Submitted:
04 July 2025
Posted:
04 July 2025
You are already at the latest version
Abstract
Keywords:
0. Introduction
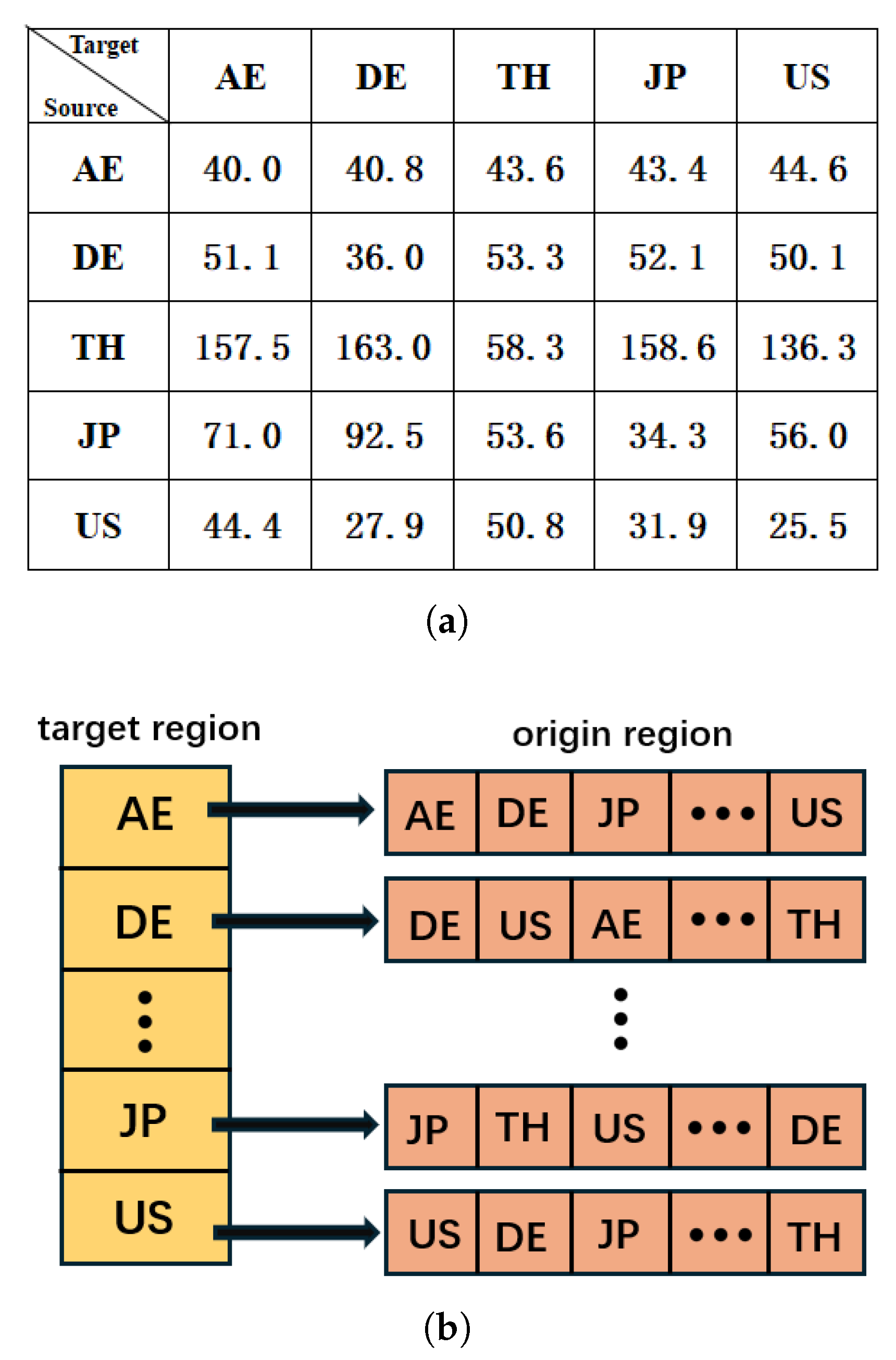
- Through experiments, we introduced the concept of location-aware. Specifically, scanning nodes in a particular country are more efficient when scanning their own country’s IP addresses compared to scanning IP addresses from other countries. This phenomenon indicates that geographical proximity has a significant positive impact on network scanning efficiency.
