1. Introduction
In 2024, an information security incident occurred that was considered the worst telecommunications hack in US history. The hacker group “Salt Typhoon,” believed to be linked to the Chinese government, breached several US telecommunications companies, including AT&T, Verizon, and T-Mobile. The hack included communications from the presidential campaign teams of Donald Trump and Kamala Harris, which ultimately became a national issue.
The private sector was no exception. In February 2024, Change Healthcare, a medical billing and insurance processing company, suffered a ransomware attack by the Russian hacker group ALPHV/BlackCat. This incident resulted in the leak of patient data for more than 100 million people. The leaked information included not only patient contact information but also financial and health information, forcing the company to pay a ransom of
$22 million [
2]. These security incidents have caused severe economic losses and significant national and societal reper-cussions. Consequently, security management strategies have become essential components of national institutions and corporate strategies [
3]. Moreover, they are increasingly seen as sources of external competitiveness for organizations [
4].
This study aims to integrate diverse academic and practical insights. It considers corporate security management activities as innovative elements of technology management and also offers recommendations for public institutions and corporations from a managerial perspective [
6]. Additionally, it seeks to objectively verify the role of security management activities using real-world data. Specifically, this study examines whether these activities serve merely as passive risk management measures or as proactive strategic elements. It also explores their direct impact on corporate performance metrics, such as actual sales revenue [
7].
With the efforts of international organizations and governments, the information security management system (ISMS) has become a widely adopted information security management tool. Government authorities actively recommend its implementation in most public institutions and corporations. This study also examines the role of ISMS in the relationship between security management activities and corporate performance [
8,
9].
Previous studies on information security have primarily focused on the inherent objectives of information protection. This focus has resulted in a limited measurement of direct correlations with corporate performance. Consequently, intuitive explanatory power regarding corporate outcomes has been insufficient [
10]. However, this study accepts prior research suggesting that information security as a form of institutional regulation and managerial constraint can lead to innovative activities essential for corporate survival [
11,
12]. This study empirically verifies whether corporate security management activities serve as innovative managerial elements.
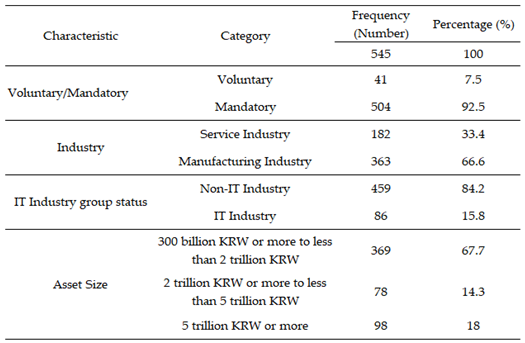
We utilized information security disclosure data from 545 sample companies available on a government portal, along with financial data collected by financial institutions. The sample includes companies with assets of over 300 billion won, categorized by industrial classification codes reported to the National Statistical Office.
Chapter 2 systematically reviews the literature on security management activities. Chapter 3 describes the research methods, including data collection and analysis techniques. Chapter 4 presents the research results, verifying the multiple regression analysis of independent variables with the simultaneous input of control variables. It also examines the interaction effects of the moderator variables for each independent variable. Chapter 5 discusses the research findings based on the interpretation of the results, and Chapter 6 summarizes the significance and limitations, offering implications for future research.
5. Discussion
This study yielded five meaningful points for discussion.
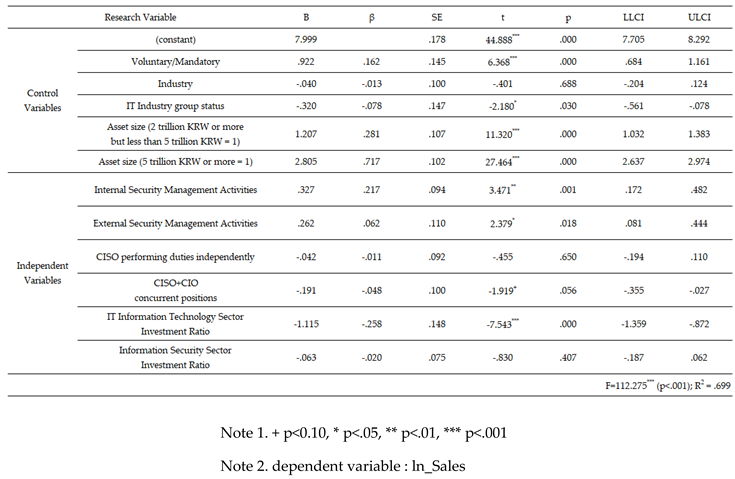
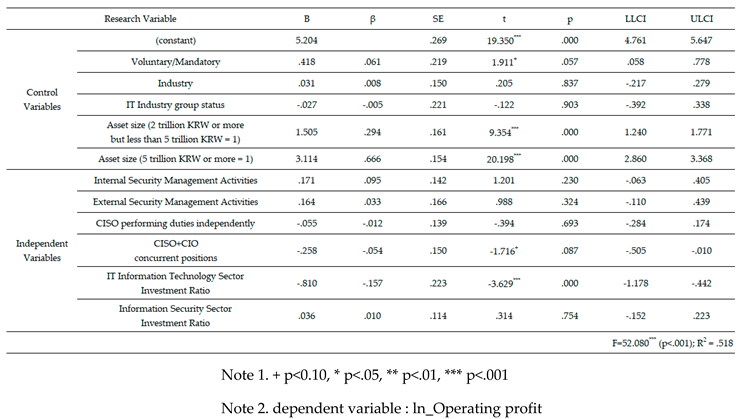
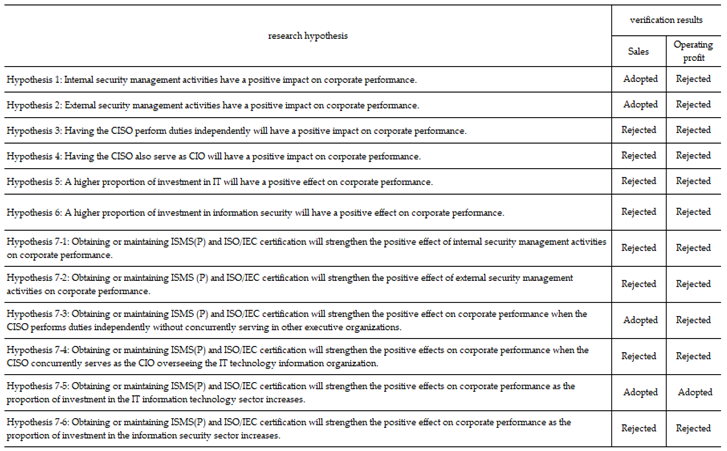
First, although sales and operating profits share commonalities as dependent variables for verifying corporate performance, they are not identical. They produced different results in terms of independent and moderating variables and responses. This indicates that managers should adopt flexible strategic decisions when seeking to achieve management goals through security management activities.
