Submitted:
20 December 2024
Posted:
23 December 2024
You are already at the latest version
Abstract
Keywords:
1. Introduction
1.1. Trust Models and DoS Attack
1.2. Research Problem and Questions
1.3. Study Contributions
- The study developed a comprehensive classification of the types of DoS attacks in WSNs that can be addressed using trust models including their key attack features and impact mechanisms. By analyzing the key features of these DoS attacks we identified the trust evidence that trust models required to recognize effectively DoS attacks.
- The study identified the optimal methods for extracting trust evidence and provided a comprehensive summary of trust evaluation methods
- The study identified the key challenges in applying trust models for the defense of WSNs against DoS attacks.
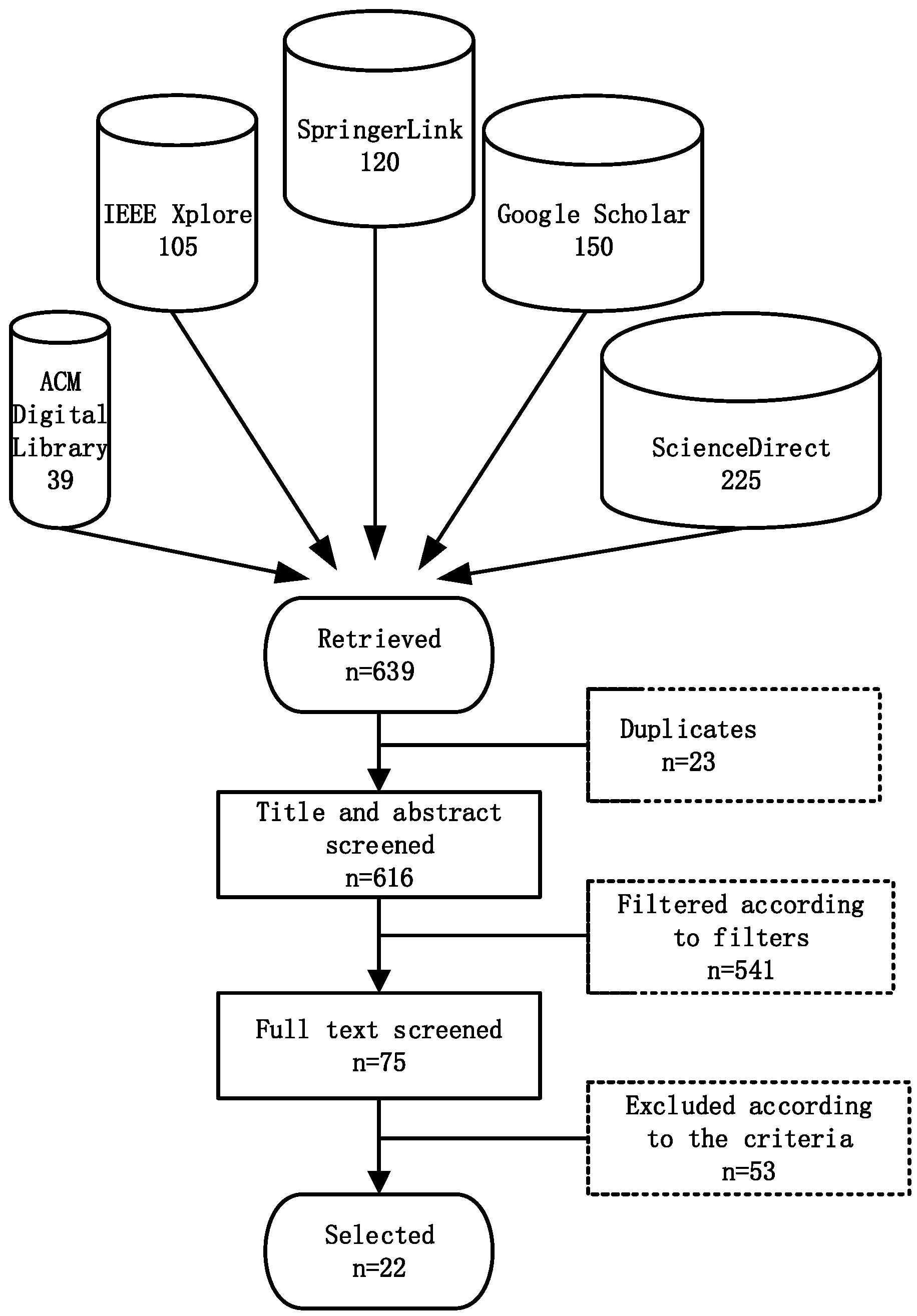
2. Methodology
2.1. Inclusion and Exclusion criteria
2.2. Search Strategy
2.3. Screening and Selection Process
2.4. Data Extraction and Synthesis Methods
3. Results
3.1. DoS attacks in WSNs
| Types of DoS attacks | Impact Mechanisms | Key Impact Features |
|---|---|---|
| 1. Selective Forwarding Attack [21] | MLNs affect the availability of the network services by dropping to a targeted destination node. |
|
| 2. Black Hole Attack [11] | The MLN claims to have the best route causing all packets to be forwarded to it. It drops all forwarded packets. |
|
| 3. Grey Hole Attack [38] | A variant of the black hole attack. The MLN drops packets intermittently or selectively. The degradation of network performance is less detectable. |
|
| 4. Flooding Attack [15] | The MLN sends a large number of connection requests or packets and forces the attacked nodes to exhaust their resources by processing an excessive number of invalid requests. |
|
| 5. Sinkhole Attack [38] | The MLN falsifies routing information and causes network congestion by attracting a large amount of network traffic. |
|
