Submitted:
11 June 2025
Posted:
16 June 2025
Read the latest preprint version here
Abstract
Keywords:
Introduction
Background of the Study
- − completeness: ascertaining the availability of a witness to the trueness of a statement
- − soundness: where a falsifier fails to prove the content of a statement or computation
- − zero- knowledge: the verifier only confirms the truism of a statement and nothing else.
- − scalability: the computing power of algorithms must be constantly increased to function at a high level after it has been dispensed.
- − restriction: all data is lost when the prover or creator of a transaction loses their personal information
- − demand more computing power: there are 2000 possible calculations per ZKP transaction, and they require individual and specified number of processing time
- − unavailability of standards, unified language, and systems to enable developers to leverage the full potential of ZKP.
Statement of Problem
Justification of Study
Aim of the Study
Objectives of the Study
- To explore how zero-knowledge proofs can enhance voting transparency in the Catalyst voting process
- To investigate how ZKPs can protect voter privacy and prevent vote disclosure and manipulation
- To develop a scalable solution that can be integrated into the Catalyst voting process
- To identify ZKP-based protocols that are most suitable for the catalyst voting process
- To assess how to design a decentralised and secure voting system that utilises ZKPs for enhanced transparency and voter privacy
Research Hypotheses
- The integration of zero-knowledge proof (ZKP) protocols in the Catalyst voting process will significantly enhance voting transparency as measured by the accuracy and verifiability of voting results.
- The use of ZKP protocols in the Catalyst voting process will discourage voters turnout due to technical glitches incurred because of delays during peak voting times.
Literature Review
Theoretical Review
Empirical Evidence
Methodology
- A multivocal literature review: this was first used to review available literature on the challenges of the transparency and privacy dilemma of blockchain technology, and to comprehensively analyse the operational frameworks and applications of various zero-knowledge proof protocols to determine their potential application in the catalyst voting process. This method is relevant because aside being exploratory and expository, it enabled the researchers to understand nuances and conversations around embedding ZKP in blockchain ecosystems for voting, which also aligns the objectives of this study to the roadmap, hence enhancing the precision and accuracy of the research findings.
- The study also utilised a survey questionnaire sent out to 100 people in the Cardano blockchain ecosystem, to investigate the opinions of the potential users of the application of ZKP-based blockchain ecosystem in the Catalyst voting system. The participants of the survey were members of the Cardano community, who are very familiar with the Catalyst voting process, understand the challenges of the traditional voting system, and seek an innovation that can enhance the transparency of voting, maintain privacy of specific information in the process and improve the efficiency of the voting system.
- ▪
-
An architectural mock-up of the ZKP-based voting integrity system. This system conceptualised the voting protocol using ZKP which ensures that a user's voting eligibility is validated without disclosing sensitive information, such as the number of ADA tokens held. It maintains voter privacy and prevents undue influence from larger ADA holders. The design aims to enhance transparency within the voting process while protecting individual privacy and preventing vote manipulation. To achieve this, an interview was carried out with the community members and four suggestions for protocol changes were made. These suggestions are categorised into two:
- −
- voting methodology change including one-on-one voting system and scaled system voting
- −
- process change including the replacement of the snapshot process, and the real-time tallying, validation and release of results.
- ⮚
- A one-on-one voting system where each user votes individually with their validated voting power. Here, the Voter Identification Module uses ZKP to confirm eligibility before allowing the vote. This is achieved by ensuring that each voter’s wallet contains the specific amount of ADA tokens required to vote in a particular session. For instance, say the eligibility criteria to vote a proposal is the voting threshold of 500 tokens, the Voters Identification Module confirms that eligible voters hold up to that number of tokens, without revealing the total amount of tokens they have in their wallet. That way, each vote is counted fairly without external influence. This voting system also facilitates better decision-making in a decentralised platform, fostering a more nuanced understanding of voter preferences while ensuring that the best proposals are selected for funding and development.
- ⮚
- A scaled voting system whereby users are assigned a range of votes based on their holdings, validated through ZKP. The system assesses the user's range and allocates votes accordingly while maintaining confidentiality. It balances power among users, by allowing people with more range to maintain their voting power, at the same time preventing them from influencing the voting outcome.
- ⮚
- Replacement of the snapshot process allowing users to vote anytime during the open voting window, with ZKP validating their voting power dynamically. Each vote is verified through ZKP at the time of casting, preventing pre-knowledge of voting power and vote buying. Simply put, this process allows the system to take a snapshot of the voter’s wallet each time before the voting is done to capture the exact amount of ADA tokens present in their wallet at that point, then categorise them accordingly to their voting power. This increases voting flexibility and security, enabling real-time validation and minimising exploitation risks. Voters can no longer cheat by borrowing tokens prior to their voting period to establish a faux voting power but are allowed to vote according to the power available to them due to their token balance at that time.
- ⮚
- Real-time validation and tallying, whereby, in the event of the conclusion of the snapshot process and voting, votes are tallied as they are cast, using ZKP to ensure accurate and secure verification. This system synchronises with either the one-on-one voting or scaled voting systems to tally the votes, followed by results being updated almost immediately. This provides transparency and instant feedback to voters, fostering trust in the electoral process.
- ○
- Cryptographic complexity which can be encountered due to the difficulty in applying or implementing the ZKP-based voting integrity assurance which relies heavily on advanced cryptographic models and techniques requiring correctness and security to meet the goal of privacy and ensure that the entire voting system is safe from attacks.