Specifically, H1 (internal security management activities) and H2 (external security management activities) were adopted for sales, but were not supported for operating profits. This suggests that internal and external security management activities incur costs related to information security, which may negatively impact operating profits. However, the positive benefits gained from these activities, such as improved work efficiency and an enhanced external image, are relatively greater. As a result, the overall effect may be favorable for corporate performance.
Seo (2015) argues that corporate security activities can overcome cost issues arising from investment in management resources and improve operational efficiency and market competitiveness, ultimately increasing corporate profits [
5]. Thus, corporate security activities should be accepted as part of an active management strategy.
Shin (2021) also confirmed that security activities in the manufacturing industry can lead to improved management performance by improving business processes in the production process [
67]. Therefore, instead of focusing on the loss of management resources due to increased costs in the management sector caused by internal and external security management activities, a different perspective is required. It is important to consider that the benefits of corporate performance may also be greater.
Second, the perception that security management activities lead only to unnecessary investments in information security or increased management costs should be discarded. These activities should not be viewed as obstacles to management. Instead, they should be accepted as essential elements of management innovation.
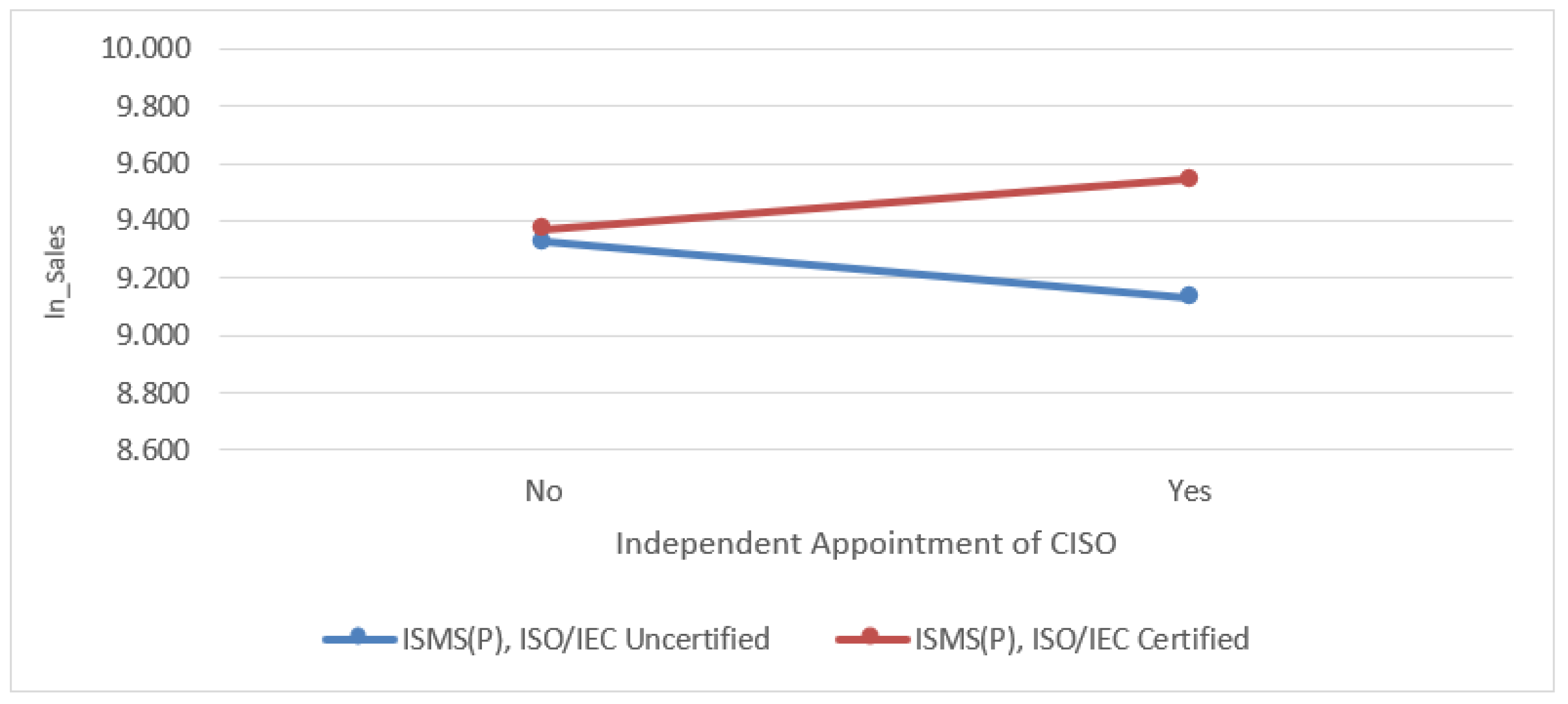
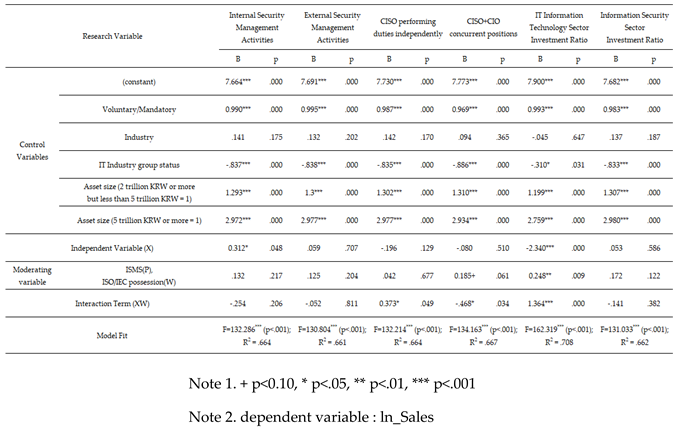
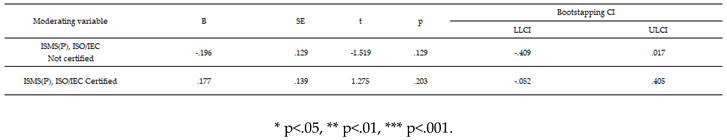
Specifically, we did not confirm whether H7-3, the sole responsibility of the CISO, had any impact on sales. However, the interaction with information security management tools was found to have a statistically significant positive effect. This suggests a moderating role of these tools in enhancing relationships. This can be accepted as an example of how strict security management activities can act as innovation factors.
In addition, in a multiple regression analysis of the control variables, companies obligated to disclose information security showed a statistically significant positive effect on corporate performance. This is in comparison with companies that voluntarily disclose. These results further support this hypothesis.
Furthermore, Byun (2019) stated that personal information protection activities regulated by legal systems can enhance the competitiveness of IT companies [
11]. Jung (2007) argued that government regulations paradoxically stimulate technological innovation in companies [
