1. Introduction
Cyber-physical systems (CPSs) are becoming increasingly important in modern science and technology, especially in areas such as ocean monitoring and defense [
1,
2,
3]. CPS closely integrates computational, cyber, and physical processes, enabling systems to sense and respond to environmental changes in real time [
4,
5,
6]. Wireless Sensor Networks (WSNs), as an integrated system, usually integrate multiple sources of sensors and information sources such as Global Navigation Satellite Systems (GNSS), Doppler Velocimeters (DVL), Inertial Navigation Systems (INS), and so on, at their core [
7,
8]. Through the effective combination of CPS and wireless sensor networks, CPS shows great potential in data acquisition, processing and transmission. Unmanned Surface Vessels (USVs), as a key application of this system [
9,
10,
11], relies on WSNs for real-time data collection and transmission for efficient monitoring and decision-making in the marine environment [
12,
13].
The reliability of data is directly related to the USVs’ ability to perform its mission [
14,
15,
16], especially in the complex maritime environment and potential cyberattacks, where ensuring the authenticity and integrity of the data is of particular importance. In USVs applications, WSNs enable these vessels to efficiently perform data acquisition and real-time monitoring in a vast marine environment. By integrating data from different sensors, USVs are able to quickly adapt to complex marine environments, enhancing their operational efficiency and safety. During data measurement and transmission, the data are susceptible to a variety of external disturbances, including marine environmental disturbances (e.g., the effects of wind, waves, currents, etc., on USVs) and signal disturbances, which can lead to variations in the data, further exacerbating the uncertainty in the system’s decision-making and thus affecting the safety and efficiency of USVs. To make the data transmission more accurate, the use of WSNs and
fusion filtering techniques is necessary. In the recent period, the rapid development of
filtering technology has provided a new solution for data processing in complex systems [
17,
18,
19]. With its superior anti-interference ability, this technology can effectively filter external interference noise and improve the reliability and accuracy of data. By fusing data from different sensors,
fusion filtering can significantly improve the accuracy of the data, thus enhancing the autonomous decision-making level of USVs. This is essential for autonomous navigation and operation of USVs in dynamic and uncertain marine environments.
Although USVs show great advantages in data acquisition and transmission, their high reliance on wireless communication also exposes them to potential cybersecurity threats, especially in terms of False Data Injection (FDI) attacks [
20,
21,
22]. FDI attacks are a type of cyber-attacks that mislead the system decision-making by tampering or falsifying data, and the attacker can influence the behaviour of the USVs through these false data, leading to wrong navigation and decision-making. FDI attacks are highly stealthy, and malicious attackers are often able to inject false information into USVs through wireless networks without being detected [
23,
24,
25]. Such attacks can not only mislead the USVs’ mission execution, e.g., wrong course selection or improper action strategies, but also lead to more serious consequences such as personnel casualties. In addition, FDI attacks may also cause a chain reaction to other USVs-dependent data systems, affecting the overall efficiency of maritime surveillance and defence. Therefore, the development of effective protective measures and data processing strategies has become an urgent need for current research.
Currently, many researches have been conducted for FDI attacks. For example, Chen et al. [
26] developed a framework capable of simultaneously estimating system states and FDI attack signals under FDI and denial-of-service attacks and implementing compensatory control. At the same time, a novel co-design methodology was developed. The method is capable of estimating and compensating unknown FDI attacks without relying on any a priori constraints on the frequency, duration, or derivatives of the FDI attack signals, and effectively suppressing their negative impacts. The compensation method is effective against jamming attacks, however, the FDI attack is detected only after the injection into the system, when the system state information has been tampered with.
To address the above FDI detection issues, Xia et al. [
27] proposed a distributed detection method, which consists of two steps: the kernel entropy-based discrimination scheme identifies secure nodes and attacked nodes by calculating the kernel entropy of the measured data between nodes, while the state-aware scheme enables each node to monitor its own state and filter reliable neighbouring nodes. They theoretically derive the conditions that guarantee the stability of the algorithm’s mean value and reveal how its performance changes under an FDI attack.
Zhang et al. [
28] introduced the adaptive backstepping technique into nonlinear CPS and integrated the dynamic surface control technique, which successfully overcame the computational complexity (computational explosion) problem existing in the traditional backstepping method. The method significantly reduces the computational burden by bypassing the direct complex computation of higher-order systems through stepwise design of virtual control inputs. In addition, they developed a novel defense strategy centered on a nonlinear interference observer. The strategy is capable of accurately estimating the external composite disturbances and substantially improving the system robustness. The nonlinear disturbance observer dynamically estimates the magnitude of the disturbance and its trend by monitoring the system state and output in real time, enabling the controller to compensate accordingly in real time, thus effectively enhances the system’s stability when it is subjected to attacks and disturbances. Although the above methods have a certain degree of fault tolerance and FDI attack resistance, they do not solve the privacy protection problem in the data transmission process.
Li et al. [
29] designed a low computational complexity encryption scheme for data based on random matrices to achieve instant detection and localisation of FDI attacks during local estimation transmission. Using the results of the encryption detection scheme, a secure fusion estimation algorithm is proposed. The algorithm is able to discard the attacked local estimation information and use only the unattacked local estimation information for fusion estimation. Although the method proposed in the article has significant advantages in terms of privacy protection of data, the static key it uses lacks forward security and the entire cryptographic detection scheme will fail once it is intercepted on the transmission link or restored through brute force decryption.
Hence, improving the ability of USVs to protect data privacy against FDI attacks and ensuring the accuracy of data estimation through dynamic key management and data encryption techniques has become very meaningful and urgent research. The primary contributions of this paper can be outlined as follows:
Aiming at the privacy leakage problem during data transmission, this paper proposes a novel dynamic data encryption scheme. The scheme encrypts the data before data transmission and dynamically updates the key by utilizing historical system data, which increases the difficulty for attackers to crack the ciphertext compared to the literature [
29].
Establish a dynamic relationship between the ciphertext, the key and the auxiliary encrypted ciphertext. Once the ciphertext or auxiliary encrypted ciphertext is maliciously tampered with, the dynamic relationship is destroyed. Based on this feature, we design an attack detection scheme based on dynamic data encryption. The scheme can detect FDI attacks in real time and immediately discard the damaged data.
fusion filters are proposed to suppress external noise and interference during data measurement and transmission. The weighted fusion algorithm fuses the data that has not received the attack to more accurately estimate and restore the real signal, ensuring the information integrity and reliability of USVs during data transmission.
The organization of this paper is as follows:
Section 2 develops the system model for the problem under consideration;
Section 3 details the proposed dynamic data encryption scheme and the FDI attack detection method;
Section 4 introduces the design of the
fusion filter and explores its applications;
Section 5 employs simulation experiments to validate the performance of the proposed scheme.
Notations: Let denotes the n-dimensional Euclidean space, I and 0 represent the identity matrix and the zero matrix of appropriate dimensions, respectively. The transpose of a matrix is indicated by a superscript T. For any matrix , the condition defines X as a real symmetric positive definite matrix (or a real symmetric negative definite matrix). ⊕ represents the XOR operator.
