Submitted:
09 May 2025
Posted:
13 May 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
- The paper presents a thorough security assessment of EV Android applications. This includes both static and dynamic analysis phases, knowledge building, and a security assessment phase, providing a detailed understanding of the cybersecurity landscape in these applications.
- The research identifies major security flaws such as poor authentication, broken encryption, insecure communication, and more. It also pinpoints the OWASP top ten vulnerabilities and analyzes for CWE, contributing valuable insights to the field of cybersecurity in EV applications.
- The paper conducts a detailed analysis of the requested permissions in these applications. It also identifies functionalities that are not present in official EV applications, leading users to rely on third-party applications, thereby increasing their attack surface.
- Finally, the research proposes defensive measures based on OWASP and CWE defenses to mitigate the identified security issues to enhance the security of EV Android applications.
1.1. Paper Organization
2. Literature Review
3. Application Selection and Functionality Influence
3.1. Group:1 - EV Manufacturers Applications
- TESLA: this user-friendly application is designed for managing Tesla vehicles. It offers features like tracking your vehicle, starting or stopping charging remotely, and even locking and unlocking your car. Additionally, it helps users locate charging stations, schedule service appointments, and download the latest updates.
- Mercedes: this application locks or unlocks the doors, remote starts, tracks the vehicle, records driving habits, and schedules service appointments.
- BMW: it performs vehicle tracking, allows remote starts, schedules service appointments, and allows maintenance updates.
- Nissan: this application is all about convenience for Nissan vehicle owners. It enables users to locate and track their vehicles and even offers keyless entry and remote start capabilities. It’s compatible with Alexa-enabled devices and Google Assistant, allowing users to use voice commands to start the car, turn on the lights, and interact with their vehicle in various other ways.
- Volkswagen: the application provides remote access, reserves parking spots, schedules service appointments, and downloads updates.
- Jaguar InControl: it can schedule maintenance and service appointments, remotely activate the vehicle’s horn and lights, access trip history and driving statistics, and remotely start.
- FordPass: it provides details on ingress fuel levels, allows lock/unlock of Ford vehicles, checks vehicle health information, finds parking spots, and uses platform assistance.
- MITSUBISHI: enables users to remotely control climate settings, manage anti-theft functions, monitor current travel information, and manage chargings.
- Land Rover InControl: allows users to remotely unlock doors, start the engine, update climate settings, use the vehicle locator, and receive maintenance alerts.
- MY FERRARI: allows users to oversee and manage Ferrari vehicles from a distance, review details of the vehicle, access vehicle location tracking, and start or stop the engine, and manage vehicular updates.
3.2. Group:2 - Third-Party Applications
- EVConnect: this app is a handy tool for EV drivers. It helps users find EV charging stations, pay for charging services, and send notifications when the charging is complete.
- EVgo: allows users to check charging information, locate charging stations, and book a charger. This application also supports loyalty programs and coupons.
- Plugshare: this app helps users find charging stations, pay for services, and monitor the charging process. It allows users to share their experiences, stories, and photos, and rate their overall experience.
- ChargeHub: this app is a helpful assistant for electric vehicle owners. It helps users find, compare, and navigate to charging stations. It provides updates on the availability of stations, making it easier for users to plan their charging.
- EV-Energy: this app is designed to help EV owners manage their home charging needs. It includes features like setting reminders, tracking charging time, and monitoring energy use, making home charging an ease for EV owners.
- A better route planner (ABRP): offers trip planning tools for, taking into account weather updates, traffic situations, and charging station amenities.
- Caura: it allows users to track car-related expenses, track charging costs, update reminders, and track vehicles.
- Bp Plus: this application is designed for businesses that manage fleets and provide battery-saving insights, find nearby charging stations, and give driving habits.
- Optiwatt: allows EV owners to optimize their charging schedule based on energy costs and grid demand. The application also provides analytics and reports on charging behavior and energy consumption.
- Octopus electroverse: gives users access to electric vehicle charging stations and uses smart charging features to take advantage of off-peak electricity pricing.
3.3. Comparative Analysis of Functionalities Offered by EV Applications
- F1.
- Charging points- These features allow users to search nearby charging point locations.
- F2.
- Vehicle controls- This allows monitor and control different functions of vehicles.
- F3.
- Calls and messages- This helps in making and receiving calls and messages in mobile applications.
- F4.
- Media controls- This controls media, audio, and other entertainment options.
- F5.
- Remote unlock- As name suggests, it unlocks a car remotely.
- F6.
- Charging status- This feature provide charging update of a vehicles.
- F7.
- Vehicle tracking- This will track the location of vehicles using the GPS coordinates.
- F8.
- Car health report- This returns a report on the health and performance of the underlined vehicle.
- F9.
- Payments- This features let a customer pay for various services, like charging.
- F10.
- Amenities- The function helps a user to find hotels and other services.
- F11.
- Energy use tracking- It tracks and analyzes the energy used by a vehicle.
- F12.
- Rewards and coupons- As the name suggests, it is linked to receiving and redeeming rewards and coupons as users use certain services.
4. Security Accessment Methodology
4.1. Static Analysis Phase
- Application permissions.
- Third-party libraries.
- Strings and XML files.
- Improper resource handling.
- Application configuration.
- Activities, services, receivers, and intents.
- Unused Variables and Resources.
4.2. Dynamic Analysis Phase
- Application interactions, inputs, outputs, and interprocess communication.
- Network activities, network protocols, traffic flow, domains, and APIs.
- System calls, file operations, processes, and socket operations.
- Resource consumption, CPU usage, memory usage, and battery usage.
- Event logs, malicious behaviors, dynamic code loading, privilege escalation, and data exfiltration.
- Obfuscation and encryption, and anti-debugging.
