1. Introduction
The digital age has seen an unprecedented surge in the adoption of cloud computing across various sectors, driven by its promises of cost efficiency, scalability, and enhanced accessibility to computing resources [
1].
Organizations and individuals are increasingly entrusting their data and applications to third-party infrastructure, leading to a change in thinking in computing services [
1]. However, this reliance on external entities for data storage and processing introduces inherent security concerns, primarily due to the relinquishing of direct control over sensitive information [
2]. Within cloud computing, cryptography represents a fundamental approach to protecting data and maintaining user trust [
2].
Cryptography, the art and science of securing information, offers a suite of techniques that go beyond mere encryption [
2]. It encompasses mechanisms for ensuring not only the confidentiality of data through encryption but also its integrity, authenticity, and availability [
2]. Digital signatures, for instance, provide a means to verify the origin and integrity of data, ensuring that it has not been tampered with during transmission or storage [
11]. Similarly, cryptographic hash functions play a crucial role in confirming data integrity by generating unique fingerprints of data, allowing for the detection of any unauthorized modifications [
11]. Furthermore, secure communication protocols, such as Transport Layer Security (TLS) and its predecessor Secure Sockets Layer (SSL), utilize cryptographic techniques to establish encrypted connections between clients and servers, safeguarding data during transit over potentially insecure networks [
11].
In summary, this research document provides a contemporary analysis of cryptography within secure cloud computing. The study explores encryption methodologies, the role of key management systems, inherent security challenges, and cryptographic applications in this domain. Furthermore, it investigates emerging trends in cryptographic research and development pertinent to cloud security. The document is structured to first review existing literature, followed by a critical evaluation of the strengths and limitations of current cryptographic approaches. Real- world applications and use cases illustrate the practical implementation of cryptography in secure cloud computing. The document concludes with a synthesis of key findings and recommendations for future research, including an outline for a mini-implementation or proof of concept to demonstrate a relevant cryptographic principle.
2. Literature Review
The landscape of cryptography in cloud computing is rich and multifaceted, encompassing a wide array of techniques and considerations. Understanding the current state of research requires a thorough examination of encryption methods, key management practices, and the security challenges that necessitate their application.
2.1. Encryption Techniques in Cloud Computing
A cornerstone of cloud security, encryption transforms data into an unreadable format to protect its confidentiality.
Various encryption techniques are employed, each with its own strengths and weaknesses.
2.1.1. Symmetric Key Cryptography
This approach utilizes a single secret key for both the encryption and decryption processes, offering efficiency for encrypting large volumes of data [
2]. Prominent algorithms in this category include the Advanced Encryption Standard (AES), which is widely adopted for its robustness and security [
2]. Other historical algorithms like the Data Encryption Standard (DES) and its successor Triple DES (3DES) are less commonly used today due to their smaller key sizes, which render them vulnerable to modern computational attacks [
2]. While symmetric encryption offers speed and efficiency, a significant challenge lies in the secure distribution and management of the secret key among authorized parties, especially in the distributed nature of cloud environments [
9]. Research has also explored enhancing symmetric encryption algorithms for cloud environments, such as developing a parallel RC4 algorithm to reduce latency during data transmission [
4].
2.1.2. Asymmetric Key Cryptography
In contrast to symmetric encryption, asymmetric cryptography employs a pair of mathematically related keys: a public key for encryption and a private key for decryption [
2]. Well-known algorithms in this category include RSA, ECC, and Diffie-Hellman [
2]. RSA is widely used for secure communication and digital signatures, leveraging the difficulty of factoring large numbers [
2].
Elliptic Curve Cryptography (ECC) offers strong security with shorter key lengths compared to RSA, making it particularly suitable for cloud-based environments and resource-constrained devices like IoT sensors [
3]. The Diffie-Hellman algorithm is primarily used for secure key exchange, allowing two parties to establish a shared secret key over an insecure channel [
2]. While asymmetric encryption provides enhanced security by separating keys, it typically involves higher computational overhead than symmetric methods.
2.1.3. Homomorphic Encryption
Representing a significant advancement in cryptographic capabilities, homomorphic encryption allows computations to be performed directly on encrypted data without need for decryption [
1]. This transformative approach has profound implications for secure cloud processing, enabling tasks such as encrypted search on cloud storage, secure medical data analysis, and privacy- preserving machine learning [
1]. Fully Homomorphic Encryption (FHE) supports both addition and multiplication operations on encrypted data, allowing for the evaluation of any arbitrary computational function [
1]. Despite its immense potential, homomorphic encryption currently faces challenges related to computational overhead and practical implementation, although ongoing research is actively addressing these limitations [
1].
2.1.4. Post-Quantum Cryptography
With the anticipated advent of powerful quantum computers, current public-key cryptographic algorithms like RSA and ECC are expected to become vulnerable to efficient quantum algorithms such as Shor's algorithm [
17]. To address this looming threat, post-quantum cryptography (PQC) focuses on developing cryptographic algorithms that are secure against attacks from both classical and quantum computers [
9]. The National Institute of Standards and Technology (NIST) has been actively involved in standardizing PQC algorithms, with the first set of standards announced in 2022 [
20]. Various types of PQC are being explored, including lattice-based cryptography, hash-based cryptography, code-based cryptography, and isogeny-based cryptography [
18]. The transition to PQC is crucial for ensuring the long-term security of cloud computing environments.
2.1.5. Hybrid Cryptography
This technique combines the strengths of both symmetric and asymmetric encryption methods to achieve both security and efficiency in cloud data protection [
3].
Typically, asymmetric encryption is used to securely exchange a symmetric key, which is then used for the bulk encryption of data due to its speed and efficiency.
2.1.6. Lightweight Cryptography
Designed for resource-constrained devices such as IoT sensors and mobile devices, lightweight cryptography algorithms offer security with minimal computational overhead and energy consumption, making them suitable for securing the growing number of such devices connected through cloud services [
3].
2.1.7. DNA Cryptography
An emerging field, DNA cryptography explores the use of DNA codes for data hiding and secure data storage and transfer, offering a novel approach to enhancing cloud security [
3].
2.2. Key Management Systems in Cloud Computing
The security of any cryptographic system hinges on the effective management of cryptographic keys. In cloud computing, key management is particularly critical due to the distributed nature of the infrastructure and the shared responsibility model [
8]. Key management encompasses the entire lifecycle of cryptographic keys, including their generation, distribution, storage, rotation, revocation, and destruction [
23]. Challenges in cloud key management arise from factors such as shared infrastructure, distributed ownership of data, and the need to ensure both the security and availability of keys [
23].
The concept of Cloud Key Management Infrastructure (CKMI) has been introduced, which includes Cloud Key Management Clients (CKMC) and Cloud Key Management Servers (CKMS) to address the specific needs of cloud environments [
23]. The Cloud Key Management Interoperability Protocol (CK-MIP) has been proposed as a potential solution for unified key management across different cloud services [
23].
Various key management solutions and techniques have been explored, including protocols for secure key management during online and offline periods, federated key management, hierarchical identity-based cryptography, multicast key management, and key agreement protocols using Elliptic Curve Diffie-Hellman (ECDH) [
12].
Different key management models have emerged in the cloud, including cloud-native key management where the cloud provider manages the keys, Bring Your Own Key (BYOK) where users generate and import their own keys, Hold Your Own Key (HYOK) where the cloud provider uses the user's key management system, and Bring Your Own Encryption (BYOE) where users manage and use their own encryption keys [
14].
