1. Background
Cloud Computing is a network of resources hosted online that are used by individuals and companies instead of hosted on a local server or computer. There are 3 main models and 4 development patterns in Cloud Computing that are used, the main models being Software as A Service (SaaS), Platform As A Service (PaaS), and Infrastructure As A Service (IaaS), and the development patterns being Public Cloud, Private Cloud, Hybrid Cloud, as well as Multi-Cloud. Cloud Computing has transformed the way data is stored, managed, and accessed and made itself integral to the lives of countless companies and individuals (Ananna et al., 2023). Its use will only grow over the years due to its usefulness in work and entertainment and its flexibility and convenience. As such, companies and individuals need to focus on security technologies related to Cloud Computing and improve it over time.
Over the years there have been many security-related technologies developed for use in Cloud Computing. In this background, we will briefly discuss Identity and Access Management (IAM), Firewalls, Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS). IAM is a set of important tools that control user identities in the workplace and manage their access to the different resources that they have access to. A few examples of IAM are Single Sign-On (SSO), Multi-Factor Authentication (MFA), and Role-Based Access Control (RBAC).
SSO streamlines user access by granting system users access to multiple systems or applications after logging in only one time. This helps to reduce password fatigue in employees or individuals who use SSO because they do not need to remember multiple passwords for multiple accounts. An example of SSO is Google which allows users to access multiple cloud-based systems and applications through one account. MFA creates a more secure environment by requiring multiple forms of authentication to verify a user before letting them access a system or website (Azam, Dulloo, Majeed, Wan, Xin, & Sindiramutty, 2023). An example of MFA would be a website that requires users to type in a password and after the password has been verified, the user will be sent a one-time authentication code through their email or a text message that needs to be typed in to gain full access. There can also be other authentication factors involved such as biometrics like fingerprints or a smart card
(IMI, 2024). RBAC grants permissions to users based on their role in the company. For example, the access, reading, writing and sharing of files can be determined by the role an employee has. It applies to other sectors of a job too, like finances as only employees with the right role can make transactions
www.okta.com (2024).
Secondly, are Firewalls. Firewalls are network security devices that are designed to monitor and filter through incoming and outgoing network traffic based on preset rules to prevent unauthorised access to resources and applications. There are also Next-Generation Firewalls that have all the functionalities of regular firewalls but also have additional features such as Packet Filtering to inspect individual packets of data to block malicious ones, Stateful Inspection to make sure that packets are part of legitimate networks, and VPN Awareness so that they can identify encrypted traffic from Virtual Private Networks (VPN) and allow it (Cloudflare, 2024).
Third, are Intrusion Detection Systems (IDS) and Intrusion Prevention System (IPS). Intrusion Detection Systems and Intrusion Prevention Systems are systems that monitor the traffic of a cloud’s network for malicious activity. An IDS does not take any active steps to halt that malicious activity if detected, it merely alerts administrators and security teams. An IPS however, is a more advanced version of an IDS that actively prevents threats and malicious activity by blocking malicious traffic, terminating malicious content, or adjusting firewall rules to prevent threats (Azam, Dulloo, Majeed, Wan, Xin, Tajwar, et al., 2023). Both systems share some threat detection methods, such as Signature-Based Detection which is done by analysing network packets for unique characteristics that only appear in malware and Anomaly-Based Detection which is done by using Artificial Intelligence and Machine Learning to create and refine a model of regular network activity over time to use as a baseline. The systems then compare ongoing network activity to the baseline model and respond when deviations occur. (IBM, 2023).
If security is not well maintained or upgraded when it comes to Cloud Computing, the consequences can be devastating. Unfortunately, many companies do not prioritise security for their Cloud Computing. A recent report showed that in 2022, 92% of companies faced security incidents related to APIs which are a core component of Cloud Computing (Keary, 2023). Another consequence that could happen if security technology isn’t maintained is data breaches. In 2023, 80% of data breaches occurred because of data that was stored in the cloud which made it a vulnerable target (SentinelOne, 2024; Azam, Tajwar, Mayhialagan, Davis, Yik, Ali, et al., 2023). Lastly, there are Distributed Denial of Service (DDoS) attacks which are done by flooding cloud services with traffic. This deluge of traffic overwhelms cloud applications (Mughal et al., 2024) and websites and renders them unusable for some time because the cloud service cannot keep up with the traffic (Basan, 2024). A simple DDoS attack can be prevented by maintaining essential security infrastructure like Firewalls and IPS.
2. Discussions on How Cloud Computing Security Works
2.1. Component
Cloud computing is an infrastructure that allows users to connect to cloud services via the internet and to use networking technologies to share resources across multiple users. The users then only need to pay for what they use, rather than investing lots of money to make and maintain physical servers or storage devices. This allows small organisations to be able to store and share resources amongst their devices with lesser costs. For IaaS, it will provide virtual computing resources over the internet. Components such as Virtual Machines, storage, and networking. The users can have the flexibility to configure and manage their operating systems and applications but are unable to manage the physical infrastructure. Next, PaaS offers a platform which allows the developer to build, run, and manage the application only. It provides an environment with tools and services, such as databases, middleware, and development frameworks, to aid in application development. Lastly, SaaS can deliver fully managed applications to users using the web browser. The service provider handles everything, from the infrastructure to the applications, and users only need an internet connection to access it.
Even though this brings much convenience and advantages to people utilising the service, it also has its flaws. For example, the data privacy and security of the data. Hosting data off-premises has always raised a lot of concerns among users about data ownership and compliance with privacy laws. The users that utilise this service may be sceptical about the choice of the company they acquire the service from as data security may be at risk if the cloud security is not managed properly. In addition to that, downtime and dependence on Internet connectivity may also be an issue while utilising cloud services as they are very dependent on Internet connectivity, meaning that any interruptions in the service could impact productivity, cause potential data losses, and restrict access to the service (Konatham et al., 2024). Due to the instability and the unpredictability of data security, different regions have different data protection laws, which can complicate storing sensitive data in global data centres.
Now let’s talk about the components of cloud computing security. Cloud computing security itself is the set of policies, and latest technology advancements that are designed to protect any sensitive data present in all the applications, and infrastructure of the cloud computing environments of an organisation. Ensuring that all three contents of the [CIA] confidentiality, integrity, and availability of all of the data stored in the cloud. The security measures (Shah et al,. 2024) can be applied from all parts of the infrastructure, including perspectives from the vendor and the user’s point-of-view.