12]. This demonstrates that information security, although regulated, has broader implications. It can also act as an innovative element that enhances corporate competitiveness through the improved operational efficiency resulting from regulatory compliance.
Third, in a growth-oriented management structure requiring significant strategic investment in IT, short-term financial performance may not fully reflect the benefits of security management activities. It is important to recognize that such benefits may take time to materialize. The results of multiple regression analysis of the control variables support this view. They showed that the positive effect on corporate performance is more pronounced in manufacturing industries and companies with larger asset sizes, whereas the negative effect is more noticeable in the IT industry.
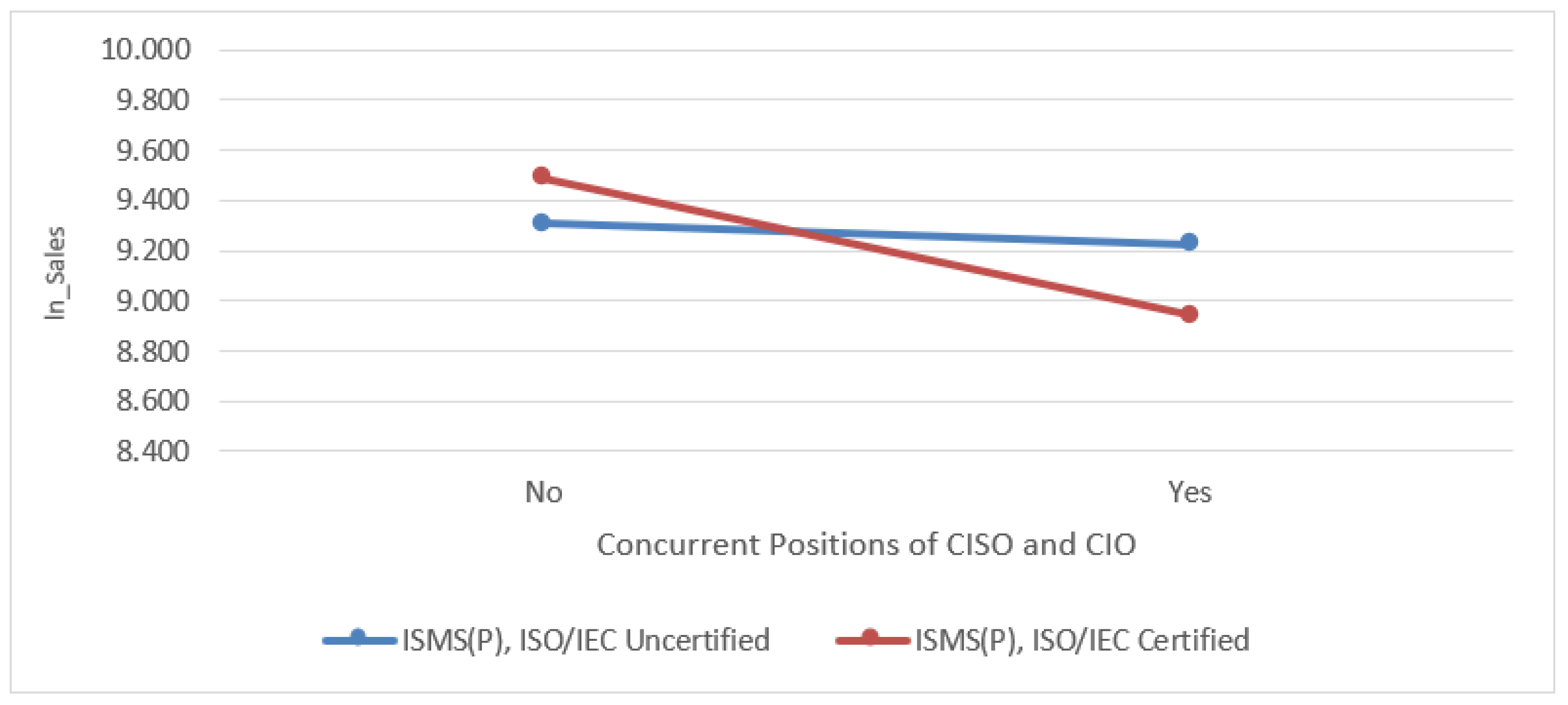
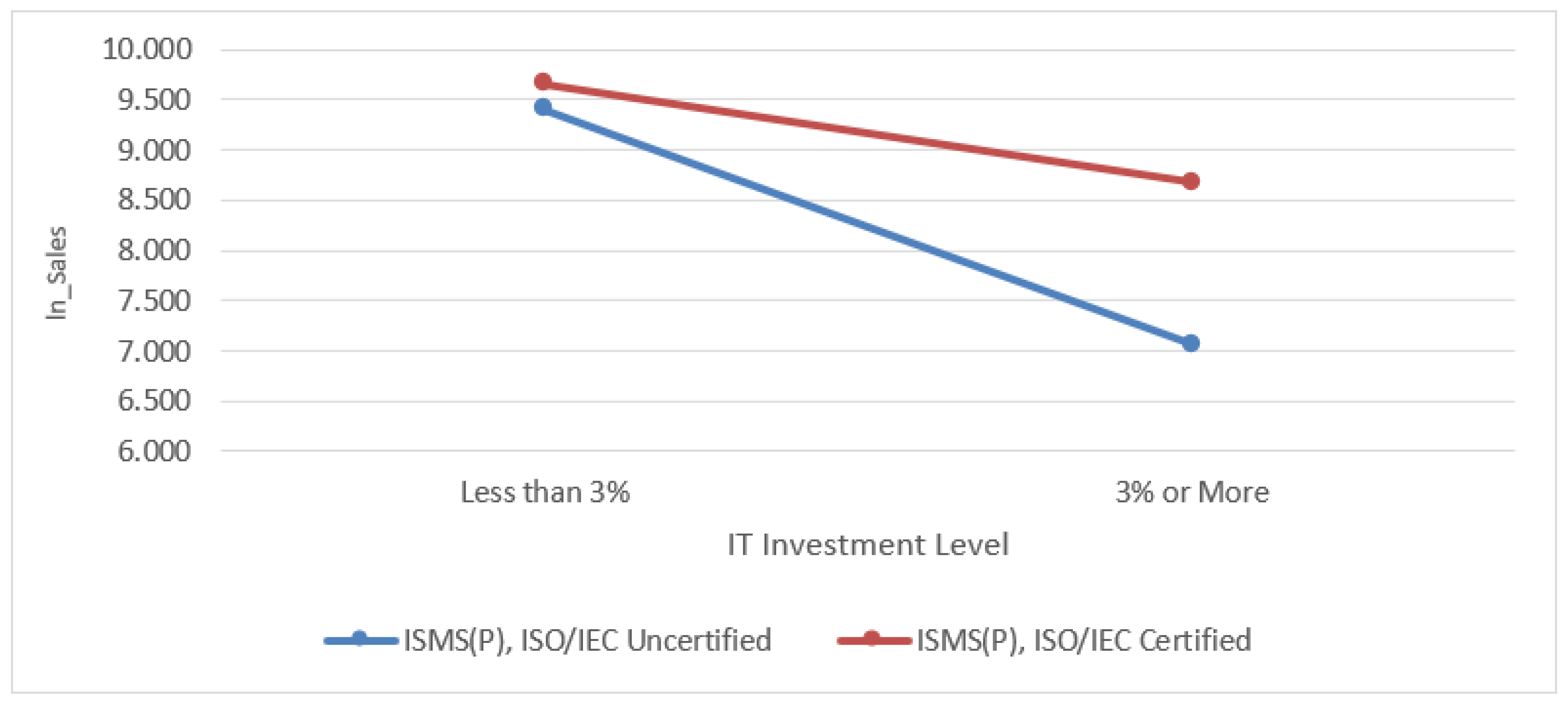
Additionally, in the multiple regression analysis of the independent variables, H4 (when the CISO and CIO are combined) and H5 (when the investment ratio in the IT sector increases) also show a significant negative impact. In other words, management activities such as combining the CIO’s role with IT system operations or increasing direct investment levels in the IT sector have a negative impact on financial performance.
