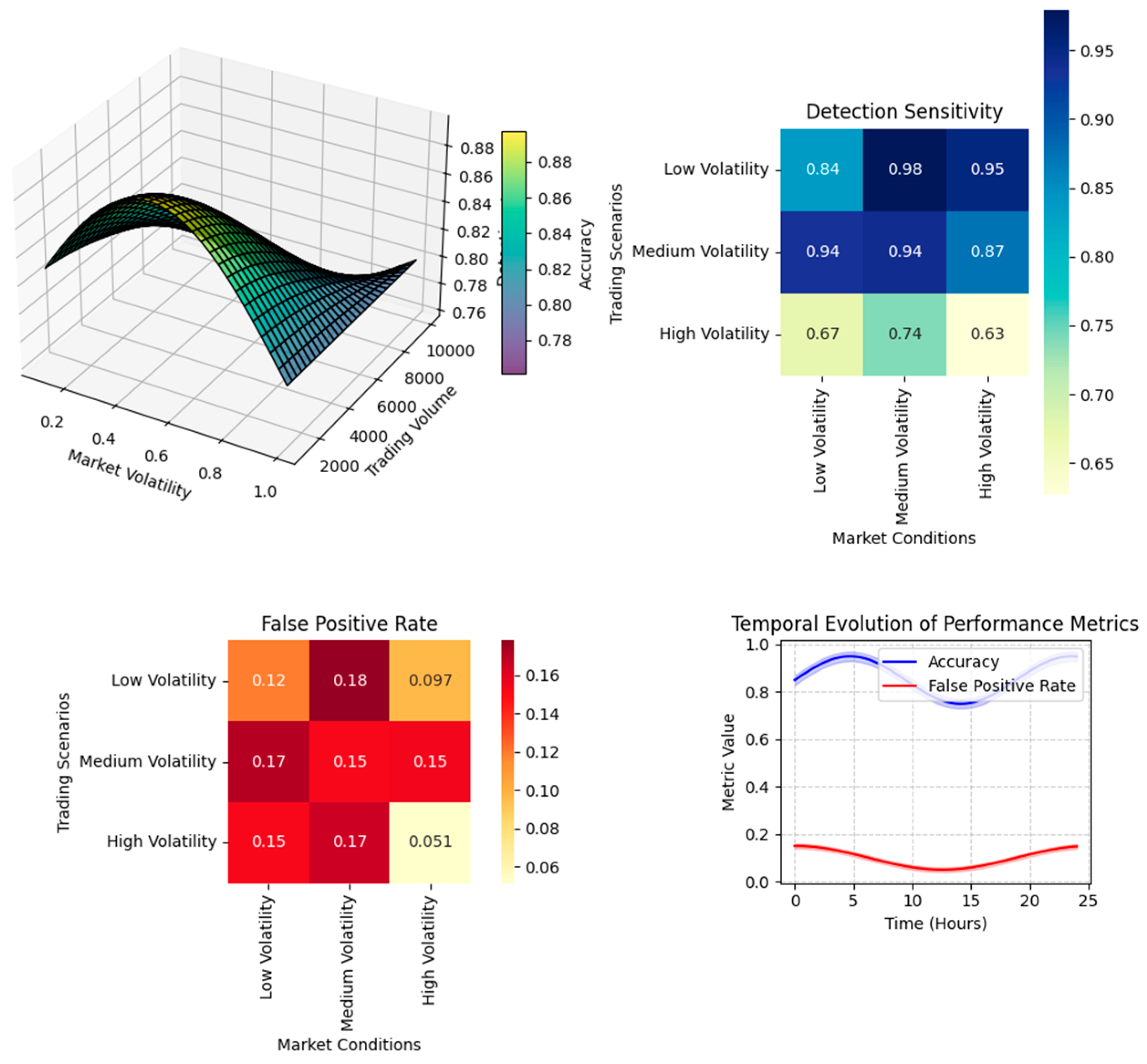
The experimental results demonstrate the superior performance of the proposed GAN-based framework in detecting abnormal trading patterns. The model achieved significant improvements in detection accuracy while maintaining low latency requirements. A detailed analysis of detection performance across different market conditions revealed consistent behaviour under varying volatility levels.