First, Identification and Access Management, also well known as IAM. It is a crucial component for ensuring cloud computing security. It enhances accessibility security as it ensures that only authorised users can access cloud resources. This process involves creating unique identities and roles, assigning roles to proper individuals, and then setting permissions to control the access in the system. Usually, multi-factor authentication (MFA) is often implemented together with the IAM to enforce greater security, making sure that the person who is claiming to be an authorised person who has legitimate access to this role is really who they claim they are. MFA achieves this by requiring users to provide two or more verification factors to gain access. Another example of IAM tools also includes the single sign-on (SSO) feature, allowing users to log in with the same set of credentials to access multiple applications (Zaman et al,. 2023) and (Javed et al,. 2023), and federated identity management, which enables users to access resources across different security domains using the same identity (IMI, 2024).
Firewalls are also a commonly used component in cloud computing security. The role of the firewall is to filter any incoming and outgoing traffic based on the predefined security rules that are set by the organisation. This is used to perform an inspection on the packets that are going in and out of the infrastructure, checking if the data packets contain any common signs of malware, mitigating the risk of infrastructure being vulnerable. Common tools used alongside the firewall are intrusion detection systems (IDS) and intrusion prevention systems (IPS) which are used to detect and block any potential threats which may pose a threat to the system. To a certain extent, Virtual Private Networks are also used by organisations when lots of sensitive data are being used and transmitted across the network, VPN makes sure that all information that is being transmitted across the channel is impossible to intercept by any unauthorised users. Additionally, network segmentation is also employed to divide the network into smaller, isolated segments, limiting the spread of potential attacks (Dawood et al., 2023; Azam, Tan, Pin, Syahmi, Qian, Jingyan, et al., 2023).
Diving in further for the security of data, it aims to focus on protecting the data that is actively being transmitted through the network while also protecting the data at rest. To do this, encryption is one of the crucial techniques that must be used, ensuring that data is unreadable and can be classified as useless to unauthorised users but only making it readable to the authorised receiver. To do this, it uses private and public keys to perform encryption so messages can only be readable by the target receiver by using the private and public key pair. Data masking can also be used to hide sensitive information (Humayun et al,. 2023), replacing it with fictional data that retains the general characteristics of the original data without exposing sensitive details (Khader and Karam, 2023). To further aid in data security, data loss prevention (DLP) tools can be used to help monitor and control the flow of data, preventing unauthorised access and transfer of sensitive information (Domnik, J. and Holland, A., 2024; Hussain et al., 2024). Lastly, it is also highly advisable to perform regular backups periodically so we can decrease the severity of the attack such as any data loss or data corruption.
Antivirus software is also an important component of cloud computing as it aims to detect and remove malware which may pose a significant threat to the devices that are connected to the cloud. For example, we can use the “Endpoint Detection and Response system” to constantly monitor our devices for any indications of suspicious activities on our device. Mobile device management solutions can also be used to enforce better security policies on our devices to mitigate the chances of being vulnerable to attacks. And to take additional precautions for our devices, good habits on keeping on track with the newest patch management would be excellent as it helps us ensure that all devices are using the newest up-to-date security software to ensure that all data contained in the devices can be secured from the unwanted view (Dissanayake et al., 2021; Jun et al., 2024).
Besides online security, cloud providers also focus on physical security measures to protect data centres and the underlying infrastructure. For example, having restricted access to major data points by using passcodes, biometrics, and video surveillance, and also having its audit lot to be able to recheck the history of activities (Gair et al, 2022). In addition to this, backup and disaster recovery models should be properly set up. Multi-regional data replication enables efficient recovery of data during attacks, ensuring the data is protected from physical and online disasters (Cloudsecurityalliance.org, 2024; Manchuri et al., 2024).
2.2. Process
Cloud computing security has many combinations of processes that are important for protecting sensitive data and information in cloud computing. This security framework includes a comprehensive set of methods, technologies, and practices designed to protect the stored data and processes in cloud computing. The cloud environments are shared and most of the time managed by a third-party provider. Security measures are important to focus on the various critical concerns, including data privacy, access control, and regulatory compliance (Dawood, M. et al, 2023). As more organisations transition their operations to cloud computing, it becomes necessary to have reliable security mechanisms. When the organisation shifts to cloud computing it aims to mitigate risks associated with cyber threats, unauthorised access, and potential data breaches (Alouffi, B., Hasnain, M., Alharbi, A., Alosaimi, W., Alyami, H. and Ayaz, M. 2021; Ravichandran et al., 2024). Effective cloud security enables both service providers and users to achieve the confidentiality, integrity, and availability of their services, and to have a secure operational framework that supports modern cloud computing.
First, one important process for cloud security will be data protection, for example, encryption in securing data during transmission and storage. By using encryption techniques, even if unauthorised access occurs, the organisations still have confidence that the data remains unreadable, and they are protected from misuse. Other protective measures, like tokenization and data masking, are also used to protect sensitive information. Tokenization replaces sensitive data elements with unique identifiers or tokens, while data masking obscures some values to minimise their exposures. These two techniques improve data security by reducing the risk of unauthorised access, ensuring that sensitive information remains protected even in the accident of a data breach (Sun, P.J. 2019; Seng et al., 2024).
Access management is another potential process of cloud security. Identity and Access Management known as IAM systems limit access to resources, ensuring that only the authorised users can interact with sensitive data and applications. Implementing Multi-Factor Authentication, and MFA adds a layer of security, making unauthorised access more difficult for them (Josic, D., Basic, M. and Zgrablic, L. 2024; Sindiramutty et al., 2024). Besides, Role-Based Access Control ensures users have access only to the necessary data for their roles. This simplification of access management not only protects sensitive data but also reduces the risk of data exposure by limiting user permissions (Mythili, K. and Rajalakshmi, S. 2022).
Network security measures are also important to protect cloud environments from attacks. Cloud service providers implement advanced and modern firewalls to control network traffic and protect against attacks such as DDoS that might disrupt operations. Furthermore, Intrusion Detection and Prevention Systems, IDPS will continuously monitor the traffic, protect against the potential attacks and allow fast responses to detected threats (Srilatha, D. and Thillaiarasu, N. 2023).
Security of applications in cloud security emphasises safe coding practices throughout the software development lifecycle. Regular security testing helps identify and fix vulnerabilities. The role of APIs in cloud communication, and reliable authentication are important to prevent unauthorised access, to protect information and service continuity (Sun, P.J. 2019; Sindiramutty, Jhanjhi, Tan, Khan, Shah, & Manchuri, 2024).
