Submitted:
22 July 2024
Posted:
24 July 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
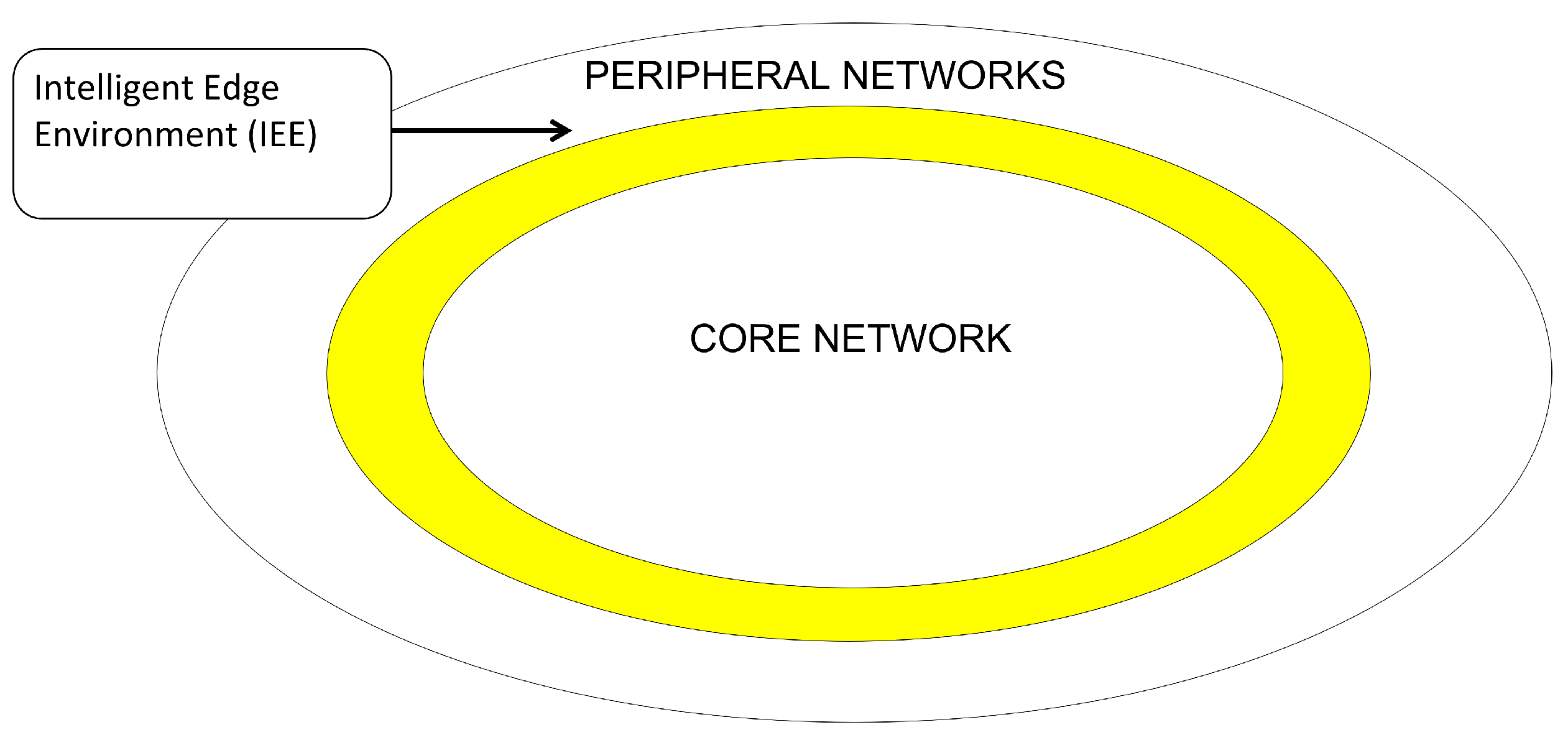
1.1. Intelligent Edge Environment Layers
- Layer 1: Heterogeneous Networking Layer (HNL): It integrates different types of wireless networks or technologies, providing connections using various technologies such as 4G, 5G, WIFI, and Cellular.
- Layer 2: Data Management Layer (DML): The layer has a crucial role in handling vast amounts of data generated by edge devices such Connected and Autonomous Vehicles (CAVs) and uses many structures such as blocks, files, databases, and Machine Learning (ML) to manage data.
- Layer 3: High-Performance Edge Cloud Systems (HPECS): This layer supports various cloud architectures and cloud types, including private, public, hybrid, and community clouds (AWS, Hadoop, etc.) using Virtual Machine (VMs) including VMware and Citrix ecosystems and Video Streaming, Augmented and Virtual Reality and Autonomous systems. Therefore, Resource Allocation Servers (RAS) are needed to manage various HPECS systems.
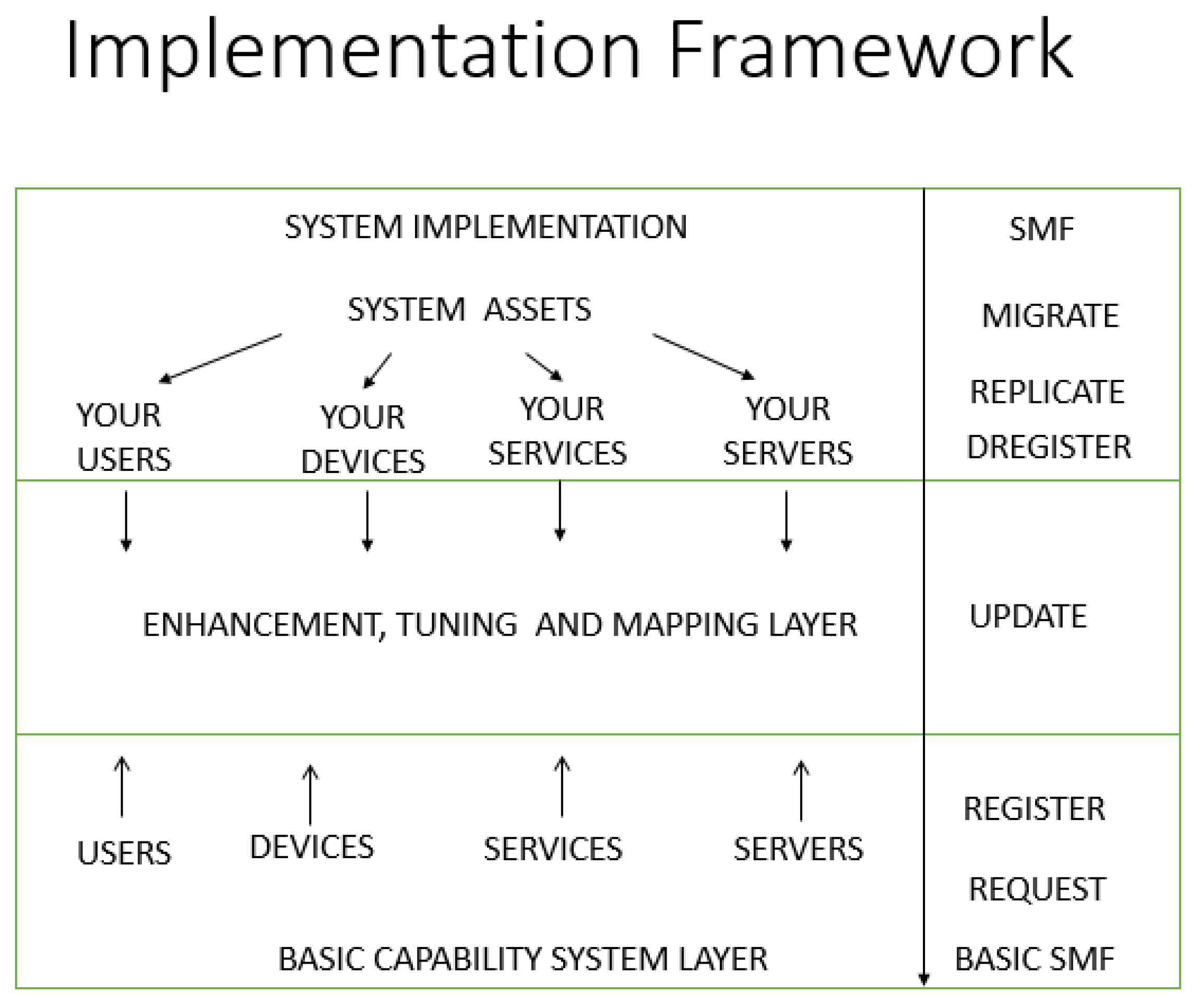
- Layer 4: Service Management Framework: This layer manages services and servers within the system. It offers mobile service support by migrating and replicating services using various migration techniques like Docker (containerization), KVM (virtualization), and Unikernels (specialized single-purpose virtual machines) to migrate services, using AI techniques to ensure that the service meets performance requirements.
