Submitted:
18 April 2025
Posted:
18 April 2025
You are already at the latest version
Abstract
Keywords:
1. INTRODUCTION
Statement of Problem:
Objective:
2. LETRATURE REVIEW
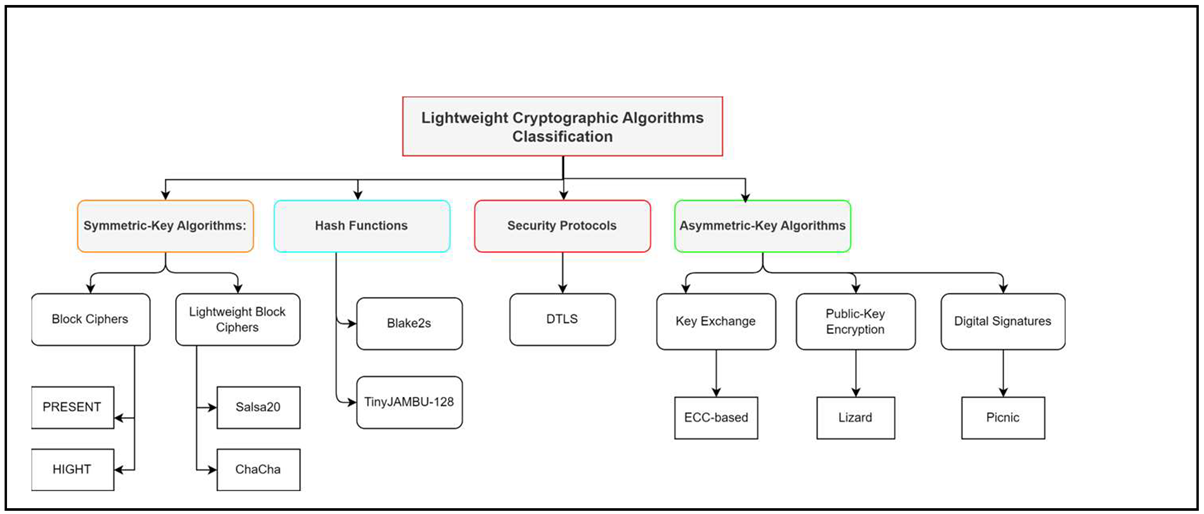
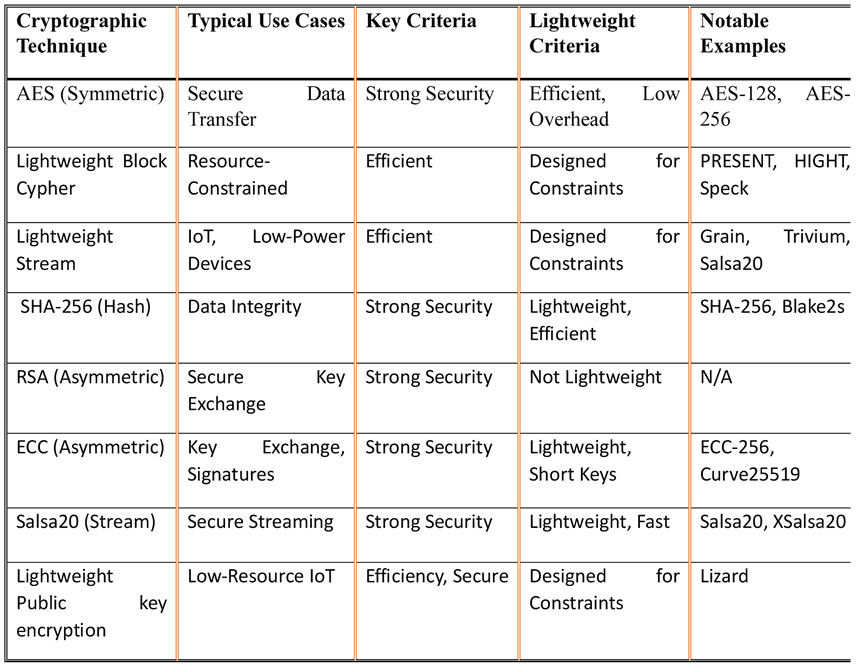
Lightweight Cryptographic (LWC)
| Algorithm | Description |
|---|---|
| AES | Block cipher encryption is a substitution-permutation network, and the number of rounds and key size have a significant impact on how safe the technique is. |
| DSS | It generates digital signatures using the Digital Signature Algorithm (DSA) and the SHA-2 family of hash functions. |
| Diffie-Hellman | To create a secret key that is shared between two parties across an unsecure channel, asymmetric key exchange method is employed. It serves as the basis for many cryptographic protocols' safe key exchange. |
| SHA-2 | SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, and SHA-512/256 are among the hash functions in the family that are constructed using the Merkl-Damgard construction. |
| SHA-3 | "Sponge construction" is used to build the hash function. A function called sponge creation may take any bit stream as input and produce an output bit stream with any length that is needed. |
| RSA | It is an asymmetric encryption method utilized for safe exchange of keys and digital signatures. RSA key pairs are made up of a key that is publicly accessible and a private key. |
