Submitted:
07 January 2025
Posted:
08 January 2025
You are already at the latest version
Abstract
Keywords:
1. Background
1.1. The Internet of Things (IoT)
1.2. An Overview of IoT Security and Existing Literature
1.3. The Significance of IoT Security
2. How Iot-Related Security Technology Works
2.1. Components, Technologies, and Processes Involved
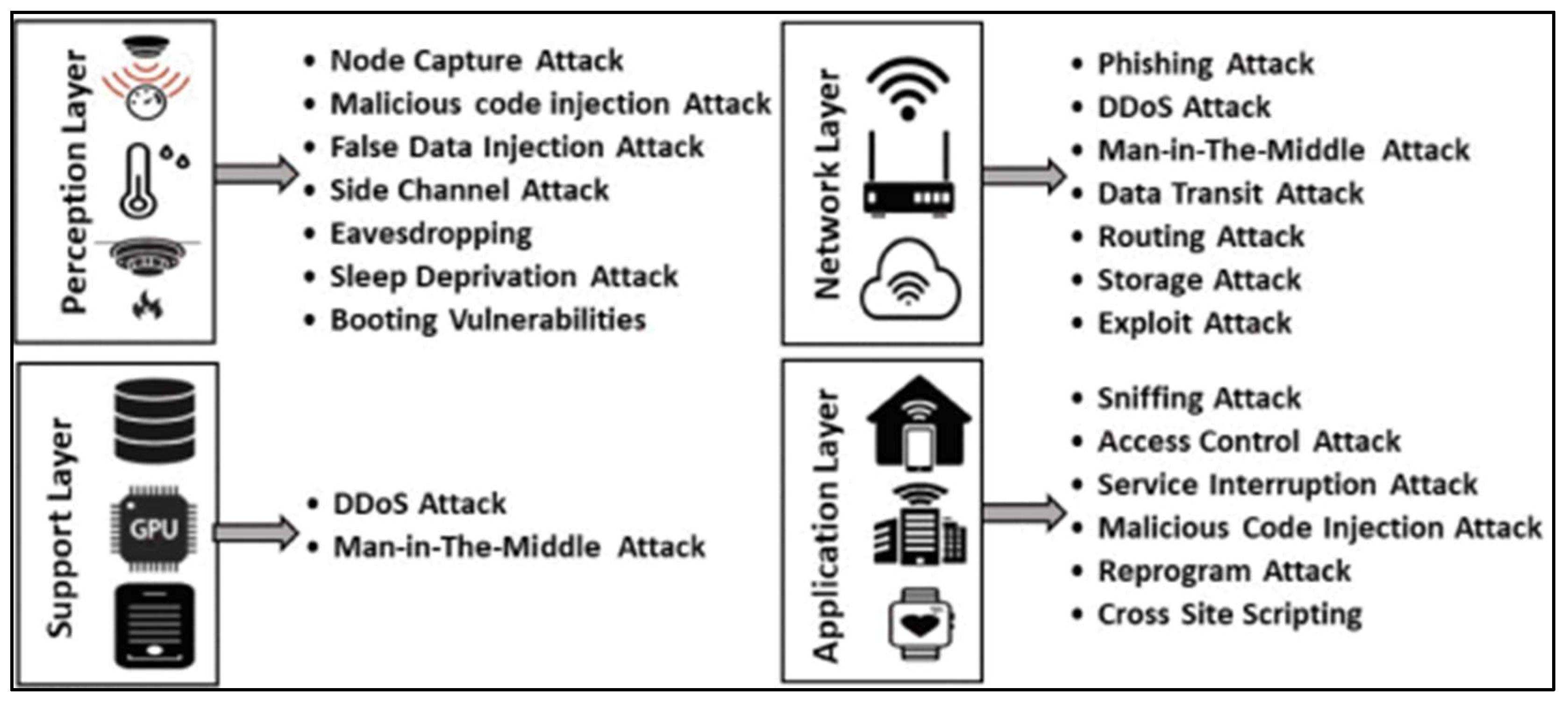
2.1.1. Perception Layer
2.1.2. Network Layer
2.1.3. Middleware Layer
2.1.4. Application Layer
2.2. Threats and Vulnerabilities of IoT Security-Related Technology
2.3. Examples of Security-Related Technology Usage
Smart Home Security
Smart Driving
Smart Toll Collection
Smart Wearables
Healthcare
3. Impacts of IoT Security
3.1. Benefits
3.1.1. Building Customer Trust
3.1.2. Prevention of Threats Against Smart Devices
3.1.3. Enhanced Business Security
3.2. Limitations of IoT Security
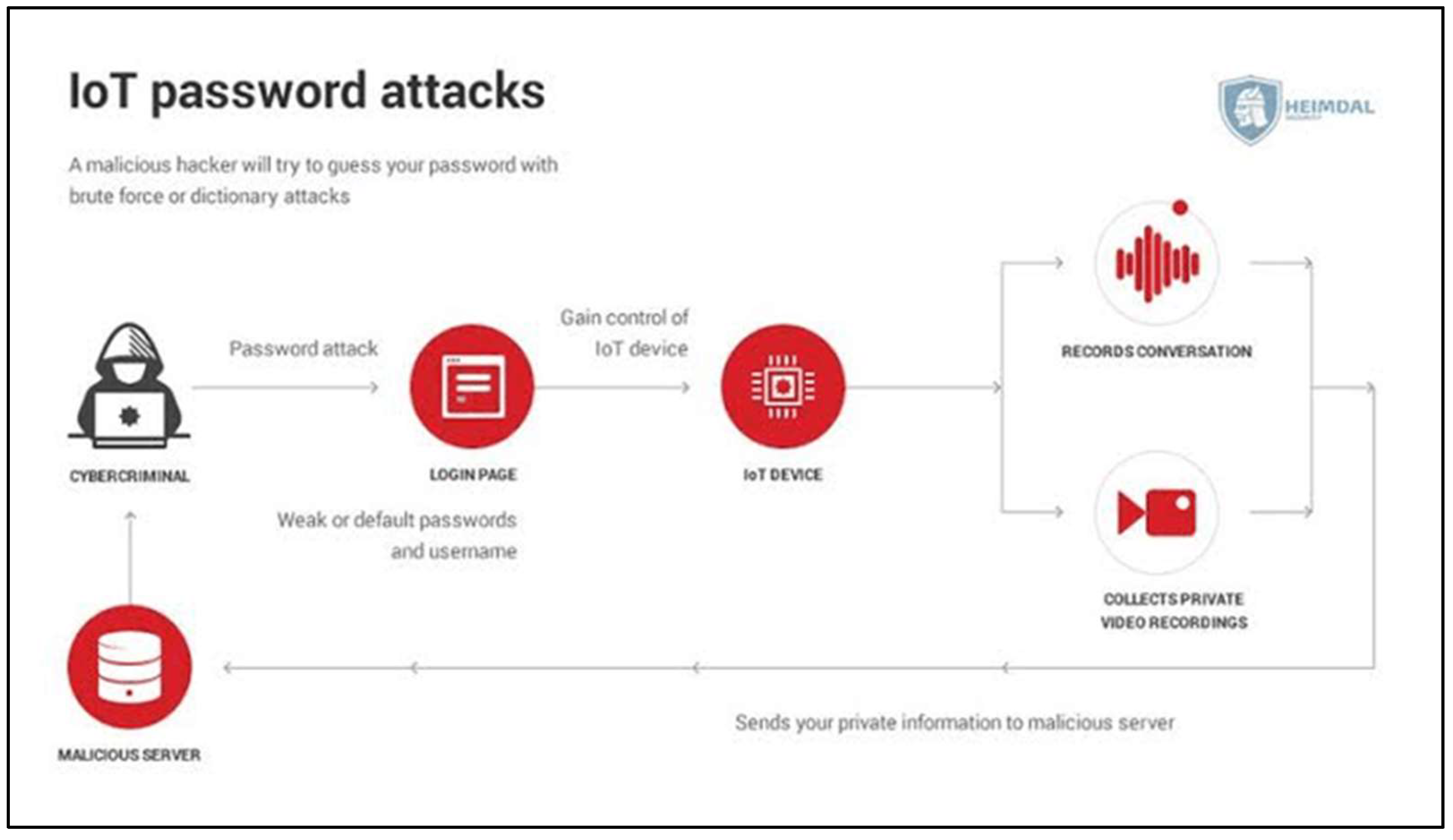
3.2.1. Authentication
3.2.2. Firmware Updates
3.2.3. Privacy
3.3. Future Potential
3.3.1. Enhanced Data Encryption
3.3.2. AI-Driven Security