- Layer 5: Microservices Layer (MSL): This layer supports for micro services and is the responsible for independently deployable services. These services should be fast and small in order to be easily migrated.
- Layer 6: Application Framework Layer (APL): This layer uses the microservices layer below to provide applications frameworks in order build applications for different environments such as Mobile Communications, Vehicular Networking, and IoT Smart Grids.
- Layer 7: Application Layer: This layer allows applications that have been built using the Application Framework Layer to be installed on the system and made available to users. Through this layer, users get applications that use all the resources of the IEE.
- A new simple Resource Allocation Algorithm (RAA) is developed to run on a Resource Allocation Server (RAS). To enable mobile service, this algorithm has to be simple and fast.
- A new secure transfer protocol called the Resource Allocation Secure Protocol (RASP) is detailed. This will involve the use of cryptographic protocols such as ProVerif to show that the transfer protocol is safe.
- A secure access control system using capabilities, this is necessary to provide the Authentication, Authorization, Accounting (AAA).
- A new Secure Service Protocol is devolved using these mechanisms.
- The development of a new Service Management Framework (SMF) which can be used to manage applications and services in the IEE.
- The design of a capability-based Secure Service Protocol (SSP) to provide a complete framework for the IEE. The SSP is shown to be safe using Proverif.
- The implementation of a prototype SSP system using a Network Memory Server (NMS) to provide backing storage for a FUSE file system in a vehicular network.
2. Related Work
3. The Simple Resource Algorithm
- 1
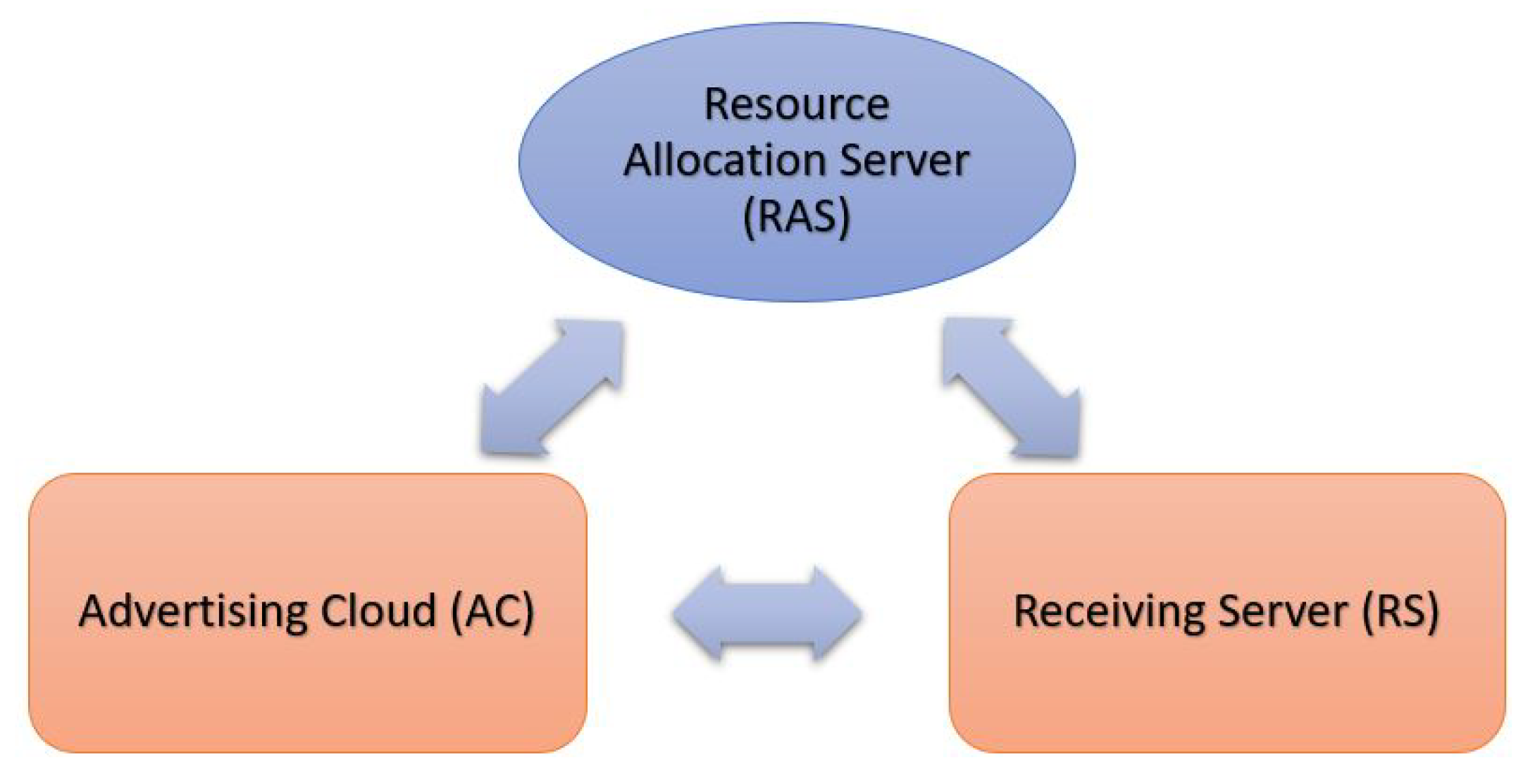
- Advertising Cloud (CA, CB, CC...etc): Each Cloud Service Provider (CSP) has a finite set of resources available for servers and services. The cloud system broadcasts its available resources (CPU, memory, network, and storage) to the Receiving Servers.
- 2
- Receiving Servers (SA, SB, SC...etc): These servers can choose to migrate their services to the Advertising Clouds based on their hosting requirements.
- 3
- Resource Allocation Server (RAS): A trusted party responsible for verifying the resources of Advertising Clouds and the hosting requirements of Receiving Servers.
| Resource Allocation Server | Adverting Cloud (CA) | Adverting Cloud (CB) | Adverting Cloud (N) |
|---|---|---|---|
| Receiving Server (SA) | CPU, Memory, Network and storage | CPU, Memory, Network and Storage | CPU, Memory, Network and Storage |
| Receiving Server (SB) | CPU, Memory, Network and Storage | CPU, Memory, Network and Storage | CPU, Memory, Network and Storage |
| Receiving Server (N)1 | CPU, Memory, Network and Storage | CPU, Memory, Network and Storage | CPU, Memory, Network and Storage |
3.1. Advertising Cloud Formulation
-
Stage 1 1. CB → SA : Advc (CB, ResCB) ) [CB → SA: Advertising Cloud (CB) sends an advertisement (Advc) to the Receiving Servers (SA), detailing the free resources (Res freeCB)].
- -
- Maximum Resource of Cloud () = [CPU (Cmc), Memory (Cmm), Storage (Cms), Network (Cmn)],
- -
- Allocated Resource of Cloud () = [CPU (Cac), Memory (Cam), Storage (Cas), Network (Can)]and
- -
- Free Resource of Cloud () = [CPU (Cfc), Memory (Cfm), Storage (Cfs), Network (Cfn)]
| Algorithm 1 Cloud CB Formation |
|
- Step 1: The resources in consideration are categorized as CPU, Network, Memory, and Storage: Resources (r) include: CPU (c), Network (n), Memory (m), and Storage (s).