Compliance and audits are important for industries which deal with specific regulations, such as healthcare under HIPAA or data privacy under GDPR. For organisations to meet these regulatory requirements, cloud providers may work on certifications and conduct regular audits to tackle potential vulnerabilities. Compliance not only reduces the risk of regulatory violations and financial penalties, but it also helps the stakeholders to trust in the organisation’s commitment to data protection (IEEE Digital Privacy 2023; Sindiramutty, Jhanjhi, Tan, Khan, Shah, Yun, et al., 2024).
For monitoring and threat detection processes, we can have Security Information and Event Management systems that compile and analyse data to initiate threat detection and quick responses. Cloud providers often use AI to enhance their intelligence over threats, detecting and addressing potential threats in real time. This integration of AI improves the overall security of cloud computing, enhancing defence against evolving cyber threats (Rosenberg, M. et al. 2024; Sindiramutty et al., 2024).
Finally, the shared responsibility model in cloud security defines the division of responsibilities between cloud service providers and customers. While providers secure the underlying infrastructure, customers are responsible for securing their data, applications, and access controls. This collaborative model promotes a culture of shared accountability and awareness, allowing organisations to significantly improve their security posture and better protect their cloud-based assets (RiskRecon 2023; Sindiramutty, Tan, Shah, et al., 2024).
In conclusion, the processes of cloud computing security form a multifaceted framework important for protecting sensitive data and maintaining operational integrity in cloud environments. As more organisations transition to the cloud, robust security measures become crucial in addressing the unique challenges associated with third-party managed infrastructures. Key security practices such as data protection through encryption, access control via IAM systems, and network safeguards like firewalls and IDPS—are important for preventing unauthorised access and cyber threats. Adherence to regulatory compliance and regular security audits reinforce trust and minimise legal risks for industries with strict data protection standards. Advanced monitoring and AI-enhanced threat detection systems further strengthen cloud security, allowing for real-time response to evolving cyber threats. The shared responsibility model in cloud security highlights the need for both cloud providers and users to collaborate, ensuring a resilient defence framework. This approach supports confidentiality, integrity, and availability, empowering organisations to better apply the advantages of cloud computing.
2.3. Threat
Cloud computing is still confronting several security threats caused by its vulnerabilities. Many well-known and common cloud computing threats, such as malware injection, denial of service, account hijacking, data breaches, unsecured interfaces, multi-tenancy, and malevolent insiders, will be briefly explained in this study. A few hazards remain unmentioned in this study, including inadequate access control, Advanced Persistent hazards (APTs), cloud service misuse, and more (Kumar and Goyal, 2019; Sindiramutty, Tan, & Wei, 2024). This study solely does not focus on addressing such concerns, which does not mean they aren't essential.
2.3.1. Malware injection
Malware attacks are a common type of attack and one of the biggest problems for cloud computing. Malware injections, which can serve as SaaS on cloud servers, are executed by running embedded code in cloud services (Ahmad et al., 2021; Waheed et al., 2024), whether it is embedded into software or by executing remote commands onto a computer to access or alter a database or website (Hong et al., 2019). Additionally, the operator's data, which is handled and kept on the cloud, is accessed through Cloud malware injection attacks (CMIAs), a sort of cybercrime particular to cloud computing (Ahanger and Aljumah, 2020). These types of attacks occur because of cloud service providers that are susceptible.
2.3.2. Denial of Service
In a Denial of Service (DoS) or distributed Denial of Service (DDoS) assault, a hacker overwhelms the network with packets that generate unnecessary traffic. This could trigger the intended cloud service to require more system resources than are allotted, which will hinder registered individuals from obtaining their data and apps because of sluggish response times or unavailable cloud resources (Kumar and Goyal, 2019; Wen et al., 2023). Improper programs, a hazardous network protocol, a failing network protection architecture, etc., will all contribute to this hazard (Ahanger and Aljumah, 2020). In addition, the inadequate supply problem of insufficient bandwidth is causing DoS assaults on virtual machines (Parast et al., 2021). To avoid this threat, it is recommended that cloud computing adopt load balancing, robust firewalls, traffic monitoring and filtering, and IPS deployment (Ahmad et al., 2021).
2.3.3. Account or Session Hijacking
Hijacking is the illegal takeover of specific permitted services by unauthorized users. This technique involves an adversary remaining in a TCP/IP conversation to steal a user's credentials, or sessions as well (Parast et al., 2021). Weak credentials and insufficient permission validations are frequently used as reasons for an account or service hijacking, and this threat can be performed from either layer (Parast et al., 2021). As a result, this gives the adversary entrance to the user's assets and enables them to steal, modify, remove or sell the user’s sensitive information and identification (Ahmad et al., 2021). Consequently, the credibility of the business would be damaged, and they might incur significant expenses. There will be legal repercussions for sectors like healthcare that prioritize user data confidentiality. These could be addressed with the use of privacy policies, two-factor authentication, and reliable encryption over the exchange of information while travelling (Díaz de León Guillén, 2020).
2.3.4. multi-tenancy
Multi-tenancy refers to the environment that cloud deployment models deliver, which allows numerous customers to share computing resources like hardware, software, services, or data while maintaining the security and segregation of their data (Ahmad et al., 2021). This operating approach may expose consumers to security issues like information leakage because many different people may be using the same piece of hardware or software simultaneously (Parast et al., 2021). Furthermore, exploitation might have occurred if an attacker had gotten hold of co-located services and hosts (Kumar and Goyal, 2019; Alex et al., 2022). This approach should guarantee the confidentiality and safety of data by offering user separation at the hardware resource and application phases, as well as system scalability and metered consumption (Kumar and Goyal, 2019).
2.3.5. Data breach
In cloud computing, a significant proportion of client data is kept in a cloud environment and is extremely precious. Data breaches pose severe threats to cloud computing because they expose confidential and delicate information to unintentional exposure. Deliberate malevolent assaults, errors by humans, cloud application weaknesses, and inadequacies in security rules in detecting threats and vulnerability minimizing are some of the many reasons for data breaches (Ahanger and Aljumah, 2020). The degree of harm caused by data breaches, which can result in monetary losses, public image damages, and other negative effects, could be evaluated based on the severity of the compromised data (Ahmadi, 2024; Alferidah & Jhanjhi, 2020). Encryption of data, digital signatures and fragmentation redundancy-scattering (FRS) are crucial methods for decreasing risk (Parast et al., 2021). Regulations and procedures for data privacy must be implemented, together with access control regulations to avoid unauthorized users (Ahmad et al., 2021).