- We propose a novel location-aware method that overcomes the limitations of geographical factors to achieve efficient network scanning. Using this method, we can more accurately identify live IP addresses across the entire network, significantly improving the detection scanning and accuracy of network resources.
- We conducted experimental analysis in real-world network environments. Compared to existing methods, our scanning efficiency is more effective, thus demonstrating the validity of the proposed method.
1. RELATED WORKS
2. CONSIDERED SCENARIO AND MOTATIVATION
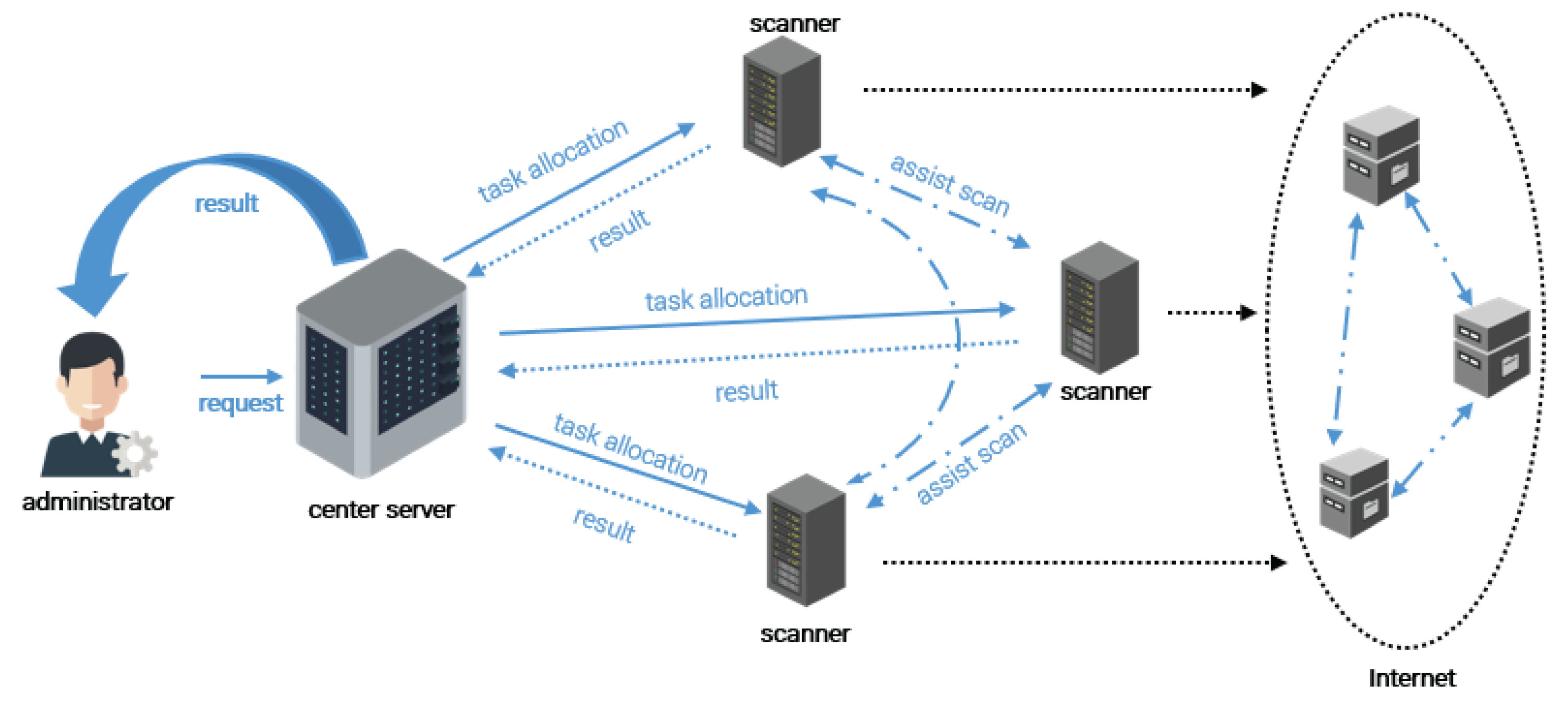
2.1. Considered Scenario
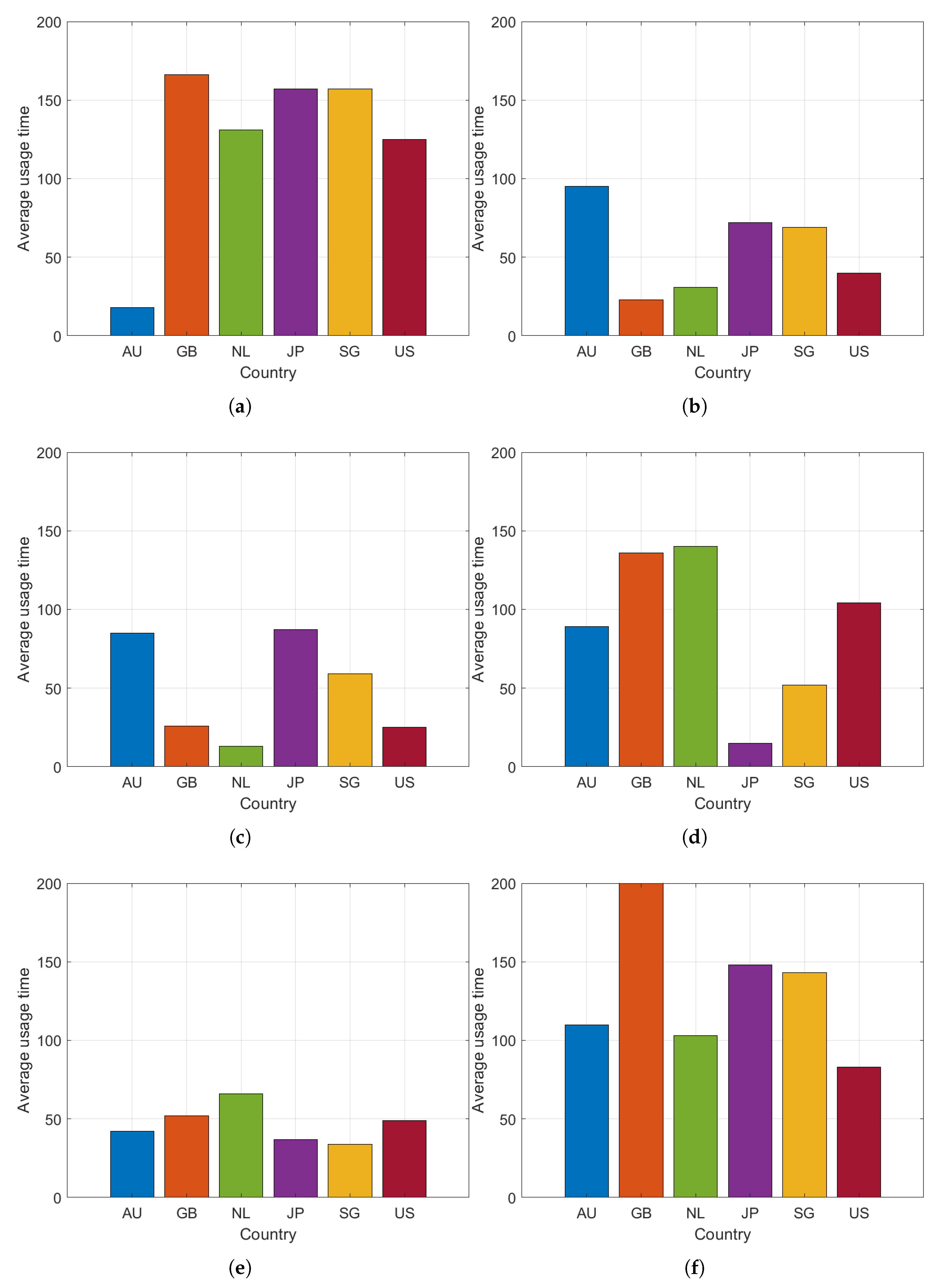