| 6. Sybil Attack [6] | The attacker disrupts the topology of the network by adding multiple fake nodes which reduces the efficiency of the routing and data transmission. |
|
| 7. Vampire Attack [13] | The MLN manipulates network routing protocols to direct packets along longer or circular paths; legitimate nodes consume more energy and fail prematurely |
|
| 8. DDoS Attack [20] | An enhanced version of the DoS attacks above; launched by multiple MLNs at the same time |
|
| 9. LDoS Attack [34] | The quality of service of the network is eroded slowly by sending intermittent, low-rate malicious traffic. It’s harder to detect |
|
| 10. Hybrid DoS attack [9] | Combines multiple attacks at the same time, such as sending malicious traffic while selectively dropping some legitimate packets. |
|
| 11. ON–OFF Attack [26] | The MLN switches randomly from attack to normal operation to prevent detection. |
|
| 12. New-Flow Attack [21] | A flooding attack targeting the control plane of SDWSNs. The large number of new-flow control messages degrade network performance. |
|
| 13. Bad Mouthing Attack [6] | The MLN spreads false negative information about legitimate nodes, causing their trust value to degrade. |
|
| 14. Good Mouthing Attack [6] |
The MLN spreads false positive information about other MLNs. |
|
3.2. Trust Evidence
3.3. Approaches to Extracting Trust Evidence
3.3.1. Extracting Packet Sending Rate
3.3.2. Extracting Packet Receiving Rate
3.3.3. Extracting Packet Forwarding Rate
3.3.4. Extracting Energy Consumption Rate
3.3.5. Extracting Data Accuracy
3.4. Trust Evaluation Methods
3.4.1. Direct trust evaluation
- Threshold-limiting methods
- 2.
- Success-failure methods
3.4.2. Indirect trust evaluation
- Dempster–Shafer
- 2.
- Arithmetic Mean
- 3.
- Weighted Average
- 4.
- Outlier detection
- 5.
- Forgetting Curve
- 6.
- Intrusion Detection System
3.4.3. Updating the Trust Value
- Weighted Average
- 2.
- Improved Weighted Average
- 3.
