Submitted:
21 March 2025
Posted:
24 March 2025
You are already at the latest version
Abstract
Keywords:
1. Introduction
2. Related Work
2.1. Evolution of Online Banking
2.2. Security Concerns in Online Banking
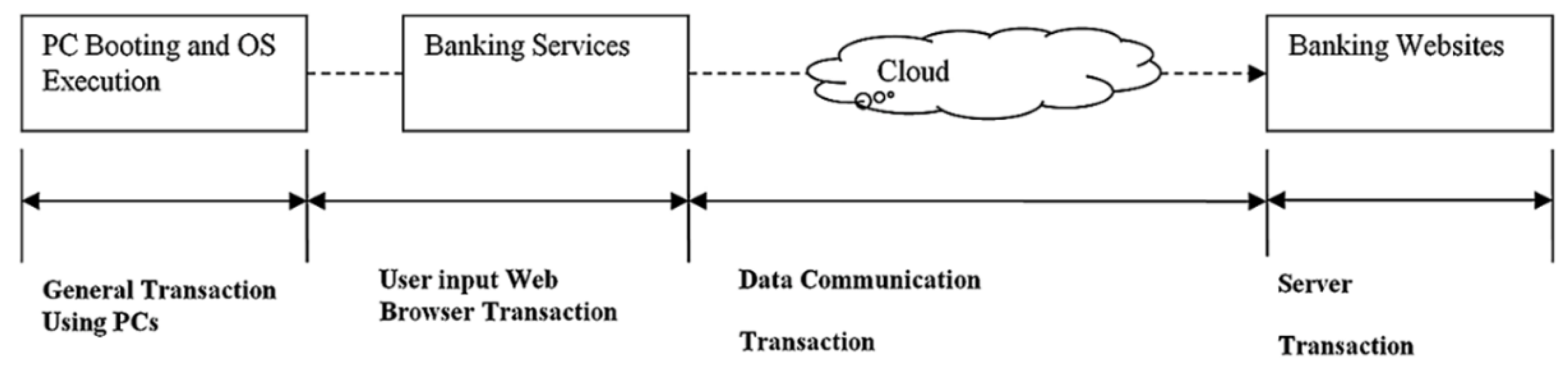
- Authentication: Ensuring that only authorized users gain access to their accounts is a primary concern [38]. The use of usernames, passwords, personal identification numbers (PINs), and security questions forms the basis of most authentication processes. However, any weakness in these systems can lead to unauthorized access and fraud.
- Data Integrity and Confidentiality: Protecting customer data from unauthorized alteration or disclosure is critical. Banks must implement robust encryption and data integrity measures to ensure that sensitive information remains secure.
- System Design and Access Control: The architecture of online banking systems must be designed with security in mind from the ground up. This includes implementing firewalls, antivirus systems, and continuous monitoring to detect and thwart potential breaches.
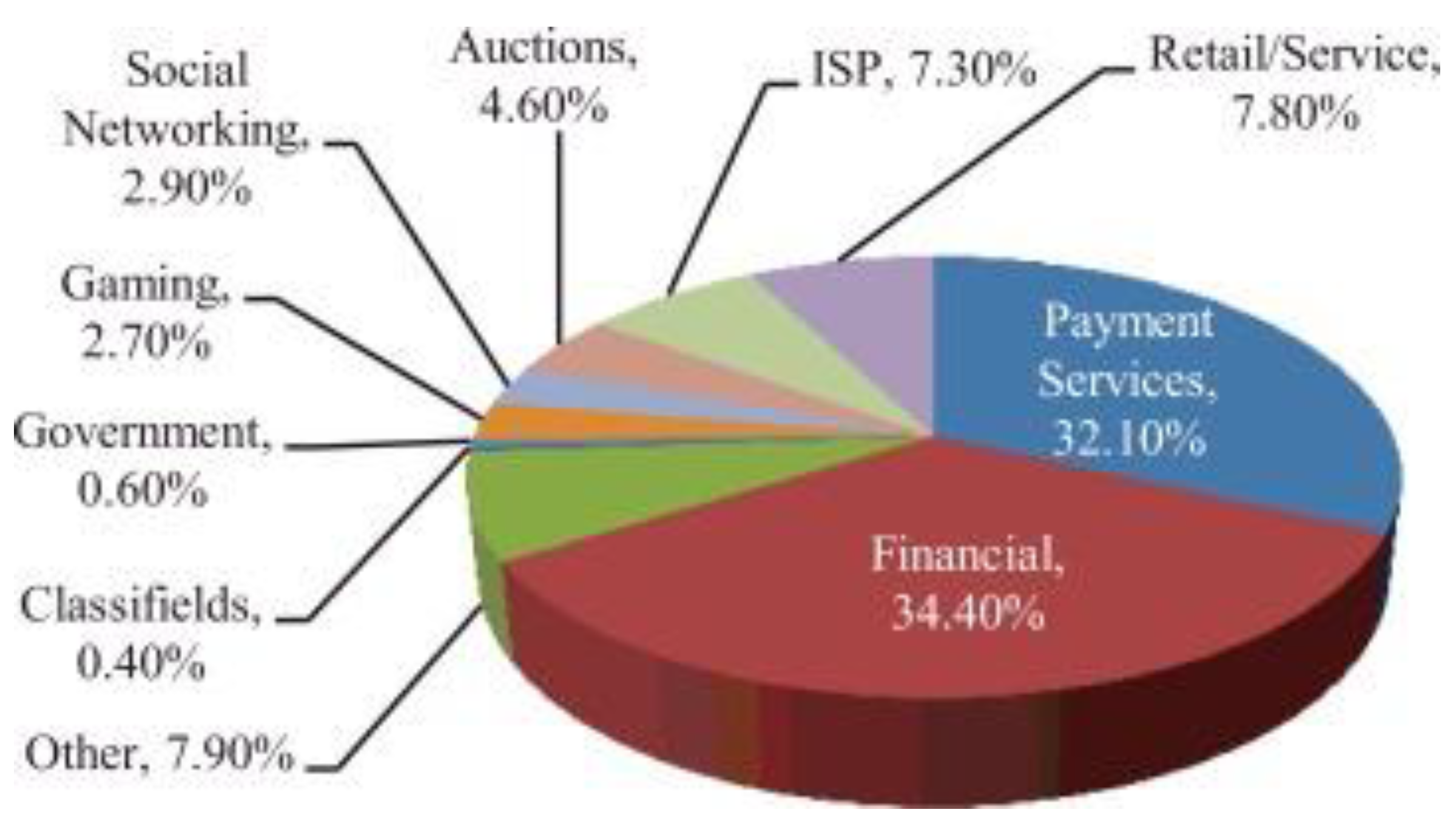
2.3. Prevailing Fraud Factors and Attack Techniques
- Phishing, Vishing, and Smishing: Fraudsters use emails (phishing), phone calls (vishing), and text messages (smishing) [34] to trick customers into divulging sensitive information [12]. These scams are designed to mimic legitimate bank communications, thereby deceiving unsuspecting users and stealing their identity, which encompasses identity fraud [31].
- Malware and Trojan Attacks: Malicious software such as keyloggers, viruses, and trojans are employed to capture login credentials and other confidential data from infected devices.
- Man-in-the-Middle and Fraudulent Website Attacks: Attackers create counterfeit websites that resemble official bank portals to capture user information as it is entered. These methods exploit the trust that customers place in familiar banking interfaces [24].