Major cloud providers like AWS and Google Cloud offer comprehensive Key Management Services (KMS) with various features such as centralized key management, hardware security module (HSM) integration, key rotation, and access control mechanisms [
25]. The standardization of key management practices and protocols is crucial for ensuring interoperability and consistent security across diverse cloud environments [
24].
2.3. Security Challenges in Cloud Computing
While cryptography provides essential tools for securing cloud computing, several inherent challenges need to be addressed. Data breaches remain a significant concern, often resulting from misconfigurations, human error, and insufficient security practices [
1]. Misconfigurations in cloud resources, such as leaving storage buckets publicly accessible, are a common vulnerability [
16].
Inadequate access controls and issues with Identity and Access Management (IAM) can lead to unauthorized access to sensitive data and cryptographic keys [
16]. Insider threats, originating from within the organization, pose another critical challenge [
16]. Insecure Application Programming Interfaces (APIs) can also be exploited to bypass access controls and gain unauthorized access to cloud services [
16].
The shared responsibility model, where security responsibilities are divided between the cloud provider and the customer, can lead to security gaps if the roles and responsibilities are not clearly understood and managed [
12]. The complexity of managing a large number of cryptographic keys (secrets sprawl) and the overall complexity of key management in diverse cloud environments present significant challenges [
12]. Lack of visibility and control over cloud resources can further exacerbate security challenges [
16]. Compliance with various data protection regulations such as GDPR and HIPAA necessitates the implementation of robust cryptographic measures and careful attention to data handling practices in the cloud [
12]. Finally, the performance overhead introduced by encryption processes can impact the efficiency of cloud applications, requiring a balance between security and performance [
1].
3. Critical Analysis
Cryptography plays a pivotal role in securing cloud computing, offering numerous strengths that address the inherent risks associated with this computing paradigm. However, it also faces certain limitations and requires continuous evolution to counter the ever-changing threat landscape.
3.1. Strengths of Cryptography in Secure Cloud Computing
One of the primary strengths of cryptography in the cloud is its ability to provide enhanced data confidentiality and privacy [
1]. By transforming sensitive data into an unreadable format, cryptography ensures that even if unauthorized individuals gain access to cloud storage or transmission channels, they cannot decipher the information without the correct decryption key [
10].
Beyond confidentiality, cryptography also plays a vital role in ensuring data integrity and authenticity [
2]. Techniques like digital signatures and hash functions enable the verification of data integrity and the authentication of data sources, providing assurance that data has not been tampered with and that it originates from a trusted source.
Cryptography is fundamental to facilitating secure communication and data transfer in the cloud [
2]. Secure protocols like TLS/SSL rely on cryptographic algorithms to establish encrypted channels for data transmission between users and cloud services, protecting sensitive information from eavesdropping and interception.
Furthermore, cryptography is often a key requirement for meeting various regulatory compliance standards, such as GDPR and HIPAA, which mandate the protection of personal and health-related data through encryption and other security measures [
12]. Ultimately, cryptography serves as a crucial line of defense, protecting against a wide range of security threats and attacks in the cloud environment [
1].
3.2. Limitations of Cryptography in Secure Cloud Computing
Despite its numerous benefits, cryptography in the cloud is not without limitations. One significant limitation is the computational overhead and performance impact associated with encryption and decryption processes [
1].
These operations can consume significant processing resources, potentially increasing latency and reducing throughput, especially for data-intensive applications and large datasets.
Another critical limitation lies in the complexity of key management [
8]. Managing the lifecycle of cryptographic keys securely in the cloud, from generation to destruction, is a challenging task.
Mismanagement of keys can lead to data breaches or even permanent data loss if keys are lost or compromised [
12].
Securing data during processing (data-in-use encryption) remains a significant challenge. While traditional encryption methods protect data at rest and in transit, data often needs to be decrypted for processing, creating a window of vulnerability [
15]. While homomorphic encryption offers a potential solution by allowing computation on encrypted data, it is still in its relatively early stages and faces limitations in terms of efficiency and the types of computations it can practically support.
Cryptographic systems can also be vulnerable to side- channel attacks, which exploit information leaked through the physical implementation of cryptographic algorithms, and advanced persistent threats that may compromise the underlying infrastructure [
16]. Furthermore, if encryption is not implemented correctly, it can potentially impact data accessibility and usability for authorized users [
13].
Finally, the evolving threat landscape, particularly the future threat posed by quantum computing, necessitates a continuous adaptation of cryptographic techniques to ensure long-term security [
9].
3.3. Future Directions of Cryptography in Secure Cloud Computing
The field of cryptography in secure cloud computing is constantly evolving to address the limitations of current techniques and to counter emerging threats. Several key future directions are shaping the research and development landscape. Advancements in homomorphic encryption are expected to improve its efficiency and practicality, making it more viable for real-world cloud applications such as secure data analysis and privacy-preserving machine learning [
1]. The development and adoption of post- quantum cryptographic algorithms are critical for ensuring long-term data security in the face of future quantum computers [
9]. Enhanced key management solutions with improved automation, security, and interoperability across diverse cloud service models are also a significant area of focus [
8].
The integration of cryptography with other security technologies, such as confidential computing (which aims to protect data in use within secure enclaves) and secure multi-party computation (which enables collaborative computation on sensitive data without revealing individual inputs), holds promise for enhancing cloud security [
6].
Further exploration of novel cryptographic techniques like DNA cryptography for data hiding and lightweight cryptography for resource-constrained devices will continue to be important [
3]. An increasing focus on cryptographic agility, the ability to easily switch between different cryptographic algorithms and protocols, will be crucial for adapting to evolving threats and standards [
14]. Finally, research into the use of machine learning and artificial intelligence in enhancing cryptographic security, for instance, in areas like anomaly detection in key usage and adaptive key management, represents a promising direction [
8]. The intersection of cryptography with AI and blockchain technologies may also yield innovative solutions for creating more resilient and intelligent cloud security systems [
3].
4. Applications and Use Cases
The principles and techniques of cryptography are applied in various real-world scenarios to secure cloud computing environments. Several notable examples illustrate the practical significance of cryptography in this domain.
4.1. End-to-End Encrypted Cloud Storage
A growing number of cloud storage providers are implementing end-to-end encryption to offer users enhanced data privacy and control. Dropbox, for instance, provides zero-knowledge end-to-end encryption for sensitive files and folders, ensuring that only the user and their intended recipients can access the content [
26].
Proton Drive, developed by the team behind ProtonMail, offers end-to-end encrypted cloud storage with the added benefit of Swiss privacy laws, providing a secure vault for user files [
27].
Apple's Advanced Data Protection for iCloud extends end- to-end encryption to a wider range of data categories, including iCloud Backup, Photos, Notes, and more, ensuring that this data can only be decrypted on the user's trusted devices [
28]. Snowflake, a cloud-based data warehousing company, offers client-side encryption for data in external stages, allowing users to encrypt their data before it is uploaded to the cloud [
29]. The increasing availability of such end-to-end encrypted cloud storage solutions reflects a growing user demand for stronger privacy guarantees and control over their data stored in the cloud [
26]. This approach ensures that data is encrypted on the user's device before being uploaded and is only decrypted on trusted devices, preventing even the cloud storage provider from accessing the content [
26].