2.3.6. Insecure APIs
APIs, virtual machines, and software interfaces play a major role in cloud computing by enabling smooth integration as well as compatibility across various platforms and services (Yanamala et al, 2024; Ahanger and Aljumah, 2020). Security issues like unauthorised authentication, encryption violations, and erroneous access controls will result from insecure APIs and interfaces (Ahanger and Aljumah, 2020; Alkinani et al., 2021). The technical causes of insecure APIs include weak API information, key management problems, operating system issues, unpatched applications, and hypervisor issues (Ahanger and Aljumah, 2020). An API is used to give users a connection to cloud services. To ensure that the content being transmitted is always confidential, CSP should make use of appropriate authorization and authentication protocols in addition to timely patching interfaces (Parast et al., 2021).
2.3.7. Malicious Insider
A malicious insider is an individual who has permitted access to an IT system, whether they are a current or previous worker or a shareholder. They purposefully abused their powers to interfere with the reliability of the system, which might have disastrous consequences because the attacks originate internally. Since they will be regarded as daily access, no alarm will be set off until the attacks occur, thus rendering them difficult to identify and prevent (Ahmad et al., 2021). Malicious insiders may arise as an aftermath of inadequate monitoring, poor management of private entry points, and an absence of cloud guidelines (Ahmad et al., 2021; Babbar et al., 2021).
2.4. Example Security-Related Technology
Cloud computing service providers implement a variety of industry-standard security measures to ensure that data is protected. Many cloud computing services provider offers optional features such as multi-factor authentication (MFA), which ensures that users desire to undergo multiple layers of verification before identity access is granted, the result of reinforcing the security of the login process and ensuring that only authenticated personnel and devices can access the cloud services (msmbaldwin, 2024; Brohi et al., 2020). Microsoft Entra ID plays an important role within Microsoft as a cloud identity management system that implements strong and enhanced security protocols for Microsoft Azure cloud computing services. Microsoft's verification security measures include the Microsoft Authenticator app, FIDO2 Security Keys, and Voice Key authentication. For example, the Microsoft Authenticator application promotes security by sending users a push notification to approve a sign-in attempt which generates a one-time code on the user’s phone, which must be entered into the computer or other devices during login to verify their identity (Justinha, 2024; Chesti et al., 2020). Other than Microsoft Azure, AWS Identity and Access Management (IAM) authentication plays a vital role in supporting users with the ability to apply MFA on their AWS cloud computing account to provide an extra security layer that secures their data resources (Talluri and Teja Makani, 2023).
Data protection is the key security which is highlighted in cloud computing. To safeguard the data, data encryption needs to be applied both during the transmission through the network or being stored. For example, Amazon Web Services (AWS) works as a famous cloud computing service provider, employing robust encryption mechanisms as their security. AWS emphasises the encryption of data rest and provides server-side encryption and client-side encryption to ensure security. For Server-side encryption, AWS provides multiple options, including Amazon S3 managed keys (SSE-S3), where data is automatically encrypted using 256-bit Advanced Encryption Standard (AES-256) algorithms (Amazon.com, 2024). Other server-side encryption (SSE) options include SSE-KMS and SSE-C, each of which provides a different level of encryption key control. With SSE-KMS (Server-Side Encryption with AWS Key Management Services), AWS KMS automatically generates and manages the encryption keys used to secure data in S3 storage buckets. Besides, SSE-C (server-side encryption using customer-supplied keys) provides clients with the ability to complete control over encryption and decryption keys themselves. In this particular model, the user is responsible for managing their keys, and AWS S3 handles the encryption process as objects and uploads them to the destination bucket (Purna et al., n.d.). For Client-side encryption, Users are available have control of the entire encryption process and can manage the encryption keys independently. Before uploading data to the AWS S3 bucket, they encrypt it locally, ensuring that only they have access to the encryption key (Amazon.com, 2024).
To ensure the security of the data in transit on the network, AWS applies AWS Web Application Firewall (AWS WAF) to monitor the HTTP/HTTPS request passing through the Amazon gateway, AWS WAF helps block malicious traffic, such as SQL injection (docs.aws.amazon.com, n.d.). AWS integrated with AWS Shield to cater for the activities of Distributed Denial of services (DDoS), it has a standard version that is automatically complementary to all AWS cloud users and the advanced version will offer enhanced features to encounter professional DDoS attacks. The AWS shield protects AWS resources from DDoS attacks at both the Network Layer (OSI layer 3) and Transport Layer (OSI layer 4) and includes the Application Layer (OSI layer 7) (Routavaara, 2020). AWS Shield detection successfully reduces threats involving attacks directly through the critical system, ensuring the security and consistent availability of the AWS system.
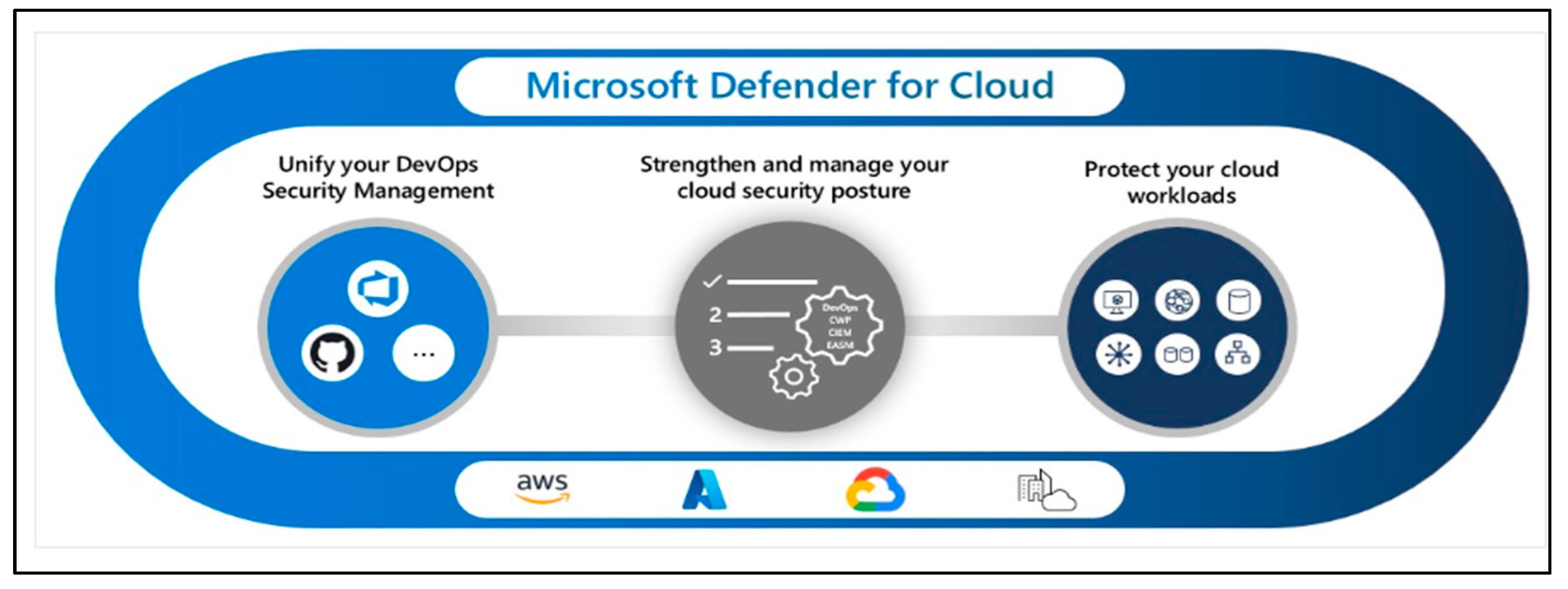
Besides, Microsoft Defender for Azure cloud computing is a cloud-native application protection platform (CNAPP) that proposes to safeguard the cloud computing services applicable to confront various types of threats (
Microsoft, n.d; Dogra et al., 2021
). Defender for Cloud-enabled cloud services security teams to manage development and operation security across multi-pipeline environments (Microsoft, n.d.). The architecture of the Cloud Defender of cloud computing services (AWS, Azure, Google Cloud) is briefly illustrated in
Figure 1.
