1. Introduction
Customer Relationship Management (CRM) systems have undergone a fundamental transformation over the past two decades. What began as on-premise contact management databases have evolved into cloud-native, multi-tenant platforms that orchestrate sales, service, marketing, commerce, and increasingly, autonomous AI agent operations across the enterprise [
1,
2]. Gartner's Magic Quadrant for Sales Force Automation reports that Salesforce has maintained its position as a Leader for 18 consecutive years, reflecting the platform's architectural maturity and market dominance [
3]. Forrester's 2025 CRM Wave describes the market as "on the cusp of change," driven by the convergence of predictive, generative, and agentic AI capabilities within CRM platforms [
4].
Despite this evolution, the software engineering literature has not kept pace with the unique architectural challenges that enterprise CRM platforms present. Classical design pattern literature — from the foundational Gang of Four catalogue [
5] through Fowler's enterprise application patterns [
6] to Hohpe and Woolf's integration patterns [
7] — was authored in the context of single-tenant, self-hosted application environments where developers had full control over infrastructure, database schemas, and execution runtimes. Multi-tenant SaaS CRM platforms fundamentally alter these assumptions.
In a multi-tenant CRM environment, applications execute within a shared infrastructure governed by platform-enforced resource limits (commonly termed "governor limits"), a metadata-driven schema architecture, and a platform-controlled order of execution [
8,
9]. These constraints are not bugs to be worked around; they are deliberate architectural guardrails that ensure fair resource distribution across tenants sharing the same compute and storage infrastructure [
10]. The challenge for enterprise architects is that classical design patterns, when applied naively to these environments, can produce anti-patterns — solutions that appear sound in isolation but fail under the unique constraints of multi-tenant execution.
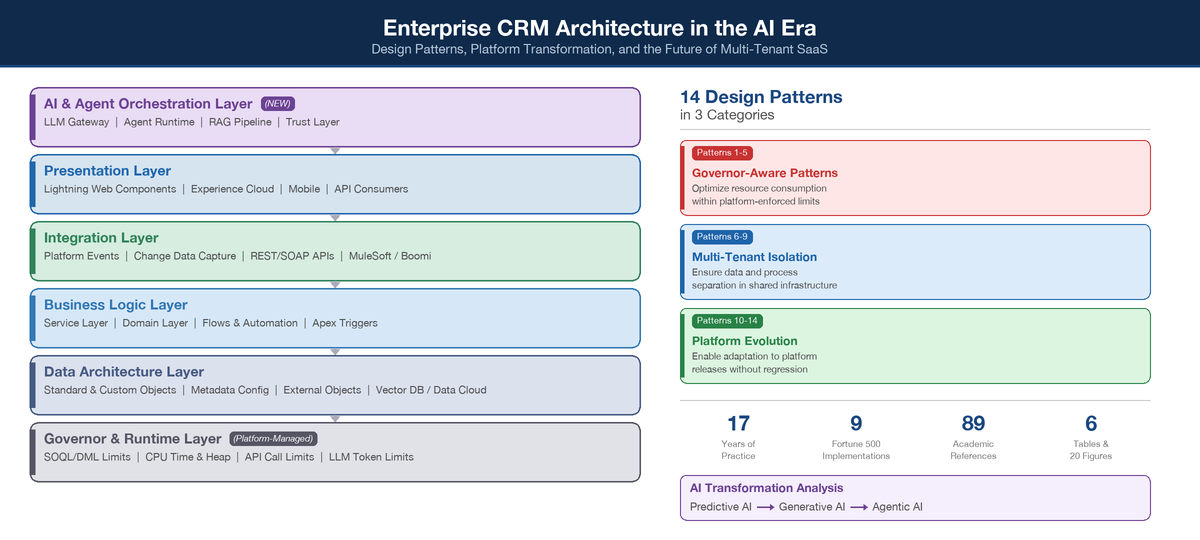
This paper addresses this gap by presenting a reference framework of 14 architecture and design patterns specifically adapted for enterprise CRM platforms operating under multi-tenant constraints. The patterns are derived from the author's 17 years of practitioner experience across Fortune 500 CRM implementations at organizations spanning telecommunications, consumer goods, automotive, data analytics, financial services, healthcare, and energy sectors, complemented by the author's published work on Apex design patterns [
11] and enterprise integration patterns [
12].
The contributions of this paper are threefold:
A four-layer CRM architecture reference model that maps classical enterprise architecture layers to multi-tenant CRM platform capabilities.
A catalogue of 14 patterns organized into Governor-Aware, Multi-Tenant Isolation, and Platform Evolution categories, each documented with context, forces, solution, and consequences.
An empirical evaluation of pattern applicability based on quality attribute trade-offs observed in production enterprise deployments.
The remainder of this paper is organized as follows:
5. Design Pattern Catalogue
We organize 14 patterns into three categories based on the primary constraint they address. Each pattern is documented following an abbreviated pattern template: Context, Problem, Forces, Solution, Consequences, and Known Uses.
