1. Introduction
1.1. Background and Motivation
The Internet of Things (IoT) represents a transformative technological revolution, with billions of devices now interconnected to enhance productivity, automation, and data-driven decision-making. IoT has seen rapid adoption across various industries, including healthcare, transportation, manufacturing, and smart cities. From wearable health monitors to autonomous vehicles, IoT innovations are reshaping how individuals and organizations interact with technology, offering real-time insights, increased operational efficiency, and cost savings. The benefits of IoT innovations are immense. In healthcare, IoT devices enable remote patient monitoring and predictive diagnostics, significantly improving patient outcomes and reducing healthcare costs. In manufacturing, IoT-driven automation optimizes production lines, minimizing downtime and maximizing resource efficiency. The integration of IoT in smart cities enhances urban living by improving traffic management, energy Efficiency and public safety. Across all sectors, IoT is becoming a critical enabler of digital transformation. This rapid growth in IoT adoption comes with emerging concerns related to security and privacy. As more devices connect to the internet, the attack surface for cybercriminals widens, exposing vulnerabilities in unsecured IoT networks and devices. Poorly implemented security protocols, inadequate encryption, and lack of regular updates make IoT devices prime targets for cyberattacks. The interconnected nature of IoT means that a single compromised device can lead to widespread disruption, impacting businesses, governments, and individuals. These concerns underscore the need for robust cybersecurity frameworks to protect the growing IoT ecosystem from cybercrime, ensuring that the benefits of IoT do not come at the cost of security and privacy.
1.2. Problem Statement
The unprecedented growth of IoT technologies is not only transforming industries but also creating new and significant opportunities for cybercrime. As the number of IoT devices rapidly increases, so too does the complexity of the ecosystem, making it challenging to secure every component effectively. These devices, often deployed with minimal security features or outdated software, provide cybercriminals with easy entry points into broader networks. The diverse applications of IoT across critical infrastructures such as healthcare, energy, and transportation further exacerbate the risks, as a single compromised device can disrupt entire systems. The interconnected nature of IoT devices creates a vast attack surface, where vulnerabilities in even the smallest devices can be exploited to launch large-scale cyberattacks, including Distributed Denial of Service (DDoS) attacks, data breaches, and ransomware incidents. Moreover, many IoT devices are designed with limited computational power, making it difficult to implement strong encryption or robust authentication mechanisms. This lack of built-in security exposes users, businesses, and governments to potential exploitation by cybercriminals who leverage these weaknesses for malicious activities. With the rise of artificial intelligence (AI) and machine learning (ML), attackers are becoming more sophisticated in their methods, using these advanced technologies to identify and exploit IoT vulnerabilities at an unprecedented scale. The problem is further compounded by the lack of uniform regulatory standards, leaving significant gaps in the governance and protection of IoT devices. As IoT continues to expand, these security challenges grow more pressing, making it essential to address how IoT technologies are fueling the future of cybercrime.
1.3. Objective of the Study
The primary objective of this paper is to explore the potential cybersecurity threats and vulnerabilities introduced by the rapid proliferation of Internet of Things (IoT) technologies. As IoT adoption accelerates across industries, it is essential to examine how these interconnected devices, while offering numerous benefits, also create a wide array of security risks. The paper aims to:
Identify and Analyze IoT Vulnerabilities: Investigate the most common security weaknesses in IoT devices, networks, and protocols, including insufficient authentication, poor encryption, and weak firmware updates.
Examine the Evolving Threat Landscape: Explore how cybercriminals are increasingly targeting IoT devices for a range of malicious activities, including data theft, network infiltration, Distributed Denial of Service (DDoS) attacks, and ransomware.
Evaluate Real-World Case Studies: Review documented cases of IoT-related cyberattacks to understand the scope and impact of these threats on industries such as healthcare, smart cities, manufacturing, and critical infrastructure.
Assess Regulatory and Policy Gaps: Analyze current IoT security policies and frameworks, identifying gaps in governance that contribute to the increasing risk of cybercrime.
Recommend Mitigation Strategies: Provide recommendations for enhancing the security of IoT devices and networks, including best practices, technological solutions, and the need for stronger collaboration between industry, government, and academia.
1.4. Structure of the Paper
Introduction: Provides an overview of the Internet of Things (IoT), highlighting its rapid adoption across various industries and the significant benefits it offers. The introduction also outlines the emerging concerns related to IoT security and privacy, leading to the central problem of how IoT innovations are creating new opportunities for cybercrime. Literature Review: Reviews existing research on IoT adoption, security challenges, and the evolving cyber threat landscape. This section discusses the current understanding of IoT vulnerabilities and how they have been exploited by cybercriminals in various sectors. Methodology: Details the research approach used to investigate IoT-related cybersecurity threats. This section describes the case studies, data collection methods, and analytical techniques employed to assess IoT vulnerabilities and cybercrime incidents. Cybercrime and IoT: Threats and Vulnerabilities: Explores the specific security weaknesses in IoT devices, networks, and protocols. It also discusses how cybercriminals are leveraging these vulnerabilities to conduct attacks and introduces the growing use of AI and machine learning in facilitating cybercrime. Case Studies/Examples: Presents real-world examples of high-profile cyberattacks involving IoT devices, examining their impact on various industries and highlighting the scale of potential damage from IoT-related breaches. Discussion: Analyzes the implications of the findings for businesses, consumers, and policymakers. It also addresses the gaps in current regulatory frameworks and explores the role of government and industry in mitigating these risks. Proposed Solutions and Mitigation Strategies: Offers recommendations for securing IoT devices and networks, including technological solutions, best practices, and the need for comprehensive cybersecurity frameworks. Conclusion: Summarizes the key findings of the paper and discusses future research directions. It emphasizes the urgency of addressing IoT security risks to prevent large-scale cybercrime incidents.