2. System Description
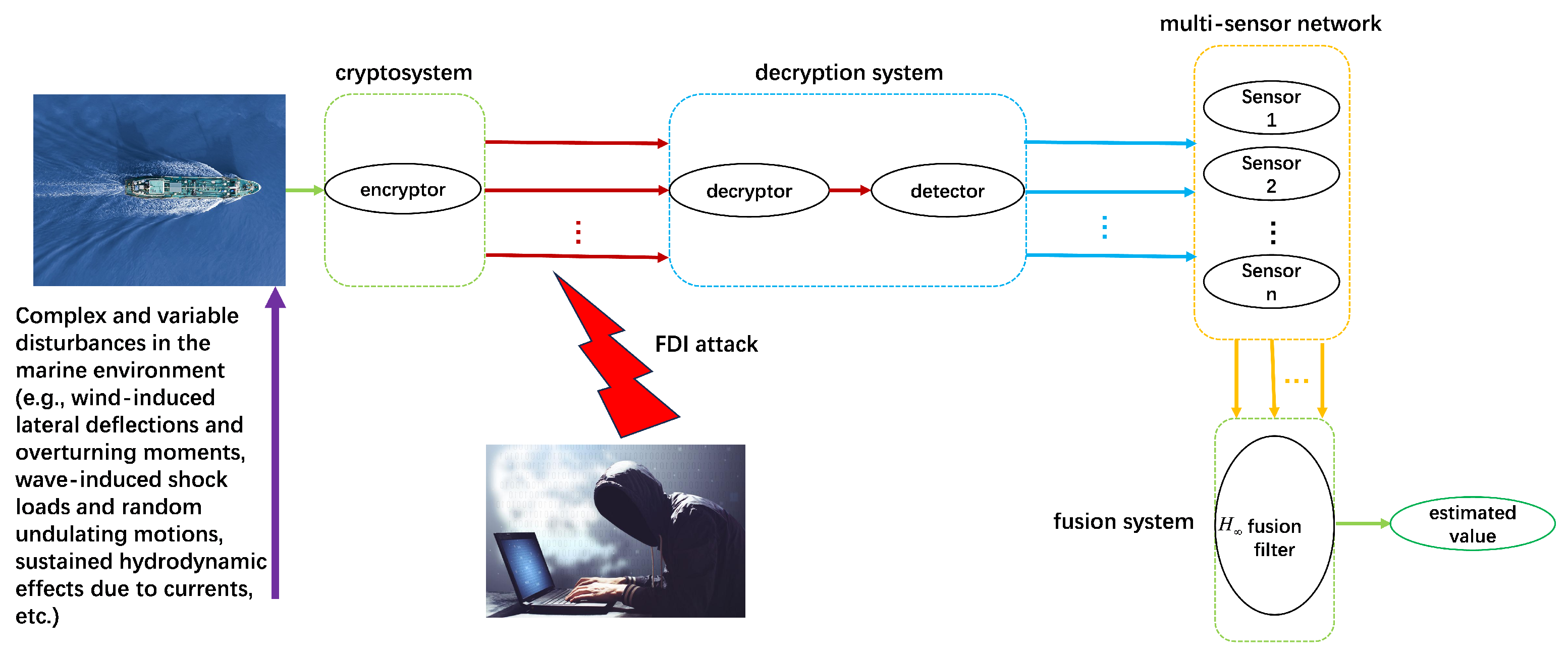
Since USVs are susceptible to the interference of unpredictable environmental factors such as wind and wave currents during navigation, they will not only directly change their motion attitude but also introduce uncertainty noise in their motion control system and sensor measurement data. As shown in
Figure 1, when the USVs transmit data to the sensors via the wireless network, the communication link may be subjected to FDI attack, which tamper with the transmitted data, resulting in distortion of the sensor reception, which in turn leads to wrong decision making by the control center.
Based on [
14], the mathematical model of the motion of the USVs can be described as
,
. In which
represents the position vector of the vessel and consisting of north-east position
and bow-rock angle
,
denotes the USVs velocity vector in the vessel coordinate system, which consists of longitudinal
u, transverse
and bow-rock angular velocities
r. The rotation matrix
is expressed as
Based on [
30], a class of discrete-time multi-sensor network systems are modelled as follows:
where, let
denotes the position state information, let
,
denotes position coordinates,
denotes bow rocker.
and
are the system state and measured output of the
ith sensor at the moment
k, respectively.
is the state to be estimated.
is an unknown external disturbance,
is a measurement noise belonging to
. Matrices A, B,
and L known to have the appropriate dimensions.
At the time of instants of k, each sensor receives a packet from the USVs containing the ciphertext and its auxiliary encrypted ciphertext. The detector applies an attack detection scheme to the packet and discards the packet that has been maliciously altered by the attacker; subsequently, it performs a decryption operation on the ciphertext in the legitimate packet. However, marine environmental disturbances (e.g., the effects of wind, waves, and currents on USVs) are inevitable during data transmission. These disturbances introduce system state noise, which in turn leads to biased data. Therefore, fusion filtering is used to filter the interference noise and estimate or restore the real information by weighted fusion algorithm.
As shown in
Figure 1, during the transmission of data packets, a malicious attacker may launch an FDI attack on unknown data in the communication links to tamper with these data. Whereas, in a multi-sensor system, due to the limited resources of the attackers, it is unlikely that they can attack all communication links at the same time. Therefore, it is reasonable to assume that there is at least one unattacked communication link in a multi-sensor system. This assumption ensures that the sensors receive at least one true system state. If all of them were attacked, then the sensors would not be able to obtain reliable data.
3. Encryption Attack Detection Scheme
This section designs an attack detection method incorporating dynamic data encryption, aiming to achieve real-time identification of FDI attacks. First, a dynamic data encryption mechanism with low computational overhead is constructed to ensure the security of transmitted data. Subsequently, based on this encryption mechanism, a corresponding attack detection scheme is designed.
3.1. Dynamic Data Encryption Scheme
As shown in
Figure 1, local data
is encrypted using a key
before transmission. Once it reaches the decryptor, it will be restored from it using the decryption scheme. The specific encryption scheme is designed as follows:
where
is the key in the encryption process,
is a matrix of random numbers with suitable dimensions,
is updated each time by summing with
based on the historical system data to achieve dynamic encryption, and
is the given initial key.
is the ciphertext corresponding to the encryption of
, and
is the auxiliary encrypted ciphertext used for detecting FDI attacks. Function
is an arbitrary encryption function about
. In addition, the encryption function
can be selected according to the application scenarios as well as the requirements of computational complexity. After the encryption is completed, the encryptor sends the packet
to the decryptor through the communication network.
To recover the original data
from
, the decryption scheme is designed as follows:
where
is the key in the decryption process,
is the decrypted value of
and
is an auxiliary value to be used in an attack detection scheme.
Notations: under the encryption method (
2) and the decryption method (
3), a random matrix
is introduced, which has to be consistent during encryption and decryption. In order to ensure that
is equal to
, the ciphertext
is recovered as
. In fact, since the use of the same seed when using a random number generator produces unique random sequences, it is possible to use in (
2) and (
3) the same random number generator seed to ensure the consistency of
, and this is a widely used solution in cryptography [
31].
In the attack-free, the following propositions about dynamic data encryption schemes (
2) and (
3) can be obtained:
Proposition 1. In the absence of FDI attacks, the following conclusions can be drawn using dynamic data encryption schemes (
2) and (
3):
Proof 1. According to the dynamic data encryption scheme (
2) and (
3),
is established, when the decryptor receives the data packet
, the decryption process is shown in (
5):
The decrypted data is then examined using the detection scheme to get the following results
According to the mathematical description of Eqs. (
5)-(
6), the correct data can be obtained in the ideal case of FDI attack free, and the attack detection scheme does not detect that the packet suffers from an FDI attack.
3.2. Scheme for Detection of Encryption-Based Attacks
Note that from Proposition 1, it is clear that in the dynamic data encryption schemes (
2) and (
3),
, this feature enables us to determine whether the system data has been tampered with by a malevolent attacker. Based on the dynamic data encryption schemes (
2) and (
3), an attack detection scheme as shown in Algorithm 1 is proposed, which can detect whether the data is attacked by FDI in a very short time.
|
Algorithm 1 Attack detection algorithm based on dynamic data encryption |
|
Step 1 (encryption process): At moment k, the encryptor executes the encryption process, generates the ciphertext and the auxiliary encryption ciphertext , and encapsulates them into a data packet .