4.2. Homomorphic Encryption for Secure Medical Data Analysis
Homomorphic encryption is finding significant applications in scenarios involving highly sensitive data, such as healthcare. Healthcare organizations can leverage the power of cloud computing to analyze sensitive patient data while preserving privacy by using homomorphic encryption [
1]. This allows for valuable medical research and analysis to be conducted on encrypted patient records without exposing the underlying personal health information, thereby facilitating compliance with stringent regulations like HIPAA [
1]. The ability to perform computations on encrypted medical data in the cloud opens up possibilities for collaborative research and improved healthcare outcomes while maintaining patient confidentiality.
4.3. Post-Quantum Cryptography Implementation
Recognizing the future threat posed by quantum computers to current cryptographic standards, major technology companies are proactively implementing post-quantum cryptography. Google has been an early adopter, using PQC for its internal communications since 2022 and experimenting with PQC for connections between Chrome Desktop and Google products [
22]. Cloudflare, a leading web infrastructure and security company, has also deployed post-quantum cryptography at scale to protect its users' data from future quantum attacks [
21]. Apple has integrated Kyber-based post-quantum cryptography into its iMessage service, taking steps to secure future communications against potential quantum decryption [
19]. These early implementations by industry leaders underscore a growing awareness of the quantum threat and a commitment to future-proofing data security in the cloud and beyond [
17]. Secure processing of sensitive data without decryption. Continued investigation and standardization of post- quantum cryptographic algorithms are essential to prepare for the eventual threat of quantum computers and to ensure the long-term security of cloud data. The development of more robust, automated, and user-friendly key management solutions that can seamlessly operate across diverse cloud service models is also paramount.
Furthermore, research should explore the synergistic integration of advanced cryptographic techniques with emerging technologies such as artificial intelligence and blockchain to create more resilient and intelligent cloud security systems [
3]. Addressing the security challenges posed by the shared responsibility model in cloud computing through better frameworks and user education is also an important area for future work. Finally, further investigation into the performance implications of different cryptographic techniques in various cloud deployment scenarios will help organizations make informed decisions about balancing security and efficiency.
5. Conclusion and Recommendations
Cryptography stands as a cornerstone in the security architecture of cloud computing, playing an indispensable role in ensuring data confidentiality, integrity, authenticity, and availability in an environment where users often relinquish direct control over their data. This research document has explored the diverse landscape of cryptographic techniques applicable to the cloud, including symmetric and asymmetric encryption, homomorphic encryption, post-quantum cryptography, and various specialized methods. It has also highlighted the critical importance and inherent challenges of key management in cloud environments, as well as the broader security challenges that cryptography aims to address.
The analysis reveals that while cryptography offers robust protection against numerous threats, it also faces limitations such as computational overhead, key management complexity, and the evolving threat landscape, including the future impact of quantum computing. The exploration of future directions indicates a vibrant and active research area focused on overcoming these limitations and developing new cryptographic solutions tailored to the unique demands of cloud computing. Advancements in homomorphic and post- quantum cryptography, along with enhanced key management practices and integration with other security technologies, promise to further strengthen the security posture of cloud environments.
Recommendations for Future Research
To continue advancing the field of cryptography in secure cloud computing, future research efforts should focus on several key areas. Optimizing the performance of homomorphic encryption schemes is crucial for their practical deployment in cloud applications, enabling
6. Mini-Implementation or Proof of Concept
To provide a practical understanding of cryptography in cloud computing, a mini-implementation or proof of concept can be outlined. This example will focus on demonstrating basic encryption and decryption using command-line tools.
6.1. Exploring Potential Software Tools and Methods
6.1.1. OpenSSL for Basic Encryption/Decryption
OpenSSL is a versatile and widely used command-line tool for performing various cryptographic operations [
3]. It can be used to demonstrate both symmetric encryption (e.g., using AES) and decryption using passwords [
30], as well as asymmetric encryption (e.g., using RSA) and decryption using key pairs [
3]. OpenSSL's availability across different platforms and its comprehensive set of cryptographic functionalities make it an ideal tool for a basic proof of concept, illustrating fundamental cryptographic operations [
30].
6.1.2. Simple Key Exchange Simulation
While a full implementation of a key exchange protocol might be complex for a mini-implementation, the fundamental principles of secure key agreement, such as in the Diffie-Hellman key exchange [
2], can be demonstrated using online tools or command-line utilities. These tools allow users to generate public and private keys and exchange public keys to derive a shared secret, showcasing the core concepts of secure key exchange that underpin many cryptographic systems in the cloud [
2].
6.2. Outline of Steps for a Mini-Implementation (Example: Basic Encrypted File Storage)
Environment Setup: Install Python (a widely used scripting language) and OpenSSL (a command-line tool for cryptography) on a local machine.
Key Generation: Use OpenSSL to generate a symmetric AES key. This key will be used to encrypt and decrypt the file.
Encryption Functionality: Develop a Python script that takes a file as input. The script will read the AES key and use the cryptography library in Python (which provides cryptographic primitives) to encrypt the content of the input file using the AES algorithm in a secure mode like GCM (Galois/Counter Mode). The encrypted content will be stored in a new file.
Decryption Functionality: Develop another Python script that takes the encrypted file and the correct AES key as input. This script will use the cryptography library to decrypt the content of the encrypted file back to its original form and store it in a new file.
-
Demonstration:
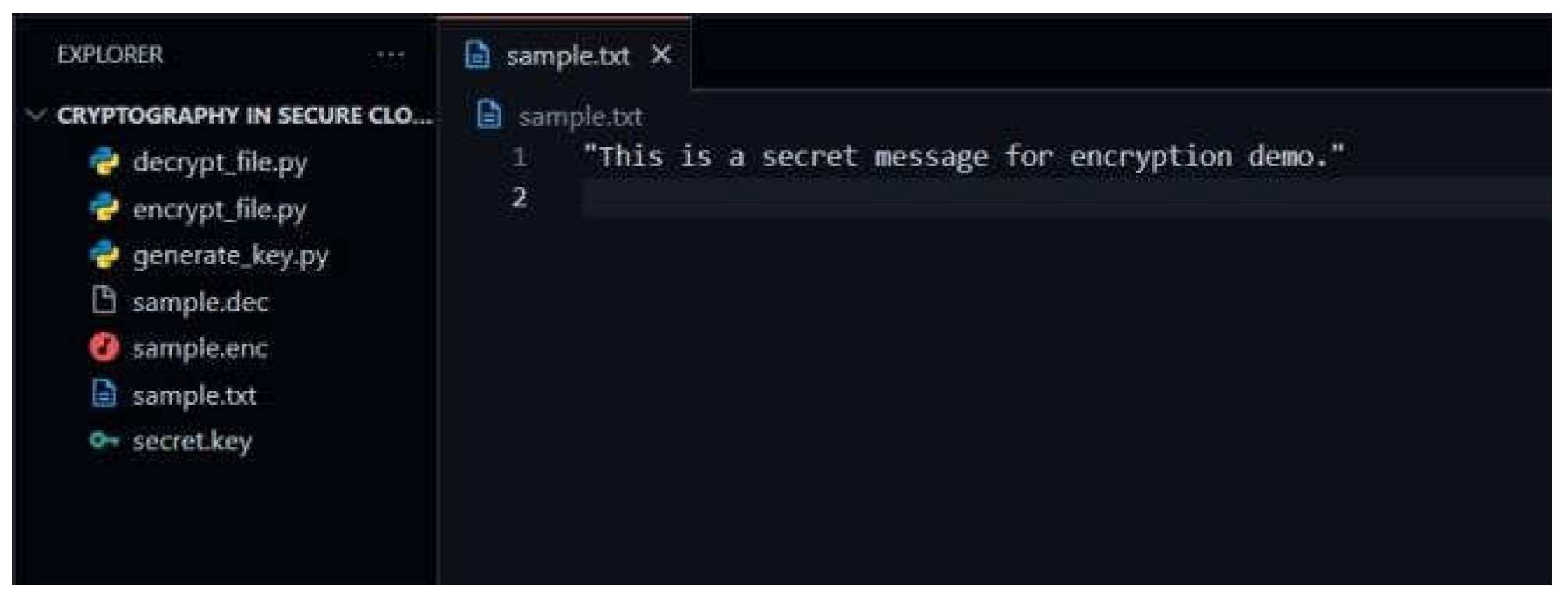
Create a sample text file with some content.