2.2. Motivation
3. PROPOSED APPROACH
3.1. Delay Model
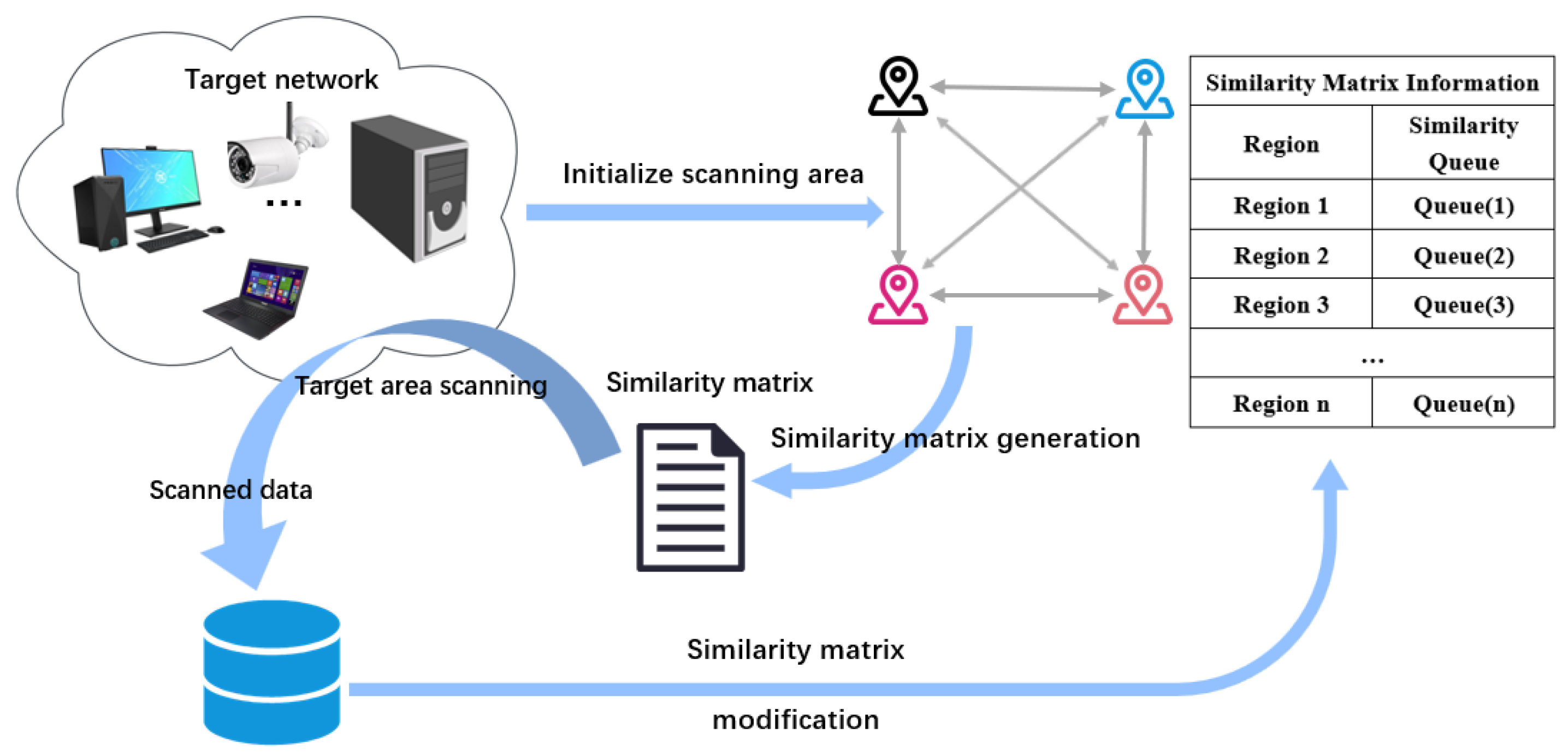
3.2. Overview of Proposed Approach
| Algorithm 1: Efficient Scanning Algorithms for Location-Aware |
 |
3.3. Approach
4. EXPERIMENTS
4.1. Experimental Setup
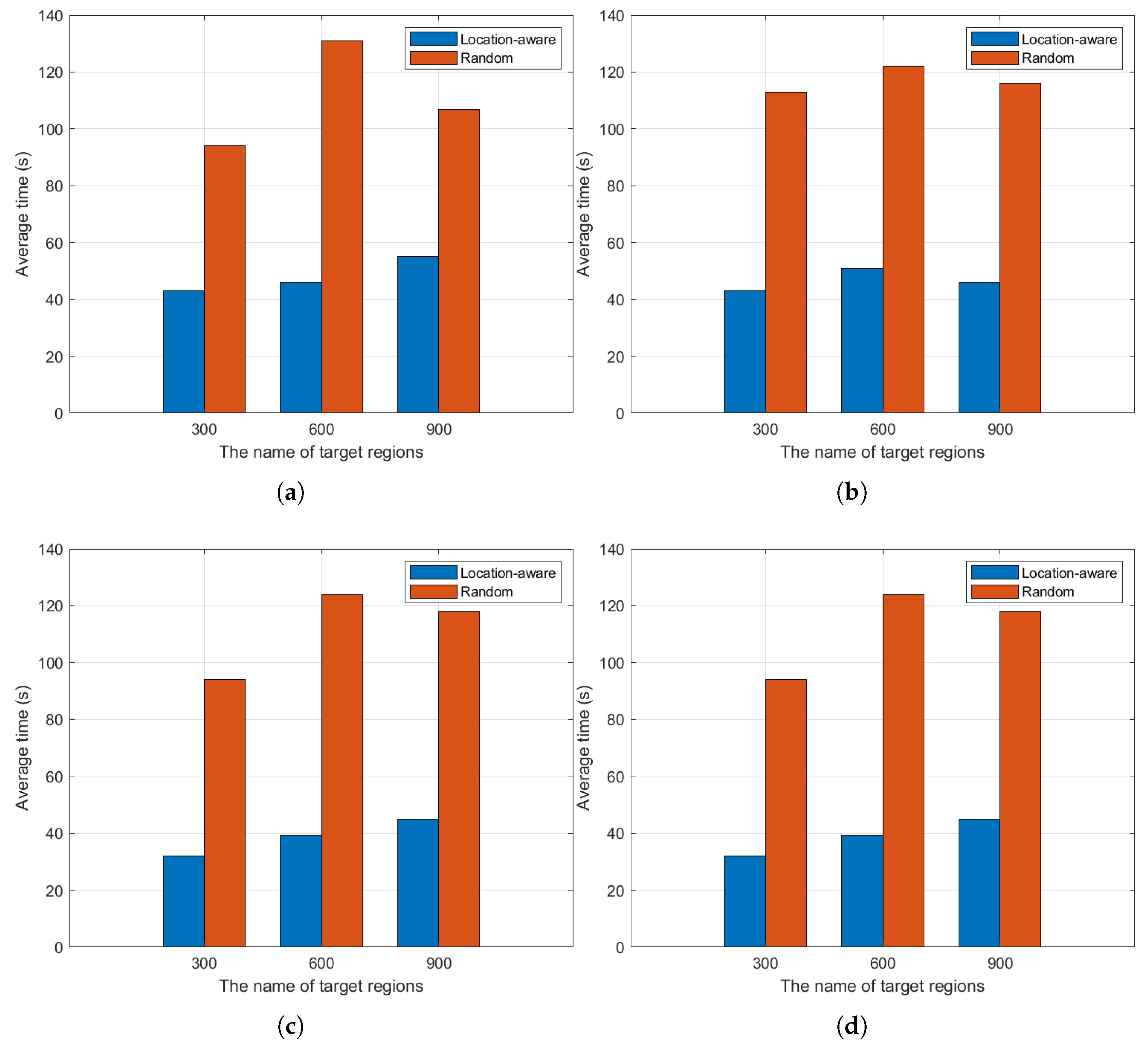
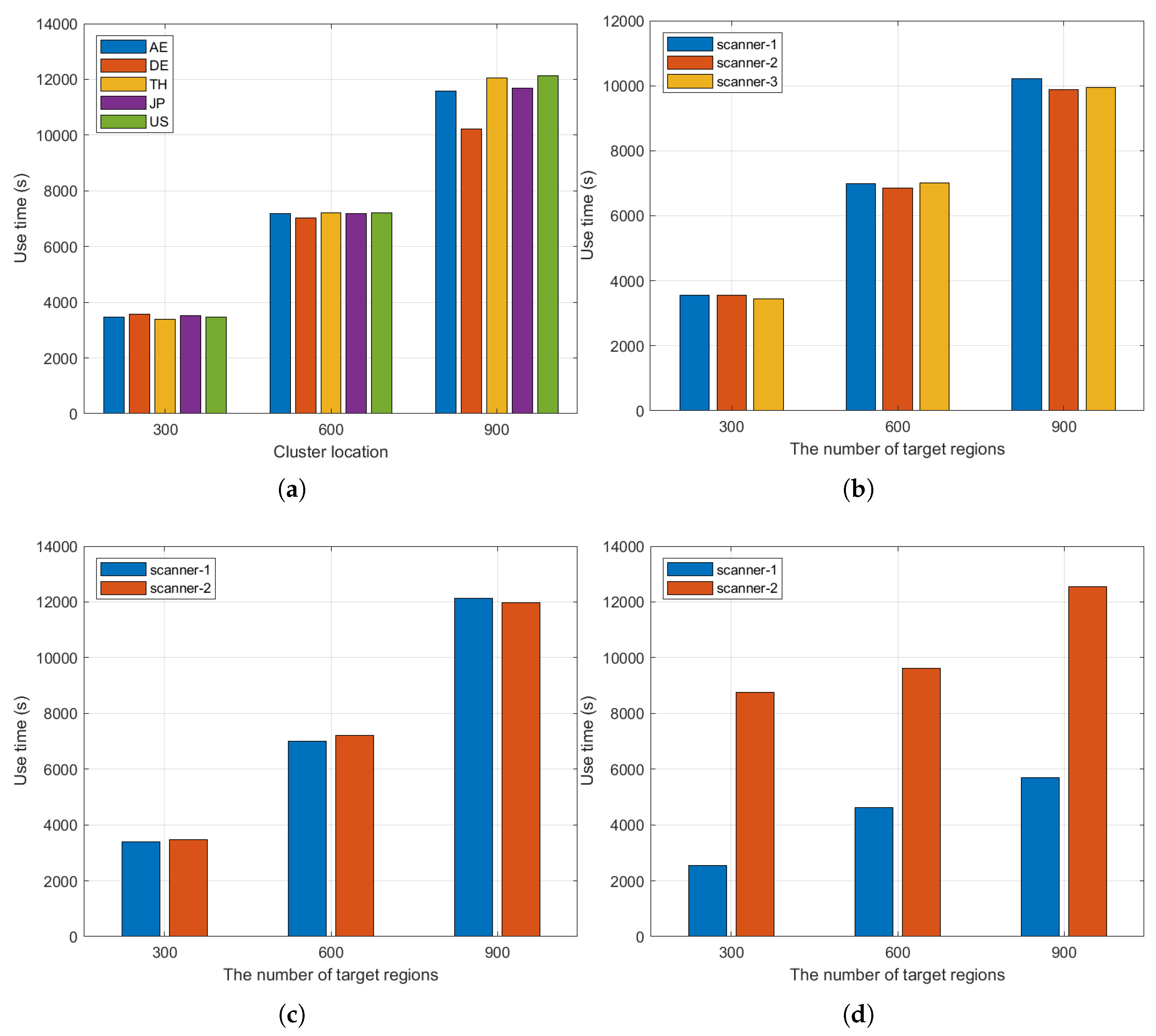
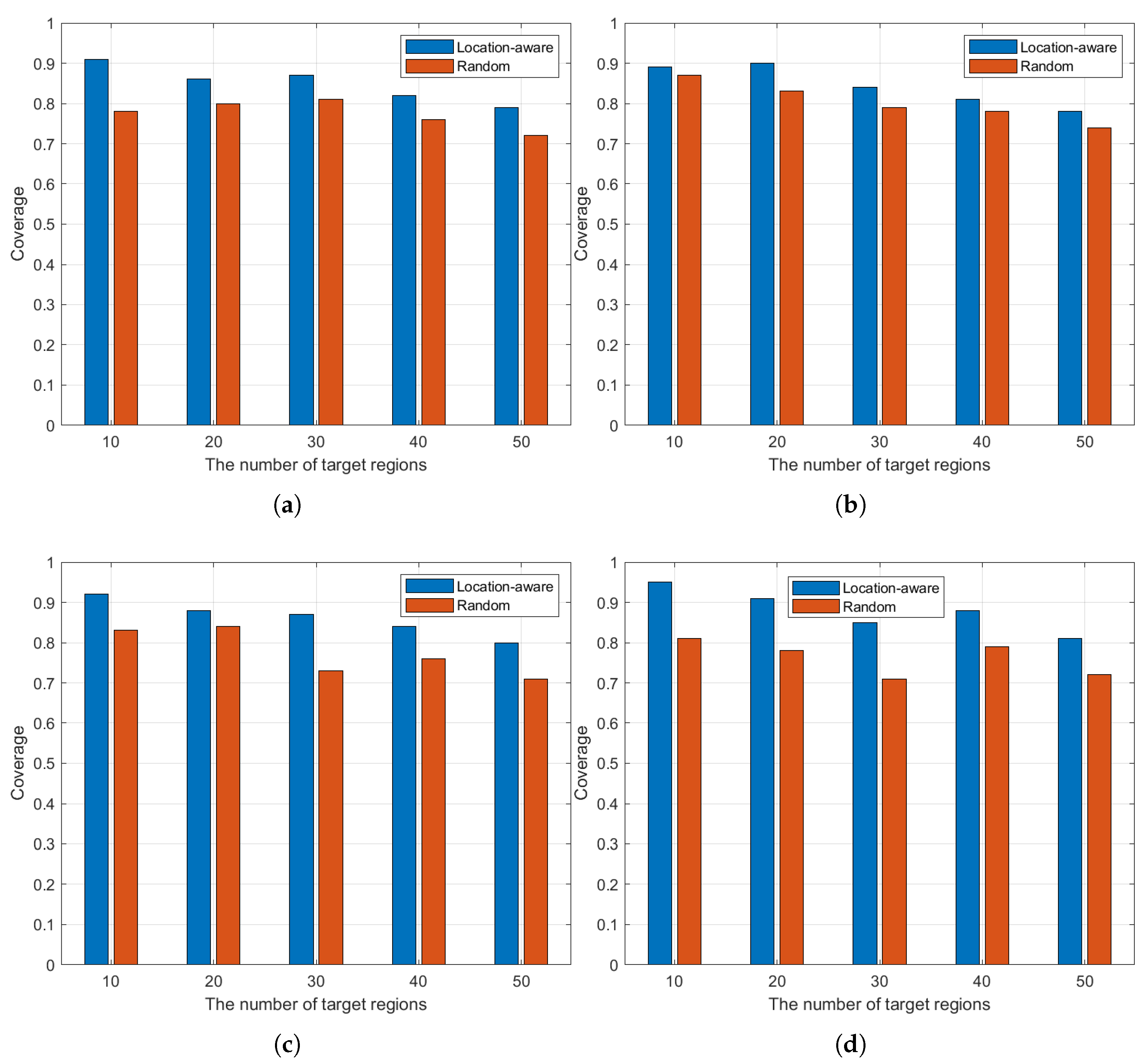
4.2. Experiments Analysis
5. CONCLUSION
References
- Mazurczyk, W.; Caviglione, L. Cyber reconnaissance techniques. Commun. ACM 2021,64, 86-95. [CrossRef]
- Hashida, H.; Kawamoto, Y.; Kato, N. Efficient delay-based internet-wide scanning method for IoT devices in wireless LAN. IEEE Internet Things J. 2020,7, 1364–1374. [CrossRef]