- ○
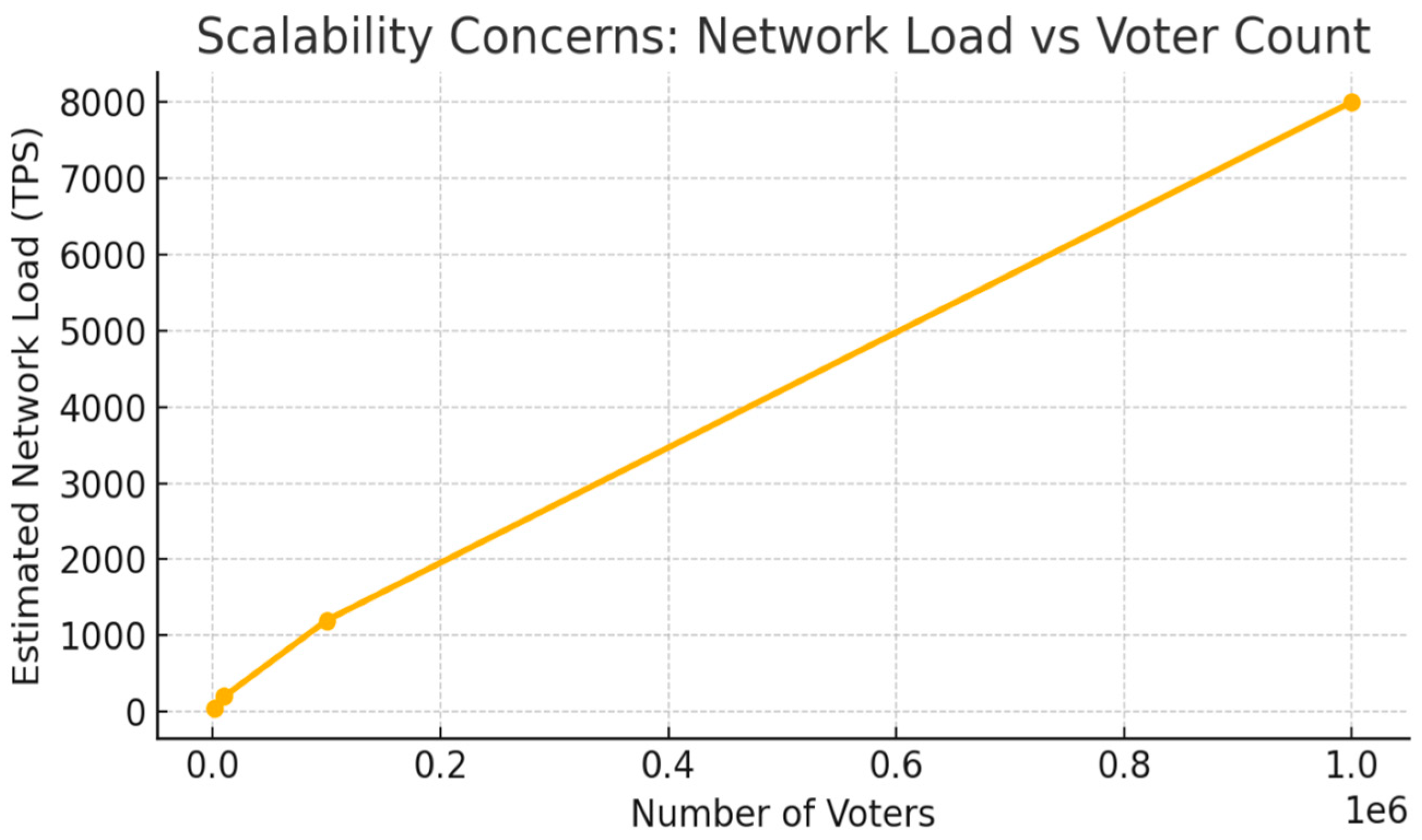
- The platform may be difficult to scale because it is tasked to operate when millions of voters are involved as the system generates and verifies zero-knowledge proofs per user via computation.
- ○
- Ballot anonymity involves the balance of the computational dilemma of maintaining both confidentiality of voters and at the same time verifying their identity.
- ○
- Ensuring that usability and accessibility of the platform is simplified, because building a system that is easy for users to operate and does not discriminate against eligible voters to bridge voters inequality gap, is practically difficult.
- ○