5.1. Governor-Aware Patterns
Governor-Aware Patterns optimize resource consumption within platform-enforced execution limits. These patterns have no direct equivalent in classical design pattern literature because they respond to constraints that do not exist in single-tenant environments.
Pattern 1: Bulkification
Context: Business logic must process records that arrive in variable batch sizes — from a single record via UI interaction to 200 records via API bulk operations or data loads.
Problem: Code written to handle a single record at a time will exceed governor limits when processing batches, causing runtime failures in production.
Forces:
Platform governor limits are per-transaction, not per-record
API and bulk operations deliver up to 200 records per trigger invocation
Developers naturally reason about single-record logic
Solution: Design all data access and manipulation logic to operate on collections (lists, sets, maps) rather than individual records. Move all SOQL queries and DML operations outside of loops. Use map-based lookups to replace repeated queries.
Figure 3.
Bulkification pattern: replacing per-record operations with collection-based processing.
Figure 3.
Bulkification pattern: replacing per-record operations with collection-based processing.
Consequences:
(+) Eliminates governor limit exceptions under bulk data operations
(+) Consistent performance regardless of batch size (1 to 200 records)
(-) Increases code complexity; developers must think in terms of collections
(-) Requires more upfront design compared to iterative single-record logic
Known Uses: Every production Salesforce implementation observed by the author employs this pattern. At a Tier-1 US telecommunications provider (Telco-A), where the org contained 400 million records on day one, bulkification was a mandatory code review criterion. At another major wireless carrier (Telco-B), refactoring Flows to use bulk processing patterns increased daily throughput from 500,000 to 4 million records (an 8x improvement).
Pattern 2: Queueable Chain
Context: A business process requires more computation than a single synchronous transaction allows (10,000ms CPU time, 100 SOQL queries) but must complete as a coordinated sequence.
Problem: Long-running processes that exceed single-transaction governor limits fail mid-execution, leaving data in an inconsistent state.
Forces:
Synchronous transactions have strict CPU and query limits
Asynchronous contexts (Queueable, Batch) have higher limits but cannot be directly chained in unlimited depth
Business processes require sequential ordering of steps
Error handling must allow resumption from the point of failure
Solution: Decompose the process into discrete units of work, each implemented as a Queueable Apex class. Each unit, upon successful completion, enqueues the next unit in the chain. State is passed between units via serialized parameters or a custom orchestration object.
Figure 4.
Queueable Chain pattern with orchestration tracking.
Figure 4.
Queueable Chain pattern with orchestration tracking.
Consequences:
(+) Enables processes that exceed single-transaction limits
(+) Provides natural checkpointing for error recovery
(+) Each step runs in its own governor context with fresh limits
(-) Introduces asynchronous complexity; harder to debug than synchronous code
(-) Platform limits on chain depth (currently 1 Queueable per Queueable in some contexts)
(-) Requires orchestration infrastructure for monitoring and retry
Known Uses: At a Fortune 500 consumer goods manufacturer (CPG-A), a Hyper Batch framework was designed using this pattern to process complex scheduling computations for 25,000 frontline employees. At a global data and analytics provider (DataCo-A), CPQ pricing calculations that exceeded synchronous limits were decomposed into chained Queueable steps.
Pattern 3: Selective SOQL
Context: Business logic requires querying related data, but query complexity and result set size vary dramatically based on runtime conditions.
Problem: Queries that retrieve all fields and all related records consume SOQL query rows (50,000 limit) and heap memory, even when only a subset is needed.
Solution: Build queries dynamically based on actual data requirements using the Selector Layer pattern [
17] to centralize query construction with field-level, relationship-level, and row-level filtering based on calling context.
Consequences: (+) Minimizes governor consumption and heap usage per transaction. (-) Dynamic query construction requires security discipline to prevent SOQL injection.
Known Uses: The fflib Selector Layer [
17] operationalizes this pattern. At Auto-A, consolidating 14 business units required Selective SOQL to manage dramatically different data volumes across business unit record types.
Pattern 4: Lazy Initialization
Context: An object or data set is expensive to construct but may not be needed in every code path within a transaction.
Problem: Eagerly loading all potentially needed data wastes governor resources when execution paths do not require it.
Solution: Defer data loading until first access using private properties with null-check accessors that initialize on first invocation and cache results within the transaction.
Consequences: (+) Reduces unnecessary governor consumption; particularly effective in trigger handlers managing multiple event types. (-) Can make execution order less predictable; cached values are not persisted across transactions.
Known Uses: Standard practice in enterprise Apex codebases. At Pharma-A, Lazy Initialization reduced average SOQL consumption by deferring queries to only the integration paths activated by each transaction across 13+ integration touchpoints.
Pattern 5: Governor Limit Monitor
Context: Complex business logic approaches governor limits during execution, and the consequences of exceeding limits (transaction abort) are unacceptable for business-critical processes.
Problem: Without runtime awareness of governor consumption, code cannot adapt its behavior when approaching limits, resulting in hard failures.
