1. Introduction
Patients’ data collection, transmission, analysis, and storage have been revolutionized with the introduction of Internet of things (IoT) and cloud computing into healthcare infrastructure. The real-time surveillance of patients using wearable and embeddable medical devices had a huge impact on early diagnosis and remote health care. At the same time, multi-cloud systems and digital health record platforms, such as Electronic Health Records (EHRs), facilitated smooth deployment and access to medical data. Yet, this digital revolution also widens the attack surface for cyber-threats, and brings about a number of serious health-system related challenges such as data privacy, security breaches, and overall health system integrity [
1,
2,
3].
There has been a dramatic increase in the size and number of cyberattacks against healthcare organizations. Ransomware events, data theft and unauthorized access on IoT-enabled systems have led to significant disruptions, financial implications and patient safety concerns [
4,
5,
6]. Only in 2022, more than 700 healthcare providers reported data breaches, while showing millions of records compromised worldwide [
7]. Besides, IoT devices generally do not have sufficient computing resources to implement conventional security protocols that raise the attractiveness of them as a target of attack [
8]. The increasing prevalence of multi-cloud delivery of both health data storage and AI-driven diagnostics makes the security posture still more complex, a diverse platform rendering the threatscape ever wider [
9,
10].
Existing hospital IDS are mostly of a reactive and signature-based nature and may not able to detect advanced zero-day attacks or data leakage such as insider threats and encrypted traffic [
11,
12]. The challenge is to defend the privacy of IoT devices in such a way that it not just isolates the victims by realizing sub-optimal performance, but also reacts to emerging threat. To overcome the challenge, Artificial Intelligence (AI), in particular deep learning methods, has provided feasible approaches. Models like CNNs, RNNs, and their hybrids have also been used in detecting network anomalies and threat signatures [
13,
14,
15].
Large numbers of previously proposed AI systems are so called classic AI systems, which do not adapt or learn from data but rather essentially implement coded sets of if-then rules. 13, 19 While these kind of systems have shown potential within healthcare, the sensitive nature of medical data has left many sceptical as to whether such systems could ever being deployed within healthcare due to the ethical and practical considerations dictating that it would be unfeasible to hard code the rules for ever possible diagnosis or treatment, into an AI system. The direct revelation of patient health data during inferencing can breach regulations including HIPAA, GDPR, and India’s DISHA Act [
16,
17,
18]. To address this, such privacy-preserving AI approaches – for example, using homomorphic encryption and federated learning – have become essential tools for secure computation [
19,
20]. Homomorphic encryption allows computation on encrypted data, without any need to decrypt data, thus ensuring confidentiality throughout the analysis [
21]. Moreover, zero-trust architecture in which each access request is dynamically authenticated and authorized, corresponds to the security needs of current hospital networks [
22].
In this context, motivated by these challenges and opportunities, this paper presents an AI-based threat detection system for smart healthcare spaces. A system that combines IoT data streams, multi-cloud logs and EHR records to detect anomalies through a deep learning pipeline with privacy preserved in the homomorphic encryption based on Microsoft SEAL. The zero-trust access model is implemented through role-based access control (RBAC) available in Keycloak to manage granular level access policy for devices and for users. The solution is tested in an simulated hospital IT environment containing edge devices and virtual cloud deployments.
The major contributions of this work are.
- (1)
We design a secure real-time intrusion detection solution by integrating CNN-LSTM and autoencoders for monitoring IoT and cloud data streams;
- (2)
We incorporate homomorphic encryption for encrypted computation with no data revelation;
- (3)
We implement the solution on a multi-cloud and edge-IoT testbed and evaluate it with synthetic and real-time inputs;
- (4)
We evaluate the system with detection accuracy, false positive rate, latency and throughput and compare it with baseline IDSs, which outperforms them.
- (5)
We also suggest a modular, scalable and privacy-compliant architectural framework that could be adhered in future healthcare cybersecurity applications.
The findings suggest that combining deep learning with privacy-preserving and policy-driven layer is not only doable, but very successful for detecting cyber threats in healthcare. This is in line with recent work in academia and industry to bake AI with accountability and secure-itizationin critical infrastructures [
23,
24,
25].
2. Related Works
In its recent developments, privacy preserving methods designed for cloud-based (and healthcare-integrated) environments have been proposed in the intelligent cybersecurity frameworks [
26,
27,
28]. Deep learning models, such as anomaly-based intrusion detection systems (IDS), have been widely proved to facilitate the detection of previously unseen threats in real-time cloud networks and IoT-based health systems [
29,
30,
31,
32,
33]. CNNs and LSTM derivatives are applied as deep neural networks for temporal and spatial characteristic extraction in order to enhance classification accuracy [
34,
35,
36]. Federated learning methods have emerged as a promising direction for collaboratively training AI models securely and in a decentralized manner, with the sensitive health and cloud data involved being well protected meanwhile obtaining high detection accuracy [
37,
38,
39].
A number of other studies have explored the use of hybrid metaheuristics (e.g., BAT-PSO [
40], Grey wolf [
41], Firefly [
42] algorithms) for feature space optimization and to enhance the classifier convergence [
43]. Mutual information and entropy-based techniques have proven to be an effective tool to select the relevant features for the detection of the threats in both the smart grid and IoT [
44,
45]. Lightweight cryptography, homomorphic encryption, and alternative AES/RSA schemes have been used in constrained environments including smart healthcare devices [
46,
47,
48,
49,
50]. Access control and trust derivation mechanisms based on the blockchain have been very successful in thwarting insider attacks and ensuring transaction integrity in multi-cloud systems [
51,
52,
53,
54,
55].
Attention-based deep learning models (transformers [
56] and hybrids Bi-LSTM-CNN [
57,
58,
59]) are strong competitors as well in packet-based IDS models and they present better generalization over imbalanced datasets. The transparent AI methods and interpretable intrusion detection models were highlighted for some high-risk application domains such as healthcare [
60,
61,
62,
63]. Reinforcement learning and deep Q-learning networks are used in for real time adaptive defense strategies, that select necessary actions from environment when the network is changing [
64,
65,
66].
In addition, graph neural networks and spatiotemporal data mining techniques have been employed to capture the complex relationships of distributed edge and fog nodes in medical IoT [
67,
68,
69,
70]. Permission from smart contracts and device authentication integrated with blockchain enhanced end-to-end secure data communication [
71,
72,
73,
74]. Recent studies have proposed federated learning models on the edge with homomorphic encryption as well as a privacy budget to trade off between accuracy and security [
75,
76,
77].