2. Literature Review
2.1. IoT Adoption and Impact
The adoption of Internet of Things (IoT) technologies has been growing rapidly across various sectors, transforming industries and enhancing efficiency, automation, and connectivity. In sectors like healthcare, manufacturing, transportation, and smart cities, IoT devices are increasingly being integrated to optimize operations and improve decision-making. In healthcare, IoT-enabled devices such as wearables and remote patient monitoring systems are improving patient care by providing real-time health data to medical professionals. In the manufacturing sector, IoT is streamlining production processes through automation and predictive maintenance, reducing downtime and operational costs. Similarly, smart cities are utilizing IoT to manage traffic, reduce energy consumption, and improve public safety.
The benefits of IoT technologies are vast and far-reaching. They offer increased convenience for consumers, allowing for seamless interactions between devices and creating smart environments in homes, workplaces, and urban settings. A business benefit from IoT’s ability to provide real-time data analytics, which improves operational efficiency, enhances customer experiences, and reduces costs. IoT also drives innovation in industries such as agriculture, where smart farming technologies enable more precise resource management and crop monitoring. Despite these advancements, the rapid adoption of IoT also raises significant security and privacy concerns. The exponential growth of connected devices introduces a larger attack surface for cybercriminals, making IoT security a critical area of concern. Understanding the balance between the benefits of IoT and its associated risks is essential to fully realizing its potential while safeguarding against emerging cyber threats.
2.2. IoT Security Challenges
The rapid growth of IoT has been accompanied by an array of security challenges, as numerous studies have highlighted vulnerabilities in IoT devices and their supporting infrastructure. These security weaknesses create significant risks for businesses, consumers, and governments alike. One of the major concerns is that many IoT devices are designed with minimal security features, often prioritizing functionality and cost over robust protection. This makes them prime targets for cybercriminals, who can exploit these vulnerabilities for malicious purposes.
2.3. Cybersecurity Threats in IoT
Several studies have documented the cybersecurity threats that stem from IoT’s interconnected nature. Common threats include Distributed Denial of Service (DDoS) attacks, where multiple compromised IoT devices are used to flood a target with traffic, rendering it unusable. The infamous Mirai botnet attack is a prominent example, where millions of compromised IoT devices were exploited to launch large-scale DDoS attacks. Data breaches are another major concern, as IoT devices frequently collect and transmit sensitive personal or business data, which can be intercepted if communication protocols are not adequately encrypted.
2.4. Known Weaknesses in IoT Devices and Infrastructure
IoT devices are often vulnerable due to several inherent weaknesses:
- -
Inadequate Authentication and Authorization: Many IoT devices lack robust authentication mechanisms, relying on weak or default passwords. This allows unauthorized users to gain access to devices and networks.
- -
Unencrypted Communication: Some IoT devices transmit data without proper encryption, making it susceptible to interception by attackers. Unsecured communication channels are particularly risky in sectors like healthcare, where sensitive patient data is at stake.
- -
Insufficient Patch Management: IoT devices frequently run on outdated software, and manufacturers may not provide timely security updates. This exposes devices to vulnerabilities that have already been exploited in the wild.
- -
Resource Constraints: Due to the limited processing power and memory of many IoT devices, implementing advanced security measures such as strong encryption or firewalls can be challenging.
2.5. Existing Cybercrime Studies
2.5.1. The Mirai Botnet Attack
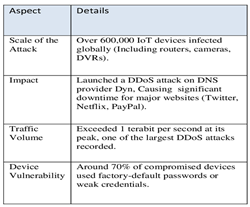
