Submitted:
01 January 2026
Posted:
04 January 2026
You are already at the latest version
Abstract
Keywords:
1. Introduction
1.1. Need for Security-Centric Architecture in Enterprise Systems
1.2. Impact of Vulnerability Exposure in Large-Scale Applications
1.3. Role of Design Patterns in Defensive Software Engineering
2. Literature Survey
| Focus Area | Methodology | Strengths | Limitations |
| Selection of Security Patterns | Formal vulnerability anti-pattern matching to select mitigations | Systematic mapping of vulnerabilities to patterns; tested on OWASP Juice Shop | Complexity in pattern selection guidance |
| Secure Design Pattern Catalog | Documentation of effective, reusable security patterns | Broad, well-documented patterns; reduces development cost and risk | Focuses on design; less on dynamic adaptation |
| IoT Security Patterns | Survey and classification of IoT-specific security patterns | Specialized for resource-constrained devices | Applicability limited to IoT contexts |
| Enterprise Secure Architecture | Proposal of novel architecture pattern for generative AI applications | Balances AI capabilities with security; tailored for enterprise | Emerging area with limited broad adoption |
3. Fundamentals of Secure Design Patterns
3.1. Definition and Characteristics of Secure Design Patterns
3.2. Relationship with Security Principles (CIA, Zero Trust, Least Privilege)
3.3. Mapping Design Patterns to OWASP, NIST, and CWE Standards
4. Modular Architectural Principles for Secure Enterprise Development
4.1. Component-Based and Layered Architecture Models
4.2. Separation of Concerns and Privileged Segmentation
4.3. Microservices and Container-Based Modular Security
5. Design Patterns to Reduce Common Vulnerability Exposure
5.1. Input Validation & Sanitization Patterns
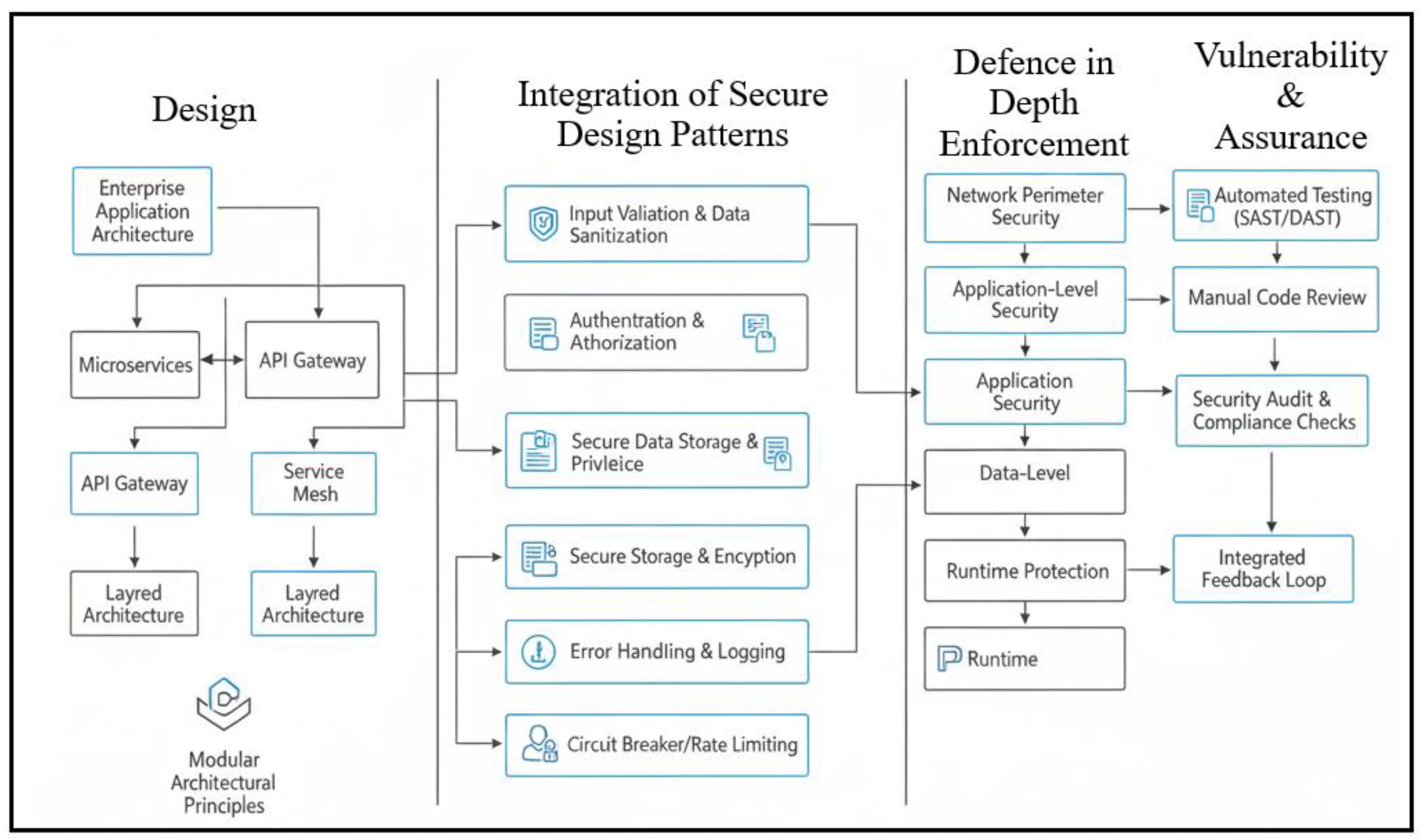
5.2. Authentication & Authorization Patterns (RBAC, ABAC, Token-Based)
5.3. Secure Session Management Patterns
5.4. Data Encryption, Masking, and Secure Storage Patterns
6. Defence-in-Depth Through Multi-Layered Pattern Deployment
6.1. Network Layer Security: API Gateways, Firewalls, Identity Brokers
6.2. Application Layer: Sanitization Layers, Policy Enforcement, Secure Middleware
6.3. Data Layer: Access Controls, Audit Trails, Tamper-Proof Logs