3.3.3. Blockchain Technology
3.3.4. Stronger Authentication Methods
4. Security Countermeasures
4.1. Prior Discussion
4.1.1. Weak Authentication
4.1.2. Lack of Firmware Updates
4.1.3. Lack of Privacy and Security
4.2. Proposed Countermeasures
5. Conclusion
References
- Ahmid, M. & Kazar, O., 2021. A Comprehensive Review of the Internet of Things Security. Journal of Applied Security Research. [CrossRef]
- AirDroid Sand Studios, 2023. 5 Common IoT Security Challenges to Be Aware Of. [Online] Available at: https://blog.airdroid.com/post/5-common-iot-security-challenges/.
- Alex, S. A., Jhanjhi, N., Humayun, M., Ibrahim, A. O., & Abulfaraj, A. W. (2022). Deep LSTM Model for Diabetes Prediction with Class Balancing by SMOTE. Electronics, 11(17), 2737. [CrossRef]
- Alferidah, D. K., & Jhanjhi, N. (2020). Cybersecurity Impact over Bigdata and IoT Growth. 2020 International Conference on Computational Intelligence (ICCI). [CrossRef]
- Ali Khattak, H. et al., 2019. Perception security in the Internet of Things. Future Generation Computer Systems, Volume 100, pp. 144-164. [CrossRef]
- Alkinani, M. H., Almazroi, A. A., Jhanjhi, N., & Khan, N. A. (2021). 5G and IoT Based Reporting and Accident Detection (RAD) System to Deliver First Aid Box Using Unmanned Aerial Vehicle. Sensors, 21(20), 6905. [CrossRef]
- Ananna, F. F., Nowreen, R., Jahwari, S. S. R. A., Costa, E. A., Angeline, L., & Sindiramutty, S. R. (2023). Analysing Influential factors in student academic achievement: Prediction modelling and insight. International Journal of Emerging Multidisciplinaries Computer Science & Artificial Intelligence, 2(1). [CrossRef]
- Appsierra, 2024. Disadvantages of the Internet of Things: Learn Major Threats. [Online] Available at: https://www.appsierra.com/blog/disadvantages-of-the-internet-of-things.
- April, T. & Kiner, E., 2023. Google mitigated the largest DDoS attack to date, peaking above 398 million reps. [Online] Available at: https://cloud.google.com/blog/products/identity-security/google-cloud-mitigated-largest-ddos-attack-peaking-above-398-million-rps.
- Available at: https://www.knowledgehut.com/blog/security/Iot-cyber-security.
