1. Introduction
The Internet of Things (IoT) is revolutionizing the way devices communicate, transforming traditional systems into interconnected ecosystems capable of data sharing and real-time decision-making. From smart homes to industrial automation, healthcare solutions, and smart cities, IoT has become an integral part of modern technology. These systems comprise a vast network of physical objects embedded with sensors, software, and other technologies, allowing them to connect and exchange data over the internet without the need for human interaction. As IoT adoption grows, it enables improved efficiency, personalized services, and innovations across multiple industries, drastically altering how businesses operate and how individuals engage with technology. For instance, in healthcare, IoT devices such as wearable monitors and remote sensors enhance patient care through continuous health monitoring. In industrial settings, IoT enables predictive maintenance, optimizing manufacturing processes and reducing downtime. Smart cities leverage IoT for better traffic management, resource allocation, and energy efficiency, while the automotive industry integrates IoT systems for autonomous driving and vehicle-to-vehicle communication. These examples represent only a fraction of the potential applications of IoT, which is expected to drive global digital transformation further in the coming years. However, alongside the advantages that IoT systems offer, significant security challenges have emerged. As billions of devices are connected to the internet, the potential attack surface for malicious actors has expanded dramatically. IoT devices, often with minimal security features, are increasingly vulnerable to cyberattacks. These vulnerabilities arise from several factors, including outdated software, weak authentication mechanisms, lack of encryption, and misconfigurations. The interconnected nature of IoT means that once a device is compromised, it can provide access to an entire network, resulting in severe consequences such as data breaches, unauthorized access to sensitive information, and even physical harm in the case of critical infrastructure like smart grids or healthcare devices. Cybercriminals are quick to exploit these security weaknesses, targeting IoT devices to launch attacks ranging from distributed denial-of-service (DDoS) attacks to ransomware. The Mirai botnet attack of 2016, which exploited vulnerable IoT devices to disrupt major internet services globally, is a notable example of the destructive potential when IoT systems are inadequately secured. As IoT adoption continues to grow, so too does the sophistication and frequency of attacks, presenting a pressing challenge for both the industry and policymakers. The rapid pace of IoT innovation has outpaced the development of effective security measures, leading to growing concerns over how to safeguard these systems from evolving cyber threats. Given this context, the primary objective of this paper is to enhance the security of IoT systems by focusing on the identification and management of key vulnerabilities that cybercriminals typically exploit. The research aims to provide a comprehensive framework for understanding the most common security weaknesses in IoT devices and networks and propose solutions that can effectively mitigate these risks. By leveraging state-of-the-art security techniques, such as artificial intelligence (AI)-based intrusion detection systems, Blockchain technology, and improved encryption methods, this paper seeks to contribute to the ongoing efforts to secure IoT ecosystems. The proposed strategies are designed to minimize the likelihood of cyberattacks while also offering scalable solutions that can be implemented across different sectors where IoT is prevalent. Addressing IoT security is of paramount importance in the fight against cybercrime. As the world becomes more interconnected, the consequences of cyberattacks targeting IoT systems are increasingly severe. In industries such as healthcare, energy, and transportation, the failure of IoT security can have life-threatening consequences, disrupt essential services, and cause significant financial losses. Furthermore, the trust that consumers and businesses place in IoT technologies depends largely on the assurance that their systems are secure from intrusion and manipulation. If security concerns are not addressed adequately, the adoption of IoT may slow, hindering the many benefits it offers in terms of efficiency, innovation, and productivity.
This study contributes to the broader field of cybersecurity by providing practical solutions to real-world problems facing IoT security. It underscores the need for collaborative efforts between device manufacturers, software developers, and regulatory bodies to implement robust security standards. By focusing on vulnerability management and cybercrime prevention, this research aims to pave the way for safer IoT deployments, ensuring that the technological advancements enabled by IoT can continue to flourish without being undermined by the growing threat of cyberattacks.
1.1. Scope and Focus
The scope of this paper is to explore the intersection of Internet of Things (IoT) technology and cybercrime, delving into the risks and challenges posed by the widespread adoption of connected devices. Internet of Things (IoT) playing a significant role in modern society for smart homes and wearable technology to industrial automation and connected healthcare. The potential for cyber threats has grown exponentially.