7. Design Patterns for Emerging Architectures
7.1. Cloud-Native and Serverless Security Patterns
7.2. Zero-Trust and Service Mesh-Based Communication Patterns
7.3. DevSecOps Aligned CI/CD Security Patterns
8. Tools and Frameworks Supporting Secure Pattern Implementation
8.1. Security Pattern Libraries and Repositories
8.2. Enforcement Through Policy Engines & Infrastructure as Code (IaC) Templates
8.3. Code Frameworks and SDK-Based Secure Defaults
9. Case Study: Enterprise Application Hardened with Secure Design Patterns
9.1. System Architecture Overview
9.2. Pattern Selection and Layer Mapping
9.3. Results: Reduced CVEs and Improved Compliance
10. Challenges and Limitations
10.1. Complexity in Legacy System Integration
10.2. Overlapping Controls and Performance Overheads
10.3. Inconsistent Implementation Across Teams
Conclusion and Future Enhancements
References
- Inbaraj, R.; Ravi, G. A survey on recent trends in content based image retrieval system. Journal of Critical Reviews 2020, 7, 961–965. [Google Scholar]
- Atheeq, C.; Sultana, R.; Sabahath, S.A.; Mohammed, M.A.K. Advancing IoT Cybersecurity: adaptive threat identification with deep learning in Cyber-physical systems. Engineering, Technology & Applied Science Research 2024, 14, 13559–13566. [Google Scholar]
- Vikram, A.V.; Arivalagan, S. Engineering properties on the sugar cane bagasse with sisal fibre reinforced concrete. International Journal of Applied Engineering Research 2017, 12, 15142–15146. [Google Scholar]
- Mohammed Nabi Anwarbasha, G.T.; Chakrabarti, A.; Bahrami, A.; Venkatesan, V.; Vikram, A.S.V.; Subramanian, J.; Mahesh, V. Efficient finite element approach to four-variable power-law functionally graded plates. Buildings 2023, 13, 2577. [Google Scholar] [CrossRef]
- Kumar, J.D.S.; Subramanyam, M.V.; Kumar, A.S. Hybrid Sand Cat Swarm Optimization Algorithm-based reliable coverage optimization strategy for heterogeneous wireless sensor networks. International Journal of Information Technology 2024, 1–19. [Google Scholar] [CrossRef]
- Siddiqui, A.; Chand, K.; Shahi, N.C. Effect of process parameters on extraction of pectin from sweet lime peels. Journal of The Institution of Engineers (India): Series A 2021, 102, 469–478. [Google Scholar] [CrossRef]