Contrary to the findings of this study, Alharbi and Gregg (2022) and Mithas and Rust (2016) state that increased investment in IT has a positive impact on corporate performance. Of course, these studies did not simply emphasize investment in IT. They emphasized the importance of harmony with IT security investments [
80] and alignment with corporate management strategies [
14].
However, even after setting aside the ongoing IT debate since Robert Solow's (1987) IT Productivity Paradox [
31], the issue remains relevant. Managers' choices regarding the proportion of their investment in the IT sector should be flexible. These decisions must account for corporate characteristics and the business environment.
Lee, Shin, and Lee (2022) also revealed in their study on the introduction of 4th industrial revolution technologies and corporate productivity that the outcomes vary among companies. They note that the results of introducing new technologies such as IT may appear with a time lag [
19].
Additionally, Winarno, Tjahjadi and Irwanto (2021), as well as Park, Koo, Ham and Lee (2006), presented similar findings. They showed that financial returns on resources invested in IT informationization and other growth foundations require a certain amount of time. These results partially support the findings of the present study.
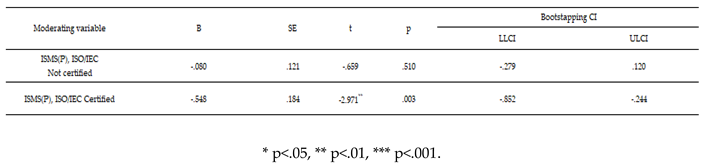
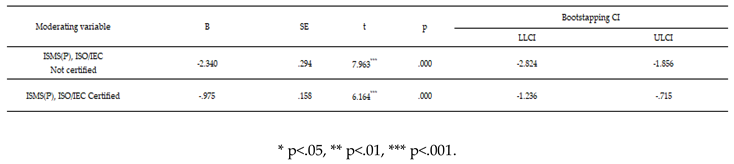
Fourth, information security management tools, such as ISMS, should be flexibly considered for adoption by companies with a future growth-oriented management structure. Specifically, in the moderation effect analysis of ISMS(P) and ISO/IEC certification status on sales revenue, the adoption of information security management tools had a notable impact. The strategic use of tools such as the ISMS significantly strengthened the negative effect of H7-4 (CISO+CIO dual-role operation). This also mitigates the negative effect of H7-5 (IT investment ratio), shifting it in a positive direction.
Notably, the moderating effect of mitigating the negative impact of the proportion of IT investment on the IT department was also confirmed. Based on these findings, two security management strategies are proposed.
First, for small and medium-sized venture companies or technology-based firms, where R&D is a core management strategy, having a CISO + CIO dual role may be unavoidable. In such business environments, the timing of adopting information security management tools, such as an ISMS, should be flexibly applied based on the company’s situation. For example, when small-scale, R&D-focused IT-based technology companies need to launch products or services quickly, strict adoption of tools such as an ISMS may not be suitable. In such cases, these tools may hinder competitiveness in fast-paced environments.
Research on the effects of the CISO’s dual roles and the mutual effects between the CISO and the ISMS is an important area of interest in information security. Choi and Kim (2024) measured the correlation between the CISO’s dual roles and the adoption of information security management tools, such as ISMS [
30]. Additionally, Ciekanowski et al. (2024) explored how the CISO's role within the organization affects ISMS. They concluded that the CISO's strategic operations help prevent cybersecurity incidents and secure sustainable competitive advantages [
28].
However, this analysis has limitations when proposing security management strategies tailored to corporate characteristics. It is also difficult to use these findings as a basis for determining the timing of ISMS implementation or identifying the appropriate target group of companies.
The next proposed security management strategy is that, in a corporate environment where continuous investment in IT is required, the adoption of information security management tools, such as ISMS, should be actively considered. Even if continuous investment in IT results in short-term negative effects on external growth and adds to ongoing management burdens, these challenges should not discourage action. It is still advisable for managers to consistently implement security management activities. This includes the adoption of ISMS and other information security management tools.
This is particularly effective for large companies with sufficient financial capacity to withstand short-term financial burden. This is supported by the results of the multiple regression analysis on the control variables, which showed that the larger the asset size, the more significant the positive impact on sales and operating profits.
In particular, Ilmudeen and Bao (2018) [
15] empirically demonstrated the full mediating effect of IT resource management capabilities on corporate performance. This finding indirectly supports the results of this study. This reinforces the moderating effect of information security management tools such as ISMS, which incorporate managerial elements related to IT resources [
15].
Finally, this reflects the research results showing that the proportion of investment in information security is unrelated to corporate performance. New investments in information security technology or security equipment are expected to be integrated into IT information systems as subordinate components. Due to the technical characteristics of IT, these investments are often patched together, resulting in concurrent investments. This is because they coexist within the IT Governance environment, making it difficult to discern their individual effectiveness [
39,
80].
In a study by Shariffuddin and Mohamed (2020), which effectively explained the importance of IT Governance, it was confirmed that investments in IT and information security sectors cannot be separated [
39]. Many previous studies have recognized the introduction of new security equipment or security technology as an element of innovation. They expect technological innovation to improve corporate performance [
82].
However, it is now expected that this will be interpreted differently. Owing to changes in the IT environment, the IT sector cannot be separated from the information security sector.
6. Conclusions
This study verifies whether the security management activities implemented by managers in business practices affect the financial performance of companies, such as sales. In particular, this study confirms the moderating effect of information security management tools, such as the ISMS. It contributes academically by proposing practical policies and indirectly demonstrating that security management activities are elements of innovation.