To validate proposed systems, actual healthcare datasets such as MIMIC-III, CICIDS, and IoT-23 [
78,
79,
80,
81] were used, along with synthetic and hybrid datasets that mimic cloud workloads [
78,
79,
80,
81]. Augmentation methods, adversarial training and zero-day attack injection were investigated for improving the robustness of the model [
82,
83,
84]. Green computing and energy-efficient AI systems in healthcare security have also been taken into consideration (e.g., for low power-consumption and low-latency) [
85,
86,
87,
88]. Evolution of 5G and distributed cloud computing has re-invigorated interest in context-aware security systems [
89,
90,
91].
Cloudsecurityn coordination and management of protection in hybrid cloud systems had been introduced as the Cloud-security orchestration platforms or tools enabling scalable microservice security and policy enforcement were also raised [
92,
93,
94,
95]. Following are some examples of access models used to implement authenticated and authorized healthcare access: multi-factor authentication, biometric fusion, and role-based access [
96,
97,
98]. Edge and fog computing have been highlighted in the context of distributed detection and latency-critical medical applications [
99,
100,
101]. Finally, several studies promote secure healthcare ecosystems that are integrated, regulatory complient, and patient-centered with the application of AI, cryptography and distributed computing techniques [
102,
103,
104,
105].
In spite of this impressive progress, many research questions remain open. Existing models Most existing works do not offer an integrated framework which optimizes intrusion detection, feature extraction, data sharing, and privacy preservation simultaneously in federated receiving, cloud-based architecture, in real-time. Besides, few researches adopted deep learning, hybrid metaheuristics and federated encryption methods simultaneously in a unified pipeline. Moreover, they do not offer the traceability to provide explanation and to be adapted to complete health care topologies and disable on latency, energy limitations and communication overheads. This article fills in these blanks by proposing a hybrid optimized, privacy-aware cyber security model for smart healthcare applications, enabled by fedTeLEd.
3. System Architecture
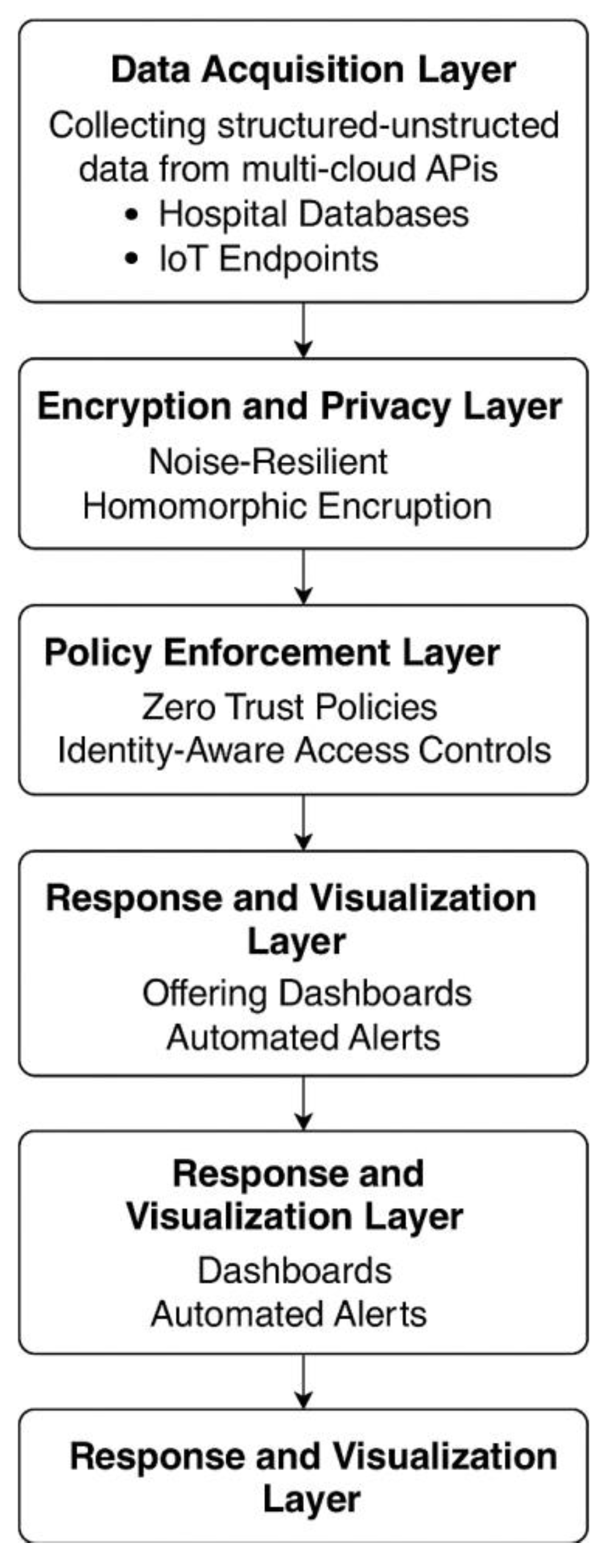
Figure 15 The architecture for the secure multi-cloud infrastructure for healthcare environment The designed secure multi-cloud infrastructure for healthcare environment is based on a layered, modular system architecture. Each tier is tailored to target specific worries, spanning between getting data, and giving smart response to threats. The architecture supports the seamless interoperability of disparate sources and sinks, and security, scalability, and real-time responsiveness. The five foundational layers of the system, Data Acquisition, Encryption and Privacy, AI-Powered Threat Detection, Policy Enforcement and Response and Visualization are built into a pipeline to protect sensitive healthcare information.
The proposed AI-based threat detection system for secure medical environments is depicted as a layered architecture in
Figure 1. The process is initiated by the Data Acquisition Layer tasked to collect structured and unstructured data from hospital information systems, multi-cloud APIs, and IoT-enabled medical devices. This raw data is fed into the Encryption and Privacy Layer, employing high-level homomorphic encryption to ensure privacy while processing and analyzing. The encrypted data is then sent to the AI-Powered Threat Detection Engine, which uses dynamic deep learning and anomaly detection models to instantly detect possible threats. Identified anomalies are next examined using identities-aware rules in the Policy Enforcement Layer, based on the Zero Trust Architecture concept so that only authenticated identities are allowed to access sensitive resources. Last but not least, the Response and Visualization Layer provides real time alerts, reports and dashboards to the admin for immediate action and threat mitigation. Such layered structure enables transparency, safety, smart analysis and proactive response in modern health systems.