Run the encryption script, providing the sample file and the AES key. Observe the creation of the encrypted file.
Attempt to view the encrypted file's content, which should appear as gibberish.
Run the decryption script, providing the encrypted file and the same AES key. Observe the creation of the decrypted file.
Verify that the content of the decrypted file is identical to the original sample file.
6.3. Detailed Explanation of Steps and Potential Outputs
- 2.
-
Step 2: Key Generation:
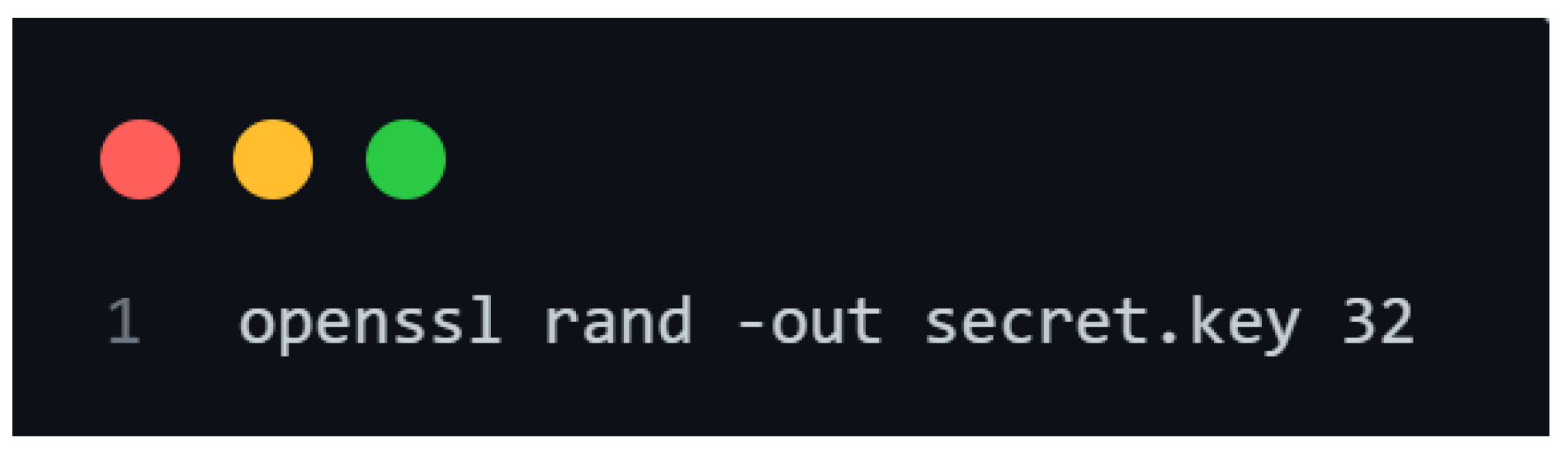
Figure 1.
OpenSSL Command to generate a 256-bit AES Key.
Figure 1.
OpenSSL Command to generate a 256-bit AES Key.
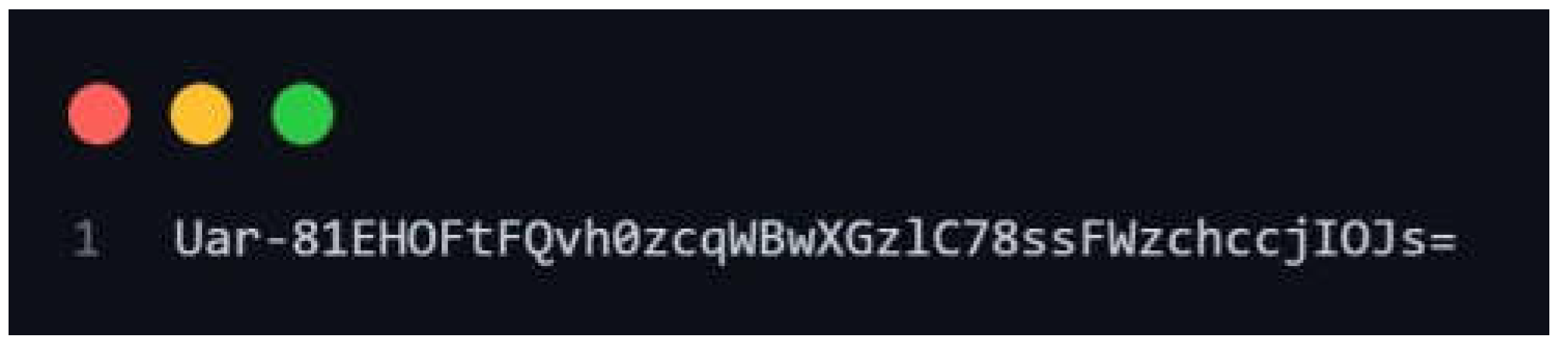
Figure 2.
Random-generated secret key.
Figure 2.
Random-generated secret key.
- 3.
