Submitted:
07 May 2025
Posted:
07 May 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
- In the context of cost, coverage, connectivity, energy efficiency, environment suitability, and scalability, what are the most effective deployment strategies for WSNs?
- What is the impact of homogeneous and heterogeneous sensor nodes on the design, functionality, and security of WSNs?
- Particularly in deployment, node types, and security, what are the main obstacles and potential future research directions in WSNs?
2. Classification of Deployment Strategies
2.1. Deployment strategies
| Aspect | Deterministic | Non-Deterministic | 3D |
|---|---|---|---|
| Deployment Cost | Higher due to precise planning, advanced sensors, and relay nodes [11,12] | Lower initial cost due to reduced planning and simple setup [11,20] | Significantly higher due to specialized equipment and precise positioning techniques [5,25,26] |
| Coverage | Full coverage using optimal patterns (e.g., triangular lattices) but susceptible to coverage holes due to placement errors and failures [13,14] | Resilient coverage due to random placement, but higher sensor density is required. Can utilize probabilistic models and mobile nodes to fill gaps [13,20,21] | Ensures coverage in complex 3D spaces using polynomial-time algorithms, distributed algorithms, and multi-objective genetic algorithms [27,28,29] |
| Connectivity | Guaranteed connectivity through strategic placement, even with obstacles [6,15] | Challenges in maintaining connectivity due to random placement; may need additional sensors or increased communication [20,23] | Maintained through truncated octahedron placement and distributed deployment algorithms [30,31] |
| Environment Suitability | Suitable for controlled, known environments with obstacles. Optimized placement for efficient communication [16,17] | Suitable for unknown, hostile environments where precise placement is not feasible. Adaptable and robust to changes [16,17,20] | Suitable for complex terrains like underwater and urban environments but requires line-of-sight and path-loss considerations [29,32] |
| Energy Efficiency | Maximized through strategic placement and optimized communication protocols. Reduced energy consumption due to minimal node movement [9,15] | Challenges due to non-uniform distribution in random deployment. Requires efficient algorithms for movement and energy management [9,20] | Achieved by minimizing active sensors while ensuring coverage, using optimal strategies and 3D-Voronoi partitioning [33,34] |
| Scalability | Demonstrated through optimal node placement strategies based on electrostatic field theory for efficient resource utilization and network performance [18,19] | Enhanced by exploiting spatio-temporal correlations and the ability to deploy large numbers of nodes without precise placement [20,24] | Enhanced through dynamic coordinate systems and virtual architectures for efficient data routing and management [33,35] |
2.2. Deterministic Coverage
2.2.1. Deployment Cost
2.2.2. Coverage
2.2.3. Connectivity
2.2.4. Environmental Suitability
2.2.5. Energy Efficiency
2.2.6. Scalability
2.3. Non-Deterministic Coverage
2.3.1. Deployment Cost
2.3.2. Coverage
2.3.3. Connectivity
2.3.4. Environment Suitability
2.3.5. Energy Efficiency
2.3.6. Scalability
2.4. Three-Dimensional Deployment
2.4.1. Deployment Cost
2.4.2. Coverage
2.4.3. Connectivity