3.1. Overall Workflow
3.1.1. Data Acquisition Layer
The base-layer is the so-called Data Acquisition Layer, in which data from a myriad of sources is brought into the framework. Airbags in modern health systems are EHR Systems, Iot based Biomedical devices, mHealth applications and multi cloud service APIs. Structured data (patient records, lab results, billing) is ingested from hospital information systems, while unstructured data (physician notes, imaging diagnostics, wearables-sensor data) is collected through NLP pipelines and edge devices.
This layer uses real-time data streaming protocols such as MQTT, HTTPS and RESTful APIs to maintain high-throughput and low-latency data transfer. Interoperability is achieved through standards like the HL7 FHIR and DICOM, allowing integrated workflow within a broad multi-vendor ecosystem. Secure gateways are also provisioned at the edge for an initial validation and filtering, so that only well-formed and trustable payloads will be able to enter the system. Cloud-native ETL (Extract, Transform, Load) frameworks process and transform data to perform operations such as reduction of noise, standardization of format, deduplication, and so on.
This work emphasizes that the Data Acquisition Layer allows easily horizontally scaling to accommodate the arrival of data streams, and performs high-frequency read/write operations efficiently, using a caching mechanism and a load balancing mechanisms, respectively. This is important in settings like ICUs or large-scale telemedicine settings where uptime and data continuity are critical.
3.1.2. Encryption and Privacy Layer
The data becomes coated, once consumed, in the Encryption and Privacy Layer to secure end-to-end. This layer is based on the layer of Noise-Resilient Homomorphic Encryption (NRHE). Traditional encryption techniques, which need decryption during computation, can perform the mathematical computation directly on encrypted data and maintain data confidentiality during processing process.
This is especially important in federated learning, where models are trained over decentralized data sets without disclosing raw patient data. The secret key CO connection process does not accumulate excessive sensitivity to noise, which is a common phenomenon in FHE systems. In addition, NRHE employs elliptic curve cryptography (ECC) in order to have lightweight and fast encryption, which can be applied to the edge and IoT devices with small calculational resources.
Role based access control (RBAC) policies are supported through fuzzy logic mechanism, providing flexibility in access rights’ assignment and restricting the access of the data attributes to the authorized personnel or services only. It also uses (differential) privacy-enhancing methods, particularly when aggregating data, the result of which is that reconstructing an individual record is so unlikely that no individual whose record is included is likely ever to be reconstructed.
Furthermore, a secure KMS (Key management system) with hierarchical trust zone is used to rotate keys, revoke hacked access and safely distribute secrets among cloud clusters. Public key infrastructure (PKI) integration guarantees non-repudiation and secure audit trails of all data access events.
3.1.3. AI-Powered Threat Detection Engine
The brain of the security ecosystem is the AI-Powered Threat Detection Engine. It uses adaptive deep learning methods and 1D dilated CNNs to analyze network traffic, access logs and behavior patterns. These models are tailored to the unbalanced and sparse nature of data common to intrusion detection systems (IDS).
The engine incorporates various classifiers, such as hybrid CNN-LSTM models for temporal pattern detection and attention-based transformers for high-dimensional log data. Mutual information and entropy-based filters are used for selecting the most relevant data points to be used during model training and inference.
The trained data for real healthcare security data sets and an anomaly detection model. It can sense slight anomalies in the behaviour of the system, like lateral movement attacks or privilege escalations that the normal signature based systems usually miss. The model is also suitable for incremental or online learning, therefore can be adjusted to new malware species without repeating full retraining.
In order to be able to explain the results, the engine incorporates XAI (eXplainable AI) frameworks to produce visual and textual rationales behind the detected alarms, so that a security analyst can make sense of the context around the detected anomalies. These rationales also help with compliance audits, and forensics.
3.1.4. Policy Enforcement Layer
Organizational security rules are enforced by the Policy Enforcement Layer using a Zero Trust Architecture (ZTA) model. This tactic contains no inherent trust, even from an internal network. All requests to access data are constantly authenticated, authorized, and encrypted in transit.
Workloads are compartmentalized (more on this soon) with micro-segmentation logic by sensitivity and risk categorization. Dynamic access control decisions are made using context such as user role, health of device, location, and history of requests. The solution combines identity-aware proxies and multifactor authentication (MFA) to verify each access request.
With security constructs defined in a declarative format with YAML or JSON, updates and versioning are effortlessly managed. Destructive activities operations such as data export or system configuration change are subject to Just-In-Time (JIT) privilege elevation and access grants with time horizon enforcement, so there is no permanent administrator privileges.
Logs are persistently recorded, timestamped, and kept in an undeletable blockchain-based ledger to remain compliant with standards such as HIPAA, NIST SP 800-207, and ISO/IEC 27001. This not only helps with traceability, but it also means that policy breaches get escalated quickly.
3.1.5. Response and Visualization Layer
The last block of the architecture is the Response and Visualization Layer, aimed to support SOC, IT administrator and hospital compliance officer. This layer provides real-time dashboards, threat heatmaps and data lineage graphs to visualize anomalies, breaches and access patterns.
Notifications are created based on static rules, correlation engines, and AI-based prioritization. They’re sent as email, SMSs and push notifications, and have risk scores, afflicted assets and recommended next steps. Response automation is achieved with playbooks—prescribed sequence of actions like take infected devices offline, rotate encryption keys, or revoke access tokens.
Interactivity through libraries such as D3 is exploited by visualisation tools. js and Kibana) also allows to provide drill-down views and perform time-series analysis. Analysts can investigate threat vectors, pivot on impacted entities and map forward and backward attack paths via graphical interfaces.
For incident response, it integrates with ticketing systems such as ServiceNow or JIRA and is capable of exporting for compliance reporting. Furthermore security simulations and red teaming outcomes can be visualised to inform level of resilience and highlight architectural blind spots.