- Step 2-4: These steps define the maximum capacity for each type of resource (), current allocation of resources () and the available (unallocated) resources () in the AC.
- Step 5-10: Condition Check and Advertisement: The condition checks if there are any free resources (). If there are free resources, the AC sends an advertisement of these resources and waits for a response. If there are no free resources, the system waits until resources become available when () is greater than 0.
3.2. Receiving Servers Formulation
-
Stage 2 2.SA → R : (SA, CB, ResCB)pkR [SA → R: Receiving or Requested Servers (SA) sends an advertisement (Advc) to the Registry to verify the free resources (Res freeCB) and adding their identities].
- -
- Requested Resource of Server (Req_Res of SA ()) = {} CPU (Src), Memory (Srm), Storage (Sms), Network (Srn)]
| Algorithm 2 Server SA Formation |
|
[H]
|
- Step 1: The resources CPU, Networks, Memory, Storage are members of resources(r).
- Step 2-3: Server SAs Requested resources are declared. Inclusion of an element Req_Res to a set of SAreqr resources.
- Step 4-5: If Requested resources are greater than 0, the cloud services needs to find the next best fit server.
- Step 6-9 Condition check before resource Migration: It checks if the AC has sufficient free resources to meet the Receiving Server’s request. If sufficient resources are available and greater than 0, the request is accepted, and the details are sent to the RAS for verification and processing. Else ignore the advertisement.
3.3. Resource Allocation Server
- Registration and Certification: The RAS confirms the registration of cloud providers and certifies the capacity of resources available with the registered cloud providers.
- Request Verification: When a request for resources is received from a Receiving Server (SA), the RAS verifies the resources based on specific criteria before approving the migration.
- Stage 2 3. R → SA: sign((CB, pkC, ResCB), pkS) [R → SA: The Registry approves the advertisement (Advc) and sends to the Receiving Servers (SA), detailing the free resources (Res freeCB) with its signature].
| Algorithm 3 RAS_CB |
|
- Step 1-2 Verify Validity: The RAS server verifies whether it is a valid cloud and if Cloud resources are greater than the requested resources. If either condition false, then it rejects the request and updates CB that its an invalid server.
- Step 2-5 Pass Conditions: If the above conditions pass, then it sends an authenticated message to CB. This message confirms the approval of the resource migration.
| Algorithm 4 RAS_SA |
|
- Step 1-2: RAS server verifies whether it is a valid server and if Cloud resources are greater than the requested resources which is not equalt 0 or not. If either conditions are false, then it rejects the request and updates SA that its an invalid Cloud.
- Step 2-5: If the above conditions pass, then it sends an authenticated message to SA.
4. RASP Protocol—An Overview
4.1. General Notations
| Notation | Explanation |
|---|---|
| CA, CB, SA and SB | Cloud and Server Identities |
| pkC/skC, pkS/skS, pkR/skR | public and private key pairs of Cloud CB, server SA & Registry |
| M_Reqc, M_Trfs, M_Ackc | Request for migration, trannsfers and acknowledgement |
| sign | Signature/signed by the Registry |
| aenc | Asymmetric Encryption |
| enc | Symmetric Encryption |
| Ksc | Symmetric session key |
| Ns, Nc | Nonce of SA and CB |
| ResSA | Requested Resources of SA & CB |
- 1
-
Stage1: Advertisement:Cloud CB actively advertises its resources Server SA receives advertisements from Cloud CB advertising Cloud Bs resources with its identity CB.1. CB → SA : Advc (CB, ResCB)
- 2
-
Stage2: Authentication of SA and CB as well as migration request and response:Server SA first requests the RAS/Registry to authenticate Cloud CB and its resources. In Step 3, the Registry (R) authenticates Server SA. In Step 4, Server SA sends a migration request to Cloud CB. In Step 5, Cloud CB sends a request to the Registry to verify that Server SA’s request for resources is valid. In Step 6, the Registry replies to Cloud CB. In Step 7, Cloud CB sends the migration response back to Server SA.2. SA → R : (SA, CB, ResCB)pkR3. R → SA : sign((CB, pkC, ResCB), pkS)4. SA → CB : aenc ((Ns, SA , ResSA), pkC)5. CB → R : (CB, SA , ResSA)pkR6. R → CB : sign((SA, pkS , ResSA), pkC)7. CB → SA : aenc((Ns, Nc, CB), pkS)
- 3
-
Stage3: Migration transfer:In Step 8, Server SA generates the session key (Ksc) to start the migration request. In Step 9, Cloud CB sends the migration initialization request. In Step 10, Server SA performs the migration transfer. In Step 11, Cloud CB sends an acknowledgment to Server SA. In Step 12, the service on Cloud CB (SB) updates the Registry on its new location.8. SA → CB : aenc((Nc, Ksc), pkC)9. CB → SA : enc ((M_Reqc, SA), Ksc)10. SA → CB : enc ((M_Trfs, ResSA), Ksc)11. CB → SA : enc ((M_Ackc), Ksc)
- 4
-
Stage4: Update of New service location to the Registry:The new service SB is now running on Cloud CB and informs the Registry that it has been successfully migrated.12. SB → R : aenc((SB, CB), pkR)
4.2. ProVerif an Overview
4.2.1. ProVerif Results
- Nonces are secured and not derived by the attacker: specific nonces (SNs, SNc, CNs, CNc) used in the protocol are not derivable by an attacker, ensuring their confidentiality. Each line indicates that the respective nonce cannot be compromised (is true).
- session key Results confirms that the session key (Ksc) and associated bitstrings (SNk, CNk) are secure from the attacker. The line "RESULT not attacker_bitstring (SNk []) is true." with Ksc also specifies the conditions under which this key is secure.
- Private keys Results confirms that the session key (Ksc) and associated bitstrings (SNk, CNk) are secure from the attacker. The line "RESULT not attacker_bitstring (SNk []) is true." with Ksc also specifies the conditions under which this key is secure.
- AuthenticationIt validates the mutual authentication between SA and CB. The use of inj-event indicates that the protocol verifies injective correspondence, meaning each event endSparam (or endCparam) has a matching beginSparam (or beginCparam), ensuring that both parties authenticate each other correctly.
| Security properties | Server SA event | Cloud CB event |
|---|---|---|
| Session key | True | True |
| Private keys | True | True |
| Nonces | True | True |
| Event begin | True | True |
| Requested resources | True | - |
| Advc Resources | - | False |
5. Capabilities
- Unique Object Identification and Access Rights
- Functionality: Capabilities can provide Role-Based Access Control (RBAC) access for users. Some capabilities are not directly assigned to users; instead, they are assigned to roles, and roles are then assigned to users. These are known as role-based capabilities.
- Role Assignment: Capabilities can be assigned to roles. Roles are then assigned to users. This structure supports RBAC, ensuring that users have access based on their roles within an organization.
- IPv6 Address Space and Capability ID System: Utilizes a modified Location/ID split based on the work of [16]. Enables the creation of a capability ID-based system for people, applications, and cloud infrastructure.
5.1. Capabilities in IEE
5.1.1. Capabilities Structure
- Type Field (8 bits): This field specifies the type of object capability being used, such as users, digital assets, facilities, etc.
- SYS Field (4 bits): This field helps manage capabilities. The four bits within the SYS field are explained below.
- Property Field (12 bits): This field defines the properties of the object associated with the capability. It relates to the properties or functions of the object that the capability refers to.
- Object ID (72 bits): This field uniquely identifies the object in the system. It includes a EUI-64 identification field to identify the object and an 8-bit netadmin field to manage the object on a network.
- Random Bit Field (16 bits): Provides unforgeability and helps uniquely identify the object. This field is generated after the type field, SYS field, property field, and Object ID field are created. When proxy certificates are created, a new random field is generated. This field also allows for easy revocation of capabilities by simply changing the random field and recomputing the capability, hence revoking previous versions.