- Trojan Attack: in this case the attacker installs a Trojan in form of key logger computer program on an unsuspicious users’ computer. [13] This often kick starts when a user visit compromised websites, downloads and installs infected programme on their electronic device.
2.4. Security Measures and Recommendations
- One-Time Passwords (OTP): Often used as a secondary authentication factor, OTPs provide a temporary code that enhances security during online transactions. One-time passwords could be static or could change periodically [14].
- Digital Certificates and Public Key Infrastructure (PKI): These technologies help verify the identities of both the user and the bank’s server, ensuring secure communication channels. However, reports [15] that several attacks on digital certificates recently involving hackers breaking into 2 digital certificates out of 3, has led to doubts regarding the safety of the models of digital certificates.
- Device Registration and Recognition: By identifying and authorizing trusted devices, banks can limit access to known endpoints.
- Biometric Verification: Technologies such as fingerprint scanning and facial recognition have become increasingly prevalent in safeguarding online banking systems.
- Pass-Phrase Verification: Often referred to a second level security method used by banks to verify transactions being carried out by users online, enabling the authorization of transactions to go through.
- CAPTCHA (Completely Automated Public Test to tell Computers and Humans Apart): as the name implies is an automated verification tool widely used in the prevention of online automated system attacks. [16] CAPTCHA is commonly used in solving Artificial Intelligence (AI) problems online by generating and grading tests that are humanly solvable but not bot solvable [33].