One of the most well-documented IoT-related cybercrime cases is the Mirai botnet attack in 2016, which demonstrated the scale at which compromised IoT devices could be used to launch Distributed Denial of Service (DDoS) attacks. Researchers identified that Mirai infected millions of IoT devices, such as routers, IP cameras, and DVRs, by exploiting default credentials. Once compromised, these devices were conscripted into a botnet that overwhelmed the servers of major internet services, resulting in widespread outages. This case illustrates how easily unsecured IoT devices can be hijacked and weaponized for cyberattacks.
Table 1.
Concise view of the key data points related to the Mirai botnet attack.
Table 1.
Concise view of the key data points related to the Mirai botnet attack.
2.5.2. Smart Home Device Hijacking
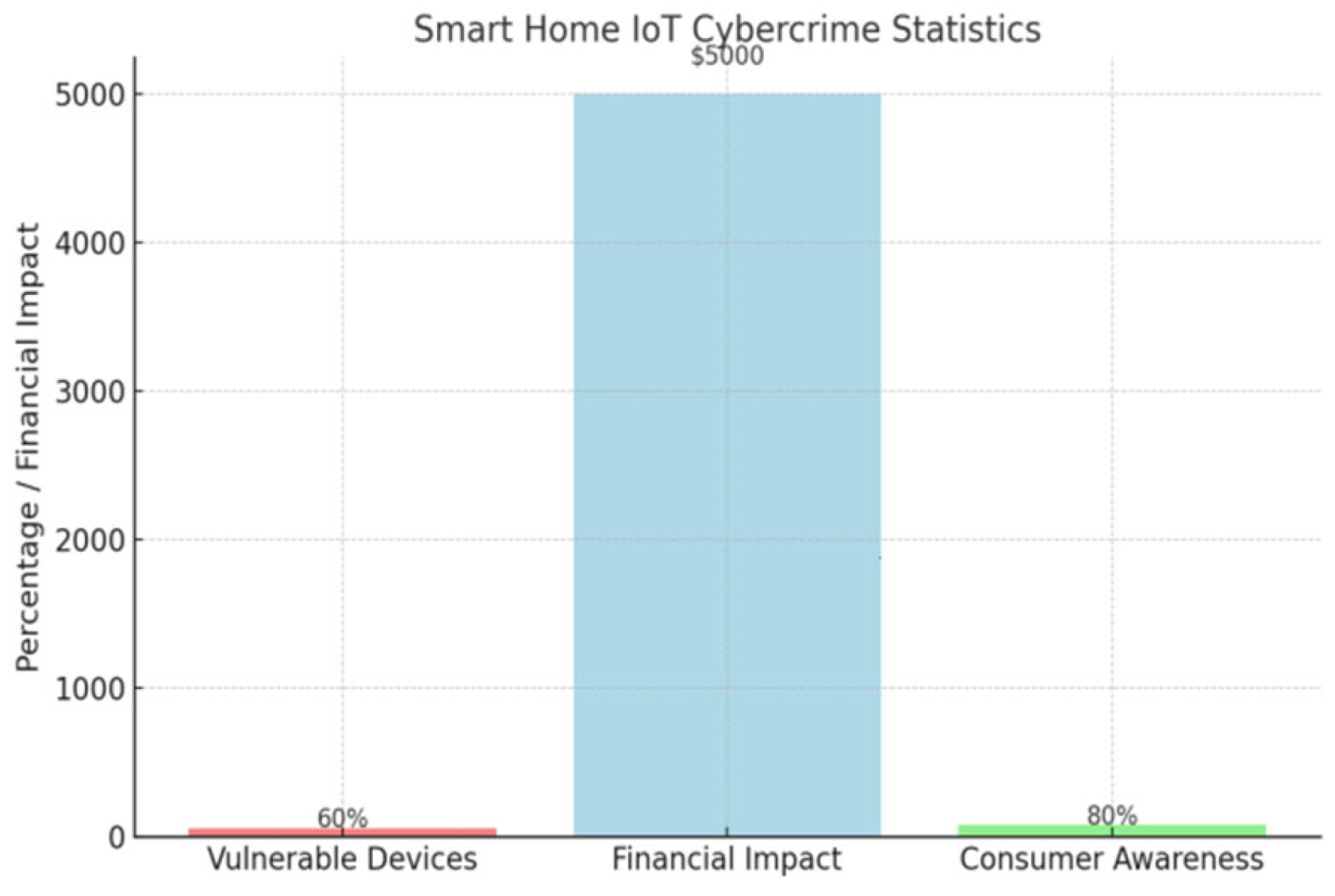
Another critical study explored the vulnerabilities in smart home devices, such as smart thermostats, locks, and cameras. In 2017, researchers analyzed the exploitation of weak authentication protocols in smart home IoT ecosystems. Hackers were able to hijack these devices and gain unauthorized access to private networks. This enabled them to surveil homeowners, compromise their privacy, and manipulate devices remotely. Smart home device hijacking poses significant risks as more consumers integrate IoT devices into their homes without proper security configurations. The study highlighted the need for stronger authentication measures, encryption, and user education in securing home IoT environments.
Figure 1.
Smart Home IoT Cybercrime Statistics.
Figure 1.
Smart Home IoT Cybercrime Statistics.
2.5.3. Healthcare IoT Device Exploitation
IoT devices in healthcare, such as connected medical devices and monitoring systems, are also prime targets for cybercriminals. A 2018 study reviewed the vulnerabilities of IoT devices in hospitals, with a specific focus on pacemakers and insulin pumps. Cybercriminals exploited these devices to manipulate medical data, interrupt treatment protocols, or even threaten patient safety. One notable case involved ransomware attacks targeting hospital networks that relied on IoT devices, leading to critical disruptions in patient care. These attacks demonstrated how IoT device exploitation in healthcare can have life-threatening consequences, and the study called for stricter security standards in medical IoT.
2.5.4. Analysis of Real-World Cases
These real-world cases highlight a common theme: cybercriminals exploit the inherent weaknesses in IoT devices to gain unauthorized access, steal data, and disrupt services. The Mirai botnet case underscores how cybercriminals can leverage large numbers of unsecured devices to launch devastating attacks on a global scale. The smart home device hijacking incidents show the personal risks of IoT device exploitation, while the healthcare IoT exploitation demonstrates the potentially fatal consequences when critical infrastructure is compromised. In all three cases, a lack of robust security measures—such as poor authentication, unencrypted communication, and outdated software—allowed cybercriminals to easily infiltrate IoT ecosystems. These studies emphasize the need for IoT manufacturers, businesses, and users to prioritize security, with stronger encryption, regular software updates, and better regulatory oversight to mitigate future cybercrime risks associated with IoT.
The analysis of real-world cases involving cyberattacks on Internet of Things (IoT) devices illustrates the serious vulnerabilities inherent in these technologies and their potential to cause significant harm. One notable example is the Target data breach in 2013, which, while not directly involving healthcare, underscores the implications of IoT vulnerabilities across industries. Cybercriminals gained access to Target’s network through an IoT-enabled HVAC system. By exploiting weak security protocols in this third-party vendor’s system, attackers infiltrated Target’s internal network and accessed sensitive customer data. The breach resulted in the theft of 40 million credit and debit card records, along with personal information from an additional 70 million customers. The fallout was considerable, with Target incurring nearly $292 million in related expenses, including legal fees, customer compensation, and system upgrades. This incident exemplifies how interconnected devices, even those seemingly unrelated to critical data storage, can serve as entry points for cyberattacks, highlighting the importance of robust cybersecurity measures in all aspects of IoT implementation.