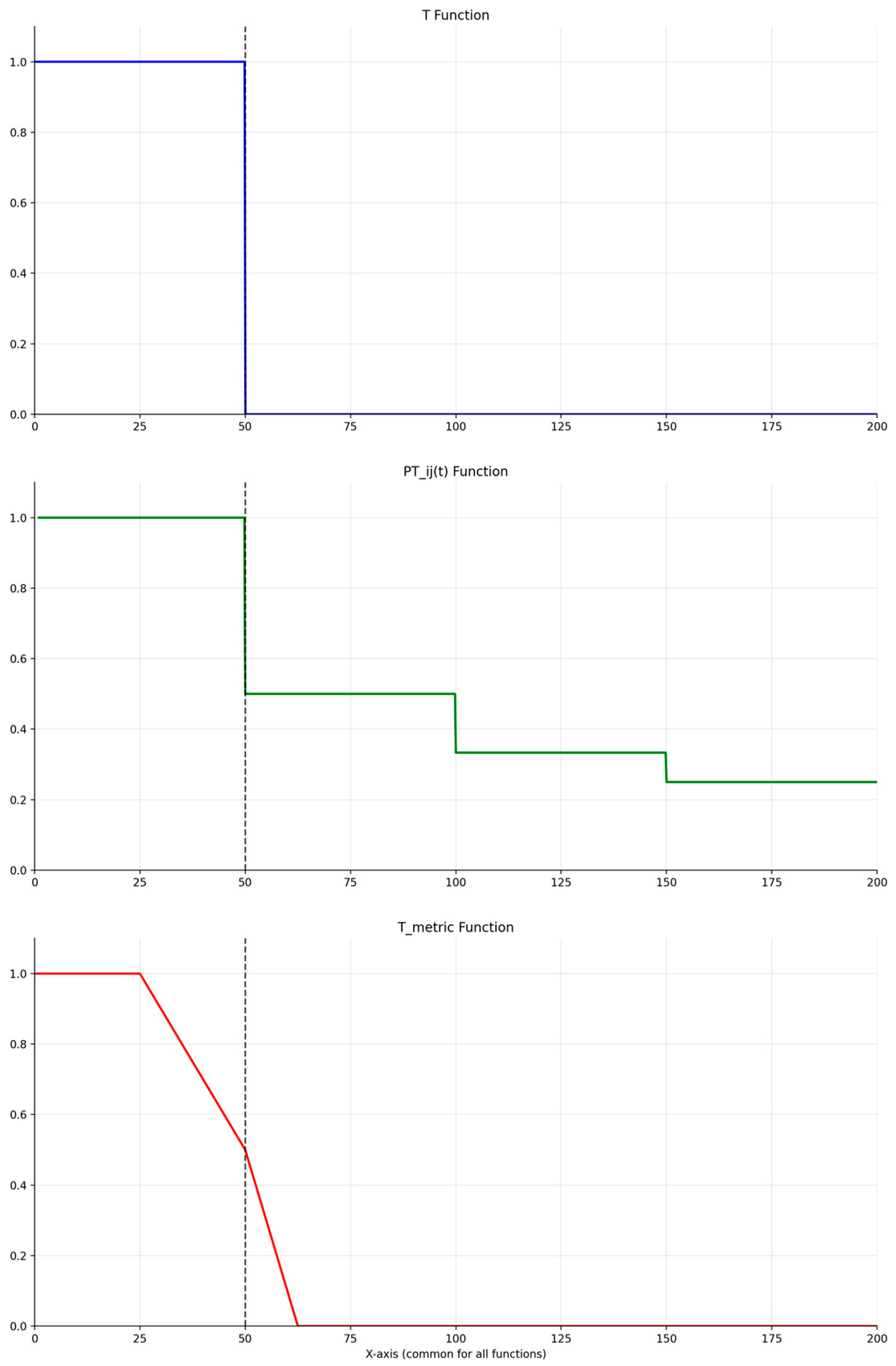
- Time Lapses Function
4. Analysis and Discussion
4.1. Threshold Limits
4.2. Weighting Trust Evidence Metrics
4.3. Loss of Trust Information
4.4. Link Quality
4.5. Authentication Delay
4.6. Trust-based Routing
5. Conclusion
5.1. Comparison with Prior Work
5.2. Summary and Directions for Further Research
5.3. Study Limitatinos
Author Contributions
Funding
Conflicts of Interest
Appendix A
| No | Author, Year | Trust evidence | Direct trust | Indirect trust | Evaluation methods | Trust metric range | Distributed | Centralized | Hybrid | Detect attacks | Defend attacks | DoS attack types | Simulation tool | Domain |
| 1 | Ganeriwal et al., 2004, 2008 [6,29] | Forwarding Trust, Data Trust. |
✓ | ✓ | Bayesian Beta method, aging factor, Dempster-Shafer belief theory and concept of belief discounting. |
a realm number between 0 and 1 | ✓ | ✓ | ✓ | Bad Mouthing Attack, Good Mouthing Attack, Sybil Attack. |
NESLsim | WSN | ||
| 2 | Cao et al., 2006 [27] | Ratio of the number of successfully solved puzzles to the number of packets sent. | ✓ | Take the logarithm of the ratio. | Negative real numbers less than or equal to 0 | ✓ | ✓ | ✓ | Flooding Attack. | Not Mentioned | WSN | |||
| 3 | Cho and Qu, 2013 [28] | Forwarding Trust. | ✓ | Bayesian Beta method, Entropy-based trust models. |
a realm number between 0 and 1 | ✓ | ✓ | ✓ | Selective Forwarding Attack. |
OPNET | WSN | |||
| 4 | Han et al., 2014 [31] | energy consumption, probability of Packet reached successfully (PPRS). |
✓ | Bayesian Beta method, aging factor. |
a realm number between 0 and 1 | ✓ | ✓ | Selective Forwarding Attack, Flooding Attack. |
NS2 | cluster-based WSN | ||||
| 5 | Gautam and Kumar, 2018 [30] | probability of Packet reached successfully (PPRS). | ✓ | ✓ | Bayesian Beta method, forgetting curve. |
a realm number between 0 and 1 | ✓ | ✓ | Unclassified. | Not Mentioned | cluster-based WSN | |||
| 6 | Jinhui et al., 2018 [9] | energy consumption, power consumption sequence. |
✓ | Bayesian Beta method, penalty factor, threshold, Pearson correlation coefficient. |
an unsigned integer between 0 and 10, | ✓ | ✓ | Hybrid DoS Attacks. | NS2 | cluster-based WSN | ||||
| 7 | Wang et al., 2018 [21] | Data Forwarding Trust, Control Forwarding Trust, Packet-in Trust. |
✓ | Bayesian Beta method, weight, threshold. |
Local trust: an unsigned integer between 0 and 100, Global trust: a realm number between 0 and 1 |
✓ | ✓ | ✓ | Selective Forwarding Attack, New-Flow Attack. |
Contiki Cooja 2.7 | SDWSN | |||
| 8 | Anwar et al., 2019 [26] | Packet Received Evaluation (PRE), Packet Sending Evaluation (PSE), Transit Packet Evaluation (TPE). |
✓ | ✓ | Bayesian Beta method, weight. |
a realm number between 0 and 1 | ✓ | ✓ | On–Off Attack, Bad-mouth Attack, DoS Attack. |