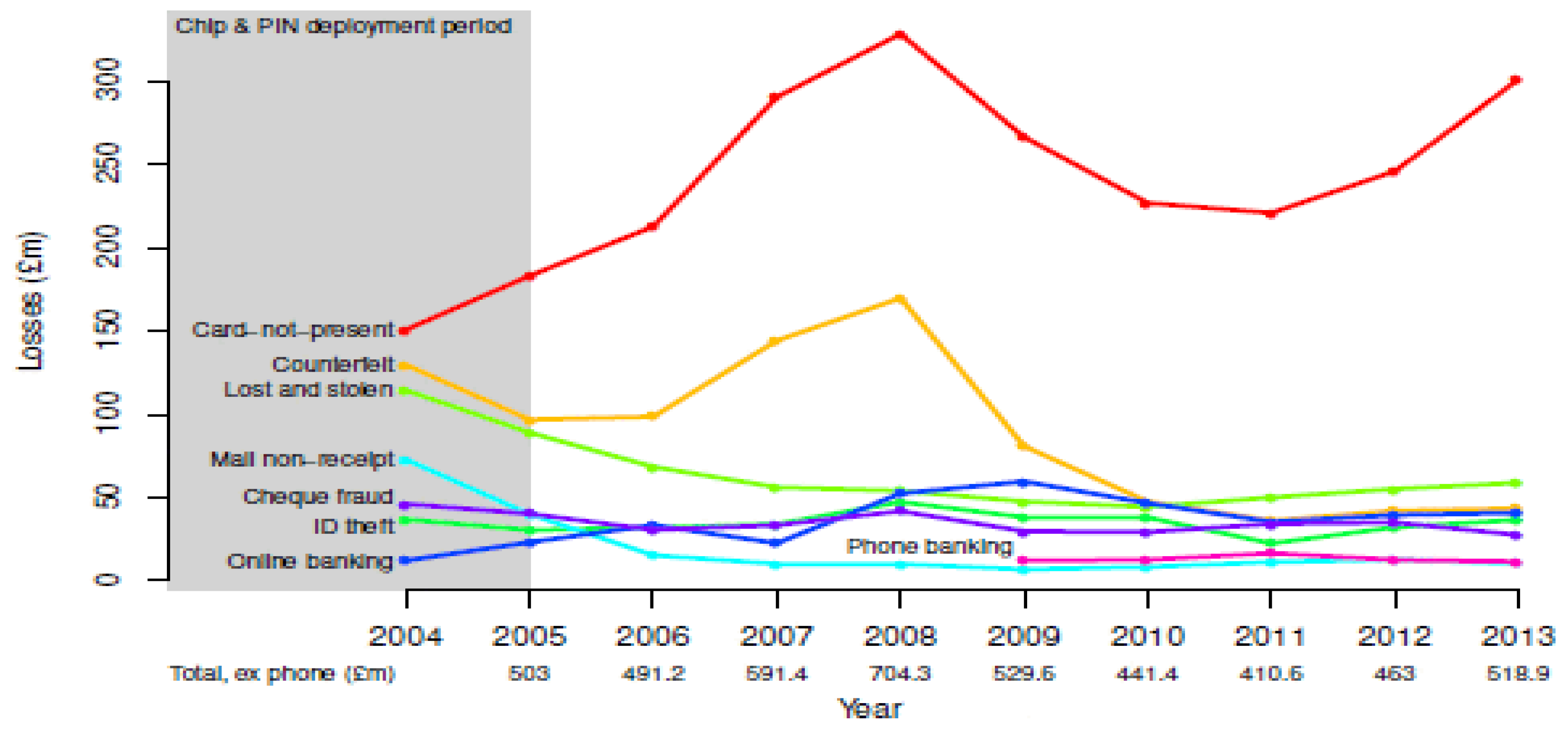
3. Methodology
3.1. Research Design and Rationale
3.2. Data Collection: Online Interviews
- General usage of online banking services
- Perceived benefits and convenience
- Experiences with and perceptions of online fraud
- Trust in the security measures implemented by banks
3.3. Data Analysis
3.4. Ethical Considerations
4. Results
4.1. Overview of Collected Data
| Classification of Responses | Percentage of Findings |
|---|---|
|
40 |
|
12 |
|
10 |
|
18 |
|
23 (57%) |
|
15 (37%) |
|
6 |
- User Demographics: The sample included both personal and business account holders with a range of experiences in online banking. A significant proportion of respondents had been banking with their institutions for over three years, indicating a well-established customer relationship.