Forces:
Platform provides runtime introspection of governor consumption (Limits class)
Some processes can degrade gracefully (defer remaining work) rather than abort entirely
Monitoring overhead must be minimal to avoid consuming the resources being monitored
Solution: Instrument business logic with checkpoints that query remaining governor limits (using the platform's Limits class). When consumption approaches thresholds (e.g., 80% of SOQL queries consumed), switch to a degraded mode: reduce query scope, defer non-critical operations to asynchronous processing, or log a warning and enqueue remaining work via the Queueable Chain pattern.
Figure 5.
Governor Limit Monitor pattern with graceful degradation.
Figure 5.
Governor Limit Monitor pattern with graceful degradation.
Consequences:
(+) Prevents hard transaction failures in complex, variable-load scenarios
(+) Enables graceful degradation rather than all-or-nothing execution
(-) Adds monitoring overhead to every checkpoint
(-) Requires defining "degraded mode" behavior for each process, increasing design complexity
Known Uses: At a major US wireless carrier (Telco-B), the integration pipeline processing 4 million records daily uses governor monitoring to dynamically adjust batch sizes. At a Fortune 500 consumer goods manufacturer (CPG-A), the Hyper Batch framework employed this pattern to ensure scheduling calculations completed even under variable data loads.
5.2. Multi-Tenant Isolation Patterns
Multi-Tenant Isolation Patterns ensure data and process separation in shared infrastructure environments. These patterns address the unique security, compliance, and operational challenges of multi-tenant architecture.
Pattern 6: Tenant-Scoped Configuration
Context: An application must behave differently across business units, regions, or customer segments within a single multi-tenant CRM organization.
Problem: Hard-coding configuration values creates deployment and maintenance overhead. Environment-specific configurations cannot be managed through code deployments in production environments.
Forces:
CRM platforms prohibit direct database manipulation in production
Configuration must be changeable by administrators without developer involvement
Different business units within the same org may require different thresholds, routing rules, or feature toggles
The Twelve-Factor App methodology [
28] prescribes strict separation of config from code
Solution: Use the platform's metadata-driven configuration mechanisms — Custom Metadata Types, Custom Settings, or Custom Labels — to externalize all environment-specific and tenant-specific configuration. Organize configurations hierarchically (org-wide defaults overridden by profile or user-level settings).
Figure 6.
Tenant-Scoped Configuration pattern with hierarchical overrides.
Figure 6.
Tenant-Scoped Configuration pattern with hierarchical overrides.
Consequences:
(+) Eliminates hard-coded values; enables admin-driven configuration changes
(+) Custom Metadata Types are deployable through CI/CD pipelines
(+) Supports multi-business-unit architectures within a single org
(-) Over-reliance on configuration can create a "configuration sprawl" anti-pattern
(-) Custom Settings cached in memory count against governor limits
Known Uses: At Auto-A, consolidating 14 business units required extensive Tenant-Scoped Configuration for unit-specific approval thresholds, routing rules, and feature toggles. At TechCo-A, configuration-driven workflows enabled different approval hierarchies per business function.
Pattern 7: Namespace Partitioning
Context: Multiple development teams or managed packages contribute code and metadata to the same CRM organization.
Problem: Without naming conventions, metadata conflicts arise between teams, packages, and org-level customizations, leading to deployment failures and runtime errors.
Solution: Establish hierarchical naming conventions prefixing all metadata with team or domain identifiers. Use unlocked packages (Salesforce DX) [
26] to create formal dependency boundaries between teams without the overhead of managed packages.
Consequences: (+) Prevents metadata collisions; enables independent development and deployment cycles; unlocked packages enforce dependency graphs. (-) Naming conventions require governance tooling; cross-package references create coupling.
Known Uses: At CPG-A, managing 50+ developers required strict namespace partitioning to prevent deployment conflicts.
Pattern 8: Security Boundary Enforcement
Context: Enterprise CRM implementations must enforce data visibility rules that align with organizational hierarchy, regulatory requirements, and partnership structures.
Problem: CRM platforms provide multiple overlapping security mechanisms (OWD, Role Hierarchy, Sharing Rules, Apex Sharing, Restriction Rules), and incorrect configuration creates data leakage or over-restriction.
Forces:
Regulatory requirements (HIPAA, GDPR, SOX) demand provable data isolation
Performance degrades with complex sharing calculations on large data volumes
Security models must accommodate both hierarchical (role-based) and lateral (team-based) access patterns
Point-in-time security requirements (financial services) conflict with platform-native sharing models
Solution: Design security from the data model outward. Start with the most restrictive Organization-Wide Defaults (Private), then layer role hierarchy, sharing rules, and programmatic sharing to open access precisely where needed. Use Restriction Rules for hard compliance boundaries that cannot be overridden. For point-in-time requirements, implement Apex-managed sharing with explicit share record management.
Figure 7.
Security Boundary Enforcement: layered access control from restrictive baseline.