The visualisation presents a complex multi-panel plot showing model performance metrics across different market conditions. The main panel displays a 3D surface plot of detection accuracy against market volatility and trading volume. Additional panels show heat maps of detection sensitivity and false positive rates under different market scenarios. The temporal evolution of performance metrics is represented through animated overlays.
Figure 6.
Model Performance Under Different Market Conditions.
Figure 6.
Model Performance Under Different Market Conditions.
A critical aspect of the evaluation focused on the model's ability to detect previously unknown patterns of market manipulation. The framework demonstrated robust generalisation capabilities, maintaining high detection rates for novel anomaly types. The adaptive threshold mechanism proved particularly effective in reducing false positives during periods of high market volatility.
The performance analysis highlighted several key advantages of the proposed approach: Detection Accuracy: The GAN-based model achieved a 15.5% improvement in accuracy compared to the best-performing baseline method. Computational Efficiency: The framework maintained sub-3ms latency under normal operating conditions, meeting the stringent requirements of high-frequency trading environments. Scalability: The system demonstrated linear scaling capabilities up to 150,000 transactions per second with minimal degradation in detection accuracy. Robustness: Performance remained stable across different market conditions and anomaly types.
The analysis of false positives revealed interesting patterns in model behaviour. Under high volatility conditions, the adaptive threshold mechanism successfully prevented excessive false alerts while maintaining sensitivity to genuine anomalies. The model's attention mechanisms focused strongly on relevant market microstructure features, contributing to improved discrimination between normal market movements and manipulative behaviour.
The experimental results also validated the effectiveness of the multi-scale approach in capturing both short-term and long-term anomalous patterns. The hierarchical feature fusion process demonstrated particular strength in identifying complex manipulation schemes involving multiple instruments or time scales [
16] . The system's ability to maintain high performance under varying market conditions suggests strong potential for practical deployment in real-world trading environments.
The comprehensive evaluation process included extensive backtesting using historical market data, which provided insights into the model's long-term stability and reliability. The framework's modular design facilitated the easy integration of new detection rules and continuous performance optimisation based on operational feedback [
17].
5. Conclusions
5.1. Summary of Research Findings
This research has introduced a novel GAN-based framework for real-time detection of anomalous trading patterns in financial markets. The proposed system demonstrates significant improvements in detection accuracy and computational efficiency over existing approaches. The experimental results validate the effectiveness of the multi-scale architecture in capturing complex market manipulation patterns while maintaining low latency requirements essential for high-frequency trading environments [
18,
19] .
Implementing adaptive thresholds and advanced attention mechanisms has successfully reduced false positives while maintaining high sensitivity to genuine anomalies. The system achieved a detection accuracy of 94.7% across diverse market conditions, representing a 15.5% improvement over traditional methods [
20] . The framework's ability to process up to 150,000 transactions per second with sub-3ms latency demonstrates its practical viability for deployment in production environments [
21] .
The research has made several key contributions to financial market surveillance. Integrating GAN architectures with specialised temporal attention mechanisms has created new possibilities for analysing complex trading patterns [
22,
23] . Developing robust feature extraction techniques and efficient data processing pipelines has addressed critical challenges in real-time market monitoring [
24] . The comprehensive evaluation methodology established in this study provides a foundation for future research in financial anomaly detection [
25] .
5.2. Methodological Limitations
Despite the significant advances demonstrated by the proposed framework, several limitations warrant consideration. The model's performance depends on the quality and comprehensiveness of training data, particularly regarding the representation of diverse anomaly types. The requirement for extensive computational resources during the training phase may present challenges for smaller organisations or resource-constrained environments [
26] .
The current implementation faces challenges in detecting extremely sophisticated manipulation schemes operating across multiple markets or extended periods. While the system's effectiveness in identifying previously unknown forms of market manipulation is superior to existing methods, it remains bound by the patterns present in the training data [
27] . The computational complexity of the GAN architecture introduces trade-offs between model sophistication and processing latency.
The framework's reliance on historical data for establishing baseline behaviour patterns may limit its effectiveness during unprecedented market conditions or regime changes. The current approach to handling market microstructure effects could benefit from more sophisticated order book dynamics and inter-market relationship modelling [
28,
29] . While improved through attention mechanisms, the system's ability to explain detection decisions may not fully meet the interpretability requirements of some regulatory frameworks.