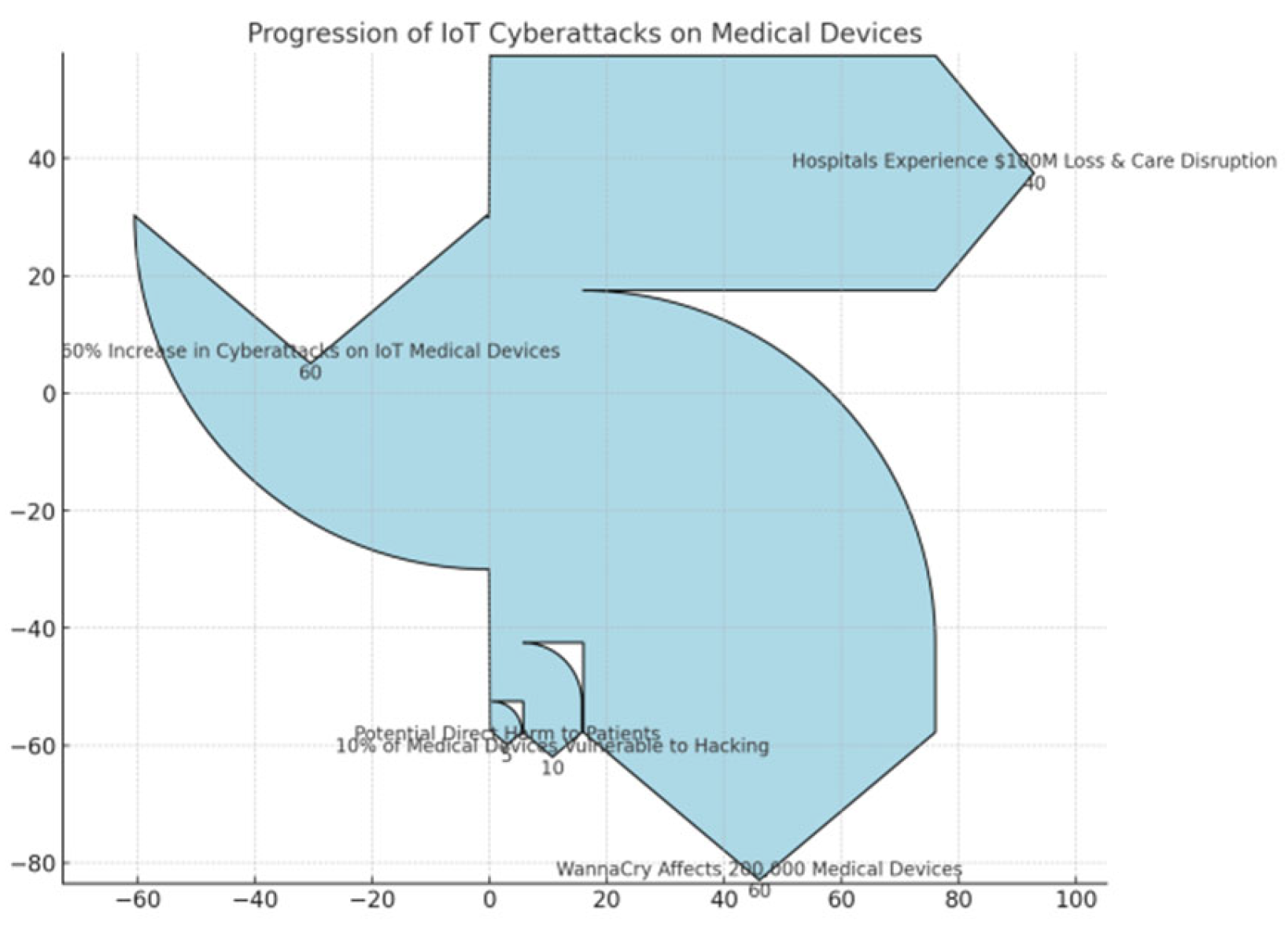
In the healthcare sector, the vulnerabilities of IoT medical devices were starkly revealed in the case of St. Jude Medical devices in 2017. Researchers identified significant security flaws in implantable cardiac devices such as pacemakers and defibrillators. These devices relied on weak encryption protocols, leaving them susceptible to remote attacks. A compromised device could be manipulated to deliver inappropriate electrical shocks to a patient’s heart or, conversely, to prevent necessary shocks, posing a direct risk to patient safety. The implications of this vulnerability were profound, as it raised alarms about the security of life-sustaining medical technologies. The Food and Drug Administration (FDA) issued warnings, and St. Jude had to initiate a recall to address these vulnerabilities, emphasizing the critical need for cybersecurity measures in medical IoT applications. Another case that drew attention to the vulnerabilities of IoT devices occurred with the Mirai botnet, which surfaced in 2016. This botnet infected over 600,000 IoT devices globally, including routers, cameras, and DVRs. By utilizing these devices to launch distributed denial-of-service (DDoS) attacks, Mirai brought down major websites such as Twitter, Netflix, and PayPal. At its peak, the botnet generated traffic volumes exceeding 1 terabit per second, marking one of the largest DDoS attacks recorded at the time. The incident highlighted the fact that many IoT devices were deployed with factory-default passwords, allowing cybercriminals to easily compromise them. The attack not only disrupted online services but also demonstrated the critical need for manufacturers to prioritize security in the design and deployment of IoT devices.
The WannaCry ransomware attack in 2017 affected healthcare systems worldwide, demonstrating the vulnerabilities of interconnected medical devices and hospital networks. This attack exploited weaknesses in Windows operating systems, affecting over 200,000 computers in more than 150 countries. The UK’s National Health Service (NHS) was particularly hard hit, as hospitals faced disruptions in patient care, leading to significant financial losses estimated at around $100 million. The ransomware locked healthcare providers out of their systems, delaying surgeries and essential treatments. The WannaCry incident revealed the urgent need for enhanced cybersecurity protocols in healthcare settings, where the stakes are often life-critical. These cases collectively underscore the pressing cybersecurity challenges posed by the proliferation of IoT devices across various sectors.
Figure 2.
Progression of IoT Cyberattacks on Medical Devices.
Figure 2.
Progression of IoT Cyberattacks on Medical Devices.
3. Methodology
A mixed-methods approach was employed to comprehensively explore the cybersecurity challenges associated with IoT devices. The combination of quantitative and qualitative research methods allowed for a more holistic understanding of the issue, addressing both the statistical prevalence of cyberattacks and the underlying vulnerabilities in IoT systems.
3.1. Quantitative Analysis
The quantitative aspect of the research involved gathering and analyzing data from various reports, databases, and case studies of real-world IoT-related cyberattacks. Statistical data on the frequency, scale, and financial impact of cyber incidents, such as the Mirai botnet attack, WannaCry ransomware, and Target breach, were collected. This data was used to identify trends in cybercrime related to IoT, including the number of devices compromised, financial losses incurred, and the volume of traffic generated in distributed denial-of-service (DDoS) attacks. By compiling this numerical data, the study aimed to quantify the growing risks posed by insecure IoT ecosystems.
