Submitted:
19 February 2024
Posted:
20 February 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
- The token mechanism implemented ensures minimal privacy disclosure, wherein only the vehicle and TA possess the true identity of the vehicle.
- By enabling the RSU to centrally manage pseudonyms, it significantly alleviates the burden on TA and effectively safeguards against pseudonym abuse through a well-maintained revocation list, and make revocation easier.
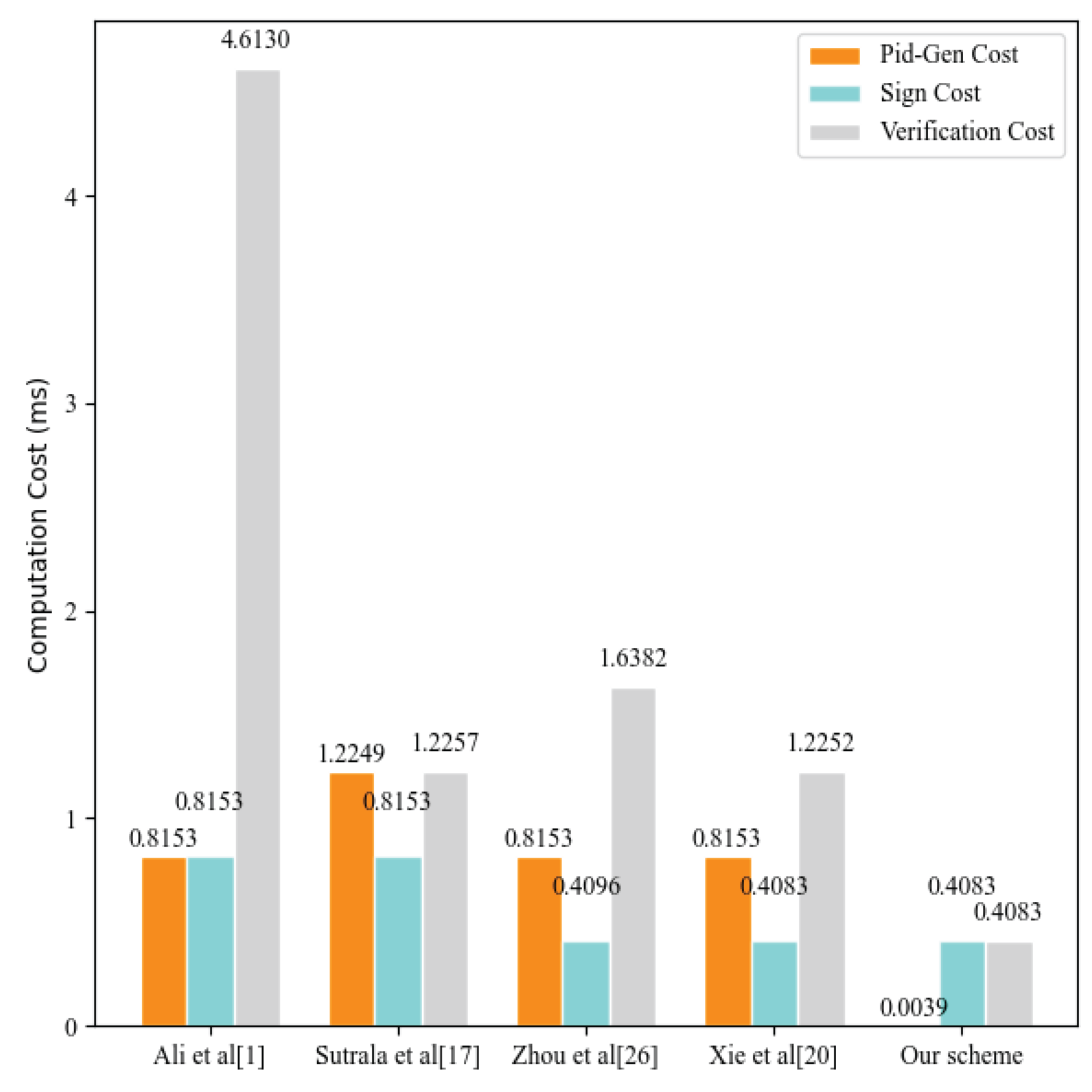
- The performance analysis demonstrates that our scheme can achieve a reduced overhead, with the generation of a pseudonym for a vehicle requiring only 0.0039ms.
