Submitted:
20 February 2025
Posted:
21 February 2025
You are already at the latest version
Abstract
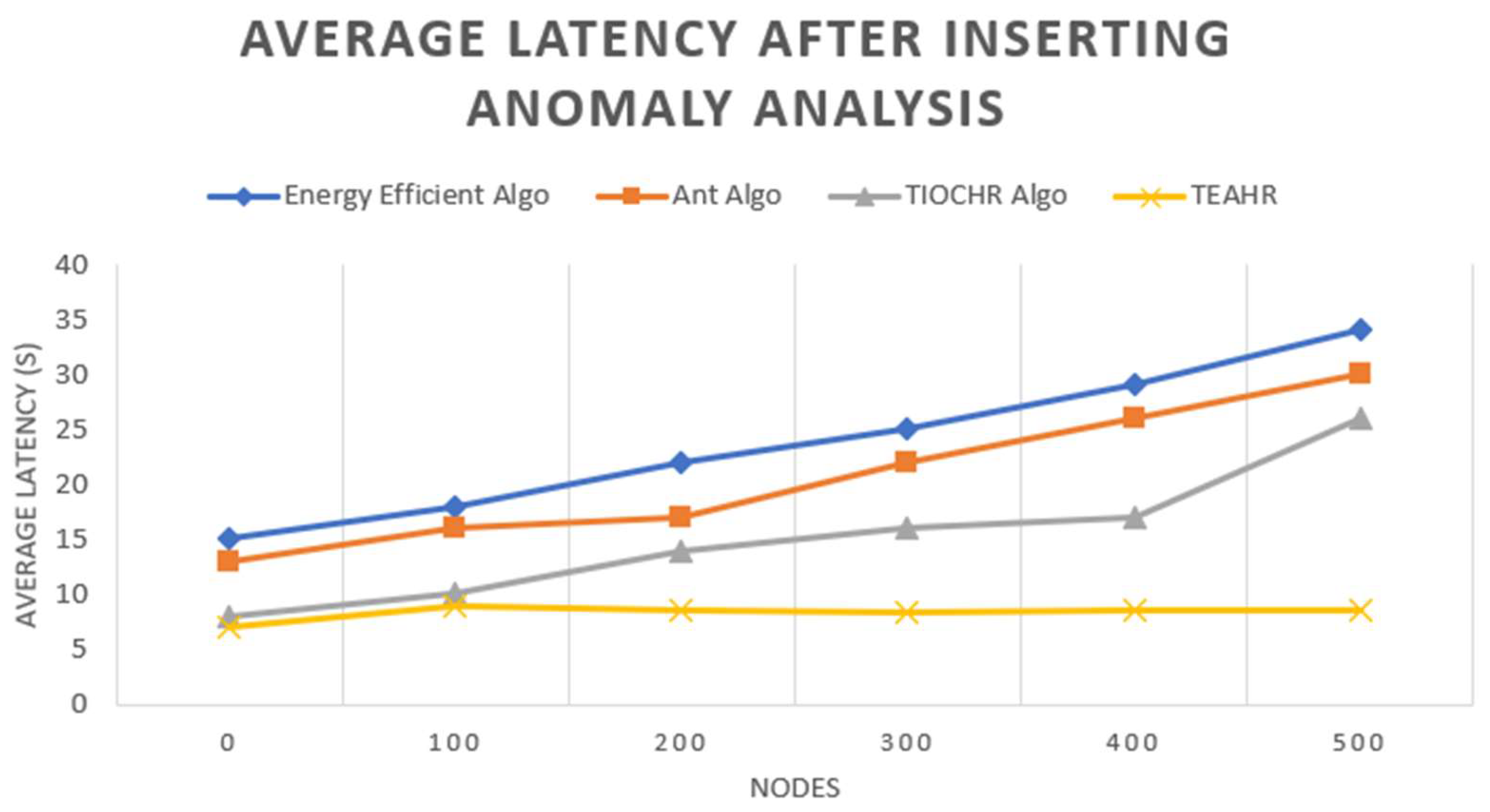
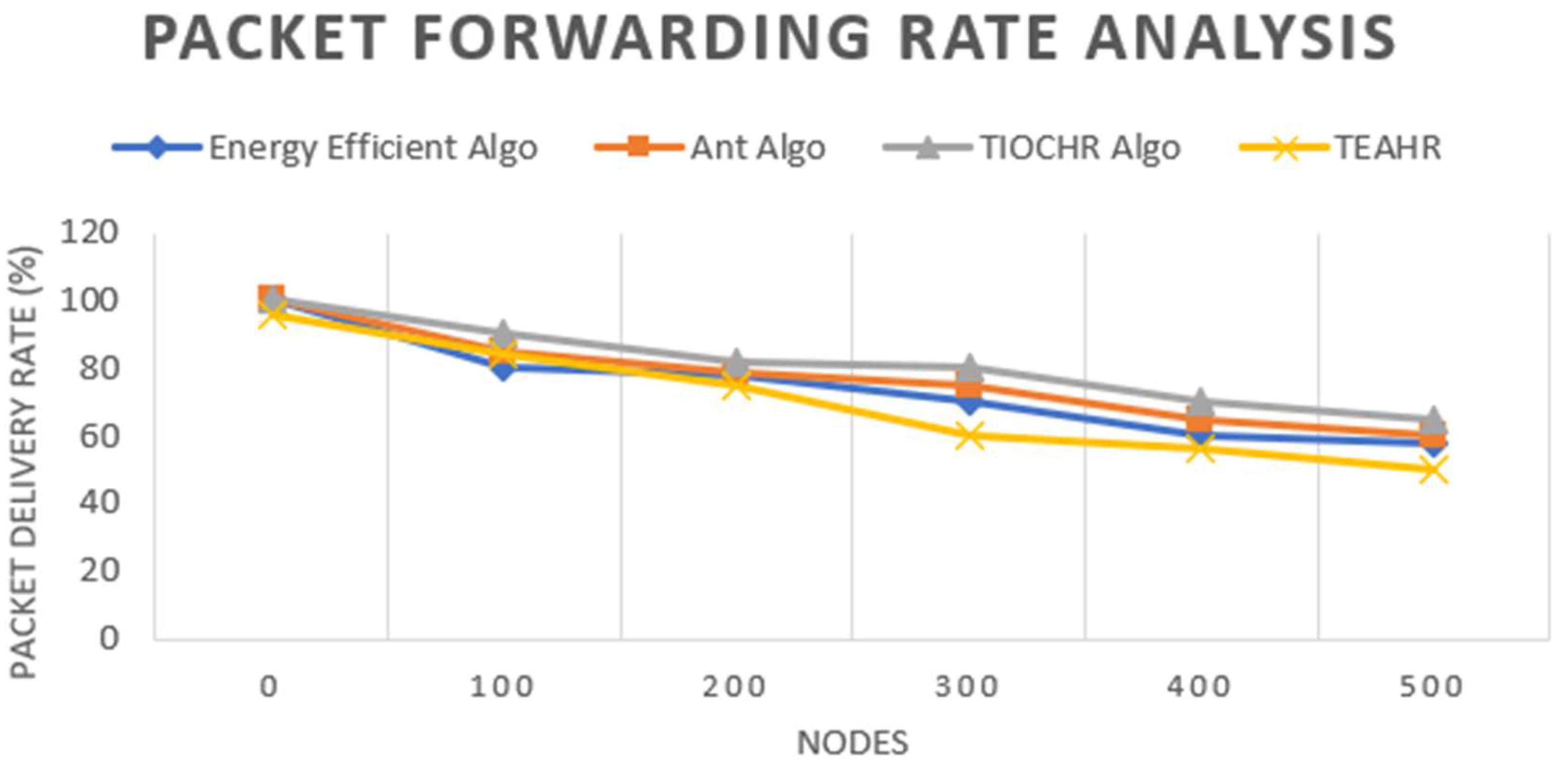
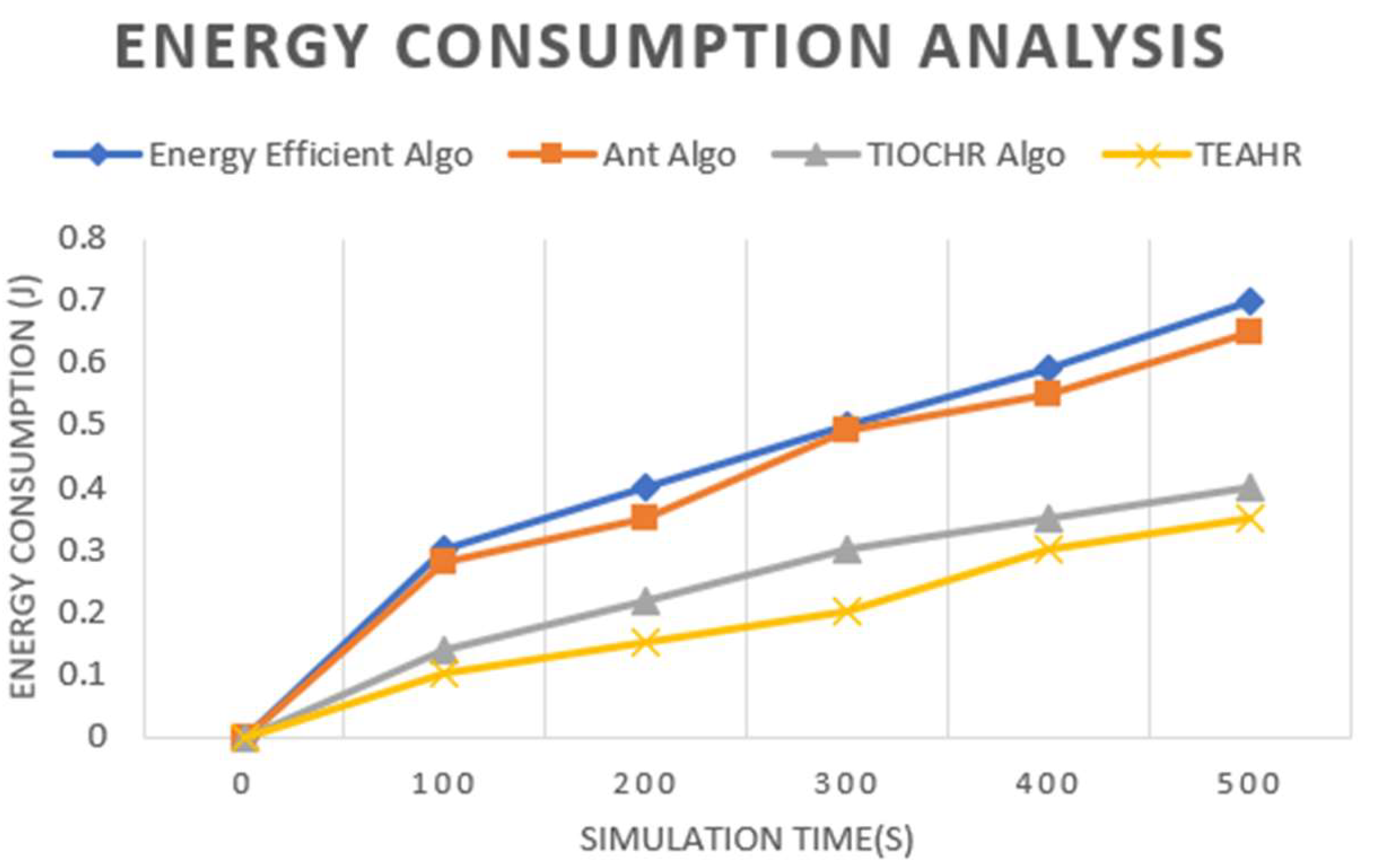
These days, wireless sensor networks (WSNs) are expanding fast and are used in many fields such as healthcare, battlefields, etc. Depending upon the sensor, they are transmitting a few bytes to megabytes, which is a considerable amount of data in a short duration, so security is a significant issue while transferring the data. Furthermore, it is essential to solve security concerns while transferring data by secure routing in wireless sensor networks, which critically depend on energy consumption. Trust is an essential parameter of reliable and safe communication between sensor nodes in dynamic WSNs. By developing trust relationships between sensor nodes, trust management is a successful method to overcome these issues. In WSNs, trust estimation methods are primarily employed in order to improve confidence, trustworthiness, system performance, lifecycle, decision-making processes, and relationships of cooperation among sensor nodes. The fundamental requirements of WSN are energy, connectivity, extended lifetime of the network, the availability of nodes, exchange of information, and memory overheads. In this paper, we present a novel trust-based algorithm to access the level of Trust among nodes called Trust-Based Energy-Aware Hierarchical Routing (TEAHR) in order to foster more reliable and energy-efficient WSNs. Several trust metrics like energy trust, forwarding Trust, consistency Trust behaviour and much more these ratings help in identifying potential malicious nodes (anomaly), hence ensuring network availability. With the exception of large-scale networks, we have performed a comparative study on another algorithm as well and demonstrated that the proposed model exhibits lower latency when compared to other models in terms of energy consumption (more significant) and the packet forwarding rate/lower. The comparisons of TEAHR with conventional techniques show that the proposed algorithm reduces total latency by 15%, enhances energy efficiency by around 20%, and maintains a stable packet forwarding rate, which is highly desirable for accurate operation in adversarial environments, as demonstrated through comparative analysis.

