1. Introduction
With the rapid development of human civilization, the public safety situation is also facing new and severe challenges. To create a good public safety environment, the public security patrol path planning plays an important role, which considers factors such as time, road conditions and distance, aiming to provide the shortest security patrol route for police to achieve higher duty efficiency.
Many scholars have reflected on the development of the policing model of public security patrols and the optimization of patrol routes, such as: Wang et al. designed a solution for collaborative execution of area coverage tasks by multiple unmanned ships for large-scale sea patrol tasks based on the multi unmanned ship area coverage traversal algorithm [
1];Xiang et al. designed an improved Partheno-genetic Algorithm (IPGA) for quickly obtaining high-quality patrol task planning schemes [
2];Li used the Rural Postman Problem (RPP) to construct a graph theory model for traffic police patrol path optimization based on the CE2 heuristic algorithm, effectively shortening the path length and saving costs [
3];Both Zhang [
4] and Kong et al [
5] achieved path planning by improving ant colony algorithm and using distance discriminant analysis to select multiple parameter indicators; Jie et al. proposed a new multi-agent based reinforcement learning algorithm to plan the optimal patrol path under arbitrary conditions of multiple defenders and attackers [
6];Liang adopted a combination of ant colony algorithm and genetic algorithm to improve the efficiency of sightseeing path planning in the intelligent navigation system of the park [
7];Shi et al combined evolutionary algorithms with optimization experiments to establish a two-layer optimization model, and combines multi-agent genetic algorithms to solve multi-objective optimization scheduling problems in complex environments [
8];Yan et al combined particle swarm optimization algorithm with predictive control, overcoming the disadvantage of traditional particle swarm optimization algorithm in generating infeasible paths during particle update process [
9];Authors developed a two-layer optimization framework to solve the patrol police force allocation problem, and then used a new iterative Bender decomposition method to solve the potential optimization problem, thereby solving the spatial police patrol allocation problem with expected crime response time [
10]. Unfortunately, various algorithms have their own shortcomings.
Over the past few decades, wolf-pack optimization algorithm has attracted widespread interest from researchers due to its high parallelism, good global convergence, and computational robustness, making it particularly suitable for solving high-dimensional, multi-modal complex functions [
11];For instance, Tang et al. developed an automatic detection scheme for wolf pack hunting behavior in videos [
12], which greatly improves the accuracy of motion state recognition, reaching up to 88%;Duan et al. proposed a target allocation method based on wolf behavior mechanism [
13], which effectively solves the problem of collaborative target allocation among drone groups; In paper [
14], an entropy-based grey wolf optimizer (IEGWO) algorithm was proposed to solve global optimization problems; Chen et al. developed a Hybrid Grey Wolf Optimizer (HGWO) that combines Halton sequences and multiple strategies, which can be used to solve practical engineering problems [
15]; Authors modelled the behavioral characteristics of wolf packs in natural environments and used it to solve the dynamic task allocation problem of drone swarms in complex scenarios [
16]; She et al. improved the wolf-pack optimization algorithm to enhance the accuracy and efficiency of solving highly nonlinear black box function structural reliability problems [
17];In paper [
18], researchers proposed a submarine cable positioning algorithm based on Improved Grey Wolf Optimization (IGWO), which achieves accuracy and effectiveness in submarine cable positioning.
Therefore, the effective utilization of the wolf-pack optimization algorithm mentioned above inspires us to intend to adopt an improved wolf-pack optimization algorithm to solve the optimization problem of public security patrol path planning, then this paper proposes a public security patrol path planning recommendation method based on an improved wolf-pack optimization algorithm (S3PRM-DAF-BRS-CWOA).
Section 2 provides the related existing works about this new proposed method.
Section 3 elaborates on the improvement and design of the new proposed method.
Section 4 shows performance verification experiment and analysis of experimental results.
Section 5 gives the conclusion of this article, summarizing its contributions, existing limitations, and future directions for improvement.
2. Related Works
2.1. Swarm Intelligence Optimization
In nature, a variety of creatures with limited individual ability show amazing abilities through constitutions and inter -individual information exchange, such as: ant colony, bee colony, wolves, and so on. The swarm intelligent optimization algorithm is designed by simulating the characteristics of biological group behaviors in nature. It uses simple rules and interactions between many bodies to optimize the optimization problem of complex functions. The origin of the swarm intelligent optimization algorithm dates back to the 1980s. At that time, some scholars began to study the calculation model of simulating the behavior of natural biological groups. In 1986, Garnier and others proposed an Ant Random Walking Model [
19], which can be regarded as an early form of the swarm intelligent optimization algorithm. The swarm intelligent optimization algorithm provides new ways and shows excellent performance when solving many practical problems.
In recent years, in order to solve the limitations of traditional swarm intelligent algorithms on certain problems, scholars have proposed many new types of swarm intelligent optimization algorithms. These new algorithms have shown stronger applicability and experimental effects in solving complex practical problems, such as: Battle algorithm proposed by British scholar yang [
20]. Essence These new algorithms can more effectively search for optimal solutions, strong adaptability, and can adapt to various types of optimization problems. However, there are still many shortcomings. For example, the adjustment of bat algorithm in certain parameters may affect the performance of the algorithm. There are few cases in practical applications, and more empirical research is required to verify its effects.
2.2. Wolf-Pack Optimization Algorithm
Among the new algorithms that have emerged in recent years, the wolf-pack optimization algorithm is a typical representative. Wolf-Pack Optimizaton Algorithm (WPOA) was first proposed by YANG et al. [
21] by imitating the habit of imitating the group of raw animals, the intelligence shown in the simulation of the wolf-pack foraging and hunting in nature, mainly The three intelligent lines of the wolf hunting behavior, calling-galloping behavior and siege are abstracted to find the optimal solution to the problem. The algorithm process mainly includes parameter initialization, migration mechanism, summon-raid mechanism, siege mechanism, and regeneration mechanism.
