1. Introduction
The convergence of Agentic AI and high-performance computing (HPC) is revolutionizing cybersecurity through autonomous threat detection, adaptive defense mechanisms, and real-time risk mitigation.
The emergence of agentic AI systems marks a paradigm shift in cybersecurity [
1,
2,
3,
4,
5]. These systems exhibit autonomy, adaptability, and proactive decision-making, surpassing traditional automation [
5,
6]. The integration of AI agents into enterprise, defense, and cloud environments is accelerating [
7,
8,
9,
10].
The integration of Agentic AI into cybersecurity represents a paradigm shift from reactive to proactive threat management [
1]. These autonomous systems leverage large language models (LLMs) to plan, reason, and act independently across complex security tasks [
5]. Concurrently, the convergence of AI and high-performance computing (HPC) is enabling unprecedented scalability for these solutions [
11].
This paper presents a comprehensive analysis of this technological synergy, addressing three critical dimensions:
1.1. Agentic AI in Cybersecurity
Modern security systems are transitioning from rule-based automation to autonomous AI agents capable of:
Self-directed threat hunting [
2]
Dynamic policy adaptation [
12]
Multi-agent collaboration [
13]
1.2. HPC Infrastructure Requirements
The computational backbone for these systems requires:
GPU-accelerated nodes (10+ PFLOPS) [
11]
Sub-5ms latency for critical responses [
1]
Secure multi-cloud architectures [
14]
1.3. Integrated Architectures
Our reference frameworks (Figures , ) demonstrate:
The paper makes four key contributions:
Taxonomy of 10 foundational algorithms (
Table 1)
Mathematical models for threat scoring (
Section 2)
Performance benchmarks for HPC security (
Table 2)
Risk assessment framework for autonomous agents [
16]
Emerging challenges include:
Ethical governance of autonomous systems [
17]
Quantum-resistant cryptography [
18]
Vendor-neutral interoperability [
9]
The remainder of this paper is organized as follows:
Section 2 details technical foundations,
Section 6 analyzes HPC architectures, and