Keywords:
1. Introduction
2. Related Work
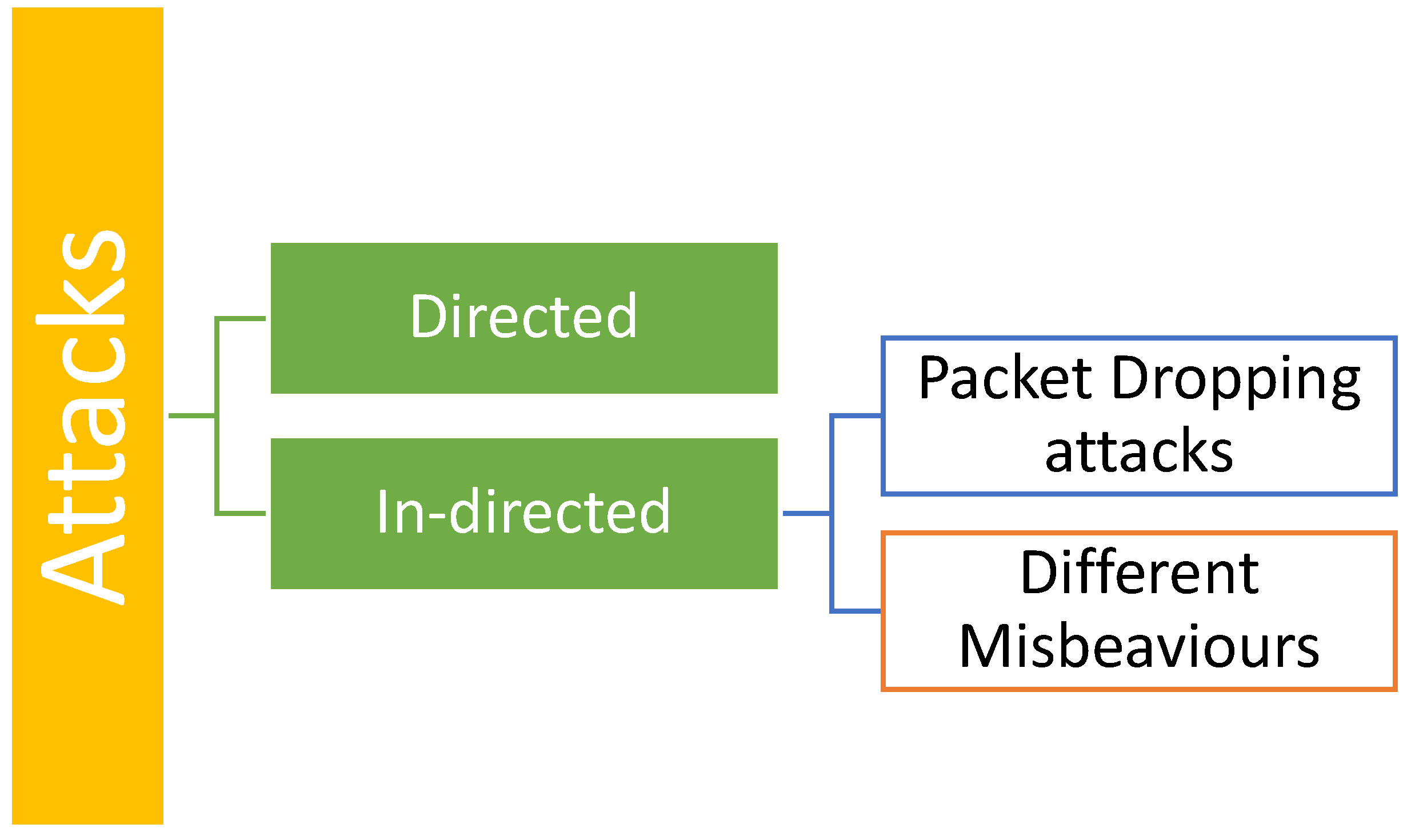
2.1. Types of attacks
- Bad-mouthing attack [8]: This attack involves malicious nodes attempting to undermine the credibility of trustworthy nodes or enhance the credibility of malicious nodes through the dissemination of dishonest suggestions.
- Ballot stuffing attack[2]: A Confederate node enhances its reputation by supplying a substantial quantity of successful interaction data to the other side. To address such assaults, it is essential to decrease the weight of the indirect trust value offered by the neighbouring Node.
- On-off attack[9]: In an on-off assault, malicious nodes exhibit intermittent performance, alternating between periods of satisfactory and unsatisfactory behaviour. Malicious nodes can retain trust values even if they exhibit subpar performance. To effectively counter-switching attacks, older behavioural observations must carry a different level of significance than the more current behavioural observations.
- Selfish attack[10]: The self-node will only delete the consent without reserving the resources to send the trust reply upon receipt of the trust request.
- Sybil attack[11]: The utilization of ID authentication and centralized trust models is a viable strategy to protect against Sybil attacks. These approaches not only enable the accurate identification of nodes but It also facilitates the detection of many false identities associated with malicious nodes through the network sink node or base station (BS).
- Sinkhole attack[12]: The assailant establishes a deceptive aggregation node to divert all data within the vicinity of the fraudulent sink node.
- Reputation time-varying attack[13]: A time-varying attack is a cyberattack strategy that changes its characteristics over time to evade detection and bypass security measures. These attacks exploit the vulnerabilities in systems designed to detect static attack patterns. By constantly changing their tactics, time-varying attacks can remain undetected for more extended periods, potentially causing more damage.
2.1. Trust Models and Their Classification
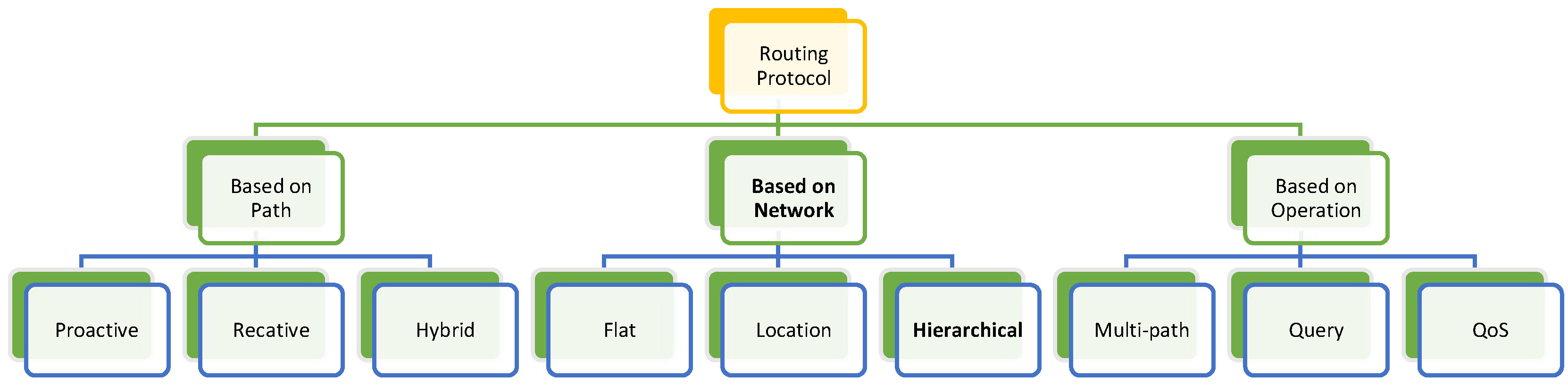
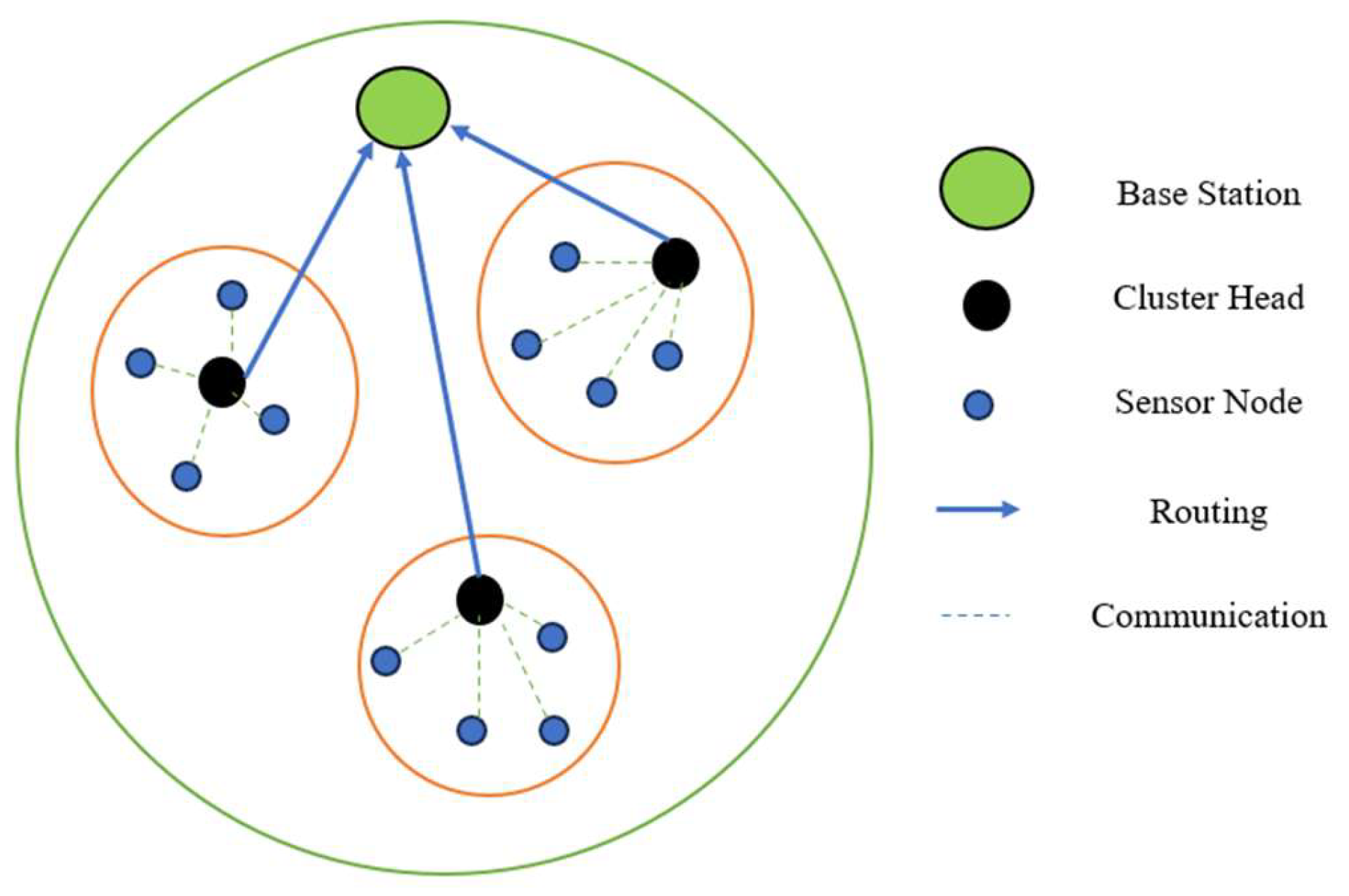
2.1. Hierarchical Routing
2.1. Problem with existing schemes
Proposed work
2.1. Research Contribution
- Energy Trust: Energy trust refers to the evaluation of a node's remaining energy levels as a measure of its operational reliability and expected lifespan. In WSNs, energy efficiency plays a critical role due to the limited power resources of sensor nodes, which are often powered by tiny batteries. Nodes with higher energy reserves are more likely to continue functioning reliably, making them more trustworthy within the network.
- Forwarding Trust: Forwarding Trust assesses a node's effectiveness in forwarding packets to their intended destination. In a WSN, the ability of a node to reliably forward data is crucial for maintaining data integrity and ensuring that information reaches the intended recipients. A node's forwarding Trust is determined by monitoring its packet forwarding history, including metrics such as the number of successfully forwarded packets, packet loss rates, and transmission delays. Nodes that demonstrate consistency and reliability in forwarding behaviour are assigned higher trust scores, which make them more favourable for inclusion in routing paths.
- Consistency Trust: The level of consistency in a node's behaviour over time, particularly in relation to packet forwarding, is evaluated by consistency trust. This metric helps detect deviations that may signal potential malignancy or hardware failure. Inconsistencies in a node's behaviour, such as sudden drops in forwarding success rates or erratic energy consumption, can indicate that the Node has been compromised or is experiencing technical issues. TEAHR can identify nodes that may pose a risk to the network and adjust routing decisions accordingly to maintain overall network stability.