- Hash Field (16 bits): Detects tampering of capabilities. When a capability is created, the type field, SYS field, property field, and Object ID field are first generated, followed by the random bit field. These fields are then used to generate a SHA-1 hash, which is placed in the Hash Field of the capability.
- Private or P bit: Restricts the list of people holding the capability. With a public capability, only the capability for the object must be presented, allowing anyone to hold it without needing the identification of the subject, the person holding the capability. With a private capability, both the object’s capability and the subject or user’s capability must be presented to ensure the sender has the right to invoke the object.
- System or S bit: Indicates whether the object involved was created by the system or by an application or user. A system capability cannot be modified or deleted by users or applications.
- Master or M bit: Indicates that the capability was created by a Certificate Authority (CA). The master capability is usually created when the object is created. If this bit is not set, it means this is a proxy capability. Proxy capabilities are derived from master capabilities and cannot be derived from other proxy capabilities.
- Change or C bit: Indicates whether this capability can be changed. If this bit is set, proxy capabilities can be derived from the master capability. If this bit is not set, the capability cannot be modified, and proxy capabilities cannot be generated.
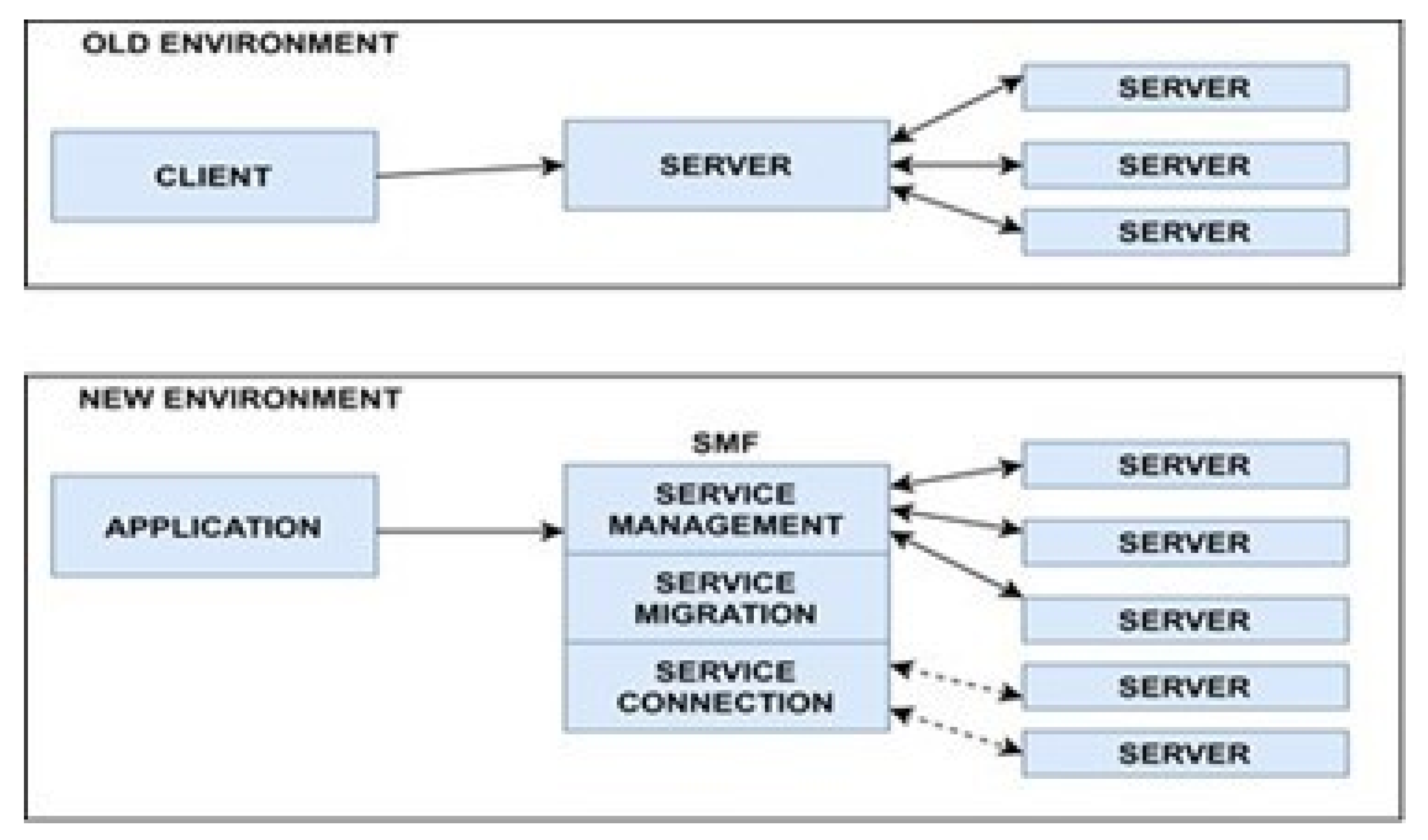
6. The Secure Service Protocol (SSP)
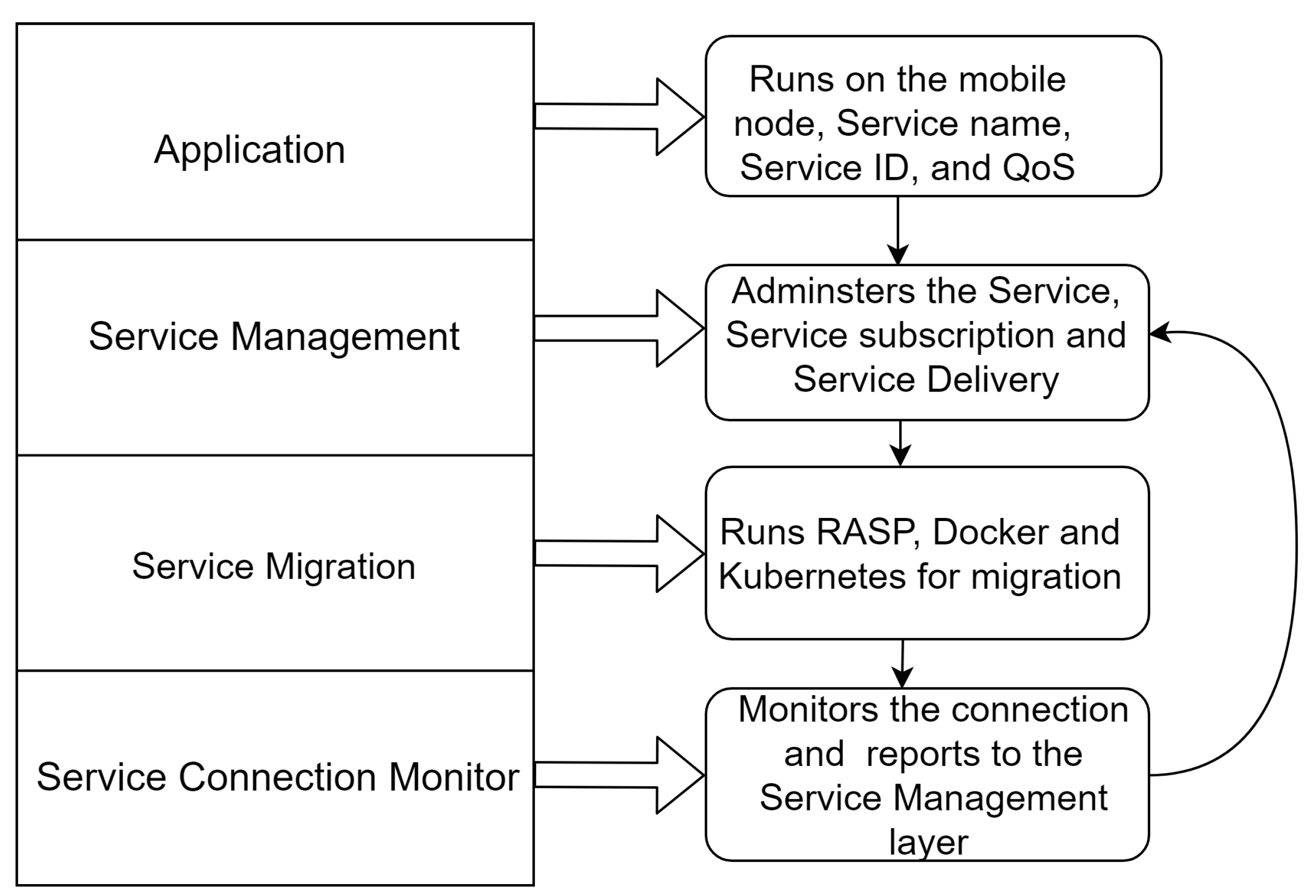
6.1. SMP Layers in Detail
- The Application Layer (AL) is the first layer of SMF. It runs on the mobile node and calls the service through the Service Management Layer (SManL). AL provides the service name, Service ID, and required QoS. When a service first comes to the SMF, it should have a unique ID for identification. The service name indicates the type of service being provided, such as CPU, Memory, or Storage. Lastly, the Application Layer must define QoS parameters for the required service, such as delay time, latency, bandwidth, reliability, and security.