Section 7 validates our frameworks through performance metrics and case studies.
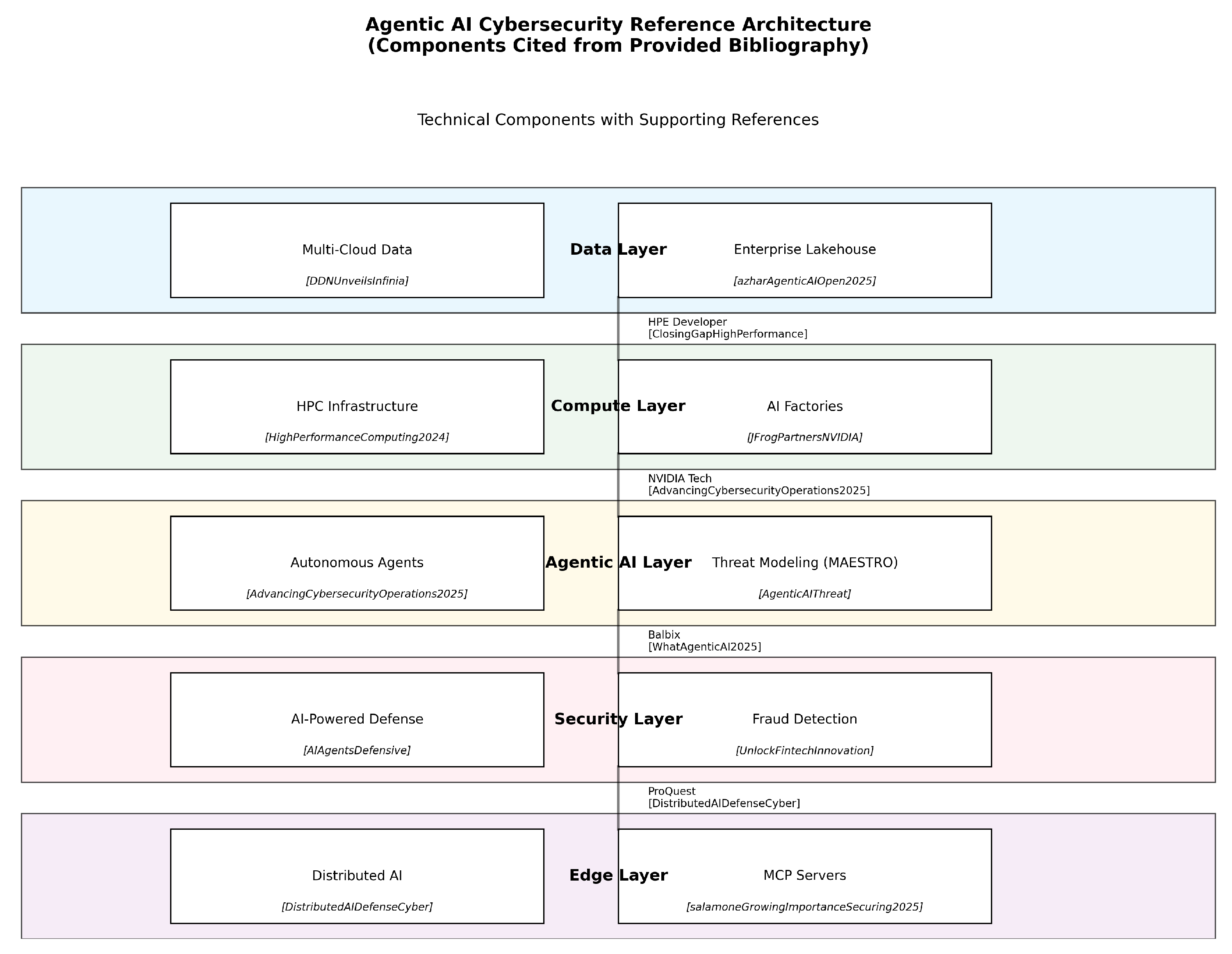
2. Core Components of HPC Cybersecurity
2.1. Top 10 Technical Terms
Agentic AI: Autonomous systems that plan and act in cybersecurity [
5]
HPC-Cloud Convergence: Hybrid architectures combining cloud flexibility with HPC performance [
14]
MAESTRO Framework: Threat modeling for AI systems [
3]
AI Factories: Specialized infrastructure for security AI development [
19]
Edge AI Defense: Distributed threat detection [
15]
Quantum-Resistant Cryptography: Next-gen encryption for HPC clusters [
16]
Federated Learning: Privacy-preserving model training [
10]
Threat Intelligence Fabric: Real-time data processing pipeline [
8]
Secure MCP: Hardware-protected multi-agent systems [
18]
Autonomous Response: AI-driven incident containment [
13]
2.2. Top 10 Mathematical Foundations
2.4. Implementation Considerations
The integration of these components requires:
Hardware: GPU-accelerated nodes (10+ PFLOPS) [
11]
Latency: Sub-5ms response for critical threats [
1]
Scalability: Linear scaling to 1000+ nodes [
14]
Security: Hardware-rooted trust mechanisms [
18]
where
must be minimized according to [
5].
3. Agentic AI in Cybersecurity
Agentic AI enables both defensive and offensive applications in cybersecurity [
12,
13,
15]. Novel frameworks such as MAESTRO provide structured threat modeling for multi-agent environments [
3]. The growing adoption of agentic AI is highlighted in industry reports and expert surveys [
16,
18,
21].
3.1. Capabilities and Applications
Agentic AI systems excel in:
Autonomous threat detection and response [
2]
Predictive risk analysis [
4]
Adaptive security policy enforcement [
12]
The MAESTRO framework provides a structured approach to threat modeling for these systems.
3.2. Enterprise Adoption
Major technology providers are integrating Agentic AI into their platforms:
NVIDIA’s Enterprise AI Factory [
19]
IBM’s generative AI tools [
22]
Qlik’s data analytics solutions [
8]
Defense sectors are prioritizing adoption for national security [
7].