- Behavioural Trust: Behavioral Trust examines a node's adherence to network protocols and its past activity patterns to detect anomalies or potential security breaches. This metric is critical for identifying nodes that may be engaging in malicious activities, such as data tampering, unauthorized access, or collusion with other compromised nodes. Behavioral Trust is assessed by analyzing a node's interaction with other nodes, its response to protocol commands, and any deviations from expected behaviour. Nodes that exhibit suspicious or non-compliant behaviour are assigned lower trust scores and may be excluded from critical network functions.
- Anomaly Detection: a vital feature of the TEAHR framework, enabling the identification and isolation of malicious nodes within the network. When a node's trust score falls below a certain threshold due to suspicious behaviour, it is flagged as potentially compromised. The TEAHR system then takes proactive measures to manage the anomaly, such as restricting the Node's access to the network or isolating it entirely. This approach ensures that the impact of malicious nodes is minimized and that the network remains secure and operational. Additionally, the system continuously monitors the trust scores of all nodes, allowing for dynamic adjustments based on real-time behaviour.
- Energy Efficiency: TEAHR improves energy efficiency across the network by using energy metrics in trust computation. Nodes that are more energy-efficient are rated positively in trust evaluations, which incentivizes the use of energy-saving practices among nodes. This focus on energy efficiency not only extends the operational life of the network but also enhances its overall performance by reducing the likelihood of node failures due to energy depletion.
- Enhanced Security: By incorporating multiple trust metrics, including energy, forwarding, consistency, and behavioural Trust, TEAHR provides a comprehensive approach to identifying and mitigating security threats. This multifaceted trust evaluation process makes it more difficult for malicious nodes to evade detection, thereby enhancing the overall security of the network.
- Optimized Energy Consumption: The integration of energy trust into the routing process ensures that nodes with sufficient energy reserves are prioritized, reducing the likelihood of network disruptions due to node failures. This focus on energy efficiency helps to extend the lifespan of the network and reduces the need for frequent maintenance or node replacement.
- Improved Network Reliability: TEAHR's emphasis on forwarding trust and consistency trust ensures that data is transmitted through reliable and consistent nodes, which enhances the integrity of the data and reduces the likelihood of packet loss or delays. This improved reliability is essential in critical applications where accurate and timely data transmission is essential.
- Scalability: The hierarchical nature of the TEAHR framework allows it to efficiently manage trust and routing decisions in large-scale WSNs. The system can scale to accommodate networks with a large number of nodes without compromising on performance or security, making it suitable for deployment in diverse and expansive environments.
- Dynamic Trust Management: TEAHR's ability to dynamically assess and adjust trust scores based on real-time behaviour ensures that the network can quickly respond to emerging threats and changes in node behaviour. This adaptability is crucial in environments where network conditions and node behaviour can change rapidly, such as in battlefield or disaster response scenarios.