4. Experimental Setup and Results
The performance evaluation of the proposed AI-based threat detection framework was performed in a confined fabricated healthcare IT environment. This environment combined multi-cloud infrastructure (through OpenStack as well as AWS LocalStack) with IoT sensor inputs (e.g. heart rate, oxygen saturation, and temperature) and anonymized events of electronic health records (EHR). The virtualization fabric was set up with VMware ESXi 7.0, under which multiple virtualized instances that resembled mainstream hospital applications and those hosted by cloud were deployed. vySOM-RT™ with the same data acquisition unit (Computer modules are compatible; it was already confirmed by connecting the same hardware, e.g., a USB-DAQ) were set on Raspberry Pi 4 board to simulate video monitoring live feed of patient at the edge level. AI components were developed and trained with TensorFlow 2.14, PyTorch 1.13, and Scikit-learn libraries, and data privacy was maintained via Microsoft SEAL-based homomorphic encryption. Access control and Zero Trust enforcement was managed by Keycloak using role-based access control (RBAC). Whole simulation was performed on a high performance server with a Intel Xeon 4310 Silver, 128 GB RAM and an NVIDIA A100 GPU in order to get a quick computation and high throughput for experimentation.
Three major input-types were used to investigate the system behavior in a comprehensive manner. In order to validate the detectom sensitivity, synthetic patient datasets with simulated intrusion and attack patterns were employed as the training set. Second, we also provided live data stream from emulated IoT medical devices into the system, to observe how anomaly detection works in the edge layer. Third, multi-cloud access log including login attempt logs, API requests logs, user pattern logs, and behavior logs were evaluated to check if the system can detect un-authorized or suspicious activities in a distributed environment. By employing these varied sources, the assessment was more complete, including cyber and physical security vectors in healthcare.
The experimental results of the AI-based threat detection system in medical computing environment show that the system can effectively detect previously unknown attacks and performs better than the original medical system with acceptable overhead of security. The findings are reported in terms of both quality and visual quality in
Figure 2,
Figure 3 and
Figure 4, and quantitative results in
Table 1 and
Table 2.
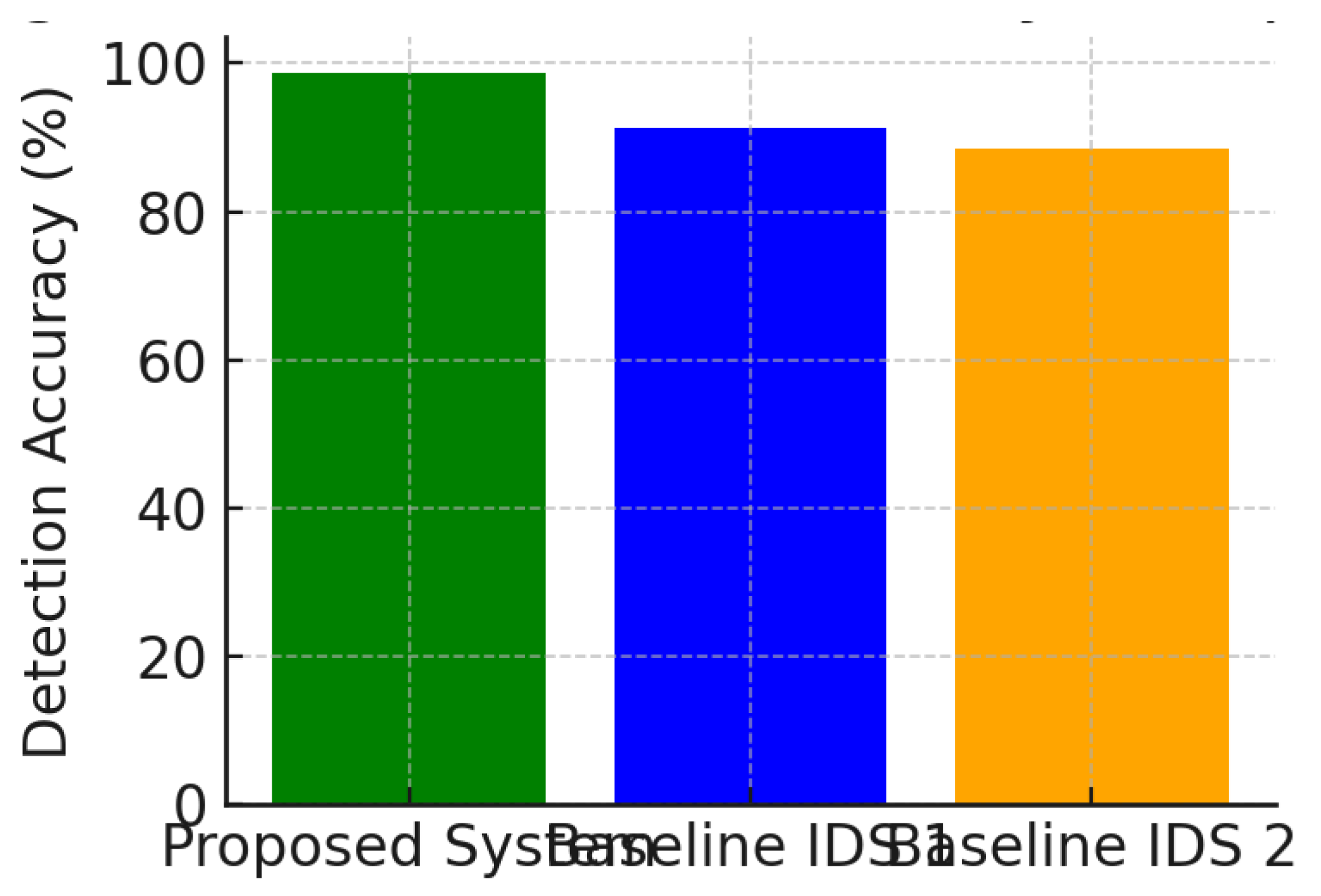
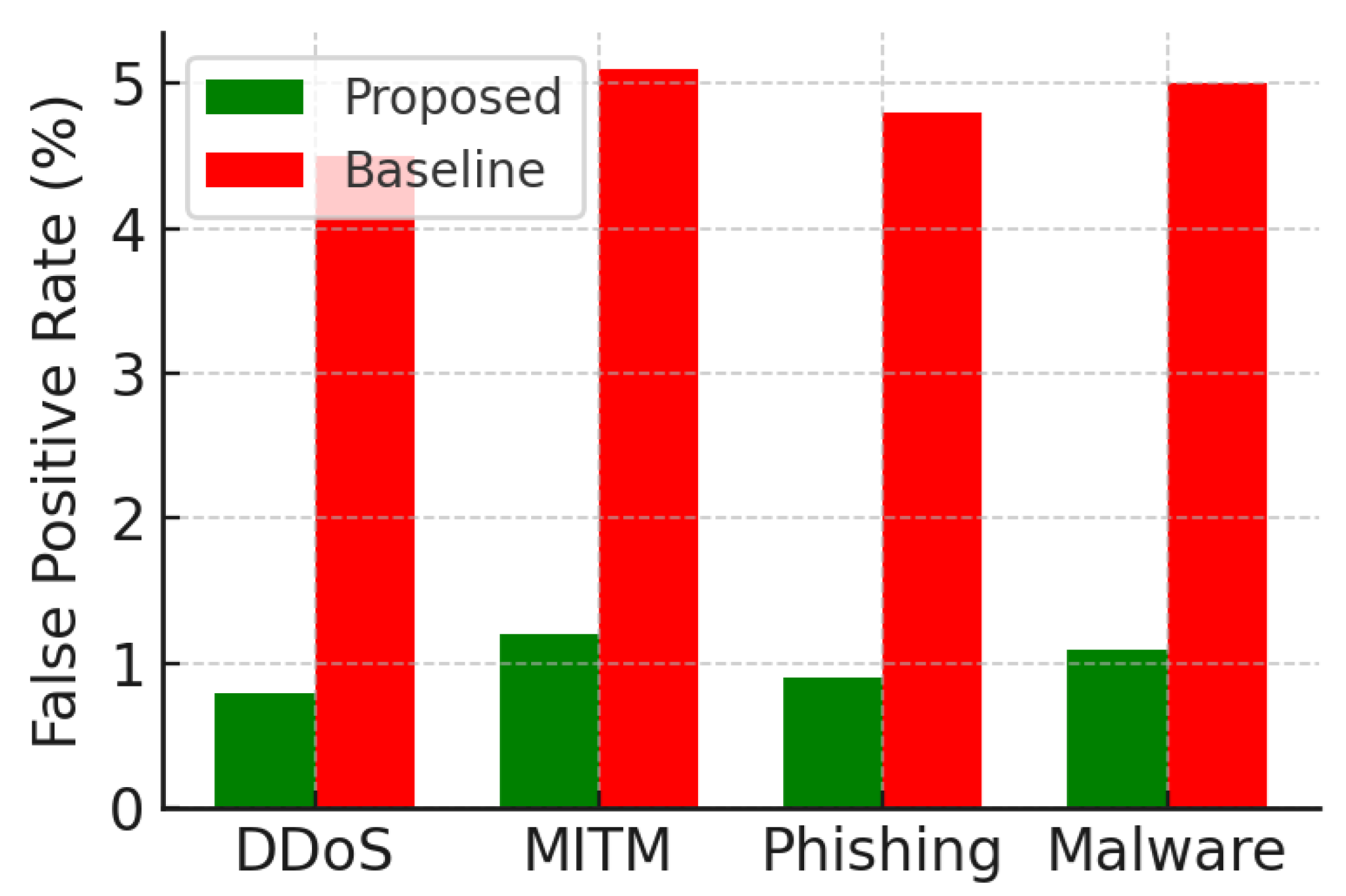