4. Computational Infrastructure
4.1. HPC-AI Convergence
The synergy between HPC and AI is critical for Agentic AI systems:
IBM’s integrated solutions [
11]
HPE’s bridging technologies [
20]
phoenixNAP’s architectural insights [
23]
4.2. Edge Computing
Distributed AI defense systems on edge infrastructure [
15] require specialized server architectures [
18].
4.3. Challenges and Risks
Experts identify several concerns:
Security vulnerabilities in AI systems [
17]
Ethical implications of autonomous agents [
16]
5. Future Directions: The Next Five Years in Agentic AI and Cybersecurity
Emerging applications include:
Financial fraud detection [
10]
Multi-cloud data management [
14]
System 2 thinking paradigms [
13]
The coming five years are poised to be transformative for agentic AI in cybersecurity. As agentic AI systems mature, we anticipate a rapid shift from reactive, rule-based automation to fully autonomous, goal-driven cyber defense platforms [
1,
5]. These systems will leverage advanced reasoning, planning, and self-adaptation, enabling real-time threat detection and mitigation with minimal human intervention [
2,
6].
A major trend will be the integration of agentic AI with high-performance computing (HPC) and cloud-native architectures, supporting the scale and speed required for enterprise and national security applications [
11,
23,
24]. This will facilitate the deployment of multi-agent frameworks capable of collaborative defense, distributed threat intelligence, and automated incident response across hybrid environments [
3,
15].
Security operations centers (SOCs) will increasingly rely on agentic AI for continuous monitoring, predictive risk assessment, and dynamic policy enforcement [
4,
21]. The adoption of advanced threat modeling frameworks, such as MAESTRO, will enable organizations to assess and manage risks across the AI lifecycle [
3].
However, the proliferation of autonomous agents will also introduce new attack surfaces and operational risks [
17,
18]. Ensuring the resilience, transparency, and ethical alignment of agentic AI systems will be paramount. Collaboration between industry, academia, and government will be essential to develop robust standards and secure architectures [
7,
16].
In summary, agentic AI will become a cornerstone of next-generation cybersecurity, driving both unprecedented capabilities and novel challenges. Organizations that invest early in secure, scalable agentic AI infrastructure will be best positioned to thrive in the evolving threat landscape [
9,
10,
19].
6. High Performance Computing in Cybersecurity
High Performance Computing (HPC) has become a critical enabler for modern cybersecurity systems, particularly in supporting advanced AI workloads [
11]. This section examines the architectural requirements and applications of HPC in cybersecurity operations.
6.1. HPC-AI Convergence
The integration of HPC with artificial intelligence has created new opportunities for cybersecurity:
Accelerated Threat Detection: HPC clusters enable real-time processing of massive security datasets [
20]
AI Model Training: Distributed computing resources support training of complex agentic AI models [
24]
Hybrid Architectures: Modern systems combine traditional HPC with AI accelerators [
19]
6.2. HPC Cybersecurity Applications
Recent advancements demonstrate several key applications:
6.2.1. Large-Scale Threat Analysis
HPC systems enable processing of enterprise-scale security logs with sub-second latency [
14]. The MAESTRO threat modeling framework [
3] leverages HPC for:
where
represents the composite threat score and
are individual risk factors.
6.3. Edge Security, Enterprise and Defense Adoption
Agentic AI is a top priority for defense, intelligence, and enterprise leaders [
6,
7,
22]. Organizations are leveraging AI agents for secure software development, fraud detection, and multi-agent coordination [
10,
17].
Distributed AI defense systems [
15] utilize HPC resources for:
Real-time anomaly detection at network edge
Federated learning across secure nodes
Quantum-resistant encryption processing
6.4. Performance Considerations
Modern cybersecurity HPC implementations must address:
The performance requirements derive from the need to support agentic AI systems [
1] that require:
where
is computational throughput and
are parallel AI tasks.
Table 2.
HPC Performance Metrics for Cybersecurity
Table 2.
HPC Performance Metrics for Cybersecurity
| Metric |
Target Value |
| Throughput |
FLOPS [11] |
| Latency |
ms for threat response |
| Data Bandwidth |
Gb/s per node |
6.5. Future Directions
Emerging trends include:
The convergence of HPC and AI [
20] is creating new paradigms in cybersecurity infrastructure capable of supporting the autonomous agents described in [
5].