2.4.4. Environment Suitability
2.4.5. Energy Efficiency
2.4.6. Scalability
3. Security Challenge and Solutions
| Authors | Date | Deployment Type | Security Challenge Addressed | Proposed Solution |
|---|---|---|---|---|
| O. Embarak, et al.[41] | 2023 | Deterministic | DoS (e.g., jamming, resource depletion) | ML-based IDS for DoS detection and mitigation. |
| A. Bassey, et al[42] | 2023 | Deterministic | Physical tampering, key compromise | Probabilistic key management using ECC and XOR operations. |
| A. Boualem, et al[43] | 2023 | Deterministic | Targeted, unpredictable attacks | Hybrid Fuzzy-Possibilistic model for node scheduling. |
| A. Khan, et al[44] | 2024 | Deterministic | Clone attacks, intrusion detection | Aperiodic tiling to create unpredictable sensor deployments. |
| Medina, F., et al[45] | 2024 | Deterministic | Coverage holes, network disconnection | Combine deterministic and random deployment for coverage. |
| H. Bian, et al[46] | 2024 | Deterministic | Malicious control, data leakage | Situ-Oracle framework using RNN models for secure analysis. |
| Elsayed et al.[47] | 2024 | Deterministic | Node capture, tampering, eavesdropping | TD3 with sensor fusion (NCNN) for real-time threat response. |
| L. Desgeorges, et al[53] | 2023 | Non Deterministic | Anomalies in SDN control | Dual-controller with ML-based anomaly detection. |
| S. Sharma, et al[52] | 2023 | Non Deterministic | General security threats | Dragonfly algorithm for trust-based node security. |
| P. Arunkumar et al[51] | 2024 | Non-Deterministic | General Security threats | Bat algorithm with Q-learning for secure routing. |
| A. Shah, et al[40] | 2023 | Deterministic & Non Deterministic | DoS: Denial of Sleep | ILSM combining RWM and GWO to optimize routing and energy use. |
| P. Sebothoma, et al[48] | 2023 | Deterministic & Non Deterministic | DoS: Denial of Sleep | DSD-RSA algorithm for attack prevention and energy optimization. |
| V. Prakash, et al[49] | 2023 | Deterministic & Non Deterministic | General security challenges in WSNs | Bio-inspired ACO and PSO algorithms for secure node placement. |
| S. Khan, et al[50] | 2024 | Deterministic & Non Deterministic | Black-hole, gray-hole, wormhole | ANN model to detect and mitigate routing attacks. |
| S. Suma Christal Mary, et al[54] | 2023 | 3D Deployment | Intrusion, wormhole, IP spoofing | Blockchain-based routing with XOR hashing. |
| Y. Kim, et al[55] | 2024 | 3D Deployment | Deployment errors | Simulate 3D terrains to improve key distribution robustness. |
| A. Afghantoloee, et al[56] | 2024 | 3D Deployment | Security challenges in 3D deployment | PO-3DVOR algorithm for optimized sensor placement. |
| S. Hafeez[57] | 2024 | 3D Deployment | DDoS, spoofing, message injection | Blockchain for secure UAV communication and authentication. |
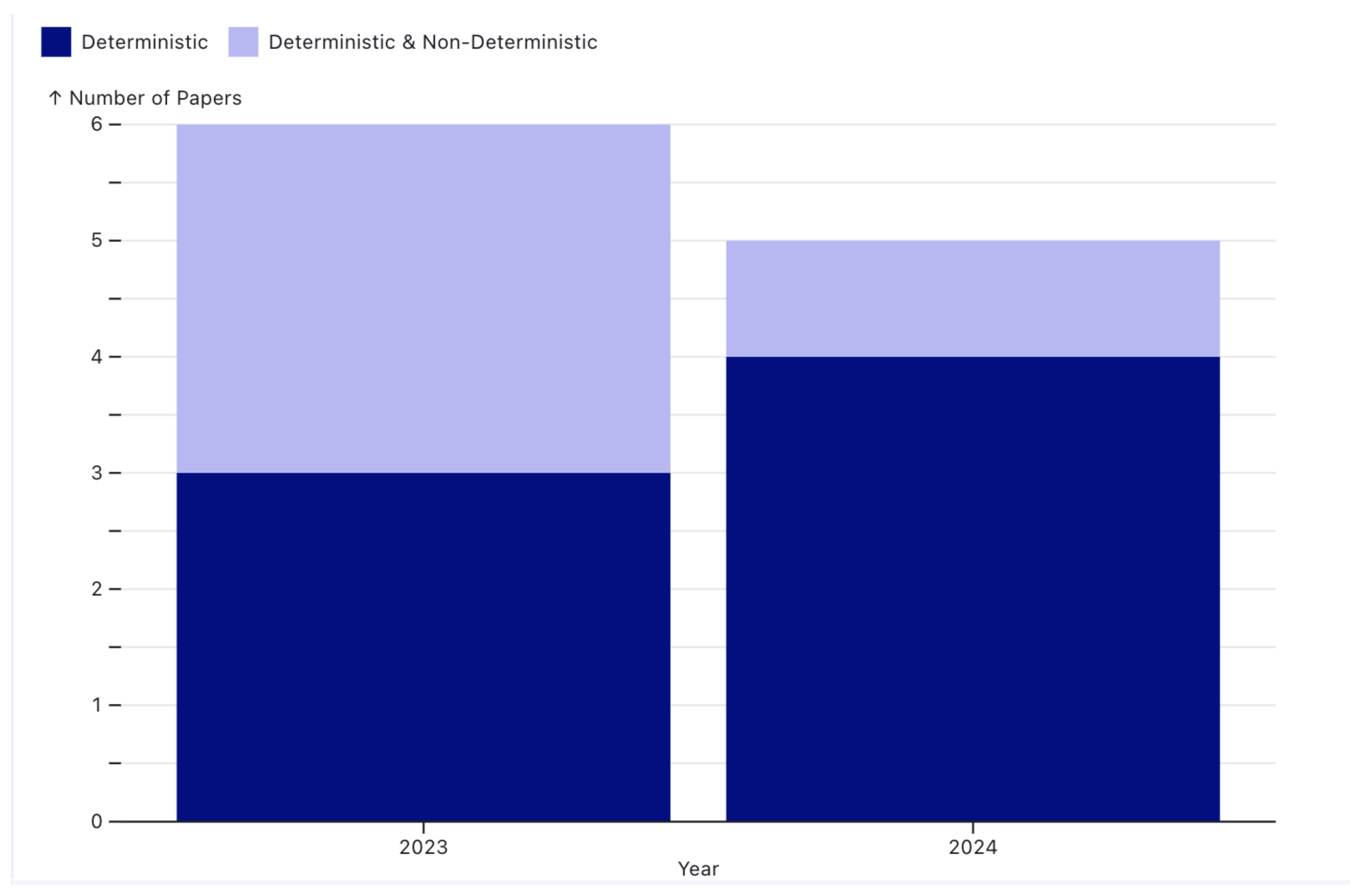
3.1. Deterministic Deployment Security Challenge
3.1.1. Conclusion
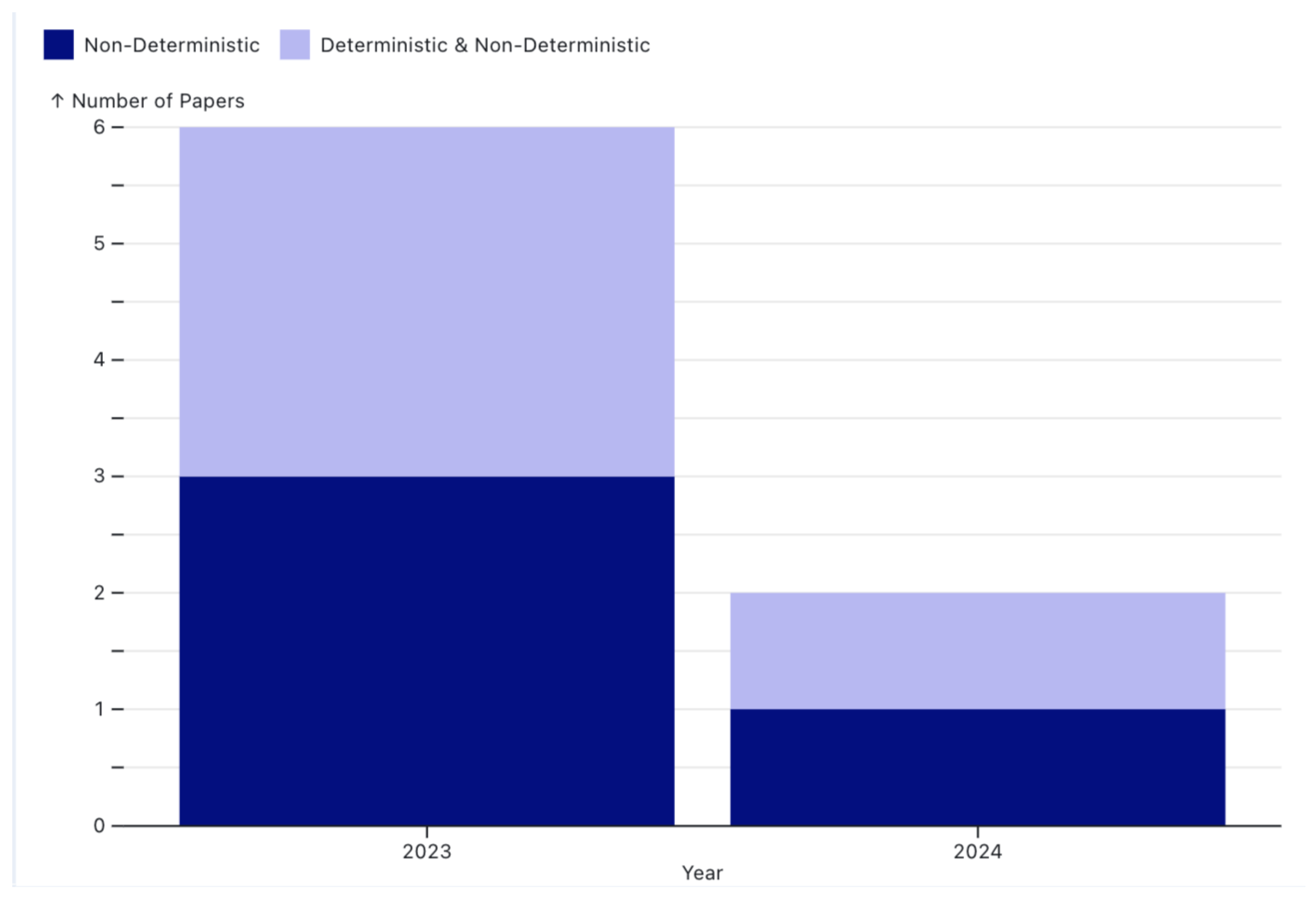
3.2. Non-Deterministic Deployment: Security Challenge
3.2.1. Conclusion
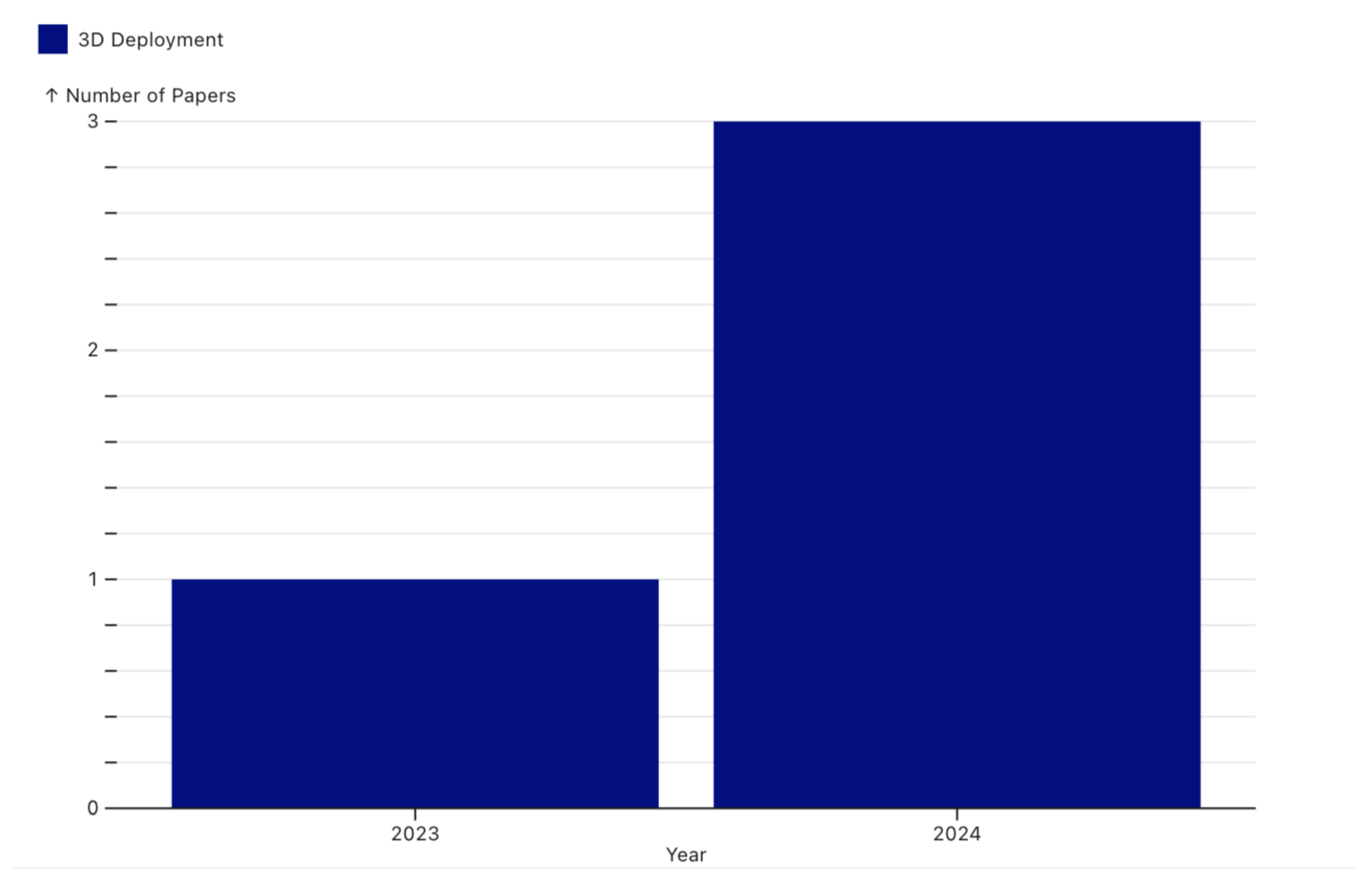
3.3. 3D Deployment Security Challenge
3.3.1. Conclusion
4. Sensor Node Types
| Aspect | Homogeneous Network | Heterogeneous Network |
|---|---|---|
| Definition | Nodes have the same function and are interchangeable | There are two or more classes of nodes categorized by both function and utility |
