1. Introduction
With the development of vehicle networking system, wide transmission coverage, high energy efficiency and secure communication have become the primary tasks of evaluating vehicle networking communication system [
1,
2]. For the Internet of Vehicles (IoV), it can share information not only with infrastructure such as roadside units (RSU) through vehicle-to-infrastructure (V2I) communication, but also with vehicles through vehicle-to-vehicle (V2V) communication [
3]. Automatic driving, intelligent driving-assist system, traffic flow and urban traffic management will bring exponential growth of massive data and computing resources consumption. Critical and real-time collaborative control messages have strict delay restrictions, while the transmission of multimedia entertainment application information can accommodate a certain degree of delay, which poses a great challenge for managing the interaction of vital information, task unloading and realizing large-scale model (LMs) based decision-making across many heterogeneous nodes within the framework of the Internet of Vehicles [
4]. The wide application of the IoV based on artificial intelligence (AI) has aroused significant extensive concern about the IoV, which involves heterogeneous computing-intensive and delay-intolerant tasks. The on-board resources of consumer vehicles can not meet such requirements, so researchers introduced the technology of multiple access edge computing (MEC), which can expand the computing power of vehicle networks by allowing vehicles to offload some tasks to MEC servers. At this point, the authors in [
5] minimize energy consumption, and develop a method based on deep reinforcement learning (DRL) to offload tasks to roadside units (RSU) or other vehicles. Similarly, the authors in [
6,
7] use the method based on DRL to unload tasks. In addition, the coverage of wireless communication networks based on high-cost base stations (BS) is still limited, and it is impossible to provide continuous, reliable and high-throughput basic services [
8,
9]. Therefore, there are obvious technical obstacles to realize reliable and extensible wireless transmission in IoV, which imposes great restrictions on the deployment of the above-mentioned intelligent vehicles and transportation systems.
RIS as a new communication technology can use a series of reflective elements to modulate electromagnetic wave signals and transmit them to the receiver, so it can effectively assist the communication between the transmitter and the receiver. For example, when the user is in an environment with poor communication quality, the RIS deployed in the surrounding area can reflect the signal to the required position to assist communication. Compared with the traditional antenna and base station technology, RIS has higher spectral efficiency, lower power consumption and better privacy [
10,
11]. In order to ensure low latency, the IoV needs ubiquitous ultra-reliable, low latency and high-speed wireless communication. In this respect, RIS assisted communication is a revolutionary way to improve the quality of wireless communication by adjusting the wireless propagation path [
12]. RIS can reconstruct the wireless channel by using electromagnetic elements to manipulate incident waves, thus enhancing the system throughput and improving the quality of service (QoS) of edge users [
13,
14]. Although BS is the central hub of information exchange, they may not be able to achieve full coverage in urban application scenarios. Some RISs are deployed in a fixed configuration, while others are flexibly and adaptively configured by drones to adapt to the complexity of wireless channels [
15,
16,
17]. On the basis of this framework, all vehicles in the IoV as terminal nodes can not only effectively transmit key information, but also offload local computing tasks to the edge or cloud server for processing. However, the hybrid architecture integrating RISs and BSs requires advanced hybrid beamforming, including digital beamforming for BS and analog beamforming for passive RIS, in order to maximize system throughput and reduce mutual interference. In addition, the combination of RIS and NOMA can further improve the performance of these systems.
In recent years, the rational use of secure channel capacity has become a focus of discussion among researchers and scholars [
18,
19], where the secrecy capacity of the transmitted data is investigated and the system is able to reach the maximum transmission rate between a legitimate transmitter and receiver, but this scheme is subject to the limitations of the information available to unauthorized receivers. The authors of [
18] proved that for discrete memoryless channels, the perfect secrecy capability is actually the difference in capacity between two users and generalized similar results to Gaussian channels [
20]. A study considered the case of full channel state information (CSI), where the transmitter has access to the channel gains of both the legitimate receiver and the eavesdropper, and this secrecy capacity under the full CSI assumption was used as an upper bound on the secrecy capacity when only the CSI of the legitimate receiver is known on the transmitter. The authors of [
21] also proposed a low-complexity on or off power allocation scheme that achieves near-optimal performance using only the primary channel CSI. More specifically, the scheme is shown to be asymptotically optimal when the average signal-to-noise ratio (SNR) reaches infinity, achieving the secrecy capability assumed by full CSI. All the above studies show that channel fading has a positive effect on the secrecy capability and rate adaptation based on channel CSI. Therefore, PLS as a technology based on the physical characteristics of the communication channel to protect the security of the communication system has gradually become an important research direction in the field of information security. PLS techniques utilize the physical characteristics of the communication channel, such as signal attenuation, multipath propagation, and time-varying properties, to design security mechanisms that enhance the security of the communication system during the transmission of data [
22]. Researchers are committed to continuously improving the performance and reliability of PLS techniques to cope with the increasingly complex and diverse security threats. And the features of PLS can effectively deal with some of the challenges faced by traditional cryptography, such as key management and side-channel attacks, as well as provide additional security guarantees. Currently, the common PLS schemes are non-orthogonal multiple access (NOMA) [
24], artificial noise (AN) and cooperative jamming [
25].