Step 2 (data transmission): The encryptor sends the packet to the decryptor through the communication network.
Step 3 (decryption process): When the decryptor receives the received packet, it performs the decryption process.
Step 4 (Attack Detection): After the decryption process, the following detection scheme is executed.
Case 1: If , this received packet is not attacked by FDI. , return to step 1.
Case 2: If , then this received packet is subject to FDI attack. Discard the data packets received on this communication link this time. , return to step 1.
|
Theorem 1. In the absence of FDI attacks, the original data can be recovered using Algorithm 1.
Proof 2. In the absence of a cyberattack, is known from Proposition 1, which implies that the original data can be recovered using Algorithm 1. Also, implies that Case 1 in Algorithm 1 is always satisfied.
Remark 1. In encryption schemes (
2) and (
3), only XOR operations and basic arithmetic operations are employed, featuring low computational complexity. It enhances data security and keeps the system performance overhead within a negligible range.
Remark 2. From Theorem 1, the system exists with a specific dynamic relation, i.e., , when there is without FDI attack. This dynamic relation will be changed when subjected to FDI attack. This property can be used as a sufficient criterion for attack detection and provides a theoretical basis for the cryptographic detection algorithm proposed in this paper.
4. Fusion Estimation Under FDI Attack
In data transmission, the effects of complex and variable marine environmental disturbances (e.g., wind-induced offsets, wave-induced impacts, etc.) on USVs are unavoidable. These powerful environmental factors can cause unpredictable attitude changes and position drifts of USVs, resulting in increased system state noise and biased data. For this reason, the fusion filtering technique is used to filter out the noise, and the real state information is estimated by a weighted fusion algorithm.
4.1. The effectiveness of the encryption-based attack detection scheme in detecting FDI attacks
In Algorithm 1, and will be packaged and sent to the decryptor via the communication network. It is assumed that the attacker can recognize and to implement the tampering. The attack strategy consists of the following three scenarios:
Scenario 1: The attacker modifies only
as follows:
Scenario 2: The attacker modifies only
as follows:
Scenario 3: The attacker modifies both
and
as follows:
where and are arbitrary non-zero attack signals of the appropriate dimensions.
Theorem 2. For Algorithm 1, if the FDI attacks Eqs. (
7)-(
9) in scenarios 1-3 at time
k, the encryption-based attack detection algorithm will trigger an alert immediately from time
k onwards.
Proof 3. If the FDI attack under Eq. (
7) in Scenario 1 starts at time
k, the decryption process is as follows:
Then, the improved format can be obtained
If the FDI attack (
8) in scenario 2 begins at the time
k, the decryption process is defined as follows:
And thus, it can be derived that
From the mathematical description of Eqs. (
10)-(
13), it can be seen that Scenario 1 and Scenario 2 always satisfy the Case 2 decision condition in Algorithm 1, which ensures that the encryption-based attack detection algorithm achieves a zero-delay alarm at the attack initiation moment
k. For the FDI attack corresponding to Scenario 3 (Eq. (
9)), the consistency conclusion can be obtained by the same methodological derivation, and its proof process is omitted here.
4.2. Fusion Estimation Based on Fast Attack Detection
Although attack detection algorithms can effectively filter out data tampered with by malicious attackers, the external noise interference inherent in the measurement and transmission process can still lead to biased system state information obtained by the sensors, which in turn affects the accuracy of control decisions. Therefore, the aim of this study is to design the filter that mitigates the effect of noise on the estimated system state. The filter is able to effectively cope with the noise and ensure that the system can still provide accurate state estimation and control in the event of noise interference. Then, a secure fusion estimation algorithm is proposed to perform optimal weighted fusion of unattacked data, thereby significantly improving the accuracy of state estimation while ensuring security and enabling more precise estimation and reconstruction of the true signal.
Consider the following local filter structure on sensor
i:
where
and
are the estimated values of
and
, respectively.
,
and
are the filter parameter matrices to be probe-based.
Introducing the local error
and combining Eqs. (
1) and (
14), the local filtering error system for sensor
i is established as follows:
In order to facilitate the derivation of the formula for the filter performance, the symbols in Eq. (
5). are denoted as follows:
denotes the state vector of the localized filtering error, is the unknown external interference, is the measurement noise belonging to , and is the gain matrix of the localized filter.
In the case of non-zero noise interference, the stability of the system can be determined by the
filter performance criterion. Specifically, when the upper bound of the filter output energy is smaller than a given performance criterion, the filter system is proved to be asymptotically stable. Based on the actual noise characteristics and filter structure analysis, the
performance criterion adopted in this chapter is expressed as follows:
where
and
are the two given positive definite real symmetric auxiliary matrices, and these two parameter matrices achieve boundedness control of the system paradigm through a weight adjustment mechanism.
Theorem 3. For a scalar
and real positive definite matrices
and
, the system (
15) is asymptotically stable, if there exists a real symmetric matrix Q satisfying under Eq. (
17).
Proof 4. According to the auxiliary matrices
P and
given below, the rewritable inequality satisfying the filter performance criterion is obtained:
where
Proof 5. Set up the Lyapunov function:
There are two scenarios that need to be discussed here.
- 1)
-
When
and
:
Considering
and combining it with Eq. (
17) shows the inequality
.
Therefore, guarantees the asymptotic stability of the filter under noiseless conditions.
- 2)
-
When
and
:
Set as
Continuing the derivation yields:
where
Combined with equation (
17), the inequality can be written as
This can be obtained after further derivation:
It can be concluded that satisfies the fusion filtering performance criteria of this paper.
Define
and
as the set of attacked local estimation indexes and the set of unattacked local estimation indexes,
, respectively, at time
k. For the multi-sensor configuration of system (
1), the proposed distributed
fusion filter design is presented below:
where
denotes the fused global estimate,
denotes the fused weights and satisfies the normalization condition
,
n denotes the total number of sensors, and
represents the filter error.
5. Simulations
To verify the effectiveness of the dynamic data encryption fusion estimation strategy for USVs-oriented FDI attacks proposed, a simulation experiment platform is constructed in this study. Based on the dynamics model of USVs and the established system model, it is assumed that the sensor network contains six nodes. In order to enhance the security, the first three sensors receive the first state component of the system, and the last three sensors receive the second state component of the system. During the measurement process, the communication data is affected by the measurement noise
. The external interference noise
is used to simulate the effect of wind, waves, and other factors on data acquisition and transmission in the marine environment. The simulation duration is set to [0, 100] seconds, and the initial state value of the system is
. The system parameter matrix is defined as
It is assumed that there exists at least one sensor that is not subject to the FDI attack in the first three sensor groups and the last three sensor groups at any time, and the location of the FDI attack occurs randomly. In addition, we set the value of the attack signal as a random value in the interval [40, 80]. In the dynamic data encryption scheme, the initial key matrix
is randomly generated, and the key
is updated according to the historical system data during the subsequent encryption process, with the update step set to 1. The encryption function
. The following
fusion filter parameters are given according to the Monte Carlo method:
To address the issue of privacy protection during data transmission, using dynamic encryption methods for protection.