| Connectivity | Optimized by equal node degrees, long girths, and short path-sums, ensuring efficient and stable communication | Enhances connectivity with low-power nodes within a macro cell network, reducing dead zones |
| Energy Efficiency | Limited by uniform energy consumption across all nodes, leading to early power depletion in some nodes | Utilizes nodes with varying energy levels, extending network lifespan and reducing energy consumption by 40% |
| Node Composition | Nodes with identical hardware and software configurations, ensuring uniform performance. Identifying key nodes is crucial for network stability, using diverse evaluation methods | Includes normal nodes (resource-constrained) and heterogeneous nodes (enhanced resources), improving reliability |
| Node Deployment | Identical nodes deployed deterministically or randomly to ensure adequate coverage and connectivity | Strategic placement of stationary and mobile nodes to optimize coverage and network lifetime |
4.1. Homogeneous Networks
4.1.1. Communication
4.1.2. Energy Efficiency
4.1.3. Node Composition
4.1.4. Classification of Critical Nodes
4.1.5. Node Deployment
4.2. Heterogeneous Networks
4.2.1. Communication
4.2.2. Energy Efficiency
4.2.3. Node Composition
4.2.4. Node Deployment
4.2.5. Classification of Critical Nodes
4.3. Security Challenge and Solutions
4.4. Homogeneous Network Security Challenge
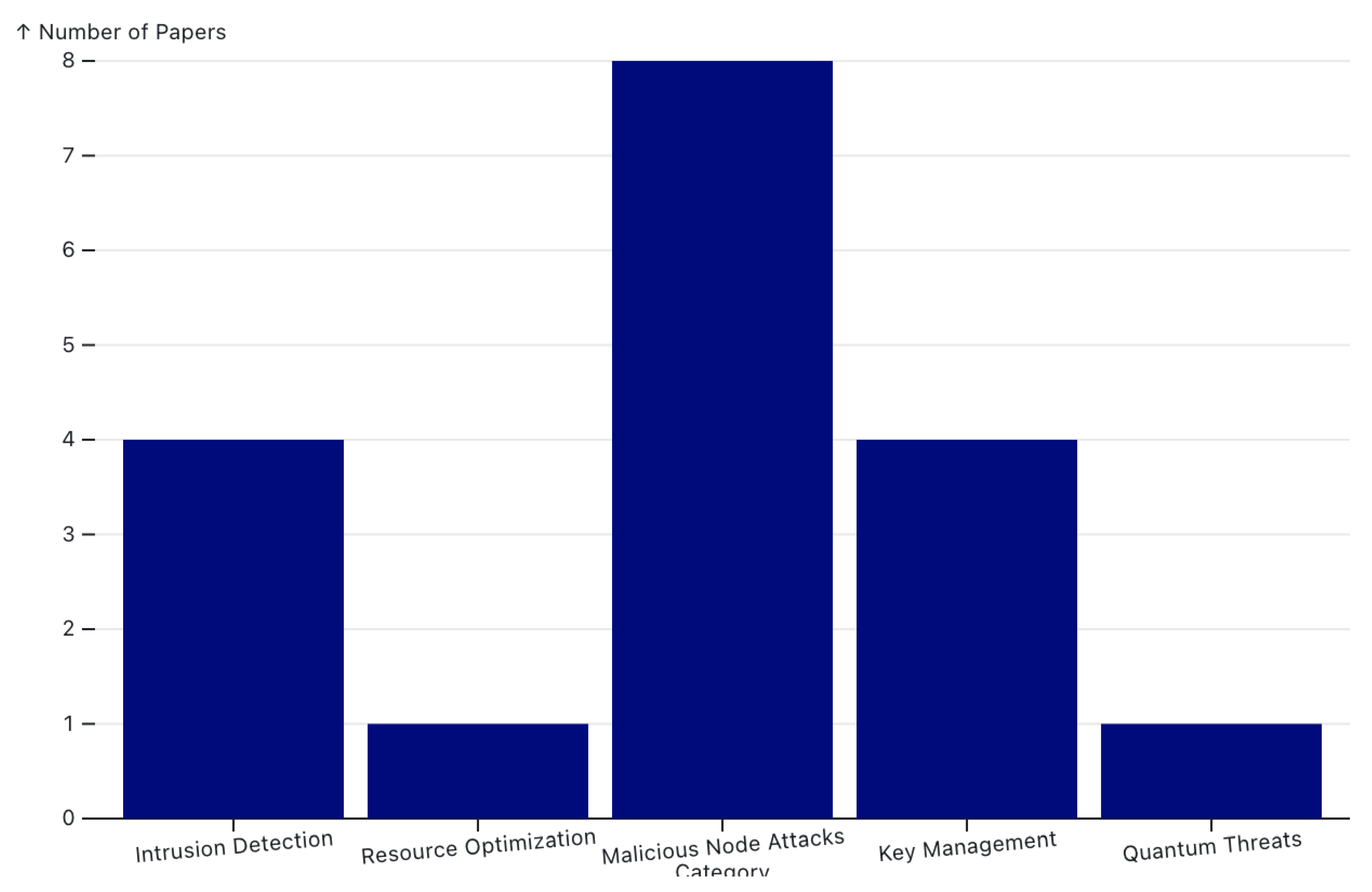
4.4.1. Intrusion Detection
| Authors | Date | Security Challenge Addressed | Proposed Solution |
|---|---|---|---|
| Z. Teng, et al.[91] | 2023 | Malicious Node Attack | TS-BRS reputation model using time series analysis |
| Z. Ahmad Mir, et al.[92] | 2023 | Malicious Node Attack | Gray Wolf Optimization (GWO) for resource allocation and node placement |
| L. Tan, et al.[79] | 2023 | Key Management | Elliptic curve cryptography with AVL search tree and LEACH model |
| S. Urooj, et al.[80] | 2023 | Key Management | ECC with AES and clustering through LEACH protocol |
| Alghamdi, et al.[81] | 2023 | Key Management | SPAR-SSO protocol using connection quality estimation and power-aware routing |
| L. H. Alhasnawy, et al.[83] | 2023 | Quantum Threats | BB84 protocol with AES algorithm for quantum key distribution |
| G. Mehta, et al.[93] | 2023 | Malicious Node Attack | Improved LEACH protocol for detection and mitigation |
| Y. Zhang, et al.[90] | 2023 | Resource Optimization | WSN technology with AI for home safety monitoring |
| I. Sharma, et al.[84] | 2024 | Intrusion Detection | Machine learning framework with decision tree, Gaussian Naïve Bayes, and random forest |
| C. Puttaswamy, et al.[94] | 2024 | Malicious Node Attack | Fuzzy logic for cluster head selection and hybrid RSA and AES encryption |
| M. A. Vieira, et al.[95] | 2024 | Malicious Node Attack | ARC-LEACH protocol with anomaly report cycling |
| K. Sedhuramalingam, et al.[87] | 2024 | Intrusion Detection | Hybrid GFSO model with DCNN and BiLSTM |
| J. Dr. LohithJ, et al.[88] | 2024 | Intrusion Detection | Quad LEACH protocol with integrated security agents |
| M. Sahaya, et al.[89] | 2024 | Intrusion Detection | Mutual information analysis for detecting critical nodes and anomalies |
| Venčkauskas, et al.[98] | 2024 | Key Management | Encrypted tunnels, periodic key exchanges, and sender’s message authentication code |
