Submitted:
02 April 2025
Posted:
03 April 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
- In order to avoid excessive reliance on public parameters, this paper proposes a multi-key homomorphic encryption scheme based on a distributed key generation protocol. Each user independently generates his or her own public and private key pair, and enhances the security and decentralization of the scheme. Based on ciphertext expansion technology, this paper proposes a distributed ciphertext decryption method suitable for multi-key scenarios. By expanding the ciphertext structure, multiple users can collaboratively participate in the decryption process.
- In order to further protect the plaintext privacy from each user, by embedding the specified target user into the ciphertext, this paper proposes an enhanced multi-key homomorphic encryption scheme that only allows only the target user to decrypt.
- By applying the proposed lattice-based multi-key homomorphic encryption scheme into the data submission stage, a crowd-sensing scheme is proposed, protecting the privacy of the users. This ensures that the data is not leaked during transmission and processing, and all entities except the data requester cannot obtain the perception results.
2. Materials and Methods
2.1. Symbols and Definitions
2.2. Multi-Key Homomorphic Encryption
- -
- : Input security parameter and output public parameter .
- -
- : Input public parameters and output the user's public key and private key .
- -
- : For the plaintext that needs to be encrypted, input the public key and output a ciphertext .
- -
- : Input the public keys of users and the ciphertext encrypted by the -th public key , and output the expanded ciphertext .
- -
- : Given a function , input extended ciphertexts , and output the ciphertext after homomorphic operation.
- -
-
: Input the private keys of users and the homomorphic operation ciphertext , and output the plaintext . The decryption process is divided into two steps, as follows:
- : Input the private key of the -th user and the homomorphic operation ciphertext , and output the partial decryption result .
- : Input the partial decryption results of users and output the plaintext .
3. Lattice-Based Multi-Key Homomorphic Encryption Scheme Without CRS
3.1. Securrity Model
- Initialization phase: Input security parameter , runs algorithm to generate system public parameter . runs algorithm to generate key pairs for users and key pair for target user , and sends , to .
- Query phase: maintains a query record table , which is empty at initialization and records all ciphertext query indexes initiated by during the entire query process. can adaptively select any plaintext and initiate a query request. runs the algorithm to generate the ciphertext and returns it to . This phase allows to perform a polynomial number of queries.
- Challenge phase: After finishes the query, it requests the challenge ciphertext. selects two plaintexts , of equal length and the target public key set , and sends them to . randomly selects a bit , calculates the challenge ciphertext , and returns to .
-
Guessing stage: outputs a guess bit based on . If , wins and the game output is 1; otherwise, the output is 0.If and only if for all PPT adversaries , there exists a negligible function such that:
3.2. Scheme Construction
- System Initialization
- 2.
- Key generation algorithm
- 3.
- Coding
- 4.
- Encryption algorithm
- 5.
- Ciphertext expansion algorithm
- 6.
- Homomorphic operation algorithm
- 7.
- Partial decryption algorithm
- 8.
- Final decryption algorithm
- 9.