Initialization: The algorithm first needs to set a series of parameters such as the size of the wolves, the location of each wolf, the step length, and the number of iterations. It is an important basis for the algorithm. Appropriate parameter settings can help algorithms to converge to optimal solutions faster, while maintaining sufficient search diversity to avoid local optimal. In the process, the wolf in the wolf-pack is assigned to the function of the function. Assuming that the number of wolves is n, and the dimension of the interpretation of the space is D, then the position of each wolf is as required as a formula (1).
Migration-Mechanism: The process of searching the prey during the hunting of the wolf-pack in the natural environment, and searching the target separately in a certain field of a certain field of the wolf-pack members. In this process, each wolf searches the target in its nearby space according to the rules. The best Q -Po Wolf except the wolf in the solution space is regarded as the exploring wolf. The exploring wolf is centered on its own position, and the long -term searches are used as a search step to explore the prey around them. Degree value. If the adaptation value of the current wolf is greater than the point of adaptation of the position of the wolf, it indicates that the prey is relatively close to the wolf I and may capture the prey. The hunting process, that is, the current exploring wolf moves in the direction of H hunting and calculates the new location and the new adaptation value. For example, the formula (2) indicates that after moving the direction of P (P = 1,2, ..., H, H ≤D), the current wolf i is currently a new position in the D -dimensional space.
Summon-Raid-Mechanism: After discovering the prey, the simulation wolf-pack will summon other wolves to quickly stride and participate in hunting by calling them by calling or other ways to increase the power of hunting. According to the formula (3), it is updated on the road of raid. If the new position obtained, the adaptation value is better than the current position, the wolf will move to the new position, otherwise it will stay in the current position. Among them, Z
id represented the position of the No. D-dimensional renewal of the No. i wolf in the wolf-pack;
Xid is the current position of the D-dimension of the I wolf; RAND is a random number evenly distributed in the interval [-1,1]; Stepb is the step-size in the process of Summon-Raid;
Xld is the position of the leader wolf in
d-th dimension.
Siege-mechanism: During the capture process, the wolf-pack appeared around the leader wolf to adopt a small step to siege prey. That is, first generate a random number of RM in [0, 1]. If RM is smaller than θ (θ is a pre -set threshold), then the I wolf does not move. The wolf surrounded the prey with the leader wolf. The updated wolf position x
it+1 is shown in the formula (4),
Stepc means the siege length;
Xl is the position of the head wolf.
Regeneration-Mechanism: Simulation of the natural evolution of wolves is a key link in the iteration of the algorithm. Reserve strong performance in the wolves, eliminate wolves with poor performance, and then randomly supplement a certain number of artificial wolves. Update the population of the wolf by evaluating the adaptation value in the population, and the suspension conditions during iteration can be set. It ensures that the wolf clusters can adapt to evolution and eventually converge to the optimal solution, which improves the efficiency and effect of algorithms when solving complex optimization problems.
2.3. Data-Sets
In order to test the optimization ability of the DAF-BRS-CWOA proposed in this article, test comparison experiments with other optimization algorithms, and select some common functions and data sets of the test optimization algorithm as shown in
Table 1 for testing. Select a variety of types of public test functions such as public test functions. Some test functions have the characteristics of multi -peak value, strong interference, high complexity, etc., and can fully test the global nature of the model. Some test functions are smooth, continuous, convex, and convex the characteristics such as the Single Peak are like a bowl shape; some test functions are very smooth and the change is relatively smooth, and test function formulas are shown in
Table 1.
2.4. S3P-Function
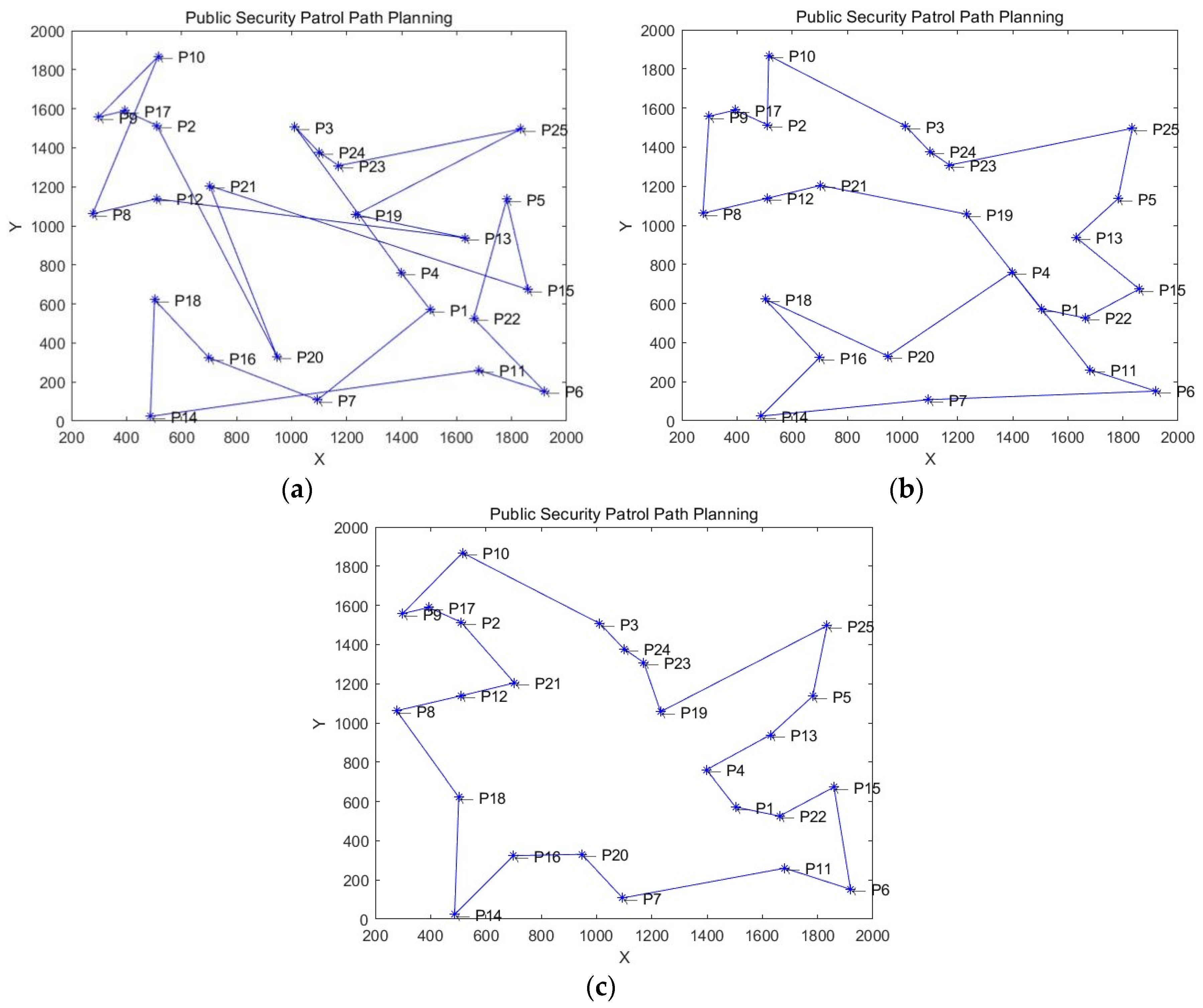
In the real social life, the task of public security patrols requires that the patrol paths of police officers must cover important nodes, and the number of important nodes is often large, so this results in multiple actual patrol paths with varying distances and disorganization, as shown in
Figure 1(a). Fortunately, police officers often have rich patrol experience and have their own "optimal patrol path" based on this kind of experience, as shown in