Figure 7.
Security Boundary Enforcement: layered access control from restrictive baseline.
Consequences:
(+) Provable data isolation for regulatory compliance
(+) Layered approach simplifies auditing
(-) Complex sharing models degrade query performance at scale
(-) Apex Managed Sharing requires careful maintenance as organizational structure evolves
Known Uses: At FinServ-A, Financial Service Cloud required point-in-time security where relationship managers could only see client data during their active advisory period, implemented through Apex-based temporal sharing. At Pharma-A, HIPAA compliance required Restriction Rules to prevent cross-division data access.
Pattern 9: Cross-Org Data Federation
Context: An enterprise operates multiple CRM organizations (due to mergers, acquisitions, or regulatory requirements) that need to share selected data without full consolidation.
Problem: Full org consolidation is prohibitively expensive and disruptive for organizations with established processes, integrations, and customizations.
Solution: Implement federation through Salesforce Connect (OData protocol) to expose external org data as External Objects, or use middleware-mediated synchronization for selected data sets. Maintain a Master Data Management (MDM) strategy designating data ownership per entity per org.
Consequences: (+) Avoids consolidation cost and disruption; respects data residency requirements; allows gradual convergence. (-) External Objects have query limitations; federated queries introduce latency; MDM governance overhead is significant.
Known Uses: At Telco-A, Salesforce Connect enabled real-time access to legacy system data without migration — the org had 400 million records on day one. At Auto-A, the architecture assessed federation vs. consolidation for 14 business units before determining consolidation was feasible.
5.3. Platform Evolution Patterns
Platform Evolution Patterns enable applications to adapt to platform releases, API version changes, and evolving capabilities without regression.
Pattern 10: Metadata-Driven Configuration
Context: Business rules and process behaviors change frequently but code deployments are governed by release management processes with lead times.
Problem: Embedding business rules in code requires developer involvement and deployment cycles for changes that are business-operational in nature.
Forces:
Business agility demands rapid rule changes (pricing rules, routing logic, SLA thresholds)
Code deployments require testing, staging, and change management
CRM platforms provide metadata mechanisms that administrators can modify in production
Not all business logic can be expressed declaratively
Solution: Decompose business logic into a stable code framework that reads its behavioral parameters from platform metadata (Custom Metadata Types, Flow definitions, or custom configuration objects). The code framework remains static across releases; behavior changes are effected through metadata changes managed by business administrators.
Figure 8.
Metadata-Driven Configuration: separating stable code from dynamic business rules.
Figure 8.
Metadata-Driven Configuration: separating stable code from dynamic business rules.
Consequences:
(+) Business rule changes do not require code deployments
(+) Reduces developer bottleneck for operational configuration changes
(+) Custom Metadata Types are versionable and deployable through CI/CD when needed
(-) Requires upfront investment in building the metadata-reading framework
(-) Complex rule interactions may exceed what metadata can express, requiring code changes
Known Uses: At TechCo-A, approval hierarchies and routing rules were metadata-driven, enabling business teams to modify procurement workflows without developers. At CPG-A, scheduling rules for 25,000 field workers were externalized to metadata for regional manager adjustment.
Pattern 11: Feature Toggle
Context: New features must be deployed to production but activated selectively — by user group, business unit, or rollout percentage.
Problem: Deploying features to all users simultaneously creates risk, and rolling back CRM deployments is complex and error-prone.
Solution: Implement feature toggles using Custom Permissions (user/profile-level) or Custom Metadata Types (org-level). Guard new feature code paths with toggle checks that can be activated or deactivated without code changes.
Consequences: (+) Enables phased rollouts and rapid feature deactivation. (-) Accumulated toggles create "toggle debt"; testing combinatorial states increases QA complexity.
Known Uses: At Auto-A, feature toggles governed the phased rollout of CPQ capabilities to 14 business units over 18 months.
Pattern 12: Backward-Compatible Polymorphism
Context: A CRM application must support multiple versions of an API, business process, or integration protocol simultaneously during migration periods.
Problem: Breaking changes disrupt downstream consumers, but indefinite backward compatibility creates unsustainable maintenance burden.
Solution: Define stable interfaces (Apex interfaces or abstract classes) that represent the contract. Implement version-specific behavior in concrete classes selected at runtime through a factory based on caller context or configuration. Deprecate old implementations on a published schedule.
Figure 9.
Backward-Compatible Polymorphism using interface-based version management.
Figure 9.
Backward-Compatible Polymorphism using interface-based version management.
Consequences:
(+) Enables non-disruptive API evolution
(+) Consumers migrate on their own timeline
(-) Maintaining multiple implementations increases codebase size
(-) Factory logic must be managed and tested for all active versions
Known Uses: At a global data and analytics provider (DataCo-A), migrating from a legacy CPQ platform to Salesforce CPQ required maintaining dual processing paths for 12+ months while downstream systems migrated.
Pattern 13: Event-Driven Decoupling
Context: Multiple systems (CRM, ERP, data warehouse, marketing automation) must stay synchronized without creating brittle point-to-point integrations.