6.1. Practical Implications
First, it can raise managers' awareness of the increased business risks posed by security incidents such as IT hacking and information leaks. Heightened awareness is crucial for proactive risk management. In addition, it can provide a decision-making guide for strategic security management activities tailored to each company’s characteristics and business environment.
Second, it provides a basis for reevaluating the role and strategic position of the CISO. This is important to realize the positive business benefits of security management activities. These benefits include improved operational efficiency and enhanced external trust.
Third, it can help raise awareness that the adoption and maintenance of information security management tools, such as ISMS, are necessary from a strategic management perspective.
6.2. Academic Implications
First, research on information security should not be limited to the prevention of cybersecurity incidents at the national or corporate levels. Managers should be accepted as essential elements of innovation, moving beyond the traditional concept of information security. Ultimately, this should be expanded to the concept of security management and incorporated into technology management.
Second, starting with this study, we can expect that research variables related to security management will continue to be developed, leading to the emergence of various follow-up studies.
6.3. Limitations of the Study and Future Research Directions
First, the latent variables influencing the relationship between corporate security management activities and financial performance are not clearly defined. This study mainly focused on an objective analysis. Consequently, there was insufficient consideration of the exploratory and qualitative components.
Second, while this study focused on a cross-sectional empirical analysis of its research objectives, measuring the longitudinal changes in each research variable could yield more robust results. In particular, observing IT investments over the long term could enrich the connections with prior studies.
Third, further subdivision of the sample companies is necessary to address the diverse research objectives more effectively. This allows for a more detailed and targeted analysis. In particular, securing additional research samples from small and medium-sized venture companies would be valuable. This would enable meaningful exploration of the security management activities of early stage firms with less than 300 billion KRW in revenue, which was not the focus of this study.
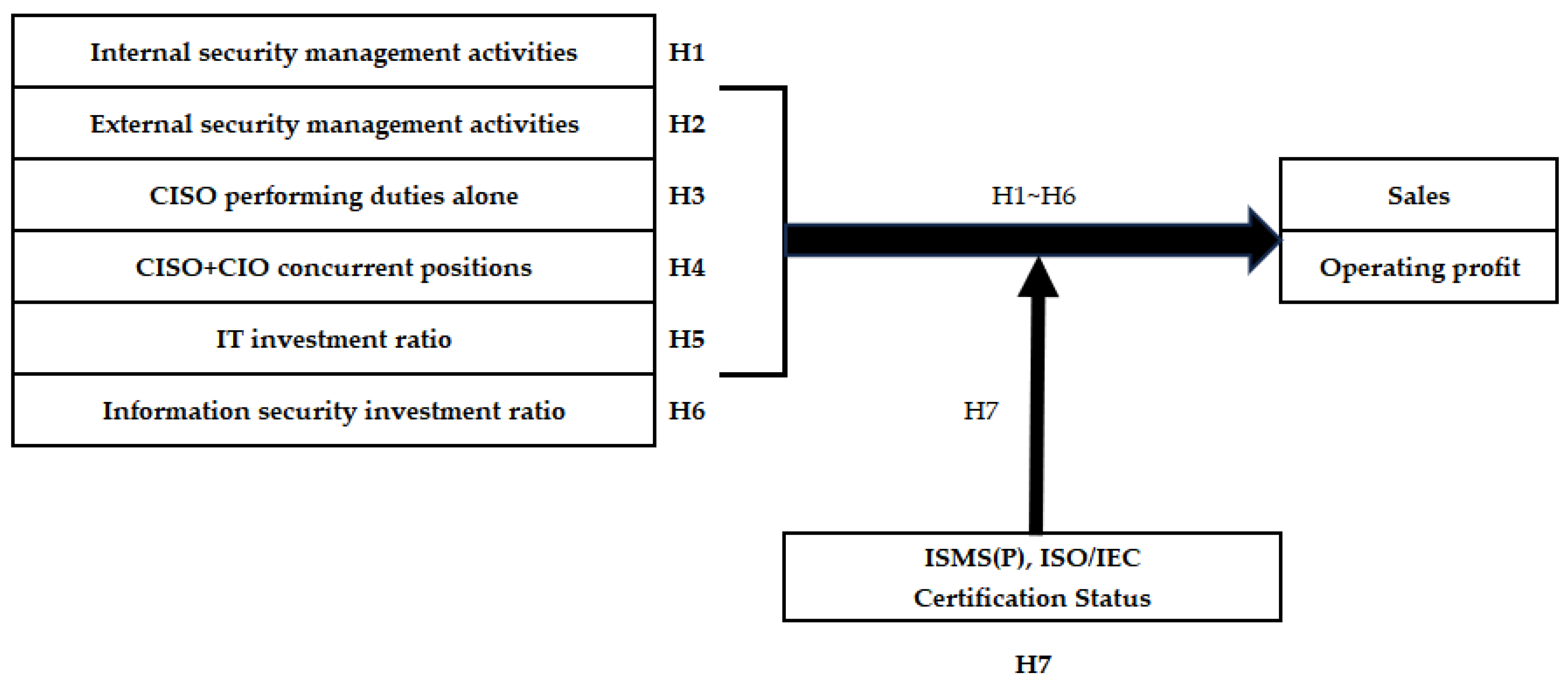
Figure 1.
Research Model.
Figure 1.
Research Model.