- Usage Patterns: Younger users were found to be more comfortable and reliant on online banking services, whereas older users tended to maintain a preference for in-person banking. This divergence was particularly evident in responses related to the frequency of physical branch visits.
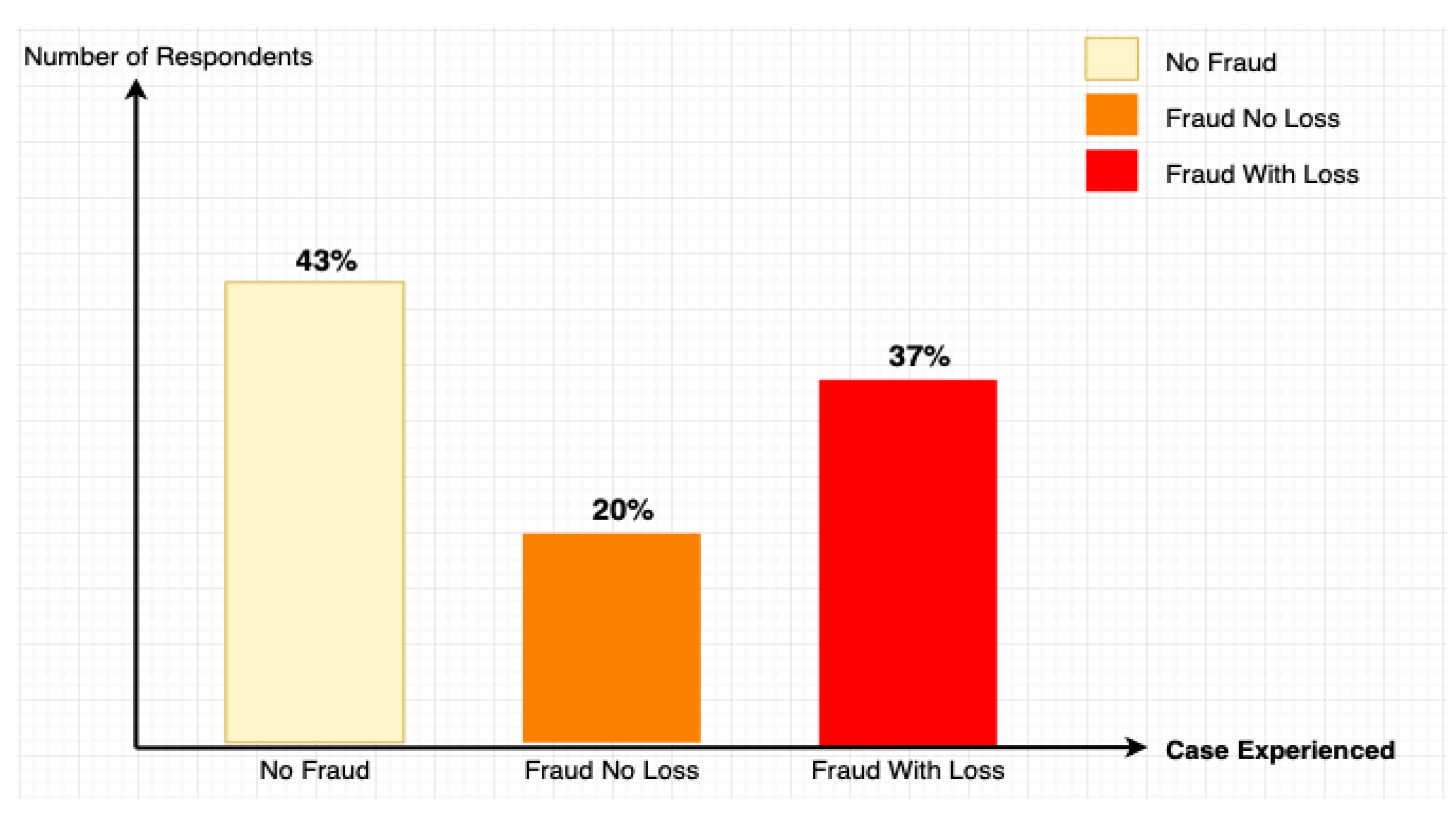
- Fraud Experience: Approximately 57% of the respondents reported having been victims of some form of online fraud. Among these, 37% experienced direct financial losses, underscoring the severe impact that fraudulent activities can have on customer finances.