- The Service Management Layer (SManL) is responsible for administering the mobile service, managing service subscriptions, and overseeing service delivery for the layers below it. Service subscription includes managing Service-Level Agreements (SLAs) and billing. Service delivery entails determining how services should move from one location to another. When this layer determines that a service should be migrated, it forwards this information to the service migration layer (SML).
- The Service Migration Layer (SML) manages migration requests from SManL and employs a Resource Allocation Security Protocol (RASP) to securely execute the migration process. Upon completion, SML informs SManL. The RASP, as described by [19], utilizes standard migration mechanisms like Docker, KVM, LXD, and Unikernels for the actual migration.
- Service Connection Layer (SCL): This layer monitors how clients connect to the services between the mobile node and the server. It reports to the SManL when the mobile node is no longer available due to handover to another network.
6.2. SSP Protocol—An overview
-
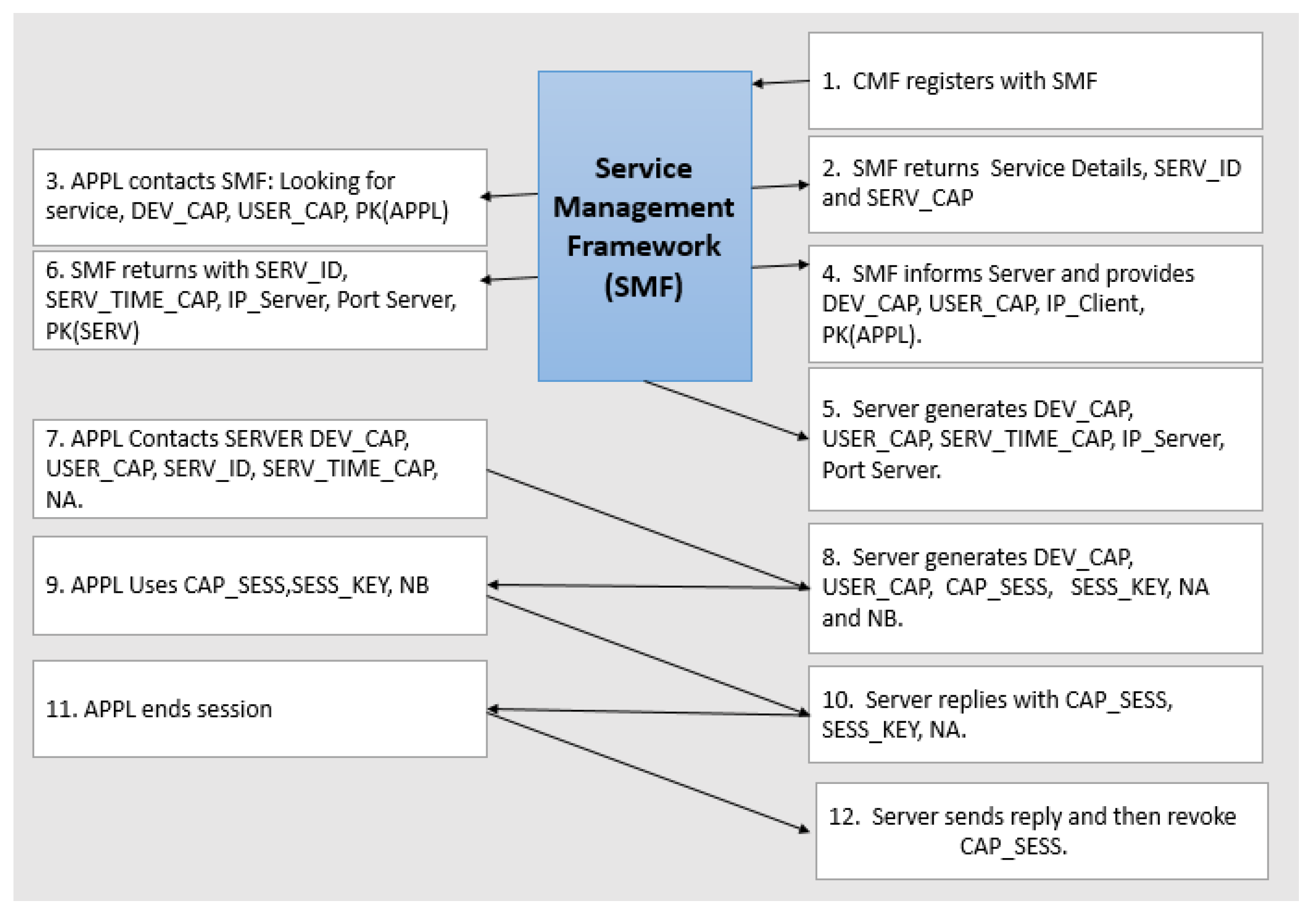
Stage 1: Registration of the Service with the SMF: In Stage 1, the Cloud Management System (CMS) registers the Service with the SMF. This involves providing a list of servers and their public keys that will be running the Service. After this, in step 2, the SMF registers the Service and returns the Service ID (SERV ID) and the Service Capability (SERV CAP). Following this, the CMS initiates the servers to implement the Service on different machines and passes the Service ID and the Service Capability.
- 1
- CMS → SMF: (Register Service (Service Details), (PK(SMF)))
- 2
- SMF → CMS: (Service Registered (Service Details, SERV ID, SERV CAP), (PK(CMS)))
-
Stage 2: The Application interacts with the SMF to get a server that implements the Service: In Stage 2, the Application interacts with the SMF to obtain a server that provides the Service. To utilize a service, an application must request the SMF to locate a suitable server. In step 3, the Application provides the Device Capability (DEV CAP), User Capability (USER CAP), Service Name, Service Version, and the Application’s public key running on the machine. In step 4, the SMF selects a server for that Service and contacts it using its public key, passing the Client’s DEV CAP, USER CAP, and IP address. In the subsequent step, the Chosen Server accepts the request. It generates a timed capability from the service capability, which expires in 60 seconds if the Application does not connect to the server. This SERV TIME CAP is a private proxy capability derived from the Service Capability and cannot be altered; only the USER CAP and DEV CAP can utilize the capability. The Chosen Server also provides its IP address and the TCP port of the Service using the public key of the SMF. In the final step of Stage 2, the SMF returns to the Application with DEV CAP, USER CAP, timed capability, the Server’s IP address, Service Port number, and public keys of the Chosen Server, enabling the Application to connect to the server.
- 3
- APPL→ SMF: (Request service (Service Name, Service Version, DEV CAP, USER CAP, PK(APPL)), (PK(SMF))
- 4
- SMF Chosen ->Server: (Usage request (DEV CAP, USER CAP, IP Client),(PK(SERV))).