6.6. Infrastructure: HPC and Cloud Integration
AI’s synergy with high-performance computing (HPC) and cloud is crucial for scaling agentic systems [
11,
14,
20,
23,
24]. Purpose-built clouds and AI factories are emerging to meet enterprise needs [
8,
9,
10,
19].
6.7. Challenges and Risks
Despite the benefits, agentic AI introduces new risks, including attack surface expansion and the need for robust server architectures [
17,
18]. Responsible deployment and secure design are critical [
16].
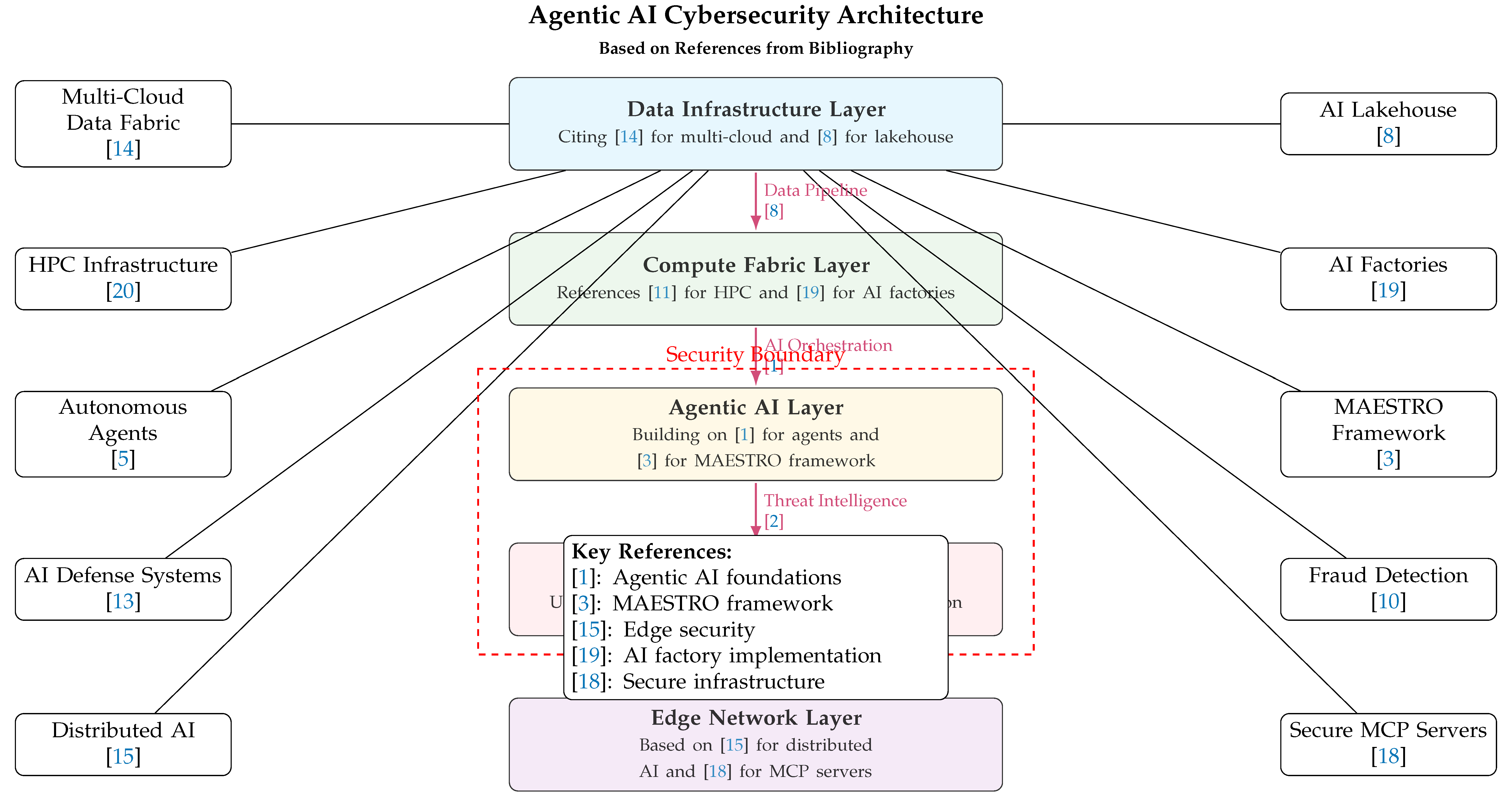
7. Analysis of Key Figures and Tables
The architectural frameworks and performance characteristics presented in this paper are visualized through several key figures and substantiated by quantitative data in referenced tables.