3.2. Qualitative Analysis
In parallel, qualitative methods were used to gain deeper insights into the causes and consequences of IoT vulnerabilities. This involved a review of existing literature, expert interviews, and case study analyses. Specific focus was placed on identifying common security flaws in IoT devices, such as weak authentication protocols, unpatched software, and inadequate encryption. Additionally, qualitative analysis of case studies, including the exploitation of medical IoT devices in healthcare, helped to contextualize the impact of these vulnerabilities on critical sectors. Expert interviews provided further depth to the understanding of evolving cybercriminal tactics and the cybersecurity measures needed to mitigate such risks.
This mixed-methods approach allowed the study to combine empirical data with qualitative insights, offering both a broad statistical overview and a nuanced examination of the cybersecurity landscape in IoT. By blending these methodologies, the research was able to provide a comprehensive analysis of the issue, identifying key trends, vulnerabilities, and potential solutions.
Data collection
This study primarily relies on secondary data and case studies to analyze IoT-related cybercrimes. The data collection process involved the following methods:
Detailed case studies of significant IoT-related cyberattacks, such as the Mirai botnet attack, WannaCry ransomware, and the Target HVAC system breach, were used to examine real-world examples of IoT vulnerabilities. These case studies provided insights into the nature of the attacks, the compromised devices, the scale of damage, and the lessons learned from these incidents. The use of case studies allowed the study to analyze both the technical aspects of the cyberattacks and their broader implications on security practices in various industries.
-
2.
Secondary Data:
Data was gathered from a range of existing reports, studies, and cybersecurity databases that track IoT-related cyberattacks. This included information from cybersecurity research firms, industry reports, governmental agencies, and academic studies. The secondary data provided statistical insights on the frequency, scale, and financial impact of cybercrimes involving IoT devices. For example, data on the number of compromised devices, DDoS traffic volumes, and financial losses from cyber incidents like WannaCry were used to quantify the risks associated with IoT technologies.
Data Analysis
The collected data was analyzed using a combination of qualitative and quantitative techniques to gain a comprehensive understanding of the relationship between IoT innovations and cybercrime. The following tools and techniques were employed:
Statistical Analysis: Quantitative data, such as the frequency of cyberattacks, financial losses due to IoT-related breaches, and the number of vulnerable IoT devices, was analyzed using statistical tools like SPSS and Excel. Descriptive statistics were used to identify trends, such as the increase in cyberattacks over time and the proportion of IoT devices affected by security vulnerabilities.
Case Study Analysis: A qualitative approach was used to examine real-world case studies of cyberattacks involving IoT devices, such as the Mirai botnet and WannaCry ransomware. The case studies provided insights into the methods used by cybercriminals and the specific vulnerabilities they exploited. These cases were analyzed to identify common attack vectors and patterns in IoT-related cybercrimes.
Network Traffic Analysis: In instances where network logs were available, Wireshark and other packet analysis tools were used to examine network traffic patterns during IoT-based cyberattacks. This helped in understanding the types of data being targeted and how attackers managed to breach IoT networks.
Content Analysis: Secondary data from research papers, reports, and surveys were reviewed using content analysis to identify common themes and challenges related to IoT security. The focus was on the security vulnerabilities frequently mentioned in the literature and the proposed mitigation strategies.
Scope and Limitations
The study focuses on the cybersecurity threats and vulnerabilities associated with consumer IoT devices (smart homes, personal wearables) and industrial IoT systems (smart factories, critical infrastructure). It analyses the technological, regulatory, and user-related factors contributing to the rise of IoT-related cybercrime. Additionally, the study investigates the role of AI and machine learning in facilitating more sophisticated cyberattacks on IoT networks.
Limitations:
Data Availability: The study relies heavily on secondary data sources and publicly available case studies. Some data, particularly from private organizations and cybercriminals, may not be fully accessible or accurately reported, leading to potential gaps in analysis.
Rapid Technological Changes: As IoT technology evolves rapidly, new threats and vulnerabilities are emerging. The study’s findings may not account for future developments in IoT security, especially as newer devices and protocols are introduced.
Focus on Certain Sectors: While the study covers a broad range of IoT applications, the in-depth analysis is limited to specific sectors like healthcare, smart homes, and industrial IoT. The implications for other sectors such as agriculture or retail may not be fully explored.
Generalization: Given the diverse range of IoT devices and use cases, the findings of this research may not be universally applicable to all IoT systems. Security requirements for industrial IoT may differ significantly from those of consumer devices, and thus some conclusions may not generalize across all IoT domains.
4. Cybercrime and IoT: Threats and Vulnerabilities
Types of Cyber Threats
4.1. Data Breaches
IoT devices collect and transmit vast amounts of sensitive data, including personal, financial, and health information. Inadequate encryption, lack of secure transmission protocols, and default credentials can leave these devices vulnerable to breaches. When cybercriminals gain access to this data, it can result in identity theft, financial fraud, or the unauthorized distribution of personal information. IoT devices used in healthcare, for example, often store critical patient information, making data breaches particularly damaging in this sector.
4.2. Distributed Denial of Service (DDoS) Attacks
Cybercriminals exploit compromised IoT devices to launch DDoS attacks, overwhelming targeted servers or networks with excessive traffic and rendering them unavailable. The Mirai botnet is one of the most notorious examples, in which thousands of insecure IoT devices were used to launch large-scale DDoS attacks on major websites and online services. With the growing number of connected devices, such attacks are becoming easier for hackers to organize and harder to defend against.
4.3. Identity Theft
IoT devices often store or transmit authentication credentials, and if improperly secured, they can be vulnerable to theft. Hackers can exploit weak authentication mechanisms to steal user credentials, giving them access to a broader range of systems, including financial accounts, emails, and even smart home environments. Identity theft can have far-reaching consequences for individuals and businesses, leading to financial loss and reputational damage.
