1. Introduction
The railroad industry, a crucial backbone of the global supply chain, has been grappling with complex security issues. These complexities are related to the physical infrastructure, human resources, and the intricacies of modern technologies that support modern rail operations. These include Internet-of-Things (IoT) devices, global positioning systems (GPS), and intelligent sensors. For instance, the recent addition of a positive train control (PTC) system has been a critical achievement toward improving safety in this industry [
1]. However, these technologies have also opened new vulnerabilities for potential cyberthreats [
2]. Cybersecurity in rail freight transportation has become crucial because of the industry’s growing dependence on digitalization, connected systems, and automation. For example, malware attacks in the railroad industry have increased by more than 200% globally in the last five years [
3]. Although extant studies have explored several areas of railroad cybersecurity, including signaling [
4] and cryptographic protocols [
5], most of these studies fail to provide a comprehensive perspective on technological, human, and operational risks in railroad cybersecurity. Several of these studies also fail to provide practical mitigation strategies for holistic adaptation. This study aims to bridge this gap by synthesizing findings and recommendations across various domains by offering a comprehensive framework while providing a practical strategy for the growing discourse. Advancing technology in the rail industry heightens the need for robust cybersecurity measures to ensure continuous operations [
6]. In addressing these issues, studies focused on various aspects of cybersecurity practices for the rail freight industry, including sustainability [
7,
8], risk assessment and management [
9], cybersecurity framework [
3], and technology innovation [
10]. The Transportation Security Administration (TSA) recently implemented a new rule for cybersecurity evaluation of the major modes of transportation, including rail freight [
11]. Although this regulation aims to enhance cyber resilience, some industry stakeholders have raised concerns about its implementation and the associated compliance costs [
12].
In the past, transportation security risks mostly stemmed from physical attacks. After 9/11, there was a notable change in focus toward securing transportation systems from potential terrorist threats, leading to comprehensive policies implemented at both national and international levels. This age saw notable advancements in transportation security due to incorporating digital technologies, which brought new vulnerabilities [
13]. The railway industry has encountered difficulties in modifying current safety protocols to effectively manage these cybersecurity threats [
14]. The literature has identified signaling and communication networks in railway systems as being susceptible to a range of cyberthreats. Other studies highlight vulnerabilities in the sector, including malware, wireless attacks, and unauthorized system access [
15]. Initiatives like Shift2Rail [
14] and standards developed by international bodies like the International Organization for Standardization [
16,
17] and National Institute of Standards and Technology [
17,
18] have aimed to enhance cybersecurity resilience in railroad operations. These efforts emphasize the importance of digital security in sustaining operational efficiency and environmental compliance [
19]. Demiridis and Pyrgidis (2022) highlighted the significance of cybersecurity in the rail freight sector for sustainable development [
20]. The study shows the importance of improving essential services in this industry, such as ensuring high reliability and punctuality to increase competitiveness with other modes of transportation. Aminzadegan et al. (2022) highlighted the environmental friendliness of rail as compared with other modes of transportation [
21], making it a priority for government and other policymakers. Rail freight transportation is advancing by integrating digital platforms such as online exchanges [
22], making cybersecurity crucial for protecting data and transactions.
This research provides a comprehensive overview of current cybersecurity practices in the rail freight industry through a combined systematic literature review (SLR) and a bibliometric analysis. This contribution highlights existing gaps and offers new insights to bridge these gaps. These insights will strengthen the rail freight sector’s defenses against current and emerging cyber hazards and open new research opportunities to enhance the industry’s cybersecurity. Given the continuous increase in cybersecurity issues in rail freight transportation, this review provides a multifaceted exploration by answering the following four research questions:
Challenges: What are the primary cybersecurity threats and vulnerabilities identified in rail freight transportation systems?
Measures: How do existing cybersecurity measures address the risks associated with rail freight transportation?
Emerging Trends: What are the emerging trends in cybersecurity technologies and practices for enhancing the safety and security of rail freight transportation?
Innovation: How effective are current cybersecurity practices in mitigating the risk of cyberattacks in rail transportation networks?
The subsequent sections of this paper are as follows.
Section 2 describes the SLR methodology.
Section 3 offers answers to the research questions based on the reviewed literature.
Section 4 discusses the results while offering implications.
Section 5 concludes the SLR, highlighting the gaps identified, limitations, and recommendations for future research.
2. Methodology
Undertaking a literature review is a complex process, with many methods available to compare and contrast the knowledge and gaps in existing literature for a particular set of research questions. These methods range from a traditional literature search, forward or snowball sampling of systematic reviews, and meta-analysis to distill trends. However, the most common contemporary guideline used is the “preferred reporting items for systematic reviews and meta-analyses” (PRISMA), which provides a degree of standardization as compared with others [
23]. The authors chose the SLR method over others like narrative, critical, and theoretical reviews for its ability to minimize bias and limitations [
24]. The SLR methodology along with the PRISMA checklist systematically identifies research gaps and provides a comprehensive and transparent review approach to evidence synthesis [
25]. The PRISMA method comprises 27 items across seven sections, which this study divides into four stages: the pre-literature collection, literature (publication) selection, systematic review, and data analysis. The authors selected PRISMA to ensure rigor and minimize biases in synthesizing a comprehensive analysis of existing studies. By following the structured stages, the study identifies critical gaps in railroad cybersecurity literature by integrating a comprehensive overview of relevant studies and narrowing it down to the ones that address the above research questions.
2.1. SLR Workflow
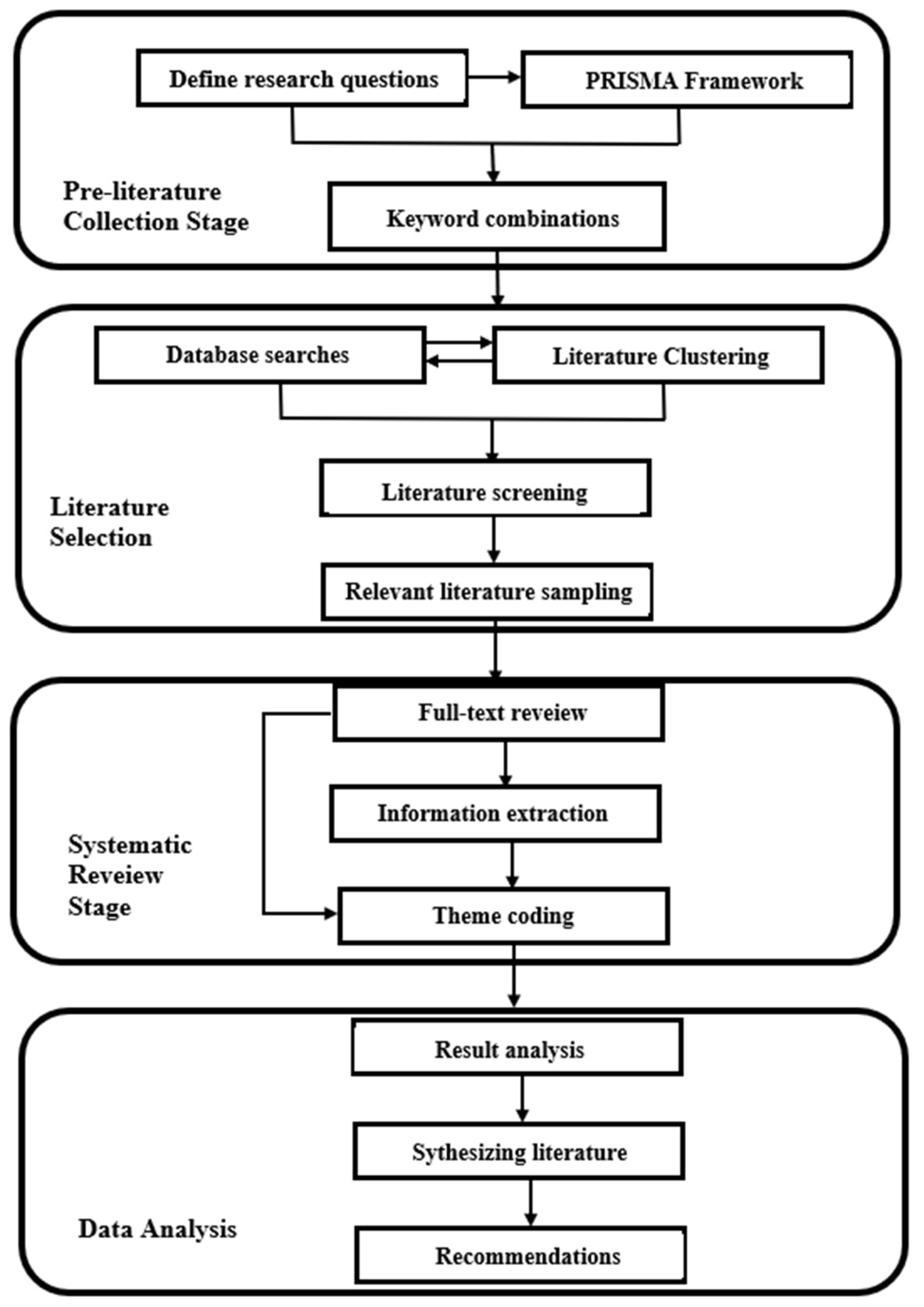
Figure 1 illustrates the framework developed in this study for the SLR.