| Speck | Block cipher encryption method, which functions similarly to ChaCha and has been fine-tuned for software implementation performance |
| Elliptic Curve Cryptography | This digital signature and asymmetric encryption technique makes use of elliptic curve mathematics. Comparing with other asymmetric algorithms, ECC provides good security with lower key lengths, making it appropriate for situations with limited resources. |
| Blowfish | It is a fast and straightforward symmetric-key block cipher. Even though it is thought to be safe, AES is now more frequently utilized instead of it. |
| 3DES | an encryption system using symmetric keys that cascades using the Data Encryption Standard (DES) algorithm three times. It is still employed in older systems since it was intended to offer a better level of security than DES. |
| HMAC | a construction for employing a cryptographic hash function (SHA-256, for example) to generate a message authentication code. It is frequently employed for authentication and data integrity verification. |
| ChaCha | encryption system known as stream cipher, whose round operations are limited to modular addition, rotation, and xor |
| RC4 | a symmetric stream cipher which was often employed in the past for wireless encryption and secure sockets layer (SSL). Nevertheless, it is now widely regarded as outdated and contains known weaknesses. |
| ECDSA | utilized in instances with asymmetric keys for digital signatures |
| zk-SNARKs | enable one party to prove possession of specific information without revealing the information itself. |
| MPC | allow different parties to collaborate on computing a result over the inputs they provide while maintaining the privacy of those inputs |
| Fully Homomorphic Encryption (FHE) | performs actions on encrypted data such as addition and multiplication. This sophisticated encryption method can handle increasingly intricate calculations while protecting the privacy of data. |
| Blockchain-Based Cryptography | Drone communication could gain from the integration of blockchain technology for safe and transparent data integrity verification, authentication, and logging. Frequently employed in blockchain-based systems are algorithms such as the Elliptic Curve Digital Signature Algorithm (ECDSA). |
| Hash-Based Signatures | Some signature schemes, like the Lamport and Merkle schemes, are considered into consideration because they can resist quantum attacks. They are involved in the PQC project at NIST. |
2.1. Typical Applications
2.2. Communication Interfaces
2.3. Drone Interfaces
3. PROPOSED METHODOLOGY
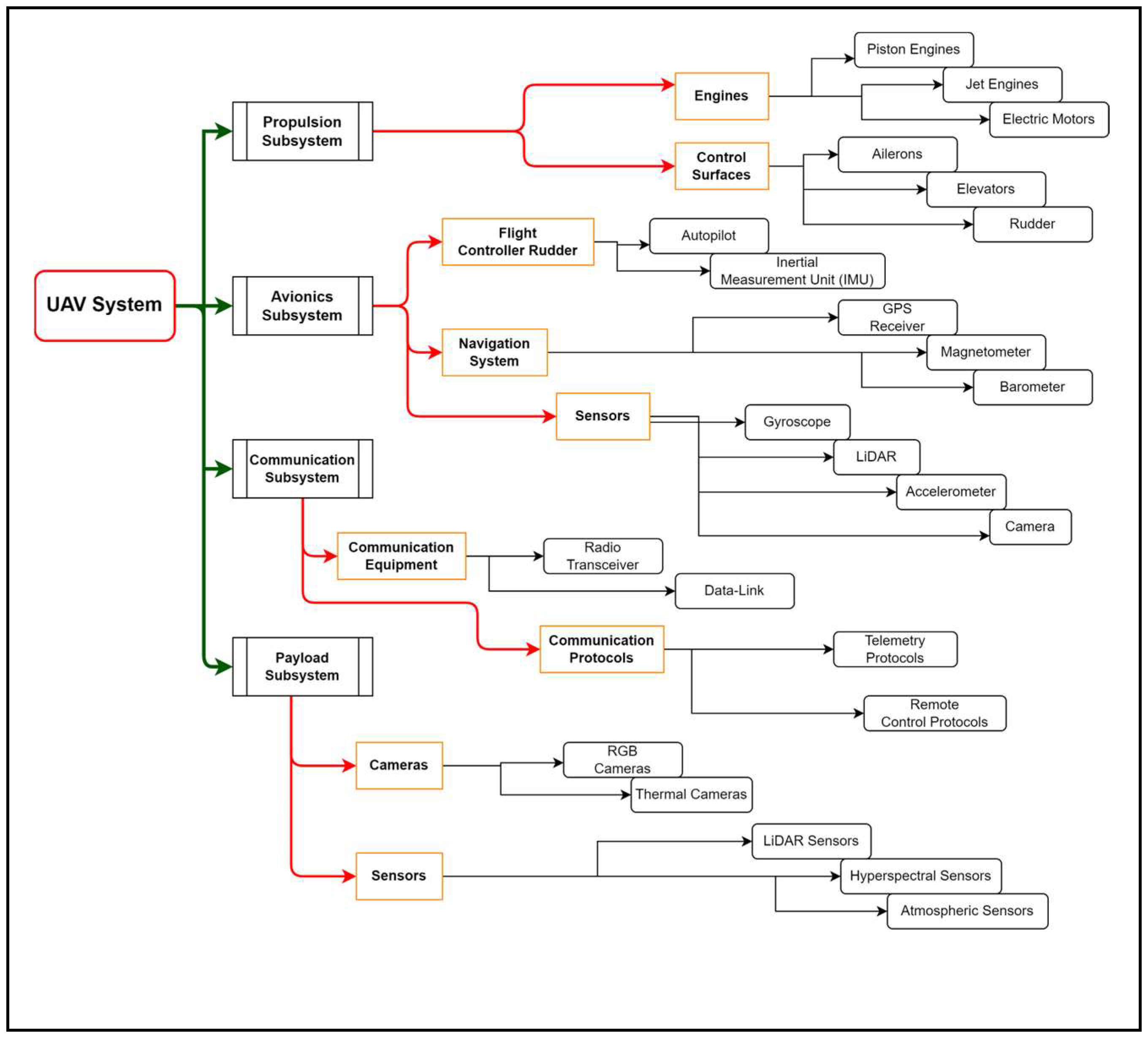
3.1. Unmanned Aerial Vehicles
3.2. State of the Art About UAV Subsystem
3.3. Cryptography Techniques:
3.3.1. Diffie–Hellman Key Exchange Protocol
| Alice | Bob |
| Public Keys available = P, G | Public Keys available = P, G |
| Private Key Selected = a | Private Key Selected = b |