- Others include ensuring trust and transparency; being able to cooperate with other voting infrastructures including voter registration databases and vote counting processes; allowing independent verification and auditing of both the integrity of the electoral process and election results respectively; resilient to attacks such as denial-of-service attacks, network interruptions, and guesses to manipulate data; ensuring legal and regulatory compliance to international standards of authority across jurisdictions; and convincing the voters and relevant stakeholders to adopt this system even with the possibility of a resistance to change.
Results and Findings
- Introduction
- Analysis of Responses on Instant Snapshots and ZKP Validation
- User Feedback on Instant Snapshots:
- Positive Responses:
- Challenges and Concerns:
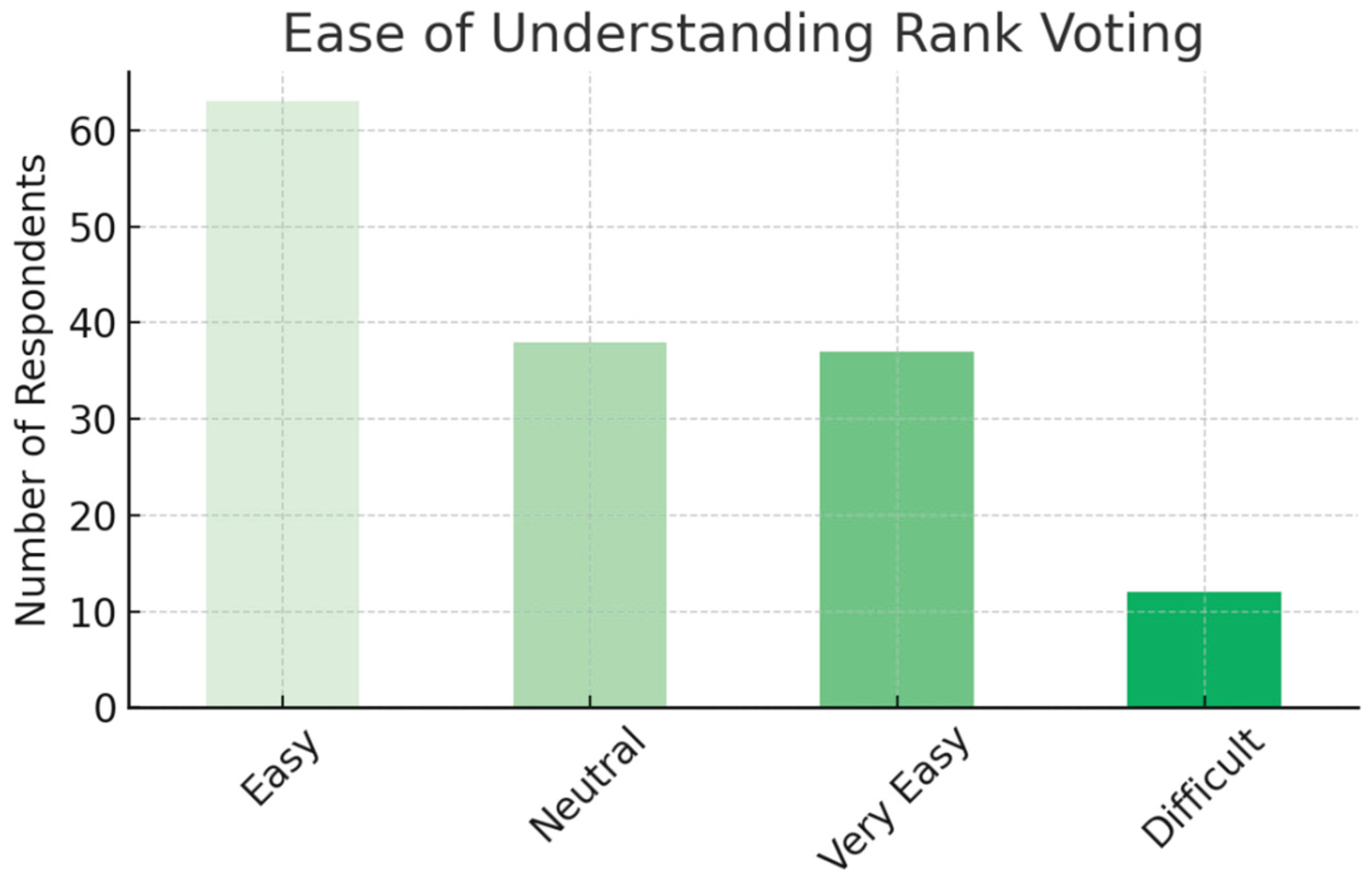
- Analysis of Rank Voting and Tier Systems
- Proportional Voting Based on ADA Holdings:
- Positive Viewpoints:
- Key Themes from Comments:
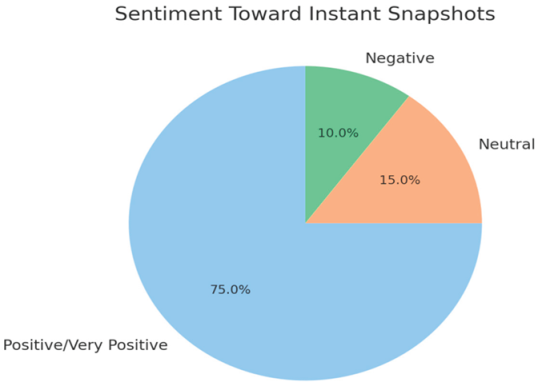
- Recurring Justifications:
- Key Issues:
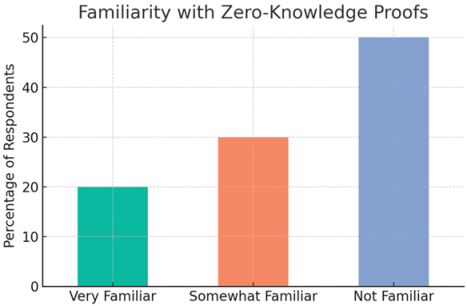
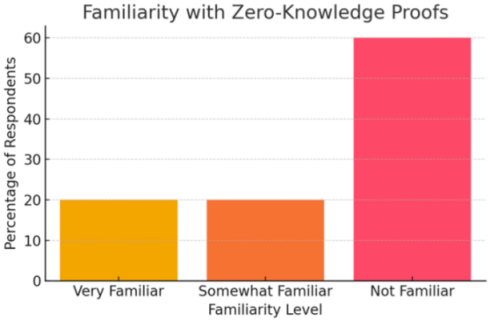
| Level | Respondents (%) |
| Very Familiar | 20% |
| Somewhat familiar | 30% |
| Not familiar | 50% |
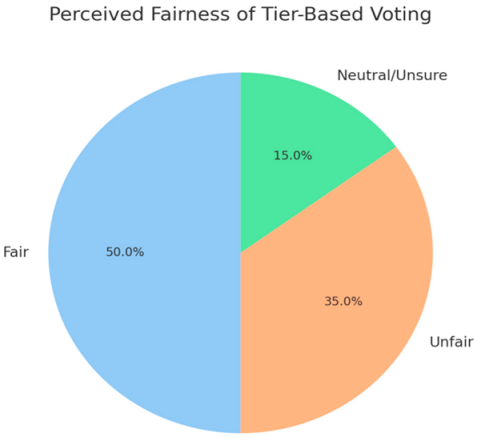
- -