4.3. Knowledge Building Phase
- Data cleaning and transformation: This is the process of removing or correcting inaccurate, incomplete, or irrelevant data from the data set, such as missing values, outliers, and duplicates.
- Data Integration and Visualization: It is the process of combining or merging data from different sources or formats into a unified data set and then displaying graphical representations of the data.
- Data Mining and Interpretation: This is the process of discovering and extracting useful patterns, and trends from the data.
4.4. Security Assessment Phase
- Analysis of requested permissions, their necessity, legitimacy, and risk level.
- Identification of OWASP Top Ten vulnerabilities, which serves as a standard reference for identifying critical security risks.
- Identifying the severity and impact of vulnerabilities, their likelihood of occurrence, and potential consequences.
- Analysis for CWE [14].
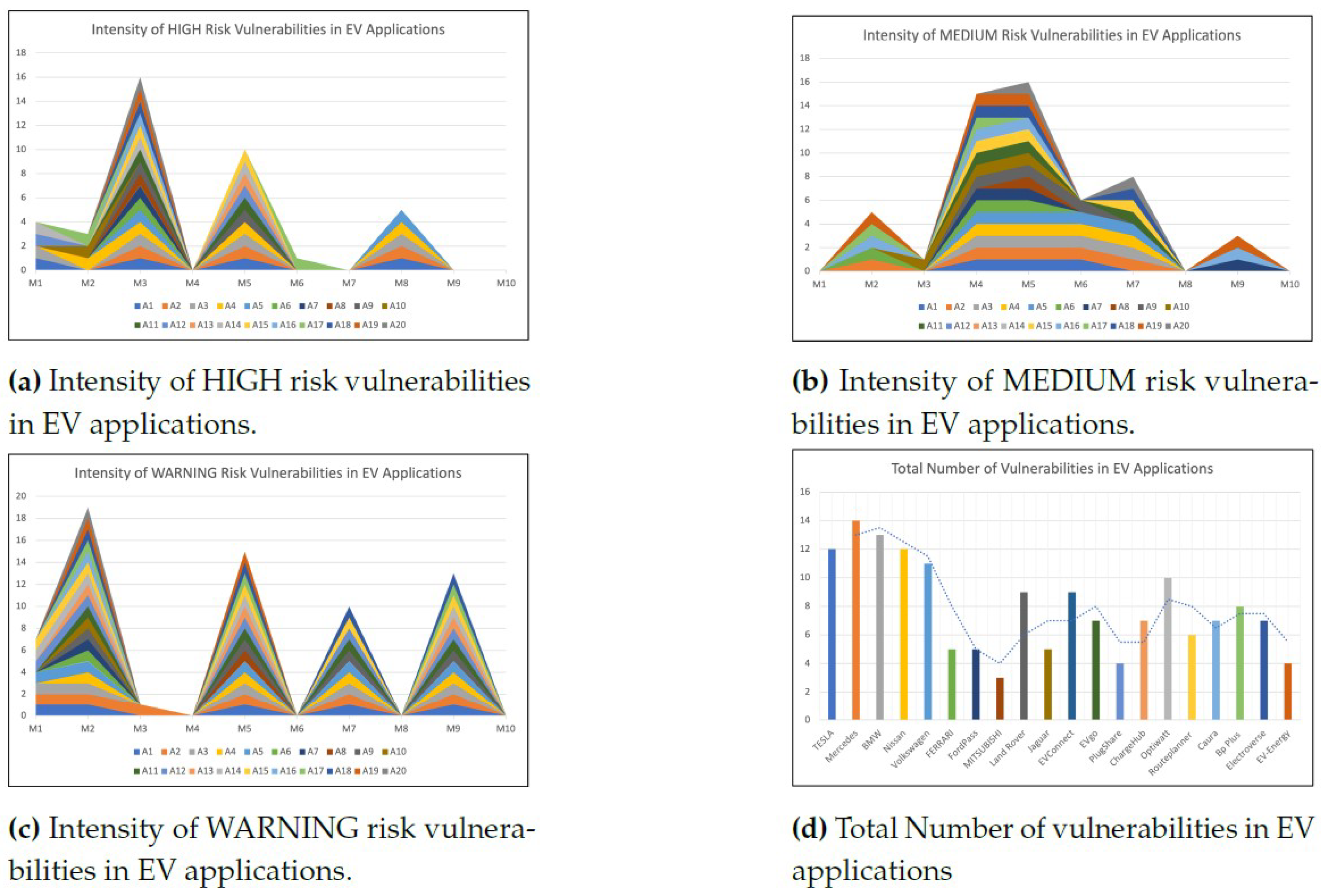
5. Results and Findings
5.1. Analysis of Requested Permissions
- P1
- Access precise location.
- P2
- Access Camera.
- P3
- Read and Update Contacts.
- P4
- Manage Calendar.
- P5
- Read/Write External storage.
- P6
- Access Call logs/records.
- P7
- Access Accounts and Stored Credentials.
- P8
- Connect Bluetooth.
- P9
- Access network state.
- P10
- Search and Connect WIFI.
5.2. Identification of OWASP top ten vulnerabilities
- V1
- Improper Platform Usage, root functionality, hardware manipulation, or bypassing security measures that can result in unauthorized access, privilege escalation, or device compromise.
- V2
- Insecure Data Storage, storing data in plain text, using weak encryption, or lacking access controls.
- V3
- Insecure communication, unauthenticated connections, exposing data to interception, or leaking data to third parties.
- V4
- Insecure authentication, default or hard-coded credentials, lagging password policies, or relying on single-factor authentication.
- V5
- Insufficient cryptography, using outdated or broken algorithms, using weak or predictable keys, or implementing cryptography incorrectly.
