3.1. Development of a Model and Methodology for Assessing the Awareness of the Intruder and Symmetrical Models and Methods for Assessing the Intelligence Security of the Elements of the DIS
To achieve the purpose of the study, the authors developed a model and methodology for assessing the awareness of the violator, designed to mathematically substantiate the required amount and semantic composition of reconnaissance database for conducting the stages of CCA, the use of certain types of SCA, tactics and techniques for their implementation.
In the study, to model the awareness of the violator at different stages of the CCA and determine the available types of SCA at its stages, a DIS with average structural-functional indicators was adopted, which has a basic set of information security tools and correctly formulated security policies.
To form the model, the analytical methods of the
“Black Box
”,
“Gray box
” and
“White box
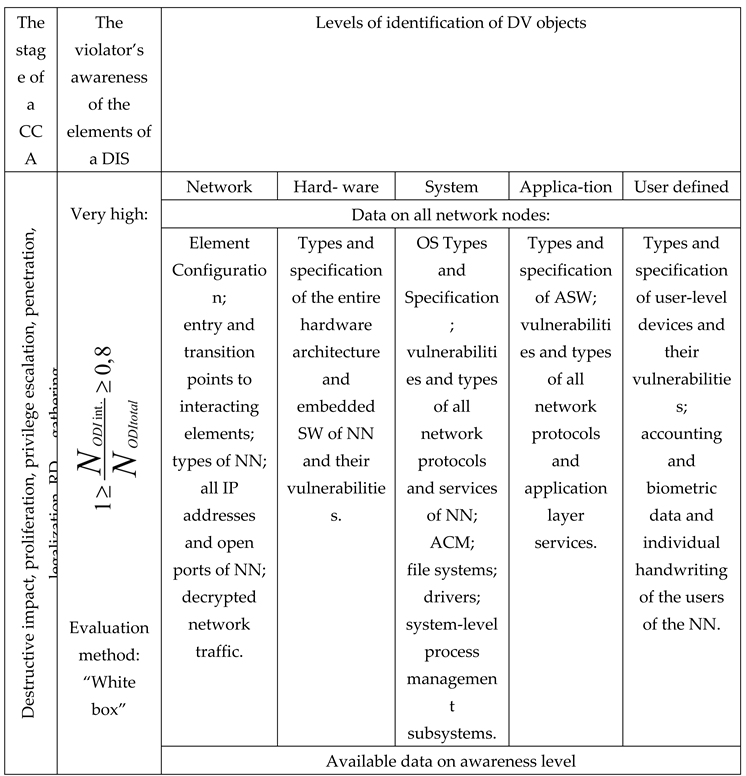
” were applied, the levels of identification of the objects of the DI, a system of structural-functional indicators and criteria for assessing the awareness of the violator about the elements of the DIS and their components, the typical structure of the CCA, as well as a scale for quantitative and qualitative assessment of the levels of awareness of the violator. This conceptual model is presented in
Table 2.
Let’s move on to its description. In general, the modeling process boils down to the following actions. The model is divided into two clusters – computational and informational.
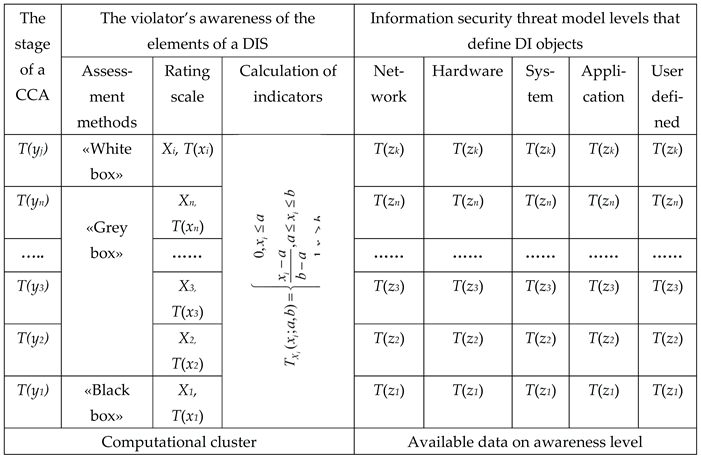
The calculation cluster displays the stages CCA (yj) and T(yj) – the linguistic terms of their description. For each of these stages, methods of investigation (testing) of the elements of the DIS are selected for the possibility of “DI “on them from the violator. These are the “Black” or “Gray Box” or “White Box” methods. In the model, in relation to the previously discussed stages of the CCA, a scale of awareness of the violator about the structural-functional indicators of the attacked elements is formed DIS. This scale displays T(xi) – linguistic terms for assessing awareness and numerical values of indicator Xi, reflecting the levels of awareness of the offender. The calculation of these characteristics is carried out using a preference function based on the theory of fuzzy sets.
The information cluster displays the RD received by the violator, according to the objects of the DI (the target objects of the SCA at the stages of the CCA) at various levels of their definition, which in the model are represented as T(zk) – linguistic terms for describing the target objects of the CCA at the kth level of the awareness scale of the violator.
Let us consider in more detail the methodology of formation and functioning of this model. Let
’s start with the foundation of its structure. To form the lower tier of the model, the
“Black Box
” system analysis method was used [
13]. The method under consideration consists in the fact that the researcher, in this case the violator, is not aware of either the structural or functional indicators of the system under study. He knows the entry point into the system, where certain data or signals can be sent, and the exit point through which the intruder receives data transformed by the internal elements of the system, which can be used to determine a certain part of the structural and functional indicators of the system under study. Such a state of awareness of the intruder about the attacked system will correspond to the stage of conducting reconnaissance from outside the network perimeter.
Next, it is necessary to determine the upper tier of this model, which is conventionally designated as a
“White Box
” in accordance with the applied testing methodology [
14].
When using the “White Box” method, the violator knows the full set of structural and functional indicators of the system under study. These are many network protocols and services at the system and application levels, many vulnerabilities of all protocols and services at the system and application levels, many hardware architectures and embedded software, many configurations, and IP addresses.
Testing of the system, the structural and functional characteristics of which are partially known to the violator, will be carried out using the
“Gray box
” method [
15]. The proposed methodology includes a step-by-step increase in this level. Each of the stages is characterized by different possibilities.