2. Related Works
3. Preliminaries
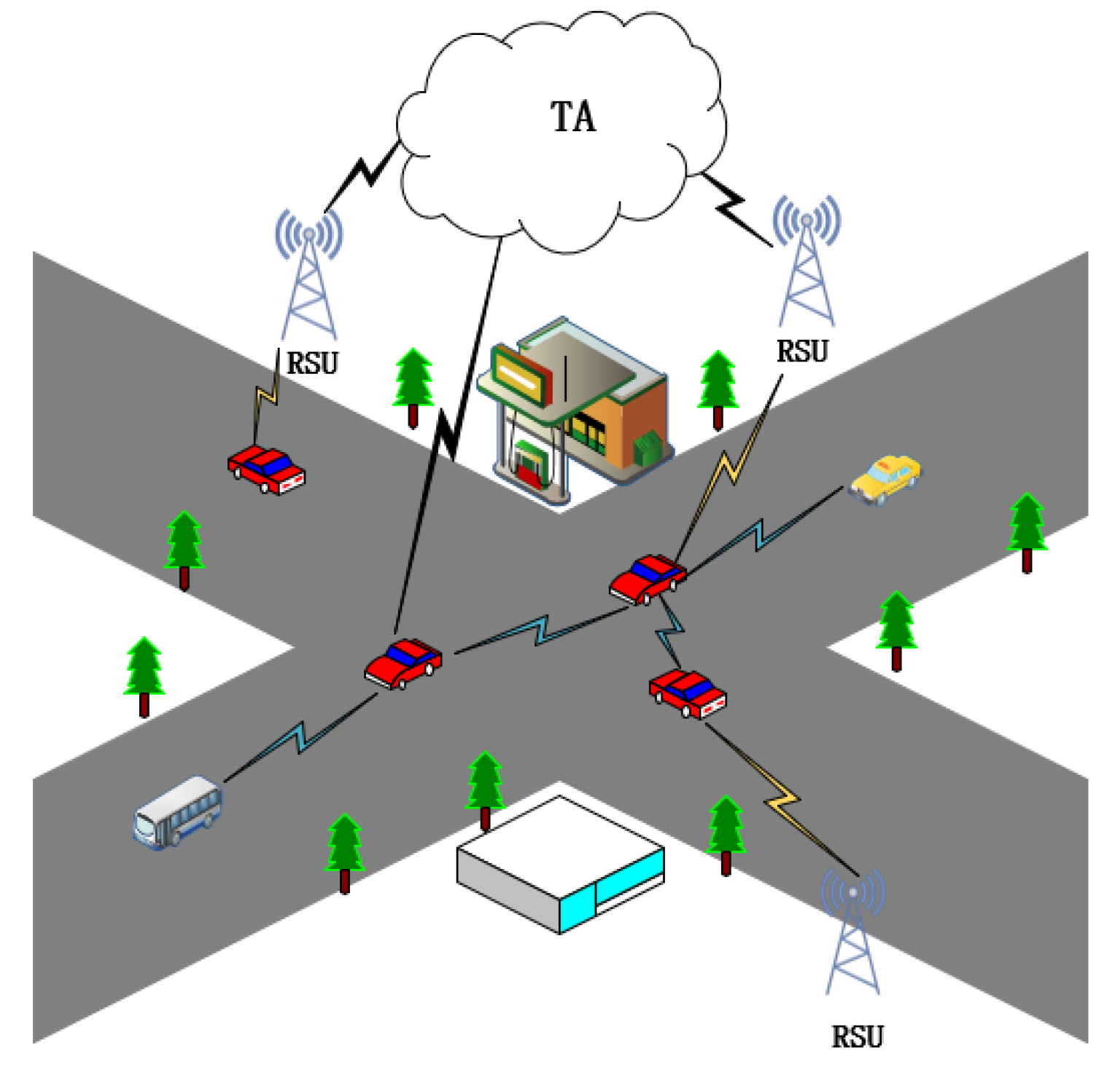
3.1. System Model
- TA: As a Authority which is trusted and cannot be compromised, TA possesses strong computing and storage resources and is responsible for the initialization operations of the entire system, as well as the registration of V and RSU within the system. Besides, TA also can track malicious vehicles.