- V6
- Insecure Authorization, lack of role-based access control, lack of checking permissions, or excessive privileges. This may result in unauthorized access, privilege escalation, or data exposure.
- V7
- Quality of the client code, using insecure libraries or frameworks, having vulnerabilities or bugs in the code, or lacking code review or testing.
- V8
- Code Tampering, adding malicious code, removing security checks, or hiding vulnerabilities.
- V9
- Reverse Engineering, encryption keys, API keys, or credentials.
- V10
- Extraneous Functionality, backdoors, debug functions, or test functions.
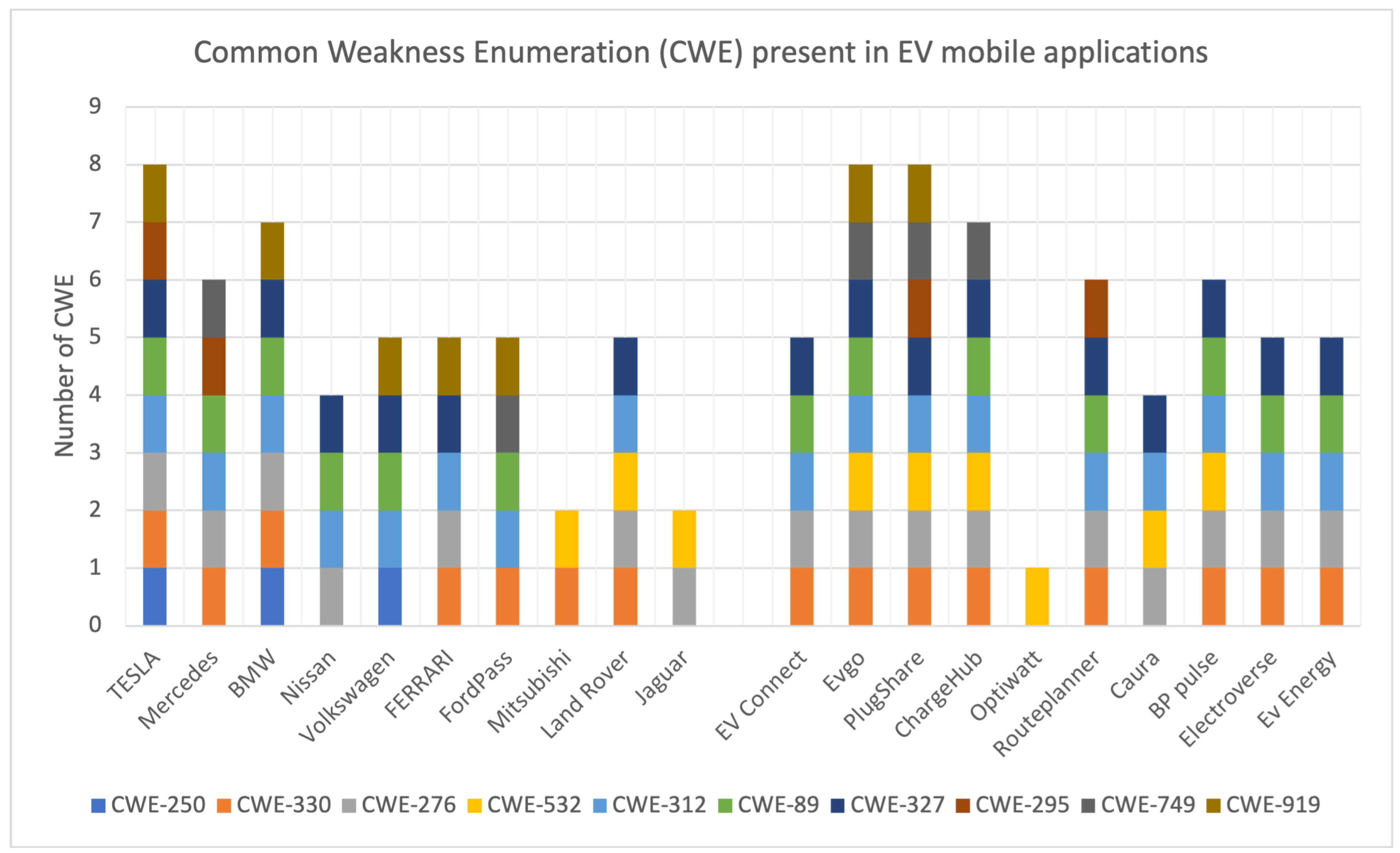
5.3. Analysis for CWE
- CWE-250: Execution with Unnecessary Privileges.
- CWE-330: Insufficiently random values are used and vulnerable to spoofing attacks.
- CWE-276: Incorrect Default Permissions.
- CWE-532: Insertion of sensitive data into the log file, passwords, tokens, or keys, into log files by mistake.
- CWE-312: Cleartext Storage of Sensitive Information.
- CWE-89: Improper neutralization of special elements used in a SQL command (’SQL injection’).
- CWE-327: Use of a Compromised or Risky Cryptographic Algorithm.
- CWE-295: Improper Certificate Validation.
- CWE-749: Exposed to dangerous methods or functions.
- CWE-919: Improper handling of sensitive data, insecure communication, or lack of authentication.
6. Discussion
6.1. User Impact Analysis
6.1.1. Case Study: Insecure Data Handling in “PlugShare”
6.2. Best Practices for Developers
7. Defensive Measures
7.1. CWE Defenses
- CWE-250: Execution with Unnecessary Privileges It is recommended to use the principle of least privilege to limit the privileges or permissions of the application [66]. Also, use user ID and process ID in containerization to isolate the application from the rest of the system or environment, and secure coding and security by design techniques to ensure that the application is safe.