Since eavesdroppers are unable to decode the information correctly after eavesdropping the data, researchers often employ artificial noise generation at the transmitter to reduce the quality of the received data for eavesdroppers [
26,
27] and to improve the security and reliability of the communication system. For some application scenarios, real-time generation, injection and processing of artificial noise signals are required, which need to be supported by corresponding hardware resources, increasing the system cost and energy consumption, and in order to avoid excessive introduction of noise leading to degradation of communication quality or insufficient security enhancement. Recently, NOMA is considered as a promising technology, which can improve the spectrum and energy efficiency [
28]. The advantage of NOMA is that it can accommodate more users on the same resource block, use superposition coding at the sending terminal and continuous interference cancellation at the receiving terminal [
29], which can reduce the interference of users with better channel quality to users with weaker channel quality, thus improving user fairness and reducing the probability of channel blockage in the IoV. Based on various channel conditions required by NOMA, RIS can be used for intelligent control of random channels, which has been further discussed in recent research. However, most of these works do not consider the influence of the number of RIS components on the safe-rate of data transmission in detail under the NOMA principle.
In the RIS-NOMA assisted IoV communication system, the secrecy capability of the system can be greatly improved even in the presence of eavesdroppers. RIS can help to suppress the interference of communication signals by malicious eavesdroppers with adjusting the characteristics of the reflected signals and improving the security of the system [
30]. RIS can also help to optimize the transmission path of the signals to reduce the signal leakage and the possibility of eavesdropping, as well as enhance the security of the channel links. In previous studies, the location of RIS is often fixed and unchanged, and it is not considered that the location change of RIS not only affects the quality of data transmission to users, but also further affects the overall safe-rate and performance of data transmission in the presence of eavesdroppers. For this reason, it is necessary to explore the impact of RIS location changes on the overall security rate of the system so as to maximize the security rate of data transmission for legitimate users.
We propose a RIS-NOMA system consisting of remote users, near users and eavesdroppers, in which eavesdroppers wiretap on the transmission source data. The maximum security rate under different RIS positions is analyzed.