- Azam, H., Dulloo, M. I., Majeed, M. H., Wan, J. P. H., Xin, L. T., & Sindiramutty, S. R. (2023). Cybercrime Unmasked: Investigating cases and digital evidence. International Journal of Emerging Multidisciplinaries Computer Science & Artificial Intelligence, 2(1). [CrossRef]
- Azam, H., Dulloo, M. I., Majeed, M. H., Wan, J. P. H., Xin, L. T., Tajwar, M. A., & Sindiramutty, S. R. (2023). Defending the digital Frontier: IDPS and the battle against Cyber threat. International Journal of Emerging Multidisciplinaries Computer Science & Artificial Intelligence, 2(1). [CrossRef]
- Azam, H., Tajwar, M. A., Mayhialagan, S., Davis, A. J., Yik, C. J., Ali, D., & Sindiramutty, S. R. (2023). Innovations in Security: A study of cloud Computing and IoT. International Journal of Emerging Multidisciplinaries Computer Science & Artificial Intelligence, 2(1). [CrossRef]
- Azam, H., Tan, M., Pin, L. T., Syahmi, M. A., Qian, A. L. W., Jingyan, H., Uddin, M. F., & Sindiramutty, S. R. (2023). Wireless Technology Security and Privacy: A Comprehensive Study. Preprints.org. [CrossRef]
- Babbar, H., Rani, S., Masud, M., Verma, S., Anand, D., & Jhanjhi, N. (2021). Load balancing algorithm for migrating switches in software-defined vehicular networks. Computers, Materials & Continua/Computers, Materials & Continua (Print), 67(1), 1301–1316. [CrossRef]
- Balbix, 2024. Internet of Things (IoT) Biggest Security Challenges. [Online] Available at: https://www.balbix.com/insights/addressing-iot-security-challenges/.
- Bevis, R., 2023. 7 Examples of IoT in Everyday Life. [Online] Available at: https://www.cbtnuggets.com/blog/technology/networking/seven-examples-of-iot-in-everyday-life.
- Bigelow, S. J., 2021. What is edge computing? Everything you need to know. [Online] Available at: https://www.techtarget.com/searchdatacenter/definition/edge-computing.
- Brohi, S. N., Jhanjhi, N., Brohi, N. N., & Brohi, M. N. (2020). Key Applications of State-of-the-Art Technologies to Mitigate and Eliminate COVID-19.pdf. TECHRxiv. [CrossRef]
- Chesti, I. A., Humayun, M., Sama, N. U., & Jhanjhi, N. (2020). Evolution, Mitigation, and Prevention of Ransomware. 2020 2nd International Conference on Computer and Information Sciences (ICCIS). [CrossRef]
- Cloudflare, 2024. What is API security? [Online] Available at: https://www.cloudflare.com/learning/security/api/what-is-api-security/.
- Conure, 2024. The Future of IoT Security: Trends and Predictions. [Online] Available at: https://www.iotforall.com/the-future-of-iot-security-trends-and-predictions?form=MG0AV3.
- Cvetković, A. S., Radojcic, V. & Adamović, S. Ž., 2021. Multi-factor Authentication for the Internet of Things. Zbornik Radova Univerziteta Sinergija, November.22(7).
- Dogra, V., Singh, A., Verma, S., Kavita, N., Jhanjhi, N. Z., & Talib, M. N. (2021). Analyzing DistilBERT for Sentiment Classification of Banking Financial News. In Lecture notes in networks and systems (pp. 501–510). [CrossRef]
- Fatima-Tuz-Zahra, N., Jhanjhi, N., Brohi, S. N., Malik, N. A., & Humayun, M. (2020). Proposing a Hybrid RPL Protocol for Rank and Wormhole Attack Mitigation using Machine Learning. 2020 2nd International Conference on Computer and Information Sciences (ICCIS). [CrossRef]
- Fei, W., Ohno, H. & Sampalli, S., 2023. A Systematic Review of IoT Security: Research Potential, Challenges, and Future Directions. ACM Computing Surveys, 56(5), pp. 1-40. [CrossRef]
- Fortinet, 2022. What Is IoT Security? Challenges and Requirements. [Online] Available at: https://www.fortinet.com/resources/cyberglossary/iot-security.