- Decoding
3.3. Correctness Analysis
3.4. Security Analysis
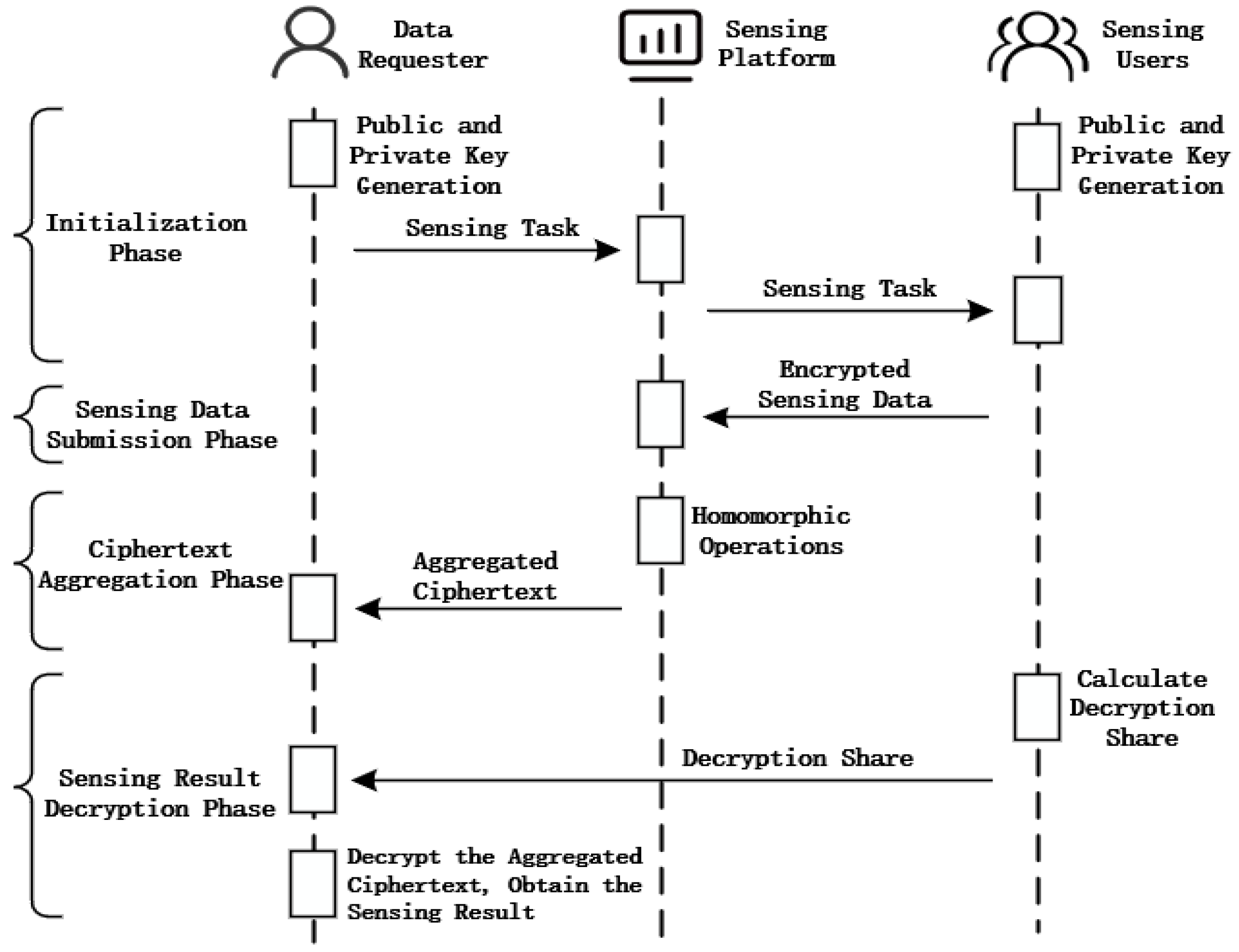
4. Crowd-sensing Scheme with privacy preservation
4.1. System Model
- Sensing users
- 2.
- Sensing platform
- 3.
- Data requester
4.2. Construction of Crowd-sensing Scheme Based on Multi-key Homomorphic Encryption
4.2.1. Initialization Phase
4.2.2. Perception Data Submission Phase
4.2.3. Ciphertext Aggregation Phase
4.2.4. Perception Result Decryption Phase
5. Security Analysis of Crowd-sensing Scheme Based on Multi-key Homomorphic Encryption
6. Conclusion
Acknowledgement
References
- Liu, L.; Zhang, J.; Song, S.H. Client-edge-cloud hierarchical federated learning. ICC 2020-2020 IEEE International Conference on Communications (ICC).
- Kim, M.; Harmanci, A.O.; Bossuat, J.P. Ultrafast homomorphic encryption models enable secure outsourcing of genotype imputation. Cell systems 2021, 12, 1108–1120.e4. [Google Scholar] [CrossRef] [PubMed]
- Kim, H.I.; Kim, H.J.; Chang, J.W. ; A secure kNN query processing algorithm using homomorphic encryption on outsourced database. Data & knowledge engineering 2019, 123, 101602. [Google Scholar]
- Yang, Y.; Huang, X.; Liu, X. A comprehensive survey on secure outsourced computation and its applications. IEEE Access 2019, 7, 159426–159465. [Google Scholar] [CrossRef]
- Sun, J.; Xu, G.; Zhang, T. Verifiable, fair and privacy-preserving broadcast authorization for flexible data sharing in clouds. IEEE Transactions on Information Forensics and Security 2022, 18, 683–698. [Google Scholar] [CrossRef]
- Kadykov, V.; Levina, A.; Voznesensky, A. Homomorphic encryption within lattice-based encryption system. Procedia Computer Science 2021, 186, 309–315. [Google Scholar] [CrossRef]
- Chen, H.; Dai, W.; Kim, M. Efficient multi-key homomorphic encryption with packed ciphertexts with application to oblivious neural network inference. Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security. 2019: 395-412.