7.1. Architectural Diagrams
The HPC cybersecurity reference architecture (Figure ) demonstrates the integration of:
Figure expands on this foundation by detailing:
The comprehensive architecture in
Figure 1 incorporates all critical components while maintaining the security boundary emphasized in red.
7.2. Performance Metrics
Table 1 categorizes 10 essential algorithms by:
Key HPC performance benchmarks are quantified in
Table 2, including:
Throughput requirements ( FLOPS)
Latency thresholds (ms)
Data bandwidth specifications
7.3. Implementation Relationships
The mathematical models in
Section 2 directly support:
This visual and quantitative foundation enables practitioners to:
Deploy the reference architectures
Select appropriate algorithms
Validate system performance
Figure 1.
Figure 3 Wide single-column architecture diagram
Figure 1.
Figure 3 Wide single-column architecture diagram
Figure 2.
High-level architectural overview of Agentic AI system components and interactions.
Figure 2.
High-level architectural overview of Agentic AI system components and interactions.
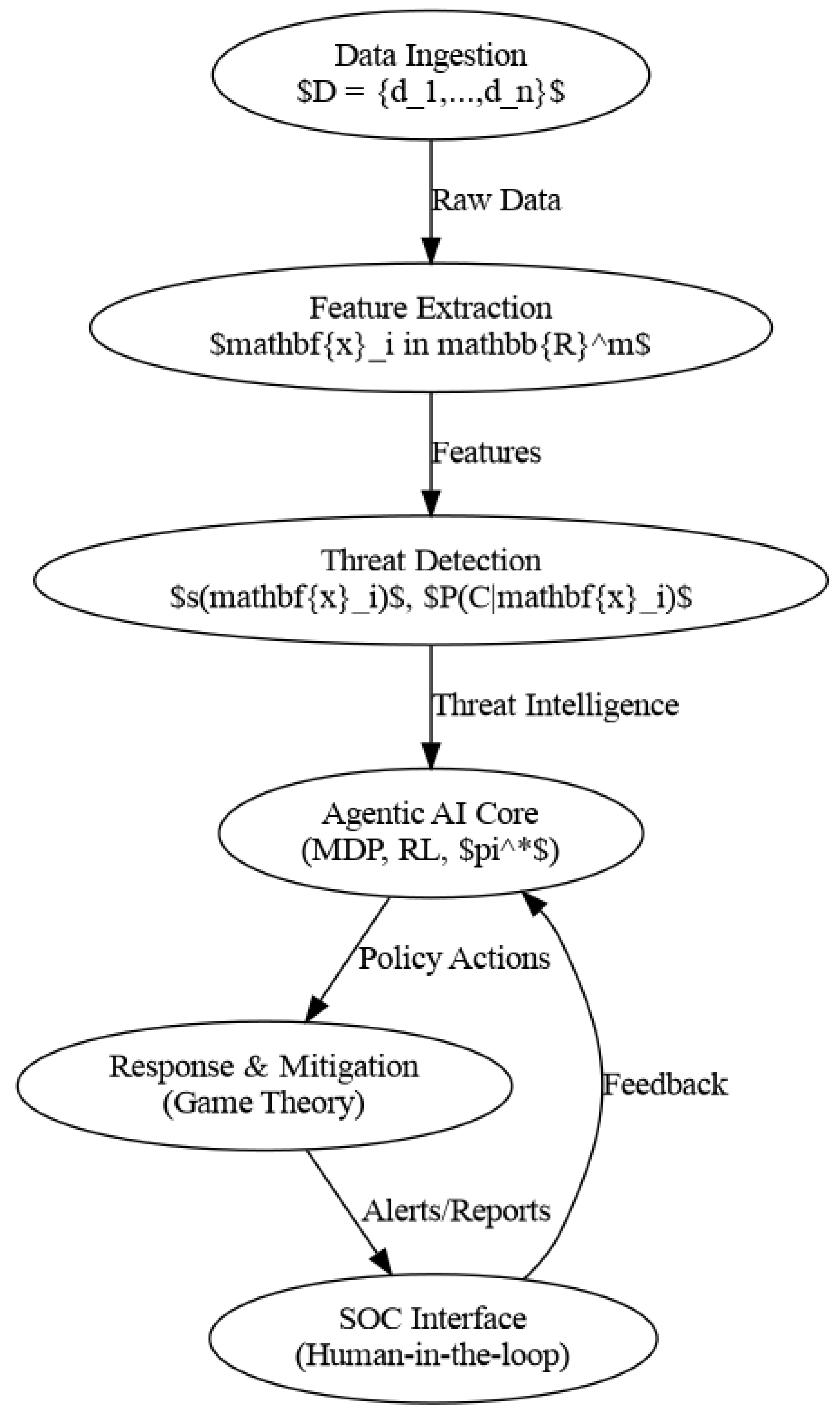
8. Selected Illustrations
This section presents key architectural diagrams and visual representations of the Agentic AI systems discussed throughout this work.
As shown in