The main stages were as follows:
Pre-literature collection: Define the research questions, and their aim and scope. State the specific methodology or tools incorporated. This stage followed the PRISMA framework, which uses combinations of keywords and search phrases to produce potentially relevant results.
- 5.
Literature selection: Conduct an electronic search of different databases using the defined search phrases that focus on the scope of the study. Screen the search results to eliminate irrelevant literature based on titles, abstracts, publication dates, language, keywords, and other criteria.47
- 6.
Systematic review: Analyze the full text of relevant studies and classify the corpus based on the research questions and themes for further analysis.
- 7.
Data analysis: Interpret the analysis by comparing and contrasting the literature analyzed.
2.2. Pre-literature Collection Stage
This stage focused on identifying literature that addresses the four core research questions: challenges, protective measures, emerging trends, and innovations in cybersecurity within rail transportation. The research questions were critical in shaping the scope, emphasizing cybersecurity in the rail freight industry. The literature search included only journal and conference papers to ensure an elevated level of rigor.
Following the PRISMA framework, this stage carefully selected keywords and search phrases to target literature directly aligned with the study’s scope. The search strategy aimed to encompass a broad range of relevant studies while systematically narrowing the results to those that best addressed the research questions. The authors then evaluated each identified source for its contribution to understanding the unique cybersecurity concerns in rail freight, as well as the industry’s adaptation to emerging threats and technologies. This approach ensured a focused and comprehensive set of literature for the analysis, emphasizing both breadth and depth in addressing the complexities of rail freight cybersecurity.
2.3. Literature Selection
Guided by the research questions, the authors developed Boolean search commands to narrow the literature search and focus on relevant publications. The central premise for selecting relevant literature was to include scope for both rail freight transportation and the implementation of cybersecurity practices. Hence, the selected keywords and Boolean operators were (“rail freight” OR “railway security” OR “train transportation”) AND (“cybersecurity” OR “cyberattacks” OR “cyber resilience” OR “cybersecurity practices”). The authors also considered regional variations of key words. For example, “train transportation” and “rail transportation” refer to the same scope reviewed in this study. The searches utilized the Google Scholar search engine and two databases: Web of Science and Science Direct. The authors selected these databases because they encompass a broad spectrum of interdisciplinary studies.
Table 1 summarizes the Boolean search commands and results from each tool. Search criteria included language, publication year, accessibility to text, uniqueness, and publication type.
Table 2 summarizes the categories and criteria considered for the selected publications. The authors excluded reports that did not address the research questions.
2.4. Bibliometric Assessment
The bibliometric analysis assessed the temporal and geographic distribution of the selected body of literature to gain insights into the trends of discourse in railroad cybersecurity. The authors also utilized the NVivo software (version 14) [
26] to categorize articles by analyzing their full text for relevance to the research questions, and to provide visualizations by a word cloud. The software provided a visualization of key terms, emphasizing gaps in extant studies. The authors also utilized the VOSviewer software (version 1.6.20) to visualize co-occurrence networks of important terms and concepts extracted from the selected body of literature [
27]. The visualizations included term co-occurrence from the titles and abstracts to highlight the bibliographic coupling of key themes and concepts. Hence, the bibliographic networks provided a qualitative assessment and validation of the subject matter focus in the selected literature, highlighting the effectiveness of the SLR workflow and screening.
3. Results
The subsections that follow present the results of the literature screening, the bibliometric analysis to visualize and validate the screening results, and an assessment of the findings with respect to addressing the four research questions, and an evaluation of current industry practices.
3.1. Literature Screening
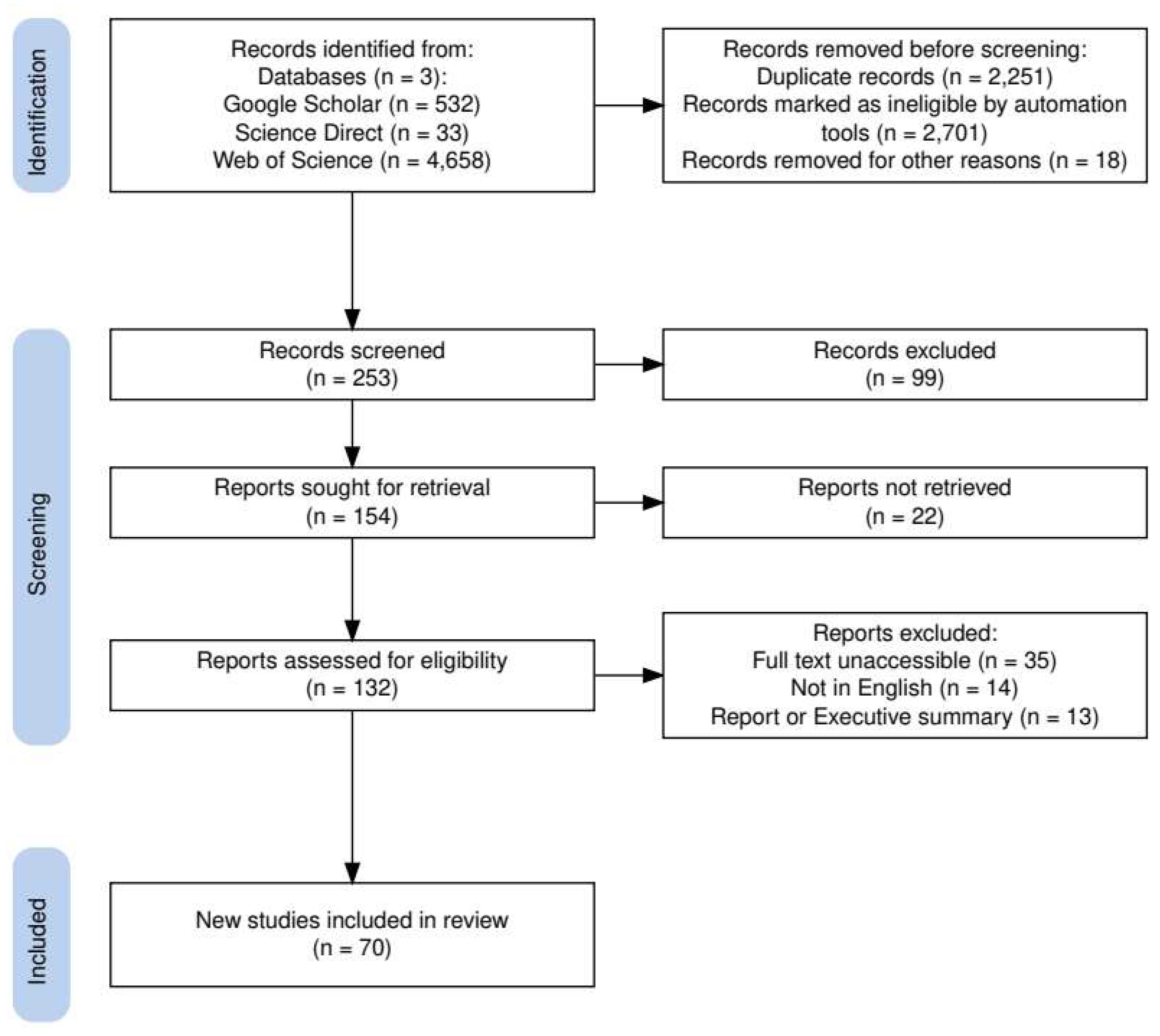
Figure 2 shows the results of the PRISMA workflow. The initial search yielded 5,223 studies across Google Scholar, Science Direct, and Web of Science. This result included peer-reviewed journal articles and conference papers from January 2017 to November 2024. To streamline the search for all the databases, the authors utilized the “refine function” for each database to limit the literature search to only journal and conference articles. Applying the inclusion and exclusion criteria in
Table 2 reduced the relevant studies to 253 for further scrutiny. The initial screening phase identified and removed 2,251 duplicates and excluded an additional 2,701 studies that focused solely on either cybersecurity or rail freight transportation, without addressing both areas.
The authors removed an additional 18 studies because the abstracts and keywords did not align with the research area. Of the 253 articles screened, 99 studies lacked comprehensive data on cybersecurity framework in rail freight transportation, leaving 154 articles for further analysis. There were additional exclusions based on full text unavailability—some of the studies had only their abstracts in English with the full text in other languages, and some studies were not journal or conference papers. The final review yielded 70 articles.