| S. Khan, et al.[99] | 2024 | Malicious Node Attack | ANN-based detection with CICIDS2017 dataset |
| P. Vennam, et al.[96] | 2024 | Malicious Node Attack | SS-ChOA for secure Cluster Head selection and routing |
| M. Shanmathi, et al.[97] | 2024 | Malicious Node Attack | CNN-FL for node categorization and NGO-optimized routing strategy |
4.4.2. Resource Optimization
4.4.3. Malicious Node Attack
4.4.4. Key Management
4.4.5. Quantum Threats
4.4.6. Conclusion
4.5. Heterogeneous Network: Security Challenges
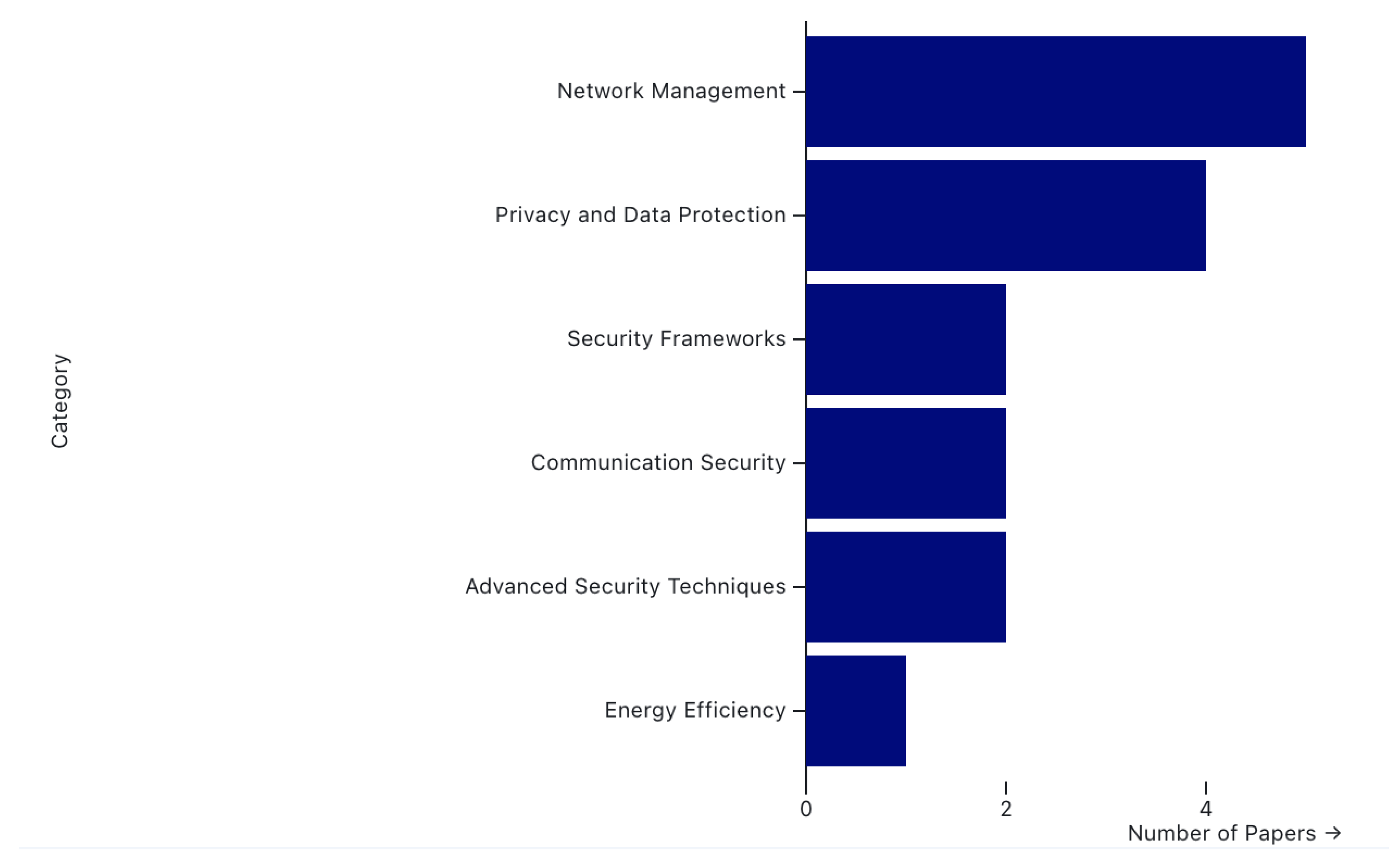
| Authors | Date | Security Challenge Addressed | Proposed Solution |
|---|---|---|---|
| Jing Li, et al.[101] | 2023 | Network Management | Rule-based reasoning using description logic for predicting network security situations |
| Lianwei Qu, et al.[102] | 2023 | Privacy and Data Protection | HNPP model with differential privacy and random perturbations for secure network publishing |
| Y. Hu, et al.[103] | 2023 | Privacy and Data Protection | Distributed Weighted Classification Method for network slicing in Space-Air-Ground integrated networks |
| Z. Han, et al.[104] | 2023 | Communication Security | Game theory-based optimization for channel access attack defense in UAV-aided networks |
| V. Bouček, M. Husák[105] | 2023 | Network Management | Graph-based tool for recommending similar devices to analyze cyber attack impact |
| Xabier, et al.[106] | 2023 | Network Management | Federated Learning with unsupervised device clustering for network anomaly detection |
| Junkai Yi, Lin Guo[107] | 2023 | Network Management | AHP-based evaluation with XGBoost for network security assessment in IIoT |
| J. Zhang, et al.[108] | 2024 | Advanced Security Threats | Attention sharing mechanism for domain adaptation in IoT intrusion detection |
| Changkui Yin, et al.[109] | 2024 | Privacy and Data Protection | STLLM-ECS framework with edge computing for secure PM2.5 level forecasting |
| D. Bhanu, et al.[110] | 2024 | Energy Efficiency | OECS-RA for optimal cluster head and secure-hop selection in WSNs |
| W. Wang, et al.[112] | 2024 | Network Management | VHetNet-enabled AFL framework with CA2C algorithm for anomaly detection in IoT |
| Wenbo Zhang, et al.[108] | 2024 | Advanced Security Technique | vBiLSTM and KGC-N model for network security knowledge graph completion |
| T. Quinn, et al.[114] | 2024 | Security Framework | PoC trust management for routing in software-defined wireless networks |
| W. Yu, et al.[115] | 2024 | Security Framework | DevSecOps and AIOps for continuous security monitoring in substation networks |
| J. Li, et al.[116] | 2024 | Privacy and Data Protection | DL-based caching framework with differential privacy for IoT network caching |
| Q. Zhang, et al.[117] | 2024 | Communication Security | AHTST strategy with Lyapunov optimization for secure heterogeneous traffic transmission |
4.5.1. Network Management
4.5.2. Privacy and Data Protection
4.5.3. Communication Security
4.5.4. Advanced Security Techniques
4.5.5. Security Framework
4.5.6. Energy Efficiency
4.5.7. Conclusion
5. Conclusion
Acknowledgments
References
- I.F. Akyildiz, W. Su, Y. Sankarasubramaniam, E. Cayirci, "Wireless sensor networks: a survey," Computer Networks, Volume 38, Issue 4, 2002, Pages 393-422, ISSN 1389-1286. [CrossRef]
- Kandris D, Anastasiadis E. Advanced Wireless Sensor Networks: Applications, Challenges and Research Trends. Electronics. 2024; 13(12):2268.