Implementing Threat Detection and Security Monitoring features is essential in cloud computing environments to further improve security. For instance, Amazon GuardDuty can assist in identifying unexpected and potentially unauthorised or malicious activity in users’ AWS environment and disclose the potential threats to cloud computing (Moitrayee Chatterjee et al., 2020; Fatima-Tuz-Zahra et al., 2020). In this layer, GuardDuty cooperates with CloudWatch to perform threat detection functions in the cloud environment to provide continuous monitoring of incoming threats (Tan, 2023). AWS GuardDuty offers free foundational threat detection to act on monitoring specific data sources and event logs such as AWS CloudTrail management events, and DNS logs. When upgraded to Use-case focused GuardDuty protection plans, It deployed additional threat detection models from other AWS services including EKS audit logs, RDS login activity, and Amazon S3 data events in CloudTrail (Amazon GuardDuty User Guide Amazon GuardDuty, n.d.). With the example above AWS implements advanced, industry-leading standards in Threat Detection and Security Monitoring within its cloud environment.
3. Discussion on the Impact
3.1. Benefits of Cloud Computing Security
Cloud computing security offers many advantages that organisations can use to better protect data, reduce risks, and improve overall security.
The first major advantage is professional security technical support. Most cloud service providers have dedicated security teams and resources that can monitor security threats in real-time and respond quickly. These service providers usually have deep network security knowledge and technical capabilities and are more capable of responding to security than general organisations (Parast et al., 2021; Gopi et al., 2021). At the same time, advanced automated and intelligent security tools are also considered. The cloud computing environment supports a large number of automated and intelligent security tools that can help detect abnormal activities, block potential threats, and provide timely alerts. For example, automated intrusion detection systems (IDS) and intrusion prevention systems (IPS) can monitor traffic and activities around the clock to quickly identify and respond to threats.
Data redundancy and backup are also one of the major advantages of cloud security. Cloud computing supports multi-regional storage of data and provides highly redundant data backup and disaster recovery options. Through functions such as automatic backup, data mirroring, and cross-regional storage, cloud services can effectively reduce the risk of data loss and ensure rapid data recovery after a security incident (Shirgaonkar et al., 2022; Gouda et al., 2022).
Another major advantage that must be mentioned is the elasticity and scalability of cloud computing platforms, which allow cloud-using companies to easily expand their security resources as security requirements increase. This allows companies to adapt security measures to actual needs without having to reconfigure extensive hardware or software resources (Abdulsalam & Hedabou, 2021).
3.2. Challenges and Limitations of Cloud Computing Security
Security risks in cloud environments differ in both nature and intensity compared to those in traditional IT setups. In cloud systems, resource pooling enables multiple users to share the same resources via multi-tenancy and virtualization. While these technologies support rapid scalability and efficient resource management, they also introduce certain vulnerabilities.
Multi-tenancy, for instance, can lead to risks associated with data visibility and tracking user operations. On-demand self-service functions, typically managed through web-based interfaces, increase the likelihood of unauthorised access compared to traditional infrastructures. Virtualized environments also present unique risks, such as potential malicious interactions between virtual machines (VMs) and the threat of VM escape. Additionally, the interdependence of cloud service models—where SaaS applications are hosted on PaaS, which itself relies on IaaS—creates a cascade of security dependencies. An attacker gaining control over IaaS could compromise PaaS, leading to potential vulnerabilities in SaaS. Therefore, a security breach at any service model layer can expose other layers to risk (Parast et al., 2021; Humayun et al., 2022).
Private cloud models, being designed for single-organisation use, retain many of the same vulnerabilities found in traditional IT environments. However, public, community and hybrid clouds face cloud-specific risks, primarily due to administrative controls managed by various users and third-party entities. The multi-tenant nature, virtualized resources, and shared file systems pose additional challenges. Effective isolation of multiple tenants and their resources demands an elevated level of security.
In the following sections, we will explore the primary security challenges in cloud computing, categorised into
(a) Communication Challenges
(b) Virtual Network Limitations
Some cloud technologies, such as virtualization, impact multiple service models—affecting both IaaS and PaaS layers simultaneously—rather than any one model specifically.
3.2.1. Communication limitations
There are significant limitations in the communication of cloud computing security, which can affect information exchange between cloud-using organisations, the sharing of threat intelligence, and collaborative processing when responding to security incidents.
The first is the legal and compliance issues of information sharing. In different countries and regions, data privacy laws and data protection regulations, such as GDPR, affect information sharing between cloud service providers and customers, especially when sensitive data or customer privacy is involved. This makes cross-border collaboration more complicated because different laws impose restrictions on data transmission and sharing (Sampson & Chowdhury, 2021; Jhanjhi et al., 2021).