2. Literature Review
The Internet of Things (IoT) has been at the forefront of technological advancements in recent years, reshaping industries and transforming how devices interact with one another. However, as IoT systems proliferate, security has become a critical concern. Various studies have addressed the challenges of securing IoT devices and networks, highlighting the multitude of vulnerabilities present within these systems and the increasing threat of cybercrime. The literature surrounding IoT security and vulnerabilities has grown substantially, with researchers and industry experts recognizing the need for enhanced protection as the attack surface continues to expand. Early studies on IoT security emphasized the lack of built-in security features in many devices. Research showed that most IoT devices are designed with a focus on functionality rather than security, which leaves them susceptible to a variety of attacks. For instance, NIST (National Institute of Standards and Technology) highlighted common vulnerabilities such as weak passwords, outdated firmware, and insecure communication protocols. Numerous incidents, such as the Mirai botnet attack, were examined in detail to demonstrate how attackers exploit these vulnerabilities. Mirai, which infected IoT devices to create a massive botnet, was used to launch a distributed denial-of-service (DDoS) attack, disrupting services on a global scale. The event underscored the need for robust security frameworks and standards in IoT ecosystems. Another aspect of IoT security that has been widely researched is the inherent challenge of maintaining secure communication between devices. Studies on wireless communication protocols, such as Zigbee, Bluetooth, and Wi-Fi, have pointed out their susceptibility to various attacks, including man-in-the-middle attacks, eavesdropping, and data manipulation. Researchers like Roman et al. (2018) have explored the implications of such vulnerabilities on both consumer IoT devices and critical infrastructure, stressing the urgent need for secure communication protocols that can protect data from unauthorized access.
2.1. Current Security Practices
Despite these growing concerns, several security solutions have been proposed and implemented over the years. Encryption is one of the most commonly recommended measures to secure IoT systems. AES (Advanced Encryption Standard) and RSA (Rivest–Shamir–Adleman) encryption techniques are frequently employed to protect data transmitted between IoT devices. Additionally, Transport Layer Security (TLS) protocols are widely used to establish secure communication channels, preventing unauthorized access to sensitive information. While these encryption standards are effective to a degree, their implementation is often inconsistent, particularly in low-power IoT devices where processing power and memory are limited. This limitation makes it difficult for such devices to adopt robust encryption without compromising performance.
Multi-factor authentication (MFA) has been another solution implemented to enhance IoT security. MFA requires users to provide two or more verification factors before accessing a system, thereby increasing the difficulty for attackers to gain unauthorized entry. However, while MFA provides an extra layer of security, it is not foolproof. Attackers have developed ways to bypass MFA, including through phishing attacks and session hijacking. Moreover, the user experience can be negatively impacted by the complexity of MFA, particularly in consumer IoT applications. AI-based intrusion detection systems (IDS) have been introduced in recent years as a more advanced approach to IoT security. These systems leverage machine learning algorithms to detect anomalous behavior in IoT networks, allowing for quicker identification of potential threats. AI-based systems have shown promising results in detecting zero-day vulnerabilities and mitigating attacks before they cause significant damage. Nevertheless, these systems still face challenges in terms of accuracy and scalability. High false-positive rates and the need for large datasets to train AI models remain obstacles that hinder the widespread adoption of AI-based security solutions.
Blockchain technology has also been explored as a means of securing IoT systems. By decentralizing data storage and establishing trustless environments, Blockchain can theoretically enhance the integrity and security of IoT data exchanges. Blockchain-based authentication mechanisms and smart contracts have been proposed as ways to secure IoT devices against tampering and unauthorized access. However, the application of Blockchain to IoT is still in its nascent stages, with scalability and energy consumption being major concerns. The processing power required to manage Blockchain operations is often too high for many IoT devices, and the speed at which Blockchain networks process transactions is currently insufficient for the real-time needs of IoT systems.