- RSU: RSU serves as the roadside infrastructure and is also a trusted entity. It provides services to the communicating vehicles and acts as an intermediary between TA and V. RSU is responsible for managing the pseudonyms of vehicles.
- V: Vehicles are the communication entities in the system and are equipped with TPD and OBU. The OBU is responsible for generating key pair, while the TPD can store the key pair and other sensitive datas.
3.2. Security Requirements
- Anonymity: The true identity of a vehicle must be transmitted in an anonymous manner, preventing a malicious adversary from analyzing the original sender’s identity.
- Traceability: If deception occurs, the true identity of the malicious vehicle can be traced.
- Message authentication and integrity: The recipient can verify the legitimacy of the sender’s identity and the validity of the message.
- Revocability: If a vehicle engages in malicious behavior, both RSU and TA can collaborate to revoke the credentials or privileges of that vehicle.
- Unlinkability: Vehicles periodically change their pseudonyms to prevent malicious third parties or vehicles from determining whether the messages originate from the same vehicle.
- Resist other attacks: The Scheme could resist typical attacks such as replay attacks, Sybil attacks, man-in-the-middle attacks, key escrow, etc.
3.3. Elliptic Curve Cryptography
4. The Proposed Scheme
4.1. System Initialization Stage
- Initially, the TA chooses an elliptic curve E, defined as over a finite field of prime order p,where p is a large prime number, and .Subsequently, the TA chooses an additive group that has an order of q. And P serves as the generator for .
- Then the TA selects randomly a number ,which serves as the master key of the system, and then computes ,which serves as the public key of the system.
- Afterward, Four general one-way hash functions are selected by TA, which include , , , .
- Lastly, TA disseminates the public parameters to all vehicles and RSUs, then, TA keeps s for itself.
4.2. Registration Stage
-
The registration of VehicleDuring the vehicle registration stage, all vehicles register offline. The registration process is as follows:
- (a)
- V generates its own private key , then computes the public key .
- (b)
- V provides its real identity and public key to TA.
- (c)
- TA first checks the registration list to determine if V has already registered. If V is already registered, TA rejects the registration. If V is not registered, then TA chooses a number randomly, and TA generates for V and adds it to the list, setting the status of V as .
- (d)
- Each row in the form is formatted as follows:.
- (e)
- The process of TA generating for V is as follows:
- (f)
- Finally, TA gets and sends it to the V.
-
The registration of RSUIn this stage, the RSU obtains two seeds for generating pseudonyms, along with the corresponding token. The entire process is as follows:
- (a)
- RSU generates its own private key , then computes which serves as its public key.
- (b)
- RSU provides its real identity and public key to TA.
- (c)
- TA randomly picks a number ,then TA generates for RSU, the process is as follows:
- (d)
- Lastly, TA generates for the RSU and selects two random seed values , which are used for pseudonym derivation. TA then sends these values to the RSU.
- (e)
- TA sends to the RSU via a protected channel.
4.3. Pseudonym Generation Stage
- V sends a service request = to the RSU where .
-
After receiving the request, The RSU will proceed with the verification.
- Firstly, The RSU checks the valid of T.If it is valid, the process continues; Otherwise, the RSU rejects the request.
- Secondly, The RSU checks if is in the revocation list (RL). If it is not in the RL, the process continues, otherwise the RSU rejects the request.
- Finally, the RSU verifies the .It computes the value of , gets the x-coordinate value of the value and checks if it equals .
- If the verification not success, then the RSU refuses to provide services to the vehicle, otherwise, the RSU uses to generate pseudonyms, taking as an example.where w represents the number of time periods in a day, is a number selected by RSU randomly in the j-th time interval,.
- After generating the pseudonym, the RSU updates the information in the revocation list. For example, it adds a new row of information , where means the pseudonym of the is avaiable. The RSU then selects a random number ,and generates a signature for . It responds to with , where .
- The process of generating is as follows:
-
Upon receiving the , performs necessary operations to verify the RSU’s identity and the information’s legitimacy. The specific steps are as follows:
- Firstly, checks whether is fresh. If that is the case, the process continues, or else the rejects the request.
- Then verifies the legitimacy of the RSU. It computes the value of and gets the x-coordinate value of that value and checks if it is equal to A.