- Sultana, R.; Ahmed, N.; Sattar, S.A. HADOOP based image compression and amassed approach for lossless images. Biomedical Research 2018, 29, 1532–1542. [Google Scholar] [CrossRef]
- Inbaraj, R.; Ravi, G. Content Based Medical Image Retrieval Using Multilevel Hybrid Clustering Segmentation with Feed Forward Neural Network. Journal of Computational and Theoretical Nanoscience 2020, 17, 5550–5562. [Google Scholar] [CrossRef]
- Sharma, T.; Reddy, D.N.; Kaur, C.; Godla, S.R.; Salini, R.; Gopi, A.; Baker El-Ebiary, Y.A. Federated Convolutional Neural Networks for Predictive Analysis of Traumatic Brain Injury: Advancements in Decentralized Health Monitoring. International Journal of Advanced Computer Science & Applications 2024, 15. [Google Scholar]
- Saravanan, V.; Sumalatha, A.; Reddy, D.N.; Ahamed, B.S.; Udayakumar, K. (2024, October). Exploring Decentralized Identity Verification Systems Using Blockchain Technology: Opportunities and Challenges. In 2024 5th IEEE Global Conference for Advancement in Technology (GCAT) (pp. 1–6). IEEE.
- Jeyaprabha, B.; Sundar, C. The mediating effect of e-satisfaction on e-service quality and e-loyalty link in securities brokerage industry. Revista Geintec-gestao Inovacao E Tecnologias 2021, 11, 931–940. [Google Scholar]
- Ganeshan, M.K.; Vethirajan, C. Skill development initiatives and employment opportunity in India. Universe International Journal of Interdisciplinary Research 2020, 1, 21–28. [Google Scholar]
- Chand, K.; Shahi, N.C.; Lohani, U.C.; Garg, S.K. Effect of storage conditions on keeping qualities of jaggery. Sugar Tech 2011, 13, 81–85. [Google Scholar] [CrossRef]
- Nizamuddin, M.K.; Raziuddin, S.; Farheen, M.; Atheeq, C.; Sultana, R. An MLP-CNN Model for Real-time Health Monitoring and Intervention. Engineering, Technology & Applied Science Research 2024, 14, 15553–15558. [Google Scholar]
- Arunachalam, S.; Kumar, A.K.V.; Reddy, D.N.; Pathipati, H.; Priyadarsini, N.I.; Ramisetti, L.N.B. Modeling of chimp optimization algorithm node localization scheme in wireless sensor networks. Int J Reconfigurable & Embedded Syst 2025, 14, 221–230. [Google Scholar]
- Saravanan, V.; Upender, T.; Ruby, E.K.; Deepalakshmi, P.; Reddy, D.N.; SN, A. (2024, October). Machine Learning Approaches for Advanced Threat Detection in Cyber Security. In 2024 5th IEEE Global Conference for Advancement in Technology (GCAT) (pp. 1–6). IEEE.