The balance between RIS deployment location and channel security rate is studied, and the fixed locations of far and near users are considered, respectively.
Numerical results verify the correctness of our analysis as well as the effectiveness of the proposed scheme, providing a significant improvements in terms of safe-rate.
2. System Model and Proposed Scheme
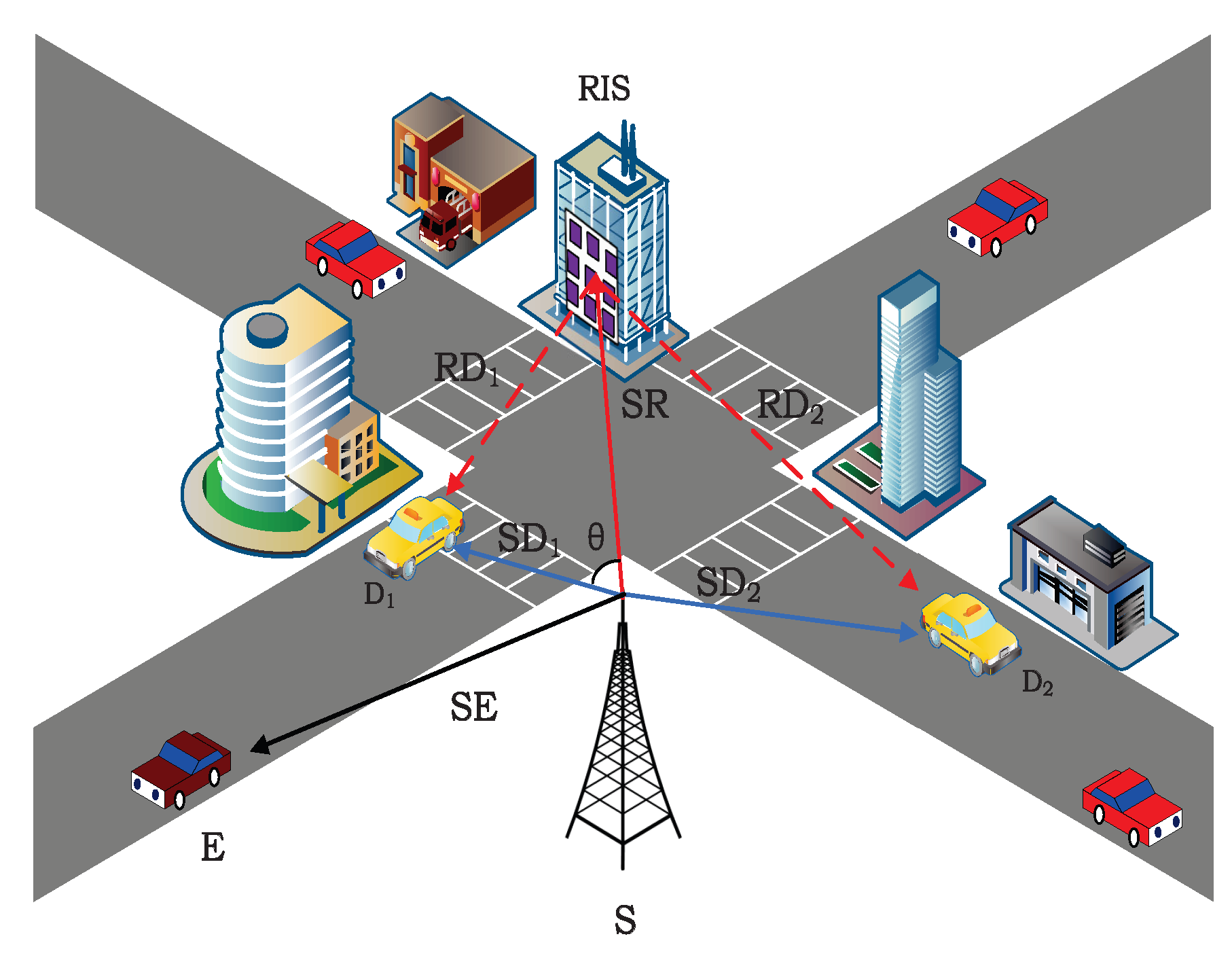
This work considers a RIS-NOMA-assisted secure communication system model, as shown in
Figure 1, which consists of the transmitting source (
S), RIS, two legitimate users
, and the eavesdropper
E. For the channel model, we assume that all nodes are equipped with single antenna, considering that
S and
are known to the eavesdropper to wiretap on the desired data
X within a long distance. With
, the valid data received by
is
, and the valid data received by
is
. Clearly, since the data received by
and
are both on the broadcasting channel, the safe-rate is extremely low. Considering the element size of RIS is much smaller than the RF signal wavelength, thus the elements are able to reflect the incident signal to each direction with constant gain. Furthermore, each element of the RIS is intelligently controllable, and the reflecting elements can control the phase shift.
In the system model of
Figure 1, the direct channels from S to RIS, user
, user
and eavesdropper E are respectively expressed as
, the reflection channel of RIS is
. In the model, user
is considered to be farther away from the transmitter than user
, so the channel gain of
is considered to be less than
, and
represents the norm of the vector. The angle of the RIS deployment position relative to the emission source is
in [0,180]. Because the NOMA scheme will actively consider the fairness of users, there will be differences in setting power distribution coefficients. The power distribution factors of service user
and user
are
and
,
, and the transmission data at S is
, where
and
are the expected signals of
and
, respectively.
2.1. Power Allocation Discussion
2.1.1.
In this section, to ensure fairness among users, we discussed power allocation with two different situations. When
, RIS is equipped with n fixed elements to serve different users with the same number of elements. The channel gains from the transmitter S to RIS and from RIS to user
are
. Similarly, the channel gains from S to RIS and RIS to
can be expressed as
. In addition, it is assumed that all channels experience Rayleigh fading distribution, and the signals received by users
and
can be expressed as
where
P is the transmission power at S,
and
are the transmitted data,
, and the phase shift matrix of RIS at user
is
. The phase shift matrix at user
is
,
is amplitude reflection coefficient. The additive white Gaussian noise (AWGN) at both
and
is characterized by a mean value of zero and a variance of
.