- CWE-330: Use of Insufficiently Random Values Developers can use cryptographically secure pseudorandom number generators (CSPRNGs) to generate random values for security purposes [67]. Also, it is recommended to use long, secure random values to resist brute-force or guessing attacks.
- CWE-276: Incorrect Default Permissions It can be essential to use secure file permissions and access control mechanisms and perform input sensitization for chmod, chown, and ACLs, among others.
- CWE-532: Insertion of sensitive information into log files Developers may use different data masking or data obfuscation techniques to protect sensitive information in log files and implement secure log libraries to write log files for the application, such as using Logback, SLF4J, or CocoaLumberjack [68].
- CWE-312: Storage of sensitive information in clear text It can be important to implement encryption at rest, hashing, and masking while storing sensitive information. Additionally, do not store any information in plain text on the device. Moreover, developers can use data minimization to reduce the amount or type of sensitive information that is stored.
- CWE-89: Improper Neutralization of Special Elements Used in an SQL Command (’SQL Injection’) This vulnerability can be mitigated by using parameterized queries or prepared statements to prevent SQL injection [69]. Similarly, implementation of input validation and output encoding can be used to prevent SQL injection.
- CWE-327: Use of a Compromised or Risky Cryptographic Algorithm It is recommended to use resilient and reliable cryptographic algorithms or protocols to protect data. Additionally, implement secure key management and distribution mechanisms to protect keys and use mechanisms such as FIPS 140-2, NIST SP 800-57, or PKCS [70].
- CWE-295: Improper Certificate Validation Developers are encouraged to use SSL/TLS certificates from trusted authorities and verify trusted authorities, such as VeriSign, DigiCert, and Let’s Encrypt. Similarly, they can use certificate pinning to prevent accepting expired or forged certificates.
- CWE-749: Exposed Dangerous Method or Function It is important to implement secure authentication and authorization mechanisms to protect the interface and secure communication to protect the data.
- CWE-919: Weaknesses in Mobile Applications The application can be secured using the OWASP MSTG and the OWASP MASVS to test and verify the security of mobile applications.
7.2. OWASP Defenses
- M1: Improper use of the platform This can be addressed by using secure coding approaches [71], limiting sticky intentions, and restricting communication to only consent-based communication. Moreover, developers can limit the use of public intents and libraries, implement access control and authorization mechanisms, and check for possible misconfigurations.
- M2: Insecure Data Storage Developers can use standard encryption algorithms such as AES 256-bit and triple DES, they can also, implement data security measures and harden the code using data masking, data obfuscation, or data minimization [72]. Finally, they can deploy multiple authorization checks that can grant or deny access to data in storage based on the user’s identity.
- M3: Insecure communication Developers can use SSL/TLS protocol to send and receive information and protect it from eavesdropping, tampering, and spoofing. They can verify the authenticity of SSL/TLS certificates before sending or receiving sensitive information. Finally, they should avoid sending sensitive information through SMS, email, and phone notifications.
- M4: Insecure authentication This vulnerability can be significantly addressed by conducting thorough tests, audits, and log data security measures with encryption, hashing, or masking. Moreover, It is required to authenticate on the server side and store data on the mobile device only after verification. Finally, encrypt client-side data when necessary, such as user preferences, session tokens, and keys.
- M5: Insufficient Cryptography It is significantly important to implement strong encryption algorithms to protect sensitive data in transit or at rest, such as AES, RSA, or SHA-256. Developers need to implement long and secure keys for encryption and not store them in device or application code. Also, they need to up-to-date encryption protocols. Encryption protocols such as SSL/TLS, HTTPS, or PGP. it is recommended to never use outdated algorithms and encryption protocols that are prone to weaknesses.
- M6: Insecure Authorization It can be significantly helpful to implement multiple authorization checks to verify user permissions or roles. Also, developers can use secure authentication protocols, such as two-factor authentication with OAuth, or OpenID Connect. In addition, they can regularly update user permissions and roles and revoke unnecessary rights.
- M7: Poor Code Quality It is beneficial to use a code review and software quality assurance testing (SQA) to fix code security weaknesses or flaws, such as broken encryption, weak hashing, or data leaks [73]. This can be fixed by updating the application regularly and performing bug fixes. Moreover, this issue can be significantly resolved if, a developer performs static and dynamic code analysis and fixes the identified issues.
- M8: Code tampering To get ahead of tempering, it is beneficial to use a code signing technique. This will increase the integrity of the code and it will also prevent code tampering and also it will stop dynamic code loading [74].
- M9: Reverse engineering is very common in Android applications, as attackers can reverse an application to see and exploit its vulnerabilities. Therefore, it is required for developers to use different code obfuscation techniques, and anti-debugging techniques that will make the code difficult to reverse engineer and to see its initial code [75,76].
- M10: Extraneous functionality Application developers can use a code-releasing mechanism when developing an application to ensure the quality and security of each interactional release. This will keep track of introduced functionalities and mitigate the impact of extraneous functionality that becomes obsolete by simply removing it. Finally, developers can use different code monitoring and runtime analytics platforms to observe and improve application crashes and fix them in the next releases.
7.3. Long-Term Security Strategies
8. Conclusion and Future Work
References
- Lau, Y.Y.; Wu, A.Y.; Yan, M.W. A way forward for electric vehicle in Greater Bay Area: Challenges and opportunities for the 21st century. Vehicles 2022, 4, 420–432. [Google Scholar] [CrossRef]
- Gelmanova, Z.; Zhabalova, G.; Sivyakova, G.; Lelikova, O.; Onishchenko, O.; Smailova, A.; Kamarova, S. Electric cars. Advantages and disadvantages. In Proceedings of the Journal of Physics: Conference Series. IOP Publishing, 2018, Vol. 1015, p. 052029.