- Salman, Dheyab & Ibrahim, & Mahdi, Abdullah & Yas, Qahtan. (2021). Challenges and Issues for Wireless Sensor Networks: A Survey. 6. 1-19.
- V. Mhatre and C. Rosenberg, "Homogeneous vs heterogeneous clustered sensor networks: a comparative study," 2004 IEEE International Conference on Communications (IEEE Cat. No.04CH37577), Paris, France, 2004, pp. 3646-3651 Vol.6. [CrossRef]
- Nasri, Nejah and Mnasri, Sami and Val, Thierry 3D Node Deployment Strategies Prediction in Wireless Sensors Network. (2019) International Journal of Electronics, 1. 1-30. ISSN 0020-7217.
- You-Chiun Wang, Chun-Chi Hu, and Yu-Chee Tseng, "Efficient deployment algorithms for ensuring coverage and connectivity of wireless sensor networks," First International Conference on Wireless Internet (WICON’05), Budapest, Hungary, 2005, pp. 114-121. [CrossRef]
- Wei Li and C. G. Cassandras, "A minimum-power wireless sensor network self-deployment scheme," IEEE Wireless Communications and Networking Conference, 2005, New Orleans, LA, USA, 2005, pp. 1897-1902 Vol. 3. [CrossRef]
- T. Andersen and S. Tirthapura, "Wireless sensor deployment for 3D coverage with constraints," 2009 Sixth International Conference on Networked Sensing Systems (INSS), Pittsburgh, PA, USA, 2009, pp. 1-4. [CrossRef]
- Nojeong Heo and P. K. Varshney, "Energy-efficient deployment of Intelligent Mobile sensor networks," in IEEE Transactions on Systems, Man, and Cybernetics - Part A: Systems and Humans, vol. 35, no. 1, pp. 78-92, Jan. 2005. [CrossRef]
- Y. Zou and Krishnendu Chakrabarty, "Sensor deployment and target localization based on virtual forces," IEEE INFOCOM 2003. Twenty-second Annual Joint Conference of the IEEE Computer and Communications Societies (IEEE Cat. No.03CH37428), San Francisco, CA, USA, 2003, pp. 1293-1303 vol.2. [CrossRef]
- Z. Cheng, M. Perillo and W. B. Heinzelman, "General Network Lifetime and Cost Models for Evaluating Sensor Network Deployment Strategies," in IEEE Transactions on Mobile Computing, vol. 7, no. 4, pp. 484-497, April 2008. [CrossRef]
- Soumya J Bhat, Santhosh K V, "A localization and deployment model for wireless sensor networks using arithmetic optimization algorithm," 2023.
- P. Balister and S. Kumar, "Random vs. Deterministic Deployment of Sensors in the Presence of Failures and Placement Errors," IEEE INFOCOM 2009, Rio de Janeiro, Brazil, 2009, pp. 2896-2900. [CrossRef]
- Ines Khoufi, Pascale Minet, Anis Laouiti, Saoucene Mahfoudh. "Survey of Deployment Algorithms in Wireless Sensor Networks: Coverage and Connectivity Issues and Challenges." International Journal of Autonomous and Adaptive Communications Systems, 2017, 10 (4), pp.341-390. [CrossRef]
- Sourour Elloumi, Olivier Hudry, Estel Marie, Agathe Martin, Agnès Plateau, et al., "Optimization of wireless sensor networks deployment with coverage and connectivity constraints," Annals of Operations Research, vol. 298, no. 1-2, pp. 183-206, 2021. [CrossRef]
- Guiling Wang, Guohong Cao, and T. La Porta, "Movement-assisted sensor deployment,"IEEE INFOCOM 2004, Hong Kong, China, 2004, pp. 2469-2479 vol.4.
- Mao, J., Jiang, X. & Zhang, X., "Analysis of node deployment in wireless sensor networks in warehouse environment monitoring systems," J Wireless Com Network 2019, 288 (2019). [CrossRef]
- S. Toumpis and L. Tassiulas, "Optimal deployment of large wireless sensor networks,"in IEEE Transactions on Information Theory, vol. 52, no. 7, pp. 2935-2953, July 2006,.
- Saadallah, N. R., & Alabady, S. A. (2024). An Energy Efficient and Scalable WSN with Enhanced Data Aggregation Accuracy. Journal of Telecommunications and Information Technology, 2(2), 48–57. [CrossRef]
- Rahul Priyadarshi, Bharat Gupta, and Amulya Anurag, "Deployment techniques in wireless sensor networks: a survey, classification, challenges, and future research issues," 2020.
- Boualem, Adda et al. “Linear and Non-Linear Barrier Coverage in Deterministic and Uncertain environment in WSNs: A New Classification.” ArXiv abs/2306.12355 (2023): n. pag.
- H. P. Gupta, S. V. Rao and V. Tamarapalli, "Analysis of Stochastic k-Coverage and Connectivity in Sensor Networks With Boundary Deployment," in IEEE Transactions on Intelligent Transportation Systems, vol. 16, no. 4, pp. 1861-1871, Aug. 2015. [CrossRef]
- P. Geng, A. Yang and Y. Liu, "Research on Connectivity and Coverage of WSNs Based on Complex Network Characteristics," 2023 12th International Conference of Information and Communication Technology (ICTech), Wuhan, China, 2023, pp. 484-488. [CrossRef]
- Mehmet C. Vuran, Özgür B. Akan, Ian F. Akyildiz, Spatio-temporal correlation: theory and applications for wireless sensor networks, Computer Networks, Volume 45, Issue 3, 2004, Pages 245-259, ISSN 1389-1286. [CrossRef]
- Niculescu, D. (2003). Positioning in ad hoc sensor networks. IEEE Network, 18(4), 24-29.
