Submitted:
13 October 2025
Posted:
14 October 2025
Read the latest preprint version here
Abstract
Keywords:
1. Introduction
2. Background
2.1. Digital Twins: Concepts, Architectures, and Connectivity Challenges
2.2. Cybersecurity and Threat Detection in IIoT/OT Environments
2.3. Intrusion Detection in the Physical–Virtual Communication of Digital Twins
2.4. Emerging Cyber Threats and Their Impacts
2.5. Literature Gaps and Proposed Contribution
- Architectures with reactive security: most architectural models treat security as an adjacent layer rather than as an intrinsic design principle. There is a lack of proposals for architectures conceived from the outset to facilitate intrusion detection within communication flows, while accounting for the performance constraints of IIoT.
- Focus on complex high-level methods: predominant detection strategies rely on computationally intensive methods (e.g., deep learning, federated learning, blockchain) or on system-level behavioral analysis, while neglecting fundamental, low-cost communication channel metrics.
- Lack of throughput-focused detection: specifically, the exploration of data throughput as a primary indicator for detecting a wide range of attacks—from service disruptions to subtle manipulations—remains notably underexplored in the Digital Twin literature.
- Limited validation against emerging threats: there is a pressing need for experimental validation of detection strategies capable of operating in real time and maintaining DT resilience under sophisticated stealthy attacks that target data integrity rather than simply causing denial of service.
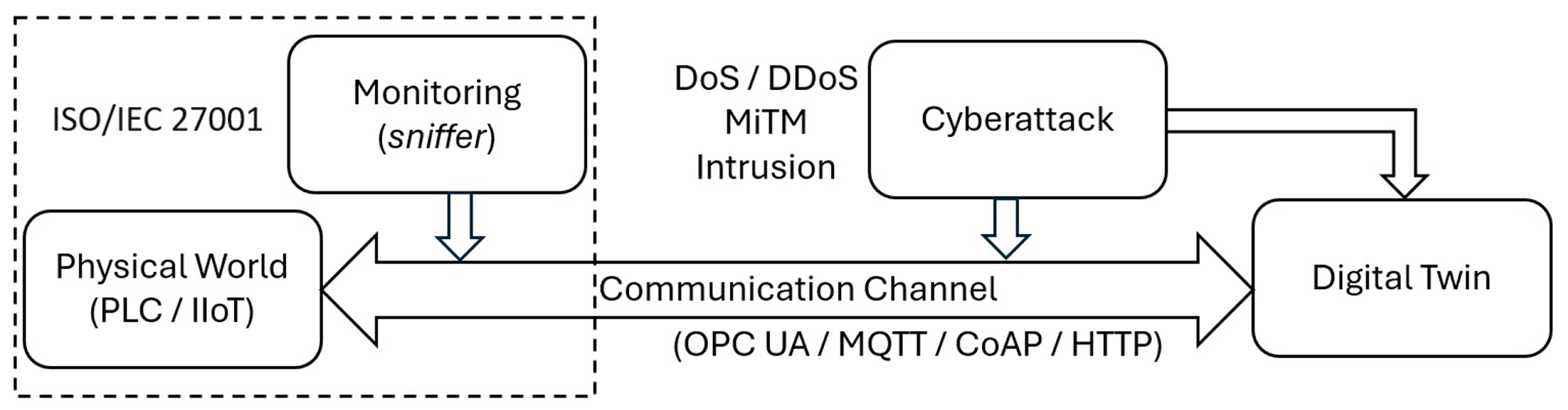
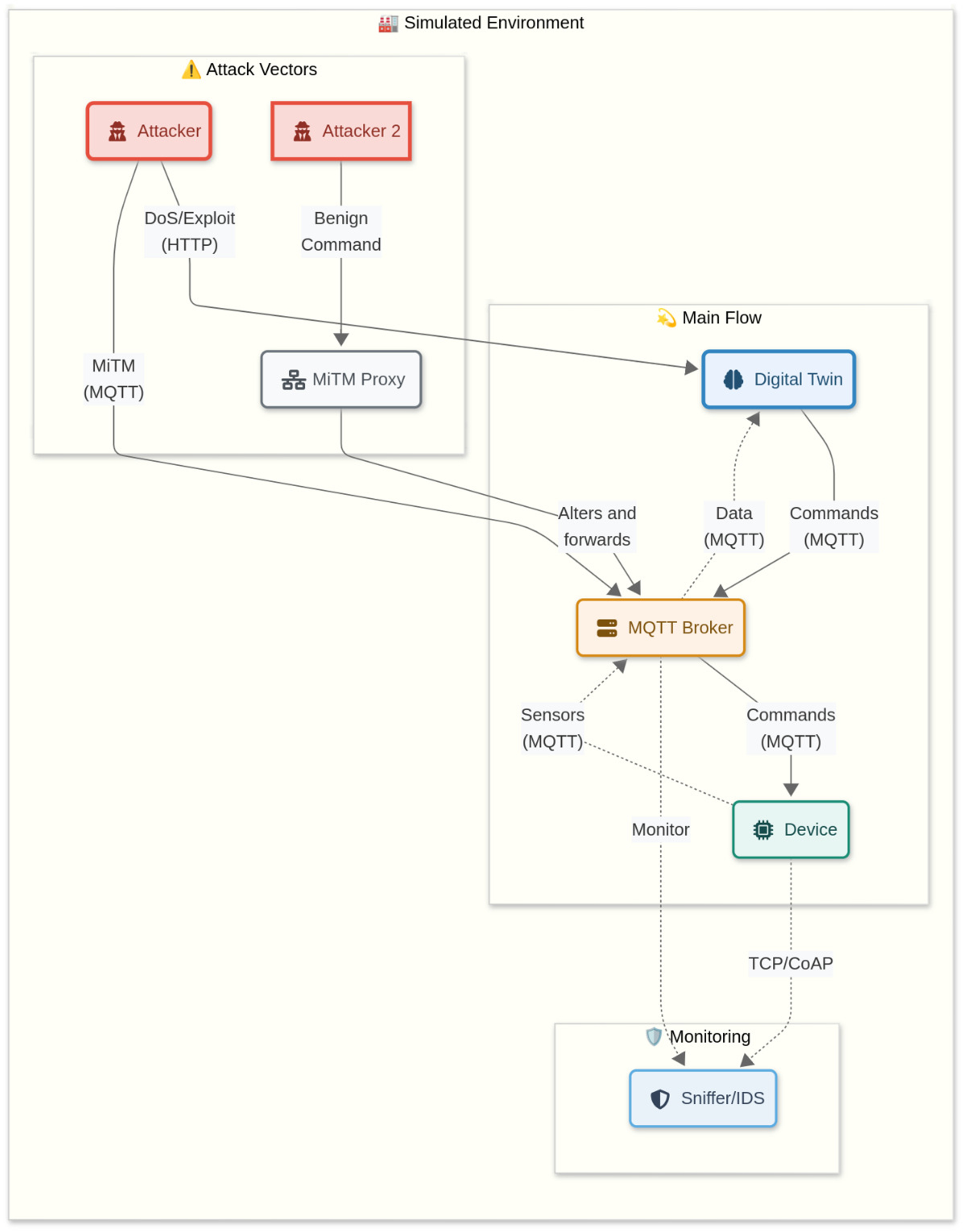
3. Materials and Methods (Methodology)
- Simulated physical device containers: These containers emulate the behavior of Programmable Logic Controllers (PLC) and Industrial Internet of Things (IIoT) devices.