| Key generated = GA modP | Key generated = Gb modP |
| Exchange of generated keys takes place | |
| Key received = y | key received = x |
|
Generated Secret Key = Ka = Ya modP |
Generated Secret Key = Kb = Yb modP |
|
Algebraically, it can be shown that Ka = Kb | |
| Users now have a symmetric secret key to encrypt | |
| Algorithm 1: The Diffie-Hellman key exchange |
 |
3.3.2. RSA Algorithm (Non-Quantum-Safe Public-Key Cryptography):
3.3.3. Lattice-Based Cryptography (Why not Included in the Table Above?)
3.3.4. Hash-Based Authentication (Quantum-Safe Cryptography):
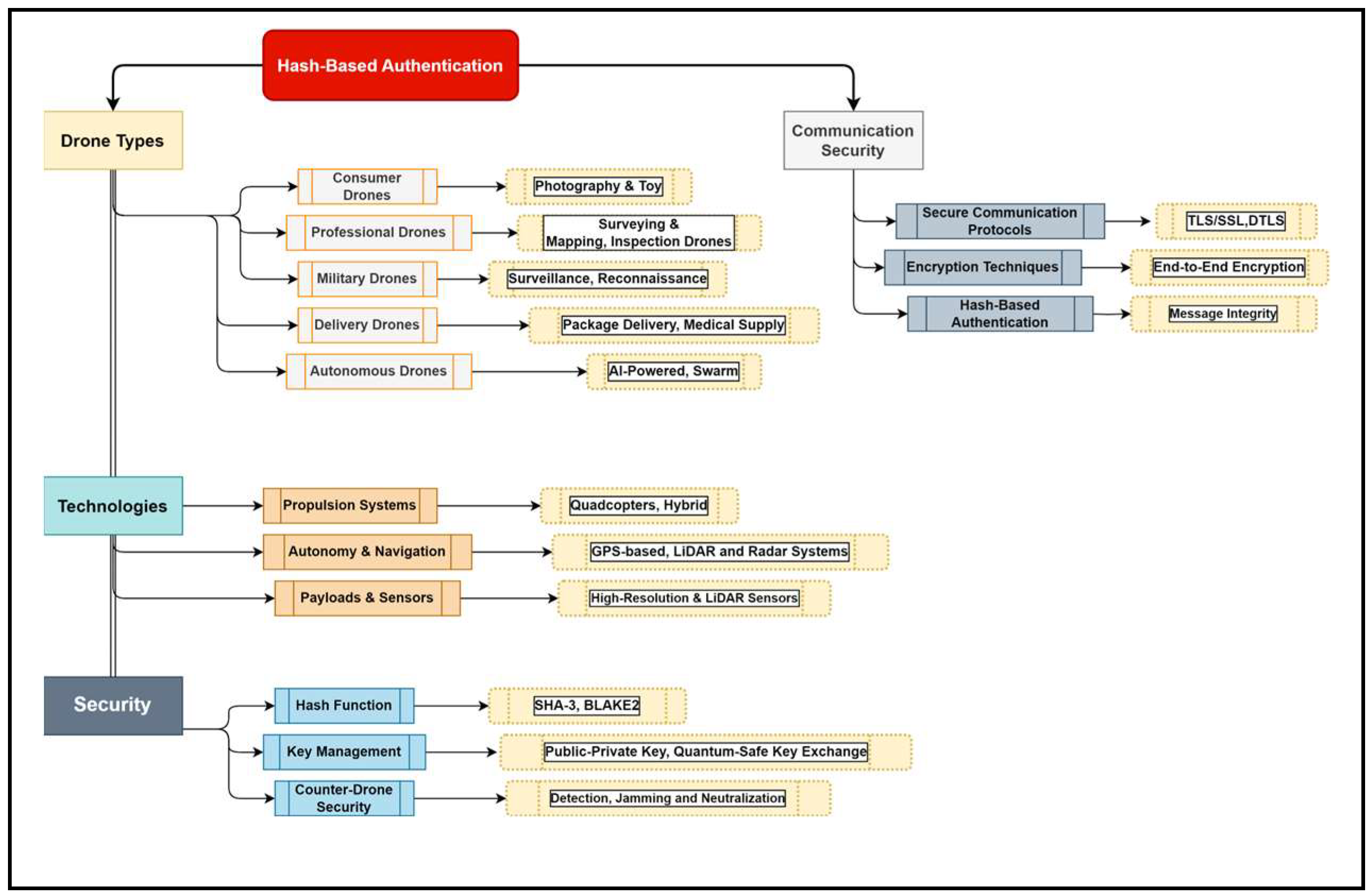
4. RESULTS AND DISCUSSIONS
4.1. Overview of the Main Findings
4.1.2. UAV Authentication Protocols
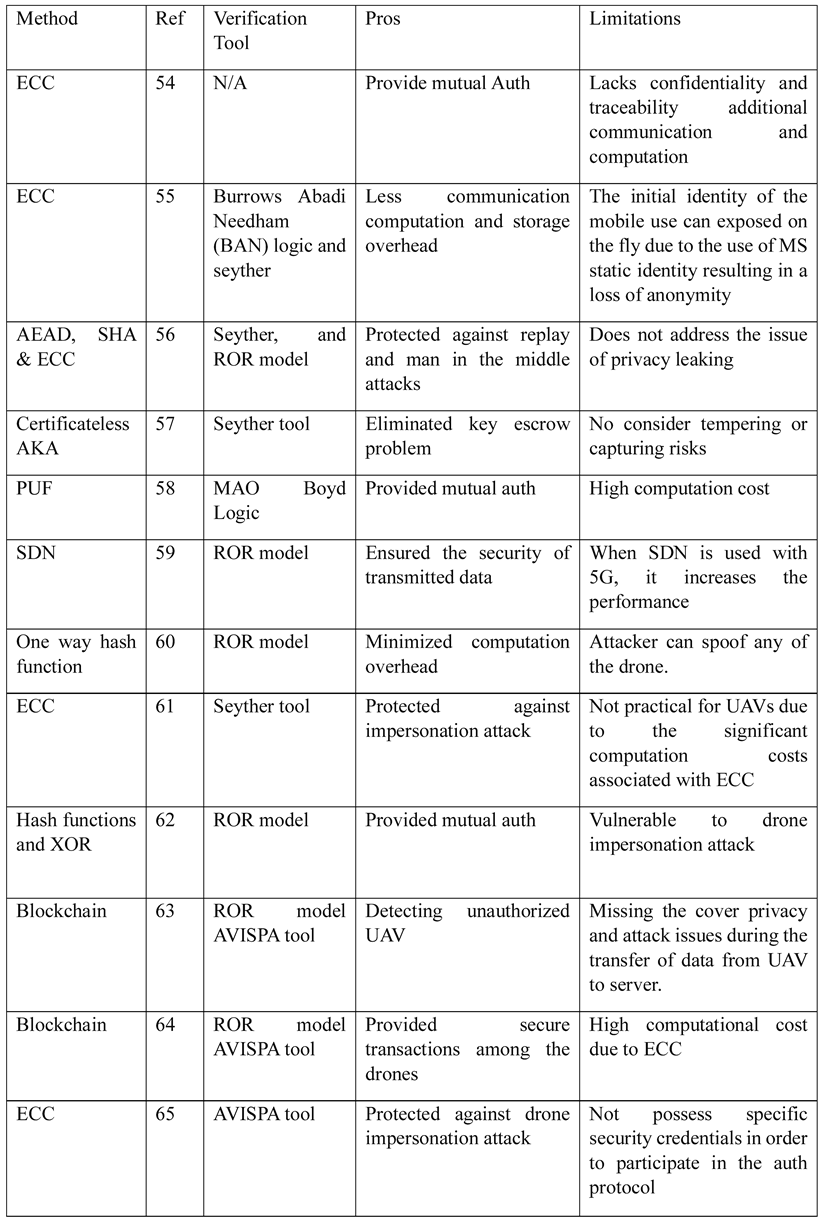
4.1.3. Implementation (UAV’s Communication Systems)
4.1.3.1. Hardware (HW)
4.1.3.1.1. FPGA
4.1.3.1.2. ASIC:
4.1.3.2. Software (SW):
4.1.3.3. Hybrid:
4.1.3.3.1. Microcontroller + FPGA/DSP:
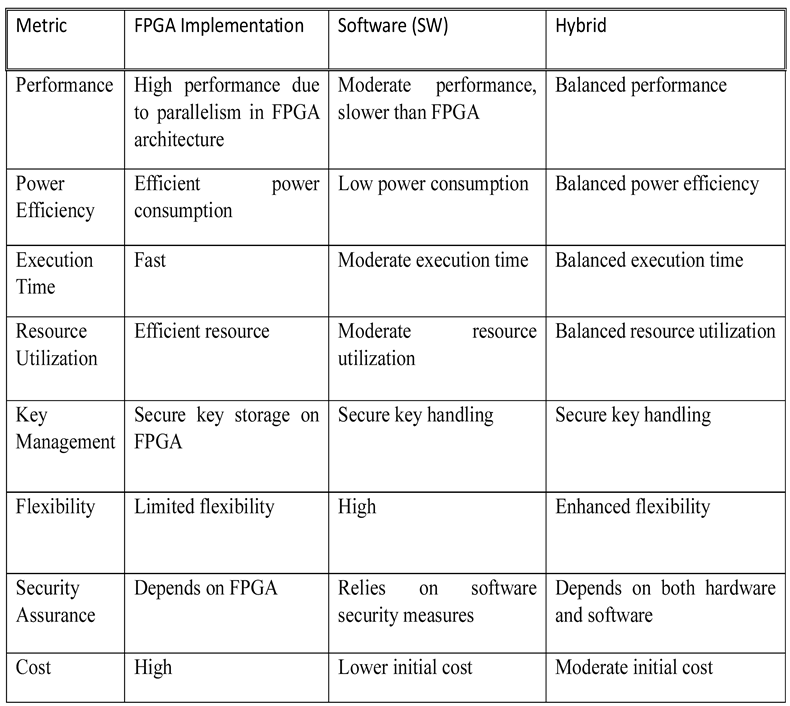
4.2. Elliptic Curve Cryptography
5. FUTURE DISCUSSIONS
CONCLUSION
References
- Hammi, M.T.; Hammi, B.; Bellot, P.; Serhrouchni, A. Bubbles of trust: A decentralized blockchain-based authentication system for IoT. Comput. Security 2018, 78, 126–142. [Google Scholar] [CrossRef]
- Alur, R.; et al. Systems computing challenges in the Internet of Things. arXiv 2016, arXiv:1604.02980. [Google Scholar]