Another issue is the lack of standardised communication protocols. Different cloud service providers may use different security protocols and communication frameworks, which may cause customers and service providers to encounter obstacles when sharing security incident data, such as delayed responses (Abdulsalam & Hedabou, 2021; Kumar et al., 2021). There is also insufficient sharing of threat intelligence. Many cloud service providers do not publicly share all relevant data when dealing with security threats. The reasons for doing so may include protecting trade secrets and avoiding potential reputation risks. However, this insufficient information sharing will prevent other customers and partners from quickly grasping the latest security trends and making it difficult to respond to similar security threats promptly.
Communication delays are also a challenge. When a security incident occurs, fast communication is essential. However, the communication response time of cloud service providers may be affected by factors such as service scale and technical support capabilities. This delay may cause the incident to spread and have a more serious impact.
3.2.2. Virtual Network Limitations
In cloud computing systems, communication occurs not only over physical networks but also heavily relies on virtualized networks. These virtual networks, logically built on top of physical infrastructure, enable efficient interaction between virtual machines (VMs) by establishing virtual connections. Through software-based network components—such as virtual bridges, routers, and software-defined network configurations—multiple VMs on the same host can communicate seamlessly, allowing for flexibility and data isolation. However, the adoption of virtualized networks also introduces distinct security challenges.
Firstly, because virtual network traffic is outside the protective scope of physical network defences, traditional security tools like firewalls and intrusion detection systems (IDS) often cannot monitor virtualized network traffic. This limitation makes malicious activities within virtual networks harder to detect and contain (Lim et al., 2019). Standard IDS and intrusion prevention systems rely on identifiable traffic and behaviour patterns to recognize anomalies and detect potential attacks. However, the isolated and dynamic nature of virtual networks impedes these tools from effectively capturing data flows between VMs, reducing their preventive effectiveness. This limitation heightens the risk of successful malicious attacks, posing a notable threat to data security in cloud environments.
Moreover, virtualized networks are commonly shared by multiple VMs, which increases susceptibility to various network-based attacks. For instance, attackers might exploit the shared nature of virtual networks to launch denial-of-service (DoS) attacks, disrupting regular services by consuming network resources. Additionally, virtual network spoofing (such as ARP spoofing) and traffic sniffing are significant concerns. Attackers can extract sensitive data by injecting false data or intercepting network traffic. In cases of malicious sniffing and spoofing, encryption keys and other sensitive information in transit are at high risk of theft, potentially resulting in costly data breaches, especially if the data includes personal or proprietary information.
In conclusion, while virtualized networks enhance the flexibility and scalability of cloud environments, they introduce specific security concerns. Therefore, cloud service providers and users must implement targeted security measures to identify and protect against potential attacks in virtualized networks during cloud environment design and deployment.
3.3. Future Potential of Cloud Computing Security
Cloud computing security has great potential in the future. With the continuous advancement of cloud technology and the increasing number of network threats, I believe that cloud security will continue to evolve and meet new challenges. As for the prediction of its future potential, I will divide it into four parts.
The first is security protection based on artificial intelligence and machine learning: As time goes by, network threat intelligence and hacker attack techniques become more and more complex, and traditional static security protection methods will become increasingly difficult to meet future security needs. AI and ML will become the core of cloud security. This threat detection system that automatically identifies abnormal behaviours, detects potential threats in real-time and responds to attacks promptly can help cloud organisations defend against a series of complex attacks such as APT more intelligently by constantly learning and adapting to new attack patterns (Shirgaonkar et al., 2022; Nayyar et al., 2021).
The second is the research and development of quantum computing security protection. With the rise of quantum computing technology, traditional encryption algorithms will gradually become vulnerable and unable to resist the cracking capabilities of quantum computing. To cope with this potential threat situation, cloud security may develop in the direction of quantum security, using quantum-resistant cryptographic algorithms and protocols to ensure data security in quantum computing environments. In the future, cloud service providers may provide quantum encryption options to enhance the long-term confidentiality of data (Parast et al., 2021; Shah et al., 2022).
Automated threat response and recovery is also a major potential direction. In the future, automated security responses will be more mature, and the response time for security incidents can be reduced by automatically detecting, isolating and processing threats (Sampson & Chowdhury, 2021). The cloud security platform will also realise a fully automated response system, including automatic repair, data recovery and real-time log auditing, making threat management and incident response more efficient and reducing the need for human intervention.
The fourth is the application of smart contracts in security protocols. In the future, perhaps smart contracts can realise automated security protocol execution in cloud computing. This smart contract-based security protocol can enhance the security of data transmission and transactions in the cloud environment, ensure that all parties follow predetermined security standards, and help achieve secure data exchange in a decentralised environment.
4. Discussion on Security Countermeasures
4.1. Security Countermeasure
Cloud computing has revolutionised the way data is preserved, shared, and retrieved (Infopark.in, 2024). However, in addition, it has brought a number of serious security concerns. Therefore, several countermeasures have been implemented against such threats seeking to compromise sensitive data, service integrity, and unauthorised access (Dawood et al., 2023). These are concerning malware injection, data breaches, account hijacking, denial of service, and insecure APIs.
Identity and Access Management (IAM) is undoubtedly an essential component of cloud security. It controls user access and ensures that cloud resources only interact with authorised users or systems. Multi-factor authentication (MFA) is a crucial element of IAM that involves multiple verification factors, and biometric authentication, such as device-based tokens, and passwords, for increased security (Dawood et al., 2023; Sharma et al., 2021). For example, Google Authenticator and hardware-based tokens such as YubiKeys add further levels of security, making it far more difficult for attackers to break in even when only one component is compromised. Single sign-on (SSO) simplifies user access by allowing authentication across numerous services with a single set of credentials, reducing password exhaustion and the risk of vulnerabilities (ElazarK, 2023). This also reduces insider threats and limits the possibility of privileges being misused either accidentally or intentionally.
Encryption is another critical measure to secure data, both in transit and at rest. Symmetric encryption algorithms, like AES-256, ensure high security with the different keys, making data unreadable for unauthorised users. As for data in transit, protocols like Transport Layer Security (TLS) encrypt communications, such as the ones over HTTPS, against interceptors and eavesdroppers (Khader and Karam, 2023; Singhal et al., 2020). At rest, server-side encryption solutions which are provided by cloud providers, for example, AWS Key Management Service (KMS), ensure that even in case physical servers are compromised, data will not be disclosed. Data masking is an enhancement on encryption where actual data is substituted with unreal yet functional look-alikes, especially within unproductive environments where testing or analytics occurs, reducing exposure but not affecting functionality.