- Reddy, D.N.; Venkateswararao, P.; Vani, M.S.; Pranathi, V.; Patil, A. HybridPPI: A Hybrid Machine Learning Framework for Protein-Protein Interaction Prediction. Indonesian Journal of Electrical Engineering and Informatics (IJEEI) 2025, 13. [Google Scholar] [CrossRef]
- Nasir, G.; Chand, K.; Azaz Ahmad Azad, Z.R.; Nazir, S. Optimization of Finger Millet and Carrot Pomace based fiber enriched biscuits using response surface methodology. Journal of Food Science and Technology 2020, 57, 4613–4626. [Google Scholar] [CrossRef] [PubMed]
- Permana, F.; Guntara, Y.; Saefullah, A. The Influence of Visual Thinking Strategy In Augmented Reality (ViTSAR) to Improve Students’ Visual Literacy Skills on Magnetic Field Material. Phi: Jurnal Pendidikan Fisika dan Terapan 2025, 11, 71–81. [Google Scholar] [CrossRef]
- Rao, A.S.; Reddy, Y.J.; Navya, G.; Gurrapu, N.; Jeevan, J.; Sridhar, M.; Anand, D. High-performance sentiment classification of product reviews using GPU (parallel)-optimized ensembled methods. [CrossRef]
- Vikram, V.; Soundararajan, A.S. Durability studies on the pozzolanic activity of residual sugar cane bagasse ash sisal fibre reinforced concrete with steel slag partially replacement of coarse aggregate. Caribb. J. Sci 2021, 53, 326–344. [Google Scholar]
- Ramaswamy, S.N.; Arunmohan, A.M. Static and Dynamic analysis of fireworks industrial buildings under impulsive loading. IJREAT International Journal of Research in Engineering & Advanced Technology 2013, 1. [Google Scholar]
- Jeyaprabha, B.; Catherine, S.; Vijayakumar, M. Unveiling the Economic Tapestry: Statistical Insights Into India’s Thriving Travel and Tourism Sector. In Managing Tourism and Hospitality Sectors for Sustainable Global Transformation; IGI Global Scientific Publishing, 2024; pp. 249–259. [Google Scholar]
- Akat, G.B.; Magare, B.K. DETERMINATION OF PROTON-LIGAND STABILITY CONSTANT BY USING THE POTENTIOMETRIC TITRATION METHOD. MATERIAL SCIENCE 2023, 22. [Google Scholar]
- Thakur, R.R.; Shahi, N.C.; Mangaraj, S.; Lohani, U.C.; Chand, K. Development of an organic coating powder and optimization of process parameters for shelf life enhancement of button mushrooms (Agaricus bisporus). Journal of Food Processing and Preservation 2021, 45, e15306. [Google Scholar] [CrossRef]
- Kamatchi, S.; Preethi, S.; Kumar, K.S.; Reddy, D.N.; Karthick, S. (2025, May). Multi-Objective Genetic Algorithm Optimised Convolutional Neural Networks for Improved Pancreatic Cancer Detection. In 2025 3rd International Conference on Data Science and Information System (ICDSIS) (pp. 1–7). IEEE.
- Vethirajan, C.; Ramu, C. Consumers’ knowledge on corporate social responsibility of select FMCG companies in Chennai district. Journal of International Business and Economics 2019, 12, 82–103. [Google Scholar]
- Kumar, J.D.S. Investigation on secondary memory management in wireless sensor network. Int J Comput Eng Res Trends 2015, 2, 387–391. [Google Scholar]
- Dehankar, S.; Amari, S.; Ashtankar, R. Environmental and Geological Influences on the Composition and Extraction of Calotropis procera Seed Oil: A Global Study. Journal of Pharmaceutical Research International 2025, 37, 127–133. [Google Scholar] [CrossRef]
- Sultana, R.; Ahmed, N.; Basha, S.M. Advanced Fractal Image Coding Based on the Quadtree. Computer Engineering and Intelligent Systems 2011, 2, 129–136. [Google Scholar]
- Nimma, D.; Rao, P.L.; Ramesh, J.V.N.; Dahan, F.; Reddy, D.N.; Selvakumar, V.; Jangir, P. Reinforcement Learning-Based Integrated Risk Aware Dynamic Treatment Strategy for Consumer-Centric Next-Gen Healthcare. IEEE Transactions on Consumer Electronics 2025. [Google Scholar] [CrossRef]
- Chand, K. Effect of pre-cooling treatments on shelf life of tomato in ambient condition. 2013. [Google Scholar]
- Akat, G.B. Structural Analysis of Ni1-xZnxFe2O4 Ferrite System. MATERIAL SCIENCE 2023, 22. [Google Scholar]
- Inbaraj, R.; John, Y.M.; Murugan, K.; Vijayalakshmi, V. Enhancing medical image classification with cross-dimensional transfer learning using deep learning. 2025, 10, 389. [Google Scholar]
- JEYAPRABHA, B.; SUNDAR, C. The Psychological Dimensions Of Stock Trader Satisfaction With The E-Broking Service Provider. Journal of Positive School Psychology 2022, 6. [Google Scholar]
- Shanmuganathan, C.; Raviraj, P. (2011). A comparative analysis of demand assignment multiple access protocols for wireless ATM networks. In International Conference on Computational Science, Engineering and Information Technology (pp. 523–533). Berlin, Heidelberg: Springer Berlin Heidelberg.