OMNET++ | WSN | |||
| 9 | Usman et al., 2019 [3] | data rate. | ✓ | threshold. | trust or not trust | ✓ | ✓ | ✓ | Unclassified | MATLAB | WBAN | |||
| 10 | Lyu et al., 2019 [32] | Forwarding Trust. | ✓ | aging factor. | a realm number between 0 and 1 | ✓ | ✓ | ✓ | Unclassified | OPNET | IoT | |||
| 11 | BinYahya and Shen, 2019 [36] | Forwarding Trust, Sending-Rate Trust, New-Flow Trust. |
✓ | ✓ | Bayesian Beta method, weight, aging factor. |
a realm number between 0 and 1 | ✓ | ✓ | Black-Hole Attack, Selective Forwarding Attack, DoS Attack. |
MATLAB | SDWSN | |||
| 12 | Wu et al., 2019 [10] | communication trust, data trust, energy trust. |
✓ | ✓ | Bayesian Beta method, weight, threshold, aging factor, LQI analysis. |
a realm number between 0 and 1 | ✓ | ✓ | Selective Forwarding Attack, DoS Attack. | MATLAB | WSN | |||
| 13 | Qureshi et al., 2020 [12] | the number of sent packets, the number of received packets, the time of sending packets, the time of receiving packets, and the packet loss rate between two nodes. | ✓ | ✓ | Bayesian Beta method, threshold. |
a realm number between 0 and 1 | ✓ | ✓ | ✓ | On and Off Attack, Bad mouthing Attack, DoS Attack. |
OMNET++ | IoT | ||
| 14 | Su et al., 2020 [15] | communication trust, data trust, and energy trust. |
✓ | ✓ | Bayesian Beta method, weight, threshold, aging factor. |
a realm number between 0 and 1 | ✓ | ✓ | Selective Forwarding Attack, Flooding Attack. |
MATLAB | UASN | |||
| 15 | Anand and Vasuki, 2021 [25] | throughput, packet rate, packet forwarding rate, hop count, and energy utilization. | ✓ | ✓ | an improved statistical method of grading factor with probability weight factor, Fleiss kappa function. |
a realm number between 0 and 1 | ✓ | ✓ | Selective Forwarding Attack, Flooding Attack. |
NS-2.33 | WSN | |||
| 16 | Rahamathullah and Karthikeyan, 2021 [20] | data packet forwarding ratio, control packets forwarding ratio, energy consumption. |
✓ | ✓ | weight, threshold. |
a realm number between 0 and 1 | ✓ | ✓ | ✓ | DDoS Attack | Contiki Cooja 3.0, Tmote sky wireless sensor board |
IoBT | ||
| 17 | Isaac Sajan and Jasper, 2021 [13] | the quantity of the packet delivered successfully, the previous history of packets dropped by the nodes, the similarity in attributes. |
✓ | ✓ | weight, threshold. |
a realm number between 0 and 1 | ✓ | ✓ | ✓ | Vampire Attack. | MATLAB | adhoc sensor network (WANET) | ||
| 18 | Rani et al., 2021 [33] | Data trust, Community trust. |
✓ | ✓ | weight. | a realm number between 0 and 1 | ✓ | ✓ | ✓ | Unclassified | OMNET++ | cluster-based WSN | ||
| 19 | Yuvaraj et al., 2022 [34] | Forwarding Trust, IMFs. |
✓ | weight, DR-HHT, Correlation Coefficient, Kolmogorov‒Smirnov Test. |
a realm number between 0 and 1 | ✓ | ✓ | ✓ | LDoS | MATLAB | IoT WSN |