- Lastly, verifies the information by computing the value of , gets the x-coordinate value of that value, and checks if it is equal to C.
- If all the above equations hold true, then accepts the information and uses the pseudonym for subsequent communication.
4.4. Message Signature Stage
- For communication, selects firstly a number randomly.
- Then, the calculates the following formulas:
- Lastly, the sends to .
4.5. Message Verification Stage
- Firtly, validates the validity of . If it is valid, the process continues, otherwise, rejects.
- Then accesses the revocation list and checks the legitimacy of . If it is marked as , the process continue, but if it is marked as , rejects.
- Next computes and the value of ,and checks if the x-coordinate value of the value is equal to Y.
- If the equation holds true, it indicates the reliability of the message.Otherwise finds that m is fake message, it will report to the RSU, which will report it to the TA by sending . Then the TA will update the status of corresponding to as . At the same time, the RSU will update the status of corresponding to in the revocation list as .The RSU will no longer distribute pseudonyms to and remove it from the system.
5. Security Analysis
- Anonymity: The anonymous identity serves to conceal the true identity, where is a number selected randomly by RSU in the j-th time interval.Therefore, an Adv can never extract the real identity of the vehicle.In addition to that, when an RSU wants to check the validity of the generated pseudonym, it bases on . It does not require knowing the real identity of the vehicle, which satisfies conditional privacy preservation.
- Traceability: The message that sent by the vehicle includes the . When the RSU sends of a malicious vehicle to the TA, the TA can get the true identity of the vehicle by check the registration list.
-
Message authentication and integrity: Upon receiving the message, the receiver will compute and then verify the authenticity by checking if the result of the equation is equal to Y. If the equation holds true, it indicates a successful authentication.
- Revocation: If a vehicle engages in malicious behavior, both the RSU and TA will revoke the vehicle by following these steps: When the detects that m is false information, they report it to the RSU, which in turn reports it to the TA by sending the . The TA updates the status of corresponding to as . Simultaneously, the RSU updates the status of corresponding to in the revocation list as . The RSU will cease distributing pseudonyms to and remove it from the system.
- Confidentiality: In the RSU registration phase, the TA sends to the RSU a pair to generate pseudonyms. and are sent via a secure channel and are known only by the TA, RSU. In the pseudonym generation stage, and are used for the generation of pseudonyms and they will never be sent. An Adv who tries to analyze a pseudonym to extract and will never succeed due to the one-way hash function used and the random number.
- Key escrow resilience:the vehicle is the only entity who knows its private key. No one else is capable of imitating the vehicle.
- Unlinkability: The pseudonyms are updated frequently by the RSU. But the pair remains unmodifiable and is only known by the TA and RSU. An malicious adversary cannot distinguish whether two messages sent at time j and are sent by the same vehicle or not.
- Mutual authentication:In the pseudonym generation stage, when the vehicle initially requests service from the RSU, the RSU will authenticate the vehicle’s legal identity based on its . Upon successful authentication, the RSU transmits a pseudonym , and signature to the vehicle, which then verifies the validity of the information and the legitimacy of the RSU’s identity based on the and signature. During inter-vehicle communication, the receiver will check the revocation list according to the pk and pseudonym of the sender to determine whether the other party is legitimate and the message is authentic by calculating .
- Replay attacks: There is a system timestamp T in each message. The recipient can prevent replay attacks by verifying the validity of T.
- Sybil attack: The RSU not only imposes time and quantity limits on pseudonyms but also enforces strict restrictions. Specifically, the RSU only allocates a single new pseudonym to each vehicle within a given time period. It updates and stores the current list of valid pseudonyms. Any requests with invalid pseudonyms are directly rejected.
- Man-in-the-middle attack: Even if a malicious third party intercepts the message, they do not possess the sender’s private key. Therefore, they can’t forge the signature. The receiver can verify the authenticity of the message using sender’s public key.