4.4. Device Hijacking
Hackers can take control of IoT devices remotely, manipulating them for malicious purposes. For instance, compromised security cameras can be used for spying, or smart home devices like thermostats and door locks can be controlled to disrupt or invade privacy. Worse yet, cybercriminals can hijack connected medical devices, such as pacemakers or insulin pumps, posing a direct threat to patients’ lives. In industrial settings, IoT device hijacking could cause massive operational disruptions.
Potential for Abuse by Cybercriminals:
Cybercriminals exploit the vulnerabilities in IoT systems in various ways, including for data theft, espionage, and sabotage. For instance, the Mirai botnet demonstrated how attackers can leverage insecure devices to create vast networks of compromised systems that can be weaponized for large-scale attacks. Similarly, ransomware attacks have started targeting IoT devices in healthcare and smart homes, where critical operations and safety are at risk. In industrial IoT environments, attackers can disrupt manufacturing processes by hijacking connected devices that control critical systems. By exploiting these vulnerabilities, cybercriminals can engage in corporate espionage, shutting down production lines or accessing proprietary business data. The impact of these attacks can be far-reaching, not only in terms of financial losses but also in terms of public safety.
Use of AI and Machine Learning by Cybercriminals
As IoT technologies evolve, so do the methods employed by cybercriminals. AI and machine learning (ML) are increasingly being leveraged to enhance the scale, complexity, and effectiveness of attacks on IoT systems. Cybercriminals use AI to analyze vulnerabilities in large IoT networks, identify patterns of weakness, and automate attacks at unprecedented speeds. For instance, AI-powered botnets can dynamically select the most vulnerable devices to compromise and adapt to defenses more quickly than traditional attacks. Machine learning algorithms can also be used to bypass anomaly detection systems, making it easier to infiltrate IoT networks undetected. Attackers can deploy AI to mimic legitimate traffic patterns or launch sophisticated phishing campaigns that deceive IoT administrators. Additionally, AI and ML techniques are being utilized to crack passwords and decrypt secure communications more efficiently. As these technologies continue to evolve, the sophistication and precision of cyberattacks targeting IoT devices will increase, presenting an even greater challenge for defenders. In conclusion, the rapid expansion of IoT technology has introduced significant security vulnerabilities that are actively being exploited by cybercriminals. The integration of AI into these attacks only heightens the risks, underscoring the need for robust security measures to protect IoT devices, networks, and data from future cyber threats.
5. Case Studies
High-Profile IoT Cybercrime Incidents:
1. The Mirai Botnet Attack
One of the most infamous IoT cyberattacks, the Mirai botnet infected over 600,000 IoT devices, including routers, security cameras, and DVRs, in 2016. The botnet used these compromised devices to launch a massive Distributed Denial of Service (DDoS) attack on Dyn, a major Domain Name System (DNS) provider, causing widespread outages for websites such as Twitter, Netflix, and PayPal. The attack generated traffic volumes of over 1 terabit per second; making it one of the largest DDoS attacks in history. The primary vulnerability exploited was the use of default factory settings, such as weak passwords and unprotected ports, which allowed the malware to spread rapidly. This incident highlighted the critical security flaws in millions of IoT devices and exposed how poorly secured devices could be turned into powerful cyber weapons.
2. WannaCry Ransomware
In 2017, the WannaCry ransomware attack affected over 200,000 systems across 150 countries, many of which were IoT-enabled medical devices. Hospitals, including the UK’s National Health Service (NHS), experienced significant disruptions, with surgeries being delayed and medical services affected. The ransomware encrypted the data on medical devices, demanding payments for decryption keys. The attack caused an estimated $100 million in financial losses to the healthcare sector. It exposed the vulnerabilities in medical IoT devices such as MRI scanners and X-ray machines, which often run outdated software with insufficient security protections, and emphasized the need for stronger safeguards in critical healthcare systems.
3. Target HVAC System Breach
In 2013, attackers exploited vulnerability in the HVAC system (heating, ventilation, and air conditioning) of Target, a leading U.S. retailer, to gain access to the company’s internal network. The attackers were able to steal the payment information of over 40 million customers. The breach was initiated through an IoT-enabled HVAC system that was connected to the main corporate network, and the attackers used this entry point to move laterally and access the company’s point-of-sale systems. This breach demonstrated how the interconnected nature of IoT devices in commercial settings could lead to significant cyberattacks and exposed the risks of failing to segment networks for critical systems.
Impact on Various Sectors
1. Healthcare
IoT devices in healthcare, such as connected pacemakers, insulin pumps, and medical imaging systems, have revolutionized patient care by providing real-time data and remote monitoring. However, these same devices have also introduced significant security risks. As seen in the WannaCry attack, compromised IoT devices can cause critical delays in patient care, leading to life-threatening situations. A survey conducted by HIMSS found a 60% increase in cyberattacks targeting IoT medical devices from 2017 to 2018. Vulnerabilities in these devices, such as outdated software and weak encryption, make them prime targets for ransomware and other forms of cyberattacks, putting both patient data and safety at risk.
2. Transportation
The rise of connected vehicles and IoT-enabled transportation systems has improved efficiency and safety, but it also opens up the sector to cyberattacks. In one prominent case, researchers demonstrated the ability to remotely hack a Jeep Cherokee in 2015, taking control of critical vehicle functions such as steering and brakes. This vulnerability, due to weaknesses in the vehicle’s onboard infotainment system, raised alarm over the potential for malicious actors to exploit connected vehicles, causing accidents or disrupting transportation networks. As autonomous vehicles and smart traffic systems become more prevalent, the risk of cyberattacks targeting transportation infrastructure will continue to grow.
3. Smart Homes
The rapid adoption of IoT devices in homes—such as smart thermostats, security cameras, and voice assistants —has increased convenience but also introduced new privacy and security risks. In many cases, these devices have been found to use default passwords, weak encryption, or even transmit unencrypted data, making them easy targets for hackers. The Mirai botnet attack exemplifies how compromised smart home devices can be weaponized to launch large-scale cyberattacks. Additionally, hacked smart home devices can lead to privacy breaches, where attackers gain unauthorized access to security cameras or personal data, threatening the privacy and safety of users.