3.2. Bibliometric Analysis
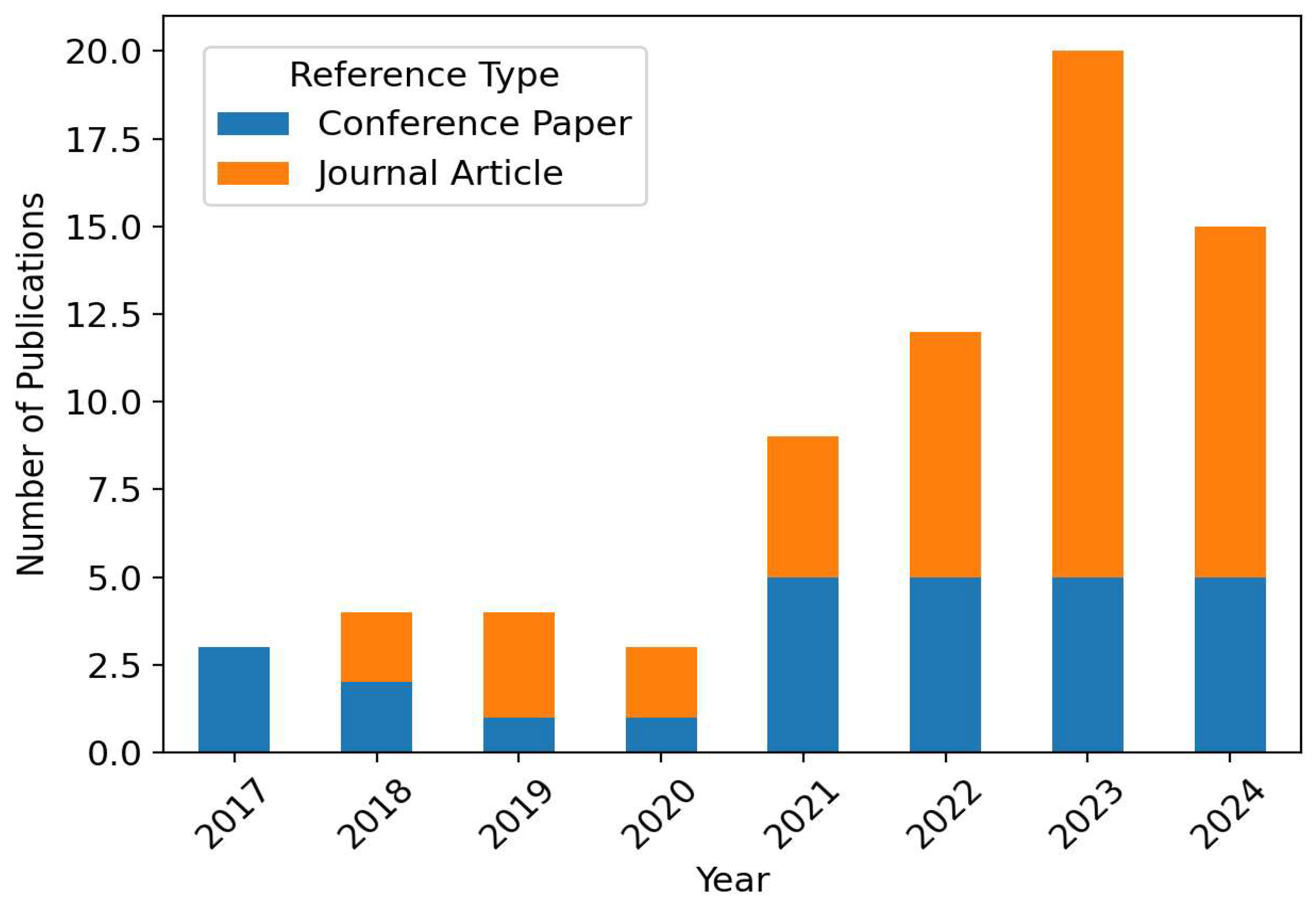
Figure 3 shows the temporal distribution of the publications. The number of publications steadily increased throughout the years, peaking in 2023. This reflects a growing trend in the integration of digital systems and autonomous operations in transportation, which has in turn increased vulnerability to cyber threats.
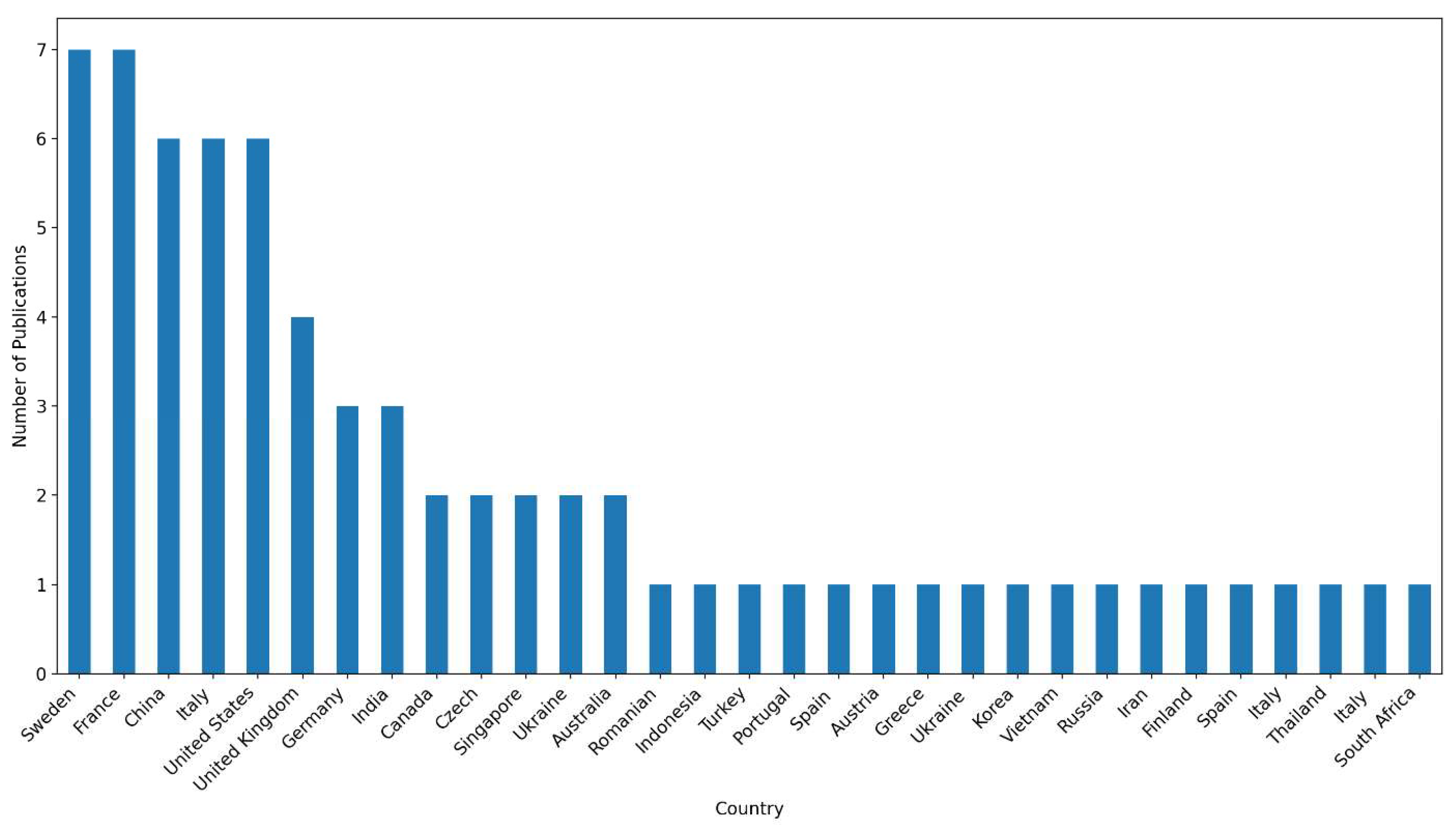
Figure 4 shows the publication distributions by country. Sweden and France had the most publications on the topic, followed by Italy, the United States, and China. This reflects Sweden and France taking a lead role in railway cybersecurity research, stemming from Europe’s continual investments in projects like Shift2Rail [
14]. The Shift2Rail initiative is essential as it employs blockchain technology to ensure the security of data communication within rail systems. Nonetheless, the initiative does not adequately represent other regions like Africa and various areas in Asia, even as they increasingly embrace railroad infrastructure. This geographical disparity results in a significant oversight for these areas, largely attributed to limited resources, ineffective regulatory structures, or a deficit in understanding how to address intricate cybersecurity challenges within the railroad industry. In order to bridge this gap, there is a need for information that highlights a comprehensive approach to integrating technological innovation with operational strategies for effective policy implementations. Relevant studies highlighted in this study, therefore, aim to address advanced cybersecurity practices across diverse economies and infrastructure.
Figure 5 shows a word cloud of the most frequently used terms in the selected corpus where the font size reflects their relative count. This word cloud validates the quality of the literature selection with the most frequent words being “railway,” “train,” “system,” “safety,” “attacks,” “cybersecurity,” and “security.”