|||
| 20 | Bin-Yahya et al., 2022 [11] | Forwarding Trust, Sending-Rate Trust, New-Flow Trust, Node Reliability. |
✓ | ✓ | Bayesian Beta method, weight, threshold, aging factor, reward and penalize. |
a realm number between 0 and 1 | ✓ | ✓ | Black-Hole Attack, Selective Forwarding Attack, DoS Attack, Good Mouthing Attack, ON–OFF Attack, Hybrid DoS Attacks, New-Flow Attack. |
MATLAB | SDWSN | |||
| 21 | Isong et al., 2023 [37] | Forwarded packets, Received packets, Traffic statistical information. |
✓ | ✓ | if drop or block packets value++, threshold, IDS module analysis. |
an unsigned integer between 0 and 10 | ✓ | ✓ | ✓ | Unclassified | not evaluated yet | SDWSN | ||
| 22 | Ahmed et al., 2024 [14] | communication trust, energy trust, data trust. |
✓ | ✓ | Bayesian Beta method, weight, aging factor, penalizing factor, load balancing. |
a realm number between 0 and 1 | ✓ | ✓ | ✓ | Unclassified | MATLAB | Edge IoT |
References
- Akyildiz, I. F.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. Wireless sensor networks: a survey. Computer Networks 2002, 38, 393–422. [Google Scholar] [CrossRef]
- Wood, A. D.; Stankovic, J. A. Denial of service in sensor networks. Computer 2002, 35, 54–62. [Google Scholar] [CrossRef]
- Usman, M.; Asghar, M. R.; Ansari, I. S.; Granelli, F.; Qaraqe, M. Trust-Based DoS Mitigation Technique for Medical Implants in Wireless Body Area Networks. ICC 2019 - 2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20-24 May 2019, (pp. 1-6), IEEE. [CrossRef]
- Gungor, V. C.; Hancke, G. P. Industrial Wireless Sensor Networks: Challenges, Design Principles, and Technical Approaches. IEEE Transactions on Industrial Electronics 2009, 56, 4258–4265. [Google Scholar] [CrossRef]
- Yick, J.; Mukherjee, B.; Ghosal, D. Wireless sensor network survey. Computer Networks 2008, 52, 2292–2330. [Google Scholar] [CrossRef]
- Ganeriwal, S.; Balzano, L. K.; Srivastava, M. B. Reputation-based framework for high integrity sensor networks. ACM Transactions on Sensor Networks 2008, 4, 1–37. [Google Scholar] [CrossRef]
- Govindan, K.; Mohapatra, P. Trust computations and trust dynamics in mobile adhoc networks: A survey. IEEE Communications Surveys & Tutorials 2012, 14, 279–298. [Google Scholar] [CrossRef]
- Reddy, V. B.; Venkataraman, S.; Negi, A. Communication and data trust for wireless sensor networks using D--S theory. IEEE Sensors Journal 2017, 17, 3921–3929. [Google Scholar] [CrossRef]
- Jinhui, X.; Yang, T.; Feiyue, Y.; Leina, P.; Juan, X.; Yao, H. Intrusion Detection System for Hybrid DoS Attacks using Energy Trust in Wireless Sensor Networks. Procedia Computer Science 2018, 131, 1188–1195. [Google Scholar] [CrossRef]
- Wu, X.; Huang, J.; Ling, J.; Shu, L. BLTM: Beta and LQI Based Trust Model for Wireless Sensor Networks. IEEE Access 2019, 7, 43679–43690. [Google Scholar] [CrossRef]