- Mohamed, S.R.; Raviraj, P. Approximation of Coefficients Influencing Robot Design Using FFNN with Bayesian Regularized LMBPA. Procedia Engineering 2012, 38, 1719–1727. [Google Scholar] [CrossRef]
- Chand, K.; Singh, A.; Kulshrestha, M. Jaggery quality effected by hilly climatic conditions. Indian Journal of Traditional Knowledge 2012, 11, 172–176. [Google Scholar]
- Khan, M.J.; Ahmed, M.R.; Taha, M.A.A.; Sultana, R. Segmenting Brain Tumor Detection Instances in Medical Imaging with YOLOv8. RICE 2024, 35–38. [Google Scholar]
- Appaji, I.; Raviraj, P. (2020, February). Vehicular Monitoring Using RFID. In International Conference on Automation, Signal Processing, Instrumentation and Control (pp. 341–350). Singapore: Springer Nature Singapore.
- Akat, G.B. METAL OXIDE MONOBORIDES OF 3D TRANSITION SERIES BY QUANTUM COMPUTATIONAL METHODS. MATERIAL SCIENCE 2022, 21. [Google Scholar]
- Balakumar, B.; Raviraj, P. Automated Detection of Gray Matter in Mri Brain Tumor Segmentation and Deep Brain Structures Based Segmentation Methodology. Middle-East Journal of Scientific Research 2015, 23, 1023–1029. [Google Scholar]
- Arunmohan, A.M.; Bharathi, S.; Kokila, L.; Ponrooban, E.; Naveen, L.; Prasanth, R. An experimental investigation on utilisation of red soil as replacement of fine aggregate in concrete. Psychology and Education Journal 2021, 58. [Google Scholar]
- Kumar, A.; Chand, K.; Shahi, N.C.; Kumar, A.; Verma, A.K. Optimization of coating materials on jaggery for augmentation of storage quality. Indian Journal of Agricultural Sciences 2017, 87, 1391–1397. [Google Scholar] [CrossRef]
- David Sukeerthi Kumar, J.; Subramanyam, M.V.; Siva Kumar, A.P. (2023, March). A hybrid spotted hyena and whale optimization algorithm-based load-balanced clustering technique in WSNs. In Proceedings of International Conference on Recent Trends in Computing: ICRTC 2022 (pp. 797–809). Singapore: Springer Nature Singapore.
- Kumar, S.N.; Chandrasekar, S.; Jeyaprabha, B.; Sasirekha, V.; Bhatia, A. Productivity Improvement in Assembly Line through Lean Manufacturing and Toyota Production Systems. Advances in Consumer Research 2025, 2. [Google Scholar]
- Inbaraj, R.; Ravi, G. Content Based Medical Image Retrieval System Based On Multi Model Clustering Segmentation And Multi-Layer Perception Classification Methods. Turkish Online Journal of Qualitative Inquiry 2021, 12. [Google Scholar]
- Ramu, C.; Vethirajan, C. Customers perception of CSR impact on FMCG companies: an analysis. IMPACT: International Journal of Research in Business Management 2019, 7, 39–48. [Google Scholar]
- Csoka, L.; Katekhaye, S.N.; Gogate, P.R. Comparison of cavitational activity in different configurations of sonochemical reactors using model reaction supported with theoretical simulations. Chemical Engineering Journal 2011, 178, 384–390. [Google Scholar] [CrossRef]
- Shinkar, A.R.; Joshi, D.; Praveen, R.V.S.; Rajesh, Y.; Singh, D. (2024, December). Intelligent solar energy harvesting and management in IoT nodes using deep self-organizing maps. In 2024 International Conference on Emerging Research in Computational Science (ICERCS) (pp. 1–6). IEEE.