- Sherali Zeadally, Ashok Kumar Das, Nicolas Sklavos. Cryptographic technologies and protocol standards for Internet of Things. Elsevier 2019, pp 1-11. [CrossRef]
- Kawle, P.; Hiwase, A.; Bagde, G.; Tekam, E.; Kalbande, R. Modified Advanced Encryption Standard. International Journal of Soft Computing and Engineering 2014, PP 1-3.
- Paulo S. L. M. Barreto, Marcos A. Simplicio Jr., "CURUPIRA, a block cipher for constrained platforms", SBRC 2007, pp 61-75.
- Bogdanov, L.R. Knudsen, G. Leander, C. Paar, A. Poschmann, "PRESENT: An Ultra-Lightweight Block Cipher", Springer 2007, pp 450-466.
- Guo, J.; Peyrin, T.; Poschmann, A.; Robshaw, M. The LED Block Cipher. International Association for Crypto logic Research 2011, pp 326-341. [CrossRef]
- KP, B. M., & Patwari, N. (2023, April). Embedded Light-Weight Cryptography Technique to Preserve Privacy of Healthcare Wearable IoT Device Data. In 2023 International Conference on Distributed Computing and Electrical Circuits and Electronics (ICDCECE) (pp. 1-6). IEEE.
- Zhang, W.; Bao, Z.; Lin, D.; Rijmen, V.; Yang, B. RECTANGLE: A Bit-slice Lightweight Block Cipher Suitable for Multiple Platforms. Springer 2015, pp 1-15. [CrossRef]
- Dinu, D.; Perrin, L.; Udovenko, A.; Velichkov, V.; Grosschad, J.; Biryukov, A. Design Strategies for ARX with Provable Bounds: Sparx and LAX. Springer 2016, pp 1-40.
- Muhammad Usman, Irfan Ahmed, M. Imran Aslam, Shujaat Khan and Usman Ali Shah, "SIT: A Lightweight Encryption Algorithm for Secure Internet of Things”, ARXIV, 2017, pp 1-10.