- Bin-Yahya, M.; Alhussein, O.; Shen, X. Securing Software-Defined WSNs Communication via Trust Management. IEEE Internet of Things Journal 2022, 9, 22230–22245. [Google Scholar] [CrossRef]
- Qureshi, K. N.; Iftikhar, A.; Bhatti, S. N.; Piccialli, F.; Giampaolo, F.; Jeon, G. Trust management and evaluation for edge intelligence in the Internet of Things. Engineering Applications of Artificial Intelligence 2020, 94, 103756. [Google Scholar] [CrossRef]
- R, I. S.; J, J. A secure routing scheme to mitigate attack in wireless adhoc sensor network. Computers & Security 2021, 103, 102197. [Google Scholar] [CrossRef]
- Ahmed, A.; Qureshi, K. N.; Anwar, M.; Masud, F.; Imtiaz, J.; Jeon, G. Link-based penalized trust management scheme for preemptive measures to secure the edge-based internet of things networks. Wireless Networks 2024, 30, 4237–4259. [Google Scholar] [CrossRef]
- Su, Y.; Mal, S.; Jin, Z.; Fu, X.; Li, Y.; Liu, X. A Trust Model for Underwater Acoustic Sensor Networks Based on Fast Link Quality Assessment. Global Oceans 2020: Singapore – U.S. Gulf Coast, Biloxi, MS, USA, 5-30 Oct. 2020, (pp. 1-6), IEEE. [CrossRef]
- Muzammal, S. M.; Murugesan, R. K.; Jhanjhi, N. Z. A Comprehensive Review on Secure Routing in Internet of Things: Mitigation Methods and Trust-Based Approaches. IEEE Internet of Things Journal 2021, 8, 4186–4210. [Google Scholar] [CrossRef]
- Alhandi, S. A.; Kamaludin, H.; Alduais, N. A. M. Trust Evaluation Model in IoT Environment: A Comprehensive Survey. IEEE Access 2023, 11, 11165–11182. [Google Scholar] [CrossRef]
- Tyagi, H.; Kumar, R.; Pandey, S. K. A detailed study on trust management techniques for security and privacy in IoT: challenges, trends, and research directions. High-Confidence Computing 2023, 3, 100127. [Google Scholar] [CrossRef]
- Zhu, R.; Boukerche, A.; Long, L.; Yang, Q. Design Guidelines On Trust Management for Underwater Wireless Sensor Networks. IEEE Communications Surveys & Tutorials 2024, 1-1. [CrossRef]
- Rahamathullah, U.; Karthikeyan, E. A lightweight trust-based system to ensure security on the Internet of Battlefield Things (IoBT) environment. International Journal of System Assurance Engineering and Management 2021. [Google Scholar] [CrossRef]
- Wang, R.; Zhang, Z.; Zhang, Z.; Jia, Z. ETMRM: An Energy-efficient Trust Management and Routing Mechanism for SDWSNs. Computer Networks 2018, 139, 119–135. [Google Scholar] [CrossRef]
- Kitchenham, B.; Charters, S. Guidelines for performing systematic literature reviews in software engineering. EBSE Technical Report EBSE-2007-01 Version 2.3. Keele University and University of Durham. 2007. https://ebse.webspace.durham.ac.uk/wp-content/uploads/sites/49/2022/08/Systematic-reviews-5-8.pdf.
