Submitted:
16 January 2026
Posted:
19 January 2026
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Materials and Methods
2.1. Sample and Study Setting
2.2. Experimental Design and Control Setup
2.3. Measurement Procedures and Quality Assurance
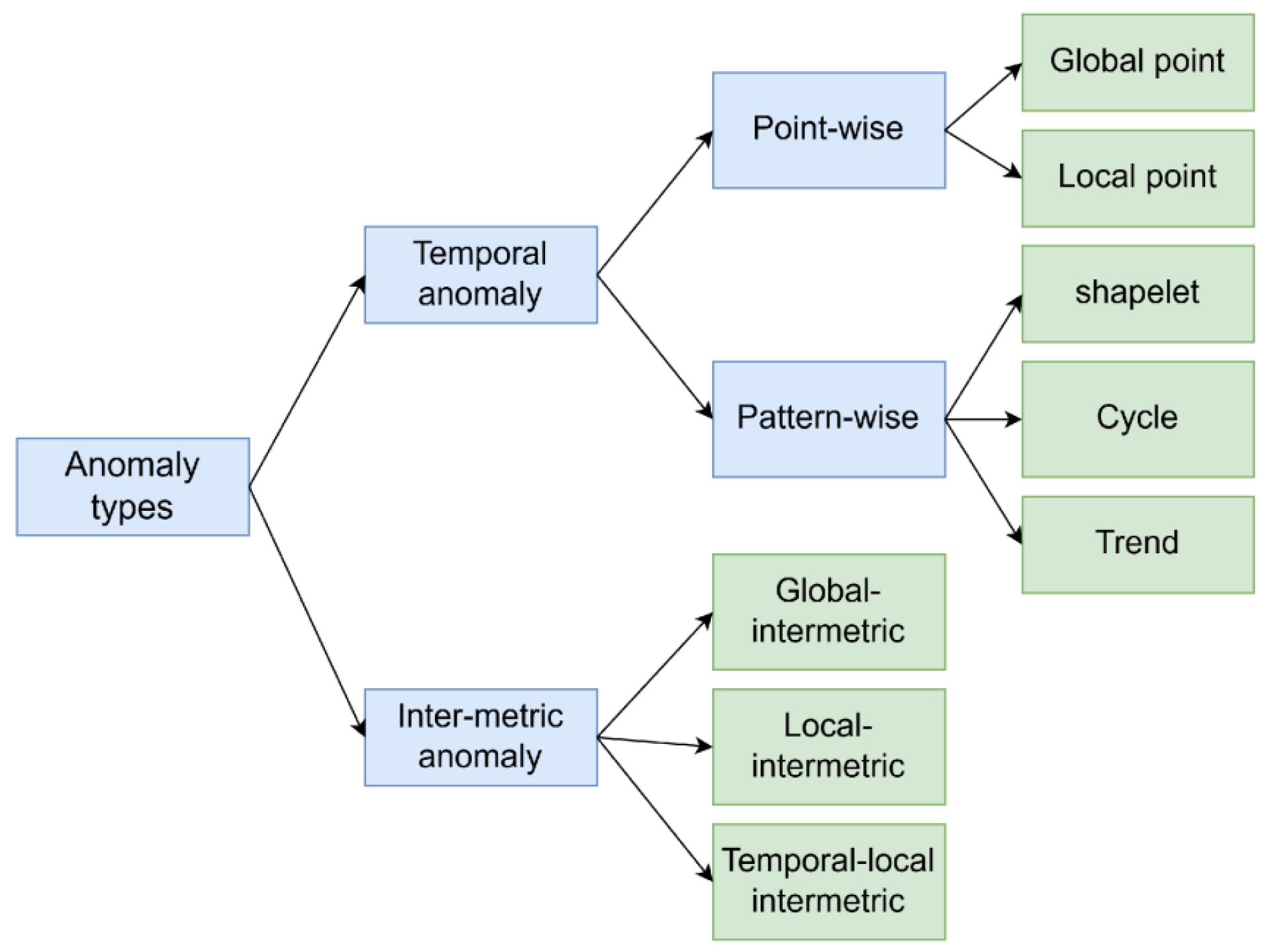
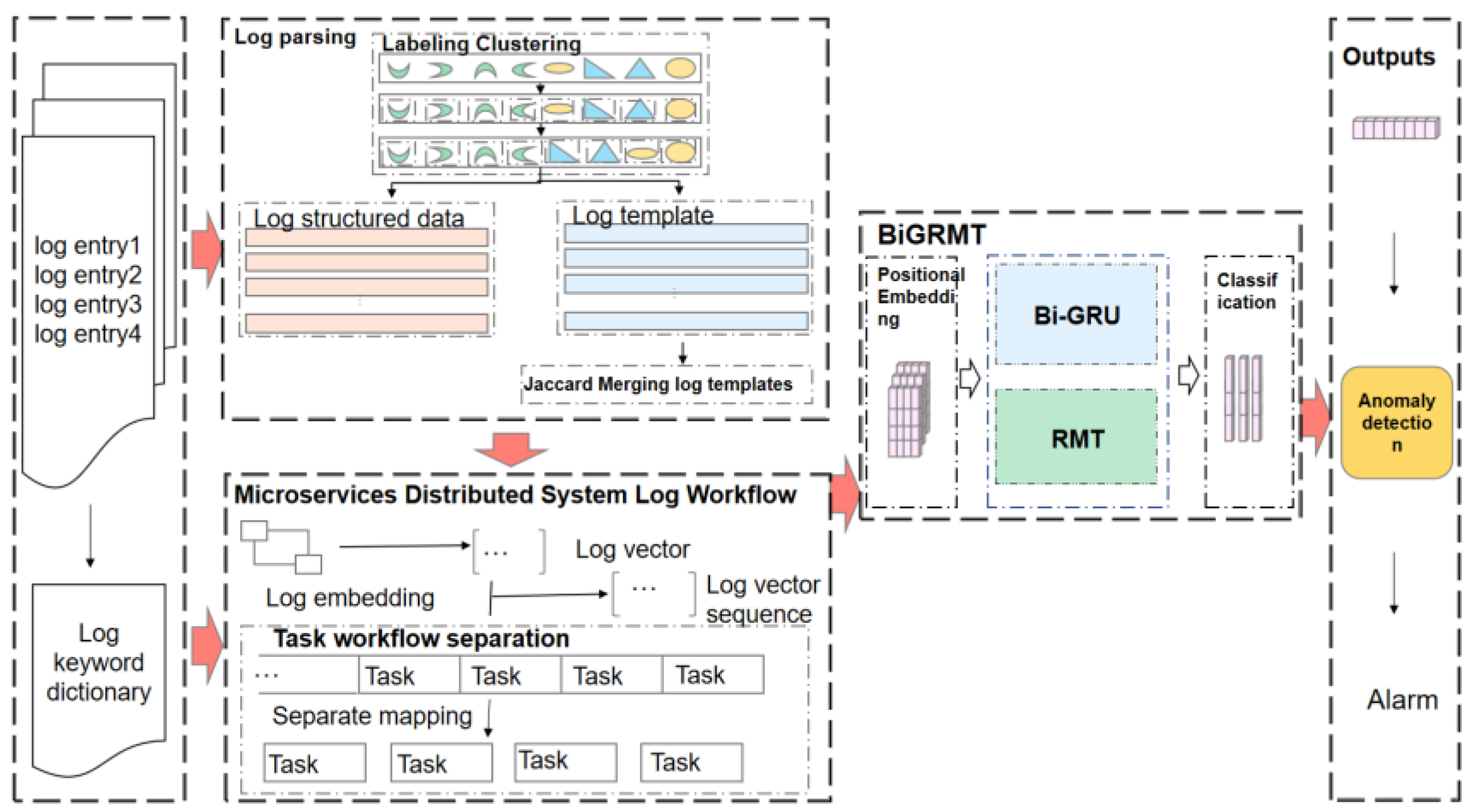
2.4. Data Processing and Model Formulation
3. Results and Discussion
3.1. Overall Anomaly Detection Performance
3.2. Detection Delay and Comparison with Baseline Methods
3.3. Self-Healing Actions and Operational Impact
3.4. Comparison with Earlier AIOps Studies and Limits of the Current Work
4. Conclusions
References
- Das, R.; Zhou, L.; Bi, S.; Wang, T.; Hou, T. Towards the Safety of Intelligent Transportation: A Survey on the Security Challenges and Mitigations in Internet of Vehicles (IoV). In ACM Transactions on Sensor Networks; 2025. [Google Scholar]
- Gui, H.; Wang, B.; Lu, Y.; Fu, Y. Computational Modeling-Based Estimation of Residual Stress and Fatigue Life of Medical Welded Structures. 2025. [Google Scholar]
- Ain, Q.U.; Jilani, A.A.A.; Butt, N.A.; Rehman, S.U.; Alhulayyil, H.A. Anomaly detection for aviation cyber-physical system: Opportunities and challenges. IEEE Access 2024, 12, 175905–175925. [Google Scholar] [CrossRef]
- Tan, L.; Liu, D.; Liu, X.; Wu, W.; Jiang, H. Efficient Grey Wolf Optimization: A High-Performance Optimizer with Reduced Memory Usage and Accelerated Convergence. 2025. [Google Scholar]
- Elbamby, M.S.; Perfecto, C.; Liu, C.F.; Park, J.; Samarakoon, S.; Chen, X.; Bennis, M. Wireless edge computing with latency and reliability guarantees. Proceedings of the IEEE 2019, 107(8), 1717–1737. [Google Scholar] [CrossRef]
- Hu, W.; Huo, Z. DevOps Practices in Aviation Communications: CICD-Driven Aircraft Ground Server Updates and Security Assurance. 2025 5th International Conference on Mechatronics Technology and Aerospace Engineering (ICMTAE 2025), 2025, July. [Google Scholar]