- Weiss, M.; Cloos, K.C.; Helmers, E. Energy efficiency trade-offs in small to large electric vehicles. Environmental Sciences Europe 2020, 32, 1–17. [Google Scholar]
- Gray, S. 125 million electric vehicles will be on the road by 2030, Agency says, 2018.
- Schloter, L. Empirical analysis of the depreciation of electric vehicles compared to gasoline vehicles. Transport Policy 2022, 126, 268–279. [Google Scholar] [CrossRef]
- House, W. President Biden announces steps to drive American leadership forward on clean cars and trucks, 2021.
- IEA. Global sales and sales market share of electric cars, 2010-2021. https://www.statista.com/statistics/665774/global-sales-of-plug-in-light-vehicles/, 2023. Accessed: 2023-11-15.
- Sarieddine, K.; Sayed, M.; Torabi, S.; Atallah, R.; Assi, C. Investigating the Security of EV Charging Mobile Applications As an Attack Surface. arXiv preprint arXiv:2211.10603 2022. [Google Scholar] [CrossRef]
- Gong, J.; Tang, Z.; Yu, X.; Yu, L.; Cheng, H. Feasibility analysis of regional electric vehicle market—A case study of Panzhihua city. In Proceedings of the Computational Social Science: Proceedings of the 2nd International Conference on New Computational Social Science (ICNCSS 2021), October 15-17, 2021, Suzhou, Jiangsu, China. Taylor & Francis, 2022, p. 81.
- Kotia, N. Ev charging app: Types, features, process, varieties, Journal of Konstant Infosolutions, 2021.
- Topman, N.; Adnane, A. Mobile applications for connected cars: Security analysis and risk assessment. In Proceedings of the NOMS 2022-2022 IEEE/IFIP Network Operations and Management Symposium. IEEE; 2022; pp. 1–6. [Google Scholar]
- Yang, K.H. Selling consumer data for profit: Optimal market-segmentation design and its consequences. American Economic Review 2022, 112, 1364–93. [Google Scholar] [CrossRef]
- Saleem, B.; Ahmed, M.; Zahra, M.; Hassan, F.; Iqbal, M.A.; Muhammad, Z. A survey of cybersecurity laws, regulations, and policies in technologically advanced nations: A case study of Pakistan to bridge the gap. International Cybersecurity Law Review 2024, 5, 533–561. [Google Scholar] [CrossRef]
- Martin, R.A.; Barnum, S. Common weakness enumeration (cwe) status update. ACM SIGAda Ada Letters 2008, 28, 88–91. [Google Scholar] [CrossRef]
- Bach-Nutman, M. Understanding the top 10 owasp vulnerabilities. arXiv preprint arXiv:2012.09960 2020. [Google Scholar]
- Shirvani, S.; Baseri, Y.; Ghorbani, A. Evaluation framework for electric vehicle security risk assessment. IEEE Transactions on Intelligent Transportation Systems 2023. [Google Scholar] [CrossRef]
- Paverd, A.; Martin, A.; Brown, I. Modelling and automatically analysing privacy properties for honest-but-curious adversaries. Tech. Rep 2014. [Google Scholar]
- Vailoces, G.; Keith, A.; Almehmadi, A.; El-Khatib, K. Securing the Electric Vehicle Charging Infrastructure: An In-Depth Analysis of Vulnerabilities and Countermeasures. In Proceedings of the Proceedings of the Int’l ACM Symposium on Design and Analysis of Intelligent Vehicular Networks and Applications, 2023, pp. 31–38.
- Hanelt, A. ; Nastjuk. Disruption on the way? The role of mobile applications for electric vehicle diffusion, Wirtschaftsinformatik Proceedings 2015.
- Stillwater, T.; Woodjack, J.; Nicholas, M. Mobile app support for electric vehicle drivers: a review of today’s marketplace and future directions. In Proceedings of the International Conference on Human-Computer Interaction. Springer; 2013; pp. 640–646. [Google Scholar]
- Chatzoglou, E.; Kambourakis, G.; Kouliaridis, V. A Multi-Tier Security Analysis of Official Car Management Apps for Android. Future Internet 2021, 13, 58. [Google Scholar] [CrossRef]
- Mandal, A.K.; Cortesi, A.; Ferrara, P.; Panarotto, F.; Spoto, F. Vulnerability analysis of android auto infotainment apps. In Proceedings of the Proceedings of the 15th ACM International Conference on Computing Frontiers, 2018, pp. 183–190.
- Panarotto, F.; Cortesi, A.; Ferrara, P.; Mandal, A.K.; Spoto, F. Static analysis of android apps interaction with automotive can. In Proceedings of the Smart Computing and Communication: Third International Conference, SmartCom 2018, Tokyo, Japan, December 10–12, 2018, Proceedings 3. Springer, 2018, pp. 114–123.
- Muhammad, Z.; Anwar, Z.; Saleem, B. A cybersecurity risk assessment of electric vehicle mobile applications: Findings and recommendations. In Proceedings of the 2023 3rd International Conference on Artificial Intelligence (ICAI). IEEE; 2023; pp. 45–51. [Google Scholar]
- Sarieddine, K.; Sayed, M.A.; Torabi, S.; Atallah, R.; Assi, C. Investigating the security of ev charging mobile applications as an attack surface. ACM Transactions on Cyber-Physical Systems 2023, 7, 1–28. [Google Scholar] [CrossRef]
- Muhammad, Z.; Anwar, Z.; Saleem, B.; Shahid, J. Emerging cybersecurity and privacy threats to electric vehicles and their impact on human and environmental sustainability. Energies 2023, 16, 1113. [Google Scholar] [CrossRef]
- Zhang, L.; Ma, D. Evaluating Network Security Configuration (NSC) Practices in Vehicle-Related Android Applications. Technical report, SAE Technical Paper, 2024.