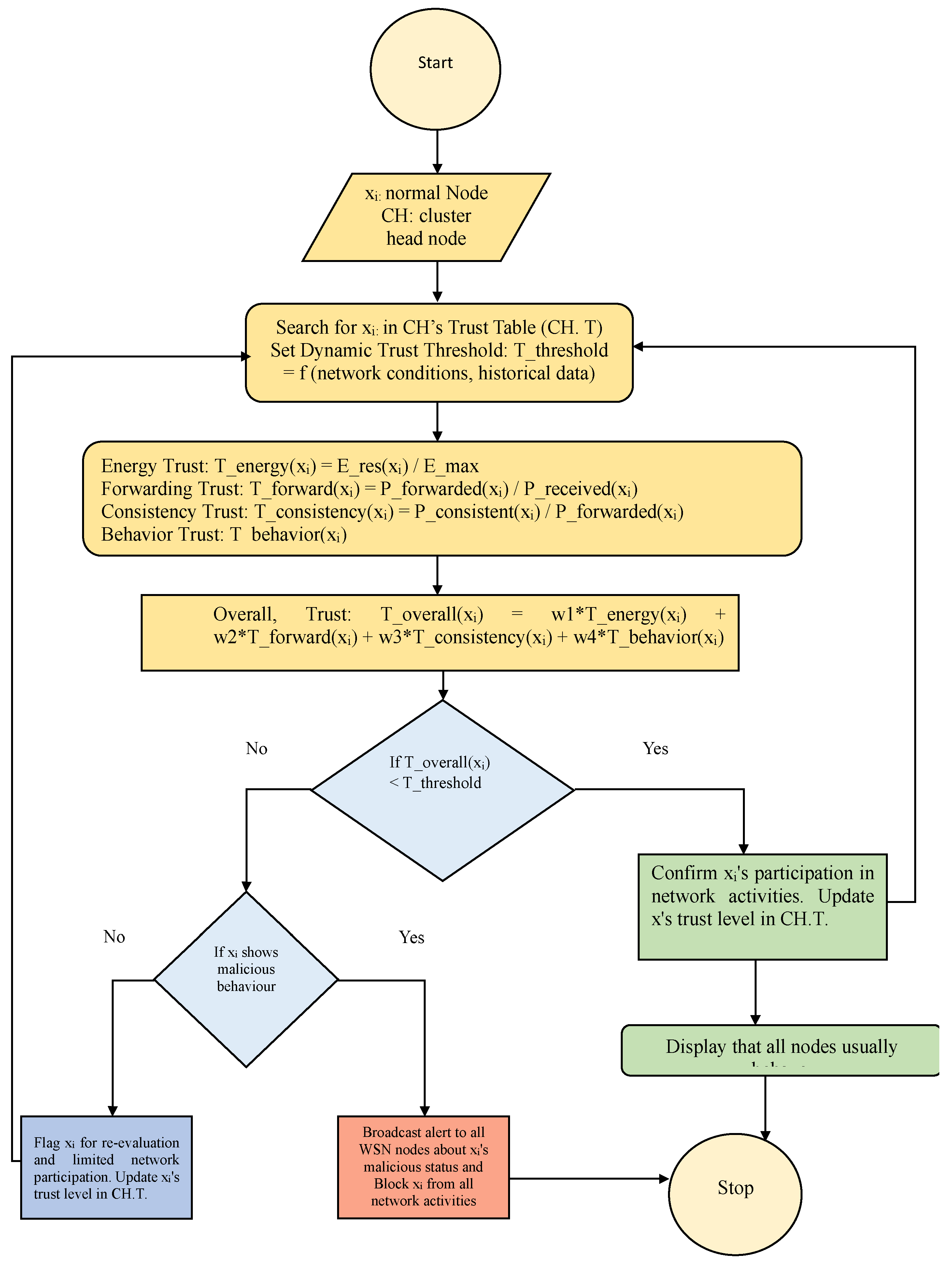
3.2. Proposed Algorithm
3.2.1. Theoretical analysis of TEAHR
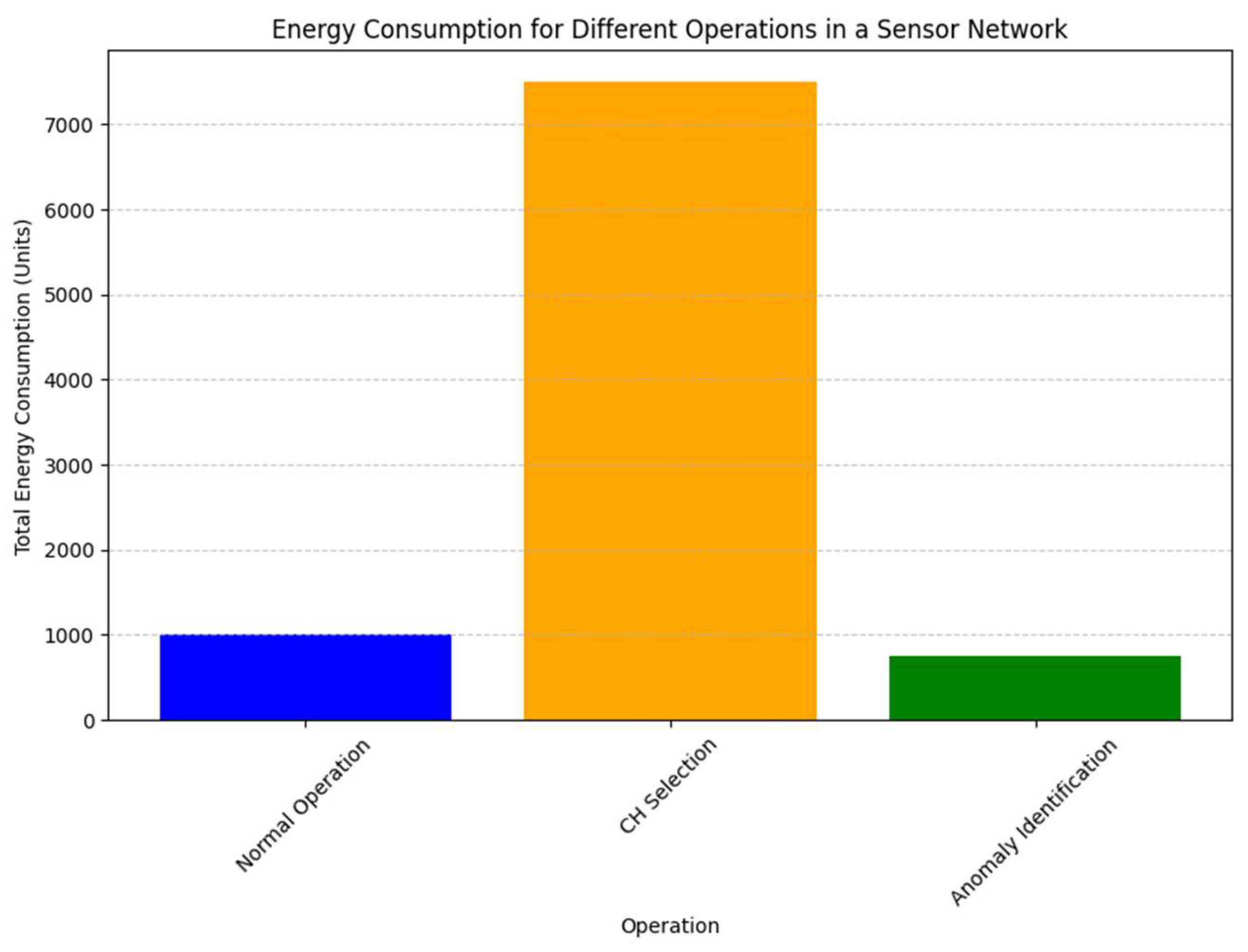
Result and Discussion
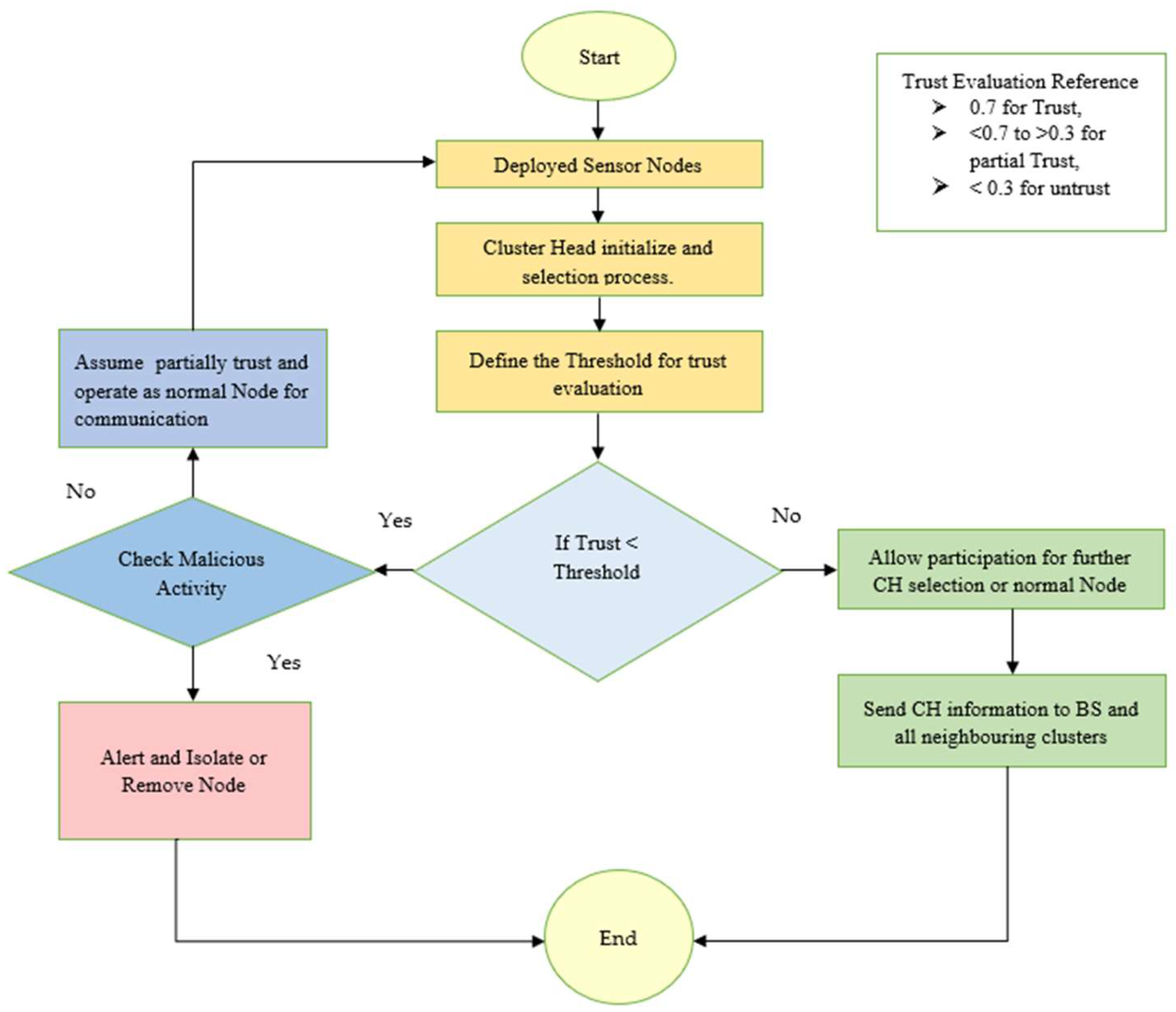
2.1. Trusted Energy Aware Hierarchical Routing (TEAHR)
2.1. Initialization
2.1. Integrating New Cluster Members
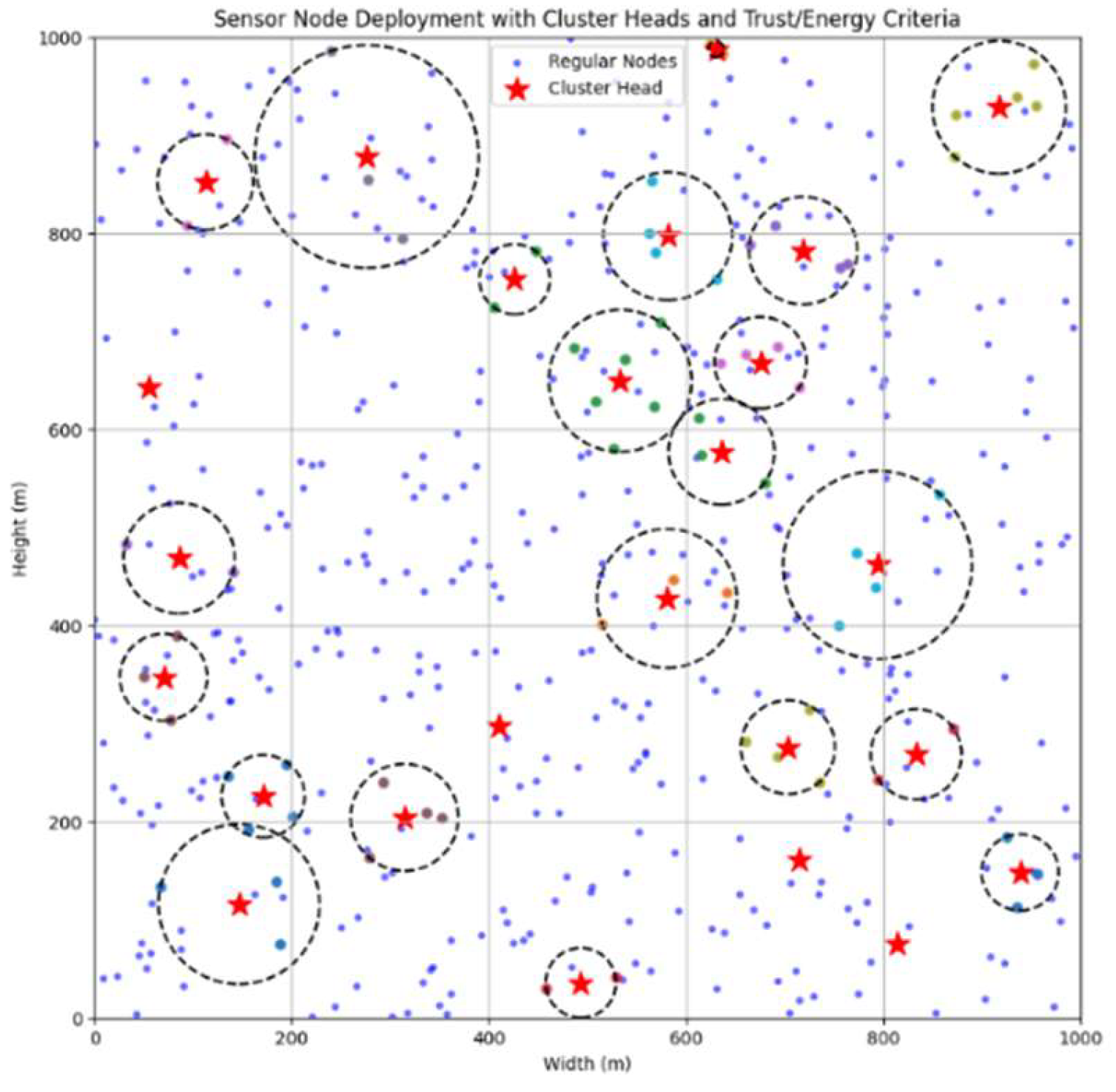
2.1. Simulation Environment
2.1. Deployment of sensor nodes
2.1. Analysis of TEAHR
Conclusions
Author Contributions
Funding Declaration
Data Availability Statement
Conflicts of Interest
References
- Ye, Z.; Wen, T.; Liu, Z.; Song, X.; Fu, C. An Efficient Dynamic Trust Evaluation Model for Wireless Sensor Networks. J. Sensors 2017, 2017, 1–16. [Google Scholar] [CrossRef]
- Fang, W.; Zhang, W.; Chen, W.; Pan, T.; Ni, Y.; Yang, Y. Trust-Based Attack and Defense in Wireless Sensor Networks: A Survey. Wirel. Commun. Mob. Comput. 2020, 2020, 1–20. [Google Scholar] [CrossRef]
- Chen, Z.; Tian, L.; Lin, C. Trust Model of Wireless Sensor Networks and Its Application in Data Fusion. Sensors 2017, 17, 703. [Google Scholar] [CrossRef]
- Vikas; Sagar, B.B.; Munjul, M.Security issues in wireless sensor network – A survey. Journal of Discrete Mathematical Sciences and Cryptography 2021, 24, 1415–1427. [CrossRef]
- Fang, W.; Cui, N.; Chen, W.; Zhang, W.; Chen, Y. A Trust-Based Security System for Data Collection in Smart City. IEEE Trans. Ind. Informatics 2021, 17, 4131–4140. [Google Scholar] [CrossRef]
- Djedjig, N.; Tandjaoui, D.; Romdhani, I.; Medjek, F. Trust Model for IoT Using Cluster Analysis: A Centralized Approach. Wirel Pers Commun 127, 715–736 (2022).