- Digital twin container: This container hosts the virtual representation of the physical devices and is implemented as a system capable of receiving, processing, and storing data across various protocols.
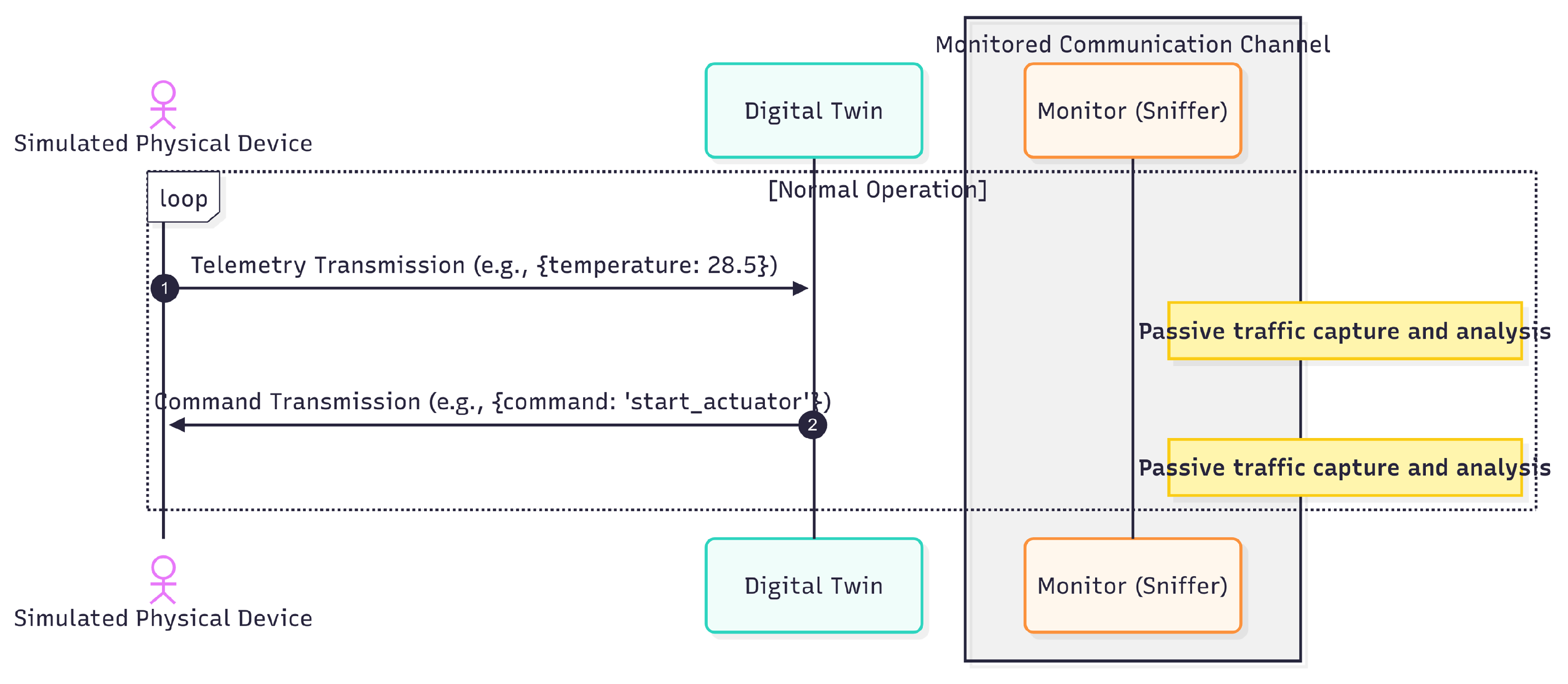
- Monitoring container (Sniffer): Operating as a dedicated component, this container is responsible for capturing and analyzing network traffic without interfering with the primary data flow.
3.1. Scenario Simulation
- Loss of connectivity: Simulation of temporary and permanent interruptions in the communication of specific devices or in the connection with the Digital Twin.
- Network latency: Introduction of variable delays in the network to observe the effect on response time and data transfer rate.
- Transmission errors: Simulation of packet transmission errors to induce retransmissions and observe the consequent changes in the data rate, mimicking potential data corruption.