We will divide the awareness scale using the tools of fuzzy logic, linguistic terms [
16,
17,
18] (
Table 2).
Linguistic terms are the values of a linguistic variable that represent words or sentences in a natural or formal language that serve as an elementary characteristic (description) of information security events (incidents) [
16].
To form the awareness scale, we will introduce the following notation:
X – invader’s awareness Х ϵ [0;1];
Xi – invader’s awareness levels Xi ϵ {[0;0,2], [0,2;0,4], [0,4;0,6], [0,6;0,8], [0,8;1]};
хi – the numerical value of the invader’s awareness at a certain level;
yj – stages of CCA;
zk – possible DI target objects at the kth level of their definition;
T(xi) – linguistic terms of awareness assessment;
T(yj) – linguistic terms of describing the stages of CCA;
T(zk) – linguistic terms of describing target objects of the CCA.
Based on the data presented in
Table 2, it becomes necessary to determine whether a certain category of awareness belongs to a specific level of the offender
’s awareness scale according to the elements of DIS. For this purpose, the mathematical apparatus of membership functions of fuzzy sets is used.
The membership functions of fuzzy sets allow us to describe the degree to which a certain category of awareness belongs to a specific level of the awareness scale, in the range from 0 to 1. This makes it possible to more flexibly analyze and classify the level of knowledge of the violator regarding the elements of the DIS, taking into account their probabilistic nature [
18].
The awareness scale is an ordered set of levels, each of which characterizes a certain set of arrays of RD received by the intruder about objects of the DI elements of the DIS. The content of the received RD allows us to determine the available SCA and apply tactics and techniques for their implementation, which are characteristic of the corresponding stage of the CCA.
Each level of awareness is described by the membership function, which sets the degree to which a specific value of the awareness indicator corresponds to this level.
For each level of awareness, the membership function T(xi) is set, where (xi) is the numerical value of the degree of awareness.
The awareness level membership function T(xi) takes values in the range [0; 1]. It can take extreme values: (x
i)=1) – full correspondence of the degree of awareness (х
i) to this level and и (T(x
i)=0) – absence of belonging of the degree of awareness (х
i) to this level. Values between 0 and 1 reflect a partial degree of compliance with any kind of level of awareness.
Table 2.
Splitting the awareness scale using linguistic terms.
Table 2.
Splitting the awareness scale using linguistic terms.
The scale of awareness levels
Xi
|
[0;0,2] |
[0,2;0,4] |
[0,4;0,6] |
[0,6;0,8] |
[0,8;1] |
| Linguistic terms for assessing awareness T(xi) |
VL |
L |
M |
H |
VH |
| Linguistic terms describing the stages of CCA T(yj) |
Reconnais-sance |
Recon- naissance, login, legaliza- tion |
Reconnaissance, login, legalization, privilege enhancement |
Reconnaissance, login, legalization, privilege enhancement, dissemination |
Reconnaissance, login, legalization, privilege enhancement, DI |
| Linguistic terms for describing CCA targets T(zk). |
Externally accessible network objects of the attacked DIS element |
The attacked node of the DIS element network |
DI objects of the attacked DIS element, available according to the access control model |
DI objects of the attacked DIS element, accessible nodes of the network of interacting elements DIS |
Objects DI of the attacked element and interacting elements DIS |
Let’s represent this function as an expression:
,
where (a, b) is the range of a specific level of the awareness scale.
Using this method, we will obtain the relative values of xi for each diapason of the offender’s awareness scale, which ranges from 0 to 1.
As noted earlier, the awareness scale includes five levels: “very low” (VL), “low” (L), “medium” (M), “high” (H), “very high” (VH).
For a “very low” (VL) level of awareness , which characterizes minimal knowledge about the system, the range is set [0; 0,2] and the following function of this level is formed:
This function has the following values:
if (х1 (хi;0,0.2) = 0, then the intruder does not have the necessary RD to apply attack scenarios available for the VL level;
if Тх1 (хi;0,0.2)= 1, then RD is sufficient to apply all attack scenarios available at the VL level, and the violator also has the opportunity to switch to a low awareness level (L) and expand intelligence capabilities;
if Тх1 (хi;0,0.2) = , the RD were not fully received and the intruder may conduct additional reconnaissance and attacks aimed at obtaining the missing RD necessary to move to the next level of awareness.
Next, let’s consider the “Low” level of awareness, at which the intruder has basic RD about the structure and functionality of the system and the attacked object DI. For this level Х2 the values of the indicator хi are set in the range [0,2; 0,4] and the following function is formed:
Based on this function, the following conditions are formed:
if Тх1 (хi;0.2,0.4) = 0, then the violator does not have the necessary RD to move to this level of awareness;
if ТХ1 (хi;0.2,0.4) = 1, then the available RD are sufficient to apply all types of attacks available at this level of awareness, move to the next level and conduct further reconnaissance with new features;
if Т(х1 (хi;0.2,0.4) = , the RD has not been fully obtained and is insufficient for the use of all types of attacks available at this level of awareness, and the use of additional intelligence tools is necessary.
At the awareness level, the “Medium” intruder has sufficient knowledge to analyze the system structure, configuration, and characteristics of the available objects DI of attacked system element. The values of the indicator хi for this level Х3 are set in the range [0,4; 0,6], on the basis of which the following function is formed:
Based on the above function, it follows that:
the intruder does not have RD corresponding to this level, and also cannot carry out possible attacks available for this level if the value of the function х3 is 0, that is, Т(х1 (хi;0.4,0.6) = 0;
if Т(х1 (хi;0.4,0.6)= , then the intruder does not have the full volume of RD arrays that corresponds to this level of awareness and additional means of reconnaissance are needed to achieve it;
the violator has the full amount of information available at this level, if Т(х1 (хi;0.4,0.6) = 1, and also moves to the next level of awareness and can take advantage of new opportunities for intelligence and conducting a SCA.