- Yang, X.; et al. Blockchain-Based Secure and Lightweight Authentication for Internet of Things. IEEE Internet of Things Journal 2022, 9, 3321–3332. [Google Scholar] [CrossRef]
- Khan, M.N.; Rao, A.; Camtepe, S. Lightweight cryptographic protocols for IoT-constrained devices: A survey. IEEE Internet of Things Journal 2020, 8, 4132–4156. [Google Scholar] [CrossRef]
- Lam, T. N., and Le, D. H. (2022, October). Implementation of Lightweight Cryptography Core PRESENT and DM-PRESENT on FPGA. In 2022 International Conference on Advanced Technologies for Communications (ATC) (pp. 104-109). IEEE.
- Zitouni, N., Sedrati, M., and Behaz, A. (2022, April). Comparing lightweight algorithms to secure constrained objects in internet of things. In New Realities, Mobile Systems and Applications: Proceedings of the 14th IMCL Conference (pp. 1040-1051). Cham: Springer International Publishing.
- Windarta, S.; Suryadi, S.; Ramli, K.; Pranggono, B.; Gunawan, T.S. Lightweight Cryptographic Hash Functions: Design Trends, Comparative Study, and Future Directions. IEEE Access 2022, 10, 82272–82294. [Google Scholar] [CrossRef]
- F. Abbas, X. Yuan, M. S. Bute, and P. Fan, “Performance analysis using full duplex discovery mechanism in 5G-V2X communication networks,” IEEE Trans. Intell. Transp. Syst., to be published. [CrossRef]
- Liao, S.; Wu, J.; Mumtaz, S.; Li, J.; Morello, R.; Guizani, M. Cognitive balance for fog computing resource in Internet of Things: An edge learning approach. IEEE Trans. Mobile Comput. 2022, 21, 1596–1608. [Google Scholar] [CrossRef]
- Wang, T.; Ke, H.; Zheng, X.; Wang, K.; Sangaiah, A.K.; Liu, A. Big data cleaning based on mobile edge computing in industrial sensor-cloud. IEEE Trans. Ind. Informat. 2020, 16, 1321–1329. [Google Scholar] [CrossRef]
- Bastami, H.; Letafati, M.; Moradikia, M.; Abdelhadi, A.; Behroozi, H.; Hanzo, L. On the physical layer security of the cooperative rate-splitting aided downlink in uav networks. IEEE Transactions on Information Forensics and Security, 2021. [CrossRef]
- Chen, L.; Qian, S.; Lim, M.; Wang, S. An enhanced direct anonymous attestation scheme with mutual authentication for network-connected UAV communication systems. China Communications 2018, 15, 61–76. [Google Scholar] [CrossRef]
- Jalan, A.; Matkovskyy, R.; Urquhart, A. What effect did the introduction of Bitcoin futures have on the Bitcoin spot market? Eur. J. Financ. 2021, 27, 1251–1281. [Google Scholar] [CrossRef]
- Hakak, S.; Khan, W.Z.; Gilkar, G.A.; Imran, M.; Guizani, N. Securing smart cities through blockchain technology: Architecture, requirements, and challenges. IEEE Netw. 2020, 34, 8–14. [Google Scholar] [CrossRef]
- Oliva, G.A.; Hassan, A.E.; Jiang, Z.M.J. An exploratory study of smart contracts in the Ethereum blockchain platform. Empir. Softw. Eng. 2020, 25, 1864–1904. [Google Scholar] [CrossRef]
- Tran, J.A.; Ramachandran, G.S.; Shah, P.M.; Danilov, C.B.; Santiago, R.A.; Krishnamachari, B. Swarmdag: A partition tolerant distributed ledger protocol for swarm robotics. Ledger 2019, 4, 25–31. [Google Scholar] [CrossRef]
- Chen, W., Y. Dong and Z. Duan. Manipulating Drone Position Control. 2019 IEEE Conference on Communications and Network Security (CNS), Washington DC, DC, USA, 2019, pp. 1-9. [CrossRef]
- Putranto, D.S.C., A. K. Aji and B. Wahyudono. Design and Implementation of Secure Transmission on Internet of Drones. 2019 IEEE 6th Asian Conference on Defence Technology (ACDT), Bali, Indonesia, 2019, pp. 128-135. [CrossRef]
- Alladi, T.; Venkatesh, V.; Chamola, V.; Chaturvedi, N. Drone-MAP: A. novel authentication scheme for drone-assisted 5G networks. in Proc. IEEE INFOCOM Conf. Comput. Commun. Workshops, 2021, pp. 1–6.
- Teng, L. et al. Lightweight security authentication mechanism towards UAV networks. in Proc. Int. Conf. Netw. Appl., 2019, pp. 379–384.