In the communication system assisted by RIS-NOMA, according to the decoding principle of NOMA, user
will first decode
with
as interference. After successfully decoding
, user
decodes
through SIC. Therefore, the SNRs of user
and user
can be respectively given as
Similarly, the SNR of eavesdropper is
,
. Therefore, the achievable rates for received data
and data
are respectively expressed as
where
is the expected value of
x, the eavesdropping rates on data
and data
by eavesdropper is as follow
Finally, the secrecy rate of data
and data
can be further obtained as
where
. Then the secrecy sum-rate of data can be obtained
In the communication system with NOMA, in order to ensure fairness, a larger power allocation factor will be assigned to the poor channel, and
. When
, the user
is closer to the transmitting source, and when
, the channel gain can be expressed as
. Therefore, it can be further deduced from Equations (3)–(5) as
,
, so Equation (
11) can be rewritten as follows
Thus Equation (
12) can be further written as
2.1.2.
In this condition, it can be deduced from Equations (3)–(5) as
so it can be further calculated
, and
. Therefore, the secrecy rate of data
and
can be expressed as
where
, then the secrecy rate can be obtained as
Considering the simple calculation, the Equations (19) and (20) can be directly substituted into Equation (
23) as
4. RIS Deployment Analysis
In this section, we can analysis the influence to RIS-NOMA assisted IoV system with uncertain RIS deployment. Assuming that the channel gain is
,
and the path loss is
, leading to
. In the same way, we have
,
,
. By substituting above results back into Equation (
27), we have
Since the deployment position of RIS and the distance from RIS to S are variable, by means of the Cosine Theorem, the distance from RIS to user
can be expressed as
as well as, the distance from RIS to user
is
Clearly, if direct membership makes the formula very complicated, where
and
are variables, Taylor expansion can be adopted to solve such problem, and the binary Taylor formula is
where
. Letting
and
be
x and
y, respectively, we can get
Let
and
, which can be obtained after substitution in the formula and simplification as
Let
and
, which can be obtained after substitution in the formula and simplification as
Substituting the function values of
and
, we can obtain
5. Numerical Results
In this section, the performance of the proposed system is evaluated by numerical results. Assuming that all channels follow Rayleigh fading, the path loss index is set to 2.2. For simplicity, the position of each node is set to .
Figure 2 shows the relationship between the total safe-rate of data transmission and the angle of RIS position relative to the transmitter. In the proposed scheme, the transmission power is
dBm, and the number of reflective elements is fixed at 1000. As can be seen from the display results in the figure, when
, the safe-rate will gradually decrease with the increase of the distance between RIS deployment location and user
, when
the security rate of data transmission will gradually increase with the decrease of the distance between RIS deployment location and user
. In the simulation, it can be found that there is an intersection between the security rates of data transmission, which is
. When RIS is at this angle, the security rates of the two are equal under different power factor allocation mechanisms, it is also the lowest value of the safe-rate, and the security at this time is the most unreliable. When it is less than this angle, the data will be transmitted by the power distribution factor transmission mode of
. When it is larger than this angle, the data will be transmitted in the transmission mode of
.
Figure 3 shows the relationship between the safe-rate and the deployment position of RIS. When the RIS is gradually away from the user
, the transmission rate of data
gradually decreases. While the eavesdropper directly eavesdrops on the data
of S, the eavesdropping rate will not change due to the change of the deployment position of RIS, but the change of the position of RIS has little influence on the transmission rate of data
, because under the NOMA principle,
will be decoded. Furthermore, the safe-rate of the total data transmitted is similar to that of the data
. Similarly, when the RIS gradually approaches the user
, its channel quality gradually passes the user
, thus changing the power factor distribution of the channel, and the safe-rate will gradually increase after crossing the point. In this paper, the simulation assumes that the initial states are all on the same level with users
,
and S.