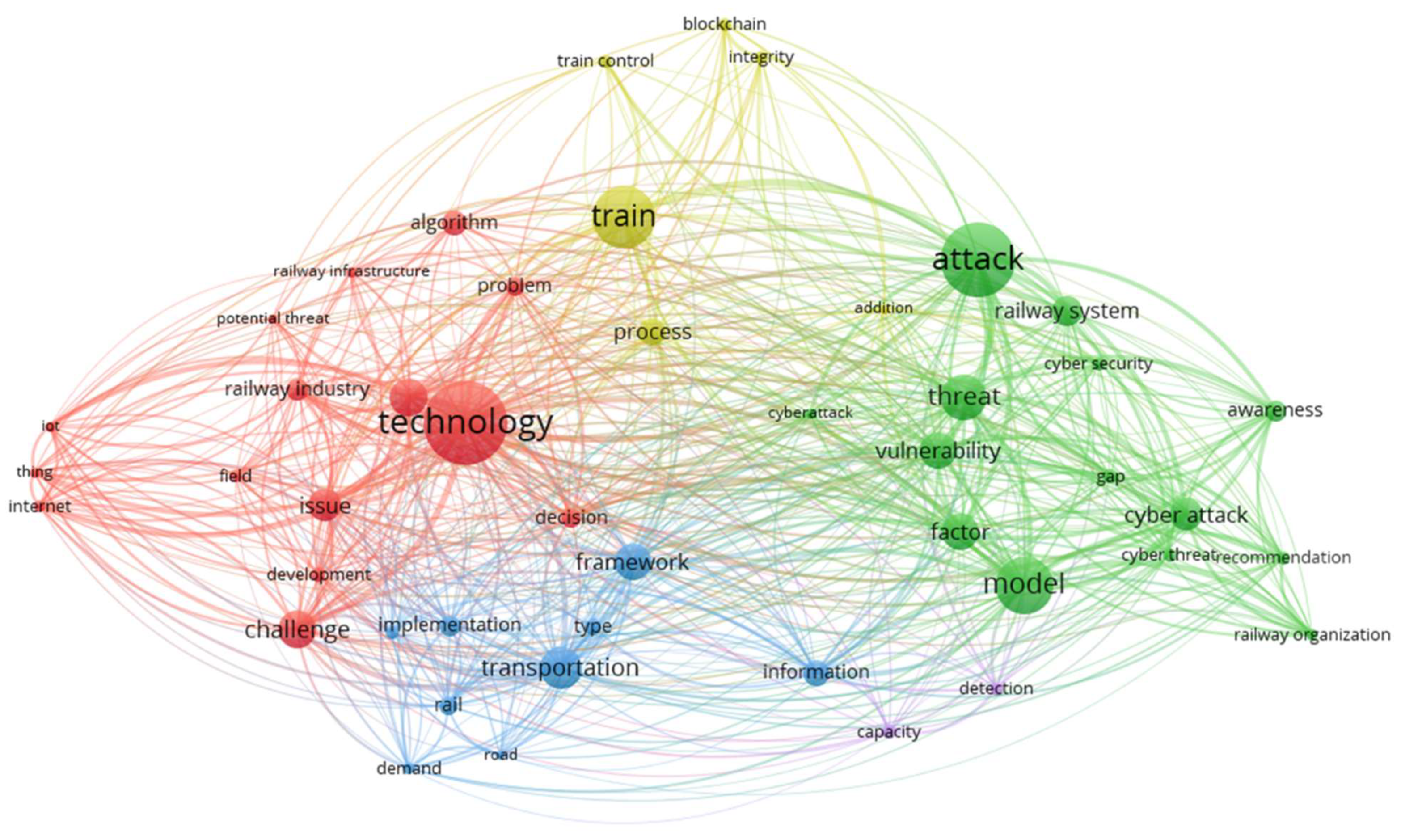
Figure 6 shows the term co-occurrence network. The size of the circles represents the relative frequency of the term in the corpus. The thickness of the lines connecting terms represents the relative frequency of their co-occurrence in the corpus. The distinct colors represent cluster terms based on their co-occurrence and relationship within document subsets.
These clusters represent thematic areas in the field. The largest cluster in red color, centered on “technology,” emphasizes the pervasive role of technological advancements in addressing cybersecurity issues in rail freight systems. The other prominent cluster in green color focus on “threat,” “attack,” and “vulnerability,” indicating concentrated research on vulnerabilities, cyberattacks, and operational impacts. Terms in the blue cluster like “transportation,” “framework,” and “implementation” reflect ongoing efforts to develop strategic and analytical approaches to mitigate risks in transportation systems. The connections among clusters demonstrate the interdisciplinary nature of cybersecurity, linking technological innovation with operational and strategic measures. This visualization highlights critical research areas and interdependencies, offering insights into emerging trends and gaps in the field.
Table 3 classifies representative studies into the five categories and 12 themes shown.
3.3. Types of Cyberattacks in the Rail Industry
There were 23 articles that focused on the types of cyberattacks common in the rail freight industry. The authors categorized them into five main types: anomaly detection, phishing, software vulnerability, malware, and denial of service, as shown in
Table 4. Identifying the type of cyberattack is the first step in fully understanding the mitigation strategy to implement. All the studies asserted that these types of cyberattacks pose vulnerability to railroad operations. Even though various organizations have implemented numerous mitigation strategies, attackers often find other ways to disrupt operations [
17]. Even though all these attacks increase vulnerability in the rail freight industry, their severity level differs [
37].
Based on an analysis of 1,496 security breaches within a railway infrastructure from January to April 2021, the authors concluded that denial-of-service, phishing, and malware were the most frequent attack types, accounting for over 40% of incidents. Malware and denial-of-service attacks affected operational systems, leading to delays [
76]. For instance, in 2016, the San Francisco rail system experienced a ransomware attack where passengers could ride for free [
77]. In October 2017, a distributed denial of service (DDoS) attack targeted Sweden's transportation network, causing a system failure to track rail locations, which led to disruptions in road traffic maps [
78]. These incidents underscore the importance of implementing layered defense strategies that include anomaly detection and training programs for employees to reduce these risks effectively. Phishing was by far the most common type of cyberattack in the rail freight industry [
79], with five of the 23 papers discussing it. Such attacks involve sending deceptive emails to employees to gain unauthorized access to sensitive information within the business or sector. Some articles also highlighted other attack types, such as SQL injection, watering holes, cross-site scripting, malware, and brute force [
17]. Despite phishing being the predominate type of attack in the railroad industry, affecting more of the recorded incidents in the sector [
76], most of the suggested mitigation strategies focus on attack detection and network vulnerabilities rather than a layered strategy that combines real-time anomaly detection and awareness tailored to bridge the gap of human contribution to those risks. This disparity highlights a critical gap the study seeks to address.
3.4. Challenges of Cybersecurity in the Rail Industry
Research question 1 focused on different themes for the types of cyberattacks commonly reported in the rail freight industry, the vulnerability of the railway systems, and the risk assessment methodologies currently implemented to mitigate these challenges. The increase in automation across the transportation industry hinges on the reliance on digitalization and connectivity. While this initiative offers to increase efficiency and reduce cost, these systems become more vulnerable to cyberattacks. With the constant evolution of technology, the rail industry has evolved significantly from using coal-powered steam locomotives to integrating sophisticated technologies like PTC, reflecting significant technological advancements [
1].
Seventeen of the relevant papers focused on network vulnerabilities in the rail freight industry. The studies asserted that the use of wireless communications makes these systems vulnerable to cyberattacks [
5,
28,
82]. For example, Kiviharju et al. (2022) highlighted the need for an extensive evaluation of the communication systems in the European Rail Traffic Management System [
5]. In addressing the issue of vulnerabilities in this industry, the authors identified three broad categories of vulnerabilities: (1) operational, (2) technical, and (3) interconnected.
Table 5 characterizes the distinct types of vulnerabilities with their corresponding relevant studies. For example, while acknowledging the railway systems as a critical infrastructure in the transportation industry, Chan (2022) discussed the operational vulnerabilities within the sector [
83]. On the other hand, Gaggero et al. (2024) highlighted the technical vulnerability within the industry, focusing on infrastructure attacks, especially the communication network [
29]. The authors concluded by highlighting the gaps within the wireless communication industry. Soderi et al. (2023) highlighted that some of the vulnerabilities exist due to the industry’s lack of a safety and security mindset during the manufacturing process [
4]. Kour et al. (2020) highlighted the importance of becoming aware of attacks and vulnerabilities when evaluating cybersecurity programs in the rail freight industry [
17].
Many relevant studies have presented steps for implementing risk assessment in the rail freight industry. Rekik et al. (2018) presented critical steps in assessing risks for train control and monitoring systems: (1) identification of critical assets, (2) assessing their vulnerabilities to cyberattacks, and (3) evaluating their likelihood and consequences of an attack [
2]. The industry has also utilized tools like simulation and predictive models to assess potential cyberattack scenarios. For example, Kour et al. (2020) adopted the cyber kill chain model in a simulation scenario to assess potential cyberattacks [
76]. The authors iterated the seven stages of this model developed by Lockheed Martin (2009), focusing more on the initial stages. Most studies asserted that the assessment should consider the cyber-physical nature of the constant evolution of technological advancements in rail freight systems to address the need for a cross-domain threat.
3.5. Risk Management in the Rail Industry
Research question 2 focused on existing cybersecurity measures in the rail freight industry through the lens of security frameworks and their components. The studies analyzed presented a broad range of mitigation methodologies for addressing risks in the rail freight industry. Each method presented a different approach to distinct types of cyberattacks. Each measure attempted to address an existing cyber security issue or to simulate a cyberattack. The authors delineated these measures into soft and hard strategies to reflect prevalent strategies implemented in the field. Soft strategies encompass measures that do not necessitate infrastructural changes but involve alterations in human training and operational methodologies within the rail freight industry. These strategies include training programs, adopting operational practices, and implementing regulations and standards. An example of a soft strategy is the new TSA regulation [
11] implemented to help safeguard the transportation sector, including the railroad industry, against cyber-related disruptions. Conversely, hard strategies involve measures that require modifications to the physical infrastructure, such as upgrading security systems, enhancing network infrastructure, and implementing real-time monitoring systems and robust cyber-physical systems.