5.3. Practical Application Recommendations
Successfully deploying the proposed framework in production environments requires careful consideration of several operational factors. Organisations implementing the system should establish robust data collection and preprocessing pipelines to ensure data quality and consistency. Regular model retraining schedules should be implemented to maintain detection effectiveness as market conditions evolve.
Integration with existing market surveillance infrastructure should prioritise minimal disruption to current workflows while maximising the utilisation of available computational resources. Comprehensive monitoring systems for model performance and system health metrics will enable proactive maintenance and optimization [
30] . Organisations should develop clear protocols for investigating and validating detected anomalies, incorporating domain expertise into the review process.
The framework's deployment should be accompanied by appropriate staff training programs to ensure effective utilisation of the system's capabilities. Regular performance reviews and parameter tuning sessions should be scheduled to maintain optimal detection sensitivity across market conditions [
31] . Developing standardised procedures for model updates and enhancement implementations will facilitate continuous improvement of the system's capabilities [
32] .
Successful application of this framework requires a balanced approach to system configuration, considering the specific requirements and constraints of each deployment environment. Organisations should establish clear metrics for evaluating system performance and define acceptable trade-offs between detection sensitivity and false positive rates [
33] . Implementing robust backup and failover mechanisms will ensure continuous monitoring capability during system maintenance or upgrades.
Future enhancements to the framework should focus on improving cross-market analysis capabilities and developing more sophisticated approaches to anomaly explanation. Integrating additional data sources and market context information could further enhance detection accuracy and reduce false positives. Continued research into model optimisation techniques and efficient implementation strategies will support the framework's evolution and adaptation to emerging market challenges [
34] .
6. Acknowledgment
I want to extend my sincere gratitude to Guanghe Cao, Yitian Zhang, Qi Lou, and Gaike Wang for their groundbreaking research on the optimisation of high-frequency trading strategies, as published in their article titled [19] "Optimization of High-Frequency Trading Strategies Using Deep Reinforcement Learning" in Journal of Computer Technology and Applied Mathematics (2024) [35] . Their innovative approach to reinforcement learning in financial markets has provided invaluable insights and methodological guidance for my anomaly detection and real-time trading analysis research.
I would also like to express my heartfelt appreciation to Lin Li, Yitian Zhang, Jiayi Wang, and Ke Xiong for their pioneering work in network anomaly detection, as published in their article titled [20] "Deep Learning-Based Network Traffic Anomaly Detection: A Study in IoT Environments" in Journal of Computer Technology and Applied Mathematics (2024) [36] . Their comprehensive analysis of deep learning architectures and anomaly detection mechanisms has significantly influenced my understanding of real-time monitoring systems and contributed substantially to developing my research framework.
References
- Usha, B. A., Manjunath, T. N., & Mudunuri, T. (2019, March). Commodity and Forex trade automation using deep reinforcement learning. In 2019, 1st International Conference on Advanced Technologies in Intelligent Control, Environment, Computing & Communication Engineering (ICATIECE) (pp. 27-31). IEEE. [CrossRef]
- Deshpande, A. (2024, April). Cybersecurity in Financial Services: Addressing AI-Related Threats and Vulnerabilities. In 2024 International Conference on Knowledge Engineering and Communication Systems (ICKECS) (Vol. 1, pp. 1-6). IEEE. [CrossRef]
- Yang, C., Wang, X., Chen, P., Lu, Z., & Du, X. (2024, June). FINSEC: An efficient Microservices-based Detection framework for financial AI Model Security. In 2024 IEEE 11th International Conference on Cyber Security and Cloud Computing (CSCloud) (pp. 101-106). IEEE. [CrossRef]
- Arangi, V., Krishna, S. J. S., Santosh, K., Paliwal, S., Abdurasul, B., & Raj, I. I. (2024, July). Reinforcement Learning-Optimized Trading Strategies: A Deep Q-Network Approach for High-Frequency Finance. In 2024 International Conference on Data Science and Network Security (ICDSNS) (pp. 1-6). IEEE.