- Song, G.; et al. Which doors are open: Reinforcement learning-based internet-wide port scanning. In Proceedings of the 2023 IEEE/ACM 31st International Symposium on Quality of Service (IWQoS), Orlando, FL, USA, 2023; pp. 1–10. [CrossRef]
- Verma, S.; Kawamoto, Y.; Kato, N. A smart internet-wide port scan approach for improving IoT security under dynamic WLAN environments. IEEE Internet Things J. 2022, 9, 11951–11961. [CrossRef]
- Hou, B.; Cai, Z.; Wu, K.; Su, J.; Xiong, Y. 6Hit: A reinforcement learning-based approach to target generation for internet-wide IPv6 scanning. In Proceedings of the IEEE INFOCOM 2021 - IEEE Conference on Computer Communications, Vancouver, BC, Canada, 2021; pp. 1–10. [CrossRef]
- Hou, B.; Cai, Z.; Wu, K.; Yang, T.; Zhou, T. 6Scan: A high-efficiency dynamic internet-wide IPv6 scanner with regional encoding. IEEE/ACM Trans. Netw. 2023, 31, 1870–1885. [CrossRef]
- Durumeric, Z. ZMap: The Internet Scanner. Available online: https://github.com/zmap/zmap (accessed on 26 July 2019).
- NMAP.ORG. Available online: https://nmap.org/ (accessed on 26 July 2019).
- Wan, G.; Izhikevich, L.; Adrian, D.; Yoshioka, K.; Holz, R.; Rossow, C.; Durumeric, Z. On the origin of scanning: The impact of location on internet-wide scans. In Proceedings of the ACM Internet Measurement Conference (IMC ’20), New York, NY, USA, 2020; pp. 662–679. [CrossRef]