- Villegas, M. M.; Solar, M.; Giraldo, F. D.; Astudillo, H. DeOTA-IoT: A Techniques Catalog for Designing Over-the-Air (OTA) Update Systems for IoT. Sensors (Basel, Switzerland) 2025, 26(1), 193. [Google Scholar] [CrossRef] [PubMed]
- Dmitriev, K.; Zafar, S. A.; Schmiechen, K.; Lai, Y.; Saleab, M.; Nagarajan, P.; Myschik, S. A lean and highly-automated model-based software development process based on do-178c/do-331. 2020 AIAA/IEEE 39th Digital Avionics Systems Conference (DASC), 2020, October; IEEE; pp. 1–10. [Google Scholar]
- Bai, W.; Wu, Q. Towards more effective responsible disclosure for vulnerability research. Proc. of EthiCS. 2023. [Google Scholar]
- Ribeiro, J.E.F.; Silva, J.G.; Aguiar, A. Scrum4DO178C: an Agile Process to Enhance Aerospace Software Development for DO-178C Compliance–a Case Study at Criticality Level A. IEEE Access 2025. [Google Scholar]
- Liu, S.; Feng, H.; Liu, X. A Study on the Mechanism of Generative Design Tools' Impact on Visual Language Reconstruction: An Interactive Analysis of Semantic Mapping and User Cognition. Authorea Preprints. 2025. [Google Scholar]
- Resch, S.; Paulitsch, M. Using TLA+ in the development of a safety-critical fault-tolerant middleware. 2017 IEEE International Symposium on Software Reliability Engineering Workshops (ISSREW), 2017, October; IEEE; pp. 146–152. [Google Scholar]
- Du, Y. Research on Deep Learning Models for Forecasting Cross-Border Trade Demand Driven by Multi-Source Time-Series Data. Journal of Science, Innovation & Social Impact 2025, 1, 63–70. [Google Scholar]
- Utami, E.; Al Fatta, H. Analysis on the use of declarative and pull-based deployment models on gitops using argo cd. 2021 4th International Conference on Information and Communications Technology (ICOIACT), 2021, August; IEEE; pp. 186–191. [Google Scholar]
- Hu, Z.; Hu, Y.; Li, H. Multi-Task Temporal Fusion Transformer for Joint Sales and Inventory Forecasting in Amazon E-Commerce Supply Chain. arXiv 2025, arXiv:2512.00370. [Google Scholar]