- Akat, G.B. OPTICAL AND ELECTRICAL STUDY OF SODIUM ZINC PHOSPHATE GLASS. MATERIAL SCIENCE 2022, 21. [Google Scholar]
- Channapatna, R. Role of AI (artificial intelligence) and machine learning in transforming operations in healthcare industry: An empirical study. Int J 2023, 10, 2069–76. [Google Scholar]
- Mubsira, M.; Niasi, K.S.K. Prediction of Online Products using Recommendation Algorithm; 2018. [Google Scholar]
- Yadav, D.K.; Chand, K.; Kumari, P. Effect of fermentation parameters on physicochemical and sensory properties of Burans wine. Systems Microbiology and Biomanufacturing 2022, 2, 380–392. [Google Scholar] [CrossRef]
- Sultana, R.; Bilfagih, S.M.; Sabahath, S.A. A Novel Machine Learning system to control Denial-of-Services Attacks. Design Engineering 2021, 3676–3683. [Google Scholar]
- Kumar, N.; Kurkute, S.L.; Kalpana, V.; Karuppannan, A.; Praveen, R.V.S.; Mishra, S. (2024, August). Modelling and Evaluation of Li-ion Battery Performance Based on the Electric Vehicle Tiled Tests using Kalman Filter-GBDT Approach. In 2024 International Conference on Intelligent Algorithms for Computational Intelligence Systems (IACIS) (pp. 1–6). IEEE.
- Yamuna, V.; Praveen, R.V.S.; Sathya, R.; Dhivva, M.; Lidiya, R.; Sowmiya, P. (2024, October). Integrating AI for Improved Brain Tumor Detection and Classification. In 2024 4th International Conference on Sustainable Expert Systems (ICSES) (pp. 1603–1609). IEEE.
- Katekhaye, S.N.; Gogate, P.R. Intensification of cavitational activity in sonochemical reactors using different additives: efficacy assessment using a model reaction. Chemical Engineering and Processing: Process Intensification 2011, 50, 95–103. [Google Scholar] [CrossRef]
- Akat, G.B. STRUCTURAL AND MAGNETIC STUDY OF CHROMIUM FERRITE NANOPARTICLES. MATERIAL SCIENCE 2022, 21. [Google Scholar]
- Singh, A.; Santosh, S.; Kulshrestha, M.; Chand, K.; Lohani, U.C.; Shahi, N.C. Quality characteristics of Ohmic heated Aonla (Emblica officinalis Gaertn.) pulp. Indian Journal of Traditional Knowledge 2013, 12, 670–676. [Google Scholar]
- Dehankar, S.P.; Joshi, R.R.; Dehankar, P.B. Assessment of Different Advanced Technologies for Pharma Wastewater Treatment: A Review. Pollution Annual Volume 2024. 2023.
- Vijay Vikram, A.S.; Arivalagan, S. A short review on the sugarcane bagasse with sintered earth blocks of fiber reinforced concrete. Int J Civil Eng Technol 2017, 8, 323–331. [Google Scholar]
- Lopez, S.; Sarada, V.; Praveen, R.V.S.; Pandey, A.; Khuntia, M.; Haralayya, D.B. Artificial intelligence challenges and role for sustainable education in india: Problems and prospects. Library Progress International 2024, 44, 18261–18271. [Google Scholar] [CrossRef]
- Niasi, K.S.K.; Kannan, E. Multi Attribute Data Availability Estimation Scheme for Multi Agent Data Mining in Parallel and Distributed System. International Journal of Applied Engineering Research 2016, 11, 3404–3408. [Google Scholar]
- Jeyaprabha, B.; Kumar, S.R.; Bolla, R.L.; Bhatt, A.S.; Sera, R.J.; Arora, K. (2025, February). Data-Driven Decision Making in Management: Leveraging Big Data Analytics for Strategic Planning. In 2025 First International Conference on Advances in Computer Science, Electrical, Electronics, and Communication Technologies (CE2CT) (pp. 1000–1003). IEEE.