RD corresponding to the “High” awareness level allow the intruder to determine the structure of all elements of the DIS, as well as the characteristics of all objects DI in the attacked DIS element. The values of the indicator хi for this level X4 will correspond to the range [0,6; 0,8]. Thus, the membership function is formed:
The following gradations are allocated for this membership function:
the expression Т(х1 (хi;0.6.2,0.8) = 0 means that the minimum RD have been obtained to achieve the “High” awareness level, but not to take its capabilities;
Т(х1 (хi;0.6,0.8 )= corresponds to incomplete acquisition of RD characteristic of a given level of awareness, according to which not all types of SCA of the “High” awareness level will be available and it is necessary to continue collecting RD;
Т(х1 (хi;0.6.2,0.8) = 1 corresponds to the violator obtaining all possible RD at a given level in terms of the characteristics of the available objects DI of DIS elements, as well as the structure and functionality of the DIS elements, the possibility of using all types of SCA at this level and moving to the next level of awareness.
The fifth level of awareness is “Very high.” At this level, the intruder receives data on the characteristics of all DI objects of all DIS elements and full access to them. The values of the indicator хi for this level Х5 are set in the range [0,8; 1] and the following membership function is formed:
The following conditions are formed for the membership function of this level:
if Т(х1 (хi;0.8.,1) = 0, the intruder has the necessary RD to move to this level of awareness, but they are not enough to carry out attacks available at this level;
if Т(х1 (хi;0.8.,1) = 1, then RD is sufficient to apply all types of available attacks for a given level;
if Т(х1 (хi;0.8,1) = , then in order to achieve the possibilities for conducting all types of SCA available for this level, additional RD is required.