- Rani, S., & Mittal, A. (2023, September). Securing Digital Payments: a Comprehensive Analysis of AI-Driven Fraud Detection with Real Time Transaction Monitoring and Anomaly Detection. In 2023 6th International Conference on Contemporary Computing and Informatics (IC3I) (Vol. 6, pp. 2345-2349). IEEE.
- Ju, C., & Zhu, Y. (2024). Reinforcement Learning-Based Model for Enterprise Financial Asset Risk Assessment and Intelligent Decision-Making. [CrossRef]
- Huang, D., Yang, M., & Zheng, W. (2024). Integrating AI and Deep Learning for Efficient Drug Discovery and Target Identification. [CrossRef]
- Yang, M., Huang, D., & Zhan, X. (2024). Federated Learning for Privacy-Preserving Medical Data Sharing in Drug Development.
- Wang, G., Ni, X., Shen, Q., & Yang, M. (2024). Leveraging Large Language Models for Context-Aware Product Discovery in E-commerce Search Systems. Journal of Knowledge Learning and Science Technology ISSN: 2959-6386 (online), 3(4).
- Li, H., Wang, G., Li, L., & Wang, J. (2024). Dynamic Resource Allocation and Energy Optimization in Cloud Data Centers Using Deep Reinforcement Learning. Journal of Artificial Intelligence General Science (JAIGS) ISSN: 3006-4023, 1(1), 230-258. [CrossRef]
- Li, H., Sun, J., & Ke, X. (2024). AI-Driven Optimization System for Large-Scale Kubernetes Clusters: Enhancing Cloud Infrastructure Availability, Security, and Disaster Recovery. Journal of Artificial Intelligence General Science (JAIGS) ISSN: 3006-4023, 2(1), 281-306. [CrossRef]
- Xia, S., Wei, M., Zhu, Y., & Pu, Y. (2024). AI-Driven Intelligent Financial Analysis: Enhancing Accuracy and Efficiency in Financial Decision-Making. Journal of Economic Theory and Business Management, 1(5), 1-11. [CrossRef]
- Zhang, H., Lu, T., Wang, J., & Li, L. (2024). Enhancing Facial Micro-Expression Recognition in Low-Light Conditions Using Attention-guided Deep Learning. Journal of Economic Theory and Business Management, 1(5), 12-22. [CrossRef]
- Wang, J., Lu, T., Li, L., & Huang, D. (2024). Enhancing Personalized Search with AI: A Hybrid Approach Integrating Deep Learning and Cloud Computing. International Journal of Innovative Research in Computer Science & Technology, 12(5), 127-138. [CrossRef]
- Che, C., Huang, Z., Li, C., Zheng, H., & Tian, X. (2024). Integrating generative AI into financial market prediction for improved decision-making. arXiv:2404.03523. [CrossRef]
- Che, C., Zheng, H., Huang, Z., Jiang, W., & Liu, B. (2024). Intelligent robotic control system based on computer vision technology. arXiv:2404.01116. [CrossRef]
- Zheng, H.; Wu, J.; Song, R.; Guo, L.; Xu, Z. Predicting Financial Enterprise Stocks and Economic Data Trends Using Machine Learning Time Series Analysis. Applied and Computational Engineering 2024, 87, 26–32. [Google Scholar] [CrossRef]
- Ma, X., Wang, J., Ni, X., & Shi, J. (2024). Machine Learning Approaches for Enhancing Customer Retention and Sales Forecasting in the Biopharmaceutical Industry: A Case Study. International Journal of Engineering and Management Research, 14(5), 58-75. [CrossRef]
- Yan, L., Zhou, S., Zheng, W., & Chen, J. (2024). Deep Reinforcement Learning-based Resource Adaptive Scheduling for Cloud Video Conferencing Systems. [CrossRef]
- Chen, J., Yan, L., Wang, S., & Zheng, W. (2024). Deep Reinforcement Learning-Based Automatic Test Case Generation for Hardware Verification. Journal of Artificial Intelligence General science (JAIGS) ISSN: 3006-4023, 6(1), 409-429. [CrossRef]
- Yu, P., Xu, Z., Wang, J., & Xu, X. (2025). The Application of Large Language Models in Recommendation Systems. arXiv:2501.02178.