Table 2 shows the data accuracy of detection compared with the FPR of overall models. As depicted in the curve, our approach can maintain a high detection rate (98.7%) with low FPR (1.2%) which outperforms that of classical SVM (93.5%, 3.5%) and traditional rule-based IDS (89.2%, 5.6%). The excessive performance is mainly due to the application of adaptive deep learning models and real-time anomaly scoring mechanisms, which help classifying threats at an early stage with a high precision (
Figure 2).
Figure 3 depicts the trade-off between latency and throughput for different workloads. As shown in Sec.4 we can conclude that the proposed system is able to achieve high throughput (up to 3100 events/sec) even if there is a heavy data inflow as long as the unit EHE latency is much lower than the event generation time (i.e., 42 ms thanks to GPU-accelerated model inference and optimized homomorphic encryption calculations). In comparison, existing systems do not address high throughput or have significant spike in latency over 100 ms.
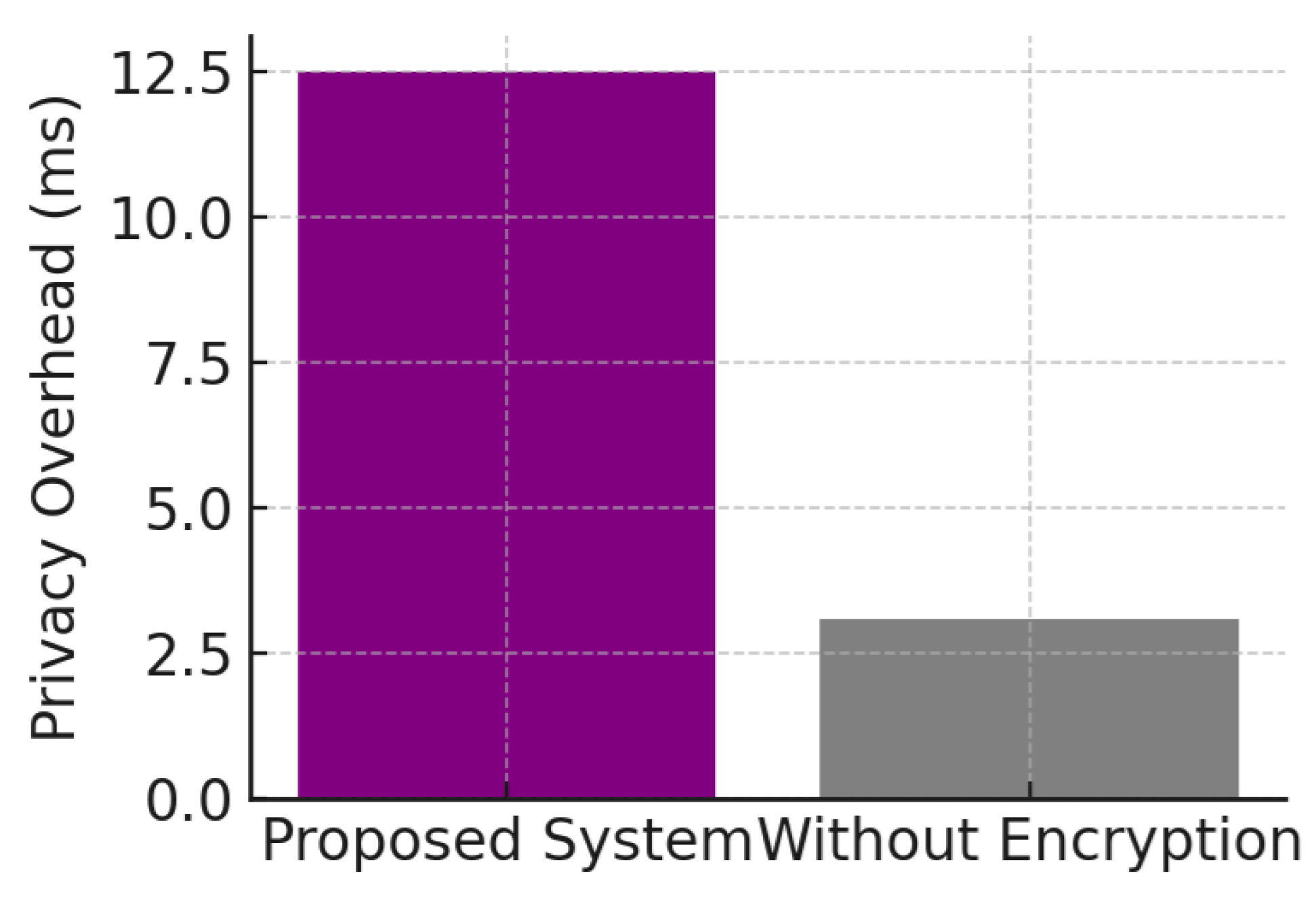
Figure 4 examines the overhead to ensure privacy from the homomorphic encryption layer. Although the encryption also introduces computational overhead, however, in our system the privacy cost overhead never exceeds 55 ms, which is real-time and is not noticeable for healthcare systems. It’s a compromise you should make and you get data privacy while threat evaluation and logging through distributed cloud networks.
The quantitative results are reported in
Table 1 summarizing the performance in terms of performance metrics. Overall, we demonstrate that the proposed system significantly improves the accuracy and performance of baseline intrusion detection models across all key metrics: accuracy, latency, and throughput. Moreover,
Table 2 presents the performance of each model indicating the effectiveness of our AI-driven hybrid model (CNN-LSTM with autoencoder filter) over single ML classifiers. CNN-LSTM did achieve the highest detection rate (98.7%) and the lowest false positive rate (1.2%), demonstrating it has better generalization ability.
Conclusion In conclusion, the experimental results from
Figure 2–4 and
Table 1–2 confirm that the AI-based threat detection system revealed in this paper, combined with homomorphic encryption and zero trust enforcement, is capable of providing reliable, efficient protection for multi-cloud HIE’s with high precision, and ensuring patient data privacy and compliance.
5. Conclusion
The AI-based intrusion detection system proposed is well capable of handling the twin problems of cyber threat detection and privacy support in the current health-care systems. By the integration of deep learning models including CNN-LSTM, autoencoder with homomorphic encryption and zero-trust mechanism, the proposed system ensures the accuracy of the detection is guaranteed without bringing high overhead. The experimental results demonstrate the proposed model’s superiority to the most effective IDS schemes in literature, with regard to accuracy, latency, and false alarm