- Mon, S.F.A.; Winster, S.G.; Ramesh, R. Trust Model for IoT Using Cluster Analysis: A Centralized Approach. Wirel. Pers. Commun. 2022, 127, 715–736. [Google Scholar] [CrossRef]
- Prathap, U.; Shenoy, P.D.; Venugopal, K.R. PCAD: Power control attack detection in wireless sensor networks. 2016 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS); pp. 1–6.
- Chae, Y.; DiPippo, L.C.; Sun, Y. L. Trust Management for Defending On-Off Attacks. IEEE Transactions on Parallel and Distributed Systems 2015, 26, 1178–1191. [Google Scholar] [CrossRef]
- Wagh, S.; More, A.; Khavnekar, A. Identification of selfish attack in cognitive radio ad-hoc networks. 2015 IEEE International Conference on Computational Intelligence and Computing Research (ICCIC); pp. 1–4.
- Dong, W.; Liu, X. Robust and Secure Time-Synchronization Against Sybil Attacks for Sensor Networks. IEEE Trans. Ind. Informatics 2015, 11, 1482–1491. [Google Scholar] [CrossRef]
- Ajaykumar, N.; Sarvagya, M.; Parandkar, P. A novel security algorithm ECC-L for wireless sensor network. Internet Technol. Lett. 2020, 3. [Google Scholar] [CrossRef]
- Fang, W.; Zhang, W.; Yang, Y.; Liu, Y.; Chen, W. A resilient trust management scheme for defending against reputation time-varying attacks based on BETA distribution. Sci. China Inf. Sci. 2017, 60, 040305. [Google Scholar] [CrossRef]
- Feng, R.; Han, X.; Liu, Q.; Yu, N. A Credible Bayesian-Based Trust Management Scheme for Wireless Sensor Networks. Int. J. Distrib. Sens. Networks 2015, 11, 678926. [Google Scholar] [CrossRef]
- Wahi, C.; Chakraverty, S.; Bhattacherjee, V. A trust-based secure AODV routing scheme for MANET. International Journal of Ad Hoc and Ubiquitous Computing 2021, 38, 231. [Google Scholar] [CrossRef]
- Alshehri, M. D.; Hussain, F. K. A fuzzy security protocol for trust management in the internet of things (Fuzzy-IoT). Computing 2019, 101, 791–818. [Google Scholar] [CrossRef]
- Reddy, V.B.; Venkataraman, S.; Negi, A. Communication and Data Trust for Wireless Sensor Networks Using D–S Theory. IEEE Sensors J. 2017, 17, 3921–3929. [Google Scholar] [CrossRef]
- Prabha, V.R.; Latha, P. Fuzzy Trust Protocol for Malicious Node Detection in Wireless Sensor Networks. Wirel. Pers. Commun. 2017, 94, 2549–2559. [Google Scholar] [CrossRef]
- Patra, M.; Acharya, S. A Fuzzy Logic-Based Trust Management Scheme for Wireless Sensor Network. in 155–166 (2022). [CrossRef]
- Han, D.; Du, X.; Wang, L.; Liu, X.; Tian, X. Trust-Aware and Fuzzy Logic-Based Reliable Layering Routing Protocol for Underwater Acoustic Networks. Sensors 2023, 23, 9323. [Google Scholar] [CrossRef]
- Patel, R.; Acharya, S. A Fuzzy Logic Based Trust Evaluation Model for IoT. in 147–156 (2024). [CrossRef]
- Abdalzaher, M.S.; Seddik, K.; Elsabrouty, M.; Muta, O.; Furukawa, H.; Abdel-Rahman, A. Game Theory Meets Wireless Sensor Networks Security Requirements and Threats Mitigation: A Survey. Sensors 2016, 16, 1003. [Google Scholar] [CrossRef]
- Abdalzaher, M. S.; Samy, L.; Muta, O. Non-zero-sum game-based trust model to enhance wireless sensor networks security for IoT applications. IET Wireless Sensor Systems 9, 218–226 (2019).
- Adnan, M., Yang, T., Das, S. K. & Ahmad, T. Utility of Game Theory in Defensive Wireless Sensor Networks (WSNs). in 895–904 (2021). doi:10.1007/978-981-15-5113-0_75.
- Wang, E.K.; Chen, C.-M.; Zhao, D.; Ip, W.H.; Yung, K.L. A dynamic trust model in internet of things. Soft Comput. 2020, 24, 5773–5782. [Google Scholar] [CrossRef]
- Yu, X.; Li, F.; Li, T.; Wu, N.; Wang, H.; Zhou, H. Trust-based secure directed diffusion routing protocol in WSN. J. Ambient. Intell. Humaniz. Comput. 2022, 13, 1405–1417. [Google Scholar] [CrossRef]
- Parvathi, C.; Talanki, S. Energy Saving Hierarchical Routing Protocol in WSN. in Wireless Sensor Networks - Design, Deployment and Applications (IntechOpen, 2021). [CrossRef]
- Palan, N.G.; Barbadekar, B.V.; Patil, S. Low energy adaptive clustering hierarchy (LEACH) protocol: A retrospective analysis. 2017 International Conference on Inventive Systems and Control (ICISC); pp. 1–12.