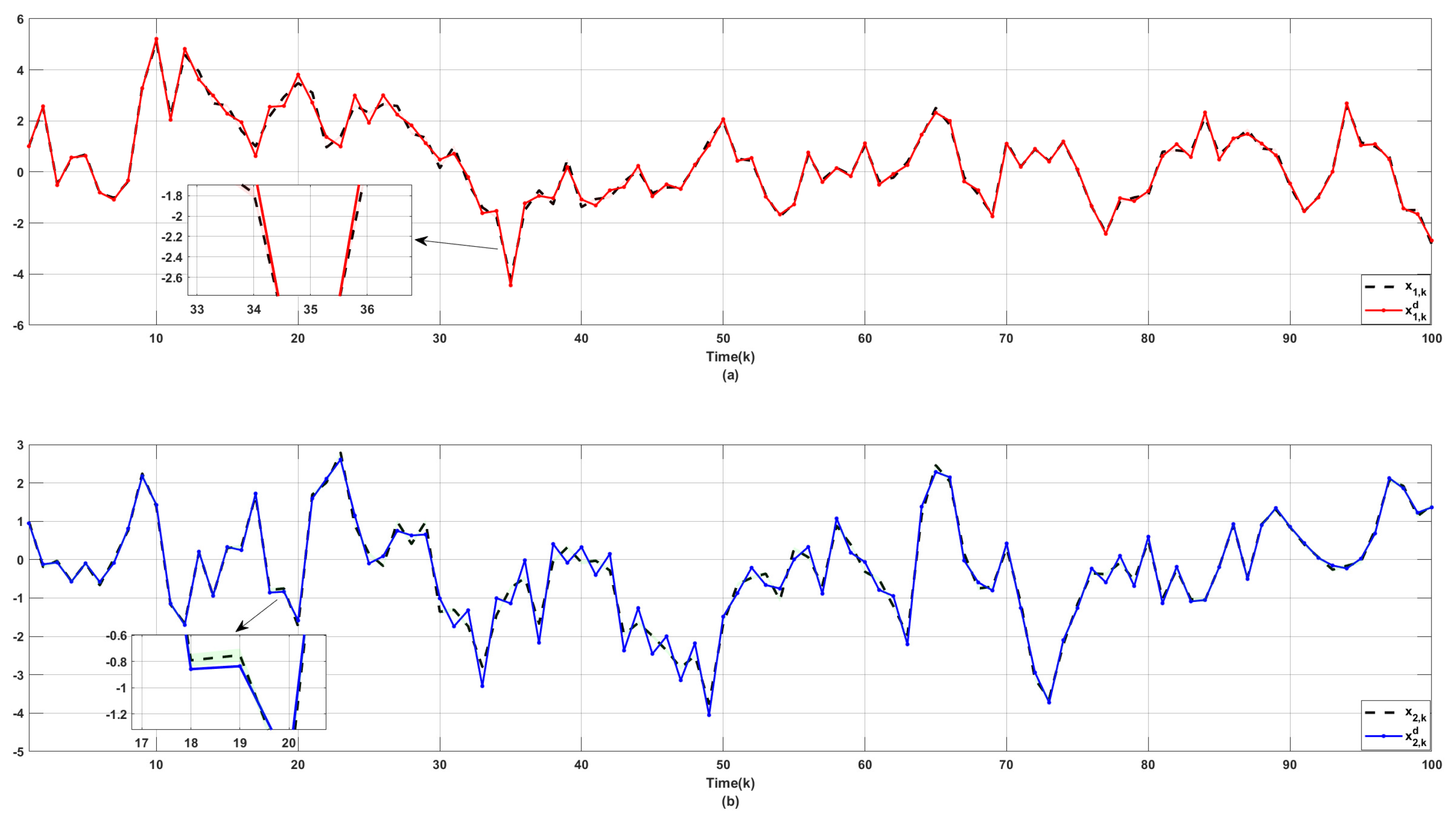
Figure 2 demonstrates the effect of the decryptor on the recovery of key state quantities of the system. Figure (a) depicts the horizontal position of the system (
) Dynamic: the black dashed line represents the true horizontal position, and the red line represents the decrypted position (
) obtained by the decryptor. Figure (b) depicts the velocity of the system (
) Dynamic: the black dashed line represents the true velocity, and the blue solid line represents the decryption velocity (
) obtained by the decryptor. The comparison shows that the positions and velocities output by the decryptor can effectively track and approximate their corresponding true values, indicating that the decryptor has a excellent performance in recovering the position and velocity states of the system.
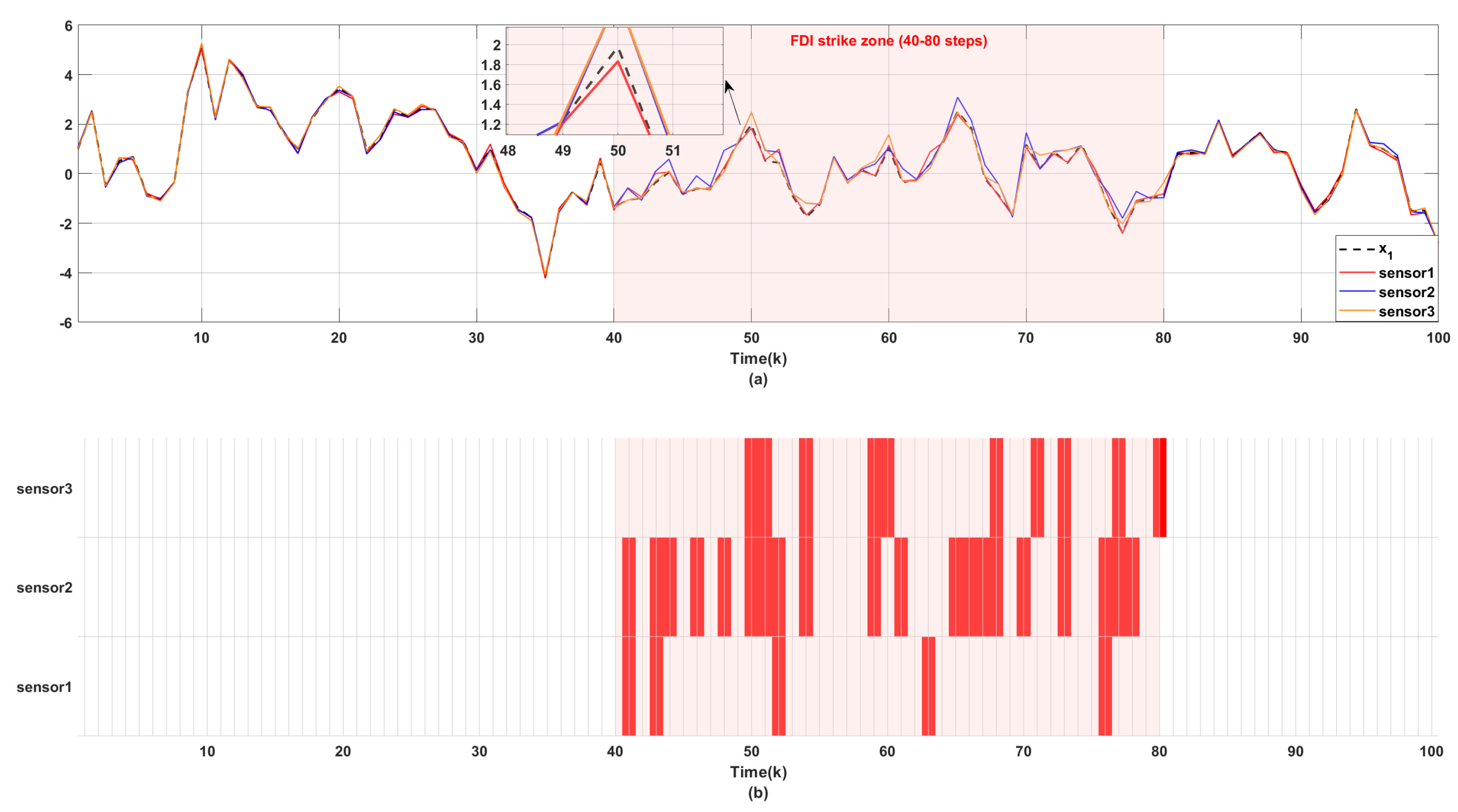
Figure 3 and
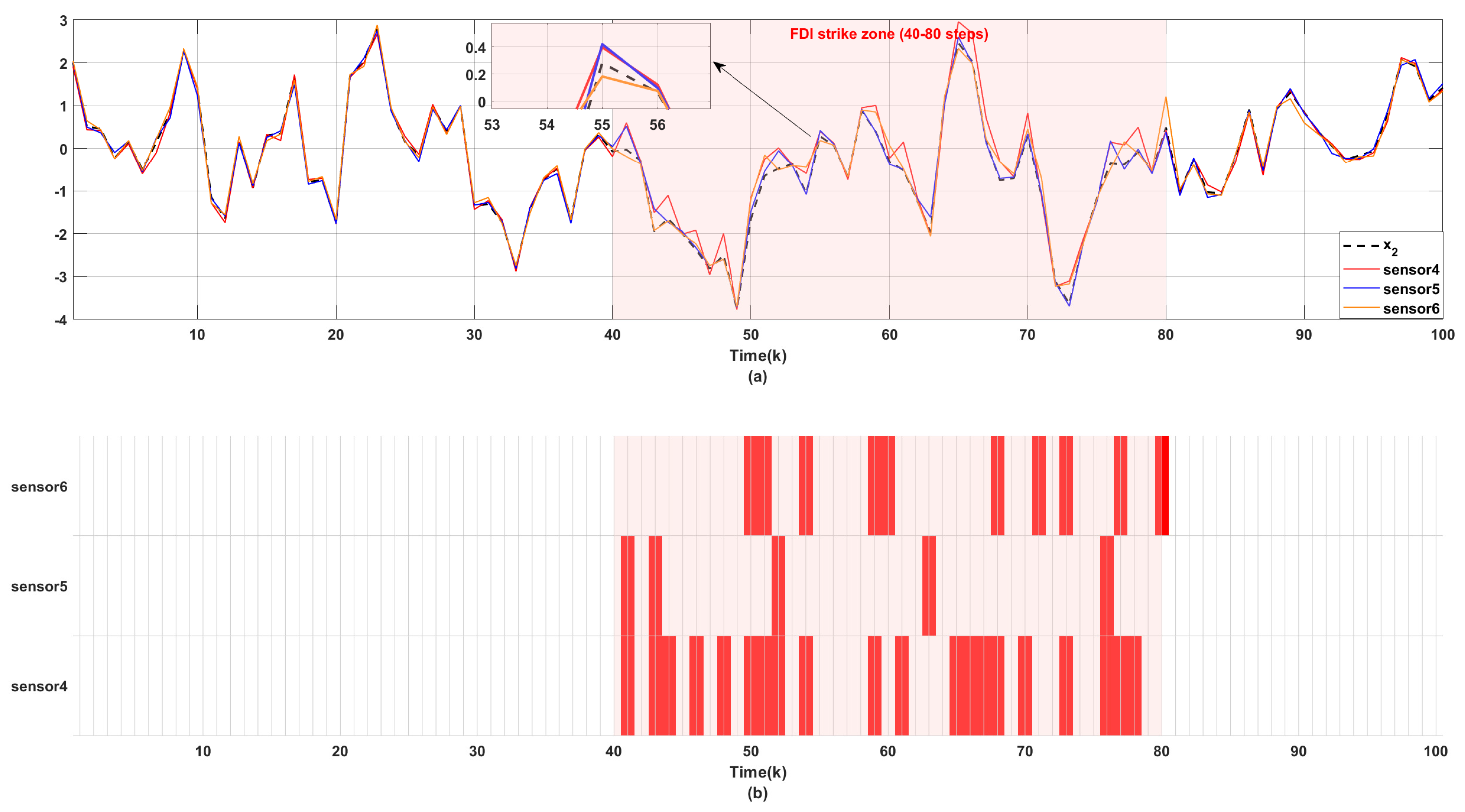
Figure 5 together show the state observation effect of the multi-sensor system under FDI attack.
Figure 3(a) marks the true horizontal position of the system (
) by the black dashed line, while presenting the observed values of sensor 1/2/3 pairs of