- Zafer, M., Senouci, M.R. and Aissani, M. (2021) ‘Efficient deployment approach of wireless sensor networks on 3D terrains’, Int. J. Data Mining, Modelling and Management, Vol. 13, Nos. 1/2, pp.114–136.
- Chi-Fu Huang, Yu-Chee Tseng and Li-Chu Lo, "The coverage problem in three-dimensional wireless sensor networks," IEEE Global Telecommunications Conference, 2004. GLOBECOM ’04., Dallas, TX, USA, 2004, pp. 3182-3186 Vol.5. [CrossRef]
- M. K. Watfa and S. Commuri, "The 3-Dimensional Wireless Sensor Network Coverage Problem," 2006 IEEE International Conference on Networking, Sensing and Control, Ft. Lauderdale, FL, USA, 2006, pp. 856-861. [CrossRef]
- Unaldi, N. and Temel, S., 2014, October. Wireless sensor deployment method on 3D environments to maximize quality of coverage and quality of network connectivity. In Proceedings of the World Congress Engineering and Computer science (Vol. 2, pp. 2078-0966).
- S. M. Nazrul Alam and Zygmunt J. Haas. 2006. Coverage and connectivity in three-dimensional networks. In Proceedings of the 12th annual international conference on Mobile computing and networking (MobiCom ’06). Association for Computing Machinery, New York, NY, USA, 346–357. [CrossRef]
- Fu, W.; Yang, Y.; Hong, G.; Hou, J. WSN Deployment Strategy for Real 3D Terrain Coverage Based on Greedy Algorithm with DEM Probability Coverage Model. Electronics 2021, 10, 2028. [CrossRef]
- A. Saad, M. R. Senouci and O. Benyattou, "Toward a Realistic Approach for the Deployment of 3D Wireless Sensor Networks," in IEEE Transactions on Mobile Computing, vol. 21, no. 4, pp. 1508-1519, 1 April 2022. [CrossRef]
- Mohamed K. Watfa and Sesh Commuri. 2008. An energy efficient and self-healing 3-dimensional sensor cover. Int. J. Ad Hoc Ubiquitous Comput. 3, 1 (December 2007), 33–47. [CrossRef]
- Gou, P.; Guo, B.; Guo, M.; Mao, S. VKECE-3D: Energy-Efficient Coverage Enhancement in Three-Dimensional Heterogeneous Wireless Sensor Networks Based on 3D-Voronoi and K- Means Algorithm. Sensors 2023, 23, 573. [CrossRef]
- Reddy, M.R., Chandra, M.L.R. "An Improved 3D-DV-Hop Localization Algorithm to Improve Accuracy for 3D Wireless Sensor Networks." SN COMPUT. SCI. 5, 245 (2024). [CrossRef]
- Rajput, Monali & Ghawte, Usama. (2017). Security Challenges in Wireless Sensor Networks. International Journal of Computer Applications. 168. 24-28. [CrossRef]
- Obodoeze, Engr. Dr. Fidelis. (2012). Wireless Sensor Network in Niger Delta Oil and Gas Field Monitoring: The Security Challenges and Countermeasures. International Journal of Distributed and Parallel systems. 3. 65-77. [CrossRef]
- Ahmad R, Wazirali R, Abu-Ain T. Machine Learning for Wireless Sensor Networks Security: An Overview of Challenges and Issues. Sensors. 2022; 22(13):4730. [CrossRef]
- Saidi, H., Gretete, D., Addaim, A. (2020). Game Theory for Wireless Sensor Network Security. In: Yang, XS., Sherratt, S., Dey, N., Joshi, A. (eds) Fourth International Congress on Information and Communication Technology. Advances in Intelligent Systems and Computing, vol 1041. Springer, Singapore.
- Shah, Ansar & Aljubayri, Mohammed & Khan, Muhammad & Alqahtani, Jarallah & Mscs, Mahmood & Sulaiman, Adel & Shaikh, Asadullah. (2023). ILSM: Incorporated Lightweight Security Model for Improving QOS in WSN. Computer Systems Science and Engineering. 46. 2471-2488. [CrossRef]
- H., O. Abu, R. "Securing Wireless Sensor Networks Against DoS attacks in Industrial 4.0," Journal of Intelligent Systems and Internet of Things, vol. , no. , pp. 66-74, 2023. [CrossRef]
- Bassey, Aniebiet & Johnson, Enyenihi & Umoh, Gabriel. (2023). Secret Key Management in Wireless Sensor Network Based on Probabilistic Technique. Journal of Engineering Research and Reports. 25. 162-170. [CrossRef]
- Adda Boualem, Cyril de Runz, Marwane Ayaida, Herman Akdag. A fuzzy/possibility approach for area coverage in wireless sensor networks. Soft Computing, 2023, 27, pp.9367-9382. ff10.1007/s00500- 023-08406-3ff. ffhal-04108659f.
- Khan, A.; Macias-Villegas, G.; Ammari, H. M. Aperiodic Tiling for Enhancing Security in Wireless Sensor Networks. Preprints 2024, 2024081495. [CrossRef]
- Medina F, Ruiz H, Espíndola J, Avendaño E. Deploying IIoT Systems for Long-Term Planning in Underground Mining: A Focus on the Monitoring of Explosive Atmospheres. Applied Sciences. 2024; 14(3):1116. [CrossRef]
- Bian H, Zhang W, Chang CK. Situ-Oracle: A Learning-Based Situation Analysis Framework for Blockchain-Based IoT Systems. Blockchains. 2024; 2(2):173-194. [CrossRef]
- Elsayed, Mahmoud Ayman Mohamed. Navigating the Rules: Integrating TD3 and Sensor Fusion for TrafficAware Autonomous Vehicle Path Planning. 2024. American University in Cairo, Master’s Thesis. AUC Knowledge Fountain. https://fount.aucegypt.edu/etds/2369.
- P. Sebothoma and T. E. Mathonsi, "An Enhanced Security Algorithm for Wireless Sensor Networks," 2023 International Conference on Electrical, Computer and Energy Technologies (ICECET), Cape Town, South Africa, 2023, pp. 1-6. [CrossRef]
- V. Prakash, A. R. Mishra and S. Pandey, "A Perspective View of Bio-Inspire Approaches Employing in Wireless Sensor Networks," 2023 International Conference on IoT, Communication and Automation Technology (ICICAT), Gorakhpur, India, 2023, pp. 1-8. [CrossRef]
- Khan S, Khan MA, Alnazzawi N. Artificial Neural Network-Based Mechanism to Detect Security Threats in Wireless Sensor Networks. Sensors. 2024; 24(5):1641. [CrossRef]
- Arunkumar, P., & Savitha, K. K. (2024). Secure and Accurate Node Localisation and Route Optimization for Wireless Sensor Network (WSN). African Journal of Bio Sciences, 6(8), 435-449.
- Sharma, S., Kaur, A., Gupta, D. et al. Dragon fly algorithm based approach for escalating the security among the nodes in wireless sensor network based system. SN Appl. Sci. 5, 376 (2023). [CrossRef]
- Loïc Desgeorges, Jean-Philippe Georges, Thierry Divoux, Detection of anomalies of a non-deterministic software-defined networking control, Computers & Security, Volume 129, 2023, 103228, ISSN 0167-4048. [CrossRef]
- S. Suma Christal Mary, S. Jothi Shri, E. Thenmozhi, K. Murugeswari, "Data Security in Wireless Sensor Networks using an Efficient Cryptographic Technique to Protect Against Intrusion," SSRG International Journal of Electronics and Communication Engineering, vol. 10, no. 4, pp. 41-50, 2023. [CrossRef]
- Kim, Y., Lim, E., & Kwon, T. (2024). On the Impact of Deployment Errors in Location-Based Key Predistribution Protocols for Wireless Sensor Networks. IEEE Access. [CrossRef]
- A. Afghantoloee and M. Abolfazl Mostafavi, "A Purpose-Oriented 3-D Voronoi Algorithm for Deployment of a Multitype Sensor Network in Complex 3-D Indoor Environments in Support of the Mobility of People With Motor Disabilities," in IEEE Transactions on Instrumentation and Measurement, vol. 73, pp. 1-13, 2024, Art no. 2519713. [CrossRef]
- S. Hafeez, "Blockchain-based Secure Unmanned Aerial Vehicles (UAV) in Network Design and Optimization," Ph.D. dissertation, School of Engineering, College of Science and Engineering, Univ. of Glasgow, Glasgow, U.K., 2024. Available: https://theses.gla.ac.uk/id/eprint/84460. [CrossRef]
- Mainwaring, Alan & Polastre, Joseph & Szewczyk, Robert & Culler, David & Anderson, John. (2002). Wireless Sensor Networks for Habitat Monitoring. Proceedings of the ACM International Workshop on Wireless Sensor Networks and Applications. [CrossRef]
- Guides Publishing.(2023). The Network Effects Bible. Retrieved July 10, 2024, from the-network-effects-bible/121732.