Collectively, the ranges of changes in the values of indicator presented above represent a scale of awareness of the violator.
This model and methodology can be symmetrically used to assess the intelligence security (IS) of DIS elements. For this purpose, we will introduce hi, which is an indicator of intelligence security assessment, and Hi, which reflects the range of its values for the intelligence security assessment scale. Their numerical values will be calculated using the formula:
The linguistic terms used in the intelligence security model are the same as in the intruder awareness assessment model. Consequently, the scale for assessing intelligence security will be inversely symmetrical in terms of the values of the range of the scale for assessing the intruder’s awareness. Their ratios are shown in
Table 3.
Thus, this methodology substantiates the dimension of the awareness scale, substantiates the type of membership function of a fuzzy set, and provides a decoding of linguistic terms of various origins. In addition, with the help of the awareness membership function, additional information was obtained on the compliance of the RD content with a specific level of awareness. This technique also allows you to identify DI objects based on a specific level of awareness that the intruder can access and the list of SCA available for this level.
In addition, it is clarified that the violator, starting from the “Medium” awareness level, gets the opportunity to conduct reconnaissance within the DIS elements, and at the “High” and “Very high” awareness levels gets the opportunity to extend to the interacting DIS elements and conduct reconnaissance of their structural-functional characteristics. Thus, by applying in practice the models and techniques presented in this study, an information security specialist gets the opportunity for a priori dynamic assessment of changes in the intelligence security indicators of the DIS elements depending on the type of applied SCA and the stages of CCA.