- Gope, P.; Sikdar, B. An efficient privacy-preserving authenticated key agreement scheme for edge-assisted internet of drones. IEEE Trans. Veh. Technol. 2020, 69, 13621–13630. [Google Scholar] [CrossRef]
- C. Pu and Li, Y. Lightweight authentication protocol for unmanned aerial vehicles using physical unclonable function and chaotic system. in Proc. IEEE Int. Symp. Local Metrop. Area Netw., 2020, pp. 1–6.
- Tan, Y.; Liu, J.; Nei, K. Blockchain-Based Key Management for Heterogeneous Flying Ad Hoc Network. IEEE Trans. Industrial Informatics 2021, 17, 7629–7638. [Google Scholar] [CrossRef]
- Li, X.; et al. Blockchain-Based Mutual-Healing Group Key Distribution Scheme in Unmanned Aerial Vehicles Ad-Hoc Network. IEEE Trans. Vehic. Tech. 2019, 68, 11309–111322. [Google Scholar] [CrossRef]
- Feng, C.; et al. Blockchain-Based Cross-Domain Authentication for Intelligent 5G-Enabled Internet of Drones. IEEE Internet of Things J. 2022, 9, 6224–6938. [Google Scholar] [CrossRef]
- Zhang, N.; Jiang, Q.; Li, L.; Ma, X.; Ma, J. An efficient three-factor remote user authentication protocol based on BPV-FourQ for internet of drones. Peer-to-Peer Networking and Applications 2021, 14, 3319–3332. [Google Scholar] [CrossRef]
- Bera, B.; Saha, S.; Das, A.; Kumar, N.; Lorenz, P.; Alazab, M. Blockchain-Envisioned Secure Data Delivery and Collection Scheme for 5G-Based IoT-Enabled Internet of Drones Environment. IEEE Trans. Veh. Technol. 2020, 69, 9097–9111. [Google Scholar] [CrossRef]
- Feng, C.; Liu, B.; Guo, Z.; Yu, K.; Qin, Z.; Choo, K. Blockchainbased Cross-domain Authentication for Intelligent 5G-enabled Internet of Drones. IEEE Internet Things J. 2022, 9, 6224–6238. [Google Scholar] [CrossRef]
- Wilson, L.; Constantine, R.; van der Boon, T.; Radford, C.A. Using timelapse cameras and machine learning to enhance acoustic monitoring of small boat sound. Ecological Indicators 2022, 142, 109182. [Google Scholar] [CrossRef]
- Khan, M.; Bhunia, S.; Yuksel, M.; Kane, L.C. Line-of-sight discovery in 3D using highly directional transceivers. IEEE Transactions on Mobile Computing 2018, 18, 2885–2898. [Google Scholar] [CrossRef]
- Wang, J.; Jiang, C.; Kuang, L. High-mobility satellite-UAV communications: Challenges, solutions, and future research trends. IEEE Communications Magazine 2022, 60, 38–43. [Google Scholar] [CrossRef]
- Geraci, G.; Garcia-Rodriguez, A.; Azari, M.M.; Lozano, A.; Mezzavilla, M.; Chatzinotas, S.; Di Renzo, M. What will the future of UAV cellular communications be? A flight from 5G to 6G. IEEE communications surveys & tutorials 2022, 24, 1304–1335. [Google Scholar]
- Zhang, C.; Zou, Y.; Wang, F.; del Rey Castillo, E.; Dimyadi, J.; Chen, L. Towards fully automated unmanned aerial vehicle-enabled bridge inspection: Where are we at? Construction and Building Materials 2022, 347, 128543. [Google Scholar] [CrossRef]
- Chen, G.; Chen, G. A Method of Relay Node Selection for UAV Cluster Networks Based on Distance and Energy Constraints. Sustainability 2022, 14, 16089. [Google Scholar] [CrossRef]
- Lu, R.R.; Wang, J.Y.; Fu, X.T.; Lin, S.H.; Wang, Q.; Zhang, B. Performance analysis and optimization for UAV-based FSO communication systems. Physical Communication 2022, 51, 101594. [Google Scholar] [CrossRef]
- Tu, C.; Shen, J.; Dai, J.; Zhang, L.; Wang, J. A lower size, weight acquisition and tracking system for airborne quantum communication. IEEE Photonics Journal 2022, 14, 1–8. [Google Scholar] [CrossRef]
- Gupta, L.; Jain, R.; Vaszkun, G. Survey of important issues in UAV communication networks. IEEE communications surveys & tutorials 2015, 18, 1123–1152. [Google Scholar]
- Li, C.T.; Cheng, J.C.; Chen, K. Top 10 technologies for indoor positioning on construction sites. Automation in Construction 2020, 118, 103309. [Google Scholar] [CrossRef]
- Jan, S.U.; Qayum, F.; Khan, H.U. Design and Analysis of Lightweight Authentication Protocol for Securing IoD. IEEE Access 2021, 9, 69287–69306. [Google Scholar] [CrossRef]
- Deebak, B.D.; Al-Turjman, F. A smart lightweight privacy preservation scheme for IoT-based UAV communication systems. Comput. Commun. 2020, 162, 102–117. [Google Scholar] [CrossRef]
- Abdalla, M.; Fouque, P.A.; Pointcheval, D. Password-based authenticated key exchange in the three-party setting. In Proceedings of the 8th International Workshop on Public Key Cryptography, Les Diablerets, Switzerland, 23–26 January 2005; Volume 3386. [Google Scholar]
- Hu, F.; Qian, H.; Liu, L. A Random Label and Lightweight Hash-Based Security Authentication Mechanism for a UAV Swarm. Wirel. Commun. Mob. Comput. 2021, 2021, 6653883. [Google Scholar] [CrossRef]
- Alladi, T.; Venkatesh, V.; Chamola, V.; Chaturvedi, N. Drone-MAP: A. novel authentication scheme for drone-assisted 5G networks. in Proc. IEEE INFOCOM Conf. Comput. Commun. Workshops, 2021, pp. 1–6.