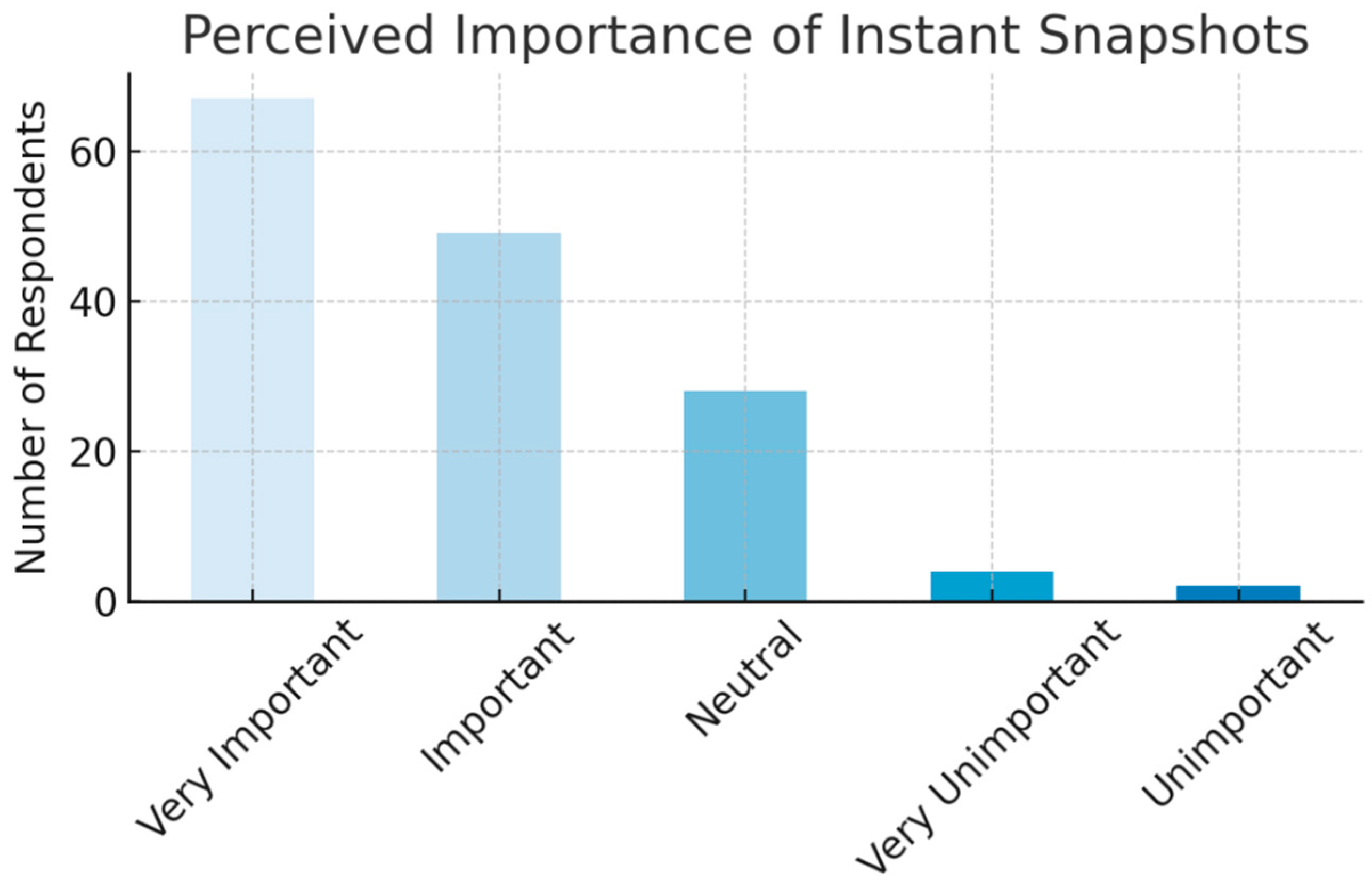
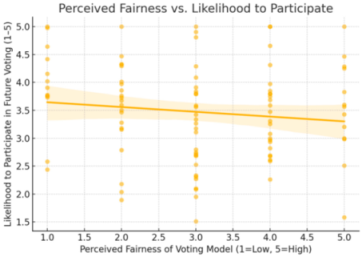
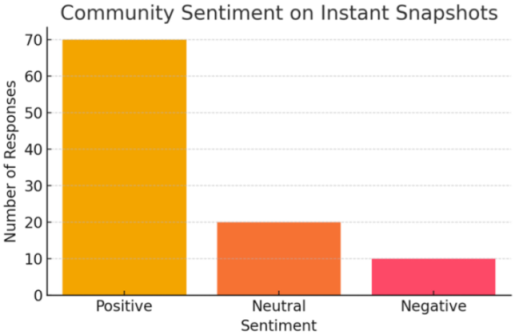
- 75% of respondents support the idea for enhancing transparency and real-time accountability.
- -
- Minor concerns focus on lag and system complexity.
- -
- 50% are not familiar — a clear barrier to adoption.
- -
- Points to the need for educational initiatives if ZKP voting is introduced.
- -
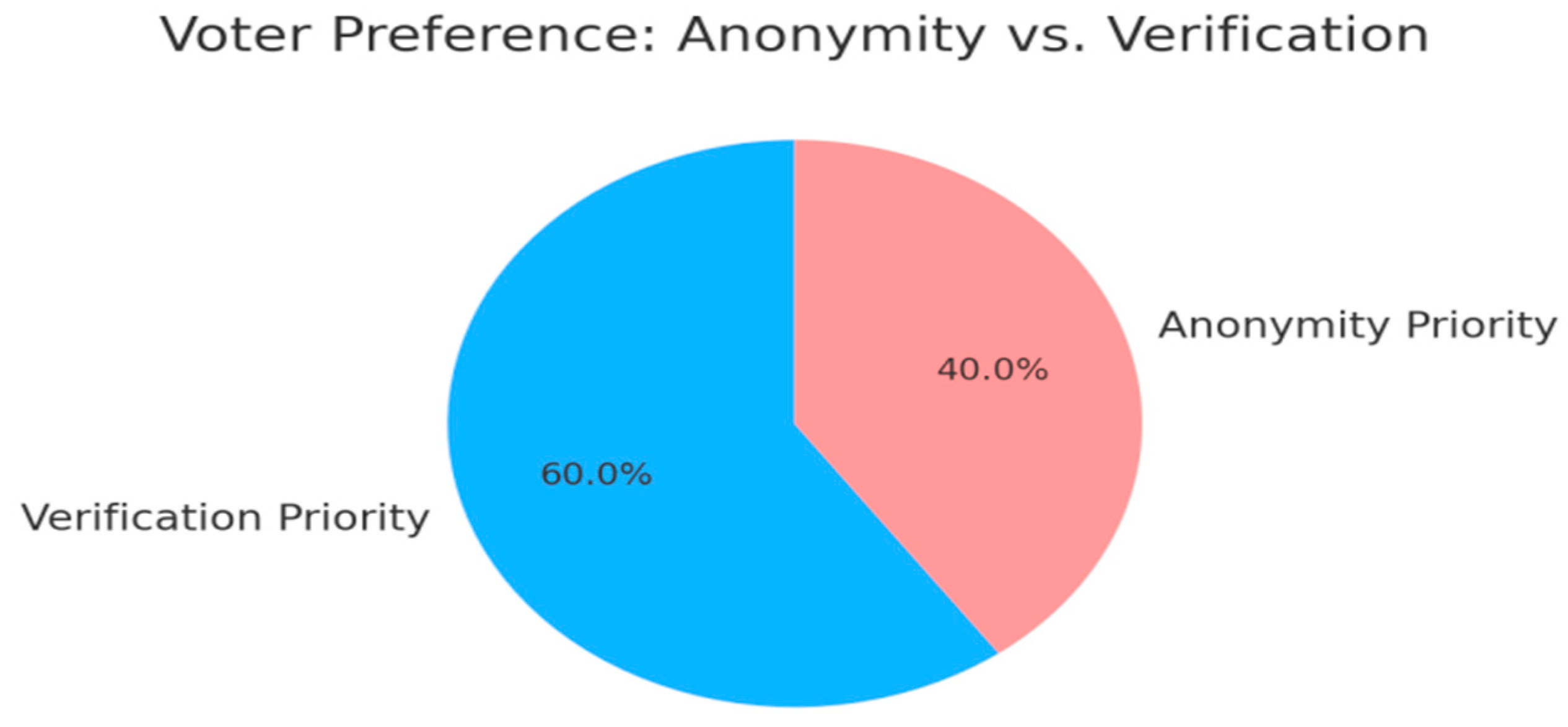
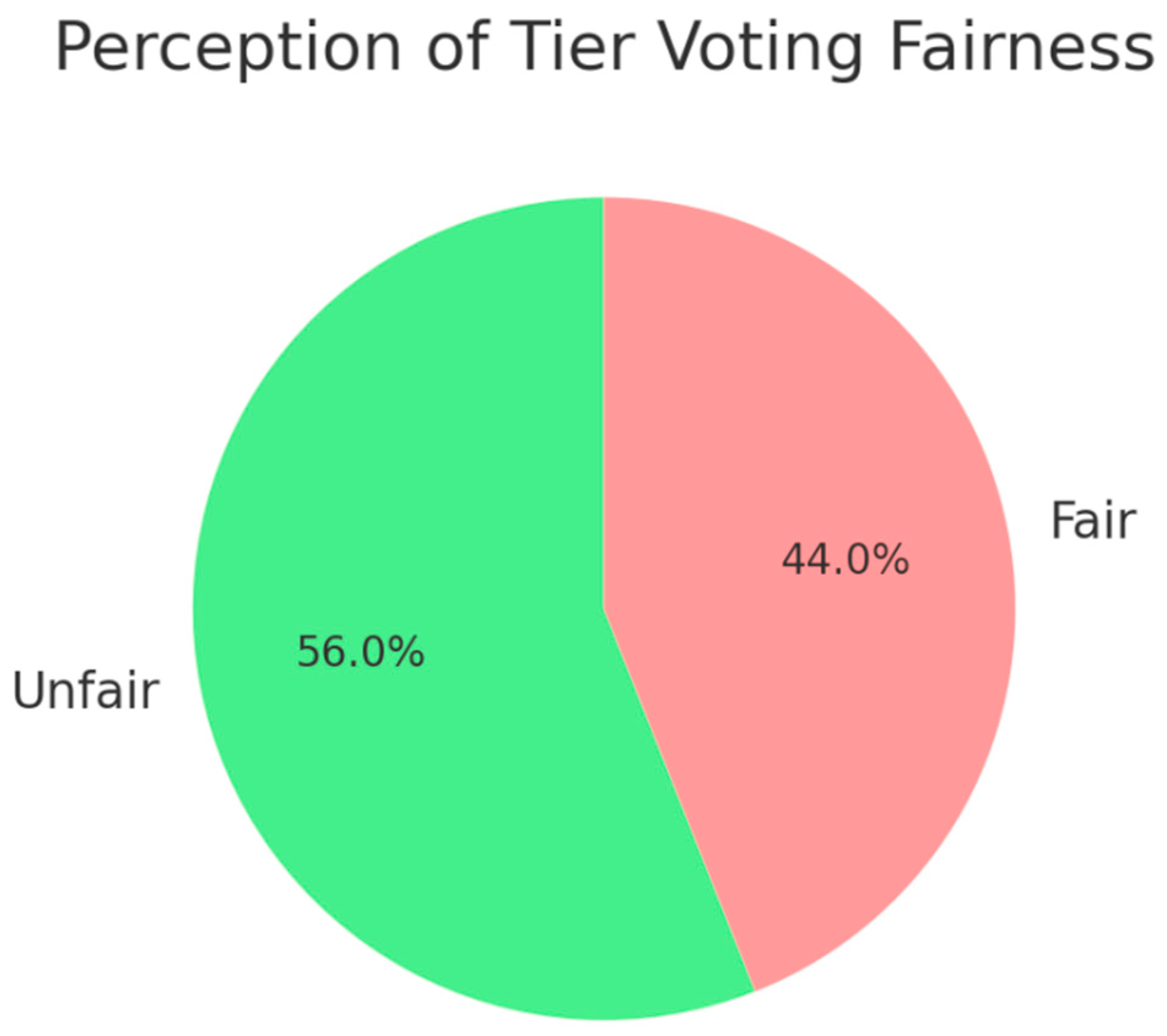
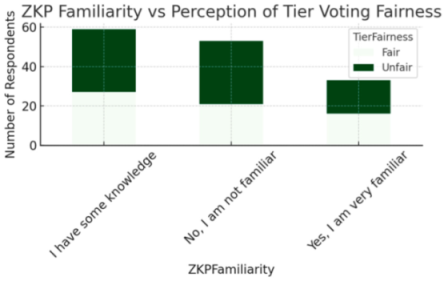
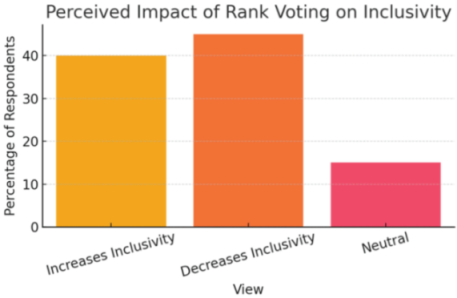
- 50% view it as fair (reflects stake-based influence), but 35% believe it's exclusionary.