Figure 1(b). However, the "optimal patrol path" based on police officers' experience shown in
Figure 1(b) is not truly optimal, especially in the case of a large number of important patrol nodes resulting to huge number of patrol path options, it is unlikely to find the globally optimal one due to limitations in human mental arithmetic ability, and
Figure 1(c) gives the true global optimal patrol path compared to
Figure 1(b).
It is based on the above problem that this article abstracts a problem model serving the planning of public security patrol paths. Without loss of generality, assuming that the security patrol task is carried out in a plain area and ignoring the influence of altitude, that is, the Euclidean distance is used to calculate the distance between all key points; thereby, this paper constructs an objective function of public security patrol path planning (S3P-Function), the calculation formula is as Equation5.(This paper takes a 2000 km by 2000 km area and 30 security patrol locations generated randomly).
Where, means the whole distance of some a public security patrol path; pn means the n-th patrol point along some a security patrol path while p1 means the first one; xpn and ypn present the horizontal and vertical coordinates respectively; N means the total number of patrol points along some a security patrol path.
Obviously, it is completely that different from classical test functions in 2.3 that the above description is a discrete problem. To solve this problem, this paper made a discrete algorithm based on the idea of WPOA to solve the discrete problem.
3. Improvement and Design of the New Proposed Method
Compared with the comparative algorithm in [
22], the article titled " an adaptive distribution size (ADS) wolf-pack optimization algorithm using the strategy of jumping for raid (for short, WDX-WPOA)" demonstrates significant advantages in optimization capabilities, including higher global search accuracy, stronger robustness, and faster convergence speed. However, WDX-WPOA also has certain shortcomings, such as significantly longer iteration times in some test function applications shown in [
23]; so this paper designed two following strategies to improve the optimization performance in response to this issue, and then the new proposed algorithm will be utilized to achieve a more efficient solution for the security patrol path planning problem.
3.1. Dynamic-Adjustment-Factor
During the raid process, in order to find the global optimal solution around the leader wolf, wolf-pack will be hoped to approach the leader wolf as soon as possible. However, the distance between wolves except the leader wolf should be precisely adjusted, that is, the distance should not be too small to avoid the wolf pack falling into local optimum, nor too large to prevent slow convergence. By setting reasonable distances, the efficiency of the optimization process can be improved while ensuring global search capability.
According to existing methods, the number of airdropped wolves in the ASGS-CWOA and WDX_WPOA does not change during the process of Summon-Raid. Obviously, this approach is insufficient to accurately reflect the dynamic changes during the raid process and may lead to a decrease in optimization performance, and to overcome this deficiency, Dynamic-Adjustment-Factor (DAF) was proposed to dynamically adjust the number of airdropped wolves based on real-time changes during the process of Summon-Raid, thereby improving the overall performance of the algorithm. The specific dynamic adjustment mechanism is shown in Equation (6) following.
Where, factor depends the number of wolves following the old strategy of Summon-Raid as in ASGS-CWOA and the number of other wolves following the new proposed strategy of Summon-Raid ; t means the number of current iteration; T means the number of the maximum iteration; numraid means the number of wolves to be replaced with new wolves; floor means a function that returns the calculated result rounded down to ensure that numraid is an integer; numW means the number of wolf-pack that is 50 in this paper; newraid_wolf_index means an index array that means the position of the wolf to be replaced with the new wolf while oldraid_wolf_index is the one in its original state; index_tem is an index array obtained by sorting the current fitness, from the worst fitness to the best fitness.
From the Equation (5), it’s observed that the factor will vary between 0.5 and 1, and it will increase the number of newraid_wolf_index as the number of iterations increases, thereby allowing more wolves to participate in the raid process. This mechanism allows the algorithm to introduce fewer new wolves in the early stages to reduce computational complexity; In the later stage, the proportion of new wolves gradually increases to better explore the search space.