3.2. Development of Experimental Models
In order to test the developed model and methodology, we will conduct an experiment, for which it is necessary to generate the initial data. The formation of initial data to assess the intruder’s awareness and intelligence security of DIS involves the collection and systematization of key information about the structural-functional characteristics of its elements and the vulnerabilities of DIS objects [
19].
As the initial data, consider the DIS, which consists of three elements: a local area networks, a data center, and a remote user. Each of the network elements consists of a certain number of switching equipment (SE) devices and network nodes (NN).
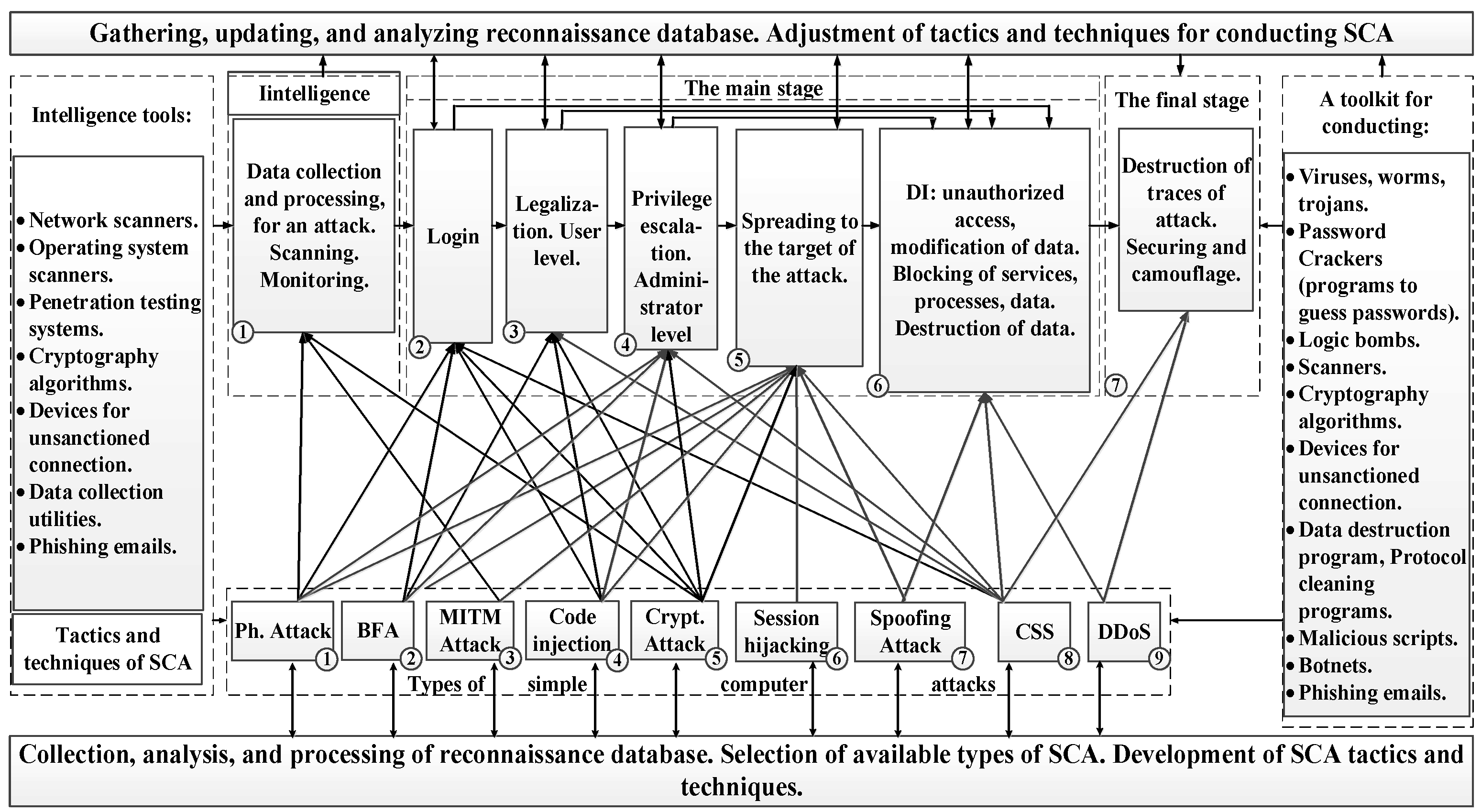
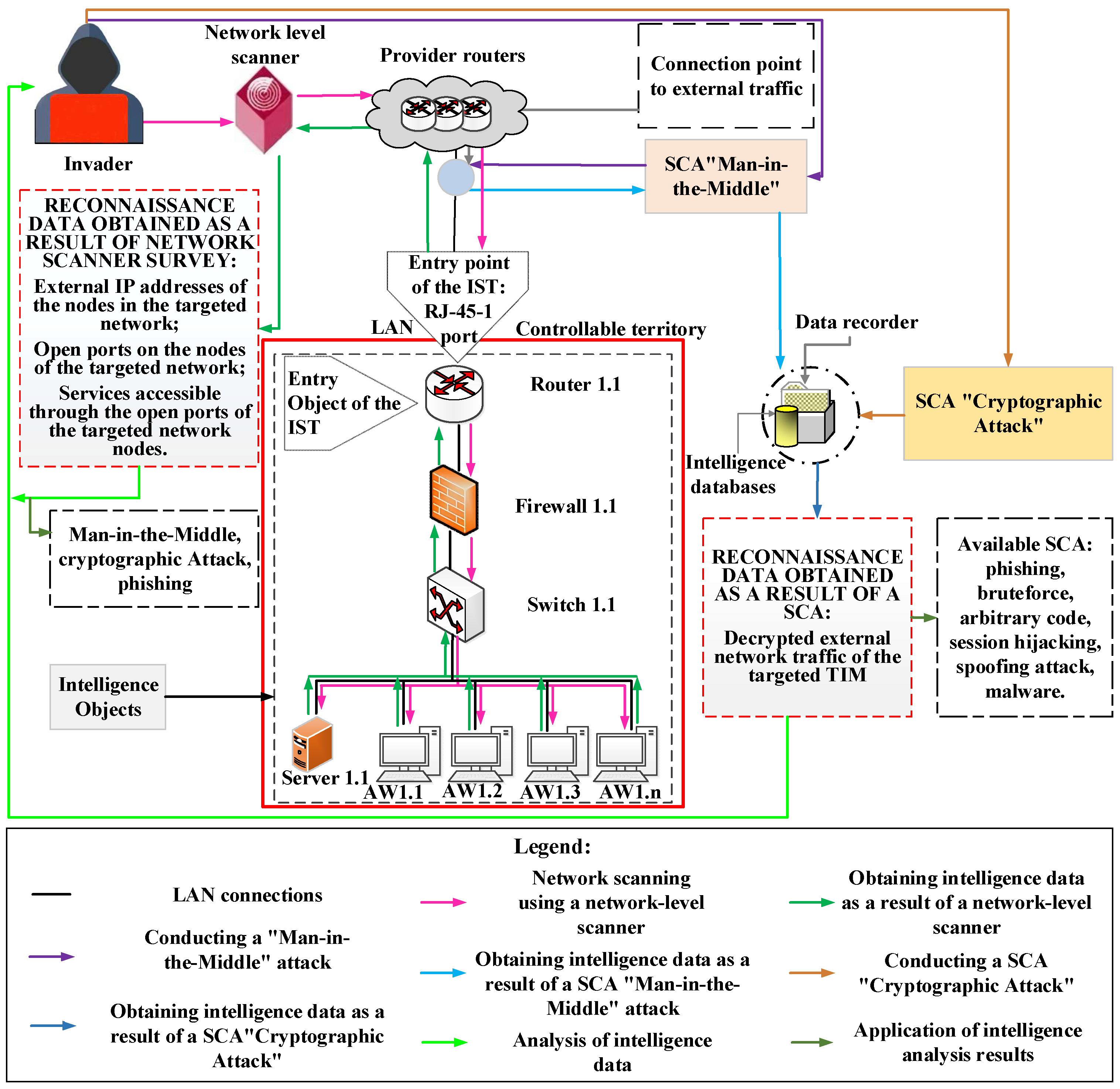
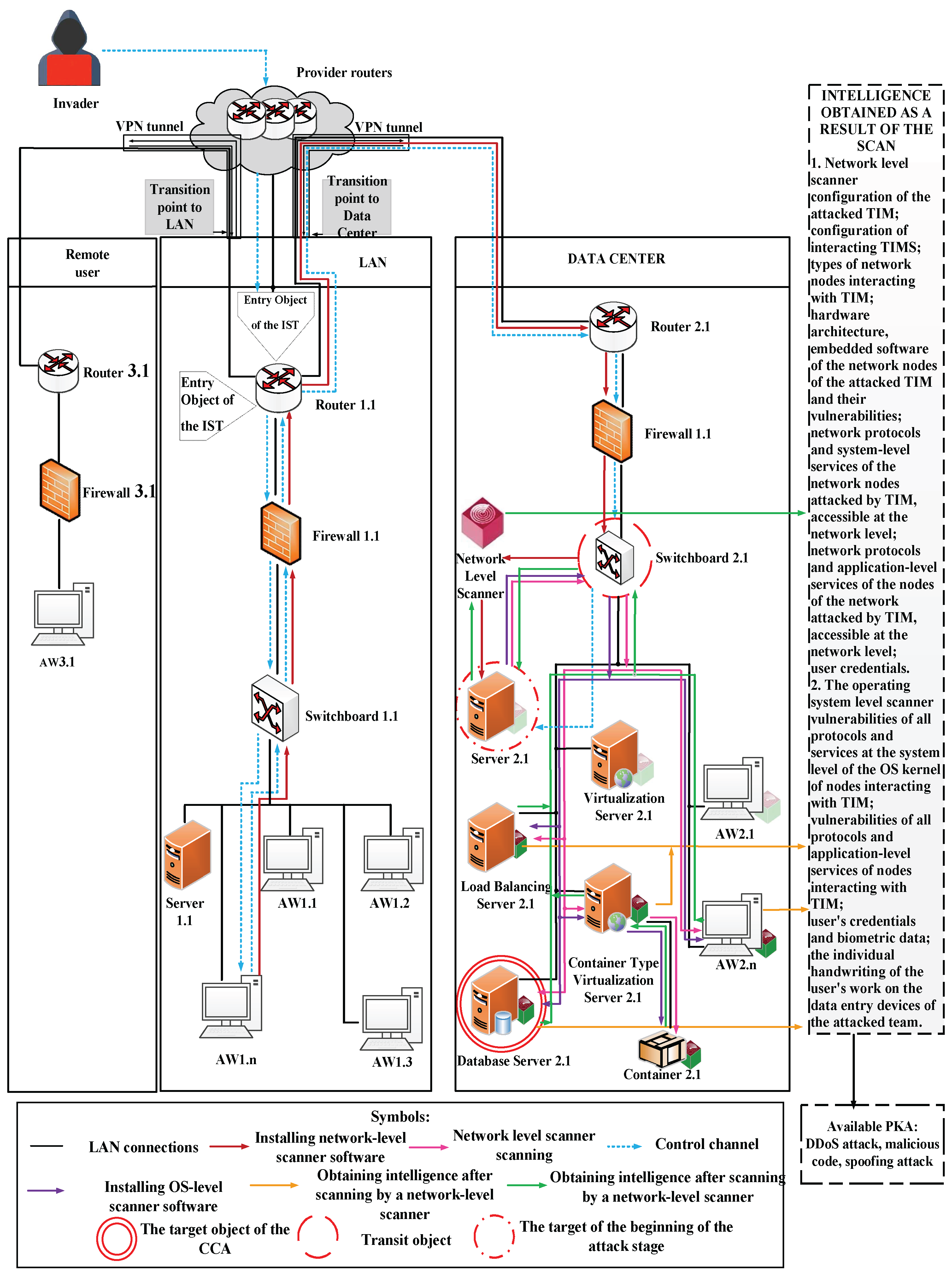
Figure 2 shows a model of active intelligence, which is carried out by an intruder from outside the perimeter of the network.
At the stage of collecting initial information about the attacked object, the attacker uses some tools to obtain information from outside the network perimeter. The main purpose of this stage is to collect RD necessary for penetration, implementation and legalization on one of the devices (NN or SE) of the attacked DIS element. To do this, the intruder uses a network-level scanner and certain types of SCA suitable for intelligence gathering.
The intruder connects a network-level scanner through the routers of the telecom operator to the entrance of the attacked element of the DIS and, as a result of scanning, receives data on the following objects of DI: IP addresses of external network nodes; open ports of network nodes; services accessible through open ports of network nodes.
If the Access Control Model (ACM) is configured correctly, services will be unavailable through open ports. Open ports will be those ports that provide network formation and intranet interaction. Based on the developed methodology, we assess the violator’s awareness of the elements of a DIS. Comparing the data obtained during this stage, it can be concluded that the RD obtained corresponds to a very low level of awareness. The results are shown in