- -
- Highlights a key trade-off between stake influence and democratic equity
- Community Feedback Themes on ZKP Voting
- Comparative Analyses
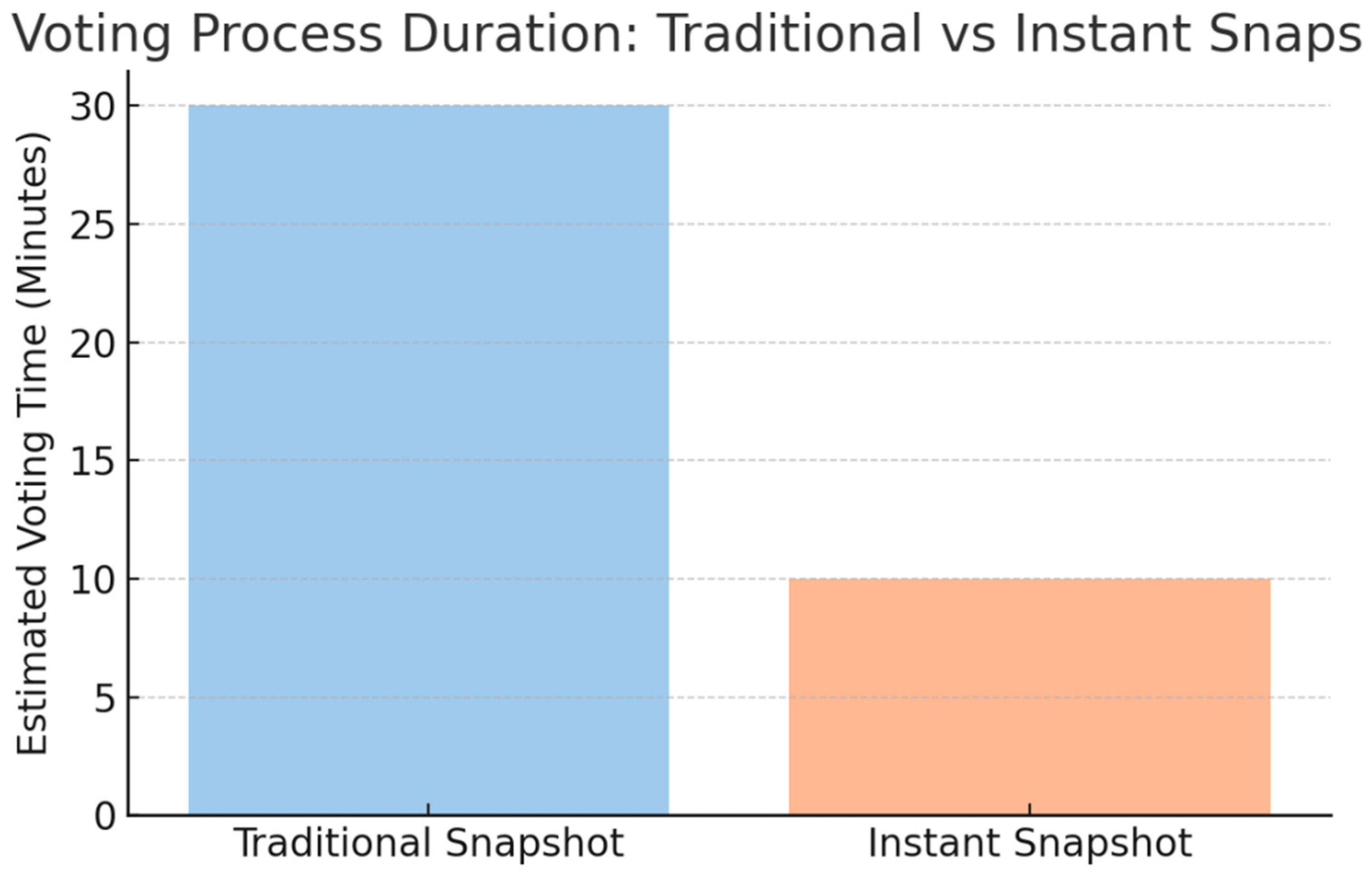
| Metric | Traditional Snapshot | ZKP-Based Snapshot |
| Snapshot Timing | Periodic (delayed) | Real-time (instant) |
| Voter Trust Rating | Medium (varied) | High (70–75%) |
| Fraud/Manipulation Risk | Higher | Lower (ZKP audit trail) |
| Result Availability | Delayed (post-tally) | Instant (live tally) |
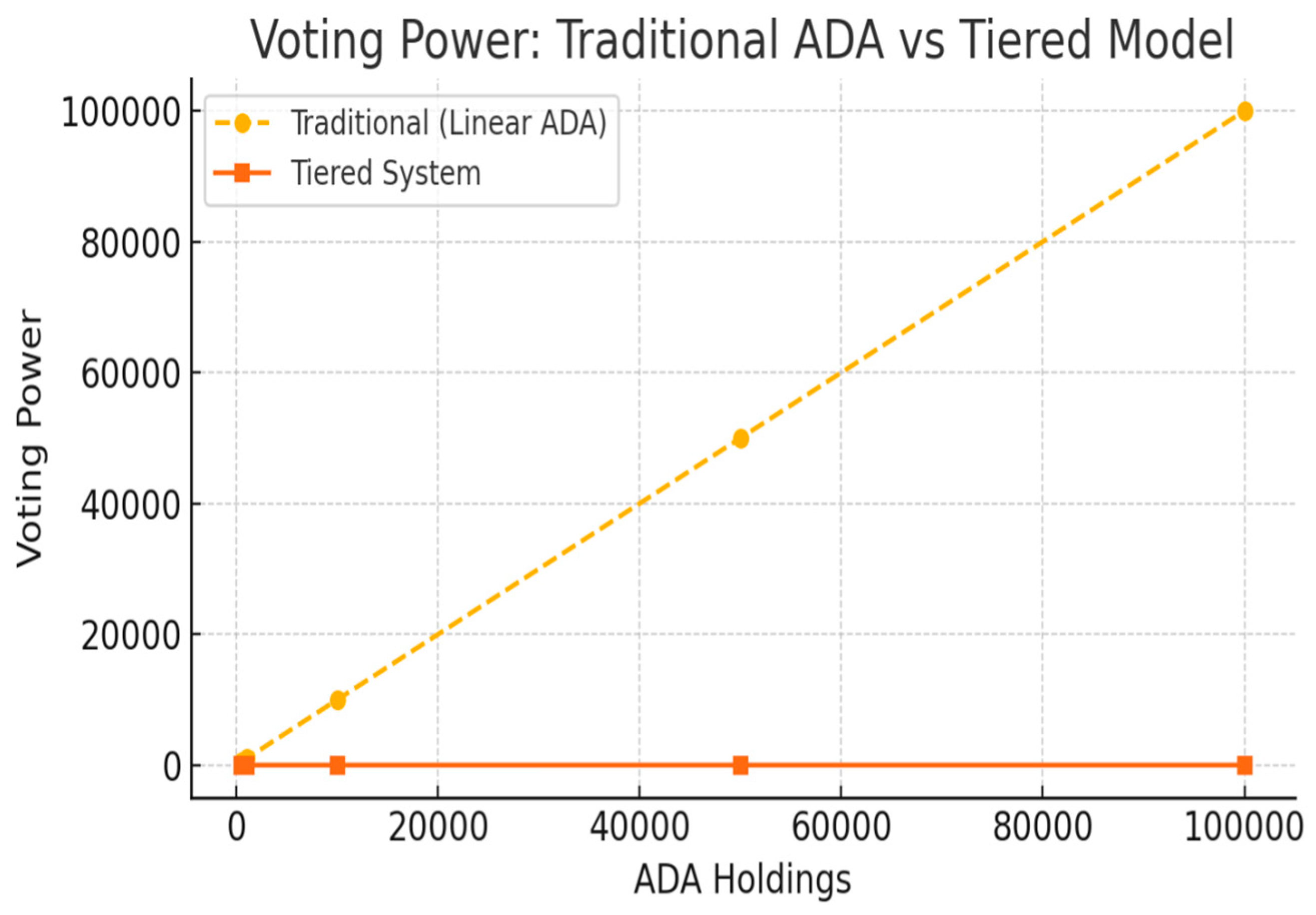
| Factor | Rank Voting (Tiered) | 1:1 Equality (Flat) |
| Inclusivity (Perceived) | Divided (45% say reduced) | High (equal voice) |
| Decentralization | Conditional on tiers | High, but risks vote dilution |
| Stakeholder Influence | Proportional to ADA | Uniform regardless of holdings |
| Privacy Balance | Supports ZKP verification tiers | Easier to implement anonymously |
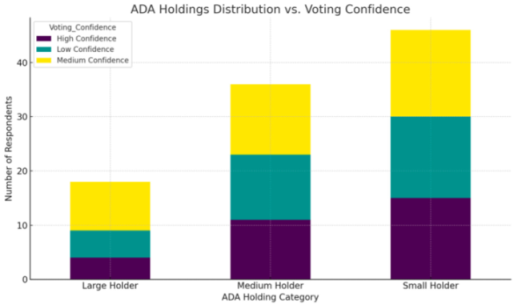
- Show a higher proportion of High Confidence in the voting system.
- Likely due to the perception that larger ADA stakes naturally align with more voting power.
- Predominantly exhibit Medium Confidence, indicating mixed perceptions about fairness and influence.
- A significant portion shows Low Confidence in the voting model.
- Reflects concerns over being marginalized by large stakeholders.
| Platform | Anonymity Support | Real-Time Snapshot | ZKP Usage | User Trust Score |
| Cardano Catalyst | Partial | Under development | Pilot | Medium-High |
| Polkadot | None | No | No | Low |
| Aleo Testnet | Yes | Yes | Native | High |
- -
- Aleo Testnet stands out with full anonymity.
- -
- Cardano Catalyst has partial support, while Polkadot lacks anonymity.
- -
- Aleo has fully implemented it.
- -
- Cardano is still developing this feature, while Polkadot does not support it.
- -
- Aleo uses native ZKPs, while Cardano is piloting the concept.
- -
- Polkadot does not integrate ZKP mechanisms.
- -
- Aleo Testnet has the highest trust score due to native support for privacy and real-time snapshots.
- -
- Cardano Catalyst maintains a medium-high trust level due to its innovative pilot projects.
- -