More than half of the studies suggested a soft strategy approach to address various rail freight industry risks. A significant body of literature highlighted the importance of continuous employee training as a cornerstone of cybersecurity. Thaduri et al. (2019) highlighted the shift toward digitalization in the rail freight industry [
7]. They hinted at various soft strategies such as human factor training, policy development and compliance, information sharing and collaboration, incident response and management, and continuous auditing to protect sensitive information within the railway freight industry. Thron et al. (2024) recommended a dynamic strategy for educating employees on cybersecurity [
36]. Rekik et al. (2018) implied undertaking a comprehensive threat landscape assessment like the one proposed in the ROLL2RAIL project to determine unmitigated cyber risks [
2]. The other half of the studies adopted the hard strategies approach. The most common strategy was an improved firewall and intrusion detection system, which is essential for early detection within the systems [
28,
82,
83]. Overall, the rail freight industry can enhance its defenses against cyberattacks by conducting cyber-physical security risk assessments and implementing customized security measures.
3.6. Emerging Trends in the Rail Freight Industry
This section focuses on research question 3 to explore trends in network security management and future directions in rail cybersecurity. This industry is evolving rapidly by integrating modern technologies and methods to improve safety and cybersecurity. For example, electric-powered trains are emerging to establish greener, more energy-efficient rail freight systems [
86]. Enhancing cybersecurity awareness and providing training is crucial for increasing the reliability and robustness of railway systems, emphasizing the beneficial influence of a cybersecurity culture in businesses [
17]. The emergence of Industry 4.0 has also assisted in the convergence of information technology in the railway industry, resulting in reliability and operational efficiency [
57]. The evolution of technology in the rail freight industry has warranted constant reliance on communication systems for signaling, thereby creating growing concerns due to system vulnerabilities [
87]. Therefore, in ensuring rail freight transportation safety, there should be comprehensive traffic management within the networks in addition to infrastructure management [
88]. Another emerging technology is the use of blockchains to provide a decentralized security framework in managing transactions, improving reliability and data distribution across various networks and components [
45]. Adopting a zero-trust architecture (ZTA) is another emerging model in the rail freight industry to ensure strict access and continuous authentication to minimize inside threats and cyberattacks [
89]. There has been a significant shift toward predictive strategies where systems are proactive to threats and provide mitigation strategies based on patterns and modern technology [
17]. Overall, the future of rail freight transportation should incorporate sustainable practices and advanced technologies while simultaneously adopting relevant cybersecurity measures.
3.7. Current Practices in the Rail Freight Industry
This section explores research question 4 in terms of the extent that current cybersecurity practices mitigate cyberattack risks in rail transportation and research gaps. As a recurring theme, the reviewed studies described the constant evolution of technology as a significant contributing factor to cyber vulnerability in the rail freight industry. For example, Kour et al. (2019) asserted that the increased vulnerability of railroads to cyberattacks stems from the integration of advanced technologies during maintenance processes [
57]. Falahati and Shafiee (2022) discussed the use of machine learning algorithms and fuzzy logic systems in detecting and responding to cyberattacks in rail freight transportation [
60]. Likewise, Singh et al. (2021) highlighted the implementation of advanced cybersecurity measures in autonomous rail operations to safeguard communication systems and operational data [
30]. Thaduri et al. (2019) shed light on the importance of comprehensive training programs as a risk mitigation tool [
7].
4. Discussion
The subsections that follow link the original research questions to the themes exposed in the results for a comprehensive understanding of cybersecurity in the rail freight industry.
4.1. Assessment of Rail Freight Mitigation Strategies
Numerous studies argued that due to the constant evolution of technology within the railway industry, a continuous and adaptive cyber mitigation strategy is essential. This suggests the need to cross-integrate some cyber assessment strategies from other sectors to tackle the issue within the railway industry. Stakeholders within the railway industry must explore benchmark practices within adjacent industries such as aviation and connected vehicles using vehicle-to-anything communications and adapt their strategies. This adoption becomes especially crucial with a greater reliance on automation, control, and communications technology to improve safety and security. Using a robust quantitative approach such as predictive models for multi-stage cyberattack simulation can be effective [
76]. Another key strategy is cybersecurity awareness and training. Railroads can cultivate a cyber hygiene culture [
32], especially where employees maintain the security and integrity of digital systems and data [
90]. This practice has been in the healthcare sector and other areas, and it has been beneficial in safeguarding sensitive electronic information [
91,
92]. Additionally, stakeholders within the railway sector should leverage technologies such as blockchains to enhance the security and integrity of their transactions [
93].
4.2. Technological Adaptation in the Rail Industry
It is evident that technological evolution is crucial in streamlining processes in the rail industry. These technological solutions will require continuous human improvement and education, organizational measures and methodologies, and improved digitalization with advanced networks. Human improvement should emphasize dynamic, scenario-based programs that replicate real-world issues, promoting a proactive cybersecurity culture within the workforce. The rail freight industry has begun adopting a ZTA to build a reliable system that combats ambiguous security boundaries within a complex network. For instance, Feng et al. (2023) proposed a theoretical use of blockchains and the Merkle tree [
89]. ZTA has demonstrated its effectiveness in implementing stringent authentication measures and restricting unauthorized access to a network by continuously verifying access requests. However, the practical implementation of this approach may result in significant challenges, including regulatory compliance, human factors, inherent security concerns, and interoperability. To effectively implement ZTA, the industry must develop targeted strategies to minimize potential risks. There will be a need for constant skills development, hands-on training, and real-life experiences through optimal training delivery methods. This research highlights the need to expand the use of the ZTA to more effectively align with predictive models, including AI-based real-time threat assessment and blockchain-supported decentralized data exchange. These improvements would bolster the resilience of rail systems, especially in tackling emerging threats within interconnected networks.
4.3. Mitigating Cybersecurity Gaps in Rail Freight
This section highlights plausible recommendations to fill strategic gaps within the rail freight industry regarding cybersecurity. A permanent solution in cybersecurity is impossible because threats continuously evolve. Hence, implementing fewer targeted strategies to enhance cybersecurity measures may improve efficiencies. In addressing the issue of human errors, the deployment of autonomous trains could be a significant step in improving safety in the rail industry [
30]. However, this also comes with a significant risk as autonomous systems possess different vulnerabilities within the rail network due to their interconnectedness for real-time information access. This may require advanced encrypted techniques to mitigate potential threats. Combining advanced technological strategies and taking a proactive organizational approach can significantly enhance the industry’s resilience against cyber threats.
4.4. Enhancing Cybersecurity Resilience in Rail Freight
Existing works on cybersecurity in the rail freight industry have focused on balancing operating efficiency and incorporating advanced technology. This review highlights the significance of maintaining a robust security framework to accommodate technological changes that avoid operation disruptions [
29,
35,
60,
83]. The theoretical work of Thron et al. (2024) highlighted the balance between human factors and cybersecurity risks [
36]. The study highlighted that many industries, including the aviation sector, also face similar challenges in balancing automation and human error [
94]. In particular, ongoing human resource training and development initiatives are necessary to reduce human error, which is a severe cybersecurity vulnerability. Furthermore, utilizing advanced technology for threat detection and response, such as machine learning and artificial intelligence, can aid in addressing changing cybersecurity issues [
60]. Current research indicates that collaboration and information sharing among stakeholders significantly improves cybersecurity in the rail industry [
93]. International cooperation and public-private partnerships can enhance the exchange of threat intelligence and best practices.
While soft strategies like human training may provide a more economical approach, their potential for scalability and long-term effectiveness has yet to be evaluated. On the other hand, hard strategies, such as firewalls and anomaly detection systems, tackle technical risks but do not provide solutions for mitigating human-centric threats like phishing. The railroad industry needs to learn from related sectors that emphasize the use of predictive analytics. For optimal effectiveness, blockchain-enabled decentralized data sharing should support these frameworks to improve resilience across interconnected networks while responding to ongoing technological advancements.
Recommendations for Policymakers
Improving cybersecurity measures in the railroad sector demands specific approaches that involve all parties, including policymakers and industry practitioners. They are essential in developing the regulatory framework and securing the funding to tackle various issues, such as cyber threats. As a result, governance must implement compulsory cybersecurity regulations while ensuring that current policies are adhered to. Frameworks such as ISO 27001 or NIST should be adopted in countries with a limited understanding of railroad cybersecurity. This will help maintain consistency among operators and ensure adherence to international best practices [
18,
49]. As mentioned earlier, incorporating Zero Trust Architecture (ZTA) [
60,
89] is essential for improving overall authentication and access management while reducing the likelihood of security breaches.
Public-private partnership between rail operators, cybersecurity firms, and academicians can foster innovation. The Shift2Rail initiative [
14,
40] serves as a successful example of how collaboration can effectively tackle cybersecurity issues in the railway sector, demonstrating its ability to address vulnerabilities within rail systems. In order for all the proposed strategies to be successful, policymakers must also budget for innovation in this area. Innovative technologies like AI-driven predictive analytics [
76] and blockchain data structures [
45] have demonstrated effectiveness in tackling cybersecurity issues, so it is essential to allocate specific funds for their implementation.
The authors accounted for both scalability and collaboration to guarantee the effective execution of these recommendations. The strategies proposed in this study are flexible for rail operators of different sizes and they are also combinable with other models to tackle the challenge of interoperability. Given that the railroad industry consists of interconnected systems, many of the proposed strategies and recommendations are relevant for achieving unified global standards and minimizing regional disparities.