- Fortinet, 2023. What Is IoT Device Vulnerability? [Online] Available at: https://www.fortinet.com/resources/cyberglossary/iot-device-vulnerabilities.
- Ganji, S., 2023. What Is IoT Security? Benefits, Challenges, and Solution. [Online] Available at: https://www.accelq.com/blog/iot-security/.
- Gavoni, L., 2021. RFID Exploitation and Countermeasures. p. 9.
- Gaur, L., Arora, G. K., & Jhanjhi, N. Z. (2022). Deep learning techniques for creation of deepfakes. In DeepFakes (pp. 23-34). CRC Press.
- Gopi, R., Sathiyamoorthi, V., Selvakumar, S., Manikandan, R., Chatterjee, P., Jhanjhi, N. Z., & Luhach, A. K. (2021). Enhanced method of ANN based model for detection of DDoS attacks on multimedia internet of things. Multimedia Tools and Applications, 81(19), 26739–26757. [CrossRef]
- Gouda, W., Almurafeh, M., Humayun, M., & Jhanjhi, N. Z. (2022). Detection of COVID-19 based on chest x-rays using deep learning. Healthcare, 10(2), 343. [CrossRef]
- Grayscale, 2023. Internet of Things (IoT) Security: A Critical Need for the Future. [Online] Available at: https://grayscale.my/internet-of-things-iot-security-a-critical-need-for-the-future/.
- Hashemi-Pour, C., Lutkevich, B. & Bigelow, S. J., 2024. XaaS (anything as a service). [Online] Available at: https://www.techtarget.com/searchcloudcomputing/definition/XaaS-anything-as-a-service.
- Hassija, V. et al., 2019. A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures. IEEE Access, 20 June, Volume 7, pp. 82721-82743. [CrossRef]
- Henke, C., 2023. What Is IoT Security? Risks, Examples, and Solutions. [Online] Available at: https://www.emnify.com/iot-glossary/iot-security.
- Humayun, M., Sujatha, R., Almuayqil, S. N., & Jhanjhi, N. Z. (2022). A Transfer Learning Approach with a Convolutional Neural Network for the Classification of Lung Carcinoma. Healthcare, 10(6), 1058. [CrossRef]
- Hussain, K., Rahmatyar, A. R., Riskhan, B., Sheikh, M. a. U., & Sindiramutty, S. R. (2024). Threats and Vulnerabilities of Wireless Networks in the Internet of Things (IoT). 2024 IEEE 1st Karachi Section Humanitarian Technology Conference (KHI-HTC), 2, 1–8. [CrossRef]
- IBM, 2024. Application layer security. [Online] Available at: https://www.ibm.com/docs/en/zos-basic-skills?topic=features-application-layer-security.
- Iordache, T., 2024. How Edge Computing is Transforming the Future of Technology. [Online] Available at: https://www.thinslices.com/insights/edge-computing-transforming-the-future-of-technology.
- IT Pillars, 2024. Security Impact of IoT: Risks and Challenges. [Online] Available at: https://www.it-pillars.com/blog/security-impact-of-iot/.
- Javed, D., Jhanjhi, N. Z., & Khan, N. A. (2023, April). Football analytics for goal prediction to assess player performance. In Innovation and Technology in Sports: Proceedings of the International Conference on Innovation and Technology in Sports,(ICITS) 2022, Malaysia (pp. 245-257). Singapore: Springer Nature Singapore.
- Jhanjhi, N., Humayun, M., & Almuayqil, S. N. (2021). Cyber security and privacy issues in industrial internet of things. Computer Systems Science and Engineering, 37(3), 361–380. [CrossRef]
- Jun, A. Y. M., Jinu, B. A., Seng, L. K., Maharaiq, M. H. F. B. Z., Khongsuwan, W., Junn, B. T. K., Hao, A. a. W., & Sindiramutty, S. R. (2024). Exploring the Impact of Crypto-Ransomware on Critical Industries: Case Studies and Solutions. Preprints.org. [CrossRef]
- Kandris, D., Nakas, C., Vomvas, D. & Koulouras, G., 2020. Applications of Wireless Sensor Networks: An Up-to-Date Survey. Applied System Innovation, 25 February, 3(1), p. 14. [CrossRef]
- Kaspersky, 2020. Why IoT security is important for your home network. [Online] Available at: https://www.kaspersky.com/resource-center/threats/secure-iot-devices-on-your-home-network.