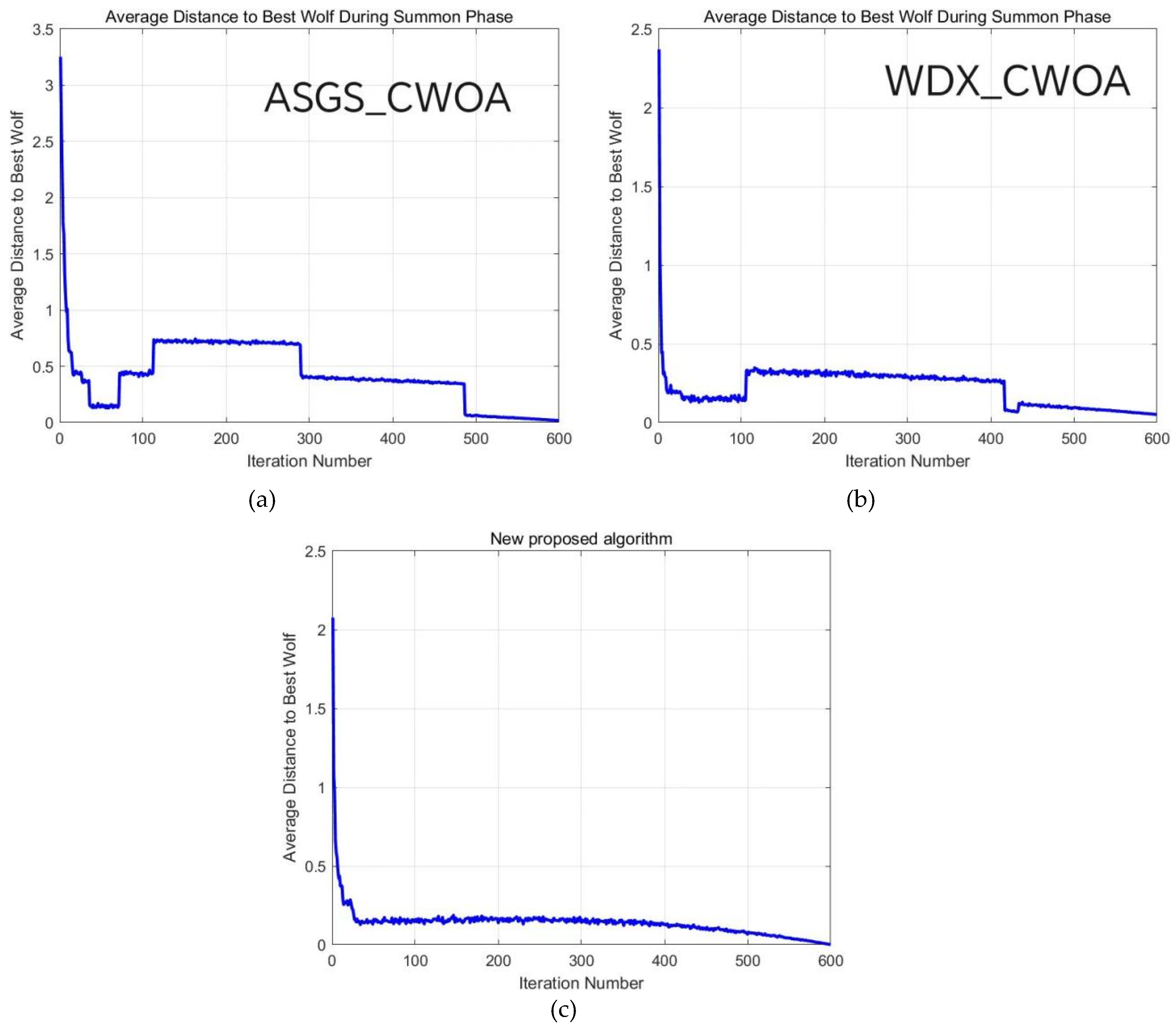
From
Figure 2, it was seen that the convergence of the wolf-pack during the siege phase as the number of iterations increases. Obviously, the curve in the
Figure 2(c) is smoother than the others, and the convergence speed of the wolf-pack is also faster. This indicates that introducing the DAF to dynamically adjust the number of airdropped wolves and wolves running according to the original strategy can not only improve the convergence speed of the wolf-pack and shorten the overall running time of the algorithm, but also not affect the algorithm's ability to globally find the optimal solution. In other words, as the number of iterations increases, the wolf-pack will get closer to the optimal solution..
3.2. Balanced-Raid-Strategy
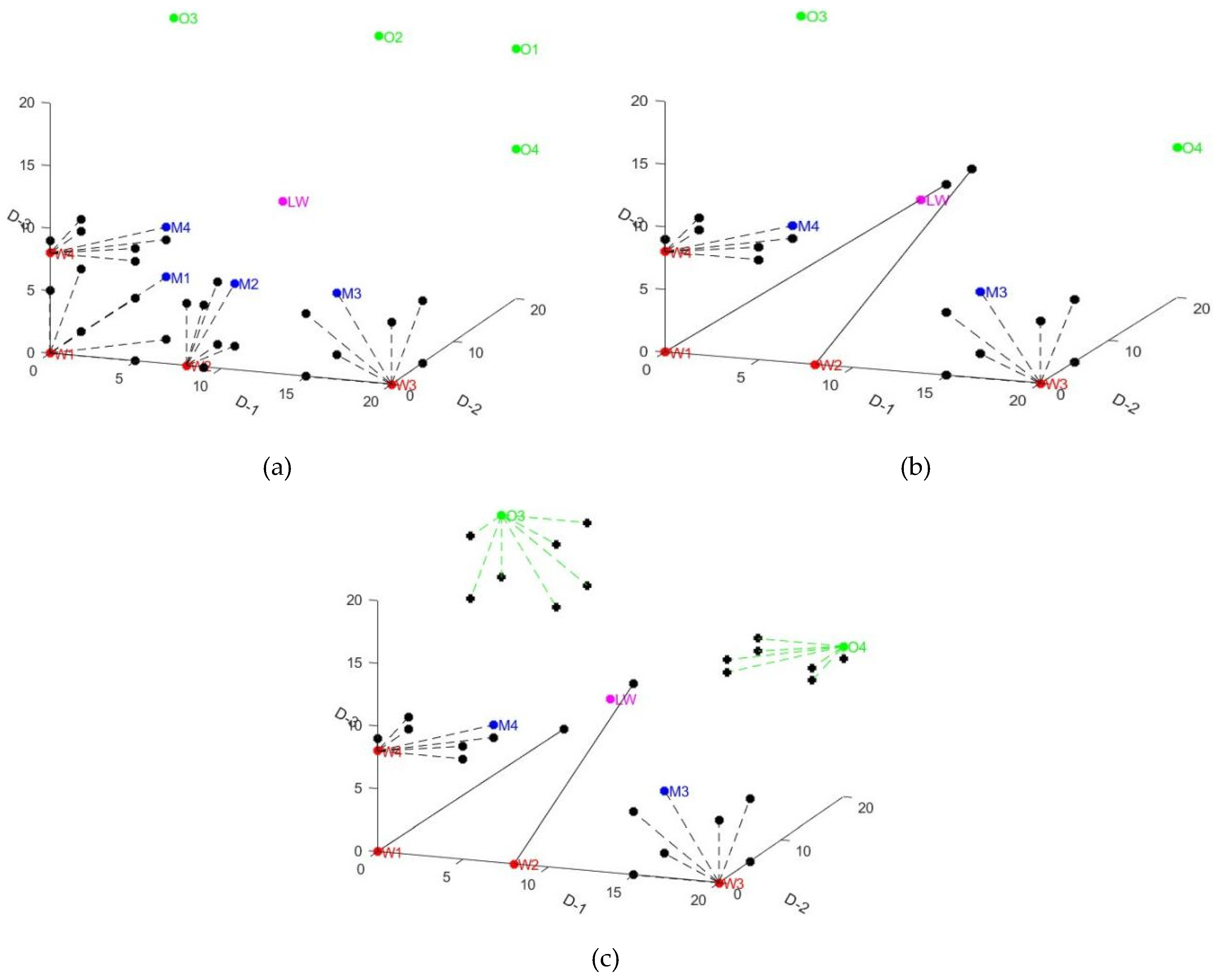
During the process of Summon-Raid, for every wolf, 2
D locations generated by the coordinate arrangement combination of current location and the middle one between the current wolf and the best wolf are checked up as well as the reverse location of the current wolf regarding the best wolf, shown in
Figure 3(a) about ASGS-CWOA. Accordingly, in WDX-WPOA, half of the wolf-pack follows the Summon-Raid strategy in ASGS-CWOA, while the other half is directly airdropped to the surrounding of current optimal wolf, which means that only 2
(D-1) + 1 locations will be checked up per wolf on average and accelerates the gathering and siege rhythm of the wolf-pack, and accelerates the convergence speed of the algorithm in another word, shown in
Figure 3(b).
Furthermore, Balanced-Raid-Strategy (BRS) was proposed in the new proposed algorithm to improve the existing original strategy of Summon-Raid by not only examining the reverse location of the current wolf, but also the ones generated according to certain rules between the reverse position of the current wolf regarding the current optimal wolf for half of wolf-pack, and in this way the search volume are increased during each iteration, which increases the possibility of finding the global optimal solution while increases the computational complexity and time consumption of the algorithm, shown in
Figure 3(c).
Where, wolfi-opposite means the opposite location of the current wolf while bestwolf means the current best wolf and pop(i,:) means the current wolf-ith; locationsopposite represents the locations between wolfi-opposite and bestwolf according to the Summon-Raid rules in WDX-WPOA; original_Summon_Raid_Mesh_Process is a function that returns some related locations determined by Summon-Raid