5. Conclusions
This work summarized the research on cybersecurity practices in the rail freight industry by focusing on the growing literature published in peer-reviewed journals and conference papers. To focus the review, the authors posed four research questions within the following categories: (1) challenges, (2) measures, (3) emerging trends, and (4) cybersecurity practices. The study collated findings from 70 relevant peer-reviewed articles and conference papers. In addressing the first research question, the study highlighted that technological evolution and human error significantly impact cybersecurity practices. Technological evolution in the rail freight industry revolves around the increasing utilization of advanced digital systems to improve operational efficiency and safety. On the other hand, the literature attributes human error to insufficient training, a lack of situational awareness, and the complexities of managing recent technologies.
The review identified common threats such as anomaly detection, phishing, software vulnerabilities, malware, and denial-of-service categorized into operational, technical, and interconnectedness vulnerabilities. The second research question focused on measures implemented to enhance cybersecurity, differentiating between hard strategies, which involve physical infrastructure changes, and soft strategies focusing on operational and training adjustments. The third research question addressed emerging trends, including automation, zero-trust architecture, blockchain, and machine learning, highlighting concerns over system vulnerabilities due to technological advancements. The research emphasized current cybersecurity practices and their effectiveness in risk reduction.
The authors identified obstacles and recommendations for future research, including the need for standardized cybersecurity protocols, investment in human resources, and stakeholder collaboration for sharing best practices and threat intelligence. Despite these strategies, uncertainty remains about whether specific strategies will effectively address ongoing cybersecurity challenges in the rail freight industry and how to best coordinate these strategies with technological functions.
Despite these developments, research must fill substantial gaps. For example, there is a need for additional investigation into integrating cybersecurity measures with existing operational technology and information technology systems while maintaining seamless functionality. Additionally, establishing a unified defense mechanism necessitates the development of standardized cybersecurity protocols specifically designed to meet the unique requirements of the rail industry.
This study also emphasized the importance of taking a proactive and unified approach to cybersecurity in the railroad sector, highlighting the need to address technical and human-related vulnerabilities. The swift development of technology and changing industry trends present substantial opportunities and challenges for cybersecurity within the rail freight industry. This research highlights various potential areas for future investigation that aim to fill existing gaps in the literature and prepare for anticipated emerging threats. Future research should aim to create adaptable frameworks that blend AI-powered predictive tools, which are gradually becoming the foundation of cybersecurity mitigation strategies across industries, with established cybersecurity standards, especially in regions often underrepresented. Policymakers and industry stakeholders should make these initiatives a priority to protect global rail systems from emerging cyber threats, ensuring the safety of critical supply chains, and promoting sustainable development around the world.
Funding
This research received funding from the United States Department of Transportation, Center for Transformative Infrastructure Preservation and Sustainability (CTIPS), Funding Number 69A3552348308.
Data Availability Statement
This article includes the data presented in the study.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- U.S. DOT, "PTC Communications: Cybersecurity Technology Review and Concept of Operations," Washington, 2023.
- Rekik, M.; Gransart, C.; Berbineau, M. Cyber-physical Threats and Vulnerabilities Analysis for Train Control and Monitoring Systems. 2018 International Symposium on Networks, Computers and Communications (ISNCC). LOCATION OF CONFERENCE, ItalyDATE OF CONFERENCE; pp. 1–6.
- Soderi, S.; Masti, D.; Lun, Y.Z. Railway Cyber-Security in the Era of Interconnected Systems: A Survey. IEEE Trans. Intell. Transp. Syst. 2023, 24, 6764–6779. [Google Scholar] [CrossRef]
- Soderi, S.; Masti, D.; Hämäläinen, M.; Iinatti, J. Cybersecurity Considerations for Communication Based Train Control. IEEE Access 2023, 11, 92312–92321. [Google Scholar] [CrossRef]
- Kiviharju, M.; Lassfolk, C.; Rikkonen, S.; Kari, H. A Cryptographic and Key Management Glance at Cybersecurity Challenges of the Future European Railway System. 2022 14th International Conference on Cyber Conflict: Keep Moving! (CyCon). LOCATION OF CONFERENCE, EstoniaDATE OF CONFERENCE; pp. 265–284.
- Woodburn, A. Rail network resilience and operational responsiveness during unplanned disruption: A rail freight case study. J. Transp. Geogr. 2019, 77, 59–69. [Google Scholar] [CrossRef]
- Thaduri, A.; Aljumaili, M.; Kour, R.; Karim, R. Cybersecurity for eMaintenance in railway infrastructure: risks and consequences. Int. J. Syst. Assur. Eng. Manag. 2019, 10, 149–159. [Google Scholar] [CrossRef]
- P. Singh, Z. P. Singh, Z. Elmi, V. K. Meriga, J. Pasha and M. A. Dulebenets, "Internet of Things for sustainable railway transportation: Past, present, and future," Cleaner Logistics and Supply Chain, vol. 4, 2022.
- Wang, Z.; Liu, X. Cyber security of railway cyber-physical system (CPS) – A risk management methodology. Commun. Transp. Res. 2022, 2. [Google Scholar] [CrossRef]
- López-Aguilar, P.; Batista, E.; Martínez-Ballesté, A.; Solanas, A. Information Security and Privacy in Railway Transportation: A Systematic Review. Sensors 2022, 22, 7698. [Google Scholar] [CrossRef] [PubMed]
- Freight Waves, "TSA proposes new cybersecurity rule for some railroads, other transit systems," 07 11 2024. [Online]. Available: https://www.freightwaves.com/news/tsa-proposes-new-cybersecurity-rule-for-some-railroads-other-transit-systems. [Accessed 12 11 2024].
- The Record, 24 September 2024. [Online]. Available: https://therecord.media/railroad-cyberthreats-tsa-regulations. [Accessed 13 November 2024].
- Newton, A. Multimodal transport security: Frameworks and policy applications in freight and passenger transport. Secur. J. 2016, 30, 328–330. [Google Scholar] [CrossRef]
- Masson and, C. Gransart, "Cyber security for railways-a huge challenge-Shift2Rail perspective," in International Workshop on Communication Technologies for Vehicles, Cham, 2017.
- THALES, "Cybersecurity for Rail," . [Online]. Available: https://www.thalesgroup.com/en/worldwide/transport/news/cybersecurity-rail. [Accessed 8 February 2024]. 18 October.
- J. Prochazka, P. J. Prochazka, P. Novobilsky, D. Prochazkova and T. Kertis, "Certification Cycles of Train Cyber Gateway," in Proceedings of the 29th European Safety and Reliability Conference (ESREL), 2020.
- R. Kour, R. R. Kour, R. Karim and A. Thaduri, "Cybersecurity for railways – A maturity model," Proceedings of the Institution of Mechanical Engineers, Part F: Journal of Rail and Rapid Transit, vol. 234, no. 10, pp. 1129-1148, 4 2020.
- Bellini, E.; Marrone, S.; Marulli, F. Cyber Resilience Meta-Modelling: The Railway Communication Case Study. Electronics 2021, 10, 583. [Google Scholar] [CrossRef]
- Szyliowicz, J.; Zamparini, L. Freight transport security and the robustness of global supply chains. Transp. Rev. 2022, 42, 717–724. [Google Scholar] [CrossRef]
- Demiridis, N.; Pyrgidis, C. Getting freight trains back on track–How railway undertakings, infrastructure owners and regulators can navigate the main dilemmas in freight business to drive sustainable growth. Front. Sustain. 2022, 3. [Google Scholar] [CrossRef]
- Aminzadegan, S.; Shahriari, M.; Mehranfar, F.; Abramović, B. Factors affecting the emission of pollutants in different types of transportation: A literature review. Energy Rep. 2022, 8, 2508–2529. [Google Scholar] [CrossRef]
- Jain, A.; van der Heijden, R.; Marchau, V.; Bruckmann, D. Towards Rail-Road Online Exchange Platforms in EU-Freight Transportation Markets: An Analysis of Matching Supply and Demand in Multimodal Services. Sustainability 2020, 12, 10321. [Google Scholar] [CrossRef]
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. The PRISMA 2020 statement: an updated guideline for reporting systematic reviews. Syst. Rev. 2021, 10. [Google Scholar] [CrossRef]
- Tranfield, D.; Denyer, D.; Smart, P. Towards a Methodology for Developing Evidence-Informed Management Knowledge by Means of Systematic Review. Br. J. Manag. 2003, 14, 207–222. [Google Scholar] [CrossRef]
- Grant, M.J.; Booth, A. A typology of reviews: an analysis of 14 review types and associated methodologies. Health Inf. Libr. J. 2009, 26, 91–108. [Google Scholar] [CrossRef]
- NVivo, QSR International, 2024. [Online]. Available: https://lumivero.com/product/nvivo/.
- N. J. v. Eck and L. Waltman, "VOSviewer," Leiden University, . [Online]. Available: vosviewer.com. [Accessed 30 June 2024]. 1 July.
- Miller, N.; Satsrisakul, Y.; Faist, K.; Fehling-Kaschek, M.; Crabbe, S.; Poliotti, M.; Naderpajouh, N.; Setunge, S.; Ergün, S.; Kanak, A.; et al. A Risk and Resilience Assessment Approach for Railway Networks. Proceedings of the 31st European Safety and Reliability Conference. LOCATION OF CONFERENCE, COUNTRYDATE OF CONFERENCE; pp. 2071–2078.