Figure 2.
Influence of ISMS(P), ISO/IEC possession status on the correlation between CISO's independent work performance and sales amount.
Figure 2.
Influence of ISMS(P), ISO/IEC possession status on the correlation between CISO's independent work performance and sales amount.
Figure 3.
Influence of ISMS (P), ISO/IEC certification on the correlation between CISO+CIO dual roles and sales revenue.
Figure 3.
Influence of ISMS (P), ISO/IEC certification on the correlation between CISO+CIO dual roles and sales revenue.
Figure 4.
Influence of ISMS (P), ISO/IEC certification on the correlation between IT investment ratio and sales revenue.
Figure 4.
Influence of ISMS (P), ISO/IEC certification on the correlation between IT investment ratio and sales revenue.
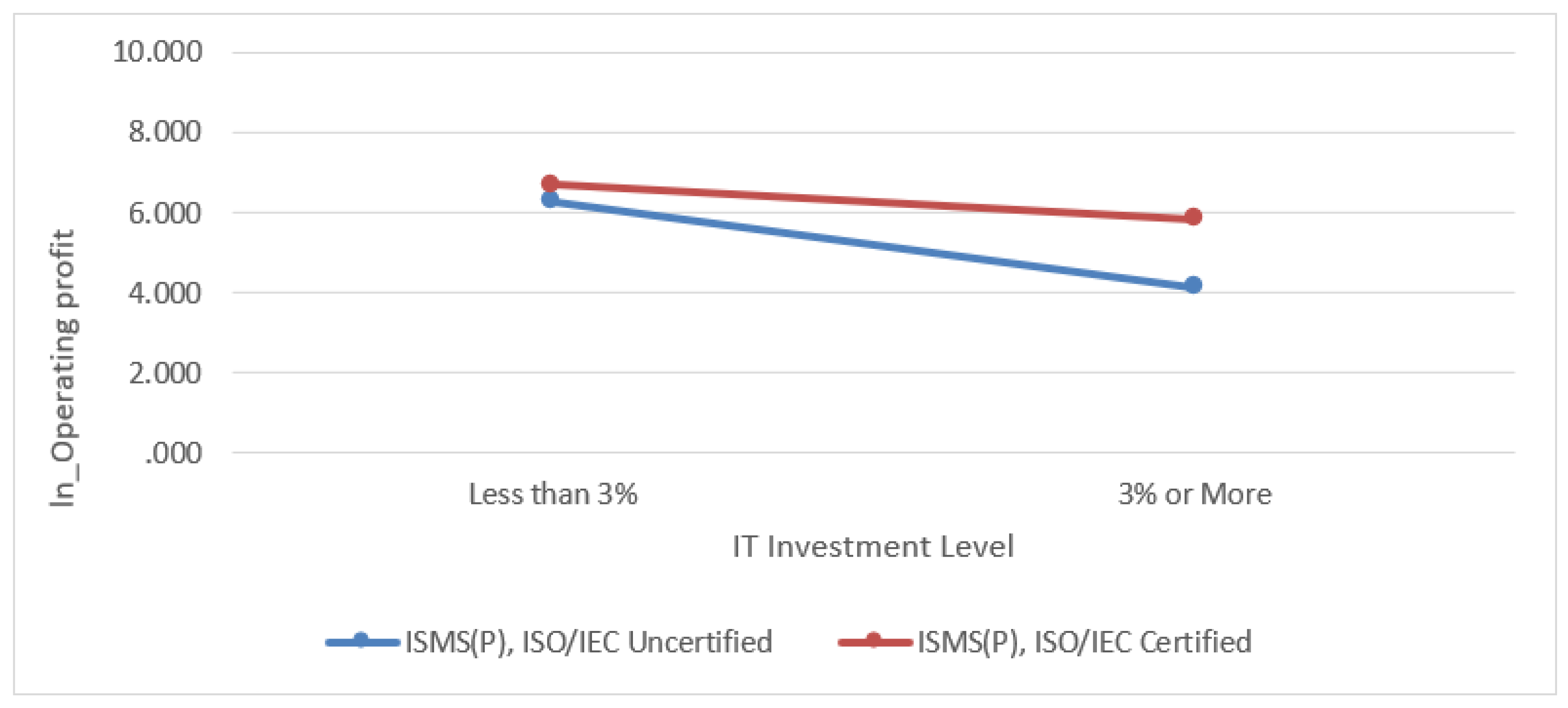
Figure 5.
Influence of ISMS (P), ISO/IEC certification on the correlation between IT investment ratio and operating profit.
Figure 5.
Influence of ISMS (P), ISO/IEC certification on the correlation between IT investment ratio and operating profit.
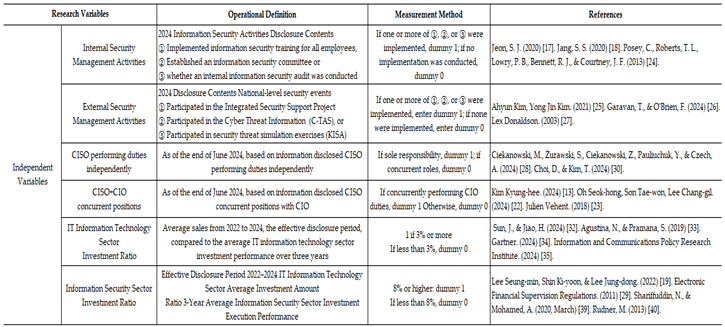
Table 1.
Independent Variables.