by the red, blue, and orange solid lines, respectively. And the red block in
Figure 3(b) marks the FDI attack occurring at the corresponding moment.
Figure 5(a) similarly presents the true speed (
, black dashed line) with the three sensors’ observations of
(red/blue/orange solid lines).
Figure 5(b) synchronizes the distribution of FDI attacks in the
channel. The comparison of the two sets of images clearly shows that the observed data acquired by the sensors during the normal operation hours without attacks maintains a remarkable consistency with the real state, while there is a significant deviation during the 40 to 80 FDI attack time period (red blocks), verifying the destructive impact of the attack on the data.
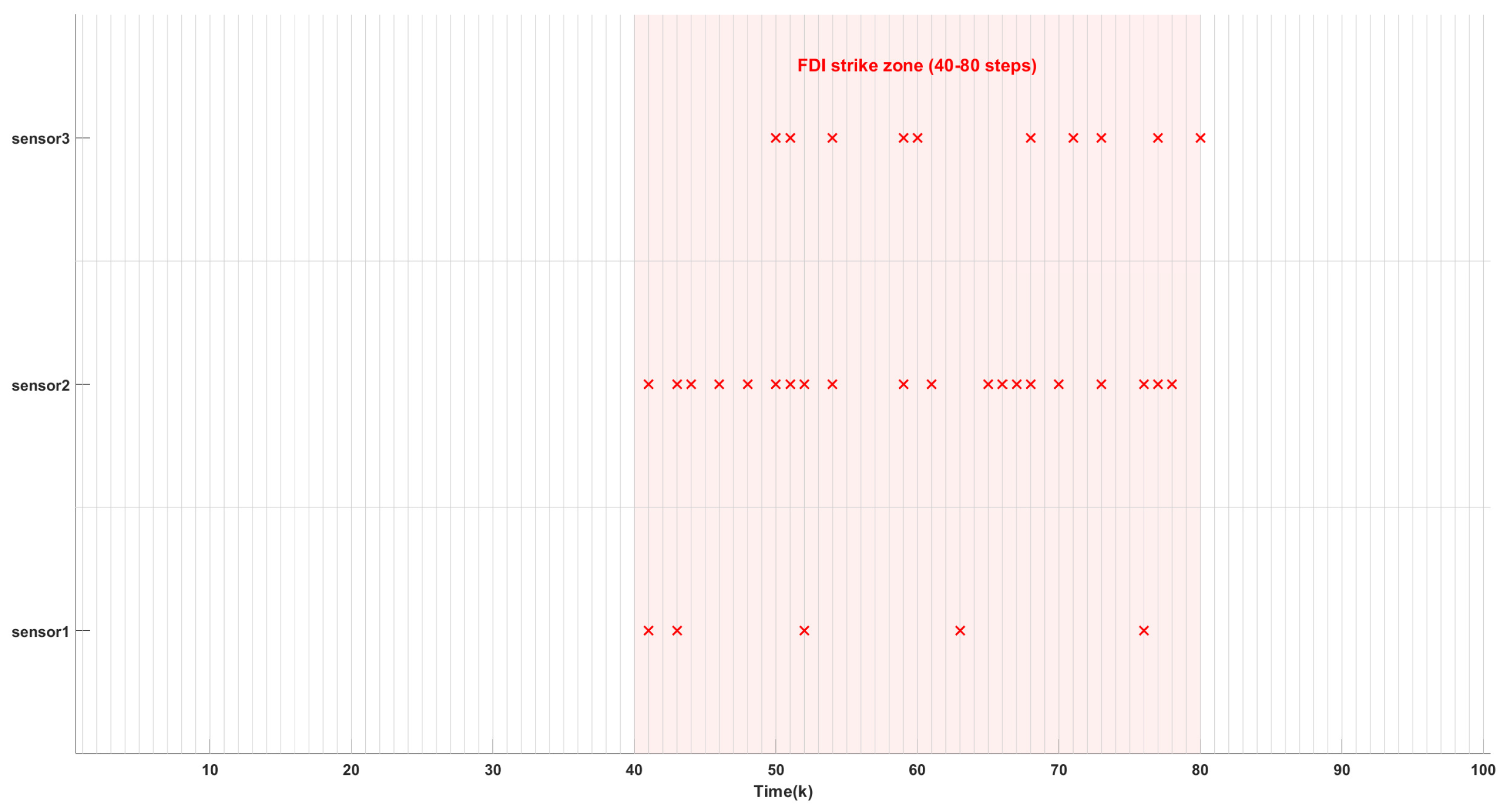
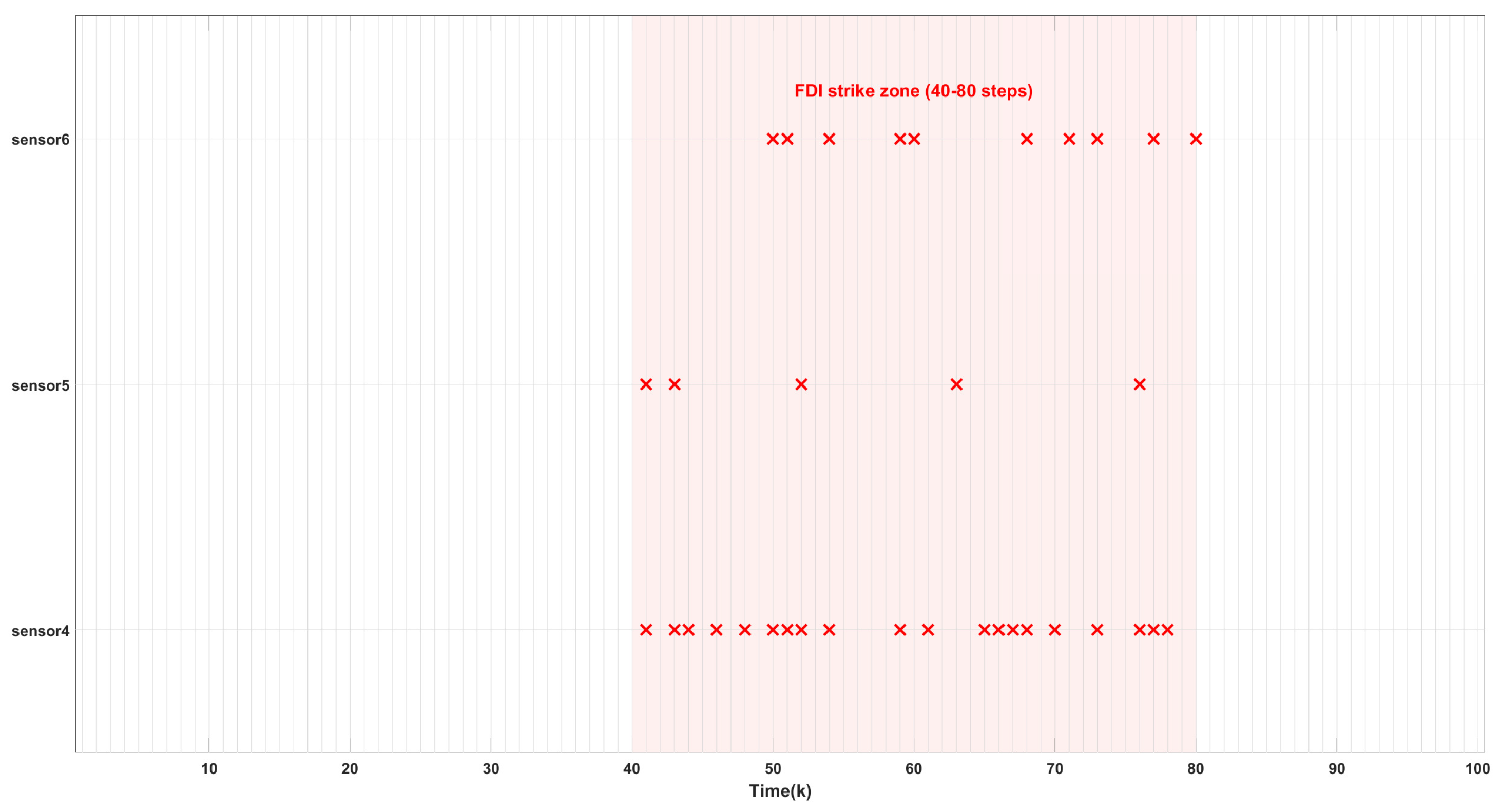
Figure 4 and
Figure 6 show the FDI attack detection results for sensors 1-3 and sensors 4-6, respectively, where the red crosses indicate that an alert is issued when an attack is detected and the corresponding data is discarded.
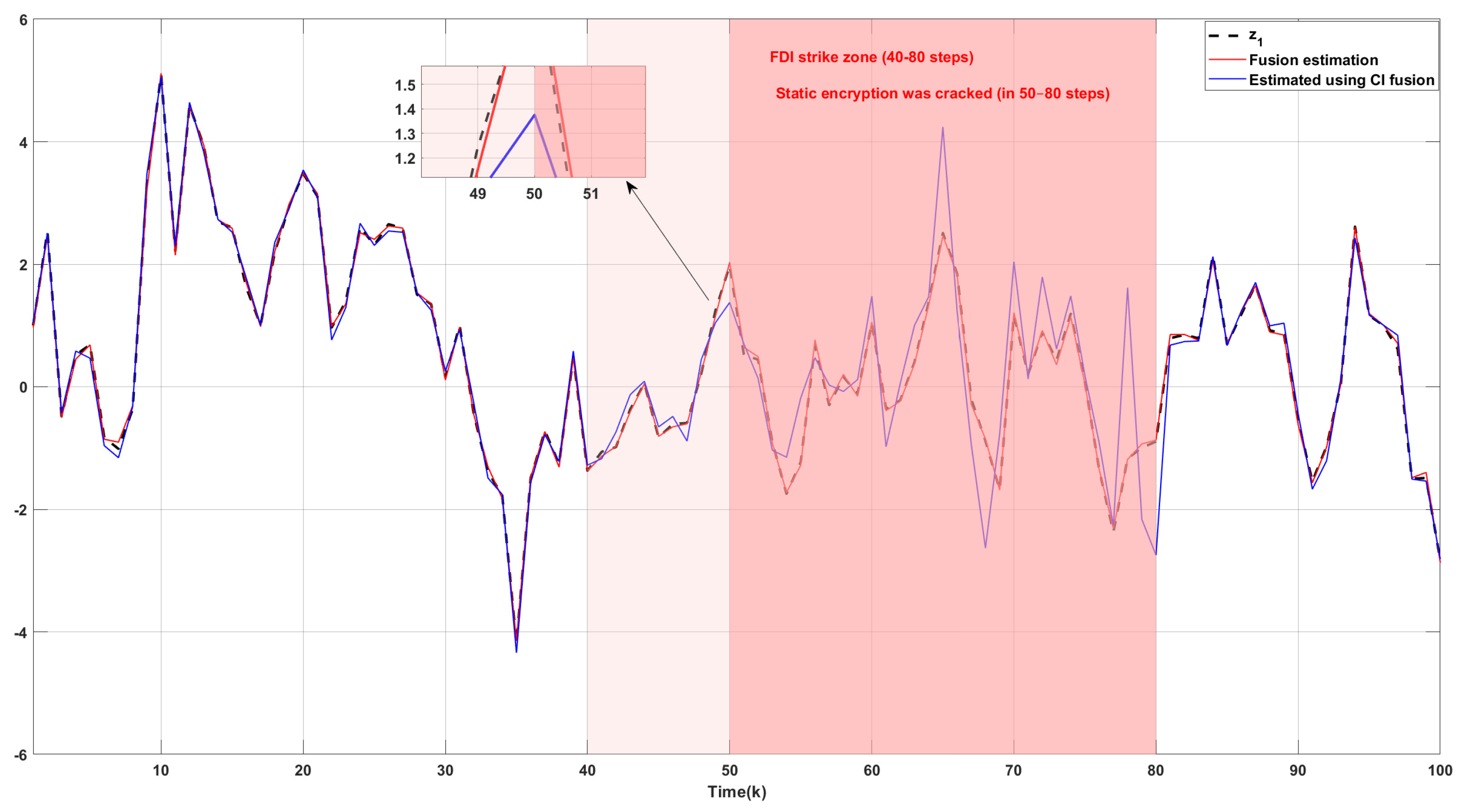
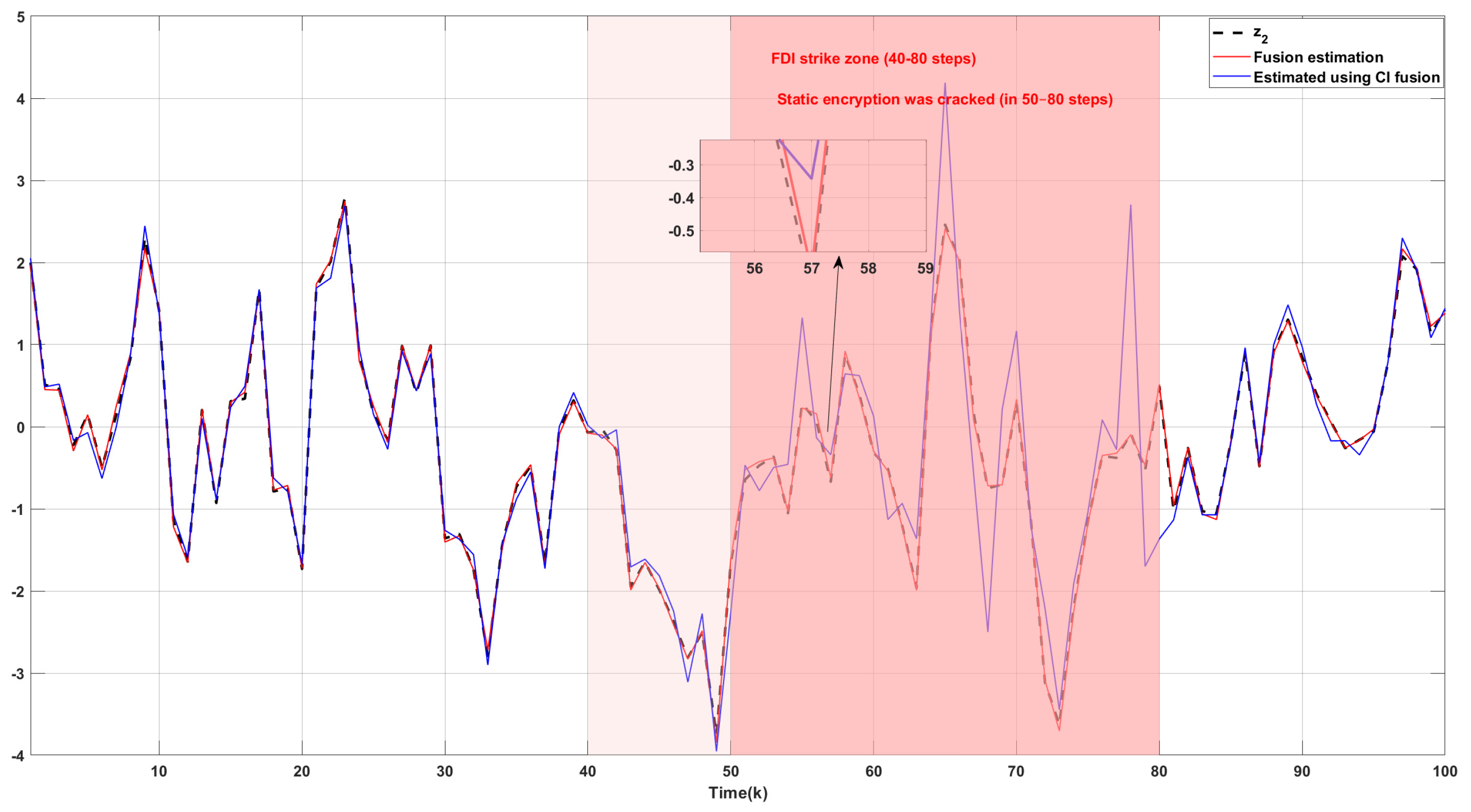
The actual values and the estimated values of the USVs’ horizontal position are shown in