- 5
- Chosen Server-> SMF : SMF (Usage request accepted (DEV CAP, USER CAP, SERV TIME CAP, IP Server, Port Server), (PK(SMF)))
- 6
- SMF→ APPL: (Request service accepted (DEV CAP, USER CAP, SERV TIME CAP, IP Server, Port Server, PK(SERV)), (PK(APPL)))
-
Stage 3: The Application sets up a secure session with the Server. During Stage 3, the Application initiates a secure session with the Server by sending a session start request. This request includes the DEV CAP (device capability), USER CAP (user capability), SERV ID (server ID), a unique random number called Nonce of A (NA), the Server’s public key, and the SERV TIME CAP (server time capability). Nonce (NA) ensures that the session is unique on the Application side. In response, the Server sends back a session capability (CAP SESS), DEV CAP, USER CAP, NA, NB (another unique random number for the Server side), and a session key (SESS KEY). The SESS KEY is a symmetric key used only once to encrypt the details in one communication session.
- 7
- APPL → Chosen Server: (Session Start Request (DEV CAP, USER CAP, SERV ID, SERV TIME CAP, NA)), (PK(SERV)).
- 8
- Chosen Server→ APPL : (Session Start Request Accepted DEV CAP, USER CAP, CAP SESS, SESS KEY, NA, NB), (PK(APPL)).
-
Stage 4: The Application gets service by using the CAP SESS key and encrypts using the SESS KEY In Stage 4 of the process, the application uses the CAP SESS key to access a service and encrypts data using the SESS KEY. The application sends a service request to the chosen server with the CAP SESS, Nonce (NB), and uses the SESS KEY. The server responds by sending CAP SESS, NA, and detailed results using the SESS KEY. NA ensures that the session is unique on the application side.
- 9
- APPL → Chosen Server : (Service Request (CAP SESS, NB, Request Details)(SESS KEY))
- 10
- Chosen Server → APPL: (Service Request Done (CAP SESS, NA, Result Details) (SESS KEY))
-
Stage 5: The Application is finished and terminates the session In Stage 5, the application terminates the session by sending end requests to the chosen server with CAP SESS, nonce (NB), and session end using the session key. The server then terminates the session and revokes the CAP SESS capability to prevent replay attacks.
- 11
- APPL → Chosen Server :(Session End Request Accepted (CAP SESS, Nonce (A), Session End)(SESS KEY)).
6.3. ProVerif results
6.4. Queries for Private Keys
- RESULT not attacker_skey(sksmf[]) is true.
- RESULT not attacker_skey(skcms[]) is true.
- RESULT not attacker_skey(skappl[]) is true.
- RESULT not attacker_skey(skS[]) is true.
6.4.1. Queries for Nonces
- RESULT not attacker_bitstring_(SERVERNA[]) is true.
- RESULT not attacker_bitstring_(SERVERNB[]) is true.
6.4.2. Queries for Symmetric Key
- RESULT not attacker_key (Ksappl[m7 = v_10131,m4 = v_10132,!1 = v_10133]) is true.
- RESULT not attacker_bitstring (SERVERk[ []) is true.
6.4.3. Queries for authentication of Server event and CMS event
-
RESULT inj-event(endSERVERparam(x_24696)) →inj-event(beginSERVERparam(x_24696)) is true.
-
RESULT inj-event(endCMSparam(x_38772)) →inj-event(beginCMSparam(x_38772)) is true.
-
RESULT event(endCMSparam(x_42655)) →event(beginCMSparam(x_42655)) is true.
7. Prototype Implementation
7.1. Basic capability System Library(BCSL)
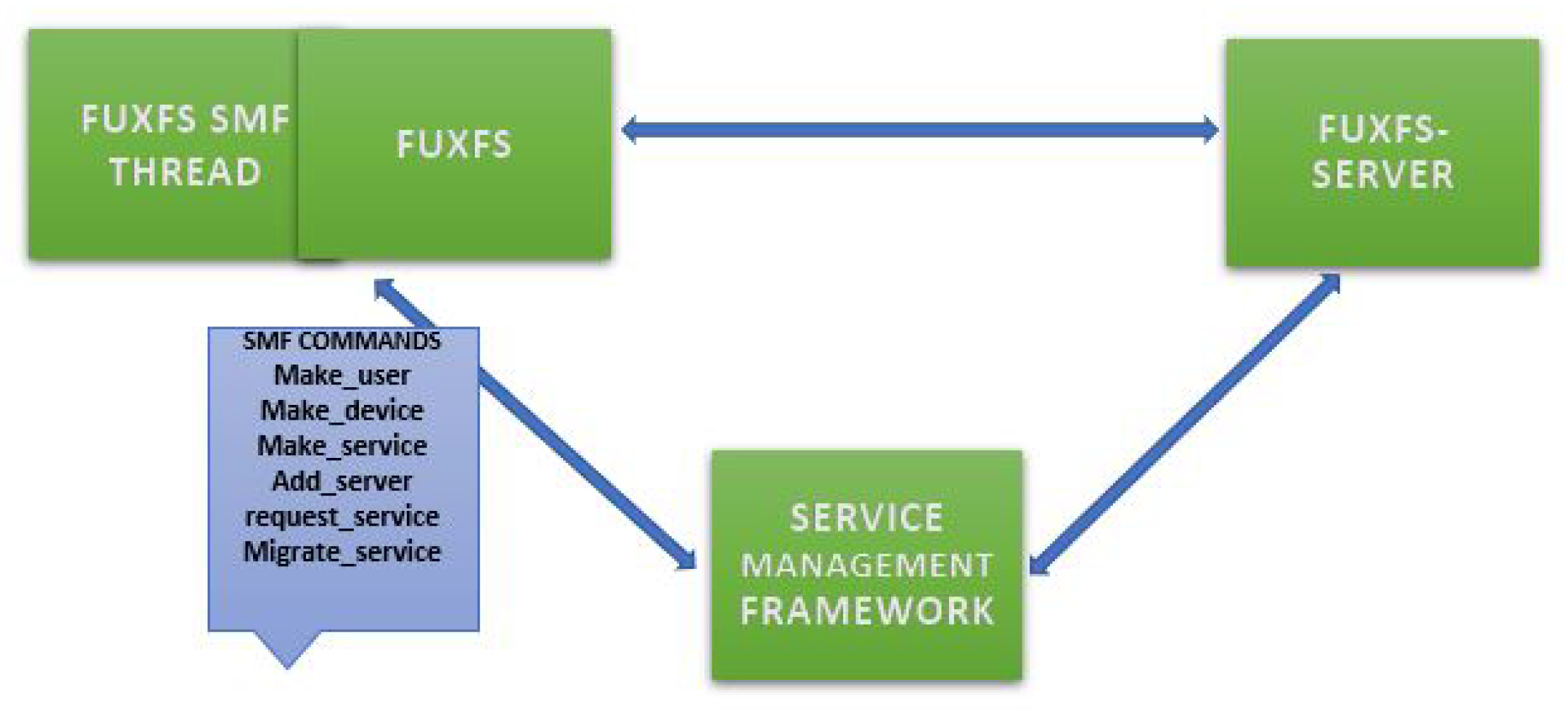
7.2. Make Fuxfs Multithreaded
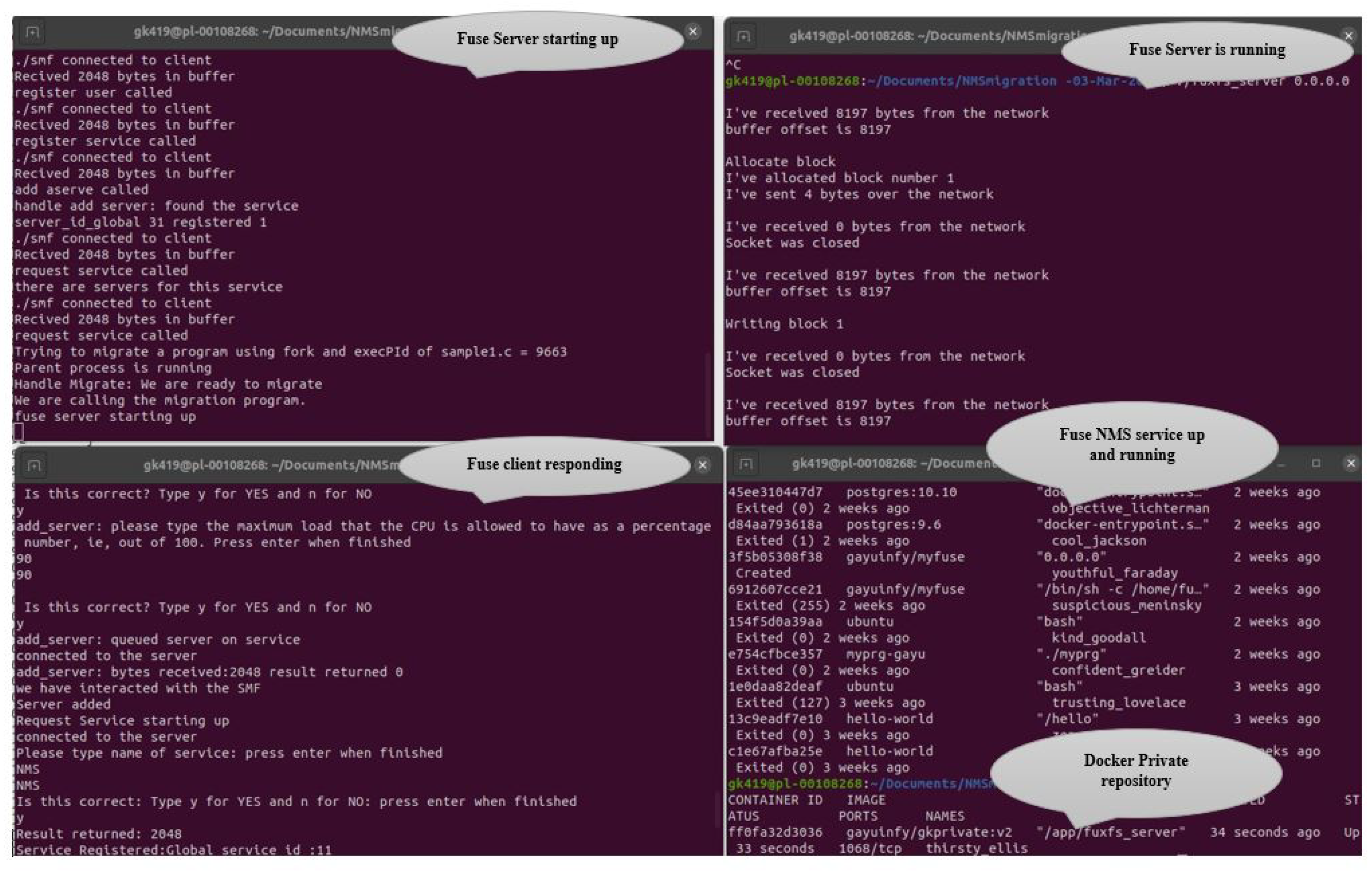
7.3. Fuxfs Server
- Compile command: gcc -o Fuxfs_server Fuxfs_server.c
- Run command: ./Fuxfs_server 0.0.0.0
7.4. Fuxfs Client
- Compile command: gcc -Wall fuxfsmg.c `pkg-config fuse –cflags –libs` -o fuxfs -w -L./ libcapab.a -lpthread
- Run command: ./Fuxfs /tmp/fuse 0.0.0.0
7.5. Make Fuxfs Multithreaded
7.6. Multithread - SMF Commands
- Register Service: The function allows the service to be registered with the SMF. It collects information on the service, including the service name, the description of the service, the version of the service (i.e., 0 is the latest version), the TCP/UDP port number, and the service capability. Once the service has been successfully registered with the SMF, the SMF generates the global_id. The local_id is generated by the client.