-
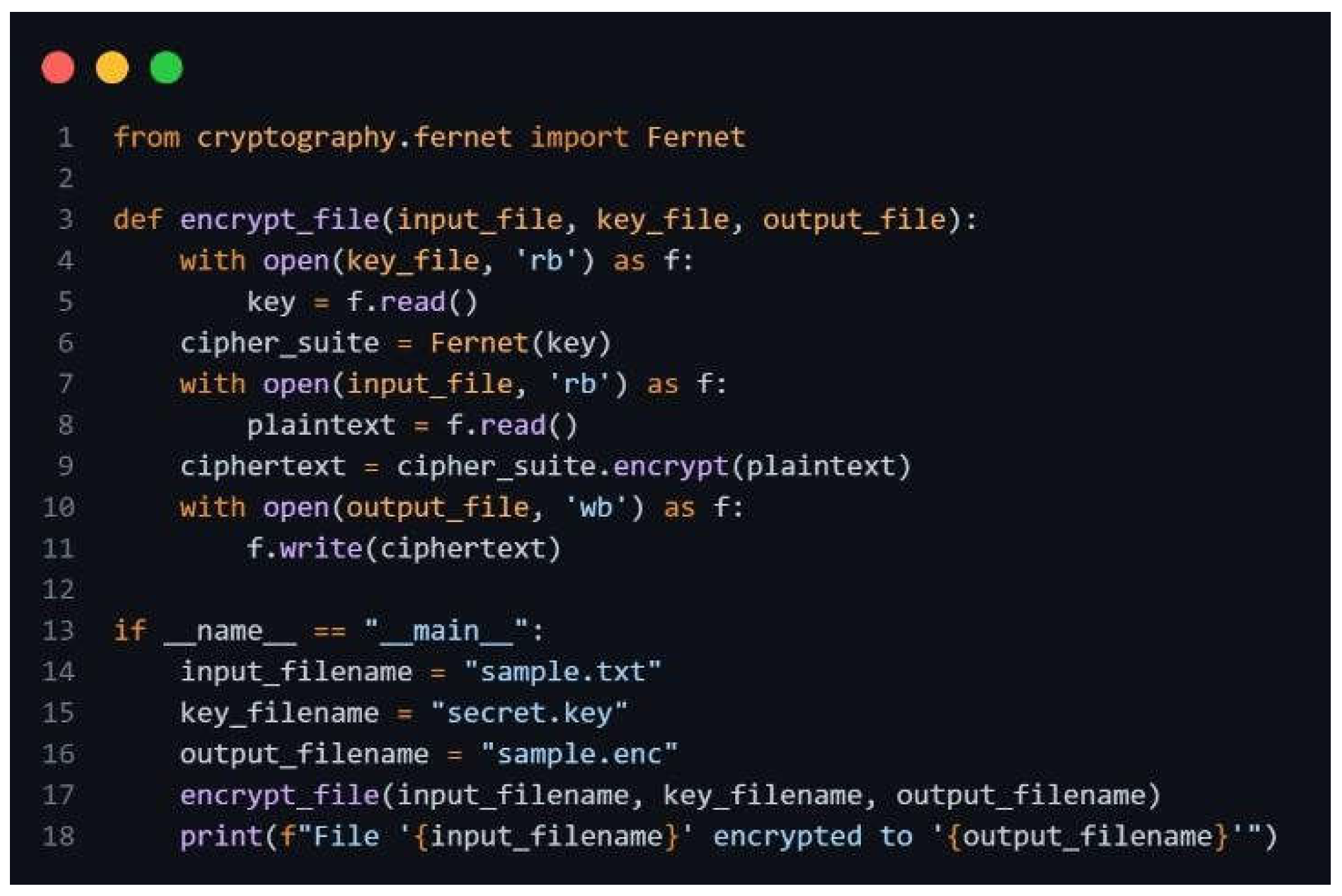
Step 3: Encryption Functionality:
Figure 3.
Encryption Script.
Figure 3.
Encryption Script.
Figure 4.
Sample.txt Script.
Figure 4.
Sample.txt Script.
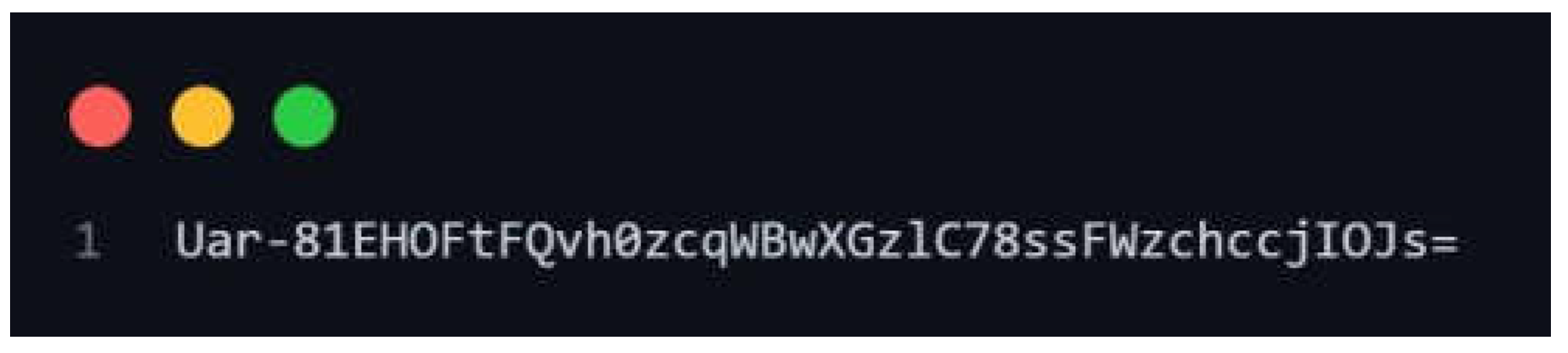
Figure 5.
Sample.enc file (encrypt.py script output).
Figure 5.
Sample.enc file (encrypt.py script output).
- 4.
-
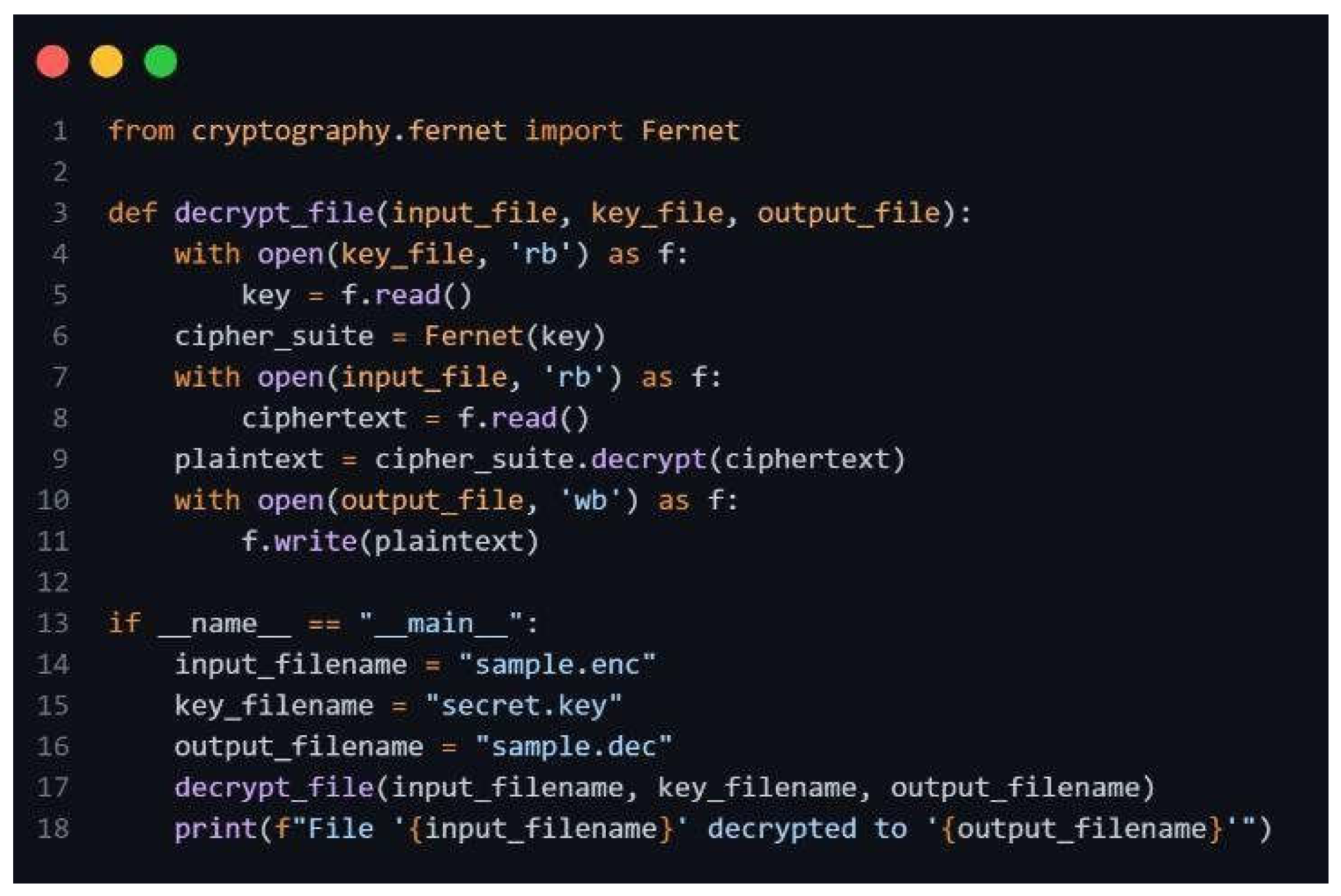
Step 4: Decryption Functionality:
Figure 6.