6. Performance Evaluation
6.1. Computational Cost
6.2. Communication Cost
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- A. Yang, J. Weng, N. Cheng, J. Ni, X. Lin, and X. Shen, “Deqos attack: Degrading quality of service in vanets and its mitigation,” IEEE Transactions on Vehicular Technology, vol. 68, no. 5, pp. 4834–4845, 2019. [CrossRef]
- J. Petit, F. Schaub, M. Feiri, and F. Kargl, “Pseudonym schemes in vehicular networks: A survey,” IEEE communications surveys & tutorials, vol. 17, no. 1, pp. 228–255, 2014. [CrossRef]
- H. Zhong, L. Chen, J. Cui, J. Zhang, I. Bolodurina, and L. Liu, “Secure and lightweight conditional privacy-preserving authentication for fog-based vehicular ad hoc networks,” IEEE Internet of Things Journal, vol. 9, no. 11, pp. 8485–8497, 2021. [CrossRef]
- I. Ali, Y. Chen, M. Faisal, M. Li, I. Ali, Y. Chen, M. Faisal, and M. Li, “Certificateless signature-based authentication scheme for vehicle-to-infrastructure communications using bilinear pairing,” Efficient and Provably Secure Schemes for Vehicular Ad-Hoc Networks, pp. 91–119, 2022. [CrossRef]
- A. K. Sutrala, P. Bagga, A. K. Das, N. Kumar, J. J. Rodrigues, and P. Lorenz, “On the design of conditional privacy preserving batch verification-based authentication scheme for internet of vehicles deployment,” IEEE Transactions on Vehicular Technology, vol. 69, no. 5, pp. 5535–5548, 2020. [CrossRef]
- X. Zhou, M. Luo, P. Vijayakumar, C. Peng, and D. He, “Efficient certificateless conditional privacy-preserving authentication for vanets,” IEEE Transactions on Vehicular Technology, vol. 71, no. 7, pp. 7863–7875, 2022. [CrossRef]
- I. Ali, Y. Chen, M. Faisal, M. Li, I. Ali, Y. Chen, M. Faisal, and M. Li, “An ecc-based conditional privacy-preserving authentication scheme for vehicle-to-vehicle communications,” Efficient and Provably Secure Schemes for Vehicular Ad-Hoc Networks, pp. 121–146, 2022. [CrossRef]
- P.-S. Xie, X.-J. Pan, H. Wang, J.-L. Wang, T. Feng, and Y. Yan, “Conditional privacy-preserving authentication scheme for iov based on ecc,” Int. J. Netw. Secur, vol. 24, pp. 501–510, 2022. [CrossRef]
- H. Artail and N. Abbani, “A pseudonym management system to achieve anonymity in vehicular ad hoc networks,” IEEE Transactions on Dependable and Secure Computing, vol. 13, no. 1, pp. 106–119, 2015. [CrossRef]
- S. Mathews and B. Jinila, “An effective strategy for pseudonym generation & changing scheme with privacy preservation for vanet,” in 2014 International Conference on Electronics and Communication Systems (ICECS). IEEE, 2014, pp. 1–6. [CrossRef]
- Y. Xu, F. Li, and B. Cao, “Privacy-preserving authentication based on pseudonyms and secret sharing for vanet,” in 2019 Computing, Communications and IoT Applications (ComComAp). IEEE, 2019, pp. 157–162. [CrossRef]
- J. Qi, T. Gao, X. Deng, and C. Zhao, “A pseudonym-based certificateless privacy-preserving authentication scheme for vanets,” Vehicular Communications, vol. 38, p. 100535, 2022. [CrossRef]
- A. Sudarsono and M. Yuliana, “An anonymous authentication with received signal strength based pseudonymous identities generation for vanets,” IEEE Access, vol. 11, pp. 15 637–15 654, 2023. [CrossRef]
- J. Qi and T. Gao, “A privacy-preserving authentication and pseudonym revocation scheme for vanets,” IEEE Access, vol. 8, pp. 177 693–177 707, 2020. [CrossRef]
- H. Artail and N. Abbani, “A pseudonym management system to achieve anonymity in vehicular ad hoc networks,” IEEE Transactions on Dependable and Secure Computing, vol. 13, no. 1, pp. 106–119, 2015. [CrossRef]
- S. Mathews and B. Jinila, “An effective strategy for pseudonym generation & changing scheme with privacy preservation for vanet,” in 2014 International Conference on Electronics and Communication Systems (ICECS). IEEE, 2014, pp. 1–6. [CrossRef]