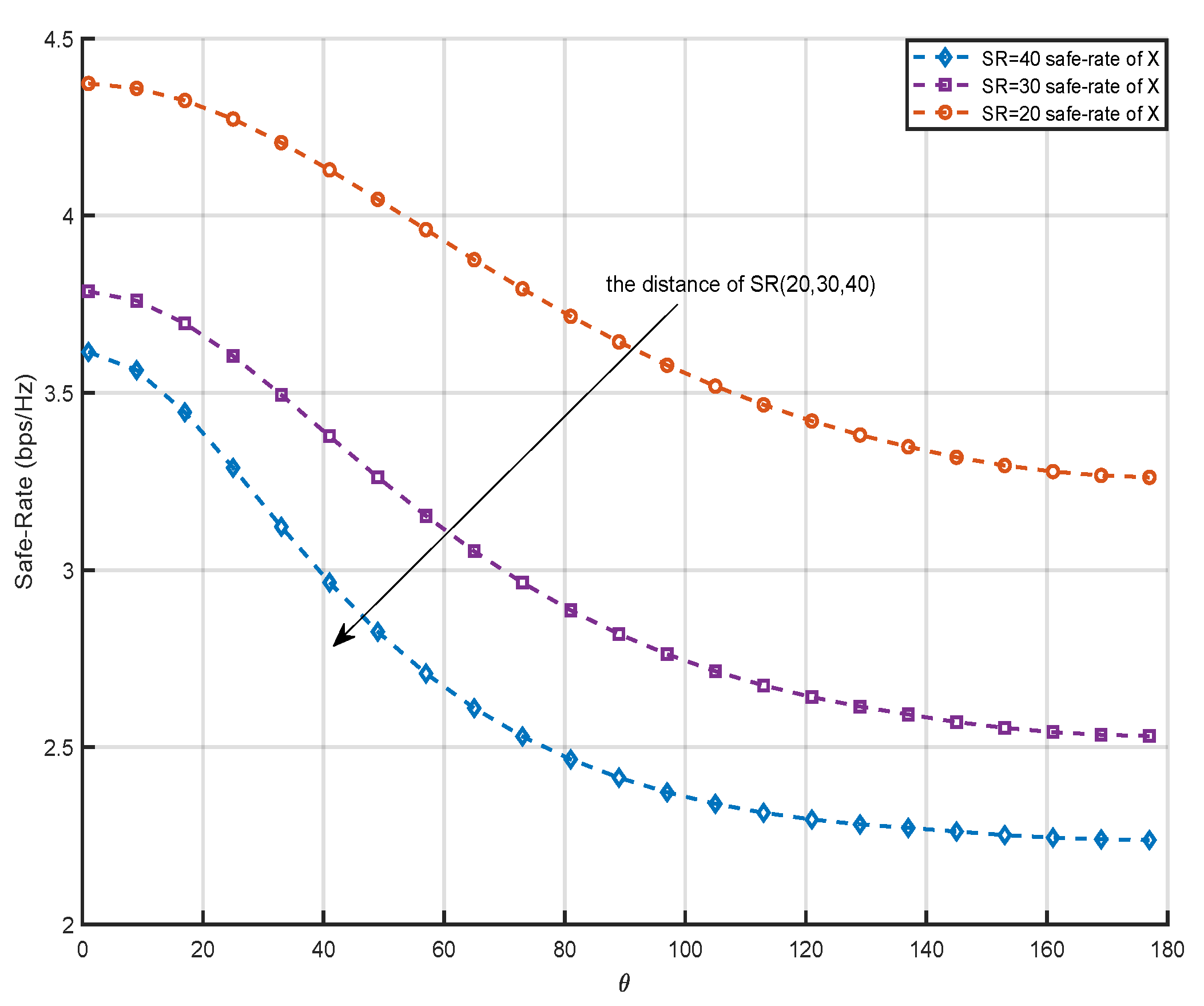
Figure 4 shows that when the S is fixed and the distance between RIS and S is changed, the performance of safe-rate is different. Assuming that the distances from S to RIS are 20m, 30m and 40m respectively, it can be seen that the safe-rate is gradually improved as the deployment position of the RIS is closer to the S. This is because when the deployment position of RIS is close to the S, the path loss decreases and the channel quality of the cascaded channel is improved, so the safe-rate will increase with the decrease of the distance from the S. The changing trend of the curve in the figure is that the RIS gradually moves away from the user
, which weakens the data transmission quality of the RIS service user
channel, so the safe-rate of data
will decrease with the increase of the angle. Similarly, because the deployment position of RIS is gradually close to user
, the safe-rate of data
will gradually increase with the increase of the deployment angle of RIS relative to the S.