- Register User: This function helps the new user register with the SMF. It collects information about the user, including the first name, surname, role, rank, and specialist, as well as the capability of the user to register. Once the user has been successfully registered with the SMF, the SMF will generate their global user ID. Each device will have a unique local device ID (generated by the SMF_THREAD) and a global device ID (generated by the SMF).
- Register Device: This register device function allows the devices to register with SMF. To register a device, the name of the device, the first name and surname of the device owner, and the device capability are also collected once the device is registered. Each device will have a unique local device ID and a global device ID.
- Add Server: This function helps the server be added to the required service. It also collects details about the server, including the server global ID given by NMS, the server’s name, the server location using the IPv4 address, and the server’s maximum load.
- Request Service : Once a service is registers with the SMF, the service can be requested by users who want to use it. Servers should provide this service to the requested applications. This function allows an application to request service. After the application sends a service request to SManL, SManL will provide the necessary parameters for the application to contact the server that runs the requested service.
- Migrate Service: This function allows the services to migrate to the required servers. It also collects details about the global service ID, the global user_id, and the global device_id and will set up the migration using Docker container technology. Once the migration is successful, a successful result will be returned to the caller.
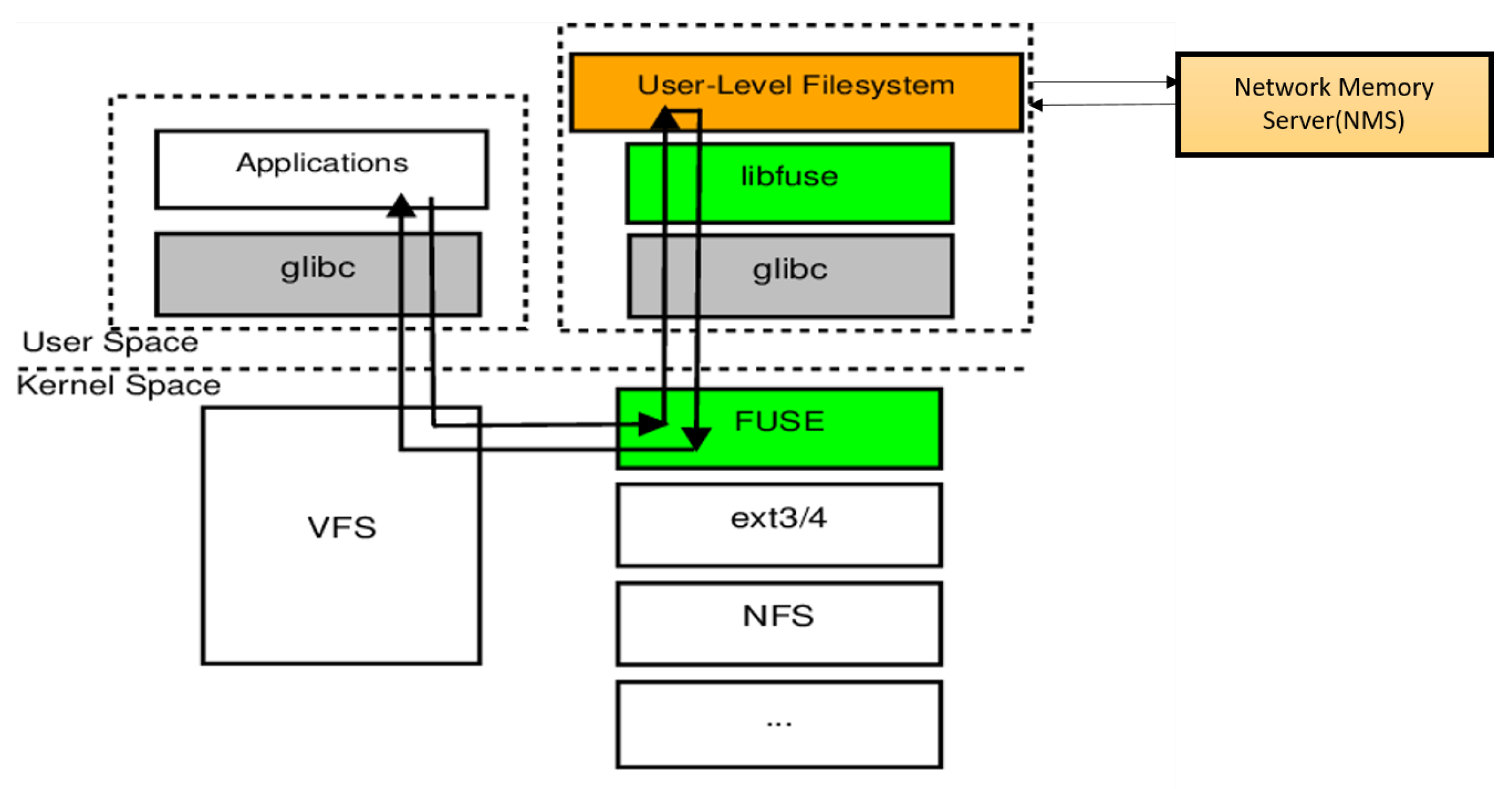
7.7. NMS Part of FUSE as a Service
7.8. SMF - NMS as a Service
8. Conclusions and Future work
Author Contributions
References
- Gayathri, K; Glenford, M; Jon, C, Building an Intelligent Edge Environment to Provide Essential Services for Smart Cities. Proceedings of MobiArch ’23, Spain,02 October 2023; Pages 13 - 18. [CrossRef]
- Xiaolong X; Bowen S; Xiaochun Y; Mohammad R, Khosravi H, "Edge Server Quantification and Placement for Offloading Social Media Services in Industrial Cognitive IoV," in IEEE Transactions on Industrial Informatics, vol. 17, no. 4, pp. 2910-2918, April 2021. [CrossRef]
- Ding. Z et al., "A Lightweight and Secure Communication Protocol for the IoT Environment," in IEEE Transactions on Dependable and Secure Computing, vol. 21, no. 3, pp. 1050-1067, May-June 2024. [CrossRef]
- Vishnu, V.P; Yonal, K; Glenford, M, Shah, M, P. and Nguyen,H. X., Exploiting Resource Contention in Highly Mobile Environments and Its Application to Vehicular Ad-Hoc Networks, in IEEE Transactions on Vehicular Technology, vol. 68, no. 4, pp. 3805-3819, April 2019. [CrossRef]
- Vishnu,V.P; Yonal, K; Glenford, M; Exploring analytical models to maintain quality-of-service for resource management using a proactive approach in highly mobile environments, 2018 7th International Conference on Computers Communications and Control (ICCCC), Oradea, Romania, 2018, pp. [CrossRef]
- Nattaruedee. V; Gayathri, K;; Glenford, M; Carolise. G; "Exploring a New Security Framework for Future Healthcare Systems," 2021 IEEE Globecom Workshops (GC Wkshps), Madrid, Spain, 2021, pp. 1-6. [CrossRef]
- Onyekachukwu A.E; Gayathri. K; G. Mapp; R. Trestian; Exploring the Provision of Reliable Network Storage in Highly Mobile Environments, 2020 13th International Conference on Communications (COMM), Bucharest, Romania, 2020, pp. 255-260. [CrossRef]
- Chen, S; and Zhou, M.; 2021. Evolving container to unikernel for edge computing and applications in process industry. Processes, 9(2), p.351.
- Kifayat. U;, Luz M.S; Joao. B. R; and Edson D.M.: A lightweight beaconing-based commercial services advertisement protocol for vehicular ad hoc network. In International Conference on Ad-Hoc Networks and Wireless, pages 279–293. Springer, 2016.
- Ullah, R.; Arslan, T. PySpark-Based Optimization of Microwave Image Reconstruction Algorithm for Head Imaging Big Data on High-Performance Computing and Google Cloud Platform. Appl. Sci. 2020, 10, 3382. [Google Scholar] [CrossRef]