- J. Qi and T. Gao, “An anonymous authentication scheme based on self-generated pseudonym for vanets,” in International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing. Springer, 2022, pp. 75–84. [CrossRef]
- M. Raya and J.-P. Hubaux, “Securing vehicular ad hoc networks,” Journal of computer security, vol. 15, no. 1, pp. 39–68, 2007. [CrossRef]
- C. Lin, D. He, X. Huang, N. Kumar, and K.-K. R. Choo, “Bcppa: A blockchain-based conditional privacy-preserving authentication protocol for vehicular ad hoc networks,” IEEE Transactions on Intelligent Transportation Systems, vol. 22, no. 12, pp. 7408–7420, 2020. [CrossRef]
- H. Zhang and F. Zhao, “Cross-domain identity authentication scheme based on blockchain and pki system,” High-Confidence Computing, vol. 3, no. 1, p. 100096, 2023. [CrossRef]
- A. Shamir, “Identity-based cryptosystems and signature schemes,” in Advances in Cryptology: Proceedings of CRYPTO 84 4. Springer, 1985, pp. 47–53. [CrossRef]
- S. Wang and N. Yao, “Liap: A local identity-based anonymous message authentication protocol in vanets,” Computer Communications, vol. 112, pp. 154–164, 2017. [CrossRef]
- X. Wang, Q. Chen, Z. Peng, and Y. Wang, “An efficient and secure identity-based conditional privacy-preserving authentication scheme in vanets,” International Journal of Network Security, vol. 24, no. 4, pp. 661–670, 2022. [CrossRef]
- H. J. Nath and H. Choudhury, “A privacy-preserving mutual authentication scheme for group communication in vanet,” Computer Communications, vol. 192, pp. 357–372, 2022. [CrossRef]
- R. Guo, L. Xu, X. Li, Y. Zhang, and X. Li, “An efficient certificateless ring signcryption scheme with conditional privacy-preserving in vanets,” Journal of Systems Architecture, vol. 129, p. 102633, 2022. [CrossRef]
- A. Yang, J. Weng, K. Yang, C. Huang, and X. Shen, “Delegating authentication to edge: A decentralized authentication architecture for vehicular networks,” IEEE Transactions on Intelligent Transportation Systems, vol. 23, no. 2, pp. 1284–1298, 2020. [CrossRef]
| Scheme | S1 | S2 | S3 | S4 | S5 | S6 | S7 | S8 | S9 | S10 |
|---|---|---|---|---|---|---|---|---|---|---|
| [5] | ✔ | ✔ | ✔ | ✔ | ✗ | ✔ | ✔ | ✔ | ✔ | ✔ |
| [8] | ✔ | ✔ | ✔ | ✔ | ✗ | ✔ | ✔ | ✔ | ✗ | ✔ |
| [6] | ✔ | ✔ | ✗ | ✔ | ✗ | ✔ | ✗ | ✔ | ✗ | ✔ |
| [4] | ✔ | ✔ | ✗ | ✔ | ✗ | ✔ | ✔ | ✗ | ✗ | ✔ |
| Our scheme | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| Notation | Description |
|---|---|
| The i-th vehicle | |
| Road Side Unit | |
| On Board Unit | |
| A reliable governmental entity | |
| Two different large prime numbers | |
| Cyclic additive group | |
| Bilinear mapping | |
| P | A generator of the group |
| E | An elliptic curve |
| s | The system’s private key |
| The system’s public key | |
| The vehicle’s true identity | |
| The vehicle’s fake identity | |
| Four one-way hash functions | |
| Current timestamp | |
| A traffic-related message | |
| Take the X-axis coordinate value | |
| the vehicle’s Valid token | |
| the RSU’s Valid token | |
| The i-th vehicle’s public key | |
| The i-th vehicle’s private key | |
| The i-th RSU’s public key | |
| The i-th RSU’s private key | |
| ⊕ | XOR operation |
| ∥ | Concatenation operation |
| Message signing |
| Notation | Description | Time(ms) |
|---|---|---|
| The time required for executing bilinear pairing operation. | 4.2039 | |
| The time required for executing one-way hash function. | 0.0013 | |
| The time required for executing point multiplication operation in bilinear pairing. | 1.537 | |
| The time required for executing point addition operation in bilinear pairing. | 0.0069 | |
| The time required for executing point multiplication operation in ECC. | 0.407 | |
| The time required for executing point addition operation in ECC. | 0.0021 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