- Alaba, S.Y.; Gurbuz, A.C.; Ball, J.E. Emerging Trends in Autonomous Vehicle Perception: Multimodal Fusion for 3D Object Detection. World Electric Vehicle Journal 2024, 15, 20. [Google Scholar] [CrossRef]
- Shahidinejad, A.; Abawajy, J. Blockchain-Based Self-Certified Key Exchange Protocol for Hybrid Electric Vehicles. IEEE Transactions on Consumer Electronics 2023. [Google Scholar] [CrossRef]
- playstore. Tesla Available at. https://play.google.com/store/search?q=tesla&c=apps&hl=en&gl=US, 2023.
- playstore. Mercedes me connect (USA) Available at. https://play.google.com/store/apps/details?id=com.mbusa.mmusa.android&hl=en&gl=US, 2023.
- playstore. BMW Available at. https://play.google.com/store/search?q=MY%20BMW&c=apps&hl=en&gl=US, 2023.
- playstore. NissanConnect® Services Available at. https://play.google.com/store/search?q=NissanConnect%C2%AE%20Services&c=apps&hl=en&gl=US, 2023.
- playstore. Volkswagen Available at. https://play.google.com/store/search?q=Volkswagen&c=apps&hl=en&gl=US, 2023.
- playstore. Available at. https://www.ferrari.com/en-EN/auto/myferrari, 2023.
- playstore. Available at. https://play.google.com/store/apps/details?id=com.ford.fordpass&hl=en&gl=US, 2023.
- playstore. Available at. https://play.google.com/store/apps/details?id=com.mitsubishi_motors.remote_ps&hl=en_GB, 2023.
- playstore. Available at. https://play.google.com/store/apps/details?id=com.bosch.myspin.launcherapp_landrover&hl=en&gl=US, 2023.
- playstore. Available at. https://play.google.com/store/apps/details?id=com.bosch.myspin.launcherapp_jaguar&hl=en&gl=US, 2023.
- playstore. Available at. https://www.evconnect.com/, 2023.
- playstore. EVGO Available at. https://play.google.com/store/search?q=EVgo&c=apps&hl=en&gl=US, 2023.
- playstore. PlugShare - EV & Tesla Map Available at. https://play.google.com/store/search?q=PLUGSHARE&c=apps&hl=en&gl=US, 2023.
- playstore. ChargeHub EV & Tesla Charging Available at. https://play.google.com/store/search?q=ChargeHub&c=apps&hl=en&gl=US, 2023.
- playstore. Available at. https://play.google.com/store/apps/details?id=com.getoptiwatt.optiwatt&hl=en&gl=US, 2023.
- playstore. Available at. https://abetterrouteplanner.com/, 2023.
- playstore. Available at. https://play.google.com/store/apps/details?id=com.caura.android&hl=en_IN&gl=GB, 2023.
- playstore. Available at. https://www.bpplus.com.au/, 2023.
- playstore. Available at. https://electroverse.octopus.energy/, 2023.
- playstore. Available at. https://www.ev.energy/, 2023.
- Rawal, H.; Parekh, C. Android Internal Analysis of APK by Droid_Safe & APK Tool. International Journal of Advanced Research in Computer Science 2017, 8. [Google Scholar]
- Grushinskiy, M. XmlStarlet Command Line XML Toolkit User’s Guide.
- Almomani, I.; Khayer, A. Android applications scanning: The guide. In Proceedings of the 2019 International Conference on Computer and Information Sciences (ICCIS). IEEE; 2019; pp. 1–5. [Google Scholar]
- Amarante, J.; Barros, J.P. Exploring USB connection vulnerabilities on Android devices breaches using the Android debug bridge. In Proceedings of the 14th International Joint Conference on e-Business and Telecommunications, ICETE 2017. SciTePress, 2017, pp. 572–577.
- Kusreynada, S.U.; Barkah, A.S. Android Apps Vulnerability Detection with Static and Dynamic Analysis Approach using MOBSF. Journal of Computer Science and Engineering (JCSE) 2024, 5, 46–63. [Google Scholar] [CrossRef]
- Balikcioglu, P.G.; Sirlanci, M.; A. Kucuk, O.; Ulukapi, B.; Turkmen, R.K.; Acarturk, C. Malicious code detection in android: the role of sequence characteristics and disassembling methods. International Journal of Information Security 2023, 22, 107–118.
- Nath, A. Packet Analysis with Wireshark; Packt Publishing Ltd, 2015.
- OLIVEIRA, L.C.C.A.d. Comparative study of techniques for detecting emulators on Android devices. B.S. thesis, 2022.
- LaMalva, G.; Schmeelk, S. MobSF: Mobile health care Android applications through the lens of open source static analysis. In Proceedings of the 2020 IEEE MIT Undergraduate Research Technology Conference (URTC). IEEE; 2020; pp. 1–4. [Google Scholar]
- Fair feature subset selection using multiobjective genetic algorithm. In Proceedings of the Proceedings of the Genetic and Evolutionary Computation Conference Companion, 2022, pp. 360–363.
- Anwar, C.; Hady, S.; Rahayu, N.; Kraugusteeliana, K.; et al. The Application of Mobile Security Framework (MOBSF) and Mobile Application Security Testing Guide to Ensure the Security in Mobile Commerce Applications. Jurnal Sistim Informasi dan Teknologi 2023, pp. 97–102.
- Khunt, A.R.; Prabu, P. An Empirical Analysis of Android Permission System Based on User Activities. J. Comput. Sci. 2018, 14, 324–333. [Google Scholar] [CrossRef]
- Li, J. Vulnerabilities mapping based on OWASP-SANS: a survey for static application security testing (SAST). arXiv preprint arXiv:2004.03216, 2020. [Google Scholar]
- Alanda, A.; Satria, D.; Mooduto, H.; Kurniawan, B. Mobile application security penetration testing based on OWASP. In Proceedings of the IOP Conference Series: Materials Science and Engineering. IOP Publishing, 2020, Vol. 846, p. 012036.