rules in WDX-WPOA while FitnessFunction is another one that returns the fitness of the given wolves or locations; ftopposite-locations means the fitness regarding locationsopposite; ftopposite-locations-best means the best one of ftopposite-locations while NOopposite-locations-best is the serial number of ftopposite-locations-best in ftopposite-locations, and wolfopposite-locations-best is the best one of locationsopposite around wolfi-opposite.
The Equation (7) gives the key rules regarding BRS during Summon-Raid process.
3.3. Steps Of DAF-BRS-CWOA
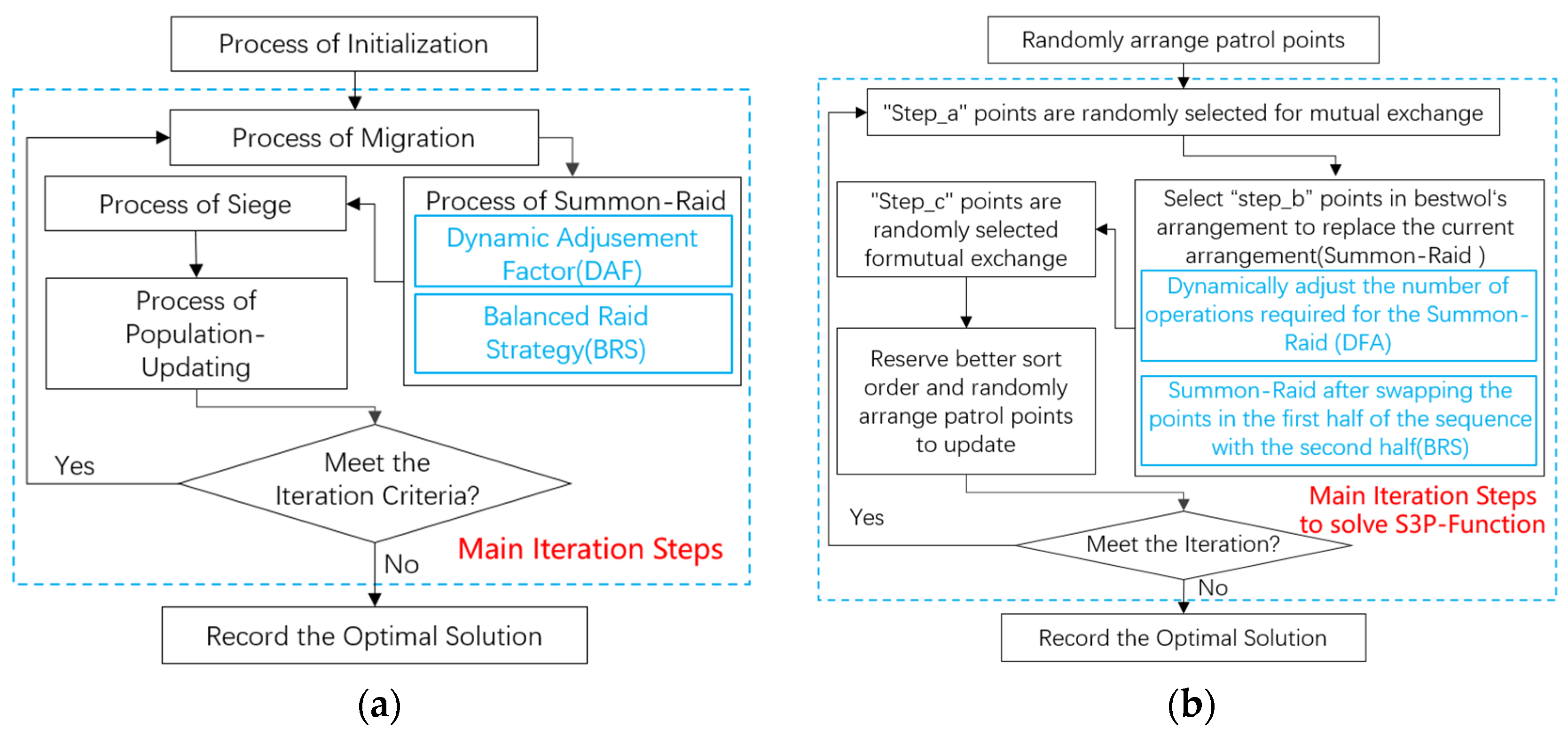
On the basis of the strategy of dynamically increasing the number of airdrop wolves and increasing the number of examined locations, WCOA was improved and DAF-BRS-CWOA was proposed. Here are the steps on how to implement the new improved algorithm, as shown in
Figure 4(a).
All steps are consistent with WDX-WPOA except DAF and BRS are used in the Summon-Raid process, detailed in 3.1 and 3.2 respectively. At the same time, we made it as a discrete -type algorithm according to the idea of DAF-BRS-CWOA to solve the S3P-Function. The general process is as shown in
Figure 4 (b).
4. Performance Verification Experiment
4.1. Experimental Designment
In order to test the optimization capabilities of DAF-BRS-CWOA, the classic genetic algorithm (GA), particle swarm algorithm (PSO) and WDX-WPOA three optimization algorithms shown in
Table 2 are used to perform experiments. And 20 test functions such as 6 multi -model methods and the distance test function of the patrol path, the theoretical optimal of order, function, expression, dimension, characteristics, scope, and each test function is given. The numerical experiment results on the 21st test function for the next test can be analyzed and studied for the next step. Details are shown in tables following.
All numerical experiments are implemented on a computer equipped with Windows 11 Home 22H2 operating system, Intel(R) Core (TM) i7-12700H processor and 16G memory while the integrated development environment is MATLAB-2024a. For genetic algorithm, toolbox in Matlab 2017a is utilized for GA experiments; the PSO experiments were implemented by a “PSOt” toolbox for Matlab; Experiments on WDX-WPOA are done according to the steps from reference [
23]; and the new algorithm DAF-BRS-CWOA is implemented by utilizing MATLAB-2024a with M programming language. The specific configuration of the above algorithms is shown in