- Xu, K.; Tan, B.H.M.; Wang, L.P. Multi-key fully homomorphic encryption from NTRU and (R) LWE with faster bootstrapping. Theoretical Computer Science 2023, 968, 114026. [Google Scholar] [CrossRef]
- Biswas, C.; Dutta, R. Secure and efficient multi-key FHE scheme supporting multi-bit messages from LWE preserving non-interactive decryption. Journal of Ambient Intelligence and Humanized Computing 2023, 14, 16451–16464. [Google Scholar] [CrossRef]
- Zhou, T.; Chen, L.; Che, X. Multi-key Fully Homomorphic Encryption Scheme with Compact Ciphertexts. Cryptology ePrint Archive, 2021.
- Li, H.; Li, X.; Gao, J. Multi-hop Multi-key Homomorphic Encryption with Less Noise Under CRS Model. International Symposium on Cyberspace Safety and Security. Cham: Springer International Publishing, 2022: 342-357.
- Luo, F.; Wang, H.; Saif, A.K. Multi-key fully homomorphic encryption without CRS from RLWE. Computer Standards & Interfaces 2023, 86, 103742. [Google Scholar]
- Ma, J.; Naas, S.A.; Sigg, S. Privacy-preserving federated learning based on multi-key homomorphic encryption. International Journal of Intelligent Systems 2022, 37, 5880–5901. [Google Scholar] [CrossRef]
- Ganesh, B.; Palmieri, P. Secure Search over Multi-key Homomorphically Encrypted Data. 2023 7th International Conference on Cryptography, Security and Privacy (CSP). IEEE, 2023: 145-151.
- Li, X.; Li, H.; Gao, J. Privacy preserving via multi-key homomorphic encryption in cloud computing. Journal of Information Security and Applications 2023, 74, 103463. [Google Scholar] [CrossRef]
- Chen, Y.; Dong, S.; Li, T. Dynamic multi-key FHE in asymmetric key setting from LWE. IEEE Transactions on Information Forensics and Security 2021, 16, 5239–5249. [Google Scholar] [CrossRef]
- Antwi-Boasiako, E.; Zhou, S.; Liao, Y. An LWE-Based Multi-Key Privacy-Preserving Distributed Deep Learning. 2021 IEEE 23rd Int Conf on High Performance Computing & Communications, 2021: 533-542.
- Che, X.; Zhou, H.; Yang, X. Efficient multi-key homomorphic encryption scheme on ring LWE. Journal of Xidian University 2023, 48, 87–95. [Google Scholar]
- Li, N.; Zhou, T.; Che, X. Research on multi-key homomorphic encryption. Journal of Cryptologic Reshearch 2020, 7, 713–734. [Google Scholar]
- Pathak, V. Lattices, homomorphic encryption, and ckks. arXiv preprint 2022, arXiv:2205.03511. [Google Scholar]
- Qiu, F.; Yang, H.; Zhou, L. Privacy preserving federated learning using ckks homomorphic encryption. International Conference on Wireless Algorithms, Systems, and Applications. Cham: Springer Nature Switzerland, 2022: 427-440.
- Li, J.; Zhu, Y.; Hua, Y. Crowdsourcing sensing to smartphones: A randomized auction approach. IEEE Transactions on Mobile Computing 2017, 16, 2764–2777. [Google Scholar] [CrossRef]
- Zheng, X.; Cui, L.; Zhang, L. The perception results based on encryption technology can verify the privacy preservation group intelligence perception scheme. Journal of Beijing Institute of Technology(Nature Edition) 2024, 44, 413–420. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).