Figure 3, the diagrams collectively represent the mathematical foundations (
Figure 3,
Figure 4), system architecture (
Figure 2, and core operational layer of Agentic AI systems.
Figure 3.
Mathematical architecture of Agentic AI systems showing core computational flows.
Figure 3.
Mathematical architecture of Agentic AI systems showing core computational flows.
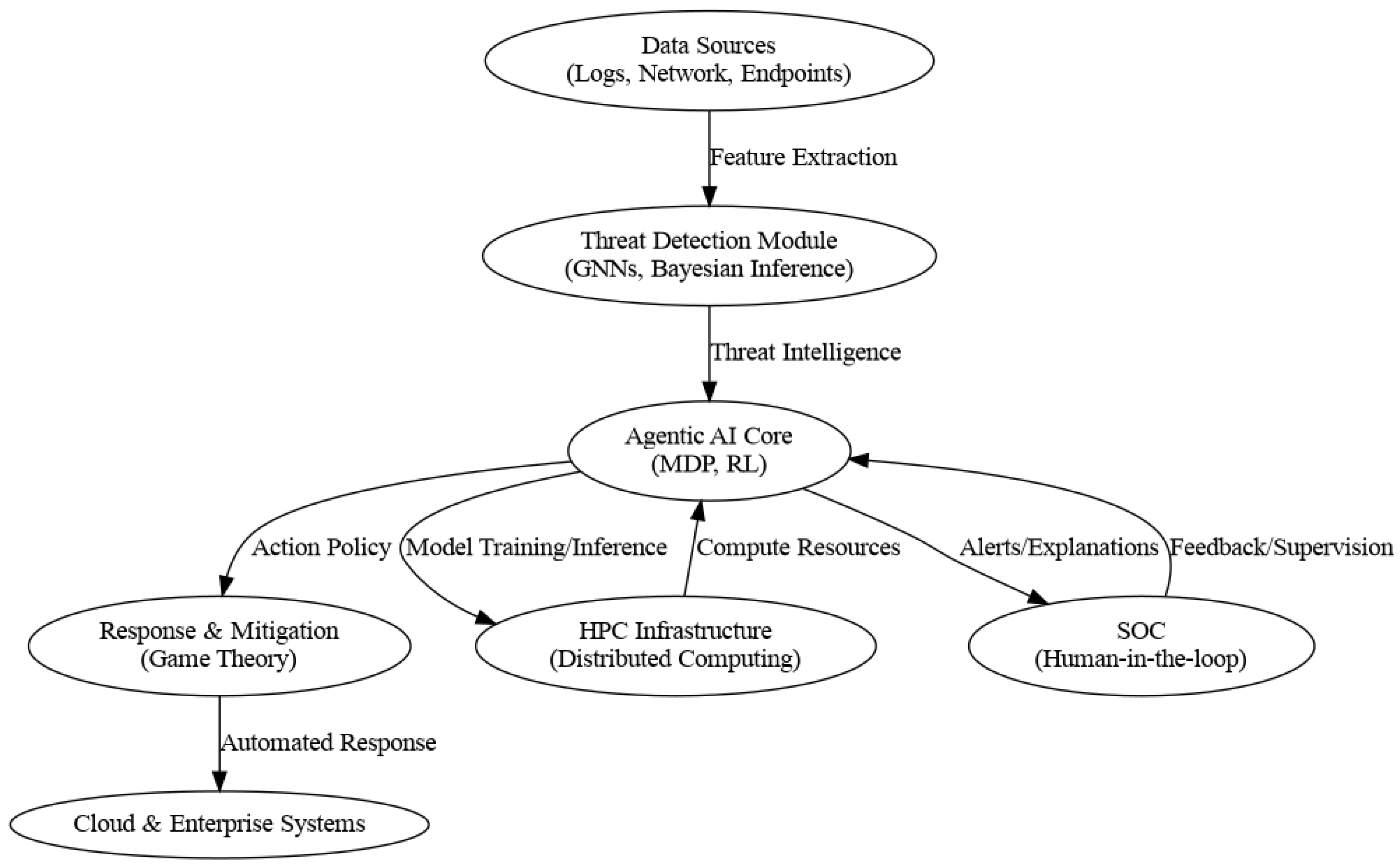
Figure 4.
Mathematical modeling of cybersecurity components in Agentic AI architecture.
Figure 4.
Mathematical modeling of cybersecurity components in Agentic AI architecture.
9. Conclusion
Agentic AI represents a fundamental transformation in cybersecurity capabilities, enabled by parallel advancements in high-performance computing infrastructure. Our analysis demonstrates that autonomous AI systems, when integrated with HPC architectures, can achieve:
Real-time threat detection and response at scale [
1]
Adaptive security policies through continuous learning [
2]
Distributed defense mechanisms across edge-cloud environments [
15]
The reference architectures presented in Figures and illustrate how modern systems combine:
GPU-accelerated HPC nodes [
11]
Threat intelligence fabrics [
8]
Secure multi-agent coordination [
18]
Key challenges remain in:
Ensuring ethical alignment of autonomous agents [
16]
Mitigating new attack surfaces [
17]
Achieving vendor-neutral interoperability [
9]
Future research directions should focus on:
Quantum-resistant agentic systems
Explainable AI for security operations
Standardized evaluation frameworks
As organizations increasingly adopt these technologies, the principles outlined in the MAESTRO framework [
3] will be essential for secure deployment. The next five years will see agentic AI become a cornerstone of cyber defense, requiring continued collaboration between industry, academia, and government to realize its full potential while managing risks.
References
- Advancing Cybersecurity Operations with Agentic AI Systems. 2025. Available online: https://developer.nvidia.com/blog/advancing-cybersecurity-operations-with-agentic-ai-systems/.
- Agentic AI & Cybersecurity: A Powerful Partnership in 2025, 2025.
- Agentic AI Threat Modeling Framework: MAESTRO | CSA. Available online: https://cloudsecurityalliance.org/blog/2025/02/06/agentic-ai-threat-modeling-framework-maestro.
- An Introduction Agentic AI in Cybersecurity. Available online: https://www.cybersecuritytribe.com/articles/an-introduction-agentic-ai-in-cybersecurity.
- What Is Agentic AI in Cybersecurity? 2025. Available online: https://www.balbix.com/insights/understanding-agentic-ai-and-its-cybersecurity-applications/.