- Meng, H.; Thing, V.L.; Cheng, Y.; Dai, Z.; Zhang, L. A survey of Android exploits in the wild. Computers & Security 2018, 76, 71–91. [Google Scholar]
- Park, C.; Moon, S.Y.; Kim, R.Y.C. Detecting Common Weakness Enumeration (CWE) Based on the Transfer Learning of CodeBERT Model. KIPS Transactions on Software and Data Engineering 2023, 12, 431–436. [Google Scholar]
- Williams, I. Evaluating a method to develop and rank abuse cases based on threat modeling, attack patterns and common weakness enumeration. PhD thesis, North Carolina Agricultural and Technical State University, 2015.
- Fischer, T. Testing cryptographically secure pseudo random number generators with artificial neural networks. In Proceedings of the 2018 17th IEEE International Conference On Trust, Security And Privacy In Computing And Communications/12th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE). IEEE, 2018, pp. 1214–1223.
- Cheng, F.; Cheng, F. The platform logging api and service. Exploring Java 9: Build Modularized Applications in Java 2018, pp. 81–86.
- Samarin, S.D.; Amini, M. Preventing SQL injection attacks by automatic parameterizing of raw queries using lexical and semantic analysis methods. Scientia Iranica. Transaction D, Computer Science & Engineering, Electrical 2019, 26, 3469–3484. [Google Scholar]
- Barker, E.B.; Barker, W.C.; Lee, A. SP 800-21 Second edition. Guideline for Implementing Cryptography in the Federal Government; National Institute of Standards & Technology, 2005.
- Tran, A.D.; Nguyen, M.Q.; Phan, G.H.; Tran, M.T. Security Issues in Android Application Development and Plug-in for Android Studio to Support Secure Programming. In Proceedings of the Future Data and Security Engineering. Big Data, Security and Privacy, Smart City and Industry 4.0 Applications: 8th International Conference, FDSE 2021, Virtual Event, November 24–26, 2021, Proceedings 8. Springer, 2021, pp. 105–122.
- Garcia, J.; Hammad, M.; Malek, S. Lightweight, obfuscation-resilient detection and family identification of android malware. ACM Transactions on Software Engineering and Methodology (TOSEM) 2018, 26, 1–29. [Google Scholar] [CrossRef]
- Nazir, M. Software Quality Assurance and Android Application Development: A Comparison among Traditional and Agile Methodology. Lahore Garrison University Research Journal of Computer Science and Information Technology 2020, 4, 1–29. [Google Scholar] [CrossRef]
- Yin, Z.; Li, Z.; Cao, Y. A web application runtime application self-protection scheme against script injection attacks. In Proceedings of the Cloud Computing and Security: 4th International Conference, ICCCS 2018, Haikou, China, June 8-10, 2018, Revised Selected Papers, Part II 4. Springer, 2018, pp. 566–577.
- Dong, S.; Li, M.; Diao, W.; Liu, X.; Liu, J.; Li, Z.; Xu, F.; Chen, K.; Wang, X.; Zhang, K. Understanding android obfuscation techniques: A large-scale investigation in the wild. In Proceedings of the Security and Privacy in Communication Networks: 14th International Conference, SecureComm 2018, Singapore, Singapore, August 8-10, 2018, Proceedings, Part I. Springer, 2018, pp. 172–192.
- Saad, M.; Taseer, M. The Study of the Anti-Debugging Techniques and their Mitigations. International Journal for Electronic Crime Investigation 2022, 6, 33–44. [Google Scholar] [CrossRef]
| Group | App Name | F 1 | F 2 | F 3 | F 4 | F 5 | F 6 | F 7 | F 8 | F 9 | F 10 | F 11 | F 12 | Total |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Group 1 | TESLA [30] | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | 5 |
| Mercedes [31] | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | 3 | |
| BMW [32] | ✓ | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | 3 | |
| Nissan [33] | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | 3 | |
| Volkswagen [34] | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | 3 | |
| FERRARI [35] | ✓ | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | 7 | |
| FordPass [36] | ✓ | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | 6 | |
| MITSUBISHI [37] | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | 5 | |
| Land Rover [38] | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | 5 | |
| Jaguar [39] | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | 5 | |
| Group 2 | EV Connect [40] | ✓ | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | 4 |
| EVgo [41] | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | 3 | |
| PlugShare [42] | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ | ✓ | ✓ | ✗ | ✗ | 4 | |
| ChargeHub [43] | ✓ | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✓ | ✗ | ✗ | 3 | |
| Optiwatt [44] | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | 5 | |
| Routeplanner [45] | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | 5 | |
| Caura [46] | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | 5 | |
| Bp Plus [47] | ✓ | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | 6 | |
| Electroverse [48] | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | 5 | |
| EV-Energy [49] | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✓ | 4 |
| Group | Application Name | Version | P 1 | P 2 | P 3 | P 4 | P 5 | P 6 | P 7 | P 8 | P 9 | P 10 | Total |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Group 1 | TESLA [30] | 4.15.1 | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ | ✓ | ✓ | 8 |
| Mercedes [31] | 3.30.1 | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | 8 | |
| BMW [32] | 2.12.3 | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✓ | ✓ | 7 | |
| Nissan [33] | 6.0.1 | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ | ✗ | 6 | |
| Volkswagen [34] | 5.5.0 | ✓ | ✓ | ✗ | ✗ | ✓ | ✓ | ✗ | ✗ | ✓ | ✗ | 5 | |
| FERRARI [35] | 3.0.5 | ✓ | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | 7 | |
| FordPass [36] | 4.25.0 | ✓ | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ | ✓ | ✓ | ✓ | 6 | |
| MITSUBISHI [37] | 1.0.1 | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ | ✗ | 2 | |
| Land Rover [38] | 1.90.0 | ✓ | ✗ | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | 6 | |
| Jaguar [39] | 1.90.0 | ✓ | ✗ | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | 6 | |
| Group 2 | EV Connect [40] | 3.12.3 | ✓ | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | 3 |
| EVgo [41] | 7.12.0 | ✓ | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✓ | ✓ | 5 | |
| PlugShare [42] | 4.0.0 | ✓ | ✓ | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✓ | 6 | |
| ChargeHub [43] | 12.11.0 | ✓ | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✓ | ✓ | 5 | |
| Optiwatt [44] | 1.3.9 | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✓ | 3 | |
| Routeplanner [45] | 4.4.0 | ✓ | ✓ | ✗ | ✓ | ✓ | ✗ | ✗ | ✓ | ✓ | ✓ | 7 | |