Problem: Direct system-to-system integrations create tight coupling where changes to one system cascade failures to all connected systems.
Forces:
Enterprise landscapes comprise 10-50+ integrated systems
Each system has different availability SLAs and maintenance windows
Data consistency requirements vary (eventual vs. strong consistency)
Integration patterns have evolved from batch ETL to near-real-time event streams [
7,
22]
Solution: Use the CRM platform's event bus (Platform Events, Change Data Capture) as the integration backbone. Publishers emit domain events without knowledge of subscribers. Subscribers process events asynchronously, with the platform managing delivery guarantees and replay capabilities. Middleware (MuleSoft, Boomi) acts as an event mediator for systems that cannot directly consume platform events.
Figure 10.
Event-Driven Decoupling using Platform Events and Change Data Capture.
Figure 10.
Event-Driven Decoupling using Platform Events and Change Data Capture.
Consequences:
(+) Eliminates brittle point-to-point integrations
(+) Publishers and subscribers evolve independently
(+) Platform-managed event delivery with replay capability
(-) Eventual consistency requires business process adaptation
(-) Event schema evolution must be managed carefully [
23]
(-) Debugging asynchronous event chains is more complex than synchronous calls
Known Uses: At Telco-A, 22 integrations were delivered in 10 weeks using MuleSoft as event mediator. At Telco-B, event-driven middleware handles 4 million daily records with retry and dead letter queues. At Pharma-A, 13+ integrations were managed through event-mediated architecture using Informatica and Boomi.
Pattern 14: Layered Test Architecture
Context: Enterprise CRM applications require comprehensive testing but platform constraints (governor limits, shared environment, metadata dependencies) make testing fundamentally different from traditional application testing.
Problem: Test methods in multi-tenant CRM platforms share governor limits with the code under test, meaning test setup and assertions consume the same finite resources as the business logic being validated.
Forces:
Platform requires minimum 75% code coverage for production deployment
Test methods run in an isolated transaction (seeAllData=false by default)
Test data creation consumes DML and SOQL limits
Integration tests that call external systems are prohibited in test context
Complex org metadata (validation rules, flows, triggers) fire during test execution
Solution: Organize tests in three layers: (1) Unit Tests that validate individual methods using dependency injection and mock objects (HttpCalloutMock, StubProvider); (2) Integration Tests that validate cross-object business processes using test data factories; and (3) End-to-End Tests executed outside the platform (Selenium, Provar) for UI-level validation.
Figure 11.
Layered Test Architecture: test pyramid adapted for multi-tenant CRM platforms.
Figure 11.
Layered Test Architecture: test pyramid adapted for multi-tenant CRM platforms.
Consequences: (+) Maximizes test coverage while minimizing governor consumption; mock-based unit tests execute quickly without org data dependency. (-) Requires investment in test data factories and mock frameworks; end-to-end tests are fragile and expensive to maintain.
Known Uses: At DataCo-A, Copado was used as the CI/CD platform with layered test execution. At CPG-A, the CoE established test architecture standards for all 50+ developers. The author's Udemy course [
26] teaches CI/CD test pipeline architecture.
8. Will AI Agents Endanger Enterprise SaaS? The Build vs. Buy Calculus Revisited
A provocative question has emerged alongside the AI developments examined in
Section 7: if AI coding agents can dramatically accelerate software development, will enterprises bypass CRM platforms entirely and build custom applications tailored to their exact needs? This section examines the disruption thesis, evaluates the evidence, and assesses the structural advantages that make enterprise CRM platforms more resilient — but also more pressured to evolve — than the disruption narrative suggests.
8.1. The Disruption Thesis
The argument is straightforward: AI coding agents (GitHub Copilot, Cursor, Claude Code, Devin) are making software development faster and cheaper. If an enterprise can instruct an AI agent to "build me a CRM system that does exactly what I need," why pay
$300/user/month for a SaaS platform loaded with features the organization never uses? Bond Capital (Mary Meeker) argues that the SaaS point-solution era is ending, with AI enabling rapid custom application assembly [
64]. SaaS stock multiples have compressed from 7x to below 5x revenue, and seat-based pricing — the economic foundation of SaaS CRM — is declining rapidly, falling from 21% to 15% of enterprise contracts in a single year [
65]. Bessemer Venture Partners' State of the Cloud reports document a "tectonic shift" where AI is collapsing the traditional SaaS value chain [
66].
Gartner predicts that by 2026, 75% of new applications will be built using low-code or no-code technologies, up from less than 25% in 2020 [
38]. Combined with AI-powered code generation, this suggests that the barriers to building custom enterprise applications are falling faster than at any point in software history.
8.2. The Productivity Evidence: More Nuanced Than Headlines Suggest
Before evaluating the disruption thesis, it is essential to examine the actual evidence on AI-assisted development productivity, which is considerably more mixed than vendor marketing suggests.
Table 5.