Figure 7, while
Figure 8 presents the actual and the estimated values of the USVs’ velocity. From
Figure 7 and
Figure 8, the proposed fusion estimation method can accurately obtain both the horizontal position and velocity of the USVs. Moreover, due to the dynamic nature of the encryption keys, the encryption scheme remains secure without risk of compromise. The estimation results demonstrate significant superiority over the CI fusion estimation results presented in the comparative literature [
29].
Table 1 demonstrates the standard deviation(SD) and mean square errors(MSEs) results for speed. The comparison shows that the mean square error value obtained from this paper’s method is smaller and has better robustness, indicating that the method is more resilient to FDI attacks.
6. Conclusions
The innovative security solution for the problem of FDI attacks faced by is investigated USVs during data transmission in CPSs. Due to the open nature of WSNs, attackers can tamper with sensor data, leading to poor decision-making in the control center. To solve this problem, a dynamic data encryption method is developed. Encrypting the data before transmission, dynamically updating the key using historical data to enhance the difficulty of cracking. At the same time, constructing a dynamic correlation mechanism between the ciphertext, the key, and the auxiliary encrypted ciphertext. The goal is to create a detection system that can quickly identify and map FDI attacks. In addition, the external noise interference is filtered by the fusion filter, and the weighted fusion algorithm is used to restore the actual information. The effectiveness of the scheme in improving the security of USVs’ data and system reliability is verified by simulation experiments.
Author Contributions
Methodology, Z.L.; Formal analysit, Z.L. and L.L.; Investigationt, Z.L. and L.L.; Writing—original draft, Z.L.; Writing—Review and Editingt, Z.L. and L.L.;Supervision, H.Y. and Z.W.; Funding acquisition, G.D. and C.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the National Natural Science Foundation of China (Grant Nos. 62273172, 62403227), Shanghai Key Laboratory of Power Station Automation Technology, and the Natural Science Foundation of Shandong Province (Grant Nos. ZR2023MF105, ZR2022MF231, ZR2022MF292).