- Gaggero, G.B.; Marchese, M.; Girdinio, P. A survey on wireless-communication vulnerabilities of ERTMS in the railway sector. J. Surveillance, Secur. Saf. 2024, 5, 52–61. [Google Scholar] [CrossRef]
- Singh, P.; Dulebenets, M.A.; Pasha, J.; Gonzalez, E.D.R.S.; Lau, Y.-Y.; Kampmann, R. Deployment of Autonomous Trains in Rail Transportation: Current Trends and Existing Challenges. IEEE Access 2021, 9, 91427–91461. [Google Scholar] [CrossRef]
- Fakhereldine, A.; Zulkernine, M.; Murdock, D. Detecting Intrusions in Communication-Based Train Control Systems. ICC 2022 - IEEE International Conference on Communications. LOCATION OF CONFERENCE, South KoreaDATE OF CONFERENCE; pp. 4193–4198.
- Bal, "Formation and management of safety culture in the railway industry: best practices and strategies," Collection of Scientific Works of the State University of Infrastructure and Technologies Series "Transport Systems and Technologies", pp. 69-80, 2023.
- Sharma, G.; Sherif, E.; He, M.; Boiten, E. Analysis of Cyber-Attacks for Modern Digital Railway System Using Cyber Range. 2022 IEEE Conference on Interdisciplinary Approaches in Technology and Management for Social Innovation (IATMSI). LOCATION OF CONFERENCE, IndiaDATE OF CONFERENCE; pp. 1–6.
- Xiong, S.-H.; Qiu, M.-R.; Li, G.; Zhang, H.; Chen, Z.-S. Balancing the signals: Bayesian equilibrium selection for high-speed railway sensor defense. Inf. Sci. 2024, 661. [Google Scholar] [CrossRef]
- Abdellaoui, S.; Dumitrescu, E.; Escudero, C.; Zamaï, E. Cyber Threat Assessment in Monitoring Turnout Railway Systems. 2023 IEEE 28th International Conference on Emerging Technologies and Factory Automation (ETFA). LOCATION OF CONFERENCE, RomaniaDATE OF CONFERENCE; pp. 1–8.
- Thron, E.; Faily, S.; Dogan, H.; Freer, M. Human factors and cyber-security risks on the railway – the critical role played by signalling operations. Inf. Comput. Secur. 2024, 32, 236–263. [Google Scholar] [CrossRef]
- Nebaba, A.N.; Savvas, I.K.; Butakova, M.A.; Chernov, A.V.; Shevchuk, P.S. Improving Multiclass Classification of Cybersecurity Breaches in Railway Infrastructure using Imbalanced Learning. ESSE 2021: 2021 2nd European Symposium on Software Engineering. LOCATION OF CONFERENCE, GreeceDATE OF CONFERENCE; pp. 100–105.
- Hoang, A.T.; Nguyen, X.K. Managing technological security of smart environment monitoring systems: study of a coastal province in Vietnam. Int. J. Crit. Infrastructures 2023, 19, 383–403. [Google Scholar] [CrossRef]
- J. Prochazka, P. J. Prochazka, P. Novobilsky and D. Procházková, "Mobile Cyber Gateway Security Control," in Proceedings of the 31st European Safety and Reliability Conference, 2021.
- Varvarigou, D.; Espes, D.; Bersano, G. Orchestrator for ensuring interdependency between safety and cybersecurity in railway control systems. Int. J. Rail Transp. 2023, 12, 749–764. [Google Scholar] [CrossRef]
- Wang, Z.; Hei, X.; Ma, W.; Wang, Y.; Wang, K.; Jia, Q. Parallel anomaly detection algorithm for cybersecurity on the highspeed train control system. Math. Biosci. Eng. 2022, 19, 287–308. [Google Scholar] [CrossRef] [PubMed]
- Bearfield, G.; Van Gulijk, C.; Thomas, R.J. Redefining rail systems verification and validation: The safety/security STAIRCASE model. Proc. Inst. Mech. Eng. Part F: J. Rail Rapid Transit 2022, 237, 266–274. [Google Scholar] [CrossRef]
- Ge, X.; Wu, Q.; Han, Q.-L.; Zhang, X.-M. Resilient Virtual Coupling Control of Automatic Train Convoys With Intermittent Communications. IEEE Trans. Veh. Technol. 2023, 73, 6183–6195. [Google Scholar] [CrossRef]
- Weaver, G.A. Scientific Data Management for Interconnected Critical Infrastructure Systems. 2021 ACM/IEEE Joint Conference on Digital Libraries (JCDL). LOCATION OF CONFERENCE, United StatesDATE OF CONFERENCE; pp. 192–201.
- Kim, S.; Kim, D. Securing the Cyber Resilience of a Blockchain-Based Railroad Non-Stop Customs Clearance System. Sensors 2023, 23, 2914. [Google Scholar] [CrossRef]
- Purwanto, Y.; Ruriawan, M.F.; Alamsyah, A.; Wijaya, F.P.; Husna, D.N.; Kridanto, A.; Nugroho, F.; Fakhrudin, A.; Itqon, M.; Febrianta, M.Y.; et al. Security Architecture for Secure Train Control and Monitoring System. Sensors 2023, 23, 1341. [Google Scholar] [CrossRef]
- Hatzivasilis, G.; Fysarakis, K.; Ioannidis, S.; Hatzakis, I.; Vardakis, G.; Papadakis, N.; Spanoudakis, G. SPD-Safe: Secure Administration of Railway Intelligent Transportation Systems. Electronics 2021, 10, 92. [Google Scholar] [CrossRef]
- S. Backman and M. Rhinard, "The European Union's capacities for managing crises," Journal of Contingencies and Crisis Management, vol. 26, no. 2, pp. 261-271, 2018.
- C. Schmittner, P. C. Schmittner, P. Tummeltshammer, D. Hofbauer, A. M. Shaaban, M. Meidlinger, M. Tauber, A. Bonitz, R. Hametner and M. Brandstetter, "Threat Modeling in the Railway Domain," in Reliability, Safety, and Security of Railway Systems, 2019.
- V. Romero and E. B. Fernández, "Towards a Security Reference Architecture for Cyber- Physical Systems," in The 15th LACCEI International Multi-Conference for Engineering, Education, and Technology: “Global Partnership for Development and Engineering Education, 2017.
- Marrone, S. Towards a Unified Definition of Cyber and Physical Vulnerability in Critical Infrastructures. 2017 IEEE European Symposium on Security and Privacy: Workshops (EuroS&PW). LOCATION OF CONFERENCE, FranceDATE OF CONFERENCE; pp. 167–173.
- Babeshko, I.; Illiashenko, O.; Di Giandomenico, F. Towards Effective Safety and Cybersecurity Co-engineering in Critical Domains. 2023 13th International Conference on Dependable Systems, Services and Technologies (DESSERT). LOCATION OF CONFERENCE, GreeceDATE OF CONFERENCE; pp. 1–8.
- Aktouche, S.R.; Sallak, M.; Bouabdallah, A.; Schon, W. Towards Reconciling Safety and Security Risk Analysis Processes in Railway Remote Driving. 2021 5th International Conference on System Reliability and Safety (ICSRS). LOCATION OF CONFERENCE, ItalyDATE OF CONFERENCE; pp. 148–154.
- Agirre, I.; Calderon, A.J.; Yarza, I.; Mugarza, I.; Garcia, D.; Borracci, L.; Uven, P.; Jover, A. UP2DATE software updating framework compliance with safety and security regulations and standards. 2023 26th Euromicro Conference on Digital System Design (DSD). LOCATION OF CONFERENCE, AlbaniaDATE OF CONFERENCE; pp. 399–406.
- Yekta, A.R.; Spychalski, D.; Yekta, E.; Yekta, C.; Katzenbeisser, S. VATT&EK: Formalization of Cyber Attacks on Intelligent Transport Systems - a TTP based approach for Automotive and Rail. CSCS '23: Computer Science in Cars Symposium. LOCATION OF CONFERENCE, GermanyDATE OF CONFERENCE; pp. 1–17.
- Wang, Q.; Yu, W.; Huang, D.; Guo, Y. Weighted Train-to-Train Communication-Based Data-Driven Consensus Tracking of Multiple HSTs Subject to Deception Attacks. IEEE Trans. Veh. Technol. 2023, 73, 6346–6356. [Google Scholar] [CrossRef]
- Kour, R.; Aljumaili, M.; Karim, R.; Tretten, P. eMaintenance in railways: Issues and challenges in cybersecurity. Proc. Inst. Mech. Eng. Part F: J. Rail Rapid Transit 2019, 233, 1012–1022. [Google Scholar] [CrossRef]
- Kour, R.; Karim, R. Cybersecurity workforce in railway: its maturity and awareness. J. Qual. Maint. Eng. 2020, 27, 453–464. [Google Scholar] [CrossRef]
- S. Chakrabarty and B. Sikdar, "Detection of Cyber Attacks on Railway Autotransformer Traction Power Systems," IEEE Transactions on Industry Applications, vol. 59, no. 6, pp. 7188-7200, 2023.