- Kim, J.-D., 2024. A Comprehensive Analysis of Routing Vulnerabilities and Defense. October.
- Konatham, B., Simra, T., Amsaad, F., Ibrahem, M. I., & Jhanjhi, N. Z. (2024). A Secure Hybrid Deep Learning Technique for Anomaly Detection in IIoT Edge Computing. Authorea Preprints. [CrossRef]
- Kumar, M. S., Vimal, S., Jhanjhi, N., Dhanabalan, S. S., & Alhumyani, H. A. (2021). Blockchain based peer to peer communication in autonomous drone operation. Energy Reports, 7, 7925–7939. [CrossRef]
- Kumar, S., Tiwari, P. & Zymbler, M., 2019. Internet of Things is a revolutionary approach for future technology enhancement: a review. Journal of Big Data, Volume 6. [CrossRef]
- Lakhanpal, M., 2024. The State of IoT Security: Challenges and Opportunities. [Online] Available at: https://the-tech-trend.com/big-data/iot-security-challenges-and-opportunities.
- Lim, M., Abdullah, A., Jhanjhi, N., Khan, M. K., & Supramaniam, M. (2019). Link Prediction in Time-Evolving Criminal Network with deep Reinforcement learning technique. IEEE Access, 7, 184797–184807. [CrossRef]
- Lynn, T. et al., 2020. The Internet of Things: Definitions, Key Concepts, and Reference Architectures. In: T. Lynn, J. G. Mooney, B. Lee & P. T. Endo, eds. The Cloud-to-Thing Continuum. s.l.:Palgrave Macmillan, Cham, pp. 1-22. [CrossRef]
- Ma, Q., Tan, H. & Zhou, T., 2023. Mutual authentication scheme for smart devices in IoT-enabled smart home systems. Computer Standard & Interfaces, Volume 86. [CrossRef]
- Manchuri, A., Kakera, A., Saleh, A., & Raja, S. (2024). pplication of Supervised Machine Learning Models in Biodiesel Production Research - A Short Review. Borneo Journal of Sciences and Technology. [CrossRef]
- MAPL World, 2024. The Future of IoT The Future of IoT Security: Trends and Predictions. [Online] Available at: https://www.linkedin.com/pulse/future-iot-security-trends-predictions-maplworld-8blrc/.
- Mazhar, T. et al., 2023. Analysis of IoT Security Challenges and Its Solutions Using Artificial Intelligence. Brain Sciences, 13(4), pp. 1-30. [CrossRef]
- Medeiros, R., Fernandes, S. & Queiroz, P. G. G., 2022. Middleware for the Internet of Things: a systematicliterature review. Journal of Universal Computer Science, 28(1), pp. 54-79. [CrossRef]
- Mirza, D., 2024. Top 10 IoT Device Vulnerabilities to Enhance IoT Security. [Online] Available at: https://www.hostduplex.com/blog/top-iot-device vulnerabilities/#What_are_the_Top_IoT_Vulnerabilities_that_Make_Devices_Insecure.