Decryption Script.
Figure 6.
Decryption Script.
Figure 7.
Sample. dec file (decrypt.py script output).
Figure 7.
Sample. dec file (decrypt.py script output).
- 5.
-
Step 5: Demonstration:
Original File (sample.txt): Contains the original plaintext (e.g., "This is a sample file for demonstrating encryption.").
Encryption Command Output: File 'sample.txt' encrypted to 'sample.enc'.
Encrypted File (sample.enc): Contains ciphertext that is unreadable.
Decryption Command Output: File 'sample.enc' decrypted to 'sample.dec'.
Decrypted File (sample.dec): Contains the same content as the original sample.txt, demonstrating successful encryption and decryption.
Figure 8.
Mini Implementation of all files.
Figure 8.
Mini Implementation of all files.
This mini-implementation provides a basic yet illustrative example of how symmetric encryption can be used to protect data, a fundamental concept in securing cloud computing environments. It highlights the importance of key management, as the same key is required for both encryption and decryption. This proof of concept can be further extended to explore more advanced cryptographic techniques and key management strategies relevant to cloud security.
7. Troubleshooting the Mini-Implementation
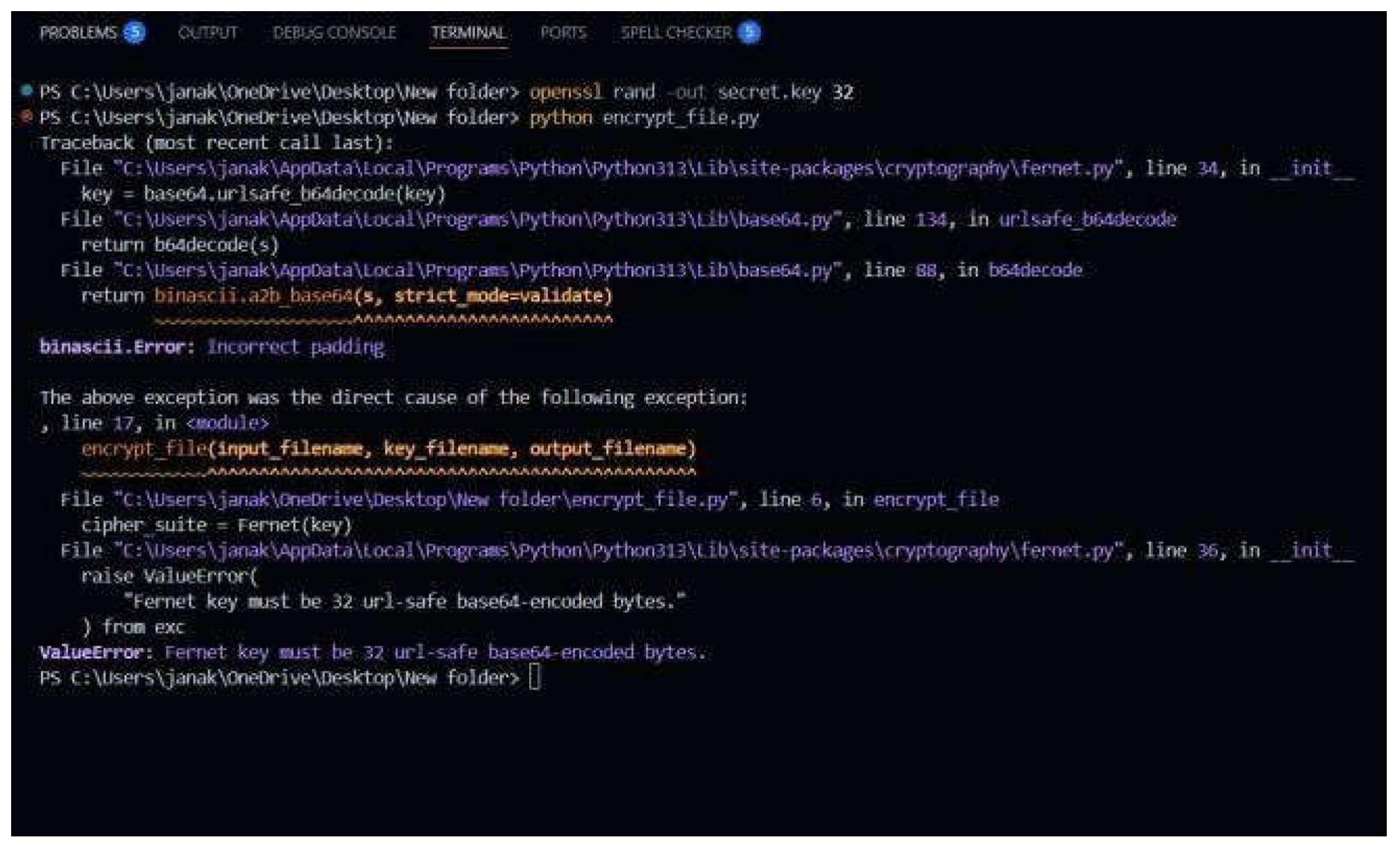
During the development and testing of the mini- implementation, a specific error was encountered related to the format of the encryption key. This section details the error, its cause, the solutions implemented, and the expected outputs after resolution.
7.1. Key Format Error Error:
ValueError: Fernet key must be 32 url- safe base64-encoded bytes
Error Message:
Figure 9.
Error encountered while executing the encrypt.py script due to missing or incorrect input parameters.
Figure 9.
Error encountered while executing the encrypt.py script due to missing or incorrect input parameters.