- Verma, S.; Kawamoto, Y.; Kato, N. A novel IoT-aware WLAN environment identification for efficient internet-wide port scan. In Proceedings of the 2020 IEEE Global Communications Conference (GLOBECOM), Taipei, Taiwan, 2020; pp. 1–6. [CrossRef]
- Tang, F.; Kawamoto, Y.; Kato, N.; Yano, K.; Suzuki, Y. Probe delay-based adaptive port scanning for IoT devices with private IP address behind NAT. IEEE Netw. 2020, 34, 195–201. [CrossRef]
- Gong, Q.; Gu, C. A baseline modeling algorithm for internet port scanning radiation flows. In Proceedings of the 2021 IEEE 6th International Conference on Signal and Image Processing (ICSIP), Nanjing, China, 2021; pp. 1255–1259. [CrossRef]
- Yanyan, L.; Shanhou, H. Application of Bayesian optimization in router port testing: An improved port scanning technique. In Proceedings of the 2023 IEEE 5th International Conference on Power, Intelligent Computing and Systems (ICPICS), Shenyang, China, 2023; pp. 98–103. [CrossRef]
- Padmanabhan, R.; Schulman, A.; Levin, D.; Spring, N. Residential links under the weather. In ACM SIGCOMM, 2019.
- Zhu, P.; Man, K.; Wang, Z.; Ensafi, R.; Halderman, J. A.; Duan, H. Characterizing transnational internet performance and the great bottleneck of China. In ACM Sigmetrics, 2020.
- Pearce, P.; Jones, B.; Li, F.; Ensafi, R.; Feamster, N.; Weaver, N.; Paxson, V. Global measurement of DNS manipulation. In USENIX Security Symposium, 2017.
- Hao, H.; Xu, C.; Zhang, W.; Yang, S.; Muntean, G.-M. Task-driven priority-aware computation offloading using deep reinforcement learning. IEEE Trans. Wirel. Commun. 2025, early access. [CrossRef]
- Hao, H.; Xu, C.; Zhang, W.; Yang, S.; Muntean, G.-M. Joint task offloading, resource allocation, and trajectory design for multi-UAV cooperative edge computing with task priority. IEEE Trans. Mob. Comput. 2024, 23, 8649–8663. [CrossRef]
- IP2Location. IP2Location API Open Platform. Available online: https://www.ip2location.com/ (accessed on 26 July 2019).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