- Shi D, Lü L, Chen G. Totally homogeneous networks. Natl Sci Rev. 2019 Oct;6(5):962- 969. [CrossRef] [PubMed] [PubMed Central]
- [51]Liang, Junbin et al. “A Survey of Coverage Problems in Wireless Sensor Networks.” (2014).
- Y. Jiang, L. Liu and J. Shu, "Overview of Key Node Evaluation in Complex Networks," 2023 3rd International Conference on Intelligent Communications and Computing (ICC), Nanchang, China, 2023, pp. 354-358. [CrossRef]
- M. Farsi, M. A. Elhosseini, M. Badawy, H. Arafat Ali and H. Zain Eldin, "Deployment Techniques in Wireless Sensor Networks, Coverage and Connectivity: A Survey," in IEEE Access, vol. 7, pp. 28940-28954, 2019. [CrossRef]
- A. Chatap and S. Sirsikar, "Review on various routing protocols for heterogeneous wireless sensor network," 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 2017, pp. 440-444.
- Singh, Samayveer & Chand, Satish & Kumar, Bijendra. (2017). Multilevel heterogeneous network model for wireless sensor networks. Telecommunication Systems. 64. [CrossRef]
- Saravanakumar, R., Susila, S. G., & Raja, J. (2011). Energy efficient homogeneous and heterogeneous system for wireless sensor networks. International Journal of Computer Applications, 17(4), 33-38. [CrossRef]
- Purkar, Santosh V., Deshpande, R. S., Energy Efficient Clustering Protocol to Enhance Performance of Heterogeneous Wireless Sensor Network: EECPEP-HWSN, Journal of Computer Networks and Communications, 2018, 2078627, 12 pages, 2018. [CrossRef]
- V. Kusla, G. S. Brar, V. K. Garg, A. Bansal and R. Kaushal, "Meta-heuristic Artificial Humming Bird Algorithm Based Energy Efficient Cluster Head Selection (MAHA-EECHS) in Wireless Sensor Networks," 2023 International Conference on Emerging Smart Computing and Informatics (ESCI), Pune, India, 2023, pp. 1-6. [CrossRef]
- L. Yu, N. Wang, W. Zhang and C. Zheng, "Deploying a Heterogeneous Wireless Sensor Network,"2007 International Conference on Wireless Communications, Networking and Mobile Computing, Shanghai, China, 2007, pp. 2588-2591.
- Elfouly, F.H.; Ramadan, R.A.; Khedr, A.Y.; Yadav, K.; Azar, A.T.; Abdelhamed, M.A. Efficient Node Deployment of Large-Scale Heterogeneous Wireless Sensor Networks. Appl. Sci. 2021, 11, 10924. [CrossRef]
- Halder, Subir & Dasbit, Sipra. (2014). Enhancement of wireless sensor network lifetime by deploying heterogeneous nodes. Journal of Network and Computer Applications. 38. 106–124. [CrossRef]
- Elif Bozkaya, Mumtaz Karatas, Levent Eriskin, Chapter 1 - Heterogeneous wireless sensor networks: Deployment strategies and coverage models,Editor(s): Kiran Ahuja, Anand Nayyar, Kavita Sharma, Comprehensive Guide to Heterogeneous Networks, Academic Press, 2023, Pages 1-32, ISBN 9780323905275.
- Singh, Anuj Kumar and Patro, B.D.K, A Novel Security Protocol for Wireless Sensor Networks Based on Elliptic Curve Signcryption (November 8, 2019). International Journal of Computer Networks & Communications (IJCNC) Vol.11, No.5, September 2019, Available at SSRN: https://ssrn.com/abstract=3483512.
- Ferreira, Adrián & de Melo, Marco Aurélio & Oliveira, Leonardo & Habib, Eduardo & Wong, Hao & Loureiro, Antonio. (2005). On the Security of Cluster-Based Communication Protocols for Wireless Sensor Networks. 449-458. [CrossRef]
- Y. Li, D. Yong and J. Ma, "Secure Message Distribution Scheme with Configurable Privacy for Heterogeneous Wireless Sensor Networks," 2008 IEEE/IFIP International Conference on Embedded and Ubiquitous Computing, Shanghai, China, 2008, pp. 10-15. [CrossRef]
- Junyao He and Feng Xu 2020 J. Phys.: Conf. Ser. 1486 022052.
- Prasan Kumar Sahoo, Jonathan Jen-Rong Chen and Ping-Tai Sun, "Efficient security mechanisms for the distributed wireless sensor networks," Third International Conference on Information Technology and Applications (ICITA’05), Sydney, NSW, Australia, 2005, pp. 541-546 vol.2. [CrossRef]
- A. AlBusaidi and F. H. Mohideen, "Analysis of Wireless Sensor Network Security Models: A Salient Approach for Deeper Inspection Using Deep Neural Networks,"2023 International Conference on Emerging Techniques in Computational Intelligence (ICETCI), Hyderabad, India, 2023, pp. 276-282,.
- Tan, L., Zheng, Q., & Chen, J. (2023). Providing an effective key management scheme to increase transaction security of homogeneous mobile wireless sensor networks. No DOI provided.
- Urooj, S., Lata, S., Ahmad, S., Mehfuz, S., & Kalathil, S. (2023). Cryptographic Data Security for Reliable Wireless Sensor Network. No DOI provided.
- Alghamdi, A., Al Shahrani, A. M., Alyami, S., Khan, I., Sri, P. S. G. A., Dutta, P., Rizwan, A., & Venkatareddy, P. (2023). Security and energy efficient cyber-physical systems using predictive modeling approaches in wireless sensor network. No DOI provided.
- Kandasamy, M., Anto, S., Baranitharan, K., Rastogi, R., Satwik, G., & Sampathkumar, A. (2023).Smart Grid Security Based on Blockchain with Industrial Fault Detection Using Wireless Sensor Network and Deep Learning Techniques. Hindawi.
- Alhasnawy, L. H., & Al-Mashanji, A. (2023). Improving Wireless Sensor Network Security Using Quantum Key Distribution. Baghdad Science Journal. [CrossRef]
- Sharma, I., Bhardwaj, A., & Kaushik, K. (2024). Enhancing agricultural wireless sensor network security through integrated machine learning approaches. Wiley Online Library. [CrossRef]
- Singh, T., & Vaid, R. (2024). Preserving Security in Terms of Authentication on Blockchain-Based Wireless Sensor Network (WSN). Journal of Sensor Networks.
- Venkat, B., Kumar, V., Gopakumar, G., Subham, D., & Murali, K. (2024). Improved Security of Network Clock Synchronization in Wireless Sensor Networks. Journal of Network Security.