- Sharma, S.; Vij, S.; Praveen, R.V.S.; Srinivasan, S.; Yadav, D.K.; VS, R.K. (2024, October). Stress Prediction in Higher Education Students Using Psychometric Assessments and AOA-CNN-XGBoost Models. In 2024 4th International Conference on Sustainable Expert Systems (ICSES) (pp. 1631–1636). IEEE.
- Sultana, R.; Ahmed, N.; Sattar, S.A. An optimised clustering algorithm with dual tree DS for lossless image compression. International Journal of Biomedical Engineering and Technology 2021, 37, 219–238. [Google Scholar] [CrossRef]
- Gogate, P.R.; Katekhaye, S.N. A comparison of the degree of intensification due to the use of additives in ultrasonic horn and ultrasonic bath. Chemical Engineering and Processing: Process Intensification 2012, 61, 23–29. [Google Scholar] [CrossRef]
- Praveen, R.V.S.; Hemavathi, U.; Sathya, R.; Siddiq, A.A.; Sanjay, M.G.; Gowdish, S. (2024, October). AI Powered Plant Identification and Plant Disease Classification System. In 2024 4th International Conference on Sustainable Expert Systems (ICSES) (pp. 1610–1616). IEEE.
- Anuprathibha, T.; Praveen, R.V.S.; Sukumar, P.; Suganthi, G.; Ravichandran, T. (2024, October). Enhancing Fake Review Detection: A Hierarchical Graph Attention Network Approach Using Text and Ratings. In 2024 Global Conference on Communications and Information Technologies (GCCIT) (pp. 1–5). IEEE.
- Kemmannu, P.K.; Praveen, R.V.S.; Banupriya, V. (2024, December). Enhancing Sustainable Agriculture Through Smart Architecture: An Adaptive Neuro-Fuzzy Inference System with XGBoost Model. In 2024 International Conference on Sustainable Communication Networks and Application (ICSCNA) (pp. 724–730). IEEE.
- Moinuddin, S.K.; Sultana, R. PAMP Routing Algorithm in Wireless Networks. International Journal of Systems, Algorithms & Applications 2014, 4, 1. [Google Scholar]
- Chunara, F.; Dehankar, S.P.; Sonawane, A.A.; Kulkarni, V.; Bhatti, E.; Samal, D.; Kashwani, R. Advancements in biocompatible polymer-based nanomaterials for restorative dentistry: Exploring innovations and clinical applications: A literature review. African Journal of Biomedical Research 2024, 27, 2254–2262. [Google Scholar]
- Arunmohan, A.M.; Lakshmi, M. Analysis of modern construction projects using montecarlo simulation technique. International Journal of Engineering & Technology 2018, 7, 41–44. [Google Scholar] [CrossRef]
- Akat, G.B.; Magare, B.K. Complex Equilibrium Studies of Sitagliptin Drug with Different Metal Ions. Asian Journal of Organic & Medicinal Chemistry 2022. [Google Scholar]
- Pandey, R.K.; Chand, K.; Tewari, L. Solid state fermentation and crude cellulase based bioconversion of potential bamboo biomass to reducing sugar for bioenergy production. Journal of the Science of Food and Agriculture 2018, 98, 4411–4419. [Google Scholar] [CrossRef]
- Kumar, S.N.; Chandrasekar, S.; Vizhalil, M.; Jeyaprabha, B.; Sasirekha, V.; Bhatia, A. Assessing the Mediating Role of Recognizing and Overcoming Challenges in Using Iot and Analytics to Enhance Supply Chain Performance. Journal of Lifestyle and SDGs Review 2025, 5, e05796–e05796. [Google Scholar] [CrossRef]
- Niasi, K.S.K.; Kannan, E.; Suhail, M.M. Page-level data extraction approach for web pages using data mining techniques. International Journal of Computer Science and Information Technologies 2016, 7, 1091–1096. [Google Scholar]