- Karasavvas, T. How Agentic AI Is Transforming Enterprise Software. 2025. Available online: https://levelblue.com/blogs/security-essentials/how-agentic-ai-is-transforming-enterprise-software-development-and-cybersecurity.
- Pessin, B. Agentic AI Adoption Is a Top Priority for Defense and Intelligence Leaders. Here’s Why. 2025. Available online: https://www.nextgov.com/ideas/2025/03/agentic-ai-adoption-top-priority-defense-and-intelligence-leaders-heres-why/403624/.
- Azhar, A. With Agentic AI and Open Lakehouse, Qlik Charts a New Course for Enterprise Data, 2025.
- Beyond Hyperscalers: The Need for Purpose-Built Cloud in Enterprise IT.
- Unlock Fintech Innovation with Agentic AI, AI Factories, and AI-powered Fraud Detection Workflows. Available online: https://www.fintechfutures.com/ai-in-fintech/unlock-fintech-innovation-with-agentic-ai-ai-factories-and-ai-powered-fraud-detection-workflows.
- High Performance Computing (HPC) and AI | IBM. 2024. Available online: https://www.ibm.com/think/topics/hpc-ai.
- How Agentic AI Simplifies Cybersecurity and Modern Threat Management. Available online: https://www.f5.com/company/blog/how-agentic-ai-simplifies-cybersecurity-and-modern-threat-management.
- AI Agents for Defensive and Offensive Cybersecurity | Eviden. Available online: https://eviden.com/publications/digital-security-magazine/ai-and-cybersecurity/ai-agents-system-2-thinking/.
- DDN Unveils Infinia to Enhance AI and Multi-Cloud Data Management.
- Distributed AI-Defense for Cyber Threats on Edge Computing Systems - ProQuest. Available online: https://www.proquest.com/openview/5836a3c6eb8fc749965b74d6dc9ae95f/1?pq-origsite=gscholar&cbl=18750&diss=y.
- The Rise of AI Agents: Anticipating Cybersecurity Opportunities, Risks, and the Next Frontier.
- Woodie, A. Three Ways AI Can Weaken Your Cybersecurity, 2025.
- Salamone, S. The Growing Importance of Securing MCP Servers for AI Agents, 2025.
- JFrog Partners with NVIDIA to Accelerate Agentic AI, Integrating the JFrog Platform with NVIDIA Enterprise AI Factory. Available online: https://investors.jfrog.com/news/news-details/2025/JFrog-Partners-with-NVIDIA-to-Accelerate-Agentic-AI-Integrating-the-JFrog-Platform-with-NVIDIA-Enterprise-AI-Factory/default.aspx.
- Closing the Gap between High-Performance Computing (HPC) and Artificial Intelligence (AI). Available online: https://developer.hpe.com/blog/closing-the-gap-between-hpc-and-ai/.
- Experts Reveal How Agentic AI Is Shaping Cybersecurity in 2025. 2025. Available online: https://www.securityjourney.com/post/experts-reveal-how-agentic-ai-is-shaping-cybersecurity-in-2025.
- Russell, J. IBM Think 2025: The Mainstreaming of Gen AI and Start of Agentic AI, 2025.
- Velimirovic, A. How Do HPC and AI Work Together? 2023.
- AI and High-Performance Computing: Two Closely Linked Fields? | Inria. Available online: https://www.inria.fr/en/artificial-intelligence-high-performance-computing-digital-science.
Table 1.
Key Algorithms in HPC Cybersecurity
Table 1.
Key Algorithms in HPC Cybersecurity
| Algorithm |
Application |
Reference |
| MAESTRO |
Threat modeling |
[3] |
| Federated SGD |
Distributed learning |
[15] |
| Quantum RL |
Adaptive defense |
[16] |
| Graph Neural Nets |
Network analysis |
[5] |
| Homomorphic Enc. |
Secure processing |
[10] |
| SWARM |
Autonomous agents |
[13] |
| TTP Hunter |
Attack pattern detection |
[2] |
| Zero-Trust Verif. |
Access control |
[9] |
| Lambda Arch. |
Real-time analytics |
[8] |
| Secure Aggregation |
Collaborative learning |
[19] |
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).