Cause:
7.2. Solution
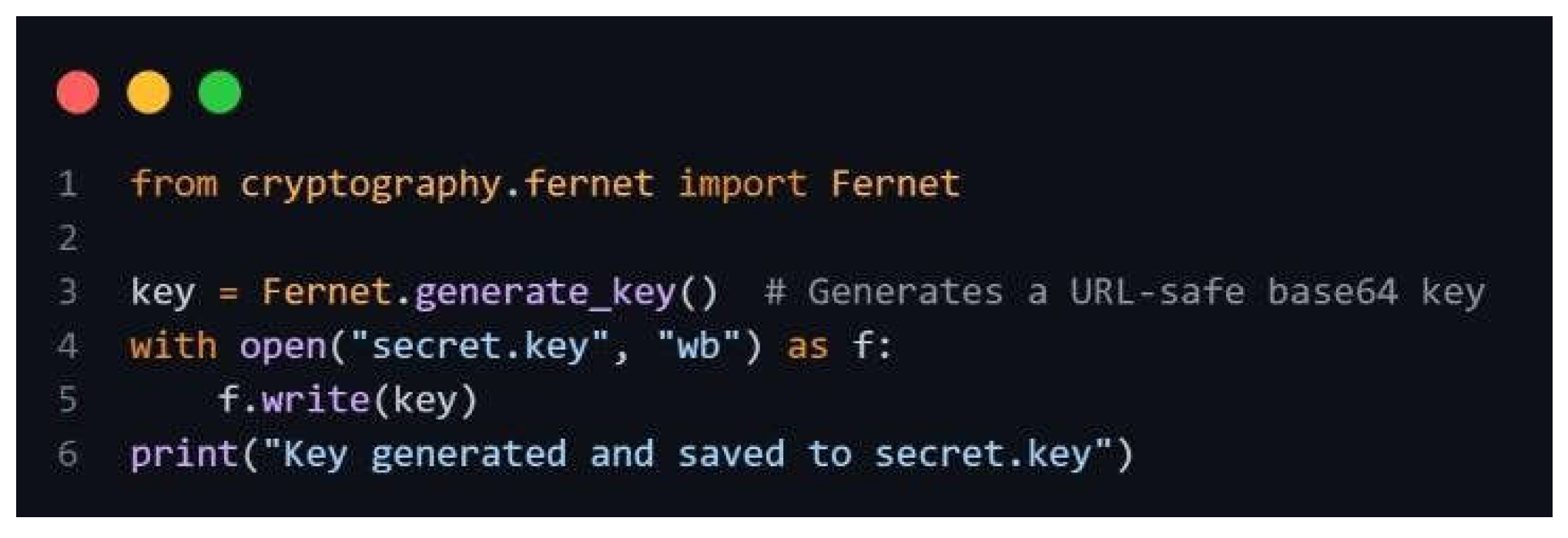
To address this error, two methods were employed to generate a Fernet-compatible key:
Method 1: Generate Fernet-Compatible Key
Figure 10.
: Generate fernet-compatible key script.
Figure 10.
: Generate fernet-compatible key script.
- 2.
Run the script:
python generate_key.py
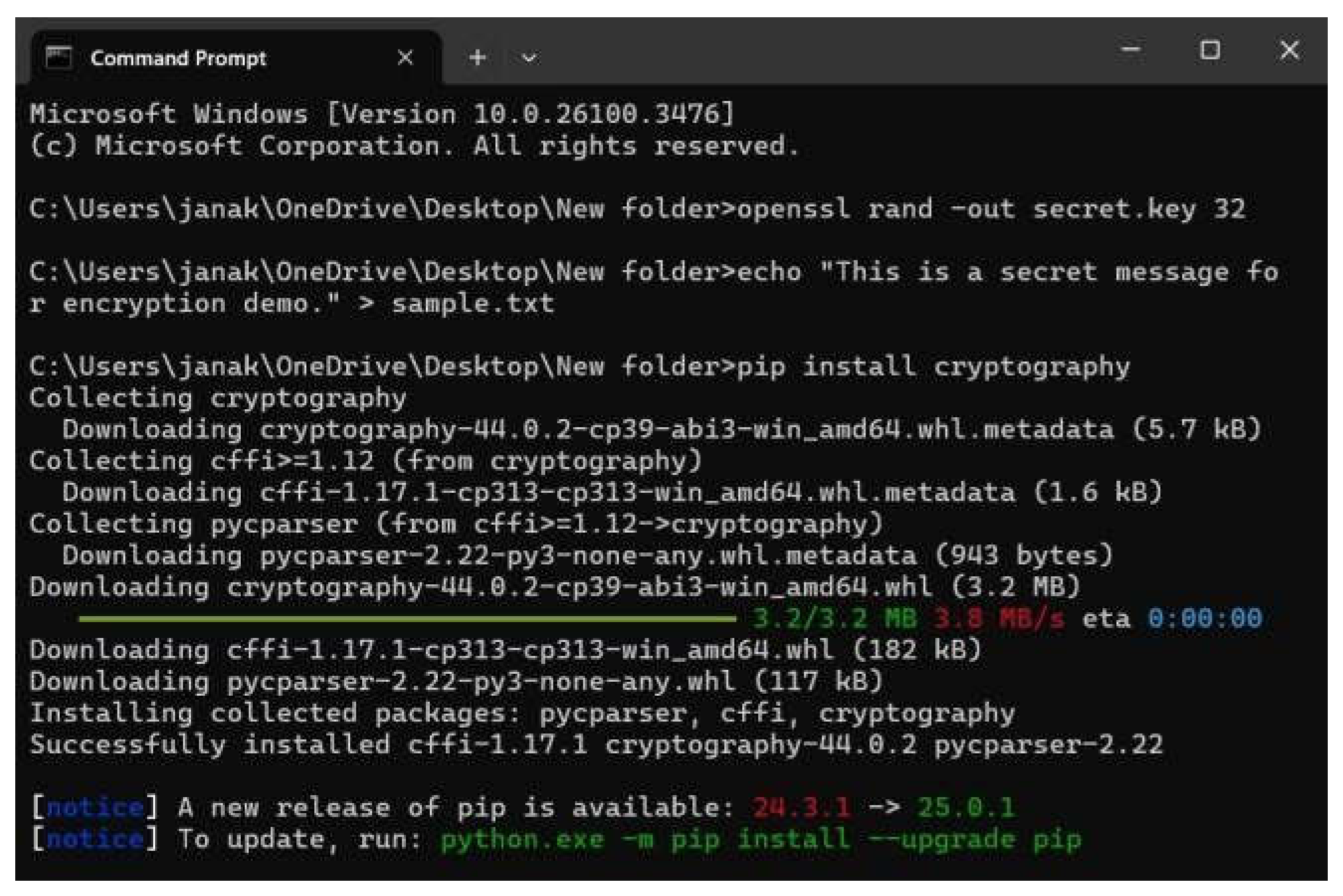
Method 2: OpenSSL with Base64 Encoding
openssl rand -base64 32 > secret.key
Figure 11.
OpenSSL secret key generated and installed cryptography.
Figure 11.
OpenSSL secret key generated and installed cryptography.
j64Cz0XJXH9YJZvV8u6Q1wT7Zq3K7yV3t8v4k6A 5B0=
7.3. Resolution Steps
The following steps were taken to resolve the error:
rm secret.key
- 2.
Regenerated the key using Method 1 or Method 2.
- 3.
Re-ran the workflow:
python encrypt_file.py python decrypt_file.py
7.4. Expected Outputs
The expected outputs after implementing the solution are shown in
Table 1.
Figure 13. All Outputs when running the scripts.
7.5. Why This Works
The error was resolved because Fernet requires keys to adhere to specific formatting requirements:
The solutions, Fernet.generate_key() and openssl rand - base64, ensure that the generated keys meet these requirements.
8. Project Implementation and GitHub Repository
To help you run the implementation on your local machine, I have created a sample project that includes all the necessary scripts and output files. The project includes:
encrypt.py: Python script for encryption.
decrypt.py: Python script for decryption.
sample.txt: A text file used to demonstrate encryption and decryption.
Other necessary output files.
9. Steps to Run the Project
Clone the repository to your local machine using the following command:
- 2.
Install Dependencies:
Navigate to the project directory and install the required dependencies:
pip install -r requirements.txt
- 3.
Generate the Encryption Key:
If you haven't already generated the Fernet key, you can use the provided script to generate it:
python generate_key.py
- 4.
Run the Encryption Script:
To encrypt the sample.txt file, run the following:
python encrypt.py
6. Run the Decryption Script:
After encryption, you can decrypt the file using the following command:
python decrypt.py
9.1. Additional Data and Support
If you need additional data or run into any issues while running the project, feel free to open an issue on the GitHub repository, or you can contact me directly through the contact details provided in the repository.