- Peipei Xiao, Yufeng Wang, Qun Jin, and Jianhua Ma. A privacy-preserving incentive scheme for advertisement dissemination in vehicular social networks. In 2016 IEEE Trustcom/BigDataSE/ISPA, pages 1741–1746, 2016. [CrossRef]
- Jennings, B. and Stadler, R., 2015. Resource management in clouds: Survey and research challenges. Journal of Network and Systems Management, 23, pp.567-619.
- Gayathri, K; Glenford, M; Kammueller and M. Aiash; Formalization and Analysis of a Resource Allocation Security Protocol for Secure Service Migration. EEE/ACM International Conference on Utility and Cloud Computing Companion (UCC Companion), Zurich, Switzerland, 2018, pp. [CrossRef]
- ProVerif: Cryptographic protocol verifier in the formal model. Available online: https://bblanche.gitlabpages.inria.fr/proverif/ (accessed on 18 July 2024).
- Bruno, Blanchet; et al. Modeling and verifying security protocols with the applied pi calculus and proverif. Foundations and Trends® in Privacy and Security, 1(1-2):1–135, 2016. Available online: chrome-extension://efaidnbmnnnibpcajpcglclefindmkaj/https://web.archive.org/web/20170924002552id_/https://hal.inria.fr/hal-01423760/document (accessed on 18-July-2024).
- Glenford, M; M. Aiash; Guardia.H.C; Jon.C, "Exploring Multi-homing Issues in Heterogeneous Environments," 2011 IEEE Workshops of International Conference on Advanced Information Networking and Applications, Biopolis, Singapore, 2011, pp. [CrossRef]
- Vithanwattana N; Karthick G; Mapp G; George C; Samuels A; Securing future healthcare environments in a post-COVID-19 world: moving from frameworks to prototypes. J Reliab Intell Environ. 2022;8(3):299-315. [CrossRef] [PubMed]
- Jose, R; Onyekachukwu, A.E; Gayathri, K; Ramona,T; and Glenford, M; "A New Service Management Framework for Vehicular Networks," 2020 23rd Conference on Innovation in Clouds, Internet and Networks and Workshops (ICIN), Paris, France, 2020, pp. 162-164. [CrossRef]
- Gayathri, K; Glenford, M; Kammueller and M. Aiash; Modeling and verifying a resource allocation algorithm for secure service migration for commercial cloud systems. Computational Intelligence, n/a(n/a), 2021. URL https://onlinelibrary.wiley. com/doi/abs/10.1111/coin.12421.8. [CrossRef]
- Docker: Containerize your applications. Available online: https://www.docker.com/ (accessed on 18-July-2024).





| Notations | Explanation |
|---|---|
| CMS | Cloud Management System |
| SMF | Service Management Framework |
| APPL | Applications |
| Chosen Server | The SMF chooses a server of that service |
| PK(SMF)/PK(APPL)/PK(SERV) | Public key of SMF/APPL/Server |
| SK(SMF)/SK(APPL)/SK(SERV)/ | Private key of SMF/APPL/Server |
| SESS KEY | Session key |
| NA and NB | Nonce of NA and NB |
| Register Service | CMS contacts to Register the Service |
| Service Details | Servers, keys and running services. |
| Service Registered | The SMF registers the Service |
| SERV ID | Service ID |
| SERV CAP | Service Capability |
| DEV CAP | The Capability for the Device |
| Request service | Request to an appropriate server |
| USER CAP | User of the Application |
| CAP SESS | User of the Application |
| Service Name | Name of the services |
| Service Version | Service Version |
| IP Client | IP address of Client |
| SERV TIME CAP | proxy capability |
| IP Server | IP address of Server |
| Port Server | TCP Port of Service |
| Usage request | SMF contacts the server |
| Usage request accepted | The Server accepts the request |
| Request service accepted | SMF returns all the details |
| Session Start Request | Time capability sends start request |
| Service request | The application requests service |
| Service request done | The application gets service |
| Request Details | Details of APPL request. |
| Result Details | Details of chose server result. |
| Session End Request | The application terminates the session |
| Session End Req accepted | Server terminates session |
| Security Properties | CMF | SMF | ERVER | APPL |
|---|---|---|---|---|
| Private Keys | True | True | True | True |
| Session Key | - | - | True | True |
| Nonces | - | - | True | - |
| Event Begin() | True | - | - | - |
| Event end() | True | - | - | - |
| inj-event begin() | - | - | True | - |
| inj-event-end() | - | - | True | - |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