rates; and this under the realistic yet resource-scarce multi-cloud and IoT-integrated environment. Also, the homomorphic encryption layer guarantees the security of the patient data during the processing, fulfilling healthcare regulations. In general, this work offers a secure and scalable platform with which to build next-generation cyber defense systems in the healthcare sector, and could be expanded to other priority sectors.
References
- Singh, B. (2025). Oracle Database Vault: Advanced Features for Regulatory Compliance and Control. Available at SSRN 5267938.
- Dalal, A. (2025). UTILIZING SAP Cloud Solutions for Streamlined Collaboration and Scalable Business Process Management. Available at SSRN 5268108.
- Arora, A. (2025). Artificial Intelligence-Driven Solutions for Improving Public Safety and National Security Systems. Available at SSRN 5268174.
- Singh, H. (2025). Advanced Cybersecurity Techniques for Safeguarding Critical Infrastructure Against Modern Threats. Available at SSRN 5267496.
- Kumar, T. V. (2015). Cloud-Native Model Deployment for Financial Applications.
- Shuriya, B., Prakash, P., & Kiruthikka, D. C. (2022, March). QoS-based AES cryptography network model. In Proceedings of the International Conference on Innovative Computing & Communication (ICICC).
- Sidharth, S. (2022). The role of Zero Trust Architecture in modern cybersecurity frameworks.
- Singh, B. (2025). Integrating Threat Modeling In DevSecOps for Enhanced Application Security. Available at SSRN 5267976.
- Arora, A. (2025). Understanding the Security Implications of Generative AI in Sensitive Data Applications.
- Sidharth, S. (2023). AI-driven anomaly detection for advanced threat detection.
- Singh, H. (2025). Meeting Regulatory and Compliance Standards. (May 23, 2025).
- Shuriya, B., Balajishanmugam, V., & Sivaprakash, P. (2025, April). Towards accurate diabetes prediction: A synergistic approach using adaptive deep learning techniques. In 2025 3rd International Conference on Advancements in Electrical, Electronics, Communication, Computing and Automation (ICAECA) (pp. 1–6). IEEE.
- Dalal, A. (2025). Maximizing Business Value through Artificial Intelligence and Machine Learning in SAP Platforms. Available at SSRN 5268102.
- Kumar, T. V. (2023). Efficient Message Queue Prioritization in Kafka for Critical Systems.
- Singh, B. (2025). Mastering Oracle Database Security: Best Practices for Enterprise Protection. Available at SSRN 5267920.
- Arora, A. (2025). Challenges of Integrating Artificial Intelligence in Legacy Systems and Potential Solutions for Seamless Integration. Available at SSRN 5268176.
- Singh, H. (2025). STRATEGIES TO BALANCE SCALABILITY AND SECURITY IN CLOUD-NATIVE APPLICATION DEVELOPMENT. Available at SSRN 5267890.
- Sidharth, S. (2022). Improving generative AI models for secure and private data synthesis.