- Bandwidth limitation: Introduction of network bottlenecks to reduce data transmission capacity and simulate congestion conditions.
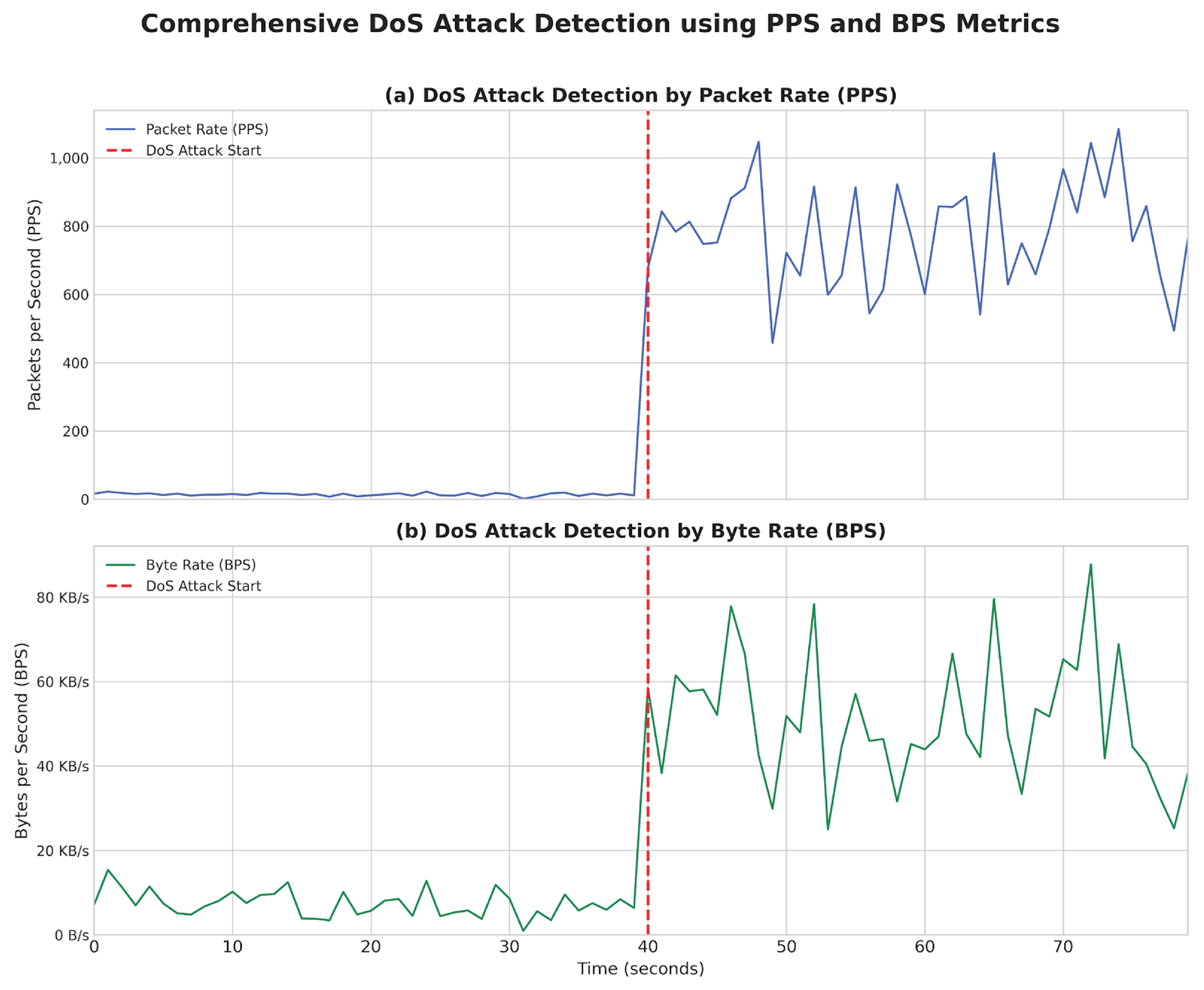
- Denial of Service (DoS) and Distributed Denial of Service (DDoS): These attacks aim to make the system unavailable by overloading the communication resources or the Digital Twin itself with an excessive volume of requests or malicious traffic. Different methods and tools were explored within the Docker environment to generate high network traffic towards the targets.
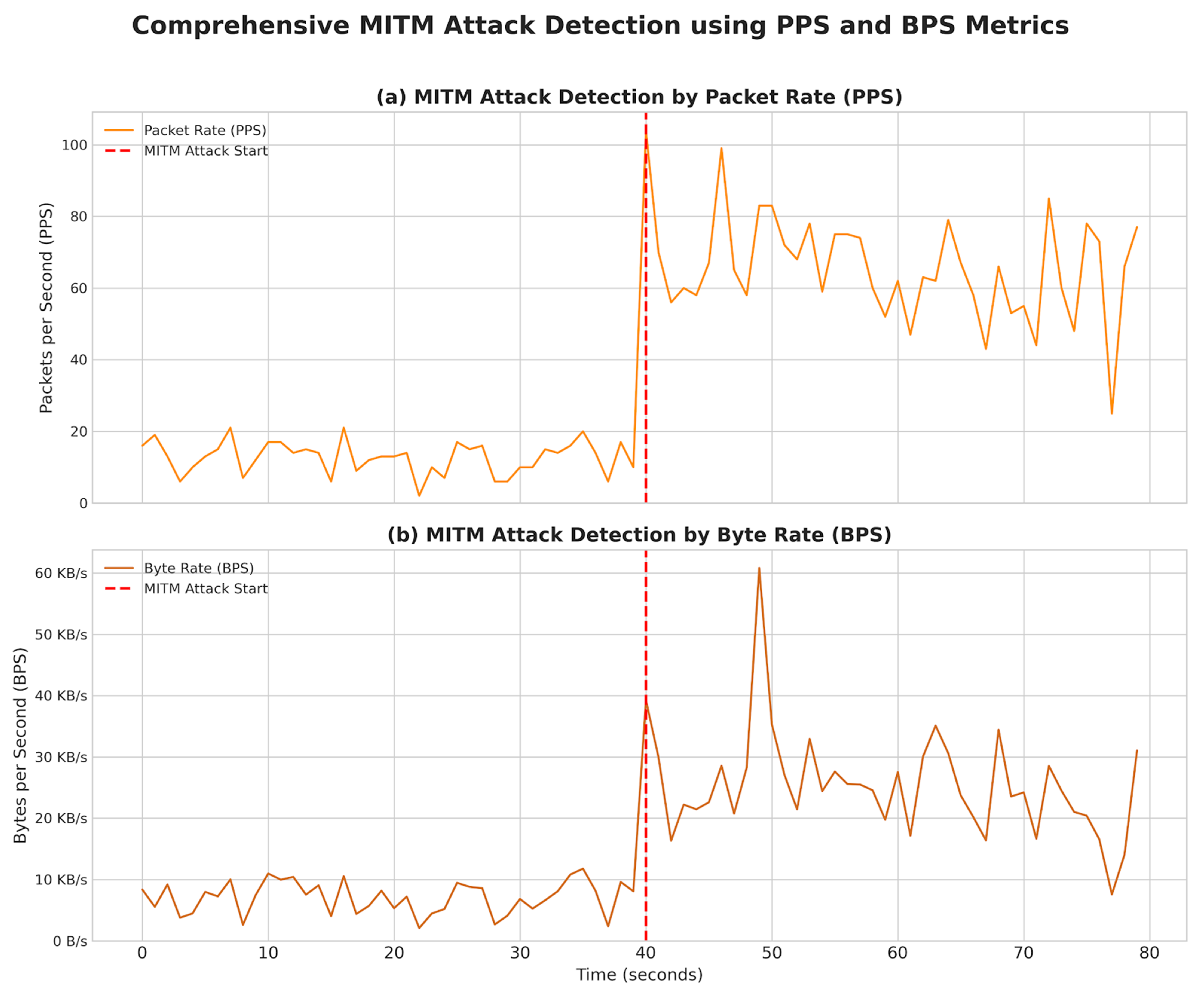
- Man-in-the-Middle (MiTM): This attack aims to intercept the communication between the physical devices and the Digital Twin, with the potential to read or modify data in transit. Various tools and network configurations in the Docker environment were used to simulate an attacker positioning itself at the communication layer to intercept traffic.