References
- "Homomorphic Encryption for Secure Cloud Computing," ResearchGate. [Online]. Available: https://www.researchgate.net/publication/382306535_Hom omorphic_Encryption_for_Secure_Cloud_Computing. [Accessed: Mar. 21, 2025].
- "A Review on Cryptography in Cloud Computing," ResearchGate. [Online]. Available: https://www.researchgate.net/publication/348460397_A_Review_on_Cryptography_in_Cloud_Computing. [Accessed: Mar. 21, 2025].
- "Comprehensive Review and Analysis of Cryptography Techniques in Cloud Computing," ResearchGate. [Online]. Available: https://www.researchgate.net/publication/379630406_Com prehensive_Review_and_Analysis_of_Cryptography_Tech niques_in_Cloud_Computing. [Accessed: Mar. 21, 2025].
- "A Survey on Data Encryption Techniques in Cloud Computing," ResearchGate. [Online]. Available: https://www.researchgate.net/publication/287914941_A_s urvey_on_data_encryption_tecniques_in_cloud_computin.
- g. [Accessed: Mar. 21, 2025].
- "Homomorphic Encryption: A Guide to Advances in the Processing of Encrypted Data," Thales. [Online]. Available: https://www.thalesgroup.com/en/worldwide/security/news/ homomorphic-encryption-guide-advances-processing- encrypted-data. [Accessed: Mar. 21, 2025].
- "IEEE HPEC Conference," IEEE HPEC. [Online]. Available: https://www.ieee- hpec.org/2014/CD/index_htm_files/FinalPapers/28.pdf. [Accessed: Mar. 21, 2025].
- "Cryptography in Cloud: An In-Depth Investigation into Encryption Mechanisms Safeguarding Cloud-Based Data," International Journal of Security Research and Applications. [Online]. Available: https://ijsra.net/content/cryptography-cloud-depth- investigation-encryption-mechanisms-safeguarding-cloud- based-data. [Accessed: Mar. 21, 2025].
- "A Dynamic Four-Step Data Security Model for Data in Cloud Computing," PMC. [Online]. Available: https://pmc.ncbi.nlm.nih.gov/articles/PMC8839104/. [Accessed: Mar. 21, 2025].
- "New Efficient Cryptographic Techniques for Cloud Computing Security," ResearchGate. [Online]. Available: https://www.researchgate.net/publication/381127672_New.
- _Efficient_Cryptographic_Techniques_For_Cloud_Compu ting_Security. [Accessed: Mar. 21, 2025].
- "Cryptography in the Cloud: Securing Cloud Data with Encryption," Digital Guardian. [Online]. Available: https://www.digitalguardian.com/resources/knowledge- base/cryptography-cloud. [Accessed: Mar. 21, 2025].
- "The Importance of Cryptography in Cloud Computing," Al-Esraa University College Journal for Engineering Sciences. [Online]. Available: https://jes.esraa.edu.iq/cgi/viewcontent.cgi?article=1054& context=journal. [Accessed: Mar. 21, 2025].
- "Encryption in Cloud Security: Challenges & Solutions," Darktrace. [Online].
- https://darktrace.com/cyber-ai-glossary/the-role-of- encryption-in-cloud-security. [Accessed: Mar. 21, 2025].
- "Why Cloud Cryptography is Important for Your Business," Shells Official Site. [Online]. Available: https://www.shells.com/blog/Why-Cloud-Cryptography-is- Important-for-Your-Business. [Accessed: Mar. 21, 2025].
- "Key Management Issues in Cloud and the Introduction of Post-Quantum Cryptography," NTT Data. [Online]. Available: https://www.nttdata.com/global/en/insights/focus/2024/key.
- -management-issues-in-cloud-and-the-introduction-of- post-quantum-cryptography. [Accessed: Mar. 21, 2025].
- "Fully Homomorphic Encryption," Cloud Security Alliance. [Online]. Available: https://cloudsecurityalliance.org/research/working- groups/fully-homomorphic-encryption. [Accessed: Mar. 21, 2025].
- "Top 12 Cloud Security Challenges," SentinelOne. [Online]. Available: https://www.sentinelone.com/cybersecurity-101/cloud- security/cloud-security-challenges/. [Accessed: Mar. 21, 2025].
- "The Quantum Computing Threat," Palo Alto Networks. [Online]. Available: https://docs.paloaltonetworks.com/network- security/quantum-security/administration/quantum- security-concepts/the-quantum-computing-threat. [Accessed: Mar. 21, 2025].
- "What is Post-Quantum Cryptography (PQC)?" Palo Alto Networks. [Online]. Available: https://www.paloaltonetworks.com/cyberpedia/what-is- post-quantum-cryptography-pqc. [Accessed: Mar. 21, 2025].
- "Quantum Threats and How to Protect Your Data," SecureWorld. [Online]. Available: https://www.secureworld.io/industry-news/quantum- threats-protect-your-data. [Accessed: Mar. 21, 2025].
- "NIST Announces First Four Quantum-Resistant Cryptographic Algorithms," NIST. [Online]. Available: https://www.nist.gov/news-events/news/2022/07/nist- announces-first-four-quantum-resistant-cryptographic- algorithms. [Accessed: Mar. 21, 2025].
- "What is Post-Quantum Cryptography (PQC)? – Cloudflare," Cloudflare. [Online]. Available: https://www.cloudflare.com/learning/ssl/quantum/what-is- post-quantum-cryptography/. [Accessed: Mar. 21, 2025].
- "Cloud CISO Perspectives: Why We Need to Get Ready for PQC," Google Cloud Blog. [Online]. Available: https://cloud.google.com/blog/products/identity- security/cloud-ciso-perspectives-why-we-need-to-get-ready-for-pqc. [Accessed: Mar. 21, 2025].
- "Key Management Infrastructure in Cloud Computing Environment: A Survey," ResearchGate. [Online]. Available: https://www.researchgate.net/publication/312025737_Key.
- _management_infrastructure_in_cloud_computing_enviro nment-a_survey. [Accessed: Mar. 21, 2025].
- "Cloud Key Management," Cloud Security Alliance. [Online]. Available: https://cloudsecurityalliance.org/research/topics/cloud-key- management. [Accessed: Mar. 21, 2025].
- "Google Cloud Security: Key Management Services," Encryption Consulting. [Online]. Available: https://www.encryptionconsulting.com/deep-dive-into- google-cloud-key-management-services/. [Accessed: Mar. 21, 2025].
- "End-to-End Encryption (E2EE) – Protect Your Data," Dropbox. [Online]. Available: https://www.dropbox.com/features/security/end-to-end- encryption. [Accessed: Mar. 21, 2025].
- "Proton Drive: Free Secure Cloud Storage," Proton. [Online]. Available: https://proton.me/drive. [Accessed: Mar. 21, 2025].
- "iCloud Data Security Overview," Apple Support. [Online]. Available: https://support.apple.com/en- us/102651. [Accessed: Mar. 21, 2025].
- "Understanding End-to-End Encryption in Snowflake," Snowflake. [Online]. Available: https://docs.snowflake.com/en/user-guide/security- encryption-end-to-end. [Accessed: Mar. 21, 2025].
- "File Encryption and Decryption Made Easy with GPG," Red Hat. [Online]. Available: https://www.redhat.com/en/blog/encryption-decryption- gpg. [Accessed: Mar. 21, 2025].
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).