2.2. Research Gap
While the current security practices mentioned above represent significant advancements in IoT security, they are not without limitations. Many existing solutions, such as encryption and MFA, are not scalable across all types of IoT devices, particularly in resource-constrained environments where processing power, storage, and battery life are limited. Furthermore, while AI-based and Blockchain security solutions hold promise, they are still in the experimental stages and face challenges regarding implementation on a large scale. One of the key research gaps identified in the literature is the lack of a comprehensive framework that integrates these emerging technologies in a way that balances security and efficiency. Existing solutions tend to focus on isolated aspects of IoT security, such as encryption or intrusion detection, without addressing the holistic nature of IoT networks, which require layered defenses that can adapt to different environments and threat levels. Moreover, the literature often overlooks the role of user behavior in securing IoT systems. Much vulnerability arises not from technical shortcomings but from misconfigurations and human error. There is a need for further research into user education, best practices for securing IoT devices, and how human factors can be better incorporated into security management.
This paper seeks to address these gaps by proposing an integrated approach that combines traditional security measures with cutting-edge technologies like AI and Blockchain, while also taking into account the limitations of IoT devices and the critical role of user behavior in maintaining security. The goal is to create a more robust, scalable, and user-friendly security framework that can effectively mitigate the growing cybercrime threats in IoT systems.
3. Methodology
3.1. Research Design
This research follows a computational and theoretical approach aimed at enhancing IoT systems through effective management of security vulnerabilities. The theoretical part involves exploring existing cybercrime prevention models and frameworks, focusing on how they apply to IoT systems. The computational component develops simulation models and vulnerability assessment tools that evaluate the effectiveness of security strategies in real-world IoT environments.
3.2. Data Collection
The data collection process involves a multi-faceted approach to ensure a comprehensive understanding of IoT security vulnerabilities:
- -
Case Studies on IoT Security Breaches: A thorough review of documented IoT security incidents from industry reports and cybersecurity databases (such as the National Vulnerability Database and OWASP). These case studies help identify the common types of vulnerabilities exploited in cybercrimes.
- -
IoT Security Vulnerability Databases: Publicly available vulnerability datasets, like CVE (Common Vulnerabilities and Exposures), are analyzed to determine prevalent weaknesses in IoT devices.
- -