Table 1.
Independent Variables.
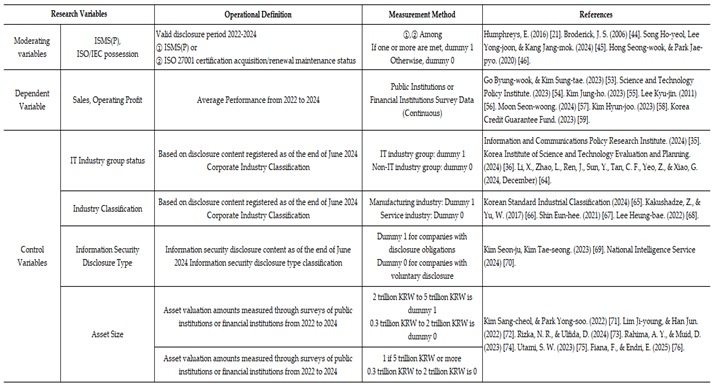
Table 2.
Moderating variables, dependent variables, and control variables.
Table 2.
Moderating variables, dependent variables, and control variables.
Table 3.
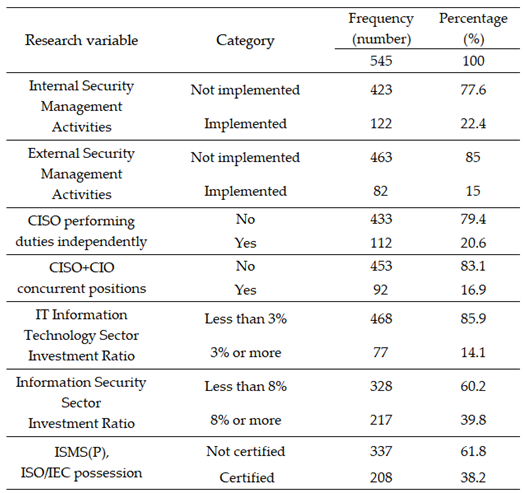
Characteristics of Research Subjects.
Table 3.
Characteristics of Research Subjects.
Table 4.
Descriptive statistical analysis of research variables (categorical variables).
Table 4.
Descriptive statistical analysis of research variables (categorical variables).
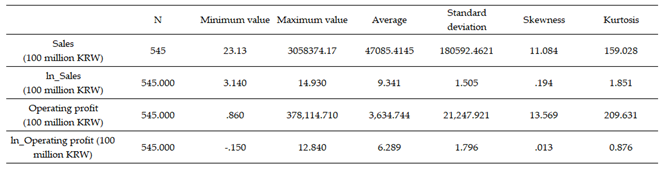
Table 5.
Descriptive statistics analysis of dependent variables.
Table 5.
Descriptive statistics analysis of dependent variables.
Table 6.
Relationship analysis of the impact of security management activities on sales revenue.
Table 6.
Relationship analysis of the impact of security management activities on sales revenue.
Table 7.
Relationship analysis of the impact of security management activities on operating profit.
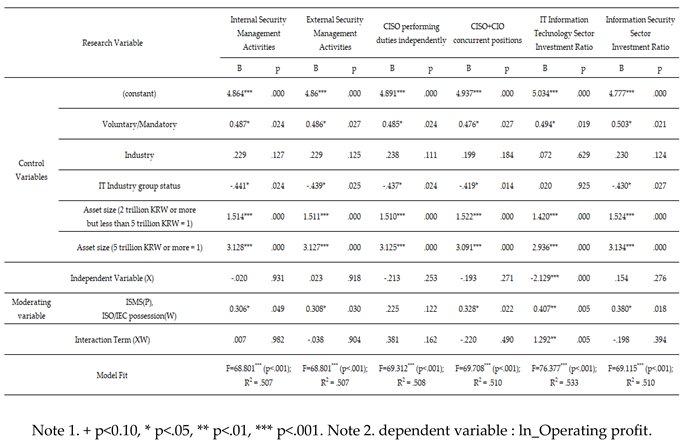
Table 7.
Relationship analysis of the impact of security management activities on operating profit.
Table 10.
Moderating effect analysis of ISMS (P), ISO/IEC certification status on the relationship between the impact of CISO+CIO dual roles on sales revenue (Bootstrapping method).
Table 10.
Moderating effect analysis of ISMS (P), ISO/IEC certification status on the relationship between the impact of CISO+CIO dual roles on sales revenue (Bootstrapping method).
Table 11.
Analysis of the moderating effects of ISMS (P), ISO/IEC certification status on the relationship between IT investment ratio and sales revenue (Bootstrapping method).
Table 11.
Analysis of the moderating effects of ISMS (P), ISO/IEC certification status on the relationship between IT investment ratio and sales revenue (Bootstrapping method).
Table 12.
Analysis of the moderating effect of ISMS (P), ISO/IEC certification on the relationship between security management activities and Operating profit (Process Macro Model 1).
Table 12.
Analysis of the moderating effect of ISMS (P), ISO/IEC certification on the relationship between security management activities and Operating profit (Process Macro Model 1).
Table 13.
Analysis of the moderating effect of ISMS (P), ISO/IEC certification on the relationship between IT investment ratio and operating profit (Bootstrapping method).
Table 13.
Analysis of the moderating effect of ISMS (P), ISO/IEC certification on the relationship between IT investment ratio and operating profit (Bootstrapping method).
Table 14.
Summary of research hypothesis verification results.
Table 14.
Summary of research hypothesis verification results.