Table 2. In order to verify the excellent performance of the new algorithm, like the other three algorithms, it runs 30 optimization calculations on each test function. Then, all algorithms are evaluated from the aspects of the best value, worst value, average, standard deviation, the number of average iterations, and the average time of the global optimal.
4.2. Experimental Results and Analysis
Firstly, as shown in
Table 3, seen from the optimal value, the DAF-BRS-CWOA can find the theoretical optimal values of all the test functions as well as WDX-WPOA, but no one else can do it; furthermore, seen from the worst value and average value, DAF-BRS-CWOA has the best performance in all 4 algorithms(PSO, GA, WDX-WPOA and DAF-BRS-CWOA) that its worst and average values both reach the theoretical optimal values while the other algorithms have no such ability. Therefore, DAF-BRS-CWOA has better optimization accuracy.
In addition, in 30 tests, the new algorithm had zero standard deviation on almost all test functions except function 2"Bukin6", function 4"Eggholder", function 6"Levy" and function 21" 3P-Function". Even so, in function 2 "Bukin6" and function 4 "Eggholder", the standard deviation of DAF-BRS-CWOA is better than the standard deviation of other algorithms. Although the standard deviation of DAF-BRS-CWOA in function 6 is larger than that of GA and PSO, GA and PSO cannot find the optimal value in 30 tests, while DAF-BRS-CWOA can, as show the standard deviation in
Table 3. Therefore, DAF-BRS-CWOA has good stability in general.
Moreover, in term of average number of iterations, DAF-BRS-CWOA has smallest iterations on all test functions except function 2 "Bukin6", function 4 "Eggholder", function 21" S3P-Function", and on function 2, 4 and 21 the number of iterations is 600 which is same to the values on other algorithms, shown in
Table 3 Average iteration. Hence, in general, DAF-BRS-CWOA has better advantage in terms of iteration.
Finally, as shown in
Table 3 Average Time, the average time spent on Functions 14, 15, 18, and 19 is minimal for DAF-BRS-CWOA. Moreover, the four algorithms spend about the same amount of time on test functions 1, 9, and 20, and DAF-BRS-CWOA runs longer than PSO or GA on the rest of the test functions, but the performance of finding the optimal value is better than that of other algorithms (PSO and GA). Nonetheless, it is a consolation that the proposed algorithm outperforms WDX-WPOA in terms of running time without losing optimization accuracy. As shown in
Table 4 and
Figure 5, In all test functions, the DAF-BRS-CWOA is improved compared to WDX-WPOA. Therefore, the DAF-BRS-CWOA has a good convergence speed.