- Polkadot has a low trust score due to lack of advanced privacy features and real-time validation.
| Focus Area | Key Findings |
| Cryptographic Complexity | Advanced ZKP protocols (e.g., SNARKs) are viable but complex. Implementation requires strong formal verification. |
| Scalability | Tallying millions of votes with ZKPs requires optimized proof generation—use of sidechains and parallel processing is recommended. |
| Ballot Anonymity vs Verifiability | Must preserve privacy while ensuring transparent audit trails. Real-time proof-based snapshots help mitigate manipulation. |
| Usability & Accessibility | Simple, user-friendly design is essential to avoid alienating low-tech users. UX must balance privacy with clarity. |
| Tools in Use | Cardano’s Plutus and Marlowe, SNARK schemes, IPFS, and Chain-link are part of the tech stack. |
| Voting Models Proposed | - 1-to-1 equality model (500 ADA = 1 vote regardless of holdings) - Tiered scale model to balance decentralization and stake |
| Theme | Dominant Sentiment | Quote / Summary |
| Instant Snapshots | 70% Positive – improves fairness & reduces manipulation. | “Snapshots create real-time trust and stop whales from shifting ADA before voting.” |
| Concerns | System overload, accessibility for new users, hacking potential | “System might lag under load” – “Worried less tech-savvy users may be confused.” |
| Rank/Tier Voting Fairness | Mixed: 50% say fair, 35% say unfair, 15% unsure | “Gives big holders too much say” vs “Reflects commitment to the ecosystem.” |
| Familiarity with ZKPs | ~60% unfamiliar or somewhat unfamiliar | “I’ve heard of it but don’t understand how it really works.” |
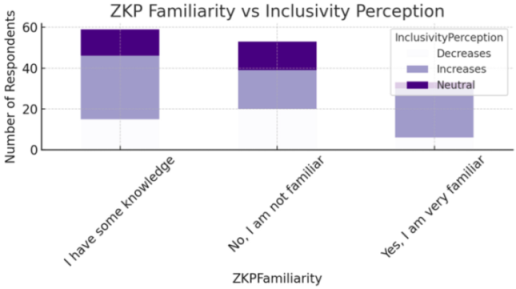
| Inclusivity Perception | Mixed: ~40% say increases inclusivity, 45% say decreases, 15% neutral | “Good ideas can be sidelined by low ADA holders.” vs “Ensures all voices are counted fairly.” |
| Voting Model Preference | ~65% support real-time tallying and one-on-one voting | “Transparency and auditability are a win” – “Need to keep voter identity private though.” |
- -
- Strong support for instant snapshots to improve trust and reduce manipulation.