- Security Perceptions: Despite the availability of multiple security measures, a significant number of respondents expressed concerns regarding data integrity and unauthorized access. The findings suggest that while users appreciate the convenience of online banking, they remain conscious of its security concerns.
4.2. Detailed Findings
4.2.1. Convenience and Efficiency
4.2.2. Fraud Incidence and Impact
4.2.3. Trust and Customer Relationship
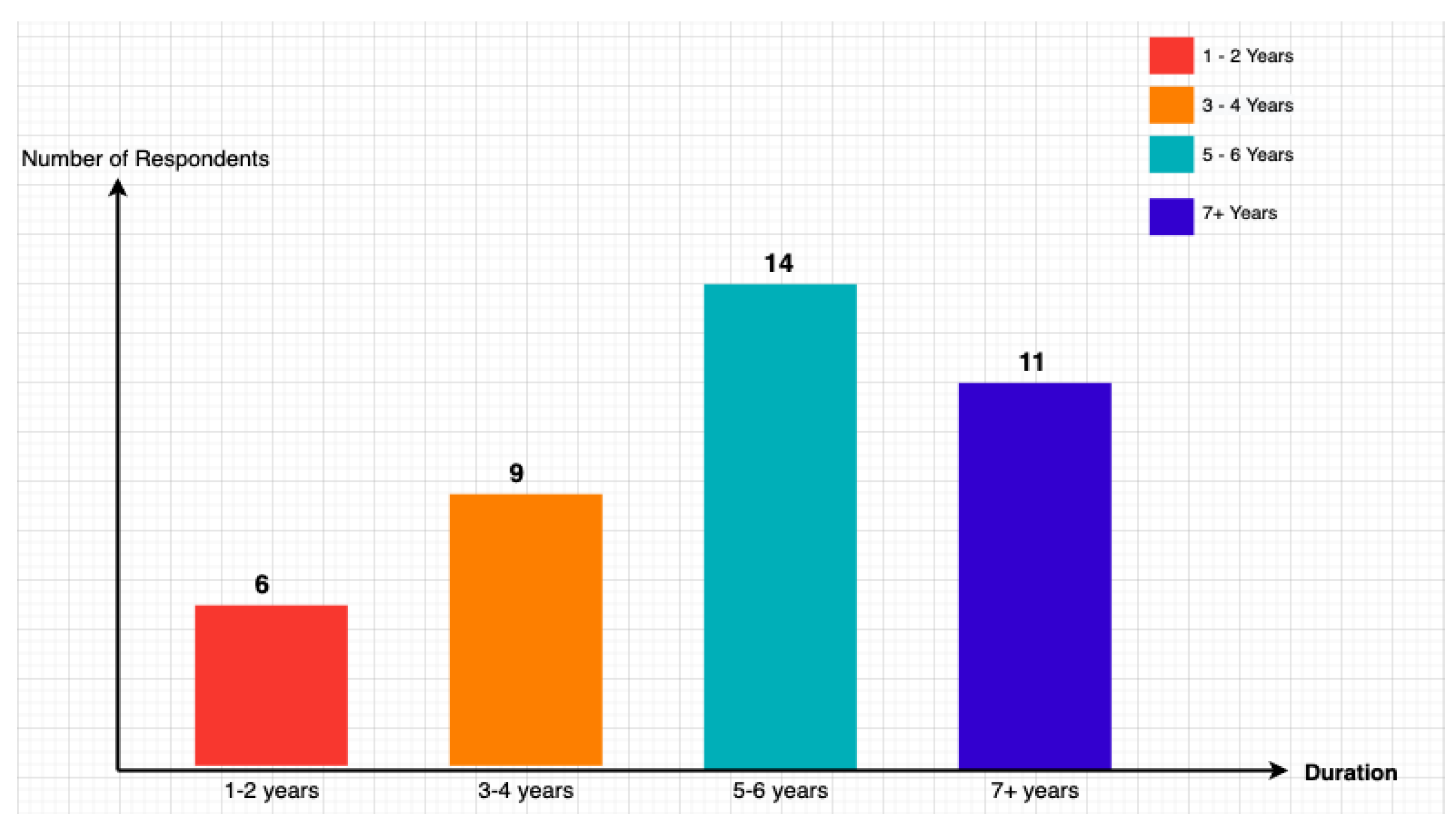
4.2.4. Effectiveness of Current Security Measures
5. Discussion
5.1. Interpreting the Findings
5.2. Security Versus Convenience
5.3. Evolving Fraud Tactics and the Need for Adaptive Security
5.4. Recommendations for Future Practice
- Enhanced Customer Awareness: banks must implement comprehensive educational programs that inform customers about the risks associated with online banking and provide guidance on how to protect themselves. This includes awareness campaigns on phishing, safe password practices and the importance of updating their software.