Table 4.
In this case, the data obtained will not be enough to carry out an attack on the implementation and legalization of the network. Therefore, the violator, as a rule, uses SCA to obtain the data necessary to enter the network, anchoring, identify and authenticate on the network node as a legitimate user.
For example, such an attack is a Man-in-the-Middle attack. Its essence is as follows. The intruder, in some way, connects to the line between the attacked element of the DIS and the provider, gets access to external encrypted network traffic and records it creating an RD. Since external traffic is protected by encryption, the intruder uses another type of SCA “Cryptographic attack”. With the help of cryptographic algorithms, he can decrypt the received RD.
A phishing attack can also be used to obtain the RD necessary for the implementation and legalization.
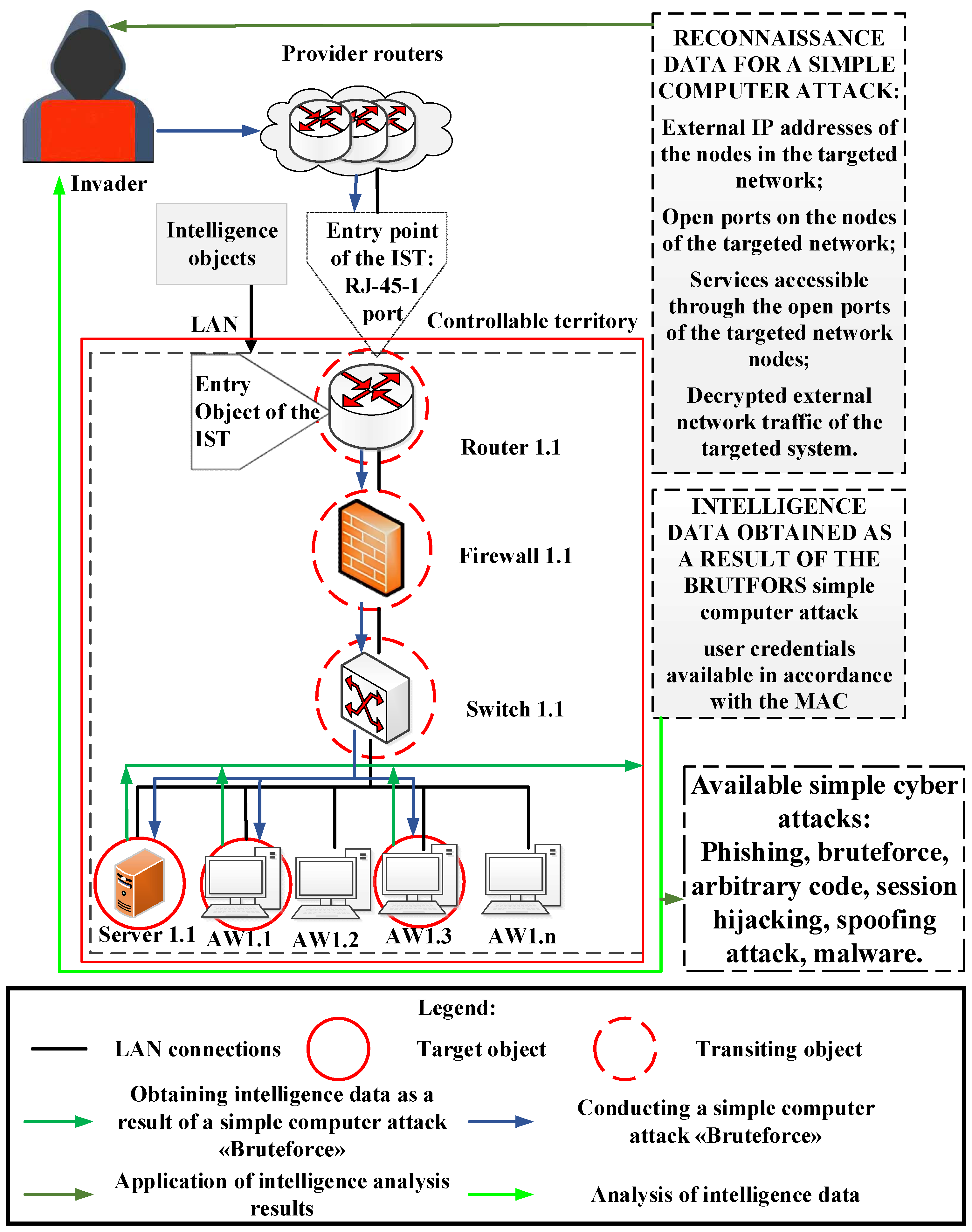
After analyzing the RD, the violator uses it to introduce and legalize it on the network. To this end, the violator conducts a “Brute Force” type attack, selects the user’s credentials on the Automated workplace (AW) 1.1, 1.3 and Server 1.1. Next, he performs identification and authentication on the LAN as a legal user and takes them under external control. As a result of the attack, the intruder is introduced and legalized in the attacked element of DIS (
Figure 3).
The arrays of RD obtained as a result of changes in their online status, the use of intelligence tools and CA are reflected in
Figure 3. Thus, the violator received some RD, which, according to the membership function, is sufficient to move to the “low level of awareness” of the corresponding scale.
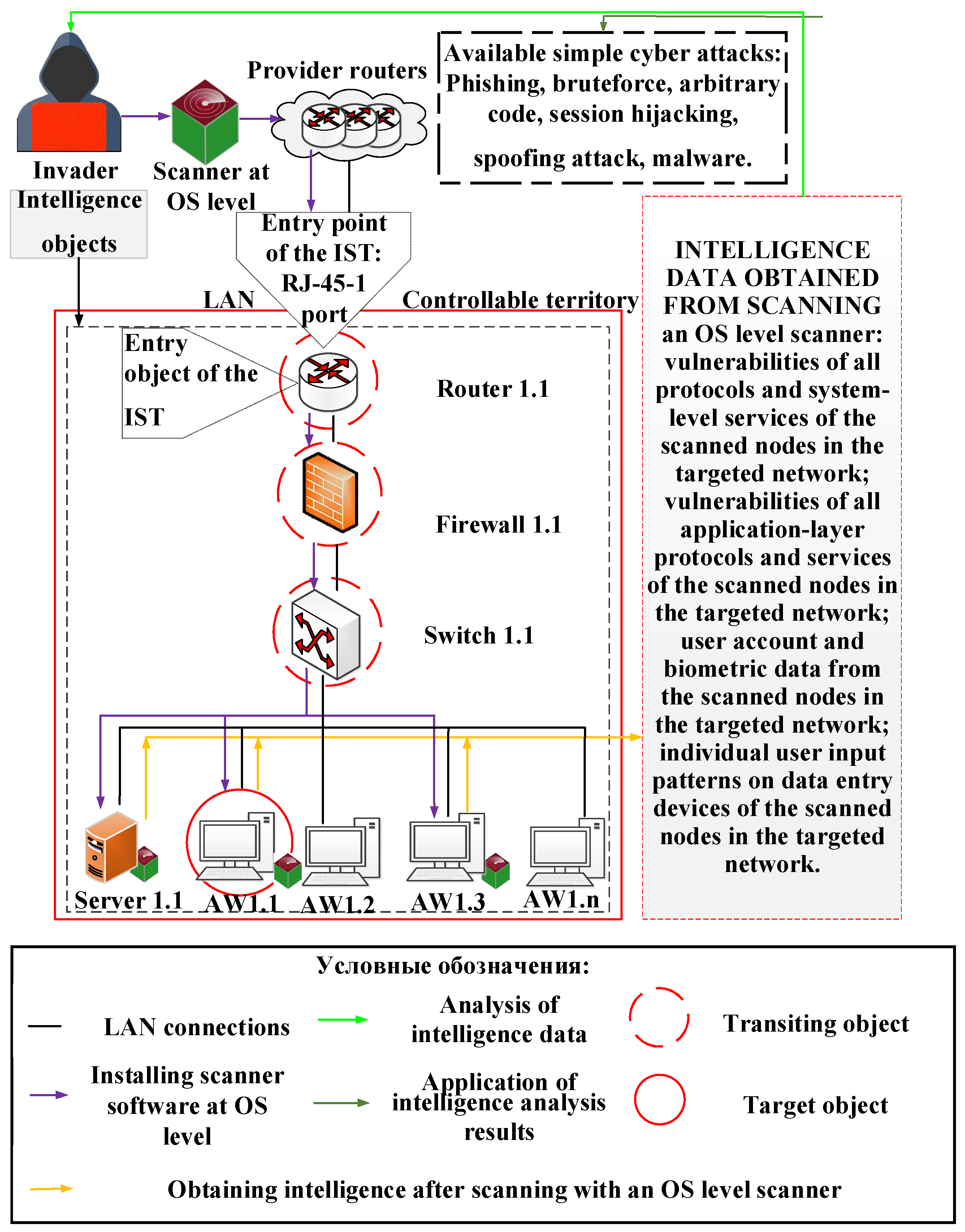
Next, we simulate the “Privilege Escalation” stage of a CCA.