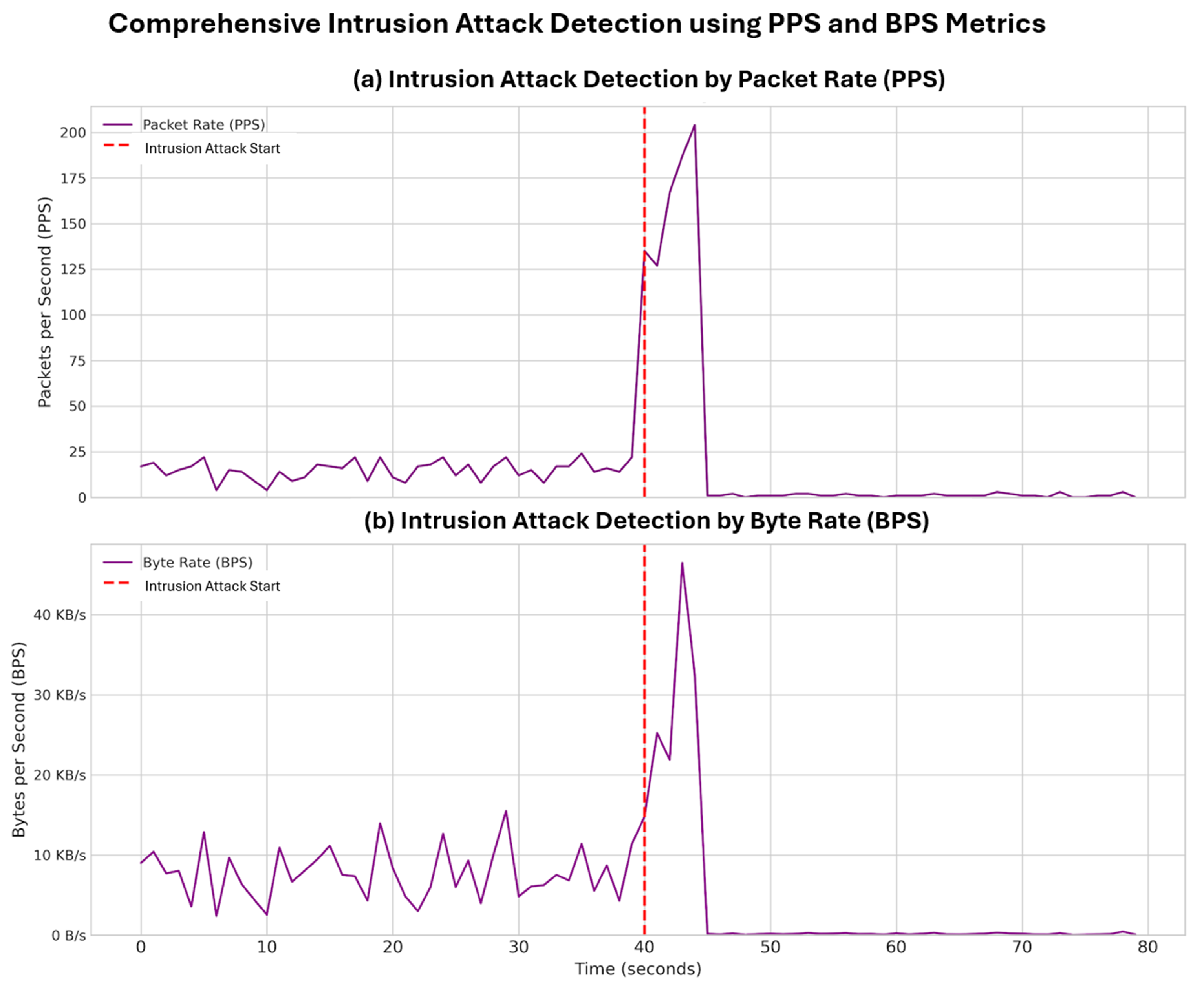
- Intrusion and Asset Compromise: This attack targets vulnerabilities to gain unauthorized access to the Digital Twin, sending malicious commands (e.g., shutting down sensors) to the physical asset. This scenario simulates targeted sabotage with the objective of disrupting physical operations through manipulation of digital control.