- Sedhuramalingam, K., & Kumar, N. S. (2024). A Hybrid Rider Optimization with Deep Learning Driven Intrusion Detection Framework in Wireless Sensor Network. Journal of Intrusion Detection Systems.
- LohithJ, J., Shreya, & Priya, H. (2024). Enhancing Wireless Sensor Network Longevity and Security: A Quad-LEACH Approach. Journal of Wireless Sensor Networks.
- Sahaya, M., Jasvant, S. A., Sathees, R. S., Jeya, V., & Anitha, R. R. (2024). Enhancing Wireless Sensor Network Security Through Mutual Information Analysis for Intrusion Detection and Resilience. Journal of Engineering Science, 14(3), 2532-2546. [CrossRef]
- Zhang, Y., Jing, R., Ji, X., & Hu, N. (2023). Application of wireless sensor network technology based on artificial intelligence in security monitoring system. De Gruyter. [CrossRef]
- Teng, Zhijun & Zhu, Sian & Li, Mingzhe & Yu, Libo & Gu, Jinliang & Guo, Liwen. (2023). Wireless sensor network security defense strategy based on Bayesian reputation evaluation model. IET Communications. 18. n/a-n/a. [CrossRef]
- Mir, Z. A., & Yadav, S. (2023). Leveraging Gray Wolf Optimization for enhanced security management in wireless sensor networks. Tuijin Jishu/Journal of Propulsion Technology, 44(4), 6295. No DOI provided.
- Mehta, G., Bhuvneshwari, & Singh, A. (2023). Improved Wireless Sensor Network Security Through Node Leach Technique. IEEE Xplore. [CrossRef]
- Puttaswamy, C., & Shivaprasad, N. P. K. (2024). Enhancing wireless sensor network security with optimized cluster head selection and hybrid public-key encryption.International Journal of Electrical and Computer Engineering, 14(3), 2976-2987.
- Vieira, M. A., & Liu, H. (2024). Defense against Black Hole Attacks in Wireless Sensor Network with Anomaly Report Cycling. Journal of Cyber-Physical Systems.
- Vennam, P., & Mouleeswaran, S. K. (2024). Spiral Shape - Chimp Optimization Algorithm for Secure Cluster-Based Routing in Wireless Sensor Network. Journal of Network and Computer Applications.
- Shanmathi, M., Sonker, A., Hussain, Z., Ashraf, M., Singh, M., & Syamala, M. (2024). Enhancing wireless sensor network security and efficiency with CNN-FL and NGO optimization. Measurement: Sensors, 24(101057). [CrossRef]
- Venčkauskas, A., Taparauskas, M., Grigaliūnas, Š., & Brūzgienė, R. (2024). Enhancing Communication Security in In-Vehicle Wireless Sensor Network. Automotive Cybersecurity Journal.
- Khan S, Khan MA, Alnazzawi N. Artificial Neural Network-Based Mechanism to Detect Security Threats in Wireless Sensor Networks. Sensors. 2024; 24(5):1641. [CrossRef]
- Idris, I. A., & Issahku, F. Y. (2024). Advancing Wireless Sensor Network Security through the Implementation of Homomorphic Encryption for Secure and Private Image Processing. International Journal for Research in Applied Science and Engineering Technology. [CrossRef]
- Jing Li, Xingjie Huang, Chan Wang, Jinmeng Zhao, Beibei Su, and Zhijie Shang "Design of heterogeneous network security device management platform based on multi-source data", Proc. SPIE 12702, International Conference on Intelligent Systems, Communications, and Computer Networks (ISCCN 2023), 127021F (16 June 2023); [CrossRef]
- Lianwei Qu, Yong Wang, Jing Yang, and Meng Zhao. 2023. A heterogeneous network structure publishing security framework based on cloud-edge collaboration. Comput. Netw. 234, C (Oct 2023). [CrossRef]
- Y. Hu, N. Shi, L. Lu and C. Wang, "Space-Air-Ground Integrated Heterogeneous Network Slicing with Native Intelligence,"2023 IEEE/CIC International Conference on Communications in China (ICCC Workshops), Dalian, China, 2023, pp. 1-6,.
- Z. Han et al., "Smart Optimization Solution for Channel Access Attack Defense Under UAV-Aided Heterogeneous Network," in IEEE Internet of Things Journal, vol. 10, no. 21, pp. 18890-18897, 1 Nov.1, 2023. [CrossRef]
- Bouček, Vladimír & Husák, Martin. (2023). Recommending Similar Devices in Close Proximity for Network Security Management. 481-484. [CrossRef]
- Xabier Sáez-de-Cámara, Jose Luis Flores, Cristóbal Arellano, Aitor Urbieta, Urko Zurutuza, Clustered federated learning architecture for network anomaly detection in large scale heterogeneous IoT networks, Computers & Security, Volume 131, 2023, 103299, ISSN 0167-4048. [CrossRef]
- Yi, Junkai, and Lin Guo. 2023. "AHP-Based Network Security Situation Assessment for Industrial Internet of Things" Electronics 12, no. 16: 3458. [CrossRef]
- Zhang J, Li Y, Zhang L. Heterogeneous network intrusion detection via domain adaptation in IoT environment. Internet Technology Letters. 2024;e531. [CrossRef]
- Yin, Changkui, Yingchi Mao, Zhenyuan He, Meng Chen, Xiaoming He, and Yi Rong. 2024."Edge Computing-Enabled Secure Forecasting Nationwide Industry PM2.5 with LLM in the Heterogeneous Network" Electronics 13, no. 13: 2581.
- Bhanu, D.. Santhosh, R.. Heterogeneous Wireless Sensor Network Design with Optimal Energy Conservation and Security through Efficient Routing Algorithm. Journal of Journal of Cybersecurity and Information Management 13, no. 2 (2024): 140-154. [CrossRef]
- Z. Wu, P. Xu and H. Fan, "Network Security Situation Assessment Method Based Eigenvector Centrality,"2024 International Wireless Communications and Mobile Computing (IWCMC), Ayia Napa, Cyprus, 2024, pp. 103-108,.
- W. Wang, O. Abbasi, H. Yanikomeroglu, C. Liang, L. Tang and Q. Chen, "A Vertical Heterogeneous Network (VHetNet)-Enabled Asynchronous Federated Learning-Based Anomaly Detection Framework for Ubiquitous IoT," in IEEE Open Journal of the Communications Society, vol. 5, pp. 332-348, 2024. [CrossRef]
- Zhang, Wenbo, Mengxuan Wang, Guangjie Han, Yongxin Feng, and Xiaobo Tan. 2024. "A Knowledge Graph Completion Algorithm Based on the Fusion of Neighborhood Features and vBiLSTM Encoding for Network Security" Electronics 13, no. 9: 1661. [CrossRef]
- T. Quinn, S. D. Ali Shah, F. Bouhafs and F. Den Hartog, "Towards trust-based routing for data plane security in heterogeneous Software-Defined Wireless Networks," 2024 IEEE 10th International Conference on Network Softwarization (NetSoft), Saint Louis, MO, USA, 2024, pp. 37-42. [CrossRef]
- W. Yu, J. Qian, R. Xu, C. Jin, H. Fang and X. Shi, "Improving Substation Network Security with DevSecOps and AIOps," 2024 IEEE 10th Conference on Big Data Security on Cloud (BigDataSecurity), NYC, NY, USA, 2024, pp. 113-118. [CrossRef]
- J. Li, M. Feng and S. Li, "A Deep Learning Cache Framework for Privacy Security on Heterogeneous IoT Networks," in IEEE Access, vol. 12, pp. 93261-93269, 2024. [CrossRef]
- Q. Zhang et al., "Optimal Age of Information and Throughput Scheduling in Heterogeneous Traffic Wireless Physical-Layer Security Communications," in IEEE Internet of Things Journal, vol. 11, no. 13, pp. 23644-23660, 1 July1, 2024. [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