AI developer productivity evidence: a divided landscape across controlled studies.
Table 5.
AI developer productivity evidence: a divided landscape across controlled studies.
| Optimistic Findings |
Cautionary Findings |
Code Quality Evidence |
| GitHub: 55% faster task completion (controlled lab) |
METR RCT: 19% SLOWER on complex real-world codebases (2025) |
Veracode: 45% vulnerability rate in AI-generated code |
| McKinsey: Up to 2x speed gains (org-level survey) |
Uplevel: No significant productivity gains, 41% more bugs (n=800) |
GitClear: Code churn UP 8x, refactoring DOWN from 25% to <10% |
| Microsoft Research: 26% faster (RCT, simple tasks) |
Google DORA 2025: Improves throughput, DECREASES stability |
CodeRabbit: 2.74x more XSS vulnerabilities |
Optimistic evidence: GitHub's research reports 55% faster task completion in controlled laboratory conditions [
67]. McKinsey documents up to 2x speed gains at organizations with 80-100% AI tool adoption [
68]. A Microsoft Research randomized controlled trial found 26% faster completion on simple programming tasks [
69].
Cautionary evidence: A 2025 METR randomized controlled trial — the most rigorous study to date — found that experienced open-source developers were actually
19% slower when using AI coding tools on complex real-world codebases, while simultaneously believing they were 20% faster, revealing a 40-percentage-point perception gap [
70]. An Uplevel study of 800 developers found
no significant productivity gains and a
41% increase in bugs [
71]. Google's 2025 DORA (DevOps Research and Assessment) report confirmed that AI tools improve developer throughput but
decrease delivery stability [
72].
The critical insight for the build-vs-buy calculus is this: AI coding tools demonstrably accelerate the creation of new code, but the evidence suggests they do not yet reduce — and may increase — the long-term maintenance burden. Building a CRM application is a 3-month project; maintaining it is a 10-year commitment.
8.3. Seven Structural Advantages of Enterprise CRM Platforms
The disruption thesis underestimates seven structural advantages that enterprise CRM platforms possess and that custom-built applications must replicate entirely from scratch:
Table 6.
The seven structural advantages of enterprise CRM platforms that custom applications must independently replicate.
Table 6.
The seven structural advantages of enterprise CRM platforms that custom applications must independently replicate.
| # |
Enterprise CRM Platform Advantage |
Custom Application Must Replicate |
| 1 |
Multi-Tenant Economics |
Build & operate own infrastructure |
| 2 |
Ecosystem Network Effects |
Build every integration from zero |
| 3 |
Regulatory Compliance |
Achieve SOC 2, HIPAA, GDPR independently |
| 4 |
Platform Evolution Velocity |
Ship 3 releases/year with own team |
| 5 |
Data Model Maturity |
Design data model from scratch |
| 6 |
Integration Pre-Built Connectors |
Build every connector from scratch |
| 7 |
Talent Ecosystem |
Hire, train, retain specialized talent |
1. Multi-Tenant Economics: Single-tenant custom deployments cost
2--5x more in infrastructure than multi-tenant platforms that amortize compute, storage, networking, and operations across thousands of tenants [
10,
16]. This cost disparity compounds annually: a multi-tenant platform spreads infrastructure upgrades, security patching, and performance optimization across its entire customer base, while a custom deployment bears these costs alone.
2. Ecosystem Network Effects: Salesforce's AppExchange hosts over 7,000 pre-built applications and integrations, with
88% of customers using at least one AppExchange product [
73]. Morningstar assigns Salesforce a "Wide Moat" rating specifically citing these network effects [
73]. A custom-built CRM starts with zero ecosystem — every integration, every extension, every add-on must be built or procured independently.
3. Regulatory Compliance at Scale: Enterprise CRM platforms maintain SOC 2 Type II, HIPAA, GDPR, FedRAMP, and industry-specific compliance certifications as a shared service. For a custom application, achieving and maintaining these certifications is a dedicated, ongoing, and expensive undertaking. Financial services, healthcare, and government sectors face particularly acute compliance burdens that strongly favor certified platforms.
4. Platform Evolution Velocity: Salesforce ships hundreds of features across three major releases per year (Spring, Summer, Winter). The 2024--2025 period alone saw the launch of Agentforce, Data Cloud Vector Database, Einstein Trust Layer, SLDS 2, and Flow orchestration capabilities [
43,
44]. A custom application team cannot match this velocity — every new AI capability, security patch, and performance optimization must be independently researched, developed, tested, and deployed.
5. Data Model Maturity: Enterprise CRM platforms encode decades of domain knowledge in their standard data models — Account-Contact-Opportunity for sales, Case-Knowledge-Entitlement for service, Lead-Campaign-Journey for marketing. These models embody best practices refined across millions of implementations. A custom application must design its data model from scratch, a process where errors are expensive to correct after production deployment.