3.2. Data Collection and Analysis
4. Results and Discussion
4.1. Results
4.2. Discussion
5. Conclusions
Data Availability Statement
Acknowledgments
Abbreviations
| DT | Digital Twin |
| DTs | Digital Twins |
| IIoT | Industrial Internet of Things |
| OT | Operational Technology |
| DoS | Denial-of-Service |
| MiTM | Man-in-the-Middle |
| PPS | Packets Per Second |
| BPS | Bytes Per Second |
| SIEM | Security Information and Event Management |
| APT | Advanced Persistent Threat |
| IDS | Intrusion Detection System |
| CIA | Confidentiality, Integrity, and Availability |
| PLC | Programmable Logic Controller |
References
- Grieve, M. W. Digital Twin: Manufacturing Excellence through Virtual Prototyping; University of Michigan, 2003; White Paper.
- Tao, F.; Cheng, J.; Qi, Q.; Zhang, M. Digital twin-driven product design, manufacturing and service with big data. Int. J. Adv. Manuf. Technol. 2018, 94, 1509–1520. [Google Scholar] [CrossRef]
- Botín-Sanabria, D.M.; García-Méndez, L.C.; Gaviria-López, C.A.; Muñoz-Guerrero, J.D.; Arango-Serna, M. Digital twins for smart cities: a review of current applications and future trends. Sustain. Cities Soc. 2024, 109, 105652. [Google Scholar] [CrossRef]
- Hosamo, H.; Al-Hussein, M.; Almashaqbeh, A.; Al-Kasasbeh, B. A Review of the Digital Twin Technology in the AEC-FM Industry. Adv. Civ. Eng. 2022, 2022, 2185170. [Google Scholar] [CrossRef]
- Al-Fawwaz, A.; Al-Qaralleh, A.; Al-Majali, A.; Qadan, M. A Comprehensive State-of-the-Art Review for Digital Twin: Cybersecurity Perspectives and Open Challenges. Sensors 2023, 23, 4635. [Google Scholar] [CrossRef]
- Bhushan, M.; Kumar, A.; Kumar, A.; Prakash, S. Advancing Security with Digital Twins: A Comprehensive Survey. arXiv 2025, arXiv:2505.17310. [Google Scholar] [CrossRef]
- Liu, C.; Ren, Y.; Wang, H.; Yu, G.; Xu, X.; Su, B. Federated Learning for Intrusion Detection in Industrial IoT and Digital Twin. IEEE Trans. Ind. Informatics 2024, 20, 9205–9215. [Google Scholar] [CrossRef]
- Liu, W.; Li, D.; Guo, Q.; Zhang, H.; Lv, Y.; Chen, J. Blockchain-Enabled Digital Twin for Secure and Resilient Industrial Systems. IEEE Trans. Ind. Informatics 2024, 20, 3841–3852. [Google Scholar] [CrossRef]
- Belay, M.A.; Rasheed, A.; Rossi, P.S. Digital Twin Knowledge Distillation for Federated Semi-Supervised Industrial IoT DDoS Detection. IEEE Internet Things J. 2025. [Google Scholar] [CrossRef]
- Zainudin, A.; Paramartha Putra, M.A.; Alief, R.N.; Kim, D.S.; Lee, J.M. Blockchain-aided Collaborative Threat Detection for Securing Digital Twin-based IIoT Networks. In Proceedings of the ICC 2024 - IEEE International Conference on Communications, Denver, CO, USA, 9–13 June 2024; pp. 4656–4661. [Google Scholar]
- Li, S.; Zhang, Z.; Shi, H.; Wang, X. A Digital Twin Anomaly Detection Method Based on a Spatiotemporal Fusion Graph Convolutional Network. Sensors 2024, 24, 1253. [Google Scholar] [CrossRef]
- Pan, J.; Chen, J.; Su, Z. Digital Twin-Based Anomaly Detection in Industrial Control Systems. IEEE Trans. Ind. Informatics 2023, 19, 11571–11580. [Google Scholar] [CrossRef]
- Yu, G.; Zhang, J.; Cao, Y.; Yu, H.; Zhang, Y. A Survey on Digital Twin-Empowered Anomaly Detection in Cyber-Physical Systems. IEEE/CAA J. Autom. Sin. 2024, 11, 833–852. [Google Scholar] [CrossRef]
- Wang, L.; Liu, C.; Li, Y.; Li, B. Digital Twin-Based Collaborative Anomaly Detection for Industrial IoT. IEEE Internet Things J. 2023, 10, 11466–11477. [Google Scholar] [CrossRef]
- Koroniotis, N.; Moustafa, N.; Schiliro, F.; Gauravaram, P.; Janicke, H. A holistic review of cybersecurity and intrusion detection systems in securing smart cities: a survey and future directions. J. Netw. Comput. Appl. 2023, 213, 103607. [Google Scholar] [CrossRef]