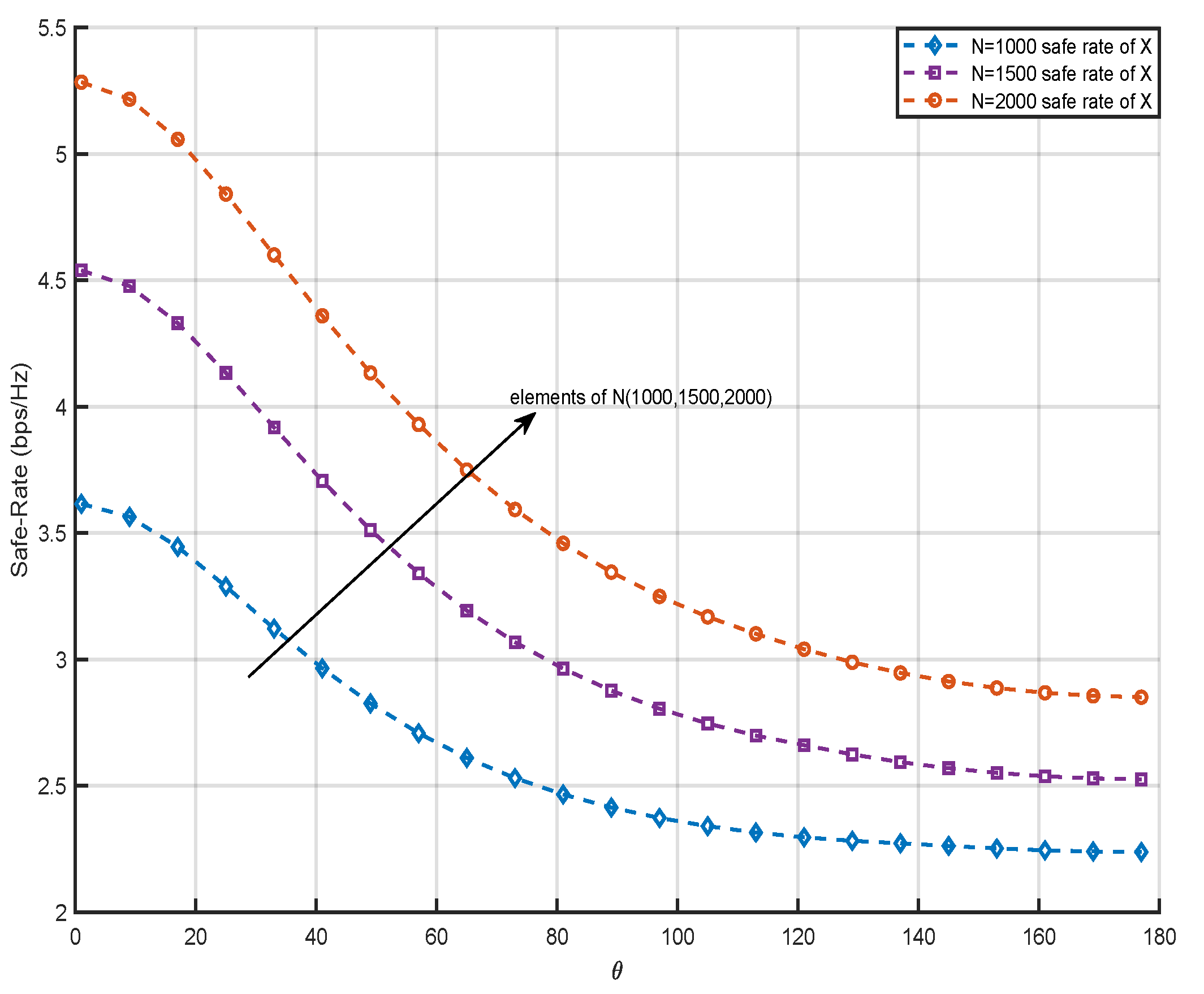
Figure 5 shows the influence of increasing the number of RIS elements on the safe-rate of data
when S is fixed. Assuming that the number of elements of RIS is 1000, 1500 and 2000 respectively, it can be seen from the graphic information that the safe-rate is more reliable with the increase of the number of RIS distribution elements, and it can be seen that the safe-rate is gradually improved with the deployment position of RIS getting closer to the S. This is because when the number of elements of RIS increases, the channel quality of the cascade channel is enhanced, so the safe-rate will increase with the increase of RIS elements number. The changing trend of the curve in the figure is that the RIS gradually moves away from the user
, which weakens the data transmission quality of the RIS service user
channel, so the safe-rate of data
will decrease with the increase of the angle. Similarly, because the deployment position of RIS is gradually close to user
, the safe-rate of data
will gradually increase with the increase of the deployment angle of RIS relative to the S.