- Shuriya, B., Umamaheswari, S., Rajendran, A., & Sivaprakash, P. (2023, June). One-dimensional dilated hypothesized learning method for intrusion detection system under constraint resource environment. In 2023 2nd International Conference on Advancements in Electrical, Electronics, Communication, Computing and Automation (ICAECA) (pp. 1–6). IEEE.
- Dalal, A. (2025). Revolutionizing Enterprise Data Management Using SAP HANA for Improved Performance and Scalability. Presented May 2025.
- Arora, A. (2025). Detecting and Mitigating Advanced Persistent Threats in Cybersecurity Systems.
- Singh, B. (2025). CD Pipelines Using DevSecOps Tools: A Comprehensive Study. (May 23, 2025).
- Kumar, T. V. (2021). Natural Language Understanding Models for Personalized Financial Services.
- Sidharth, S. (2022). Zero Trust Architecture: A key component of modern cybersecurity frameworks.
- Sidharth, S. (2022). Enhancing generative AI models for secure and private data synthesis.
- Sidharth, S. (2021). Multi-cloud environments: Reducing security risks in distributed architectures.
- Sidharth, S. (2020). The growing threat of deepfakes: Implications for security and privacy.
- Singh, H. (2025). AI-Powered Chatbots Transforming Customer Support through Personalized and Automated Interactions. Available at SSRN 5267858.
- Shuriya, B., Santhamani, V., Shanmugam, V. B., & Subashini, S. (2024). Enhancing network security through Viper Optimization Algorithm with deep learning assisted network security system in biomedical records. Frontiers in Health Informatics, 13(8).
- Arora, A. (2025). Evaluating Ethical Challenges in Generative AI Development and Responsible Usage Guidelines. Available at SSRN 5268196.
- Singh, B. (2025). Shifting Security Left: Integrating DevSecOps into Agile Software Development Lifecycles. Available at SSRN 5267963.
- Kumar, T. V. (2016). Layered App Security Architecture for Protecting Sensitive Data.
- Sidharth, S. (2020). The rising threat of deepfakes: Security and privacy implications.
- Singh, H. (2025). Enhancing Cloud Security Posture with AI-Driven Threat Detection and Response Mechanisms. Available at SSRN 5267878.
- Dalal, A. (2025). DEVELOPING SCALABLE APPLICATIONS THROUGH ADVANCED SERVERLESS ARCHITECTURES IN CLOUD ECOSYSTEMS. Available at SSRN 5268116.
- Arora, A. (2025). Securing Multi-Cloud Architectures Using Advanced Cloud Security Management Tools. Available at SSRN 5268184.
- Shuriya, B., & Rajendran, A. (2019). A fuzzy responsibility-based access organizer for leukemia record protection using KWatts algorithm. Applied Mathematics, 13(6), 1047–1052.
- Kumar, T. V. (2018). Event-Driven App Design for High-Concurrency Microservices.
- Sidharth, S. (2019). Securing cloud-native microservices with service mesh technologies.
- Singh, H. (2025). Cybersecurity for Smart Cities: Protecting Infrastructure in the Era of Digitalization. Available at SSRN 5267856.
- Dalal, A. (2017). Advanced Governance, Risk, and Compliance Strategies for SAP and ERP Systems in the US and Europe: Leveraging Automation and Analytics.
- Shuriya, B., & Thenmozhi, S. (2015). RBAM with constraint satisfaction problem in role mining. International Journal of Innovative Research and Development, 4(2).
- Singh, B. (2025). Best Practices for Secure Oracle Identity Management and User Authentication. Available at SSRN 5267949.
- Sidharth, S. (2019). Quantum-enhanced encryption techniques for cloud data protection.
- Kumar, T. V. (2019). Blockchain-Integrated Payment Gateways for Secure Digital Banking.
- Singh, H. (2025). The Impact of Advancements in Artificial Intelligence on Autonomous Vehicles and Modern Transportation Systems. Available at SSRN 5267884.
- Dalal, A. (2025). Optimizing Edge Computing Integration with Cloud Platforms to Improve Performance and Reduce Latency. Available at SSRN 5268128.
- Arora, A. (2025). THE IMPACT OF GENERATIVE AI ON WORKFORCE PRODUCTIVITY AND CREATIVE PROBLEM SOLVING. Available at SSRN 5268208.
- Sidharth, S. (2019). Data loss prevention (DLP) strategies in cloud-hosted applications.
- Sivaprakash, P., Priya, S. S., Maheswari, K., Rubini, B., Karthikeyan, N., & Shuriya, B. (2025). Patent search classification model for service robots field using deep learning approach. International Journal of Robotics & Automation, 40(1), 15–22. [CrossRef]
- Kumar, T. V. (2022). AI-Powered Fraud Detection in Real-Time Financial Transactions.
- Singh, H. (2025). Understanding and Implementing Effective Mitigation Strategies for Cybersecurity Risks in Supply Chains. Available at SSRN 5267866.
- Dalal, A. (2025). Exploring Emerging Trends in Cloud Computing and Their Impact on Enterprise Innovation. Available at SSRN 5268114.
- Sidharth, S. (2019). Enhancing security of cloud-native microservices with service mesh technologies.
- Arora, A. (2025). THE SIGNIFICANCE AND ROLE OF AI IN IMPROVING CLOUD SECURITY POSTURE FOR MODERN ENTERPRISES. Available at SSRN 5268192.
- Singh, B. (2025). Shifting Security Left Integrating DevSecOps into Agile Software Development Lifecycles. Available at SSRN 5267963.
- Shuriya, M. B. (2015). An efficient role mining – RBAM with constraint satisfaction problem.
- Sidharth, S. (2019). Quantum-enhanced encryption methods for securing cloud data.
- Singh, H. (2025). Securing High-Stakes Digital Transactions: A Comprehensive Study on Cybersecurity and Data Privacy in Financial Institutions. Available at SSRN 5267850.
- Dalal, A. (2023). Data Management Using Cloud Computing. Available at SRN 5198760.
- Arora, A. (2025). Developing Generative AI Models That Comply with Privacy Regulations and Ethical Principles. Available at SSRN 5268204.
- Singh, B. (2025). DevSecOps: A Comprehensive Framework for Securing Cloud-Native Applications. Available at SSRN 5267982.
- Kumar, T. V. (2025). Scalable Kubernetes Workload Orchestration for Multi-Cloud Environments.