- Integrated Security Solutions: Financial institutions are encouraged to adopt a multi-layered security approach that integrates various authentication and monitoring tools. Combining traditional methods (such as OTPs and digital certificates) with emerging technologies (like biometrics and AI-based fraud detection) [22,32] can create a more resilient security environment.
- Regular Security Audits and Updates: Given the rapid evolution of cyber threats, regular security audits are critical. Banks must routinely assess the effectiveness of their security measures and update them to counter emerging vulnerabilities. Engaging with external cybersecurity experts to conduct these audits can also provide an independent perspective on potential weaknesses.
- Improved Communication and Transparency: To rebuild and maintain trust, banks should enhance their communication strategies regarding security practices. Transparent reporting on security breaches, along with clear explanations of the steps being taken to mitigate risks, can help restore customer confidence.
- Research and Collaboration: Finally, there is a need for continued research and collaboration between financial institutions, cybersecurity experts, and academic researchers. Joint efforts can foster innovation in security technologies and create industry standards that are better equipped to handle the evolving landscape of online fraud.
6. Conclusions
References
- Pilcher, J. (2012). Infographic: The History of Internet Banking (1983 – 2012). Available online: https://thefinancialbrand.com/25380/yodlee-history-of-internet-banking/.
- Sarreal, R. , Segal, B., Woods, L. (2019).History of Online Banking: How Internet Banking went Mainstream. Available online: https://www.gobankingrates.com/banking/banks/history-online-banking/.
- Sarreal, R. (2017). History of Online Banking: How Internet Banking went Mainstream. Available online: http://www.neville-associates.com/blog/history-online-banking-how-internet-banking-went-mainstream.
- Woods, L. (2014). How Online Banking Evolved into a Mainstream Financial Tool. Available online: https://www.fool.com/investing/general/2014/11/09/how-online-banking-evolved-into-a-mainstream-finan.aspx.
- Kesharwani, A. , & Bisht, S. S. (2012). The Impact of Trust and Perceived Risk on Internet Banking Adoption in India: An Extension of Technology Acceptance Model. In International Journal of Bank Marketing (Vol. 30 Iss: 4, pp 303 – 322). Available online: https://www.researchgate.net/publication/243459780_The_impact_of_trust_and_perceived_risk_on_Internet_banking_adoption_in_India. [CrossRef]
- Singh, S. (2013). Service Quality Gap Issues in Online Banking. In International Conference on Management and Information Systems (pp. 616). Retrieved from https://www.researchgate.net/publication/308746656_Service_Quality_Gap_Issues_in_Online_Banking.
- Emefiele, C. , Obim, E. N., & Nkamare, S. E. (2018). Impact of Electronic Banking on Detection of Fraud in Nigerian Banking. In International Journal of Research in Finance and Marketing (IJRFM), Vol. 8 Issue 9. Retrieved from https://www.academia.edu/37850988/IMPACT_OF_ELECTRONIC_BANKING_ON_DETECTION_OF_FRAUD.
- Nagar, N. , & Suman, U. (2017). Prevention, Detection, and Recovery of CSRF Attack in online banking system. in aljawarneh, s. a. (ed.), Online Banking Security Measures and Data Protection (pp. 172-188). Retrieved from https://www-igi-global-com.ezproxy.napier.ac.uk/gateway/chapter/full-text-html/166871.
- Kassim, N. M. , & Ramayah, T. (2013). Security Policy Issues in Internet Banking in Malaysia. In Management Association, I. (Ed.), IT Policy and Ethics: Concepts, Methodologies, Tools, and Applications (pp. 1274-1293). Retrieved from https://www-igi-global-com.ezproxy.napier.ac.uk/gateway/chapter/full-text-html/75078. [CrossRef]
- Khande, R. , & Patil, Y. (2014). Online Banking in India: Attacks and Preventive Measures to Minimize Risk. In International Conference on Information Communication and Embedded Systems (ICICES2014), Chennai, 2014 (pp. 1-5). Retrieved from https://ieeexplore-ieee-org.ezproxy.napier.ac.uk/document/7033940. [CrossRef]
- Moghimi, M. , & Varjani, A. Y. (2016). New Rule-Based Phishing Detection Method. In Expert Systems with Applications, Vol. 53 (pp. 231-242). Available online: https://www.sciencedirect.com/science/article/pii/S0957417416000385#bbib0013. [CrossRef]
- Drolet, M. (2019). Smishing and vishing: How These Cyber Attacks Work and How to Prevent Them. In Infosec At Your Service. Available online: https://www.csoonline.com/article/3411439/smishing-and-vishing-how-these-cyber-attacks-work-and-how-to-prevent-them.html.