- Mishra, N. & Pandya, S., 2021. Internet of Things Applications, Security Challenges, Attacks, Intrusion Detection, and Future Visions: A Systematic Review. IEEE Access, Volume 9, pp. 59353-59377. [CrossRef]
- Nayyar, A., Gadhavi, L., & Zaman, N. (2021). Machine learning in healthcare: review, opportunities and challenges. In Elsevier eBooks (pp. 23–45). [CrossRef]
- Obaidat, M. A. et al., 2020. A Comprehensive and Systematic Survey on the Internet of Things: Security and Privacy Challenges, Security Frameworks, Enabling Technologies, Threats, Vulnerabilities and Countermeasures. Computers, 9(2), p. 44. [CrossRef]
- Oliynyk, K., 2024. IoT Security: Risks, Examples, and Solutions. [Online] Available at: https://webbylab.com/blog/iot-security-issues-and-solutions/.
- Omolara, A. E. et al., 2022. The internet of things security: A survey encompassing unexplored areas and new insights. Computers & Security, Volume 112. [CrossRef]
- Rahmani, A. M., Bayramov, S. & Kalejahi, B. K., 2021. Internet of Things Applications: Opportunities and Threats. Wireless Personal Communications, Volume 122, pp. 451-476. [CrossRef]
- Rajmohan, T., Nguyen, P. H. & Ferry, N., 2022. A decade of research on patterns and architectures for IoT security. Cybersecurity, 5(2). [CrossRef]
- Rana, P. & Patil, P. B., 2023. Cyber security threats in IoT: A review. Journal of High Speed Networks, 29(2), pp. 105-120. [CrossRef]
- Ravichandran, N., Tewaraja, T., Rajasegaran, V., Kumar, S. S., Gunasekar, S. K. L., & Sindiramutty, S. R. (2024). Comprehensive Review Analysis and Countermeasures for Cybersecurity Threats: DDoS, Ransomware, and Trojan Horse Attacks. Preprints.org. [CrossRef]
- Sama, N. U., Zen, K., Humayun, M., Jhanjhi, N. Z., & Rahman, A. U. (2022). Security in wireless body sensor network: A multivocal literature study. Applied System Innovation, 5(4), 79. [CrossRef]
- Saini, M. K. & Saini, R. K., 2019. Internet of Things (IoT) Applications and Security Challenges: A Review. SSRN Electronic Journal, 7 June.
- Sandoval, N., 2020. What Is Over-the-Air? OTA Provisioning Explained. [Online] Available at: https://www.emnify.com/iot-glossary/over-the-air [Accessed 20 November 2024].
- Seng, Y. J., Cen, T. Y., Raslan, M. a. H. B. M., Subramaniam, M. R., Xin, L. Y., Kin, S. J., Long, M. S., & Sindiramutty, S. R. (2024). In-Depth Analysis and Countermeasures for Ransomware Attacks: Case Studies and Recommendations. Preprints.org. [CrossRef]
- Shah, I. A., Jhanjhi, N. Z., & Laraib, A. (2022). Cybersecurity and blockchain usage in contemporary business. In Advances in information security, privacy, and ethics book series (pp. 49–64). [CrossRef]
- Shah, I. A., Jhanjhi, N. Z., & Ray, S. K. (2024). Enabling Explainable AI in Cybersecurity Solutions. In Advances in Explainable AI Applications for Smart Cities (pp. 255-275). IGI Global.
- Sharma, R., Singh, A., Kavita, N., Jhanjhi, N. Z., Masud, M., Jaha, E. S., & Verma, S. (2021). Plant disease diagnosis and image classification using deep learning. Computers, Materials & Continua/Computers, Materials & Continua (Print), 71(2), 2125–2140. [CrossRef]
- Sharma, V., 2024. IoT Cyber Security: Trends, Challenges and Solutions. [Online].