- Lindsey, S.; Raghavendra, C. PEGASIS: Power-efficient gathering in sensor information systems. In Proceedings of the Aerospace Conference Proceedings, Big Sky, MT, USA, 9–16 March 2002; Volume 3, pp. 1125–1130. [Google Scholar]
- Perkins, C.E.; Royer, E.M. Ad-hoc on-demand distance vector routing. In Proceedings of the 2nd IEEE Workshop on Mobile Computing Systems and Applications (WMCSA 1999), New Orleans, LA, USA, 25–26 February 1999; pp. 90–100. [Google Scholar]
- Babu, S.S.; Geethanjali, N. Lifetime improvement of wireless sensor networks by employing Trust Index Optimized Cluster Head Routing (TIOCHR). Meas. Sensors 2024. [Google Scholar] [CrossRef]
- Mostafaei, H. Energy-Efficient Algorithm for Reliable Routing of Wireless Sensor Networks. IEEE Trans. Ind. Electron. 2019, 66, 5567–5575. [Google Scholar] [CrossRef]
- Li, X.; Keegan, B.; Mtenzi, F.; Weise, T.; Tan, M. Energy-Efficient Load Balancing Ant Based Routing Algorithm for Wireless Sensor Networks. IEEE Access 2019, 7, 113182–113196. [Google Scholar] [CrossRef]
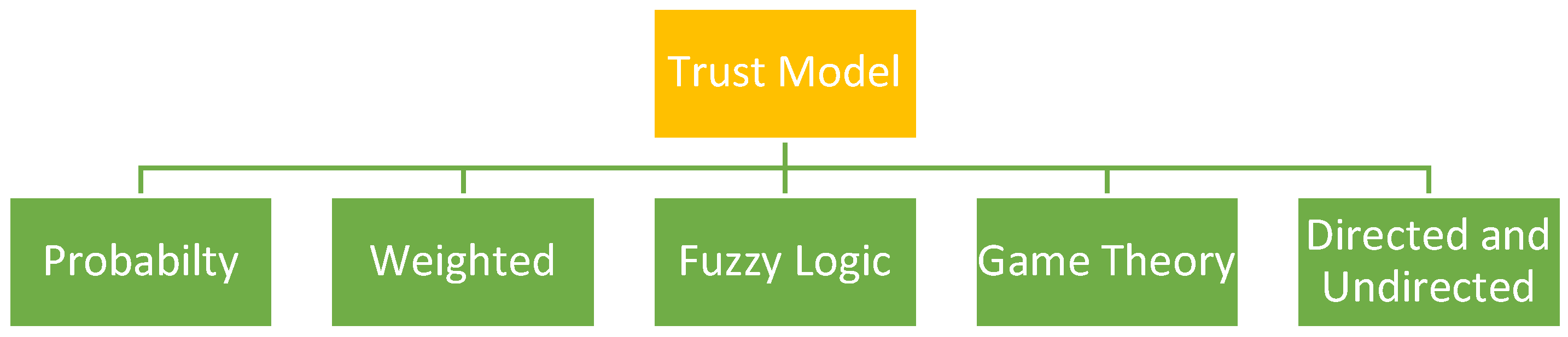


| Feature/Aspect | Probability Trust Model | Weighted Trust Model | Fuzzy Logic Trust Model | Game Theory-Based Trust Model | Directed Graph-Based Trust Models | Undirected Graph-Based Trust Models |
|---|---|---|---|---|---|---|
| Trust Calculation Method | Updates trust based on Bayesian inference; uses past behaviour to adjust trust scores. | Aggregates various trust metrics with weighted importance factors | Uses fuzzy logic to combine various metrics; Trust is determined by fuzzy inference rules | Models trust as a game where nodes interact and adjust strategies based on outcomes | Trust is calculated by summing the weights of incoming edges from other nodes | Trust is calculated based on the average weight of connected edges |
| Inputs Considered | Previous trust values, successful interactions, and total interactions | Metrics like packet forwarding ratio, data reliability, energy levels | Message success rate, elapsed time, correctness, fairness | The payoff, node actions, utility functions | Weights of edges in the directed graph | Weights of edges in the undirected graph |
| Handling of Uncertainty | Incorporates prior probabilities to handle uncertainty | Handles uncertainty by adjusting weights dynamically | Fuzzy logic manages uncertainty by handling imprecise input values | Game theory models interactions under uncertainty and evolves strategies over time | Directly handles asymmetric trust relationships | Handles symmetric trust relationships |
| Applicability | Suitable for scenarios with historical behavior data | Best for networks where multiple trust metrics are relevant | Ideal for networks with complex, multifaceted trust metrics | Effective in dynamic and adversarial environments where strategies evolve | Useful in networks where Trust is not reciprocal or equal between nodes | Applicable in scenarios where mutual Trust is required between nodes |
| Strengths | Adjusts well to new data, incorporates past behaviours | Flexible and adaptable with various trust metrics | Handles complex and vague data inputs effectively | Encourages cooperative behaviour, handles adversarial nodes well | Effective for modelling directed trust relationships | Provides a clear model for mutual Trust in networks |
| Weaknesses | It can be computationally intensive, requires a lot of historical data | Requires careful selection of weights, might be sensitive to metric importance | Complexity in defining fuzzy rules and membership functions | Requires sophisticated modelling, might be complex to implement | May not handle symmetric relationships well | It may not represent asymmetric trust relationships effectively |
| Notation | Description |
|---|---|
| The fundamental trust score of Node I is based on its residual energy relative to a reference energy level. | |
| Normalized trust score of nodes i relative to the maximum residual energy in the network. | |
| The weighted trust score of nodes considers energy-based Trust and additional factors like centrality or mobility. | |
| Updated CH probability for node j based on residual energy and the average residual energy of neighbouring nodes. | |
| Suitability metric for selecting a tentative CH based on residual energy, distance, and CH probability. | |
| A composite metric for selecting the most suitable CH based on energy, distance, and communication cost. | |
| Dynamic trust threshold that adapts based on network conditions and historical data. | |
| The new trust value for Node i at time t was adjusted based on observed actions and initial Trust. |
| S.No. | Parameter | Description | Typical Values or Ranges |
|---|---|---|---|
| 1 | Trustworthiness (TB(xi)) | Range from 0 (untrustworthy) to 1 (fully trustworthy), with thresholds for roles based on value. | > 0.7 for Trust, <0.7 to >0.3 for partial Trust, < 0.3 for untrust |
| 2 | Packet Forwarding Rate (PFR) | Part of PxiF() indicates reliability in forwarding packets; closer to 1 is better. | Close to 1 |
| 3 | Anomaly Factor (AF) | It reflects a deviation from expected behaviour, part of AF(xi); being closer to 0 indicates normal behaviour. | Close to 0 |
| 4 | Residual Energy for CH Selection | Nodes with more than a specified percentage of their initial energy (e.g., > 50%) are eligible for CH selection. | > 50% |
| 5 | Trust Level for CH Selection | Minimum trust level (e.g., > 0.7) required for a node to be considered for CH selection. | > 0.7 |
| 6 | Malicious Threshold (TB(xi)) | Nodes with a trust level below a certain threshold (e.g., < 0.3) are considered malicious and blocked. | < 0.3 |
| 7 | Key Refresh Interval | The frequency of cryptographic key refreshes depends on security requirements (e.g., every 24 hours). | Every 24 hours or as needed |
| 8 | Trust Evaluation Interval | Frequency of trust evaluations, adjusted based on environment stability (e.g., every hour in stable environments). | Every hour to every 10 minutes |
| 9 | New Node Trust Initialization | A neutral initial trust level is assigned to new nodes until enough behavioural data is collected (e.g., 0.5). | 0.5 |
| 10 | Cluster Size Range | Adjustable range based on network density and area, typically 5 to 20 nodes per CH. | 5 to 20 nodes per CH |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).