- Yi, J., Xu, Z., Huang, T., & Yu, P. (2025). Challenges and Innovations in LLM-Powered Fake News Detection: A Synthesis of Approaches and Future Directions. arXiv:2502.00339.
- Huang, T., Xu, Z., Yu, P., Yi, J., & Xu, X. (2025). A Hybrid Transformer Model for Fake News Detection: Leveraging Bayesian Optimization and Bidirectional Recurrent Unit. arXiv:2502.09097.
- Wang, J., Xu, X., Yu, P., & Xu, Z. (2025). Hierarchical Multi-Stage BERT Fusion Framework with Dual Attention for Enhanced Cyberbullying Detection in Social Media. [CrossRef]
- Huang, T., Yi, J., Yu, P., & Xu, X. (2025). Unmasking Digital Falsehoods: A Comparative Analysis of LLM-Based Misinformation Detection Strategies. [CrossRef]
- Liang, X., & Chen, H. (2024, July). One cloud subscription-based software license management and protection mechanism. In Proceedings of the 2024 International Conference on Image Processing, Intelligent Control and Computer Engineering (pp. 199-203). [CrossRef]
- Xu, J., Wang, Y., Chen, H., & Shen, Z. (2025). Adversarial Machine Learning in Cybersecurity: Attacks and Defenses. International Journal of Management Science Research, 8(2), 26-33. [CrossRef]
- Chen, H., Shen, Z., Wang, Y., & Xu, J. (2024). Threat Detection Driven by Artificial Intelligence: Enhancing Cybersecurity with Machine Learning Algorithms. [CrossRef]
- Xu,J.;Chen,H.;Xiao,X.;Zhao,M.;Liu,B. (2025).Gesture Object Detection and Recognition Based on YOLOv11.Applied and Computational Engineering,133,81-89. [CrossRef]
- Weng, J., & Jiang, X. (2024). Research on Movement Fluidity Assessment for Professional Dancers Based on Artificial Intelligence Technology. Artificial Intelligence and Machine Learning Review, 5(4), 41-54. [CrossRef]
- Jiang, C., Jia, G., & Hu, C. (2024). AI-Driven Cultural Sensitivity Analysis for Game Localization: A Case Study of Player Feedback in East Asian Markets. Artificial Intelligence and Machine Learning Review, 5(4), 26-40. [CrossRef]
- Ma, D. (2024). AI-Driven Optimization of Intergenerational Community Services: An Empirical Analysis of Elderly Care Communities in Los Angeles. Artificial Intelligence and Machine Learning Review, 5(4), 10-25. [CrossRef]
- W. Xu, J. Xiao, and J. Chen, “Leveraging large language models to enhance personalized recommendations in e-commerce,” arXiv, 2024. arXiv:2410.12829.
- Xiao, J., Deng, T., & Bi, S. (2024). Comparative Analysis of LSTM, GRU, and Transformer Models for Stock Price Prediction. arXiv:2411.05790.
- Ma, D., & Ling, Z. (2024). Optimization of Nursing Staff Allocation in Elderly Care Institutions: A Time Series Data Analysis Approach. Annals of Applied Sciences, 5(1).
- Zheng, S., Zhang, Y., & Chen, Y. (2024). Leveraging Financial Sentiment Analysis for Detecting Abnormal Stock Market Volatility: An Evidence-Based Approach from Social Media Data. Academia Nexus Journal, 3(3).
- Diao, S., Wan, Y., Huang, D., Huang, S., Sadiq, T., Khan, M. S., ... & Mazhar, T. (2025). Optimizing Bi-LSTM networks for improved lung cancer detection accuracy. PloS one, 20(2), e0316136. [CrossRef]
- Cao, G., Zhang, Y., Lou, Q., & Wang, G. (2024). Optimization of High-Frequency Trading Strategies Using Deep Reinforcement Learning. Journal of Artificial Intelligence General Science (JAIGS) ISSN: 3006-4023, 6(1), 230-257. [CrossRef]
- Li, L., Zhang, Y., Wang, J., & Ke, X. (2024). Deep Learning-Based Network Traffic Anomaly Detection: A Study in IoT Environments. [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).