- Falahati, A.; Shafiee, E. Improve Safety and Security of Intelligent Railway Transportation System Based on Balise Using Machine Learning Algorithm and Fuzzy System. Int. J. Intell. Transp. Syst. Res. 2021, 20, 117–131. [Google Scholar] [CrossRef]
- J. Nunes, T. J. Nunes, T. Cruz and P. Simões, "Railway Infrastructure Cybersecurity: An Overview," in Proceedings of the 23rd European Conference on Cyber Warfare and Security, 2024.
- Abdellaoui, S.; Dumitrescu, E.; Escudero, C.; Zamaï, E. Temporal Assessment of Malicious Behaviors: Application to Turnout Field Data Monitoring. 2024 International Conference on Control, Automation and Diagnosis (ICCAD). LOCATION OF CONFERENCE, FranceDATE OF CONFERENCE; pp. 1–6.
- Avcı. ; Koca, M. A Novel Security Risk Analysis Using the AHP Method in Smart Railway Systems. Appl. Sci. 2024, 14, 4243. [Google Scholar] [CrossRef]
- B. v. Niekerk, "Vulnerability of South African Commodity Value Chains to Cyber Incidents," Scientia Militaria: South African Journal of Military Studies, vol. 51, no. 3, pp. 161-186, 2023.
- Zoppi, T.; Mungiello, I.; Ceccarelli, A.; Cirillo, A.; Sarti, L.; Esposito, L.; Scaglione, G.; Repetto, S.; Bondavalli, A. Safe Maintenance of Railways using COTS Mobile Devices: The Remote Worker Dashboard. ACM Trans. Cyber-Physical Syst. 2023, 7, 1–20. [Google Scholar] [CrossRef]
- Ge, X.; Han, Q.-L.; Zhang, X.-M. Secure virtual coupling control of connected train platoons under cyber attacks. Veh. Syst. Dyn. 2024, 63, 93–120. [Google Scholar] [CrossRef]
- S. G. Predescu, D. S. G. Predescu, D. Savu and V. E. Badea, "Cybersecurity in the Railway Sector," Romanian Cyber Security Journal, vol. 4, no. 2, 2022.
- Fakhereldine, A.; Zulkernine, M.; Murdock, D. CBTCset: A Reference Dataset for Detecting Misbehavior Attacks in CBTC Networks. 2023 IEEE 34th International Symposium on Software Reliability Engineering Workshops (ISSREW). LOCATION OF CONFERENCE, ItalyDATE OF CONFERENCE; pp. 57–62.
- M. H. ter Beek, A. M. H. ter Beek, A. Fantechi, S. Gnesi, G. Lenzini and M. Petrocchi, "Can AI Help with the Formalization of Railway Cybersecurity Requirements?," in International Symposium on Leveraging Applications of Formal Methods, 2024.
- Voronko, I. The security of IoT systems in railway transport. Collect. Sci. Work. State Univ. Infrastruct. Technol. Ser. "Transport Syst. Technol. 99. [CrossRef]
- K. Vayadande, A. K. Vayadande, A. Bhoyar, A. Gorave, H. Behare, Y. Bhale and O. Bhojane, "Secure Stations: Revolutionizing Railway Security Using AI," in International Conference on Innovations and Advances in Cognitive Systems, 2024.
- S. Janani, S. S. Janani, S. Vijayaram and R. C. Vijayganesh, "IoT-SafeRails: Revolutionizing Railway Collision Avoidance Technology," 2024 International Conference on Inventive Computation Technologies (ICICT), pp. 1666-1673, 2024.
- M. Heinrich, J. M. Heinrich, J. Vieten, T. Arul and S. Katzenbeisser, "Security Analysis of the RaSTA Safety Protocol," in 2018 IEEE International Conference on Intelligence and Security Informatics (ISI), Miami, Florida, 2018.
- M. Dai, G. M. Dai, G. Li and W. Du, "Research on data sharing and exchange technology in the railway industry based on blockchain," in 7th International Conference on Traffic Engineering and Transportation System (ICTETS 2023), 2024.
- Kongsap, P.; Kaewunruen, S. Agent-based modelling of high-speed railway interdependent critical infrastructures facing physical and cyber threats. Front. Built Environ. 2024, 10, 1249584. [Google Scholar] [CrossRef]
- R. Kour, A. R. Kour, A. Thaduri and R. Karim, "Predictive model for multistage cyber-attack simulation," International Journal of System Assurance Engineering and Management, vol. 11, no. 3, pp. 600-613, 3 2020.
- MIT Technology Review, "Ransomware Took San Francisco’s Public Transit for a Ride," MIT Technology Review, . [Online]. Available: https://www.technologyreview.com/2016/11/28/69496/ransomware-took-san-franciscos-public-transit-for-a-ride/. [Accessed 1 December 2024]. 28 November.
- B. Barth, "DDoS attacks delay trains, stymie transportation services in Sweden," SC Media, . [Online]. Available: https://www.scworld.com/news/ddos-attacks-delay-trains-stymie-transportation-services-in-sweden. [Accessed 1 December 2024]. 13 October.
- Osliak, O.; Saracino, A.; Martinelli, F.; Mori, P. Cyber threat intelligence for critical infrastructure security. Concurr. Comput. Pr. Exp. 2023, 35. [Google Scholar] [CrossRef]
- Zou, B.; Choobchian, P.; Rozenberg, J. Cyber resilience of autonomous mobility systems: cyber-attacks and resilience-enhancing strategies. J. Transp. Secur. 2021, 14, 137–155. [Google Scholar] [CrossRef]
- Ungkap, P.; Daengsi, T. Cybersecurity Awareness Modeling Associated with Influential Factors Using AHP Technique: A Case of Railway Organizations in Thailand. 2022 International Conference on Decision Aid Sciences and Applications (DASA). LOCATION OF CONFERENCE, ThailandDATE OF CONFERENCE; pp. 1359–1362.
- Gao, B.; Bu, B.; Wang, X. A Comprehensive Resilient Control Strategy for CBTC Systems Through Train-to-Train Communications Under Malicious Attacks. IEEE Trans. Intell. Transp. Syst. 2022, 23, 21015–21033. [Google Scholar] [CrossRef]
- R. Chan, "A Security Framework for Railway System Deployments," Cham, 2022.
- Rahiminia, S.; Mehrabi, A.; Aghaee, M.P.; Jamili, A. Adopting a Bi-level Optimization Method for the Freight Transportation Problem: A Multi-objective Programming Approach. Transp. Res. Rec. J. Transp. Res. Board 2023, 2677, 490–504. [Google Scholar] [CrossRef]
- Valdivia, L.J.; Adin, I.; Arrizabalaga, S.; Anorga, J.; Mendizabal, J. Cybersecurity-The Forgotten Issue in Railways: Security Can Be Woven into Safety Designs. IEEE Veh. Technol. Mag. 2018, 13, 48–55. [Google Scholar] [CrossRef]
- Merchan, A.L.; Belboom, S.; Léonard, A. Life cycle assessment of rail freight transport in Belgium. Clean Technol. Environ. Policy 2020, 22, 1109–1131. [Google Scholar] [CrossRef]
- H. Steele, C. H. Steele, C. Roberts and S. Hillmansen, "Railway smart grids: Drivers, benefits and challenges," Proceedings of the Institution of Mechanical Engineers, Part F: Journal of Rail and Rapid Transit, vol. 233, no. 5, pp. 526-536, 2019.
- Kanis, J.; Dolinayova, A.; Kmetik, M. Draft of strategy of the European rail freight corridor Amber. MATEC Web Conf. 2018, 235, 00023. [Google Scholar] [CrossRef]
- Feng, Y.; Zhong, Z.; Sun, X.; Wang, L.; Lu, Y.; Zhu, Y. Blockchain enabled zero trust based authentication scheme for railway communication networks. J. Cloud Comput. 2023, 12, 1–21. [Google Scholar] [CrossRef]
- Kour, R.; Thaduri, A.; Karim, R. Railway Defender Kill Chain to Predict and Detect Cyber-Attacks. J. Cyber Secur. Mobil. 2020, 47–90. [Google Scholar] [CrossRef]
- Nifakos, S.; Chandramouli, K.; Nikolaou, C.K.; Papachristou, P.; Koch, S.; Panaousis, E.; Bonacina, S. Influence of Human Factors on Cyber Security within Healthcare Organisations: A Systematic Review. Sensors 2021, 21, 5119. [Google Scholar] [CrossRef]
- R. Alkhaledi and S. Hawamdeh, "Electronic Health Records and Cyber Hygiene: A Qualitative Study of the Awareness, Knowledge, and Experience of Physicians in Kuwait," Proceedings of the Association for Information Science and Technology, vol. 60, no. 1, 2023.
- Laiton-Bonadiez, C.; Branch-Bedoya, J.W.; Zapata-Cortes, J.; Paipa-Sanabria, E.; Arango-Serna, M. Industry 4.0 Technologies Applied to the Rail Transportation Industry: A Systematic Review. Sensors 2022, 22, 2491. [Google Scholar] [CrossRef] [PubMed]
- Miranda, A.T. Understanding Human Error in Naval Aviation Mishaps. Hum. Factors: J. Hum. Factors Ergon. Soc. 2018, 60, 763–777. [Google Scholar] [CrossRef] [PubMed]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).