Figure 4 shows an example when an infringer, having obtained the rights of users of AWs 1.1, 1.2 and Server 1.1, implements the operating system (OS) -level scanner software (SW) on them. The OS–level scanner is used to identify SW vulnerabilities, available network nodes (NN), and obtain the data necessary to achieve the goal of this stage, which is to upgrade privileges to the network administrator level. Based on the data obtained (the presence of vulnerabilities in the OS protocols, application software (ASW) or hardware architecture), the violator decides to upgrade privileges at the AW 1.1. As a result of upgrading privileges to the network administrator level, the violator gets access to all NN and the opportunity to scan them with a network-level scanner after receiving the necessary RD to carry out the “Spread” stage of a CCA.
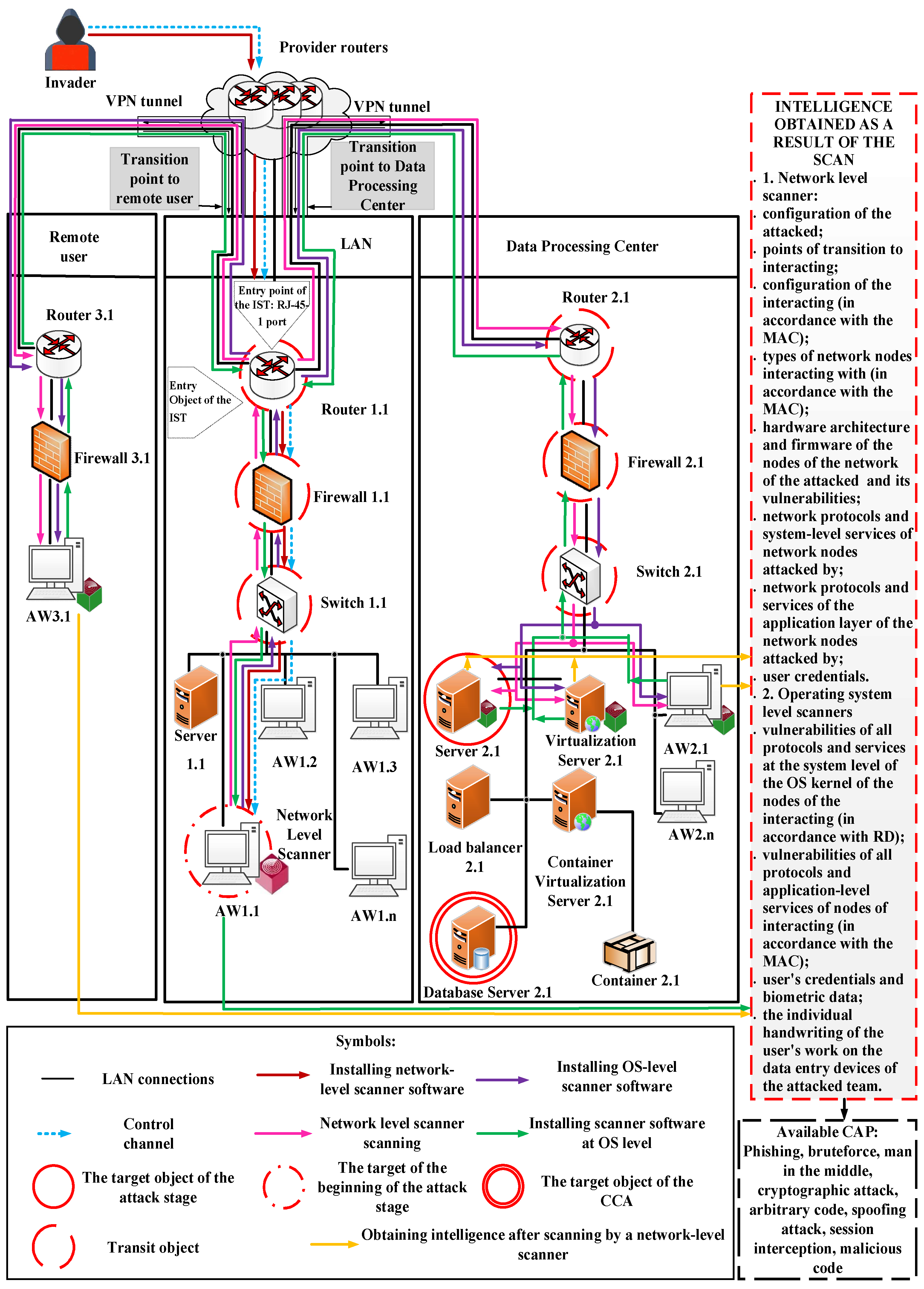
The
“Spread
” stage of a CCA is shown in
Figure 5. To implement it, the intruder installs a network-level scanner at an AW 1.1.
By scanning with a network-level scanner from an Automated workplace 1.1, the intruder receives data on the points of transition to the interacting elements of the DIS, access to the elements of the interacting elements of the DIS in accordance with the ACM and the presence of vulnerabilities in these elements. As a result, the intruder receives information about the configuration and types of NN available in accordance with the ACM, as well as about their hardware architecture, embedded SW and their vulnerabilities, network protocols and services at the system and application levels, as well as user credentials. By increasing their privileges after being legalized on the network, the violator gets access to additional data on the attacked NN, which corresponds to an average awareness of the elements of a DIS. However, the data obtained as a result of scanning by a network–level scanner from an AW 1.1 LAN does not allow access to the target object of a CCA - the Database Server 2.1 of the Data Center (DC). To obtain the missing data, the intruder implements the OS scanner SW on the objects of DI of the DC and the remote user available in accordance with the Access Control Model and the vulnerabilities found.
After the SW scanner is implemented, they are scanned and data is obtained on vulnerabilities in protocols and services of the system and application layer of the NN and SE of interacting elements of the DIS, as well as user credentials and biometric data, and the individual handwriting of their work on data entry devices.