- Khrais, L. T. (2015). Highlighting the Vulnerabilities of Online Banking System. In Journal of Internet Banking and Commerce. Available online: http://www.icommercecentral.com/open-access/highlighting-the-vulnerabilities-of-online-banking-system.php?aid=61518.
- Nilsson, M. , Adams, A., & Herd, S. (2005). Building Security and Trust in Online Banking. In CHI ’05 Extended Abstracts on Human Factors in Computing Systems (pp. 1701–1704). https://doi.org/10.1145/1056808.1057001. [CrossRef]
- Leavitt, N. (2011). Internet Security Under Attack: The Undermining of Digital Certificates. In Computer Vol. 44 (12), pp. 17-20. Retrieved from https://ieeexplore.ieee.org/abstract/document/6096548. [CrossRef]
- Yan, J. & Ahmad, A. S. E. (2008). Usability of CAPTCHAs or Usability Issues in CAPTCHA Design. In Proceedings of the 4th Symposium on Usable Privacy and Security (SOUPS ‘08) pp. 44-52. [CrossRef]
- Reurink, A. (2016). Financial Fraud: A Literature Review. In MPIFG Discussion Paper 16/5. Retrieved from https://www.mpifg.de/pu/mpifg_dp/dp16-5.pdf.
- Aboobucker, I. ,& Bao, Y. (2018). What Obstruct Customer Acceptance of Internet Banking? Security and Privacy, Risk, Trust and Website Usability and the Role of Moderators. In Journal of High Technology Management Research. Vol. 29 (1) pp. 109–123. [CrossRef]
- Aljawarneh, S. A. (2017). Emerging Challenges, Security Issues, and Technologies in Online Banking Systems. In Aljawarneh, S. A. (Eds.), Online Banking Security Measures and Data Protection (pp. 90-112). Retrieved from https://www-igi-global-com.ezproxy.napier.ac.uk/gateway/chapter/166866. [CrossRef]
- Bond, M. , Choudary, O., Murdoch, S. J., Skorobogatov, S., & Anderson, R. (2014). Chip and Skim: Cloning EMV Cards with the Pre-play Attack. In 2014 IEEE Symposium on Security and Privacy, San Jose, CA, 2014, pp. 49-64. Retrieved from https://ieeexplore.ieee.org/abstract/document/6956556. [CrossRef]
- Buchanan, T. , & Whitty, M. T. (2014). The Online Dating Romance Scam: Causes and Consequences of Victimhood. In Psychology, Crime & Law Vol. 20 (3), pp. 261-283. Retrieved from https://www.tandfonline.com/doi/full/10.1080/1068316X.2013.772180?src=recsys. [CrossRef]
- Chen, J. , & Guo, C. (2006). Online Detection and Prevention of Phishing Attacks. In First International Conference on Communication and Networking in China, Beijing. pp 1-7. [CrossRef]
- Coffee, J. C. (2015). What Went Wrong? An Initial Inquiry into the Causes of the 2008 Financial Crisis. In Journal of Corporate Law Studies. Vol. 9 (1) pp. 1-22. [CrossRef]
- Hoffman, A. O. I. , Birnbrich. C. (2012). The Impact of Fraud Prevention on Bank-Customer Relationships – An Empirical Investigation in Retail Banking. In International Journal of Bank Marketing. Vol. 30 (5), pp. 390-407. http://arvidhoffmann.nl/Hoffmann_Birnbrich_2012.pdf.
- Lin, W. , Wang, Y., & Hung, Y. (2020). Analysing the Factors Influencing the Adoption of Internet Banking: Applying DEMATEL-ANP-SEM Approach. [CrossRef]
- Mermod, A.Y. (2012). Fraud in Modern Banking: Highlights on Online Internet Banking Fraud. In Çaliyurt, K., & Idowu, S. (eds) Emerging Fraud (pp. 149-161). [CrossRef]
- Ohman, A. (2005). Qualitative Methodology for Rehabilitation Research. Available online: http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.451.9315&rep=rep1&type=pdf.