- Xie, J.; Zuo, H.; Fu, S.; Liu, S. IoT and Digital Twin assisted Deep Reinforcement Learning for Cyber-Physical Industrial Control Systems Security. IEEE Trans. Ind. Informatics 2023, 19, 11571–11580. [Google Scholar] [CrossRef]
- Zuo, H.; Xie, J.; Fu, S. Digital Twin-Driven Threat Detection for Industrial Control Systems via Dynamic Graph Learning. IEEE Trans. Ind. Cyber-Phys. Syst. 2024. [CrossRef]
- Liang, Z.; Tang, B.; Liu, Y.; Wang, S.; Chen, S. Hybrid Anomaly Detection for Industrial Control System Based on Digital Twin. IEEE Trans. Circuits Syst. II Express Briefs 2024, 71, 999–1003. [Google Scholar] [CrossRef]
- Wang, J.; Li, W.; Li, X.; Li, M. Digital Twin—A Review of the Evolution from Concept to Technology and Its Analytical Perspectives on Applications in Various Fields. Sensors 2024, 24, 5454. [Google Scholar] [CrossRef]
- Yang, Y.; Wang, H.; Li, M.; Liu, Z.; Zhang, C. Anomaly detection in industrial IoT based on digital twin and deep learning. Digit. Commun. Netw. 2023, 9, 1276–1286. [Google Scholar] [CrossRef]
- Li, H.; Ota, K.; Dong, M. Digital Twin-Based Intrusion Detection for Industrial Cyber-Physical Systems. IEEE Netw. 2023, 37, 180–186. [Google Scholar] [CrossRef]
- Li, S.; Zhang, Z.; Shi, H.; Wang, X. A Digital Twin Anomaly Detection Method Based on a Spatiotemporal Fusion Graph Convolutional Network. Sensors 2024, 24, 1253. [Google Scholar] [CrossRef]
- Ma, R.; Labbe, A.; Malo, A.; G-B. de Lamotte, F. Digital twin for situational awareness in industrial cybersecurity: A review and a new concept. Comput. Ind. 2023, 148, 103901. [Google Scholar] [CrossRef]
- Puerto-Santana, F.; Puerto-Santana, E.; O’Leary, P.; Gutierrez-Estevez, M. A Digital Twin with HMMs for Industrial Anomaly Detection. Sensors 2022, 22, 7436. [Google Scholar] [CrossRef]
- Shukla, S.; L-F. Pau, L.F.; Balasubramaniam, S.; Mustafa, M.A. Digital Twin-Based Anomaly Prediction in Industrial Control Systems. In Proceedings of the 2021 IEEE 20th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Shenyang, China, 29–31 October 2021; pp. 836–845.
- Abolfazi, S.A.; Tabaee, T.; G-B. de Lamotte, F. Digital-Twin-Enabled Intrusion Detection System for Industrial Control Systems: A GAN-Based Implementation. Sensors 2023, 23, 3209. [Google Scholar] [CrossRef]
- Gnanaprakasam, A.; Anand, S.J.S.; Balasubramanian, S.; Akila, D. A trust management model using digital twin and blockchain for industrial IoT networks. Peer-to-Peer Netw. Appl. 2024, 17, 118. [Google Scholar] [CrossRef]
- Sharma, A.; Singh, H. Digital Twin Empowered Autonomic Security Management in Industrial IoT Network. IEEE Internet Things J. 2024. [Google Scholar] [CrossRef]
- Niyonzuima, R.; Al-Maqbali, A.; Al-Bahri, Y.; Al-Barami, B.; Al-Hinai, M. Digital twin: a unified definition, issues, challenges, and opportunities. J. Cyber Secur. Data Prot. 2024, 1, 1–15. [Google Scholar]
- Zhang, S.; Yang, J.; Hu, Z.; Yan, S.; Liu, Y. A systematic review of the digital twin technology in buildings, landscape and urban environment from 2018 to 2024. Buildings 2024, 14, 3475. [Google Scholar] [CrossRef]
- Niyonzuima, R.; Al-Maqbali, A.; Al-Bahri, Y.; Al-Barami, B.; Al-Hinai, M. Digital twin: a unified definition, issues, challenges, and opportunities. J. Cyber Secur. Data Prot. 2024, 1, 1–15. [Google Scholar]
- National Institute of Standards and Technology (NIST). Security and trust considerations for digital twin technology. NISTIR 8356 2025. [Google Scholar] [CrossRef]
- Digital Twin Consortium. Understanding DTC’s digital twin platform stack architectural framework. Technical Report, November 2023. Available online: https://www.digitaltwinconsortium.org/2023/11/understanding-dtcs-digital-twin-platform-stack-architectural-framework/.