4. Critical Infrastructure
IoT devices play a crucial role in critical infrastructure systems, including power grids, water treatment plants, and oil pipelines. However, their use has also introduced new vulnerabilities. In one case, hackers were able to manipulate the controls of a German steel mill in 2014, causing significant damage to the facility’s blast furnace. Attackers exploited weaknesses in the mill’s industrial IoT systems to disrupt operations, underscoring the dangers of poor security in critical infrastructure. The interconnected nature of these systems, combined with insufficient cybersecurity measures, increases the potential for cyberattacks that could have far-reaching consequences on public safety and national security.
6. Discussion
Emerging Threat Landscape
As IoT technology continues to evolve and proliferate, it presents a growing risk of enabling more sophisticated and large-scale cybercrimes. The sheer volume of connected devices—ranging from smart home gadgets to industrial control systems—creates an expanded attack surface for cybercriminals. Future threats may involve the exploitation of AI-powered IoT devices, where compromised systems could be used to carry out automated, highly targeted attacks. As devices become more autonomous and integrated into critical infrastructure, such as healthcare, transportation, and utilities, the consequences of IoT-related cybercrimes could become more severe, potentially disrupting essential services and endangering lives. Additionally, the rise of 5G networks will accelerate IoT connectivity, enabling even larger botnets, such as Mirai, to orchestrate Distributed Denial-of-Service (DDoS) attacks of unprecedented scale. Ransomware attacks may also evolve, with cybercriminals locking not just data, but entire fleets of IoT devices, threatening significant operational shutdowns until a ransom is paid.
Implications for Businesses and Consumers
For businesses, IoT innovation brings both benefits and risks. The integration of IoT devices into operations increases efficiency and productivity, but it also opens up new vulnerabilities. Cybercriminals could exploit weaknesses in these devices to gain unauthorized access to corporate networks, leading to data breaches, financial loss, and reputational damage. A compromised IoT device could act as an entry point for attacks that spread throughout the organization, such as the 2013 Target breach. Moreover, industrial sectors reliant on IoT for automation and process control—such as manufacturing, energy, and logistics—are particularly vulnerable to attacks that could cause widespread disruption. For consumers, the risks are equally significant. IoT devices in smart homes—such as security cameras, thermostats, and medical devices—often lack robust security features. This makes them easy targets for hackers, who could invade privacy, steal personal data, or compromise critical devices such as pacemakers or insulin pumps. The consequences for individuals could range from financial theft to life-threatening situations. As IoT becomes more ingrained in daily life, consumers need to be aware of the security risks associated with their devices and take steps to protect them.
Policy and Regulatory Gaps
Despite the growing importance of IoT security, current policies and regulations are lagging behind the technological advancements. While there are initiatives like the NIST Cybersecurity Framework and the EU Cybersecurity Act, many IoT devices still lack standard security protocols, leaving them vulnerable to attacks. Regulations often focus on data protection rather than securing the devices themselves, leading to a gap in ensuring the security of the IoT infrastructure. Moreover, existing policies tend to be reactive, addressing security breaches after they occur rather than enforcing preventive measures. There is a lack of universal standards that IoT device manufacturers must follow, such as requirements for encryption, regular software updates, and strong authentication protocols. This regulatory gap enables manufacturers to prioritize cost and time-to-market over security, resulting in a large number of insecure devices on the market. To address this, new policies need to enforce stricter security requirements for all IoT devices from development through to deployment.
The Role of Government and Industry
Government bodies and the tech industry have a crucial role to play in addressing the evolving threats posed by IoT devices. Governments should take the lead in developing and enforcing regulations that mandate security standards for IoT devices. This could include legislation requiring manufacturers to implement strong encryption, ensure patchable firmware, and eliminate the use of default passwords. Regulatory bodies could also establish certification programs that test IoT devices for compliance with security standards before they are allowed to enter the market. Beyond legislation, governments can also invest in cybersecurity research to anticipate and counter emerging threats in the IoT space. Collaboration between countries is necessary as cybercrime is often global in scope, with attackers exploiting cross-border vulnerabilities. The tech industry, on the other hand, must take a proactive approach to improving IoT security. Manufacturers should embed security into the design of their products, ensuring that devices are secure by default. Tech companies also need to collaborate with cybersecurity experts, conducting regular vulnerability assessments and sharing information on emerging threats. Industry consortia could work together to develop universal standards and best practices that prioritize IoT security across all sectors. At the same time, companies should invest in user education, ensuring that consumers are aware of the potential risks and know how to protect their devices.
7. Proposed Solutions and Mitigation Strategies
IoT Security Frameworks
One of the most effective approaches to securing IoT devices and networks is the implementation of comprehensive IoT security frameworks. These frameworks provide structured guidelines and standards for securing IoT environments across various sectors. For instance, the IoT Security Framework by NIST (National Institute of Standards and Technology) offers guidelines that address device identification, secure onboarding, data protection, and system monitoring. A strong security framework emphasizes the need for device authentication, secure boot processes, regular patching, and network segmentation to ensure that IoT devices cannot be easily compromised. Additionally, zero-trust architectures are becoming popular in IoT environments, where every device and connection is continuously verified before being granted access to the network. By adhering to standardized security frameworks, businesses can significantly reduce the attack surface of their IoT systems.
Technological Solutions
Emerging technologies are playing a key role in enhancing IoT security. Artificial Intelligence (AI) and Machine Learning (ML) are being increasingly integrated into IoT systems for real-time threat detection and mitigation. AI-driven security solutions can analyze large datasets, identify patterns in network traffic, and detect anomalies that may signal an ongoing attack. AI-based intrusion detection systems (IDS) can significantly reduce response times and improve defense mechanisms against sophisticated cyberattacks. Another vital solution lies in encryption technologies. Strong end-to-end encryption ensures that data transmitted between IoT devices and servers is secure, protecting it from interception and tampering. Advanced Encryption Standard (AES) and public-key infrastructure (PKI) are widely used encryption methods that can safeguard IoT communications and stored data. Secure device management is also critical for protecting IoT ecosystems. This includes ensuring that devices can be regularly updated with security patches, monitored for vulnerabilities, and properly decommissioned when necessary. Firmware over-the-air (FOTA) updates allow manufacturers to remotely update device software and address emerging threats, while secure boot mechanisms ensure that devices start only with authorized software, preventing malicious tampering.