| Caura [46] | 2.2.7 | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✓ | ✗ | 3 | |
| Bp Plus [47] | 2.5.1 | ✓ | ✗ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✓ | ✓ | 4 | |
| Electroverse [48] | 56.0 | ✓ | ✗ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✓ | 3 | |
| EV-Energy [49] | 2.12 | ✓ | ✗ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✓ | ✓ | 4 |
| Vul. | Risk | A 1 | A 2 | A 3 | A 4 | A 5 | A 6 | A 7 | A 8 | A 9 | A 10 |
|---|---|---|---|---|---|---|---|---|---|---|---|
| V 1 | HIGH | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ |
| MEDIUM | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | |
| WARNING | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | |
| V 2 | HIGH | ✗ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ |
| MEDIUM | ✗ | ✓ | ✗ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | |
| WARNING | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | |
| V 3 | HIGH | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ |
| MEDIUM | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | |
| WARNING | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | |
| V 4 | HIGH | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ |
| MEDIUM | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | |
| WARNING | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | |
| V 5 | HIGH | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ |
| MEDIUM | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| WARNING | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ | ✓ | ✗ | |
| V 6 | HIGH | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ |
| MEDIUM | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✓ | ✗ | |
| WARNING | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | |
| V 7 | HIGH | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ |
| MEDIUM | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | |
| WARNING | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✓ | ✗ | |
| V 8 | HIGH | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ |
| MEDIUM | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | |
| WARNING | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | |
| V 9 | HIGH | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ |
| MEDIUM | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | |
| WARNING | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✓ | ✗ | |
| V 10 | HIGH | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ |
| MEDIUM | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | |
| WARNING | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | |
| Total | Total | 12 | 14 | 12 | 11 | 10 | 5 | 5 | 3 | 9 | 5 |
| Vul. | Risk | A 11 | A 12 | A 13 | A 14 | A 15 | A 16 | A 17 | A 18 | A 19 | A 20 |
|---|---|---|---|---|---|---|---|---|---|---|---|
| V 1 | HIGH | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ |
| MEDIUM | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | × | |
| WARNING | ✗ | ✓ | ✗ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | × | |
| V 2 | HIGH | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ | ✗ | × |
| MEDIUM | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | |
| WARNING | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| V 3 | HIGH | ✓ | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ |
| MEDIUM | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | |
| WARNING | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | |
| V 4 | HIGH | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ |
| MEDIUM | ✓ | ✗ | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | |
| WARNING | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | |
| V 5 | HIGH | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ |
| MEDIUM | ✓ | ✗ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | |
| WARNING | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | |
| V 6 | HIGH | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ |
| MEDIUM | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ||
| WARNING | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | |
| V 7 | HIGH | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ |
| MEDIUM | ✓ | ✗ | ✗ | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | ✓ | |
| WARNING | ✓ | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ | |
| V 8 | HIGH | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ |
| MEDIUM | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | |
| WARNING | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | |
| V 9 | HIGH | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ |
| MEDIUM | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | |
| WARNING | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✗ | ✗ | |
| V 10 | HIGH | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ |
| MEDIUM | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | |
| WARNING | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | |
| Total | Total | 9 | 7 | 4 | 7 | 10 | 6 | 6 | 8 | 7 | 4 |
| Application | CWE-250 | CWE-330 | CWE-276 | CWE-532 | CWE-312 | CWE-89 | CWE-327 | CWE-295 | CWE-749 | CWE-919 | Total |
|---|---|---|---|---|---|---|---|---|---|---|---|
| TESLA [30] | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | 8 |
| Mercedes [31] | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✗ | 6 |
| BMW [32] | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ | 7 |
| Nissan [33] | ✗ | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | 4 |
| Volkswagen [34] | ✓ | ✗ | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ | 5 |
| FERRARI [35] | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | 5 |
| FordPass [36] | ✗ | ✓ | ✗ | ✗ | ✓ | ✓ | ✗ | ✗ | ✓ | ✓ | 5 |
| Mitsubishi [37] | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | 2 |
| Land Rover [38] | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ | 5 |
| Jaguar [39] | ✗ | ✗ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | 2 |
| EV Connect [40] | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | 5 |
| EVgo [41] | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | 8 |
| PlugShare [42] | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | 8 |
| ChargeHub [43] | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | 7 |
| Optiwatt [44] | ✗ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | 1 |
| Routeplanner [45] | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | 6 | |
| Caura [46] | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ | 4 |
| BP pulse [47] | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | 6 |
| Electroverse [48] | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | 5 |
| Ev Energy [49] | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | 5 |
| Total | 3 | 15 | 16 | 8 | 17 | 13 | 15 | 4 | 5 | 7 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