6. Integration Pre-Built Connectors: Enterprise CRM platforms provide pre-built connectors to hundreds of external systems (ERP, marketing automation, telephony, data providers). At a Tier-1 telecommunications provider (Telco-A), 22 integrations were delivered in 10 weeks using MuleSoft's pre-built connectors — a timeline impossible with custom integration development.
7. Talent Ecosystem: The Salesforce ecosystem includes over 4 million certified professionals. The CRM talent market is mature, with established training paths, certification programs, and a global workforce. Custom application development requires specialized talent that is harder to recruit, more expensive to retain (tech industry turnover is 36% [
74]), and creates key-person risk when developers with institutional knowledge leave.
8.4. The Hidden Costs of Custom: Why Enterprise CRM Replacements Fail
The historical evidence on custom enterprise application development is unambiguous in its severity:
Table 7.
Hidden cost evidence for custom enterprise application development.
Table 7.
Hidden cost evidence for custom enterprise application development.
| Metric |
Finding |
Source |
| Project failure rate |
75--85% of custom IT projects fail to meet objectives |
Gartner [75] |
| Build-vs-buy failures |
67% of enterprise failures trace to wrong build-vs-buy decisions |
Forrester [65] |
| Cost multiplier |
Custom builds cost 3--5x more upfront than SaaS alternatives |
McKinsey [68] |
| Post-deployment costs |
65% of total custom AI solution costs materialize post-deployment |
a16z [76] |
| Maintenance burden |
Enterprise applications require 15--20% of initial build cost annually for maintenance |
Industry consensus |
The post-deployment cost finding is particularly relevant: 65% of total costs emerge after the application is live, in the form of bug fixes, security patches, performance optimization, compliance updates, user training, and feature enhancements [
76]. AI coding agents can accelerate the initial build, but they do not eliminate — and current evidence suggests they may exacerbate — the long-term maintenance burden [
70,
71,
72].
Furthermore, McKinsey's analysis of enterprise AI strategy now frames the decision as four options rather than a binary build-vs-buy:
build, buy, blend, or partner [
77]. Their recommendation is clear: buy standardized capabilities (CRM, ERP) and reserve custom development for proprietary workflows that create genuine competitive differentiation. Only
24% of enterprise AI use cases are now custom-built, down from a majority in 2024, with 76% being purchased or blended from vendor platforms [
76].
8.5. AI-Generated Code: The Quality and Security Problem
Even if AI tools reduce the time to write code, the evidence on code quality raises serious concerns for mission-critical enterprise applications that handle customer data:
Security vulnerabilities: Veracode's analysis of code generated by 100+ LLMs found a
45% security vulnerability rate — nearly half of all AI-generated code contained exploitable security flaws [
78]. CodeRabbit's independent analysis found
2.74x more cross-site scripting (XSS) vulnerabilities and
1.7x more issues overall in AI-generated code compared to human-written code [
79].
Code quality degradation: GitClear's 2025 research found that code duplication increased
8x in repositories with heavy AI coding tool usage, while refactoring activity declined from 25% to less than 10% of code changes [
80]. This pattern — more new code, less maintenance of existing code — is the precise opposite of sustainable software engineering practice.
Shadow AI risk: IBM's 2025 Cost of Data Breach report found that security breaches involving shadow AI cost organizations an average of
$670,000 more than breaches without AI involvement [
81]. Gartner reports that
69% of organizations have evidence of prohibited GenAI use by employees [
82].
For enterprise CRM applications handling personally identifiable information (PII), financial data, and healthcare records, these quality and security risks are not abstract concerns — they are potential regulatory violations with material financial consequences.
Table 8.
The divergent trajectories of custom-built vs. platform-based CRM in the AI era.
Table 8.
The divergent trajectories of custom-built vs. platform-based CRM in the AI era.
| Step |
Build Custom CRM with AI Agents |
Buy Enterprise CRM Platform |
| 1 |
AI generates code — 45% vulnerability rate |
Platform-managed security — SOC 2, HIPAA certified |
| 2 |
Team deploys fast but maintenance backlog grows |
3 releases/year, auto-upgraded |
| 3 |
Security audit reveals XSS, SOQL injection, PII exposure |
AppExchange ecosystem — 7,000+ pre-built apps |
| 4 |
Remediation costs exceed SaaS licensing savings |
AI features (Agentforce) included in platform |
| 5 |
Organization migrates to SaaS platform |
Focus on business differentiation |
8.6. Historical Precedent: Why Every "Build Your Own CRM" Movement Has Failed
The current AI-enabled "build your own" narrative is not novel. Four previous waves of technology promised to make custom CRM development feasible at enterprise scale, and each was ultimately absorbed into — rather than displacing — the dominant platform ecosystem:
Wave 1 -- 4GL and RAD Tools (1990s): Fourth-generation programming languages and rapid application development tools promised to accelerate custom application development. Enterprise CRM vendors (Siebel, SAP) absorbed the productivity gains into their own platforms.