- Orange, J. Network digital twin: concepts and reference architecture. IETF Internet-Draft draft-irtf-nmrg-network-digital-twin-arch-10 2025. Expires August 31, 2025.
- Tange, K.; De Donno, M.; Fafoutis, X.; Dragoni, N. A systematic survey of industrial internet of things security: requirements and fog computing opportunities. IEEE Access 2020, 8, 123456–123478. [Google Scholar] [CrossRef]
- Herath, J.D.; Yan, G. Real-Time Evasion Attacks against Deep Learning-Based Anomaly Detection from Distributed System Logs. In Proceedings of the Eleventh ACM Conference on Data and Application Security and Privacy, Virtual Event, USA, 26–28 April 2021; pp. 29–40. [Google Scholar]
- Rasheed, A.; Javed, A. R.; Habib, M. F.; Abbas, S.; Fatima, T.; Farooq, M. S. Privacy and security challenges of the digital twin: systematic literature review. J. Univers. Comput. Sci. 2024, 30, 1782–1806. [Google Scholar] [CrossRef]
- International Organization for Standardization. ISO/IEC 27001:2022 - Information security, cybersecurity and privacy protection — Information security management systems — Requirements. ISO, 2022.
| Reference | System Type |
Security Focus |
Detection | Monitor. Metric |
Technique | Attacks | Validation |
|---|---|---|---|---|---|---|---|
| [9] | IIoT | D, P | AN | DR, SC | FL, DL | DDoS | Simulation |
| [7] | Industrial | I, R, A | PR | SC, NF | BC | DI, FR | Theoretical |
| [10] | IIoT | D, I | CA | NF | BC, ML | GA | Simulation |
| [11] | ICS | D | AN | SC | DT, ML | GA | Simulation |
| [12] | ICS | D | AN(S) | SC | DT, Sim. | GA | Simulation |
| [13] | CPS | D | AN | SC | ML, DT | GA | Simulation |
| [8] | IIoT | D, P, R | CA | NF, SC | FL | IN | Simulation |
| [14] | CPS | D | AN(C) | NF | DT | GA | Simulation |
| [15] | IIoT | D, I | AD | NF | Testbed | DA | Testbed |
| [16] | CPS | D | TD | SC | DRL, IoT, DT | TCPS | Simulation |
| [17] | ICS | D | AN | SC | DT, DL | GA | Simulation |
| [18] | CPS | D, R | HY(A) | SC, NF | DT, Hybrid | GA | Simulation |
| [19] | IIoT | D | AN(B) | SC | DT, ML | GA | Simulation |
| [20] | IIoT | D | AN | SC | DT, ML | GA | Simulation |
| [21] | ICS | D | IN(A) | SC | DT, ML | IN | Simulation |
| [22] | ICS | D | AN(D) | SC | DT, ML | CA | Simulation |
| [23] | ICS | C, I, D | SA | SC, NF | DT, Data | GT | Simulation |
| [24] | Industrial | P | AN | SC | HMMs | FA | Dataset |
| [25] | Industrial | A, I | PD | SC | BC, AI | FR | Simulation |
| [26] | ICS | D | FD | SC | DT | CA | Simulation |
| [27] | IIoT | C, A | TM | SC | DT, BC | MB | Simulation |
| [28] | Industrial | D | AN(SH) | SC | DT, ML | GT | Simulation |
| Attack Type | Period | Mean PPS | Std. Dev. PPS | Mean BPS | Std. Dev. BPS |
|---|---|---|---|---|---|
| DoS | Normal | 13.75 | 4.27 | 7309.92 | 3082.47 |
| DoS | Attack | 779.30 | 156.03 | 50904.75 | 15049.37 |
| MiTM | Normal | 12.70 | 4.59 | 7085.28 | 2656.04 |
| MiTM | Attack | 65.68 | 14.97 | 25445.80 | 8674.89 |
| Intrusion | Normal | 14.95 | 5.08 | 7721.48 | 3213.76 |
| Intrusion | Attack | 21.52 | 55.55 | 3664.50 | 10141.59 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