Surveys and Interviews: Conduct surveys or structured interviews with IoT system administrators, developers, and cybersecurity professionals to gather insights on the challenges they face in identifying and managing vulnerabilities.
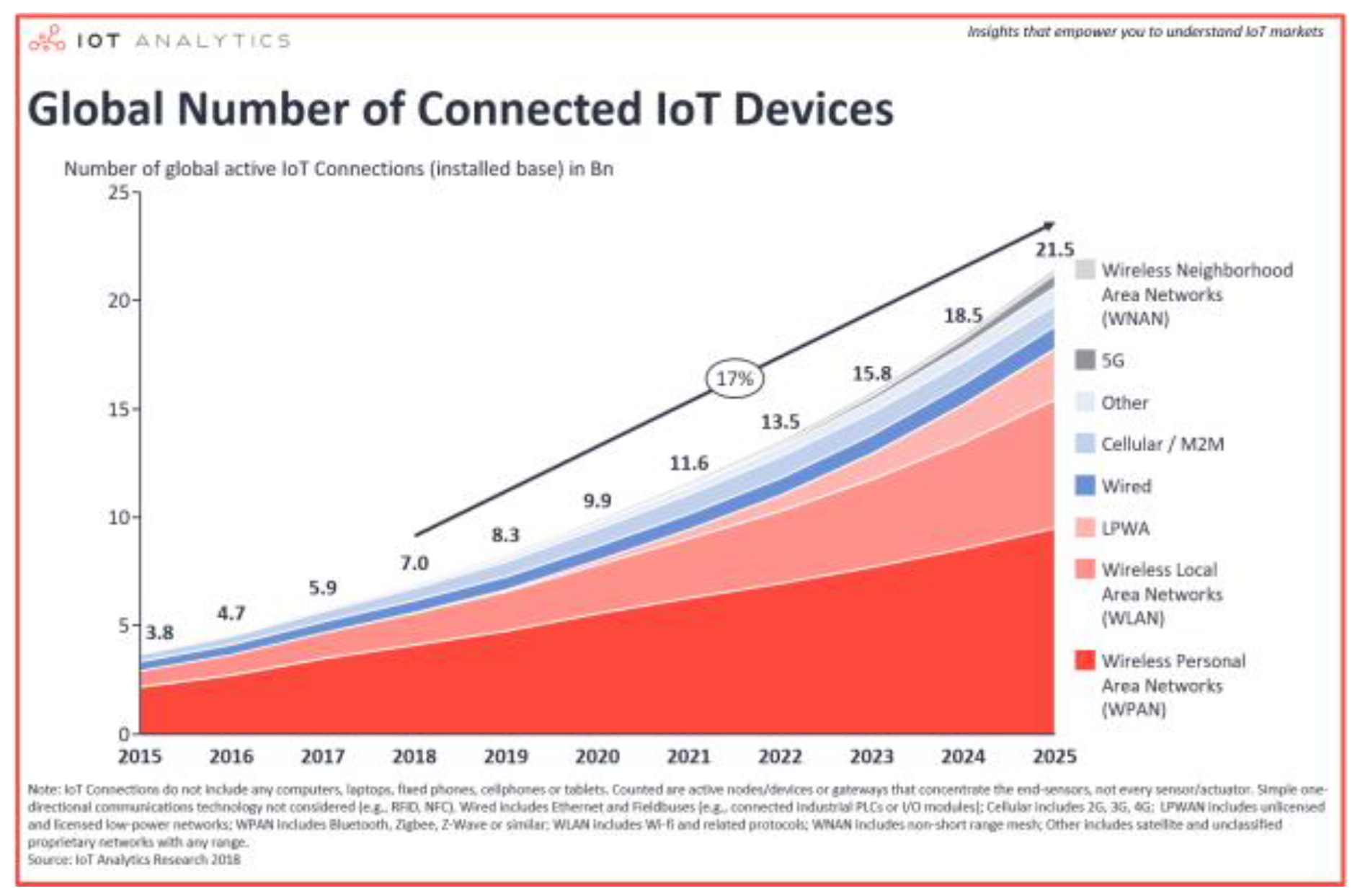
Figure 1.
Number of IoT devices worldwide 2015-2025.
Figure 1.
Number of IoT devices worldwide 2015-2025.
3.3. Analysis Framework
The analysis is carried out using both qualitative and quantitative methods to evaluate IoT security vulnerabilities and assess the effectiveness of preventive strategies:
3.3.1. Qualitative Analysis:
Thematic Analysis of case studies and interview data to understand the underlying factors contributing to IoT vulnerabilities and the gaps in current security practices.
Content Analysis of reports and literature to identify existing preventive strategies and their effectiveness.
3.3.2. Quantitative Analysis:
Statistical Analysis of vulnerability databases (e.g., NVD, CVE) to quantify the most common vulnerabilities, the frequency of exploitation, and the sectors most affected.
Correlation Analysis to assess the relationship between different IoT device characteristics (e.g., device type, complexity, network size) and vulnerability rates.
3.3.3. Simulation Models:
Attack Simulation Models to replicate potential cyberattacks on IoT systems, measuring the impact of different vulnerability types. These simulations help assess the robustness of various security measures and suggest improvements.
Risk Assessment Models to calculate the risk associated with each vulnerability and prioritize mitigation strategies accordingly.
3.3.4. Comparative Analysis:
Comparison of cybercrime prevention strategies against identified vulnerabilities to evaluate their effectiveness.
Benchmarking against industry best practices and standards to assess whether they adequately address the vulnerabilities found.
4. Functionality and Components of Internet of Things
The basic functionality of IoT involves collecting data from physical devices, transmitting it for processing, and using it to enable automation, monitoring, and data-driven insights. The core components of IoT include devices and sensors, connectivity, data processing and analytics, user interfaces, and security and privacy measures. Together, these components create a robust IoT ecosystem that can be applied to a wide range of use cases across industries and everyday life.
4.1. Basic Functionality
At its core, IoT involves collecting data from physical devices, transmitting that data for processing, and then using the processed information to make informed decisions, automate tasks, or generate insights. This cycle of data collection, transmission, processing, and response is the foundation of IoT’s functionality.
4.2. Components of IoT
The IoT ecosystem comprises several key components that work together to enable this functionality:
4.2.1. Devices and Sensors
Devices: These are the “things” in IoT—physical objects embedded with technology that allows them to collect, process, and exchange data. