1. Introduction
In today’s interconnected world, a reliable and scalable network infrastructure is critical for mid-sized organizations to meet operational demands and support growth. Efficient network design ensures seamless connectivity for employees and clients, enhances security, and accommodates future expansion (Forouzan, 2012). This document outlines the design and implementation of a network infrastructure for a mid-sized organization housed within a two-story building. The proposed network has to be in service for at least twenty staff, each requiring one wire and two wireless connections, and also should meet a wide range of administration, IT, staff, and client zones simultaneously. It should focus on aiming for scalability, performance optimization, and security implementation through a hierarchical topological network design. The key highlights are segmenting the traffic by configuring VLANs, providing wireless access using dual-band, and implementing redundancy to ensure high availability. Besides, considerations for effective network monitoring and scalability in the future have been made for adaptation to organizational growth as well as technological changes. In essence, this infrastructure lays the base for efficient, secure, and future-ready networking to meet medium-sized enterprise needs.
2. Related Works
Designing and implementing a scalable network infrastructure for mid-sized organizations is daunting, requiring attention to performance, security, and future growth. A review of the literature provides insight into the best practices and methodologies related to this area. According to Forouzan (2012), it has been shown that hierarchical network design plays an important role in making organizational networks more scalable and easier to manage. This allows for effective traffic management and minimizes troubleshooting time. The MEDP from cisco gives comprehensive guidance on the LAN design for the medium enterprise. MEDP necessitates a well-structured and organized LAN architecture with core technologies to accommodate the requirements of an organization. Yuan, 2021 this work has shown some network designing strategies in SMEs by incorporating identity authentication mechanism to make more secure network architectures. The guide is part of the best practices in network design provided by Auvik Networks: for efficiency and reliability, any network design has to observe very effective planning, with strict adherence to established protocols. Paillisse et al. (2020) discuss the deployment of SDN in enterprise environments, presenting practical experiences in deploying SD-Access solutions to enhance network flexibility and scalability. Moisio (2022) addresses capacity planning as a vital part of network architecture design and argues for strategies that can handle organizational growth without performance degradation. HP Networking presents the integration of wireless and wired networks, discussing unified solutions that support mobility and BYOD policies to improve employee productivity. ComScore, 2022, describes how a modern IT infrastructure for a mid-sized business should be built by upholding the importance of scalable network solutions in meeting business goals and objectives.
Supply chain optimization can be enhanced through proper network design; AIMMS offers case studies that demonstrate how such strategic network planning has enabled a company to achieve operational efficiencies. Meter.com has provided examples of network design for both corporate and retail environments to show how customized network architecture can meet the demands of particular industries. Opex Analytics discusses the role of network design in mergers and acquisitions, showing how good network planning can ensure frictionless organizational integration. Lex Technology (2024) presents the basics of network design for small and medium-sized businesses, discussing strategies toward robust, efficient, and secure network architectures able to scale with business growth. IT Jones, 2022, describes the procedures of designing computer networks for businesses, emphasizing the best and most economical solution to meet specific business needs. According to Jejeniwa et al. (2024) and Roux et al. (2023), the increased demand for scalable data solutions, especially by SMEs, has been influenced by the ever-growing dependence on data-driven decision-making across industries. In such a competitive and dynamic market, managing, processing, and analyzing large volumes of big data efficiently becomes very crucial for these companies. This discusses scalability in data solutions, the main reasons behind the need for scalability, and how to achieve it using data virtualization elements of scalable data infrastructures and underlines the benefits of these solutions for SMEs.
Scalability in data solutions refers to the capability of a system to handle growing amounts of data and an increasing number of users seamlessly and cost-effectively (Ediae et al., 2024). A scalable data solution can adapt to the expanding needs of a business without requiring significant redesign or incurring substantial additional costs. This adaptability is essential for SMEs, which often experience rapid growth and must respond quickly to market changes. In the context of data solution, scalability has been considered as both vertical and horizontal scalability (Adenekan et al., 2024). Vertical scaling up would mean increasing the capacity of existing hardware or software by adding more resources to the CPU, memory, or storage. Horizontal scaling out means adding nodes or machines to a system, and hence the system is enabled to share its workload across multiple devices. Both approaches are critical to ensure that a data system continues to be responsive and efficient as more demands are placed on it. Scalability also involves sustaining performance levels and ensuring reliability as the system grows. This covers the ability to handle larger data sets, more complex queries, and data integrity and security. A truly scalable data solution provides consistent performance and reliability irrespective of the data volume or user load.
Developing scalable data solutions involves integrating several key components, each of which must be designed to scale efficiently (Joel and Oguanobi, 2024). These components include data storage, data processing, data analytics, and data security. Data storage is the foundation of any data solution, and its scalability is critical for managing growing datasets. Scalable data storage solutions must accommodate increasing volumes of data without compromising performance or accessibility. One of the most popular scalable storages. Another popular solution is cloud storage. Cloud providers like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform have made available scalable storage options in which businesses only pay for the amount of storage they utilize (Kaushik et al., 2021). This gives SMEs virtually unlimited storage capacity for scaling up or down depending on demand.
These platforms offer virtually unlimited storage capacity, and hence SMEs can upscale or downscale their storage needs based on demand. Cloud storage also offers redundancy and replication of data across multiple geographic locations for high availability and disaster recovery. Another scalable storage solution is the usage of distributed file systems, such as HDFS or GFS. These systems store data on a lot of machines to provide horizontal scalability. They handle a large amount of data by breaking down data into small chunks and then distributing these chunks among different nodes. This does not only enhance storage but also the access speed as all processes that involve retrieving data can now be parallelized. Database sharding refers to a process where the separation of a database into smaller pieces, or shards, distributes it across multiple servers. Each shard operates as an independent database, allowing the system to scale horizontally. This method is particularly useful for relational databases that require high availability and performance. Efficient data processing is essential for transforming raw data into valuable insights. Scalable data processing solutions must handle increasing data volumes and complexity without sacrificing speed or accuracy (Shoetan et al., 2024). Distributed computing frameworks like Apache Hadoop and Apache Spark are designed to scale for data processing. These frameworks distribute data processing tasks across multiple nodes, thus allowing parallel processing. This drastically cuts down the processing time and enables businesses to quickly analyze big chunks of data. Real-time analysis of data demands scalable stream-processing solutions. Tools like Apache Kafka and Apache Flink avail the infrastructure needed to process continuous streams of data in real time (Ediae et al., 2024). These platforms can scale horizontally by adding more processing nodes, ensuring that data is processed promptly as it arrives. Serverless computing, offered by cloud providers like AWS Lambda and Azure Functions, allows businesses to run code without provisioning or managing servers.
Because this model scales automatically with the underlying infrastructure workload, it would work perfectly for situations that have quite unpredictable, or highly variable data processing demands (Gopi et al,. 2022) and (Dogra et al,. 2021). A good data analytics solution should be scaled to support more complex analyses on larger datasets. Scalable analytics tools provide much-needed computational power and flexibility to draw out insights from large volumes of data. In particular, platforms designed for big data analytics (Alex et al,. 2022), (Chesti et al,. 2020) and (Alkinani et al, 2021), including Apache Hive, Apache Impala, and Google BigQuery, support running even complex queries at the level of Peta scale datasets. Applying distributed computing methods enables faster processing in parallel with profound insights possible via tools and platforms from a wide set (Nihar et al., 2023). For example, with machine learning scalability, some other popular options involve Tensor Flow and PyTorch, among those allowing a company to develop models based on big datasets(Alferidah et al, 2020), (Humayun et al,. 2020) and (Srinivasan et al, 2021). These platforms support both distributed training and inference, whereby SMEs have the ability to leverage advanced analytics and predictive modeling at scale. BI analytics tools such as Tableau, Power BI, and Looker include scalable analytics capabilities. Integrations with diverse data sources can be done(Humayun et al,. 2023), (Mughal et al,. 2024), along with complex data visualization and reporting within these tools. They are planned for large volumes of data that support interactive exploratory data analytics; hence they are suitable for agile and growing businesses (Konatham et al,. 2024).
3. Materials and Methods
Physical Layout:
First, the ground floor of the building represents one operational center where, besides core IT infrastructure, important supportive administration can take place. Here, there exist many functional areas in an intricately crafted space.
First Floor:
The first operational level contains essential server rooms and important working zones relating to IT. It includes:
Server Room: Incorporates four servers: Server 1, Server 2, Server 3, and another unnamed server and is the central component of the organization’s IT structure.
Admin Room: Ideal for administrative work and small conferences and for this it requires one server, one printer and a conference table.
Staff Room: Equipped with 10 chairs and table for workers and it can employ a sizable number of employees within the firm.
IT Department: It has a collection of furniture such as three chairs, a 3-seater sofa, a six-seater round table, a wireless connector as well as a printer which makes Information Technology collaborative work possible.
Reception: Has direct communication with the first line of clientele and customers
Client Waiting Area: With furniture like 3 sofas, wireless connector and wireless access point to make clients comfortable while waiting.
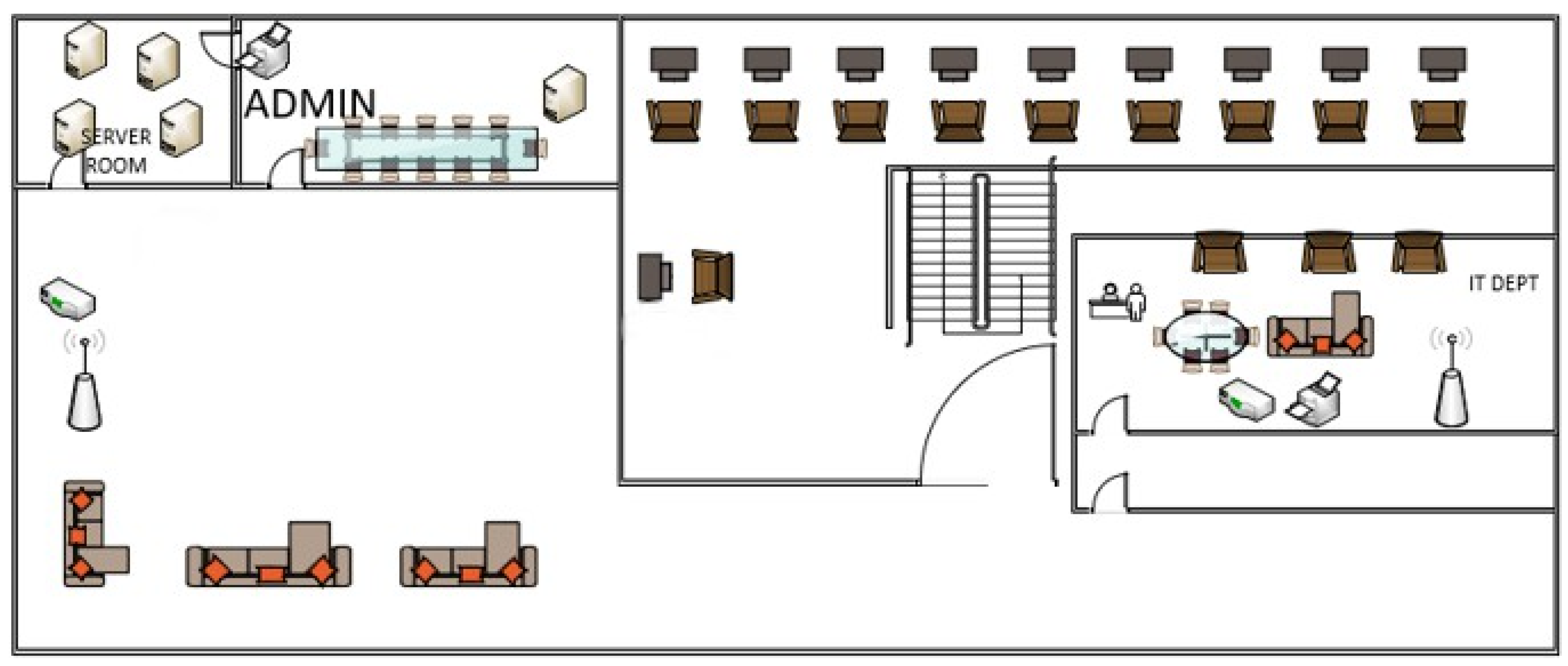
Figure 1 shows the First-floor layout for a medium-sized organization with the following key areas highlighted: the Server Room, hosting the central IT infrastructure on four servers supporting different organizational operations; the Admin Room, located next to it, housing one server, a printer, and a conference table for administrative purposes; and the Staff Room, with individual desks and chairs to sit down and work. The IT Department is designed to be a collaborative environment, equipped with chairs, tables, a wireless connector, and a printer to support group work. The reception is located at the entrance and is the first point of contact for clients, while the Client Waiting Area is equipped with sofas and wireless access points to make visitors comfortable and connected.
Second Floor:
The second floor expands the company's operational capacity with additional office spaces:
Help Desk Room: Has 1 table with 1 chair and 2 sofas probably for interactions that may be IT support related.
Admin Office: Located operating rooms, houses 9 computers and a wireless access point for the administrative workers.
IT Department Room: Furnishes 4 computers, 1 printer, 1 WAP, and 1 WPC that in turn enhances IT firepower.
Conference Room: Has a very large table for a conference also has LCD for the meetings and the presentations.
Client Waiting Area: Has 4 sofas for 3 people each and a wireless connector for the convenience of the clients and integration purposes.
Escalator: It helps people to move across the floors of the building or from one floor to the next.
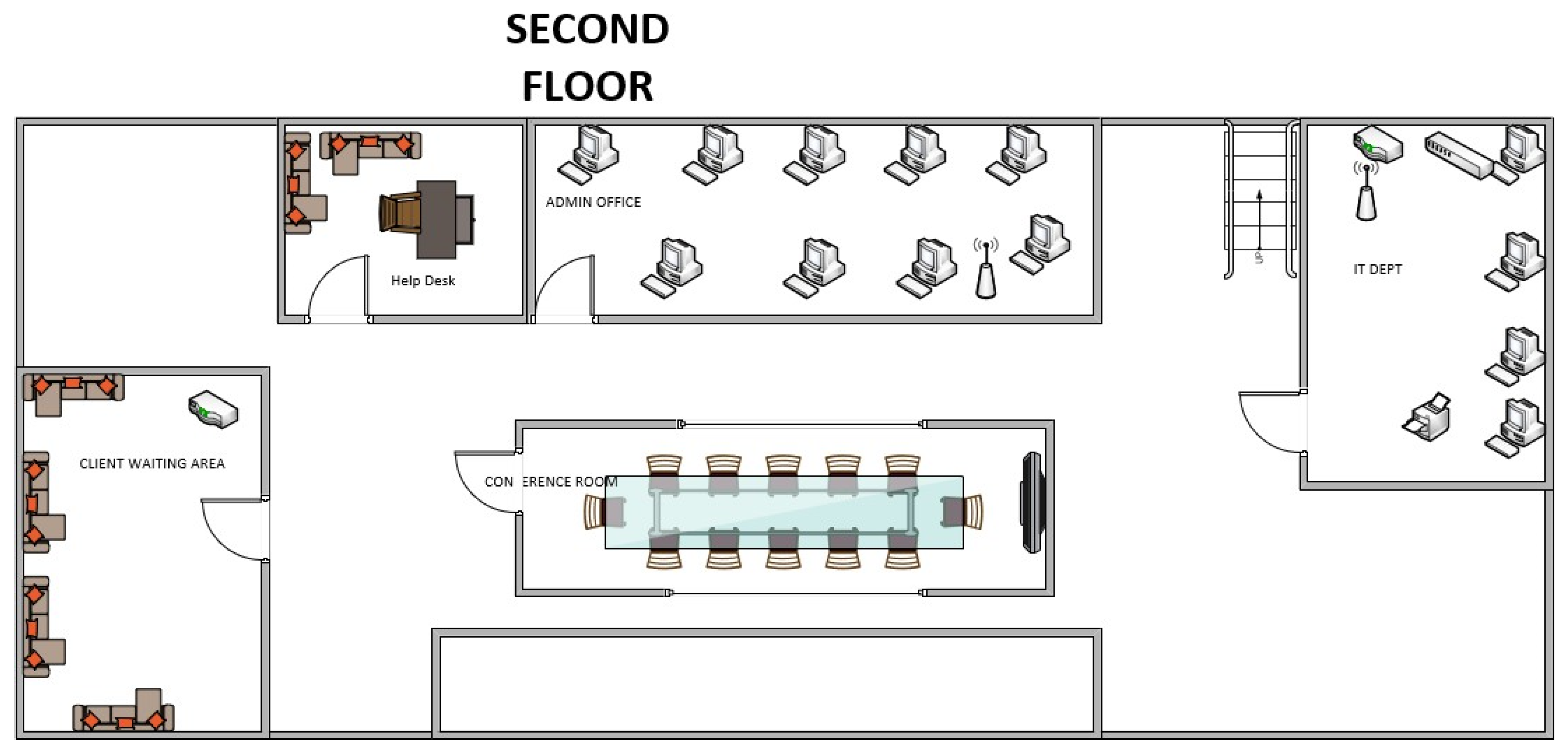
Figure 2 illustrates the Second-Floor Layout supporting a variety of different organizational functions: the Help Desk Room has an installed desk with chair and sofas; the Admin Office - also on this level - has computers, with access by wireless; finally, the room of the IT Department, IT purposes-consisted of computers printers with added Access points. The Conference Room has a large conference table and an LCD screen, which is appropriate for meetings. Finally, the Client Waiting Area is like the one on the first floor, with additional seating and wireless connectivity to make visitors comfortable.
Network Infrastructure:
The physical topology that is used to lay down the network is a hierarchical one then a mixture of wired and wireless network is implemented to suit the needs of the company.
- a)
Internet Connectivity:
This building has access to the internet through an Internet Service Provider (ISP) most probably through a fast conduit appropriate for a middle-sized organization.
- b)
Core Network:
In this network, the essence of each branch resides at the local area router AR3 (192. 168. 3. 0), which connects the intranet and the Internet. This router plays a significant role in the routing of traffic from one segment to another as well as the ISP connection.
- c)
Firewall:
Although a Firewall is not depicted in the diagram it is considered that this has been implemented, either as a separate device or a part of the AR3 router. This is critical especially when aiming at safeguarding the internal network from some extrude rents.
- d)
Switching Infrastructure:
The network utilizes multiple switches to create a robust and segmented network:
LSW1: Primary switch for the first floor
LSW4: Possibly a secondary switch for the first floor or a specific department
LSW5: Connects to the server room devices
LSW9: Primary switch for the second floor
LSW10 and LSW11: Additional switches for the second floor, possibly for different departments
- e)
Wireless Infrastructure:
Wireless connectivity is provided through multiple access points:
AP1: Located on the first floor, offering both 2.4GHz (600Mbps) and 5GHz (1300Mbps) connections
Additional access points are presumed on the second floor, though not explicitly shown in the diagram
- f)
Server Infrastructure:
The server room houses multiple servers:
Server1 (192.168.40.1): Likely a primary application or file server
Server2 and Server3: Additional servers for various services or redundancy
An unnamed server, possibly for backup or specific applications
- g)
VLAN Configuration:
The network implements VLANs for traffic segmentation and security:
- h)
IP Addressing Scheme:
The network uses a private IP addressing scheme with multiple subnets:
192.168.1.0/24: Network department first floor
192.168.2.0/24: Second floor general network
192.168.3.0/24: Core router network
192.168.40.0/24: Admin and server network
192.168.42.0/24: Additional subnet, possibly for specific departments or services
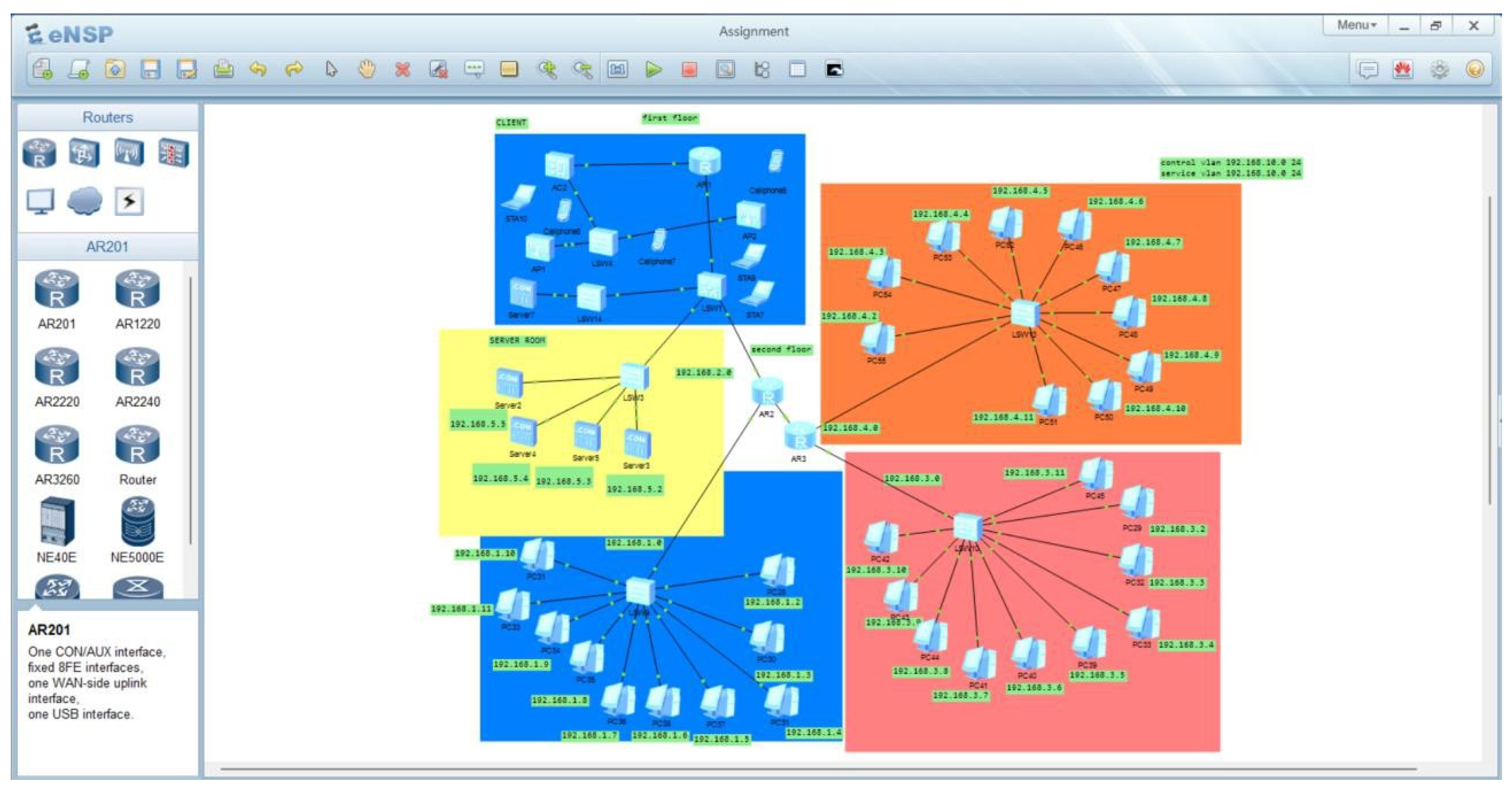
Figure 3 shows the hierarchical network infrastructure. The core network is comprised of an AR3 router acting as a part of the internal and external networking routing. Its switching infrastructure involves several switches, which entail the LSW1, LSW4, LSW5, LSW9, LSW10, and LSW11, which segment and manage network traffic across both floors in the building. The solution will use access points that provide wireless connectivity, ensuring dual-band connectivity at 2.4GHz and 5GHz for both employees and clients. It also focuses on the VLAN configuration to show how the network traffic is segmented for enhanced security and efficiency. The IP addressing scheme also shows the distribution of subnets across different departments and devices within the network.
IP Scheming
The tables below show in detail the IP addressing plan for the network infrastructure. This scheme ensures that there is a logical and efficient use of network resources while considering security and scalability. Below is an explanation of each table. For
Table 1, This table enumerates the wireless devices operating on the first floor, including staff and cell phones. All the devices are configured to acquire their IP addresses dynamically via Access Controller 2. They share the same subnet mask and gateway, which are 255.255.255.0 and 192.168.10.0, respectively, for easy connectivity’s within the first-floor wireless network. For
Table 2, This table outlines the wireless devices on the second floor, including staff and client devices. The IP addresses are also assigned dynamically through AC2, using the same subnet mask and gateway as the first floor, 255.255.255.0 and 192.168.10.0, respectively, for consistency in network configuration between floors.
Table 3, It carries within the same network a subset of PCs having static IP addresses from 192.168.3.2 up to 192.168.3.11 with a subnet mask of 255.255.255.0 and a gateway of 192.168.3.0. This segment, therefore, hosts a certain kind of departmental or operation zone that really relies on such 'dedicated IPs'.
Table 4, The second segment at the second floor uses another IP range, 192.168.1.x. The static IPs of the devices here range from 192.168.1.2 to 192.168.1.11. The subnet mask is 255.255.255.0, and the gateway is 192.168.1.0. Such segmentation is done to facilitate different activities or departments and thus ensure proper isolation and management of traffic.
Table 5, The third segment uses yet another unique range: 192.168.4.x. Static IPs are assigned to devices in the range of 192.168.4.2 to 192.168.4.11, with a subnet mask of 255.255.255.0 and a gateway of 192.168.4.0. This segmentation probably caters to specialized equipment or users who need further isolation or bandwidth management. The network's IP addressing scheme is well-planned, as it follows best practices. Each segment is designed for optimum performance, security, and scalability. The wireless devices get their IP dynamically via AC2, which is easy to administer and flexible. Static IP addressing will be used for wired devices to provide stability and make troubleshooting easier. Subnetting will be in place to logically separate network segments from each other, enhancing security and segmenting traffic between departments or functionalities. This will allow the efficient use of IP resources, manageability of the network, and scalability for any future expansion.
Detailed Network Analysis:
- 1.
First Floor Configuration:
The first floor's network is centered around LSW1, which connects to various devices:
Admin area: PC1 (192. 168. 40. 2) and PC2 are connected, most probably for the administrative employees of the given company.
Server room: Connected via LSW5, which hosts the main servers for the base of operations.
Staff area: Another wired connectivity for the employees is appended as Multiple PCs such as PC7, PC9 and so on connect.
Wireless: AP1 offers a 2. 4 GHZ band and the 5. 0 GHZ band to ensure that the devices in the residence are all covered.
- 2.
Second Floor Configuration:
As for the second floor, the main management of the network is carried out by LSW9, LSW10, and LSW11:
Admin office: LAN connected Pcs (PC28, pc 29, PC30, PC31 etc.) for office related works.
IT Department: PC and printers linked for employees especially the IT team.
Wireless: Though not illustrated, it is understood that access point offers wireless coverage.
- 3.
Inter-floor Connectivity:
The AR3 also plays a very crucial role because it relies on switches on two different floors and regulates the traffic between the two.
- 4.
Wireless Coverage:
The wireless infrastructure is designed to provide comprehensive coverage across both floors:
Smoking is prohibited in any area of the hospital, and there is no smoking areas located within any parts of AP1 on the first floor. The length of the stay is between 2. 4 distributed in a range of 4GHz and 5GHz bands that cater for all devices’ requirements.
As it is, extra access points placed on the second floor are not illustrated, yet they would guarantee coverage.
The dual-band provision boosts speeds which on 5GHz can go up to 1300Mbps for compatible devices while supporting older 2. 4GHz devices
- 5.
Employee Connectivity:
The network design meets the requirement of providing each employee with at least one wired and two wireless connections:
Wired: A local area network connection of Ethernet type is provided at each workstation and in the shared spaces.
Wireless: There is dual band coverage Wi-Fi to guarantee multiple device connection for the employees in the firm without the usual wired connection.
- 6.
Client Areas:
Both floors have different sitting arrangements for the clients waiting to be attended, these areas are equipped with wireless internet connection to enable the clients work while waiting.
- 7.
Scalability:
The application of many switches and VLANs makes adding more nodes into the network quite flexible. More devices or even an organization of a new department can be simply connected to existing switches or new switches can be included to the switch network hierarchy.
- 8.
-
Security Considerations:
VLAN segmentation came into the limelight as organization started adopting networking to powerfully segment separated portions of an organization so as to bring about security.
The art imagined to be situated at the network periphery shields against external threats
Organization of subnets that provide exclusive areas for certain departments (for example, admin, staff, IT) makes the process more detailed concerning access to certain channels.
- 9.
-
Performance:
Gigabit switches (inferred from the network design) guarantee a network bandwidth of gigabit to wired devices.
The feature of the dual-band wireless setup is also usable for attaining the high- speed wireless connection which is vital in the business of the current world.
- 10.
Redundancy:
Although the exact implementation is not clearly outlined, it is evident that there are connections to multiple servers and switches, which means there is some redundancy in the setup for the network and this is highly important in cases where the hardware is faulty.
4. Star Topology Overview:
In a star topology, all the Network devices are connected to a central hub or mediator generally a switch. This central hub is used for data transmission, meaning that it serves to connect the devices in a system. The star topology has a number of advantages, primarily in the case of the given middle-sized company located on two floors.
Justification for Star Topology:
- 1.
Centralized Management:
The main part or core component in star configuration is easy to maintain.
Multiple connected devices can be easily managed from a single point by the Network administrators improving on the authority and supervision.
- 2.
Scalability:
The above-described star topology thus favors easy scalability. Such change as incorporation of new devices or extending the network can simply be done by extending the network of the devices connected to the central hub. This is mainly important in case a growing company may wish to expand the setting to accommodate many employees or devices in the future.
- 3.
Performance Optimization:
The star topology has a single line between the central hub and each device connected to it so there is a very low collision rate. This is especially the case in a business context where quick exchange of data and dependable connection is critical.
- 4.
Fault Isolation:
It is to be noted that a network where a star topology is used, does not collapse in event of a cable or device failure. Other linked devices can be also allowed to communicate with the central hub so that the communication process will not take much’ time and the network can remain stable.
- 5.
Ease of Troubleshooting:
Concentration of connection helps to resolve problems easily. For example, it is much easier to troubleshoot a network at the central point than doing it over and over again at every remote location making it easier to manage the network.
A number of key recommendations have to be implemented for long-term reliability, efficiency, and security of the network infrastructure. First, a robust network monitoring system must be in place to monitor real-time issues and resolve quickly any problems arising. For better online availability, inclusion of hot standby internet connections from alternate ISPs is imperative. Routers, switches, and access points should be updated and patched regularly for better performance and safety. A well-rounded security policy has to be instituted and reviewed at least annually along with continuous employee training in cybersecurity practices. QoS policies should be implemented to give priority to key business traffic. Besides, good documentation of the network layout and IP addressing scheme is crucial for smooth administration and troubleshooting. The IP addressing scheme and switch port allocation should be pre-planned for future expansion to cater to organizational growth. Finally, a highly developed backup and disaster recovery plan will protect key servers and data to make the organization resilient against any potential disruption.
Conclusion
The proposed network infrastructure for this mid-sized company provides a robust foundation for efficient and secure operations. Designed to support at least 20 employees across two floors, the network integrates both wired and wireless connections to ensure seamless connectivity for diverse organizational activities. It will enhance performance by segmenting the traffic further with the use of VLANs and hierarchical design and create a foundation for scalability when future expansion in the company introduces more network demand. It has to be a hybrid system to allow the networking of computers via wires or wirelessly, depending on requirements and specific employee and customer needs. This will really give a strong turn in regard to its reliability, safety, and better management by being on track with the recommendations such as a tough network monitoring system, non-interrupted internet through duplicate links by ISPs, constant updating and patching, proper documentation, etc. This includes implementing QoS policies to give priority to business-critical traffic, developing a holistic security policy that is regularly reviewed and educated to employees, and providing for future scalability in terms of IP addressing and switch port allocation. Lastly, a solid backup and disaster recovery strategy will ensure the protection of critical data and systems for operational continuity in the face of unexpected challenges. With these measures in place, the network will be a cornerstone for the company's operational success and long-term growth.
References
- Forouzan, B. A. (2012). Data Communications and Networking. McGraw-Hill Education.
- Jordão, R. V. D., & Novas, J. C. (2024). Information and knowledge management, intellectual capital, and sustainable growth in networked small and medium enterprises. Journal of the Knowledge Economy, 15(1), 563-595. [CrossRef]
- Valeri, M., & Baggio, R. (2021). Italian tourism intermediaries: A social network analysis exploration. Current Issues in Tourism, 24(9), 1270-1283. [CrossRef]
- Moisio, T. (2022). Capacity planning in network architecture: Strategies for sustainable growth. Network Design Journal.
- HP Networking. (2022). Unified network solutions for mobility and BYOD policies. HP Networking White Paper.
- ComScore. (2022). Modern IT infrastructure for mid-sized businesses: Building scalable solutions. ComScore Insights.
- AIMMS. (2022). Case studies in strategic network planning for supply chain optimization. AIMMS White Paper.
- Meter.com. (2022). Custom network design for corporate and retail environments. Meter Blog.
- Opex Analytics. (2022). Network design in mergers and acquisitions: Ensuring seamless integration. Opex Analytics Reports.
- Lex Technology. (2024). Network design basics for small and medium-sized businesses. Lex Technology White Paper.
- Jejeniwa, T.O., Mhlongo, N.Z., & Jejeniwa, T.O. (2024). A comprehensive review of the impact of artificial intelligence on modern accounting practices and financial reporting. Computer Science & IT Research Journal, 5(4), 1031-1047. [CrossRef]
- Roux, M., Chowdhury, S., Kumar Dey, P., Vann Yaroson, E., Pereira, V., & Abadie, A. (2023). Small and medium-sized enterprises as technology innovation intermediaries in sustainable business ecosystem: interplay between AI adoption, low carbon management and resilience. Annals of Operations Research, 1-50.
- Ediae, A.A., Chikwe, C.F., & Kuteesa, K.N. (2024). Empowering youth through sexuality and leadership education: Approaches and outcomes. World Journal of Advanced Research and Reviews, 22(1), 1250-1265.
- Adenekan, O.A., Ezeigweneme, C., & Chukwurah, E.G. (2024). Driving innovation in energy and telecommunications: next-generation energy storage and 5G technology for enhanced connectivity and energy solutions. International Journal of Management & Entrepreneurship Research, 6(5), 1581-1597. [CrossRef]
- Joel O. T., & Oguanobi V. U. (2024). Data-driven strategies for business expansion: Utilizing predictive analytics for enhanced profitability and opportunity identification. International Journal of Frontiers inEngineering and Technology Research, 2024, 06(02), 071–081. [CrossRef]
- Kaushik, P., Rao, A.M., Singh, D.P., Vashisht, S., & Gupta, S. (2021, November). Cloud computing and comparison based on service and performance between Amazon AWS, Microsoft Azure, and Google Cloud. In 2021 International Conference on Technological Advancements and Innovations (ICTAI) (pp. 268-273). IEEE.
- Shoetan, P.O., Oyewole, A.T., Okoye, C.C., Ofodile, O.C. (2024). Reviewing the role of big data analytics in financial fraud detection. Finance & Accounting Research Journal, 6(3), 384-394. [CrossRef]
- Nihar, A., Ciardi, T.G., Chawla, R., Akanbi, O., Chaudhary, V., Wu, Y., & French, R.H. (2023, December). Accelerating time to science using CRADLE: a framework for materials data science. In 2023 IEEE 30th International Conference on High Performance Computing, Data, and Analytics (HiPC) (pp. 234-245). IEEE.
- Gopi, R., Sathiyamoorthi, V., Selvakumar, S., Manikandan, R., Chatterjee, P., Jhanjhi, N. Z., & Luhach, A. K. (2022). Enhanced method of ANN based model for detection of DDoS attacks on multimedia internet of things. Multimedia Tools and Applications, 1-19.
- Dogra, V., Singh, A., Verma, S., Kavita, Jhanjhi, N.Z., Talib, M.N. (2021). Analyzing DistilBERT for Sentiment Classification of Banking Financial News. In: Peng, SL., Hsieh, SY., Gopalakrishnan, S., Duraisamy, B. (eds) Intelligent Computing and Innovation on Data Science. Lecture Notes in Networks and Systems, vol 248. Springer, Singapore. [CrossRef]
- Alex, S. A., Jhanjhi, N. Z., Humayun, M., Ibrahim, A. O., & Abulfaraj, A. W. (2022). Deep LSTM model for diabetes prediction with class balancing by SMOTE. Electronics, 11(17), 2737. [CrossRef]
- Chesti, I. A., Humayun, M., Sama, N. U., & Jhanjhi, N. Z. (2020, October). Evolution, mitigation, and prevention of ransomware. In 2020 2nd International Conference on Computer and Information Sciences (ICCIS) (pp. 1-6). IEEE.
- Alkinani, M. H., Almazroi, A. A., Jhanjhi, N. Z., & Khan, N. A. (2021). 5G and IoT based reporting and accident detection (RAD) system to deliver first aid box using unmanned aerial vehicle. Sensors, 21(20), 6905. [CrossRef]
- Alferidah, D. K., & Jhanjhi, N. Z. (2020, October). Cybersecurity impact over bigdata and iot growth. In 2020 International Conference on Computational Intelligence (ICCI) (pp. 103-108). IEEE.
- Humayun, M., Jhanjhi, N. Z., Hamid, B., & Ahmed, G. (2020). Emerging smart logistics and transportation using IoT and blockchain. IEEE Internet of Things Magazine, 3(2), 58-62. [CrossRef]
- Srinivasan, K., Garg, L., Chen, B. Y., Alaboudi, A. A., Jhanjhi, N. Z., Chang, C. T., ... & Deepa, N. (2021). Expert System for Stable Power Generation Prediction in Microbial Fuel Cell. Intelligent Automation & Soft Computing, 30(1).
- Humayun, M., Niazi, M., Jhanjhi, N. Z., Mahmood, S., & Alshayeb, M. (2023). Toward a readiness model for secure software coding. Software: Practice and Experience, 53(4), 1013-1035. [CrossRef]
- Mughal, M. A., Ullah, A., Cheema, M. A. Z., Yu, X., & Jhanjhi, N. Z. (2024). An intelligent channel assignment algorithm for cognitive radio networks using a tree-centric approach in IoT. Alexandria Engineering Journal, 91, 152-160. [CrossRef]
- Konatham, B., Simra, T., Amsaad, F., Ibrahem, M. I., & Jhanjhi, N. Z. (2024). A Secure Hybrid Deep Learning Technique for Anomaly Detection in IIoT Edge Computing. Authorea Preprints.
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).