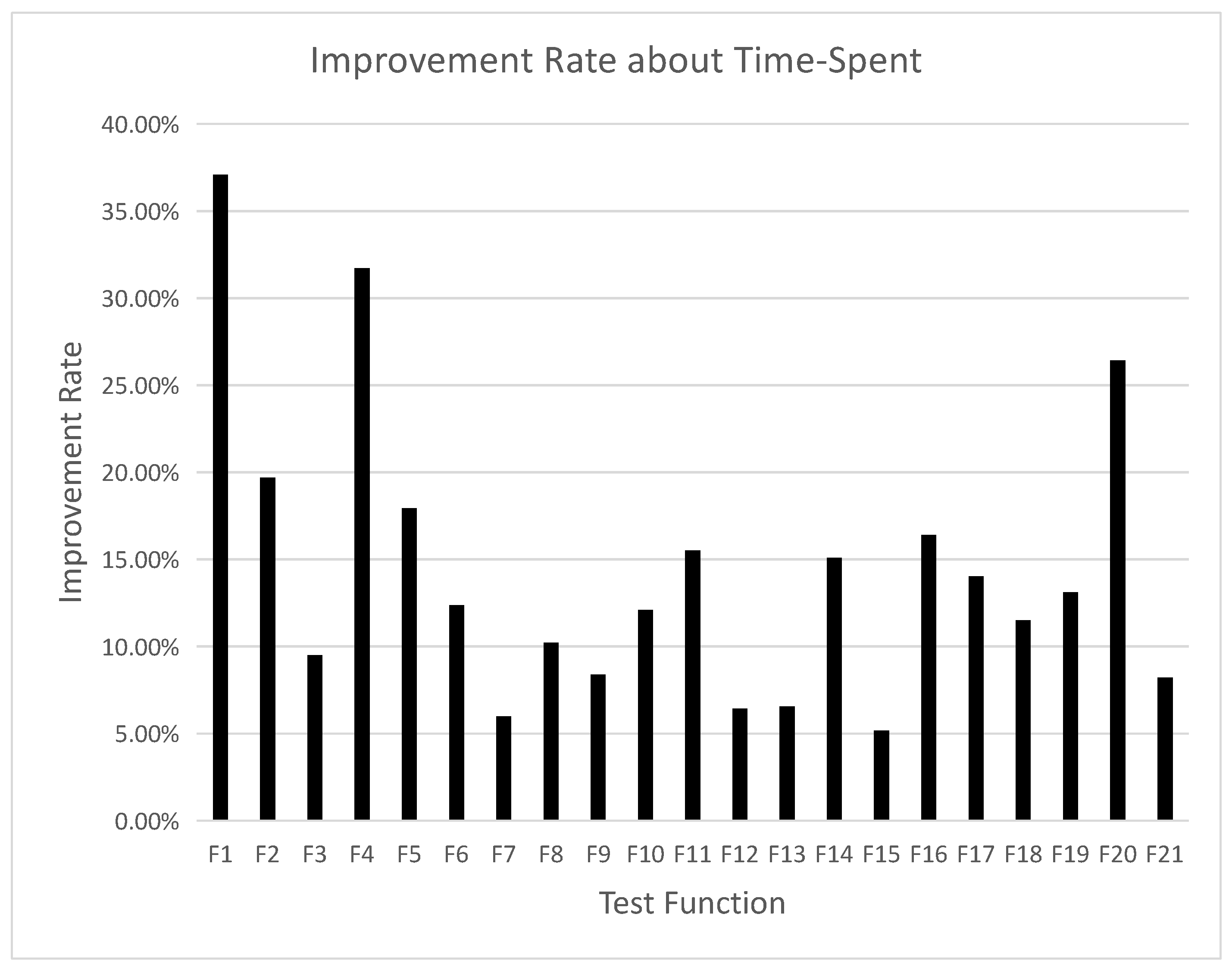
In fact, on the premise of guaranteeing the absolute global optimization ability, the conclusion shows that DAF-BRS-CWOA spent less time seen from
Table 4 and
Figure 3, it is seen that all the improvement rates are positive and that means DAF-BRS-CWOA spent less time than WDX-WPOA on all the 21 algorithms involved in this paper. Especially, it is worth mentioning that the improvement rates on function “Ackley’’ and “Eggholder” are both more than 30% and the value on function ‘‘Bohachevsky3’’ is more than 20% as well as most of the functions are both more than 10%. On the other functions, all the improvement rate are more than 5% and the worst improvement rate reaches about 5.17%.
Moreover, in the optimization of the function 21 patrol path, DAF-BRS-CWOA is the algorithm with the smallest path length, shortest time-spent, and smallest the length of the path among all algorithms (PSO, GA, WDX-WPOA and DAF-BRS-CWOA) during 30 independent experiments. DAF-BRS-CWOA has an absolutely small path length compared to GA and PSO. Compared to WDX-WPOA, the DAF-BRS-CWOA has a certain improvement in time-spent, as shown in
Table 3. Therefore, DAF-BRS-CWOA has excellent performance in public security patrol path planning.
In a word, DAF-BRS-CWOA possesses excellent optimization accuracy, good stability, less time-spent and quick peed of convergence.
5. Conclusions
The public security patrol path planning is very important in public security work, however, the existing public security patrol path planning has some shortcomings to varying degrees. To address these shortcomings, this paper proposes a public security patrol path planning recommendation method based on an improved wolf-pack optimization algorithm, which mainly focuses on three aspects. Firstly, Dynamic-Adjustment-Factor was introduced in WDX-WPOA to dynamically adjust the number of airdropped wolves; Moreover, Balanced-Raid-Strategy with symmetric property was proposed to improve the existing original strategy of Summon-Raid by not only examining the reverse position of the current wolf, but also the ones generated according to certain rules between the reverse position of the current wolf and the current optimal wolf; Finally, an optimization objective function regarding the public security patrol path planning was abstracted and counted to obtain the optimal recommendation for the public security patrol path planning. Comparative and numerical experiments with four similar swarm intelligence optimization algorithms (PSO, GA, WDX-WPOA and DAF-BRS-CWOA) on 20 public datasets and the proposed objective function RPB Function were conducted and the results demonstrated that the DAF-BRS-CWOA has superior performance.