- Kumar, J.D.S.; Subramanyam, M.V.; Kumar, A.P.S. Hybrid Chameleon Search and Remora Optimization Algorithm-based Dynamic Heterogeneous load balancing clustering protocol for extending the lifetime of wireless sensor networks. International Journal of Communication Systems 2023, 36, e5609. [Google Scholar] [CrossRef]
- Banu, S.S.; Niasi, K.S.K.; Kannan, E. Classification Techniques on Twitter Data: A Review. Asian Journal of Computer Science and Technology 2019, 8, 66–69. [Google Scholar] [CrossRef]
- Praveen, R.V.S. Data Engineering for Modern Applications; Addition Publishing House, 2024. [Google Scholar]
- Sutar-Kapashikar, P.S.; Gawali, T.R.; Koli, S.R.; Khot, A.S.; Dehankar, S.P.; Patil, P.D. Phenolic content in Triticum aestivum: A review. International Journal of New Technology and Research 2018, 4, 01–02. [Google Scholar] [CrossRef]
- Inbaraj, R.; Ravi, G. Multi Model Clustering Segmentation and Intensive Pragmatic Blossoms (Ipb) Classification Method based Medical Image Retrieval System. Annals of the Romanian Society for Cell Biology 2021, 25, 7841–7852. [Google Scholar]
- Ghouse, M.; Muzaffarullah, S.; Sultana, R. Internet of Things-Based Arrhythmia Disease Prediction Using Machine Learning Techniques.
- Praveen, R.V.S.; Hundekari, S.; Parida, P.; Mittal, T.; Sehgal, A.; Bhavana, M. (2025, February). Autonomous Vehicle Navigation Systems: Machine Learning for Real-Time Traffic Prediction. In 2025 International Conference on Computational, Communication and Information Technology (ICCCIT) (pp. 809–813). IEEE.
- Akat, G.B.; Magare, B.K. Mixed Ligand Complex Formation of Copper (II) with Some Amino Acids and Metoprolol. Asian Journal of Organic & Medicinal Chemistry 2022. [Google Scholar]
- Praveen, R.V.S.; Raju, A.; Anjana, P.; Shibi, B. (2024, October). IoT and ML for Real-Time Vehicle Accident Detection Using Adaptive Random Forest. In 2024 Global Conference on Communications and Information Technologies (GCCIT) (pp. 1–5). IEEE.
- Sivakumar, S.; Prakash, R.; Srividhya, S.; Vikram, A.V. A novel analytical evaluation of the laboratory-measured mechanical properties of lightweight concrete. Structural engineering and mechanics: An international journal 2023, 87, 221–229. [Google Scholar]
- Akat, G.B. EFFECT OF ATOMIC NUMBER AND MASS ATTENUATION COEFFICIENT IN Ni-Mn FERRITE SYSTEM. MATERIAL SCIENCE 2021, 20. [Google Scholar]
- Farooq, S.M.; Karukula, N.R.; Kumar, J.D.S. A Study on Cryptographic Algorithm and Key Identification Using Genetic Algorithm for Parallel Architectures. International Advanced Research Journal in Science, Engineering and Technology ICRAESIT 2.
- Dehankar, S.P.; Dehankar, P.B. Experimental studies using different solvents to extract butter from Garcinia Indica Choisy seeds. International Journal of New Technologies in Science and Engineering 2018, 5, 113–117. [Google Scholar]
- Rahman, Z.; Mohan, A.; Priya, S. Electrokinetic remediation: An innovation for heavy metal contamination in the soil environment. Materials Today: Proceedings 2021, 37, 2730–2734. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2026 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