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed at the corresponding authors the system, when the system state information has been tampered with.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Kim, S.; Park, K.J.; Lu, C. A survey on network security for cyber–physical systems: From threats to resilient design. IEEE Communications Surveys & Tutorials 2022, 24, 1534–1573. [Google Scholar]
- Cui, D.; Li, H. Dual self-triggered model-predictive control for nonlinear cyber-physical systems. IEEE Transactions on Systems, Man, and Cybernetics: Systems 2021, 52, 3442–3452. [Google Scholar] [CrossRef]
- Lu, K.D.; Wu, Z.G.; Huang, T. Differential evolution-based three stage dynamic cyber-attack of cyber-physical power systems. IEEE/ASME Transactions on Mechatronics 2022, 28, 1137–1148. [Google Scholar] [CrossRef]
- Yu, Z.; Gao, H.; Cong, X.; Wu, N.; Song, H.H. A survey on cyber–physical systems security. IEEE Internet of Things Journal 2023, 10, 21670–21686. [Google Scholar] [CrossRef]
- Zhang, Y.; Fei, M.; Du, D.; Hu, Y. Security State Assessment in Cyber-Physical Systems Post-DoS Attack Based on Cyber Layer Partitioning. IEEE Transactions on Industrial Informatics 2024. [Google Scholar] [CrossRef]
- Xu, Q.; Li, X.; Jiang, Y.; Zhu, S.; Yang, B.; Chen, C.; Duan, S.; Guan, X. Transportation-Energy-Communication Integrated Management of Ship Cyber-Physical Systems Against Cyber Attacks. IEEE Transactions on Smart Grid 2025. [Google Scholar] [CrossRef]
- Younus, M.U.; Khan, M.K.; Bhatti, A.R. Improving the software-defined wireless sensor networks routing performance using reinforcement learning. IEEE Internet of Things Journal 2021, 9, 3495–3508. [Google Scholar] [CrossRef]
- Zheng, Y.; Hu, J.; Zhao, Y.; Yang, K. Average age of sensing in wireless powered sensor networks. IEEE Transactions on Wireless Communications 2024, 23, 9265–9281. [Google Scholar] [CrossRef]
- Fei, Z.; Wang, X.; Wang, Z. Event-based fault detection for unmanned surface vehicles subject to denial-of-service attacks. IEEE Transactions on Systems, Man, and Cybernetics: Systems 2021, 52, 3326–3336. [Google Scholar] [CrossRef]
- Su, N.; Wang, J.B.; Zeng, C.; Zhang, H.; Lin, M.; Li, G.Y. Unmanned-surface-vehicle-aided maritime data collection using deep reinforcement learning. IEEE Internet of Things Journal 2022, 9, 19773–19786. [Google Scholar] [CrossRef]
- Tang, C.; Zhang, H.T.; Wang, J. Flexible formation tracking control of multiple unmanned surface vessels for navigating through narrow channels with unknown curvatures. IEEE Transactions on Industrial Electronics 2022, 70, 2927–2938. [Google Scholar] [CrossRef]
- Ghoumid, K.; Ar-Reyouchi, D.; Rattal, S.; Yahiaoui, R.; Elmazria, O.; et al. Protocol wireless medical sensor networks in IoT for the efficiency of healthcare. IEEE Internet of Things Journal 2021, 9, 10693–10704. [Google Scholar]
- Karimi-Bidhendi, S.; Guo, J.; Jafarkhani, H. Energy-efficient deployment in static and mobile heterogeneous multi-hop wireless sensor networks. IEEE Transactions on Wireless Communications 2021, 21, 4973–4988. [Google Scholar] [CrossRef]
- Wu, C.; Zhu, G.; Lu, J. Indirect adaptive neural tracking control of USVs under injection and deception attacks. Ocean Engineering 2023, 270, 113641. [Google Scholar] [CrossRef]
- Duan, H.; Yuan, Y.; Zeng, Z. Distributed robust learning control for multiple unmanned surface vessels with fixed-time prescribed performance. IEEE Transactions on Systems, Man, and Cybernetics: Systems 2023, 54, 787–799. [Google Scholar] [CrossRef]
- Liu, C.; Jiang, B.; Wang, X.; Zhang, Y.; Xie, S. Event-based distributed secure control of unmanned surface vehicles with DoS attacks. IEEE Transactions on Systems, Man, and Cybernetics: Systems 2024, 54, 2159–2170. [Google Scholar] [CrossRef]
- Wang, L.; Wang, Z.; Han, Q.L.; Wei, G. Event-Based Variance-Constrained H∞ Filtering for Stochastic Parameter Systems over Sensor Networks with Successive Missing Measurements. IEEE transactions on cybernetics 2017, 48, 1007–1017. [Google Scholar] [CrossRef]
- Zhang, L.; Sun, S. Distributed H∞ fusion filtering for multi-sensor networked systems with DoS attacks and sensor saturations. Digital Signal Processing 2023, 134, 103908. [Google Scholar] [CrossRef]
- Hu, Z.; Chen, K.; Deng, F.; Luo, S.; Hu, S. H∞ controller design for networked systems with two-channel packet dropouts and FDI attacks. IEEE Transactions on Cybernetics 2023, 54, 1661–1670. [Google Scholar] [CrossRef]
- Li, Y.G.; Yang, G.H. Optimal stealthy false data injection attacks in cyber-physical systems. Information Sciences 2019, 481, 474–490. [Google Scholar] [CrossRef]
- Liu, C.; He, W.; Deng, R.; Tian, Y.C.; Du, W. False-data-injection-enabled network parameter modifications in power systems: Attack and detection. IEEE Transactions on Industrial Informatics 2022, 19, 177–188. [Google Scholar] [CrossRef]
- Xiao, L.; Chen, H.; Xu, S.; Lv, Z.; Wang, C.; Xiao, Y. Reinforcement Learning-Based False Data Injection Attacks in Smart Grids. IEEE Transactions on Industrial Informatics 2025. [Google Scholar] [CrossRef]
- Jafari, M.; Rahman, M.A.; Paudyal, S. Optimal false data injection attack against load-frequency control in power systems. IEEE Transactions on Information Forensics and Security 2023, 18, 5200–5212. [Google Scholar] [CrossRef]
- Guo, H.; Sun, J.; Pang, Z.H. Residual-based false data injection attacks against multi-sensor estimation systems. IEEE/CAA Journal of Automatica Sinica 2023, 10, 1181–1191. [Google Scholar] [CrossRef]
- Du, M.; Wang, L.; Zhou, Y. High-stealth false data attacks on overloading multiple lines in power systems. IEEE Transactions on Smart Grid 2022, 14, 1321–1324. [Google Scholar] [CrossRef]
- Chen, X.; Hu, S.; Li, Y.; Yue, D.; Dou, C.; Ding, L. Co-estimation of state and FDI attacks and attack compensation control for multi-area load frequency control systems under FDI and DoS attacks. IEEE Transactions on Smart Grid 2022, 13, 2357–2368. [Google Scholar] [CrossRef]
- Xia, W.; Zhang, Y. Resilient distributed estimation against FDI attacks: a correntropy-based approach. Information Sciences 2023, 635, 236–256. [Google Scholar] [CrossRef]
- Zhang, Q.; He, D. Adaptive neural control of nonlinear cyber–physical systems against randomly occurring false data injection attacks. IEEE Transactions on Systems, Man, and Cybernetics: Systems 2022, 53, 2444–2455. [Google Scholar] [CrossRef]
- Li, T.; Weng, P.; Chen, B.; Zhang, D.; Yu, L. Encryption-based attack detection scheme for multi-sensor secure fusion estimation. IEEE Transactions on Aerospace and Electronic Systems 2024. [Google Scholar]
- Ma, Y.; Nie, Z.; Hu, S.; Li, Z.; Malekian, R.; Sotelo, M. Fault detection filter and controller co-design for unmanned surface vehicles under DoS attacks. IEEE Transactions on Intelligent Transportation Systems 2020, 22, 1422–1434. [Google Scholar] [CrossRef]
- Blum, M.; Micali, S. How to generate cryptographically strong sequences of pseudo random bits. In Providing sound foundations for cryptography: on the Work of Shafi Goldwasser and Silvio Micali; 2019; pp. 227–240.
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).