- Gope, P.; Sikdar, B. An efficient privacy-preserving authenticated key agreement scheme for edge-assisted internet of drones. IEEE Trans. Veh. Technol. 2020, 69, 13621–13630. [Google Scholar] [CrossRef]
- Ever, Y.K. A secure authentication scheme framework for mobilesinks used in the Internet of Drones applications. Comput. Commun. 2020, 155, 143–149. [Google Scholar] [CrossRef]
- Tanveer, M.; Zahid, A.H.; Ahmad, M.; Baz, A.; Alhakami, H. LAKEIoD: Lightweight authenticated key exchange protocol for the internet of drone environment. IEEE Access 2020, 8, 155645–155659. [Google Scholar] [CrossRef]
- Tanveer, M.; Khan, A.U.; Kumar, N.; Hassan, M.M. RAMP-IoD: A robust authenticated key management protocol for the Internet of Drones. IEEE Internet Things J. 2022, 9, 1339–1353. [Google Scholar] [CrossRef]
- Semal, B.; Markantonakis, K.; Akram, R.N. A certificateless group authenticated key agreement protocol for secure communication in untrusted UAV networks. in Proc. IEEE/AIAA 37th Digit. Avionics Syst. Conf., 2018.
- Alladi, T.; Naren; Bansal, G.; Chamola, V.; Guizani, M. SecAuthUAV: A novel authentication scheme for UAV-ground station and UAV-UAV communication. IEEE Trans. Veh. Technol. 2020, 69, 15068–15077. [Google Scholar] [CrossRef]
- Zhang, Y.; He, D.; Li, L.; Chen, B. A lightweight authentication and key agreement scheme for Internet of Drones. Comput. Commun. 2020, 154, 455–464. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Kumar, N.; Rodrigues, J.J.P.C. TCALAS: Temporal credential-based anonymous lightweight authentication scheme for Internet of Drones environment. IEEE Trans. Veh. Technol. 2019, 68, 6903–6916. [Google Scholar] [CrossRef]
- Nikooghadam, M.; Amintoosi, H.; Islam, S.H.; Moghadam, M.F. A provably secure and lightweight authentication scheme for Internet of Drones for smart city surveillance. J. Syst. Architecture 2021, 115. [Google Scholar] [CrossRef]
- Zhang, Y.; He, D.; Li, L.; Chen, B. A lightweight authentication and key agreement scheme for Internet of Drones. Comput. Commun. 2020, 154, 455–464. [Google Scholar] [CrossRef]
- Son, S.; Lee, J.; Park, Y.; Park, Y.; Das, A.K. Design of blockchain-based lightweight V2I handover authentication protocol for VANET. IEEE Trans. Netw. Sci. Eng. 2022, 9, 1346–1358. [Google Scholar] [CrossRef]
- Bera, B.; Saha, S.; Das, A.K.; Kumar, N.; Lorenz, P.; Alazab, M. Blockchain-envisioned secure data delivery and collection scheme for 5G-based IoT-enabled Internet of Drones environment. IEEE Trans. Veh. Technol. 2020, 69, 9097–9111. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V.; Rodrigues, J.J.P.C. Design and analysis of secure lightweight remote user authentication and key agreement scheme in Internet of Drones deployment. IEEE Internet Things J. 2019, 6, 3572–3584. [Google Scholar] [CrossRef]
- Jan, S.U.; Qayum, F.; Khan, H.U. Design and analysis of lightweight authentication protocol for securing IoD. IEEE Access 2021, 9, 69287–69306. [Google Scholar] [CrossRef]
- Rana, M.U.; Ali Shah, M.; Ellahi, O. Malware Persistence and Obfuscation: An Analysis on Concealed Strategies. 2021 26th International Conference on Automation and Computing (ICAC), Portsmouth, United Kingdom, 2021, pp. 1-6. [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