Conclusions
This study has shown that while IoT innovation brings immense benefits across various sectors, it also introduces new vulnerabilities that are increasingly being exploited by cybercriminals. The rapid adoption of IoT devices, often with insufficient security measures, has led to a rise in cyberattacks such as the Mirai botnet, WannaCry ransomware, and the Target HVAC system breach. These cases illustrate the critical weaknesses in IoT systems, including the use of default passwords, weak encryption, and inadequate network segmentation. The research highlights that as IoT devices become more embedded in essential infrastructure—such as healthcare and smart homes—the potential damage from cyberattacks grows significantly. Cybercriminals are exploiting these vulnerabilities to launch large-scale attacks, often with devastating financial, operational, and even safety-related consequences. Given the growing risks posed by IoT-related cybercrime, future research should focus on developing more advanced security protocols and technologies to protect IoT ecosystems. This includes creating enhanced encryption algorithms, robust authentication mechanisms, and secures device management systems that can address the specific vulnerabilities found in IoT devices. Additionally, research should explore AI-driven cybersecurity solutions capable of detecting and mitigating threats in real-time. More attention should also be given to IoT device standardization, ensuring that manufacturers follow stringent security guidelines from the outset. Further investigation into the legal and regulatory frameworks governing IoT security, as well as the role of global cooperation in countering these cyber threats, is essential for a comprehensive approach to mitigating the risks of IoT-related cybercrime. As IoT continues to transform industries, there is an urgent need for increased awareness of the security risks associated with these technologies. Governments, businesses, and manufacturers must collaborate to establish stronger policies that mandate secure design, development, and deployment of IoT devices. This includes enforcing regular software updates, encouraging end-user education, and promoting responsible usage of IoT devices. Furthermore, collaborative efforts between public and private sectors are crucial to building a safer IoT environment. By prioritizing security in the IoT development lifecycle and fostering a proactive approach to cybersecurity, we can prevent future cybercrimes and ensure that the benefits of IoT innovation are not undermined by its risks.
References
- Altulaihan, E.; Almaiah, M.A.; Aljughaiman, A. Cybersecurity threats, countermeasures, and mitigation techniques on the IoT: Future research directions. Electronics 2022, 11, 3330. [Google Scholar] [CrossRef]
- Antonakakis, M.; et al. “Understanding the Mirai Botnet”. 26th USENIX Security Symposium. 2017. [CrossRef]
- Babar, S.; Stango, A.; Prasad, N.; Sen, J.; Prasad, R. Proposed embedded security framework for Internet of Things (IoT). Wireless Personal Communications 2011, 61, 443–464. [Google Scholar] [CrossRef]
- Burhan, M.; Rehman, R.A. , Khan, B.; Kim, B.S. IoT elements, layered architectures, and security issues: A comprehensive survey. Sensors 2018, 18, 2796. [Google Scholar] [CrossRef] [PubMed]
- Faisal, K.M. , & Nauman, M. Exploring the intersection of IoT and cybersecurity: A systematic review. ACM Computing Surveys 2020, 53, 125. [Google Scholar]
- Lee, I. Internet of Things (IoT) cybersecurity: Literature review and IoT cyber risk management. Future Internet 2020, 12, 157. [Google Scholar] [CrossRef]
- Luo, J.; Luo, X.; & Zhang, C.; & Zhang, C. A framework for IoT healthcare systems: Addressing cybersecurity challenges and risks. Journal of Medical Systems 2020, 44, 92. [Google Scholar]
- Mahajan, M.; Gupta, K.; Kant, V. IoT devices as vectors for cyberattacks: A comprehensive analysis of the security challenges and threats. Journal of Network and Computer Applications 2020, 162, 102655. [Google Scholar] [CrossRef]
- Nespoli, P.; Mariani, S.; & Chessa, S.; & Chessa, S. Cybersecurity in IoT-based smart homes: A review of current challenges. Journal of Cyber Security Technology 2021, 5, 139–161. [Google Scholar]
- Obaidat, I.; et al. Creating a Large-scale Memory Error IoT Botnet Using NS3DockerEmulator. IEEE 2023. [CrossRef]
- Singh, K.J. , Kapoor, D.S. Create your own internet of things: A survey of IoT platforms. IEEE Consumer Electronics Magazine 2017, 6, 57–68. [Google Scholar] [CrossRef]
- Taketzis, D.; Demertzis, K.; Skianis, C. Cyber threats to industrial IoT: A survey on attacks and countermeasures. IoT 2021, 2, 163–186. [Google Scholar] [CrossRef]
- Tao, F.; Zhang, H.; Liu, A.; Nee, A.Y.C. Digital twin in industry: State-of-the-art. IEEE Transactions on Industrial Informatics, 2019, 15, 2405–2415. [Google Scholar] [CrossRef]
- Xu, X.; Zheng, K.; Zhang, Y. An IoT-based framework for health monitoring systems. IEEE Internet of Things Journal, 2014, 1, 32–37. [Google Scholar]
- Yang, Z.; Cai, H.; Zheng, L. A survey on security and privacy issues in IoT-based smart environments. IEEE Internet of Things Journal 2022, 9, 7548–7562. [Google Scholar]
- Zahra, K.; Ejaz, W.; Jo, M.; Ahmad, A. Secure resource allocation for IoT devices with malicious device detection in cognitive radio networks. IEEE Internet of Things Journal 2020, 7, 2082–2093. [Google Scholar]
- https://doi.org/10.1109/JIOT.2020.2971925.
- Li, S.; Xu, L.D.; Zhao, S. The internet of things: A survey. Information Systems Frontiers 2018, 20, 241–259. [Google Scholar]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).