Although the algorithm proposed in this paper is superior, there are still some shortcomings. Such as shown in
Table 3, DAF-BRS-CWOA spent more time than GA and PSO in 14 test functions. And it is in function-21 that DAF-BRS-CWOA spent a considerable amount of time as well as the results of each operation are not so stable due to the higher complexity, which confirms a principle: no perfect standard that applies universally. The authors will continuously improve this algorithm and make it play an increasingly important role in various different fields in the future work.
Acknowledgments
The authors are grateful for peer experts for full support of this paper and thank University of Science and Technology Beijing for supporting necessary scientific environment. This study was funded by National Natural Science Foundation of China (NO.62332017), Science and Technology Research Project of Henan Provincial Department of Science and Technology (NO.24210232103y), Fujian Province's 2024 Science and Technology Driven Police Research Special Project (No. 2024Y0065).
References
- Wang, C., Wang, S., Song, S., Wang, K, Wu, S., &Huang, G. (2023). Multi unmanned ship path planning method and simulation for maritime patrol. Chinese Journal of Image and Graphics, 28(8), 2536-2548.
- Xiang, R., Zhu M., &Xu, L. (2022). Planning Method for Multi UAV Highway Patrol Tasks. Radio Engineering (007), 052.
- Li, L. (2020). Research and Application Development of Traffic Police Patrol Route Optimization Based on Open-Source GIS and Rural Postman Problem (Doctoral dissertation, East China Normal University).
- Zhang, L., Fan X. (2020). Key patrol route planning under ant colony algorithm. Practice and Understanding of Mathematics, 50(16), 9.
- Kong, L., Zhang, G., Su, Z., &Jiang, J. (2018). Ambulance emergency rescue path planning based on improved ant colony algorithm. Computer Engineering and Applications.
- Jie, Yi., Gu, Yi. (2017). Multi agent reinforcement learning police patrol path planning based on Stackelberg strategy. Journal of Beijing Institute of Technology 37(1), 7.
- Liang, J. (2024). Optimization of Tourist Park Sightseeing Path Planning Based on Improved Ant Colony Algorithm. Control and Information Technology.
- Shi, W., Fu, Y., Zhao, X., Liu, H., &Li, P. (2021). Research on Patrol Task Allocation and Path Optimization Method Based on Multi Agent. Journal of the Chinese Academy of Electronic Sciences, 16(7), 6.
- Yan, Z., He, Li., &Li, J. (2017). Multi domain limited multi AUV patrol route planning method. Journal of Underwater Unmanned Systems, 25(4), 6.
- Mukhopadhyay, A., Zhang, C., Vorobeychik, Y., Tambe, M., Pence, K., & Speer, P. (2016). Optimal allocation of police patrol resources using a continuous-time crime model. In Decision and Game Theory for Security: 7th International Conference, GameSec 2016, New York, NY, USA, November 2-4, 2016, Proceedings 7 (pp. 139-158). Springer International Publishing.
- Zhang, L., Gao, T., Cai, G., & Hai, K. L. (2022). Research on electric vehicle charging safety warning model based on back propagation neural network optimized by improved gray wolf algorithm. Journal of Energy Storage, 49, 104092. [CrossRef]
- Tang, D., Huang, C., Xiang, X., Zhou, H., Zhu, S., & Hu, T. (2023). Behavior automatic analysis for wolf pack hunting: making fast behavior analysis of massive data possible. Behavioral Ecology and Sociobiology, 77(6), 67. [CrossRef]
- Duan, H., Yang, Q., Deng, Y., Li, P., Qiu, H., Zhang, T., ... & Shen, Y. (2019). Unmanned aerial systems coordinate target allocation based on wolf behaviors. Science China. Information Sciences, 62(1), 14201. [CrossRef]
- Yao, K., Sun, J., Chen, C., Cao, Y., Xu, M., Zhou, X., ... & Tian, Y. (2023). An information entropy-based grey wolf optimizer. Soft Computing, 27(8), 4669-4684. [CrossRef]
- Chen, S., & Zheng, J. (2024). A hybrid grey wolf optimizer for engineering design problems. Journal of Combinatorial Optimization, 47(5), 86. [CrossRef]
- Wang, Z., & Zhang, J. (2022). A task allocation algorithm for a swarm of unmanned aerial vehicles based on bionic wolf pack method. Knowledge-Based Systems, 250, 109072. [CrossRef]
- She, A., Wang, L., Peng, Y., & Li, J. (2023, November). Structural reliability analysis based on improved wolf pack algorithm AK-SS. In Structures (Vol. 57, p. 105289). Elsevier. [CrossRef]
- H, W., Wen, J., & Xu, Z. (2024) Underwater robot submarine cable positioning algorithm based on improved grey wolf swarm optimization algorithm. Control and decision-making1-7.
- Cortes C , Vapnik V .Support-Vector Networks[J].Machine Learning, 1995, 20(3):273-297. [CrossRef]
- YANG X S. A new metaheuristic bat-inspired algo rithm[J]. Computer knowledge & technology, 2010, 284: 65-74.
- Yang C, Tu X, Chen J.Algorithm of marriage in honey bees optimi zation based on the wolf-pack search[C] //International Conference on Intelligent Pervasive Computing.Jeju: IEEE Computer Society, 2007: 11-13.
- Wang, D. , Qian, X. , Liu, K. , & Ban, X. . (2018). An Adaptive Shrinking Grid Search Chaos Wolf Optimization Algorithm with Adaptive Standard-Deviation Updating Amount.
- Wang, D. , Qian, X. , Liu, K. , Ban, X. , & Guan, X. . (2018). An adaptive distributed size wolf-pack optimization algorithm using strategy of jumping for raid (september 2018). IEEE Access, PP, 1-1. [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).