- Sindiramutty, S. R., Jhanjhi, N. Z., Tan, C. E., Khan, N. A., Shah, B., & Manchuri, A. R. (2024). Cybersecurity measures for logistics industry. In Advances in information security, privacy, and ethics book series (pp. 1–58). [CrossRef]
- Sindiramutty, S. R., Jhanjhi, N. Z., Tan, C. E., Khan, N. A., Shah, B., Yun, K. J., Ray, S. K., Jazri, H., & Hussain, M. (2024). Future trends and emerging threats in drone cybersecurity. In Advances in information security, privacy, and ethics book series (pp. 148–195). [CrossRef]
- Sindiramutty, S. R., Jhanjhi, N. Z., Tan, C. E., Yun, K. J., Manchuri, A. R., Ashraf, H., Murugesan, R. K., Tee, W. J., & Hussain, M. (2024). Data security and privacy concerns in drone operations. In Advances in information security, privacy, and ethics book series (pp. 236–290). [CrossRef]
- Sindiramutty, S. R., Jhanjhi, N., Tan, C. E., Lau, S. P., Muniandy, L., Gharib, A. H., Ashraf, H., & Murugesan, R. K. (2024). Industry 4.0. In Advances in logistics, operations, and management science book series (pp. 342–405). [CrossRef]
- Sindiramutty, S. R., Tan, C. E., & Wei, G. W. (2024). Eyes in the sky. In Advances in information security, privacy, and ethics book series (pp. 405–451). [CrossRef]
- Sindiramutty, S. R., Tan, C. E., Shah, B., Khan, N. A., Gharib, A. H., Manchuri, A. R., Muniandy, L., Ray, S. K., & Jazri, H. (2024). Ethical considerations in drone cybersecurity. In Advances in information security, privacy, and ethics book series (pp. 42–87). [CrossRef]
- Singhal, V., Jain, S. S., Anand, D., Singh, A., Verma, S., Kavita, N., Rodrigues, J. J. P. C., Jhanjhi, N. Z., Ghosh, U., Jo, O., & Iwendi, C. (2020). Artificial Intelligence Enabled Road Vehicle-Train Collision Risk Assessment Framework for Unmanned railway level crossings. IEEE Access, 8, 113790–113806. [CrossRef]
- Sinha, S., 2024. State of IoT 2024: Number of connected IoT devices growing 13% to 18.8 billion globally. [Online] Available at: https://iot-analytics.com/number-connected-iot-devices/.
- Taherdoost, H., 2023. Security and Internet of Things: Benefits, Challenges, and Future Perspectives. Electronics, 8(12). [CrossRef]
- The European Commission, 2022. Use of Internet of Things in enterprises. [Online] Available at: https://ec.europa.eu/eurostat/statistics explained/index.php?title=Use_of_Internet_of_Things_in_enterprises#Enterprises_using_IoT.
- Waheed, A., Seegolam, B., Jowaheer, M. F., Sze, C. L. X., Hua, E. T. F., & Sindiramutty, S. R. (2024). Zero-Day Exploits in Cybersecurity: Case Studies and Countermeasure. preprints.org. [CrossRef]
- Wen, B. O. T., Syahriza, N., Xian, N. C. W., Wei, N. G., Shen, T. Z., Hin, Y. Z., Sindiramutty, S. R., & Nicole, T. Y. F. (2023). Detecting cyber threats with a Graph-Based NIDPS. In Advances in logistics, operations, and management science book series (pp. 36–74). [CrossRef]
- Williams, P., Dutta, I. K., Daoud, H. & Bayoumi, M., 2022. A survey on security in internet of things with a focus on the impact of emerging technologies. Internet of Things, August. Volume 19. [CrossRef]
- Xu, Y., 2023. Routing Strategies and Protocols for Efficient Data Transmission in the Internet of Vehicles: A Comprehensive Review. International Journal of Advanced Computer Science and Applications, January, 14(9), pp. 955-965. [CrossRef]
- Yasar, K., Shea, S. & Wigmore, I., 2023. IoT security (internet of things security). [Online] Available at: https://www.techtarget.com/iotagenda/definition/IoT-security-Internet-of-Things-security.
- Zhang, J., Ma, M., Wang, P. & Sun, X.-d., 2021. Middleware for the Internet of Things: A survey on requirements, enabling technologies and solutions. Journals of Systems Architecture, August.Volume 117. [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