- Bukar, U. A.; Othman, M. Architectural Design, Improvement, and Challenges of Distributed Software-Defined Wireless Sensor Networks. Wireless Personal Communications 2022, 122, 2395–2439. [Google Scholar] [CrossRef]
- Ouzzani, M.; Hammady, H.; Fedorowicz, Z.; Elmagarmid, A. Rayyan—a web and mobile app for systematic reviews. Systematic Reviews 2016, 5, 210. [Google Scholar] [CrossRef]
- Anand, C.; Vasuki, N. Trust Based DoS Attack Detection in Wireless Sensor Networks for Reliable Data Transmission. Wireless Personal Communications 2021, 121, 2911–2926. [Google Scholar] [CrossRef]
- Anwar, R. W.; Zainal, A.; Outay, F.; Yasar, A.; Iqbal, S. BTEM: Belief based trust evaluation mechanism for Wireless Sensor Networks. Future Generation Computer Systems 2019, 96, 605–616. [Google Scholar] [CrossRef]
- Cao, Z.; Zhou, X.; Xu, M.; Chen, Z.; Hu, J.; Tang, L. Enhancing Base Station Security Against DoS Attacks in Wireless Sensor Networks. 2006 International Conference on Wireless Communications, Networking and Mobile Computing, Wuhan, China, 22-24 Sept. 2006, (pp. 1-4), IEEE. [CrossRef]
- Cho, Y.; Qu, G. Detection and Prevention of Selective Forwarding-Based Denial-of-Service Attacks in WSNs. International Journal of Distributed Sensor Networks 2013, 9, 205920. [Google Scholar] [CrossRef]
- Ganeriwal, S.; Srivastava, M. B. Reputation-based framework for high integrity sensor networks. Proceedings of the 2nd ACM workshop on Security of ad hoc and sensor networks, Washington DC, USA, 25 October 2004. [CrossRef]
- Gautam, A. K.; Kumar, R. A Robust Trust Model for Wireless Sensor Networks. 2018 5th IEEE Uttar Pradesh Section International Conference on Electrical, Electronics and Computer Engineering (UPCON), Gorakhpur, India, 2-4 Nov. 2018, (pp. 1-5), IEEE. [CrossRef]
- Han, G.; Shen, W.; Duong, T. Q.; Guizani, M.; Hara, T. A proposed security scheme against Denial of Service attacks in cluster-based wireless sensor networks. Security and Communication Networks 2014, 7, 2542–2554. [Google Scholar] [CrossRef]
- Lyu, C.; Zhang, X.; Liu, Z.; Chi, C. H. Selective Authentication Based Geographic Opportunistic Routing in Wireless Sensor Networks for Internet of Things Against DoS Attacks. IEEE Access 2019, 7, 31068–31082. [Google Scholar] [CrossRef]
- Rani, P.; Gupta, N. K. Composite Trust for Secure Routing Strategy through Energy based Clustering in WSN. 2021 International Conference on Advances in Electrical, Computing, Communication and Sustainable Technologies (ICAECT), Bhilai, India, 19-20 Feb. 2021, (pp. 1-6), IEEE. [CrossRef]
- Yuvaraj, D.; Priya, S.-S.; Braveen, M.; Krishnan, S.-N.; Nachiyappan, S.; Mehbodniya, A.; Ahamed, A.-M.-U.; Sivaram, M. Novel DoS Attack Detection Based on Trust Mode Authentication for IoT. Intelligent Automation \& Soft Computing 2022, 34, 1505–1522. [Google Scholar] [CrossRef]
- Miyazaki, T.; Yamaguchi, S.; Kobayashi, K.; Kitamichi, J.; Song, G.; Tsukahara, T.; Hayashi, T. A software defined wireless sensor network. 2014 International Conference on Computing, Networking and Communications (ICNC), Honolulu, HI, USA, 3-6 Feb. 2014, (pp. 847-852), IEEE. [CrossRef]
- Bin-Yahya, M.; Shen, X. HTM: Hierarchical Trust Management for Software-Defined WSNs. 2019 IEEE Globecom Workshops (GC Wkshps), Waikoloa, HI, USA, 9-13 Dec. 2019, (pp. 1-6), IEEE. [CrossRef]
- Isong, B.; Manuel, M.; Dladlu, N.; Abu-Mahfouz, A. Trust Management Framework for Securing Software-Defined Wireless Sensor Networks. 2023 International Conference on Electrical, Computer and Energy Technologies (ICECET), Cape Town, South Africa, 16-17 Nov. 2023, (pp. 1-6), IEEE. [CrossRef]
- Webber, J. L.; Arafa, A.; Mehbodniya, A.; Karupusamy, S.; Shah, B.; Dahiya, A. K.; Kanani, P. An efficient intrusion detection framework for mitigating blackhole and sinkhole attacks in healthcare wireless sensor networks. Computers and Electrical Engineering 2023, 111, 108964. [Google Scholar] [CrossRef]