Wave 2 -- Open Source CRM (2004--2015): SugarCRM raised
$110 million in venture funding on the thesis that open-source CRM could displace proprietary platforms. Despite significant investment and a capable product, SugarCRM never achieved meaningful enterprise market penetration against Salesforce [
83]. SuiteCRM, vTiger, and other open-source alternatives remain niche solutions.
Wave 3 -- Low-Code Platforms (2014--Present): Low-code and no-code platforms (OutSystems, Mendix, Appian) promised to democratize application development. The market reached
$30 billion, but rather than displacing CRM platforms, low-code capabilities were
absorbed into them — Salesforce Flow, Microsoft Power Platform, and ServiceNow App Engine are now the largest low-code platforms in their respective ecosystems [
38,
83].
Wave 4 -- AI Coding Agents (2023--Present): The current wave. The pattern from Waves 1--3 is instructive: productivity-enhancing development technologies do not eliminate the need for enterprise platforms; they are absorbed by them. Salesforce's Einstein for Developers, Agentforce, and Flow generation capabilities represent the platform absorption of AI coding assistance, just as Salesforce Flow absorbed the low-code movement.
The consistent historical pattern is not that enterprise platforms are disrupted by development productivity tools — it is that enterprise platforms incorporate those tools, using them to increase their own velocity while maintaining the structural advantages (multi-tenancy, compliance, ecosystem) that custom applications cannot replicate.
8.7. Where AI Actually Threatens SaaS: The Real Pressure Points
While AI agents are unlikely to replace enterprise CRM platforms wholesale, the disruption thesis identifies real pressure points that CRM vendors must address:
1. Point Solution Displacement: Narrow, single-function SaaS tools (email sequencing, call logging, data enrichment) are genuinely vulnerable. An AI agent can replicate a
$50/user/month email sequencing tool in hours. The SaaS applications most at risk are those with shallow feature sets, limited data moats, and easily replicable logic [
64,
66].
2. Pricing Model Pressure: AI agents commoditize per-seat licensing by automating tasks that previously required human users. If an AI agent handles 70% of customer service cases autonomously [
43], the per-seat economic model breaks down. Forrester documents the rapid decline of seat-based pricing [
65], and CRM vendors are responding with outcome-based and consumption-based pricing models.
3. Customization Layer Competition: The most expensive part of CRM implementations is customization — the triggers, flows, integrations, and UI components that tailor a platform to organizational needs. AI coding agents directly compete in this layer, potentially enabling smaller teams to achieve customization that previously required large consulting engagements. This threatens the CRM consulting ecosystem more than the CRM platforms themselves.
4. Platform Lock-In Backlash: Counterintuitively, Forrester finds that AI is
deepening vendor lock-in rather than reducing it, as major vendors use AI features to increase switching costs [
84]. This risks provoking a backlash: Gartner recommends that 30% of enterprise GenAI spending target open models by 2028 as an antidote to vendor lock-in [
82].
8.8. The Market Verdict: Acceleration, Not Displacement
Despite the disruption narrative, the CRM market is not contracting — it is accelerating:
Table 9.
CRM market indicators show acceleration, not displacement, despite the AI disruption narrative.
Table 9.
CRM market indicators show acceleration, not displacement, despite the AI disruption narrative.
| Metric |
Value |
Source |
| Global CRM market (2024) |
$128 billion (13.4% growth) |
Gartner [85] |
| CRM market projection (2032) |
$263 billion |
Fortune Business Insights [86] |
| AI-in-CRM subsegment growth |
28% CAGR ($4.1B to $48.4B by 2033) |
Grand View Research [87] |
| Salesforce CRM revenue (FY25) |
$21.6 billion (4x nearest competitor) |
IDC [88] |
| Salesforce Data Cloud + AI ARR |
$900 million |
Salesforce [49] |
The evidence suggests that AI is not replacing CRM platforms but rather becoming the
primary growth driver within them. The AI-in-CRM subsegment is growing at 28% CAGR — faster than any other CRM category — and platform vendors are capturing this growth by embedding AI capabilities directly into their platforms [
87].
8.9. The Composable Middle Ground
The true architectural response to the build-vs-buy tension is not a binary choice but a
composable architecture that combines platform capabilities with targeted custom development. Gartner's Composable Enterprise framework predicts that 70% of organizations will use composability as a key selection criterion for new technology [
89]. The MACH (Microservices, API-first, Cloud-native, Headless) architecture movement reinforces this trend, with 60% of new digital commerce solutions projected to use composable principles by 2027 [
89].
In this model, enterprises buy the CRM platform for its structural advantages (multi-tenancy, compliance, ecosystem, data model, evolution velocity), build custom components only where they create genuine competitive differentiation (proprietary algorithms, industry-specific workflows), and blend through composable API-first services that enable both platform and custom components to interoperate. AI coding agents accelerate the "build" and "blend" layers without eliminating the need for the "buy" foundation.
Figure 17.
The composable middle ground: combining platform capabilities with targeted custom development through API-first integration.
Figure 17.
The composable middle ground: combining platform capabilities with targeted custom development through API-first integration.