Firewalls and Intrusion Detection Systems (IDS) are the essential elements of network traffic monitoring and control. Firewalls block unauthorised access to any network by filtering out incoming and outgoing traffic based on predetermined security rules. Intrusion detection systems, on their part, continuously monitor networks for suspicious activities. Both are quite efficient in identifying and preventing malware injection or distributed denial of service (DDoS) attacks that may cripple cloud systems (Ahanger and Aljumah, 2020).
Regular mechanisms for data backup and recovery go a long way in assuring that business operations remain uninterrupted. The use of regular backups and multi-regional data replication is considered important in building resiliency within an organisation so that restoration can easily be done by the organisation in case of a disaster such as data loss due to either a cyber-attack or system failure (Alouffi et al., 2021).
Zero Trust Architecture (ZTA) introduces a new system in the field of cloud security by eliminating the trusting assumption within a network. Instead, every user, device, or application must be continuously verified and checked before being granted access. This approach uses principles such as micro-segmentation, dividing the network into smaller, isolated zones, and enforcing strict access controls for each. Device health checks apply to organisational security policies requiring updated antivirus software or encrypted storage. Using the least-privilege principle, ZTA confines a user or device to access the minimum possible number of resources. This greatly reduces the potential damage there could be in case of a breach. For instance, even if an attacker can gain access to one part of the network, he cannot move laterally inside to more critical parts thanks to micro-segmentation (Tan, 2023).
Blockchain technology is increasingly being used to enhance security in cloud computing. Its decentralised and fixed nature brings incomparable transparency and accountability. Each transaction or access event is recorded in a blockchain ledger, which cannot be changed or manipulated. Therefore, the integrity of the data is guaranteed, while auditing processes are easier. Furthermore, blockchain-based identity management systems avoid depending on centralised identity providers which reduces risks of credential thefts or tampering. Cryptographic hashing techniques associated with blockchain further extend the verification and integrity of the data stored in the cloud.
4.2. Proposed Countermeasure
Cloud Computing services bring a lot of conveniences and benefits to the users, but security issues are indeed a major criticism of the cloud computing service and this also affects the users’ confidence in using the technology of cloud computing. Therefore, we need to take advanced and dynamic countermeasures to deal with complex and evolving security threats in cloud environments. For example, using artificial intelligence, blockchain and adaptive authentication mechanisms, which have become key countermeasures to reduce risks, and strengthen data protection against insider threats, credential leakage and unauthorised access.
One important aspect is that Artificial Intelligence (AI) plays a key role in the security strategy of cloud security services. It provides tools that are used to analyse large amounts of data at scale, learn from security events and respond to threats in real-time as well as identify the potential vulnerabilities and predict threats before they occur. This is because using AI-driven access control can detect anomalies that human analysts may miss, and this helps to build the cloud environment more robust and less vulnerable to attacks (Oduri, 2019). AI-driven access control provides dynamic security by evaluating user behaviour and background factors such as devices, locations, and login times. By evaluating these variables, AI can identify abnormal patterns and adjust access rights, thereby reducing the risks associated with internal threats and leaked credentials. It is well known that cybercriminals now use advanced technologies including machine learning and automation to attack. Therefore, we need to implement and deploy machine learning models that can continuously monitor and analyse cloud users’ login time and capture their device type and geographic location to establish patterns of normal user behaviour. In this situation, the system under AI-driven control will adjust the access privileges or require additional verification when the system detects unusual activities such as a user accessing sensitive files from an unusual location from the user side to reduce potential security risk. Continuous monitoring and adjusting the access based on real-time behaviour may help to reduce the risk of insider threats and credential compromise significantly. However, AI-driven control cannot completely cover all security vulnerabilities, so if AI-driven access control is combined with traditional security measures, it can more comprehensively deal with diverse threats. (Olabanji et al., 2024).
Another significant point is about the Automated Failover System with Malicious IP record which can improve the elasticity of the cloud services provided by ensuring the cloud service provider remains operational even if an attack happens or facing system failure. The system can block repeated attempts from flagged sources by maintaining the record of malicious IP addresses. These functions ensure that the key service can remain available and secure which may result in minimising the downtime of cloud service and also reduce the risk of distribution of target attack. The implementation of an Automated Failover system is about configuring a server load balancer to the system which functions in detecting the overloads of failures automatically, then it will take action in switching the traffic flow to backup servers in an instant way (Amazon Web Services, 2019). At the same time, through an integrated threat intelligence system, the maintenance and upgrading of the record of malicious IP supports the function of detecting malicious activity. The system will log the offending IP block the IP from re-assessing the service and generate an alert notification to the administrator to ensure a quick response to any unusual pattern (Usman et al., 2021). The implementation of an Automated Failover System with a Malicious IP Record may ensure the cloud service remains accessible for the cloud service users even if the cloud provider side is facing unexpected failures or attacks and prevents repeat access from malicious IPs. The prevention of repeat access from malicious IPs helps to reduce and minimise recurring threats and downtime. The system will ultimately improve service reliability and safety while reducing operational costs associated with extended service interruptions.
Additionally, countermeasures can be used in cloud security also including the Blockchain-based Cloud Security which uses the blockchain decentralised architecture. Decentralised architecture provides secure identity management and ensures data integrity. Decentralised architecture provides secure identity management and ensures data integrity. Blockchain technology strengthens identity verification, reduces the risk of unauthorised access and ensures all modifications to data are fully traceable by a decentralised approach since this technology enables a transparent and tamper-proof record of the action made by users by recording every transaction on an immutable ledger (Velmurugadass et al., 2020). By implementing the Blockchain architecture into cloud security, we can deploy the blockchain-based system within the cloud service environment as a consortium blockchain and grant access to specific stakeholders. It can create an immutable trail of transactions by recording sensitive identity credentials and data on the blockchain. The system can automate access control policies such as only permitting authorised action and receding any data by using smart contracts and the administrator of the cloud system can easily audit these blockchain records to verify the source and legitimacy of all actions. Blockchain-based cloud security makes identity management more secure and decentralised and helps to reduce vulnerabilities associated with centralised systems. Any unauthorised modification is allowed to be immediately traceable since the immutable transaction records enhance data integrity. This transparency provides stronger auditability ensures compliance with the regulatory standard and builds user trust in the security of the cloud environment provided.