- -
- Mixed views on rank voting fairness; concerns about inclusivity and centralization.
- -
- ZKP familiarity correlates with higher trust in tiered systems and inclusivity.
- -
- Voting efficiency, transparency, and scalability were identified as key priorities.
Discussion
Summary, Recommendations and Conclusion
Recommendations
- ▪
- To achieve both privacy and transparency of voting in blockchain-based ecosystems, ZKP can be implemented. This is due to its ability to maintain decentralisation, auditability, transparency and community involvement.
- ▪
- There should be established standardised ZKP protocols in the system such as side chain tools to enhance interoperability and scalability.
- ▪
- For future studies, further investigation into the scalability and performance of ZKP-based voting systems in large-scale settings should be done. This also includes ensuring the specific features to be implemented in the platform which aids usability and accessibility of the platform.
- ▪
- Studies should also understand the dynamics of regulatory and legal frameworks across different jurisdictions, analyse similarities and differences in the trend for their development and implementation. This includes ensuring accurate testing of the platform prior to its adoption by the public, making sure that its operation is seamless and effective for the course which it was developed for.
Conclusion
References
- Aleo — revolutionizing blockchain with Zero-Knowledge Proofs. Available at: https://medium.com/@ur4ix/aleo-revolutionizing-blockchain-with-zero-knowledge-proofs-ec307abe088a.
- Chi, P.W., Lu, Y.H. and Guan, A., 2023. A privacy-preserving zero-knowledge proof for blockchain. IEEE Access. [CrossRef]
- Feng, T., Yang, P., Liu, C., Fang, J. and Ma, R., 2022. Blockchain data privacy protection and sharing scheme based on zero-knowledge proof. Wireless Communications and Mobile Computing, 2022, pp.1-11. [CrossRef]
- Han, M., Yin, Z., Cheng, P., Zhang, X. and Ma, S., 2020. Zero-knowledge identity authentication for internet of vehicles: Improvement and application. Plos one, 15(9), p.e0239043. [CrossRef]
- Hasan, J., 2019. Overview and applications of zero knowledge proof (ZKP). International Journal of Computer Science and Network, 8(5), pp.2277-5420.
- Hryniuk, O., 2023. How is Marlowe different from Plutus. Available online at: https://www.essentialcardano.io/faq/how-is-marlowe-different-from-plutus.
- King, S., 2023. Marlowe: Simplifying Financial Smart Contracts on Cardano’s Blockchain. Available online: https://forum.cardano.org/t/marlowe-simplifying-financial-smart-contracts-on-cardanos-blockchain/124320.
- Li, W., Guo, H., Nejad, M. and Shen, C.C., 2020. Privacy-preserving traffic management: A blockchain and zero-knowledge proof inspired approach. IEEE access, 8, pp.181733-181743. [CrossRef]
- Methmal, J., 2023. Zero Knowledge Proofs: A Comprehensive Review of Applications, Protocols, and Future Directions in Cybersecurity. [CrossRef]
- Panja, S. and Roy, B.K., 2018. A secure end-to-end verifiable e-voting system using zero knowledge based blockchain. Cryptology ePrint Archive.
- Partala, J., Nguyen, T.H. and Pirttikangas, S., 2020. Non-interactive zero-knowledge for blockchain: A survey. IEEE Access, 8, pp.227945-227961. [CrossRef]
- Prasad, S., Tiwari, N., Chawla, M. and Tomar, D.S., 2024. Zero-Knowledge Proofs in Blockchain-Enabled Supply Chain Management. In Sustainable Security Practices Using Blockchain, Quantum and Post-Quantum Technologies for Real Time Applications (pp. 47-70). Singapore: Springer Nature Singapore.
- Principato, M., Babel, M., Guggenberger, T., Kropp, J. and Mertel, S., 2023. Towards Solving the Blockchain Trilemma: An Exploration of Zero-Knowledge Proofs.
- Pruden, A., 2021. The future of zero-knowledge with Aleo. Available at: https://aleo.org/post/the-future-of-zero-knowledge-with-aleo/.
- Sanjaya, M.D., 2021. A Blockchain Based Approach for Secure E-Voting System (Doctoral dissertation).
- Sedlmeir, J., Völter, F. and Strüker, J., 2021. The next stage of green electricity labeling: using zero-knowledge proofs for blockchain-based certificates of origin and use. ACM SIGENERGY Energy Informatics Review, 1(1), pp.20-31.
- Twenhoven, T., 2023. Trust, But Verify: Potentials for Zero Knowledge Proofs in Supply Chain Management. Zoom Research Seminar / 5th Floor EE Lecture 2. Available online at:https://www.klu.org/event/trust-but-verify-potentials-for-zero-knowledge-proofs-in-supply-chain-management.
- Tyagi, S. and Kathuria, M., 2022, May. Role of Zero-Knowledge Proof in Blockchain Security. In 2022 International Conference on Machine Learning, Big Data, Cloud and Parallel Computing (COM-IT-CON) (Vol. 1, pp. 738-743). IEEE.
- VanticaTrading, 2023. What is Midnight, Cardano’s Privacy Sidechain? Available online at: https://www.vanticatrading.com/post/what-is-midnight-cardano-s-privacy-sidechain.
- Xu, X., 2024. Zero-knowledge proofs in education: a pathway to disability inclusion and equitable learning opportunities. Smart Learning Environments, 11(1), p.7. [CrossRef]
- Yang, X. and Li, W., 2020. A zero-knowledge-proof-based digital identity management scheme in blockchain. Computers & Security, 99, p.102050. [CrossRef]
- Zero-knowledge Proofs: An Intuitive Explanation. Available online at: https://minaprotocol.com/blog/zero-knowledge-proofs-an-intuitive-explanation#:~:text=The%20purpose%20of%20zero%2Dknowledge,without%20giving%20them%20the%20solution.
- Zhou, L., Diro, A., Saini, A., Kaisar, S. and Hiep, P.C., 2024. Leveraging zero knowledge proofs for blockchain-based identity sharing: A survey of advancements, challenges and opportunities. Journal of Information Security and Applications, 80, p.103678. [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).