- Merlin, P.W. Green Light for Green Flight: NASA's Contributions to Environmentally Friendly Aviation (No. HQ-E-DAA-TN76912). National Aeronautics and Space Administration. 2020. [Google Scholar]
- Fu, Y.; Gui, H.; Li, W.; Wang, Z. Virtual Material Modeling and Vibration Reduction Design of Electron Beam Imaging System. 2020 IEEE International Conference on Advances in Electrical Engineering and Computer Applications (AEECA), 2020, August; IEEE; pp. 1063–1070. [Google Scholar]
- Tae, C.J.; Pang, M.S.; Greenwood, B.N. When your problem becomes my problem: The impact of airline IT disruptions on on-time performance of competing airlines. Strategic Management Journal 2020, 41, 246–266. [Google Scholar] [CrossRef]
- Yang, M.; Cao, Q.; Tong, L.; Shi, J. Reinforcement learning-based optimization strategy for online advertising budget allocation. 2025 4th International Conference on Artificial Intelligence, Internet and Digital Economy (ICAID), 2025, April; IEEE; pp. 115–118. [Google Scholar]
- Memon, Z.; Saini, I. A Comparative Survey of Blockchain-Based Security Mechanisms for OTA updates in CAVs. 2024 IEEE/ACM 17th International Conference on Utility and Cloud Computing (UCC), 2024, December; IEEE; pp. 423–428. [Google Scholar]
- Gu, J.; Narayanan, V.; Wang, G.; Luo, D.; Jain, H.; Lu, K.; Yao, L. Inverse design tool for asymmetrical self-rising surfaces with color texture. In Proceedings of the 5th Annual ACM Symposium on Computational Fabrication, 2020, November; pp. 1–12. [Google Scholar]
- Lian, L.; Li, Y.; Han, S.; Meng, R.; Wang, S.; Wang, M. Artificial intelligence-based multiscale temporal modeling for anomaly detection in cloud services. In Proceedings of the 2nd International Conference on Intelligent Computing and Data Analysis, 2025, August; pp. 956–964. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2026 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).