- Chandrasekaran, S. K.; Rajasekaran, V. A. Trust evaluation model in IoT environment: a review. Environment, Development and Sustainability 2024, 1-32. [CrossRef]
| Criteria | Description |
|---|---|
| Inclusion criteria | Studies focusing on trust models addressing DoS attacks in WSNs. |
| Studies focusing on trust models addressing DoS attacks in SDWSNs. | |
| Peer-reviewed articles, conference papers. | |
| Studies published in English. | |
| Exclusion criteria | Studies focusing on artificial intelligence or blockchain solutions for WSNs. |
| Review papers. | |
| Non-peer-reviewed sources. | |
| Studies without available full text. |
| Trust Evidence Category | Trust Evidence |
|---|---|
| Communication trust evidence [11] | Sending rate – data packets |
| Sending rate – control packets | |
| Receiving rate – data packets | |
| Receiving rate – control packets | |
| Forwarding rate – data packets | |
| Forwarding rate - control packets | |
| Energy trust evidence [10] | Energy consumption rate |
| Data trust evidence [10] | Data accuracy |
| Trust evidence | Extraction Methods | Most Efficient | |
|---|---|---|---|
| PSR | 1. Direct interaction. | Included in Method 2. | |
| 2. Nodes' promiscuous receiving mode. | ✓ | ||
| 3. Retrieve from flow table. | The statistical information in the flow table is derived from Method 2. | ||
| PRR | 1. Direct interaction. | Included in Method 2. | |
| 2. Nodes' promiscuous receiving mode. | ✓ | ||
| PFR | 1. Watchdog plus sender overhearing receiver. | ✓ | |
| 2. Watchdog plus third-party overhearing sender and receiver. | Redundant (with Method 1 selected); increases complexity. | ||
| 3. Based on ACK messages. | It can serve to supplement Method 1 | ✓ | |
| 4. Based on traffic profiles. | Relies on interactions involving request and response messages related to traffic profiles, leading to communication overhead. | ||
| ECR | 1. Calculate the energy consumption rate based on beacon message. | ✓ | |
| 2. Convert the energy consumption sequence into the power consumption sequence. | Based on sensor nodes monitoring their own energy consumption with high precision, not very realistic. | ||
| DA | 1. Extract differences in data sequences of the evaluating node and the evaluated node. | Less accurate than Method 2. | |
| 2. Extract the accuracy of the data using an outlier detection algorithm based on all neighborhood data references. | ✓ | ||
| Trust Models | Methods | Comparison |
|---|---|---|
| [6,29] | Dempster–Shafer belief theory method | Suitable for trust models that propagate trust metrics; has strong theoretical support |
| [12,13,20,26,33] | Arithmetic mean method | Suitable for trust models that propagate trust values and do not consider the trustworthiness of the recommendation information; accuracy is low |
| [10,14,15] | Weighted average method | Suitable for trust models that propagate trust values and consider the trustworthiness of the recommendation information based on the recommender's trust value; accuracy is moderate |
| [11,25,36] | Outlier detection | Suitable for trust models that propagate trust values, using outlier detection methods to evaluate the trustworthiness of the recommendation information; accuracy is high |
| [30] | Forgetting curve method | Suitable for trust models that propagate trust values and do not consider the trustworthiness of the recommendation information; accuracy is low |
| [37] | Intrusion Detection System | Using the IDS to detect network anomalies from the network statistical data |
| Models | Methods | Comparison |
| [6,10,14,15,29,31,32,36] | Weighted average | Do not consider poor past performance |
| [11] | Improved weighted average | Consider poor past performance |
| [30] | Time lapses function | Do not consider poor past performance |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