- Özkul, F. U. , & Pamukçu, A. (2012). Fraud Detection and Forensic Accounting. In Çaliyurt, K., & Idowu, S. (eds) Emerging Fraud (pp. 19-41). Retrieved from https://link.springer.com/chapter/10.1007/978-3-642-20826-3_2. [CrossRef]
- Peotta, L. , Holtz, M. D., David, B. M., Deus, F. G., & Timóteo, D. S. R. (2018). A Formal Classification of Internet Banking Attacks and Vulnerabilities. In International Journal of Computer Vision and Machine Learning (IJCVML), Vol. 1 (3), pp. 186-197. Retrieved from https://www.academia.edu/39010214/A_FORMAL_CLASSIFICATION_OF_INTERNET_BANKING_ATTACKS_AND_VULNERABILITIES.
- Randhawa, K. , Loo, C. K., Seera, M., Lim, C. P., & Nandi, A. K. (2018). Credit Card Fraud Detection Using AdaBoost and Majority Voting. In IEEE Access, vol. 6, pp. 14277-14284. [CrossRef]
- Saunders, K. M. , & Zucker, B. (2010). Counteracting Identity Fraud in the Information Age: The Identity Theft and Assumption Deterrence Act. In International Review of Law, Computers & Technology (pp. 183-192). [CrossRef]
- Vanhoeyveld, J. , Martens, D., & Peeters, B. (2020). Value-added Tax Fraud Detection with Scalable Anomaly Detection Techniques. In Applied Soft Computing. [CrossRef]
- Yan, J. , & Ahmad, A. S. E. (2008). Usability of CAPTCHAs or Usability Issues in CAPTCHA Design. In Proceedings of the 4th Symposium on Usable Privacy and Security (SOUPS ‘08) pp. 44-52. [CrossRef]
- Adams, J. (2009). FRAUD: A Text Alert for Community Banks: Small Banks Bear the Brunt of ’smishing’ Attacks. In Bank Technology News, 22 (9), 1. Retrieved from https://search-proquest-com.ezproxy.napier.ac.uk/docview/208165966?rfr_id=info%3Axri%2Fsid%3Aprimo.
- Bergman, M. M. (2008). Advances in Mixed Methods Research. Available online: https://books.google.co.uk/books?hl=en&lr=&id=hWT6mWbnGC0C&oi=fnd&pg=PR5&dq=mixed+methods+research&ots=Tnzbq77RrB&sig=c9ahUPlGhZGvqocQcJ4Ye4jLlz0&redir_esc=y#v=onepage&q=mixed%20methods%20research&f=false.
- Cavaglieri, C. (2020). Best Banks for Dealing with Bank Fraud. In How Does Your Bank Handle Fraud? Exclusive Data by Which? Money reveals the best and Worst Firms for Handling Fraud Complaints. Retrieved from https://www.which.co.uk/money/banking/banking-security-and-new-ways-to-pay/online-banking-security/best-banks-for-dealing-with-bank-fraud-a8qp45d23x3l.
- Creswell, J. W. (2015). A Concise Introduction to Mixed Methods Research. Available online: https://books.google.co.uk/books?hl=en&lr=&id=51UXBAAAQBAJ&oi=fnd&pg=PR1&dq=mixed+methods+research&ots=69LrS8StIw&sig=3aiOqlIJXKk0ovJWda2szOX6nj0&redir_esc=y#v=onepage&q=mixed%20methods%20research&f=false.
- Dolma, K. (2020). A Study on the Impact of Online Banking Fraud: Customer’s Perspective. Retrieved from https://www.academia.edu/27182517/_A_Study_on_The_Impact_of_Online_Banking_Frauds_Customers.
- Drolet, M. (2019). Smishing and vishing: How These Cyber Attacks Work and How to Prevent Them. In Infosec At Your Service. Available online: https://www.csoonline.com/article/3411439/smishing-and-vishing-how-these-cyber-attacks-work-and-how-to-prevent-them.html.
- FNB. (2017). FNB Warns Against New Online Banking Scam. In Financial Services Monitor Worldwide. Retrieved from https://search-proquest-com.ezproxy.napier.ac.uk/docview/1975913855/fulltext/27413BD0FA334968PQ/1?accountid=16607.
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).