Furthermore, applying the Zero Trust Architecture (ZTA) model integrated with AI-driven behavioural analytics into cloud security is also one of the countermeasures used to keep the cloud environment secure and responsive. Insider threats, credential misuse, and unauthorised access are particularly effective when using an advanced Zero Trust Architecture (ZTA) model integrated with AI-driven behavioural analytics (Ahmadi, 2024). This model makes security more adaptive and responsive by dynamically adjusting access permissions based on user behaviour patterns and real-time risk assessments, while continuously verifying identities and identifying anomalies that may indicate potential security threats (Grobler, Gaire and Nepal, 2021). Login frequency, device usage and access location were gathered by the Advance ZTA with AI and Behavioural data to establish a user-specific baseline. The machine learning models analyse data in real-time which the models will learn from normal patterns to detect anomalies (Butt et al., 2020). The system will access permission, prompt for additional authentication or restrict access temporarily when unusual activity is detected. Continuous monitoring and model re-evaluation improve the accuracy of threat detection and response over time. Early detection of insider threats and credential misuse provided by the advanced ZTA approach enhances security through AI-driven behavioural analytics. To create a balanced and user-friendly security environment, the system needs to proactively respond to suspicious behaviour, reducing unauthorised access risk and containing threats quickly to benefit users by providing them with a seamless experience for routine action while security intensifies high-risk activities.
In the same vein, Adaptive Multi-Factor Authentication (MFA), as an integral component of the Zero Trust Architecture (ZTA) model integrated with AI-driven behaviour analytics, adjusts authentication requirements based on the risk level of each access attempt to provide a dynamic, context-sensitive approach to the cloud security. Adaptive MFA strikes a balance between usability and strong security because this countermeasure effectively reduces user friction, while it also improves security in high-risk scenarios by reducing the steps of routine operations and performing stricter verification for sensitive access (Mostafa et al., 2023). To implement adaptive MFA in cloud security, cloud service systems need to adjust the authentication steps based on the risk level of each operation. For example, the low-risk activities only need users to key in the password or one-time code for verification, while when facing a higher-risk action such as users trying to access sensitive data, the system will require the users to go through biometric verification in addition to a password. The combination of machine learning and the system are more effective in tracking the login pattern and aloud adjustment of the security level dynamically to ensure only authorised individuals access critical resources. The implementation of Adaptive MFA prevents unauthorised access to sensitive information and enhances security for high-risk operations through layered authentication. Cloud service users can enjoy a simplified experience for daily tasks with minimal friction while they still benefit under a strong and reliable cloud security framework since this countermeasure reduces the risk of credential compromise and enhances overall the cloud security group without sacrificing usability (Mostafa et al., 2023).
In conclusion, innovative and dynamic solutions are needed to safeguard user trust and data integrity on the cloud, even though cloud computing offers substantial benefits and convenience for users, cloud security is important in cloud service. Therefore, the key strategies to ensure the security environment such as AI-driven access control, Automated Failover Systems, Blockchain-based security, Zero Trust Architecture and Adaptive Multi-Factor Authentication play a vital role in protecting against evolving cyber threats, inside risks and unauthorised access. Cloud service providers can create resilient defence frameworks that address diverse vulnerabilities. Cloud security is critical to prevent data breaches and also increase user confidence in the cloud service provided, thereby ensuring the continued growth and safe adoption of cloud technology.
5. Conclusion
Overall, although cloud computing brings many conveniences to users, security issues remain crucial for maintaining user trust and data protection. Therefore, it’s essential to use advanced security measures to keep cloud environments safe. AI-driven access control can monitor user behaviour dynamically, reducing the risks of internal threats and credential leaks. The automated failover system records malicious IP addresses, ensuring services remain available even if there’s an attack or system failure. Blockchain technology protects identity management and data integrity through decentralisation, providing transparent and unchangeable records that help with compliance and build user trust. The Zero Trust Architecture requires users and devices to go through multiple levels of verification, limiting unauthorised access. Even if an intrusion happens, it prevents attackers from moving freely across the network, reducing the damage. Adaptive Multi-Factor Authentication (MFA) adjusts verification steps based on risk level, balancing security and user experience. Low-risk actions have simpler verification, while sensitive data access has stricter checks. Together, these measures form a layered defence system, helping cloud providers protect data in a complex threat environment and enhancing user confidence. With these innovative security methods, the cloud environment can not only defend against external attacks but also improve its resilience and adaptability, creating a strong foundation for the long-term, safe use of cloud technology.
We understand that while cloud computing brings convenience, it also faces security risks such as data breaches and malware attacks. This reminds us of the importance of data protection and access control. We have learned about some key security measures, such as Identity and Access Management (IAM), encryption, firewalls, and Intrusion Detection Systems (IDS), which help secure the cloud environment. Additionally, advanced methods like Zero Trust Architecture can effectively limit unauthorized access, enhancing data security and user trust. This knowledge helps us better understand the importance of cloud security and guides us to strengthen data protection in practical applications.
Some key security measures were mentioned, helping us understand how to protect the security of cloud environments. First, Identity and Access Management (IAM) is a basic technology for cloud security. By controlling user identities and access permissions, it can effectively prevent unauthorized users from accessing sensitive data. IAM systems can use methods like Multi-Factor Authentication (MFA) to ensure that only verified users can access critical resources. In addition, firewalls and Intrusion Detection Systems (IDS) can help filter network traffic and monitor suspicious activities, further reducing the risk of malicious attacks. The combined use of these security technologies can enhance the overall defence capabilities of the cloud computing environment.
Explained the importance of data encryption. Encryption can ensure data is kept private during the transmission and storage process, even if a leak happens, unauthorized persons cannot read data content. Combined with data backup and disaster recovery measures, it can quickly recover when data is lost or under attack, ensuring business continuity and reliability. Moreover, technical measures like data segmentation and network isolation are important means to prevent attack spreading.
Besides these traditional measures, also introduced more advanced Zero Trust Architecture. This method emphasizes that it needs multi-level verification before accessing any resource, and divides strict access permissions in the network, ensuring even if intrusion occurs, attackers are difficult to move freely and expand attack range. Zero Trust Architecture through continuous verification and strict control access, greatly improves data security and enhances users' trust in cloud environments.
Furthermore, mentioned using blockchain technology to protect data integrity, through unchangeable records to guarantee operation transparency and credibility. This decentralized technology can further enhance users' confidence in data security. All operations recorded by blockchain can be traced back, which is especially suitable for data storage and management needing high compliance and transparency.
Through learning, we realize that in complex threat environments, multi-layer defence strategies and advanced protection technologies of cloud computing security are extremely important. We should adopt these security measures in practical applications to protect data, including IAM, encryption, firewall, Zero Trust Architecture, etc., further strengthening the protection of data, and ensuring the security and reliability of cloud services. This knowledge helps us fully understand the necessity of cloud computing security and also makes us more clearly aware of how to take more effective measures in practice to deal with constantly changing security challenges.