As a result, the violator receives the data necessary for distribution and privilege escalation on the 2.1 DC. By spreading through the network, the violator increases his awareness-level of the elements of the DIS in accordance with the evaluation criteria to a high level, which gives him access to move to the next level to carry out a DI.
At this point, the “grey box” testing stage is complete. Its results are presented in Tables 5,6,7.
Testing at the stage of high intruder awareness is carried out using the
“white box
” method. Its model is presented in
Figure 6.
Table 5.
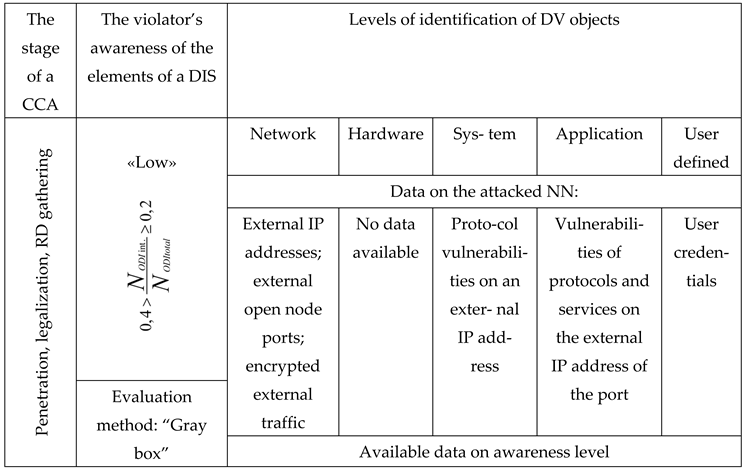
Indicators of the level of “Low awareness of the violator”.
Table 5.
Indicators of the level of “Low awareness of the violator”.
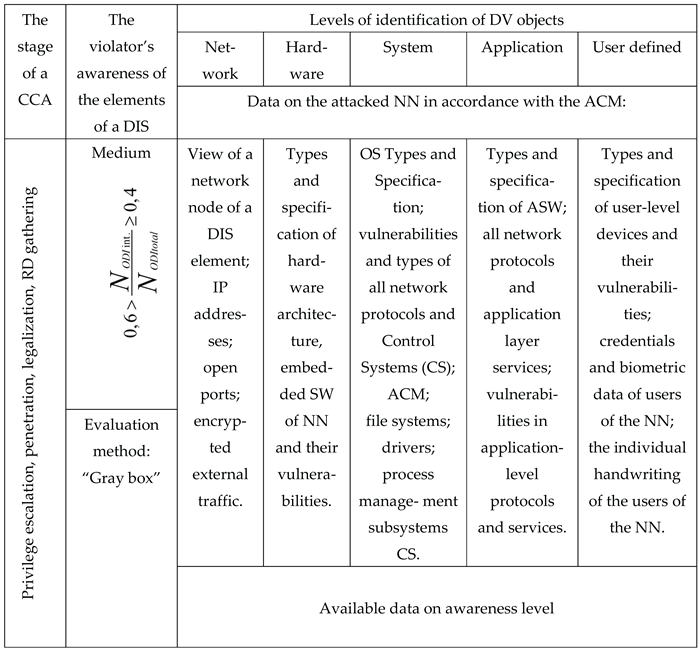
Table 6.
Indicators of the level of “Medium awareness of the violator”.
Table 6.
Indicators of the level of “Medium awareness of the violator”.
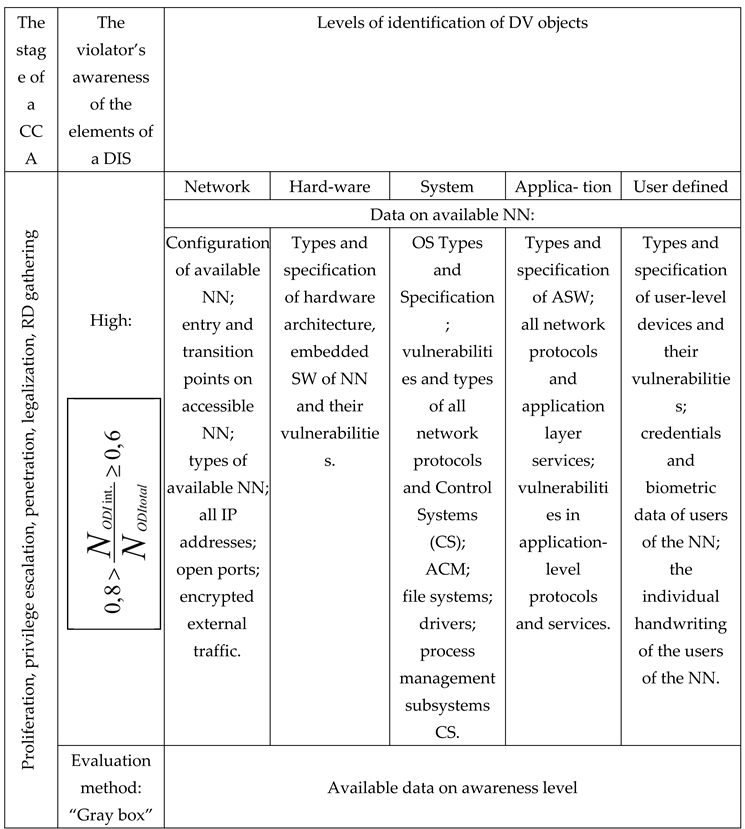
Table 7.
Indicators of the levels of “High awareness of the violator”.
Table 7.
Indicators of the levels of “High awareness of the violator”.
At this stage, the violator has a complete array of RD on all potential objects of DI of elements of a DIS. By elevating the privileges on the 2.1 DC Server to the network administrator level, the attacker gains access to the target object of the DI of a CCA – the 2.1 DC DB Server and carries out a SCA such as
“Malicious code
” in order to take over the DC database. This completes the
“White box
” testing phase. The results are presented in
Table 8.
If necessary, the numerical values of the intruder awareness indicator can be converted into numerical values of the indicator for assessing the intelligence protection of RIS elements.
The results of the experiments conducted to verify the practical applicability of the developed models and techniques confirm the possibility of proactive assessment the awareness of the violator and analyzing the typical RD arrays available to him.