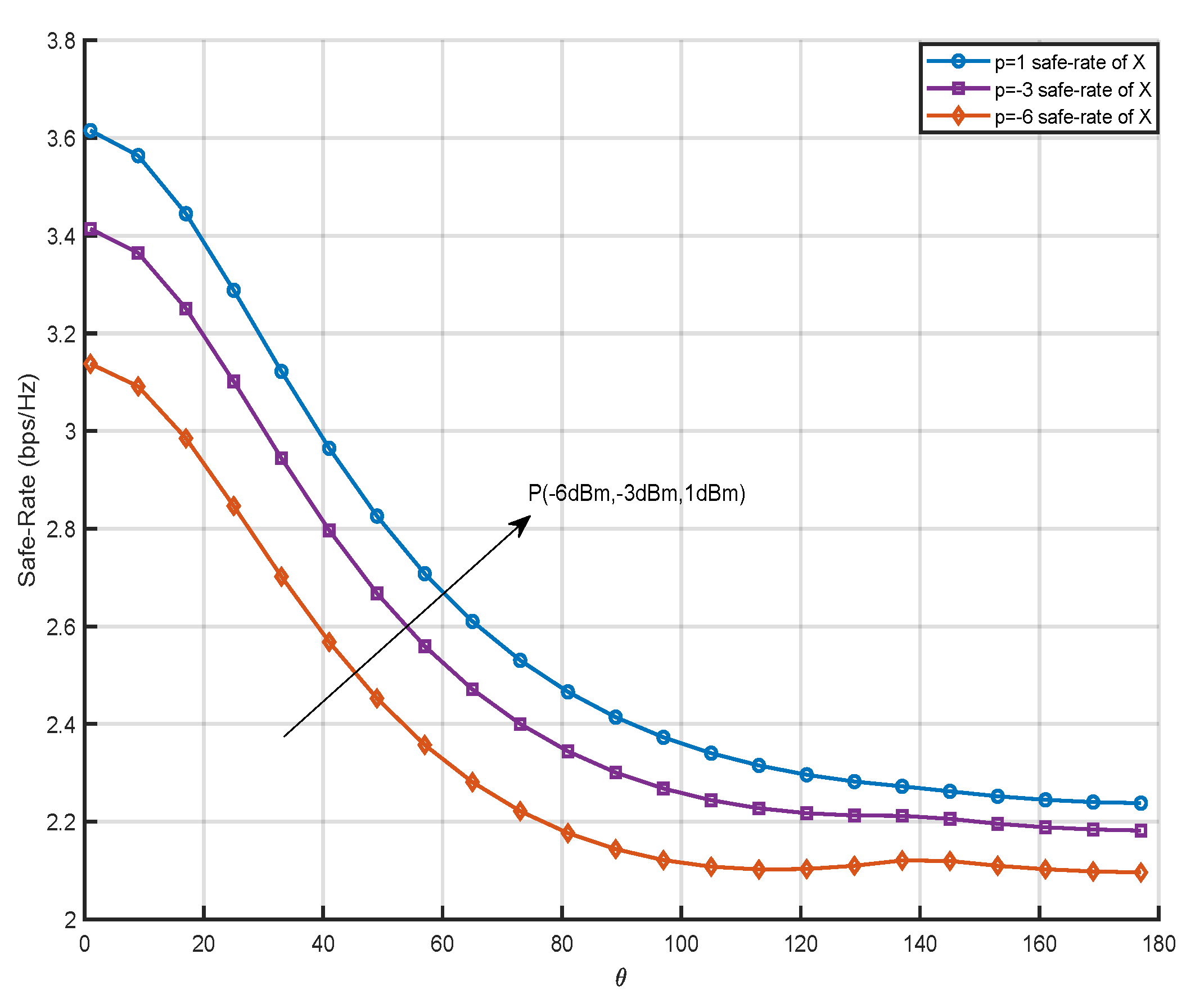
Figure 6 shows the influence on the safe-rate of data
when the S is fixed and the transmission power is increased. Assuming that the transmission power is 1dBm, -3dBm and -6dBm respectively, it can be seen that with the increase of the transmission power, the safe-rate is more reliable. This is because when the transmission power increases, the channel quality of the cascade channel is enhanced, so the safe-rate will increase with the increase of the transmission power. The changing trend of the curve in the figure is that the RIS gradually moves away from the user
, which weakens the data transmission quality of the RIS service user
channel, so the safe-rate of data
will decrease with the angle increase. Similarly, because the deployment position of RIS is gradually close to user
, the safe-rate of data
will gradually increase with the increase of the deployment angle of RIS relative to the S.