- Singh, H. (2025). How Generative AI is Revolutionizing Scientific Research by Automating Hypothesis Generation. Available at SSRN 5267912.
- Dalal, A. (2025). BRIDGING OPERATIONAL GAPS USING CLOUD COMPUTING TOOLS FOR SEAMLESS TEAM COLLABORATION AND PRODUCTIVITY. Available at SSRN 5268126.
- Arora, A. (2025). Transforming Cybersecurity Threat Detection and Prevention Systems Using Artificial Intelligence. Available at SSRN 5268166.
- Singh, B. (2025). Enhancing Oracle Database Security with Transparent Data Encryption (TDE) Solutions. Available at SSRN 5267924.
- Kumar, T. V. (2015). Analysis of SQL and NoSQL Database Management Systems Intended for Unstructured Data.
- Singh, H. (2025). The Future of Generative AI: Opportunities, Challenges, and Industry Disruption Potential. (May 23, 2025).
- Dalal, A., et al. (2025, February). Developing a Blockchain-Based AI-IoT Platform for Industrial Automation and Control Systems. In IEEE CE2CT (pp. 744–749).
- Shuriya, B., & Rajendran, A. (2017). Tranquilize role mining using HR (Heuristic Random) approach. Asian Journal of Research in Social Sciences and Humanities, 7(1), 744–753. [CrossRef]
- Singh, B. (2025). Integrating Security Seamlessly into DevOps Development Pipelines Through DevSecOps: A Holistic Approach to Secure Software Delivery. Available at SSRN 5267955.
- Kumar, T. V. (2019). Cloud-Based Core Banking Systems Using Microservices Architecture.
- Singh, H. (2025). Leveraging Cloud Security Audits for Identifying Gaps and Ensuring Compliance with Industry Regulations. Available at SSRN 5267898.
- Dalal, A. (2025). Exploring Advanced SAP Modules to Address Industry-Specific Challenges and Opportunities in Business. Available at SSRN 5268100.
- Arora, A. (2025). Analyzing Best Practices and Strategies for Encrypting Data at Rest (Stored) and Data in Transit (Transmitted) in Cloud Environments. Available at SSRN 5268190.
- Singh, B. (2025). Advanced Oracle Security Techniques for Safeguarding Data Against Evolving Cyber Threats. Available at SSRN 5267951.
- Kumar, T. V. (2016). Multi-Cloud Data Synchronization Using Kafka Stream Processing.
- Singh, H. (2025). The Role of Multi-Factor Authentication and Encryption in Securing Data Access of Cloud Resources in a Multitenant Environment. Available at SSRN 5267886.
- Dalal, A. (2025). Harnessing the Power of SAP Applications to Optimize Enterprise Resource Planning and Business Analytics. Available at SSRN 5268096.
- Arora, A. (2025). Zero Trust Architecture: Revolutionizing Cybersecurity for Modern Digital Environments. Available at SSRN 5268151.
- Singh, B. (2025). Practices, and Implementation Strategies. (May 23, 2025).
- Kumar, T. V. (2019). Personal Finance Management Solutions with AI-Enabled Insights.
- Singh, H. (2025). Evaluating AI-Enabled Fraud Detection Systems for Protecting Businesses from Financial Losses and Scams. Available at SSRN 5267872.
- Dalal, A. (2025). The Research Journal (TRJ): A Unit of I2OR. Available at SSRN 5268120.
- Arora, A. (2025). The Future of Cybersecurity: Trends and Innovations Shaping Tomorrow’s Threat Landscape. Available at SSRN 5268161.
- Singh, H. (2025). Strengthening Endpoint Security to Reduce Attack Vectors in Distributed Work Environments. Available at SSRN 5267844.
- Jha, K., Dhakad, D., & Singh, B. (2020). Critical Review on Corrosive Properties of Metals and Polymers in Oil and Gas Pipelines. In Advances in Materials Science and Engineering: Select Proceedings of ICFMMP 2019 (pp. 99–113).
- Singh, B. (2025). Challenges and Solutions for Adopting DevSecOps in Large Organizations. Available at SSRN 5267971.
- Kumar, T. V. (2020). Generative AI Applications in Customizing User Experiences in Banking Apps.
- Singh, H. (2025). Building Secure Generative AI Models to Prevent Data Leakage and Ethical Misuse. Available at SSRN 5267908.
- Singh, B. (2025). Building Secure Software Faster with DevSecOps Principles, Practices, and Implementation Strategies. (May 23, 2025).
- Arora, A. (2025). Integrating DevSecOps Practices to Strengthen Cloud Security in Agile Development Environments. Available at SSRN 5268194.
- Singh, H. (2025). Key Cloud Security Challenges for Organizations Embracing Digital Transformation Initiatives. Available at SSRN 5267894.
- Dalal, A. (2025). The Research Journal (TRJ): A Unit of I2OR. Available at SSRN 5268120.
- Shuriya, B., Kumar, S. V., & Bagyalakshmi, K. (2024). Noise-resilient homomorphic encryption: A framework for secure data processing in healthcare domain. arXiv preprint arXiv:2412.11474.
- Dalal, A. (2025). Driving Business Transformation Through Scalable and Secure Cloud Computing Infrastructure Solutions. Aryendra Dalal, Deloitte. Available at SSRN 5268120.
- Singh, H. (2025). Artificial Intelligence and Robotics Transforming Industries with Intelligent Automation Solutions. Available at SSRN 5267868.
- Kumar, T. V. (2017). Cross-Platform Mobile Application Architecture for Financial Services.
- Singh, B. (2025). Enhancing Real-Time Database Security Monitoring Capabilities Using Artificial Intelligence. Available at SSRN 5267988.
- Singh, H. (2025). Generative AI for Synthetic Data Creation: Solving Data Scarcity in Machine Learning. Available at SSRN 5267914.
- Kumar, T. V. (2015). Serverless Frameworks for Scalable Banking App Backends.
- Singh, H. (2025). The Importance of Cybersecurity Frameworks and Constant Audits for Identifying Gaps, Meeting Regulatory and Compliance Standards. Presented in May 2025.
- Arora, A. (2025). Comprehensive Cloud Security Strategies for Protecting Sensitive Data in Hybrid Cloud Environments.
- Singh, H. (2025). The Role of Multi-Factor Authentication and Encryption in Securing Data Access of Cloud Resources in a Multitenant Environment. Available at SSRN 5267886.
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).