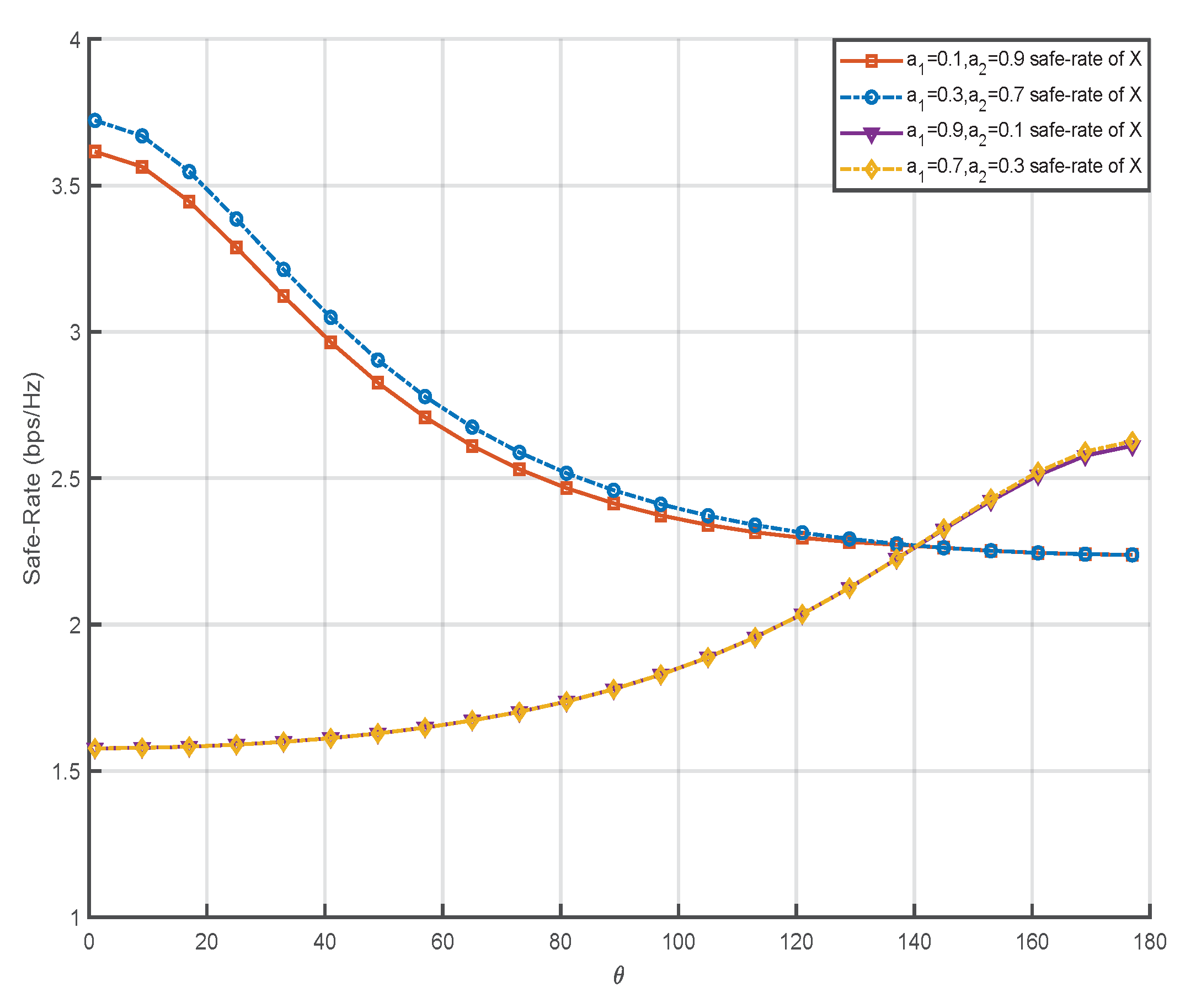
Figure 7 shows the relationship between the power allocation factor coefficient and the angle of RIS relative to the S. In the proposed scheme, the power is
dBm and the number of RIS elements is fixed at 1000. It can be seen from the display results in the figure that when the power allocation factor coefficient changes, it will not have a great influence on the trend of the simulation curve. When
, the safe-rate of data transmission will gradually decrease with the increase of the distance between the RIS deployment position and the user
. While
, the safe-rate of data transmission will gradually increase with the decrease of the distance between the deployment position of RIS and the user
. In the simulation, it can be found that even if the power allocation factor coefficient changes, the intersection point of the safe-rate of data transmission will not change, and the lowest value of the safe-rate will not change. Because there is no power allocation factor in Equation (
36), and the simulation results also verify the correctness of the formula derivation.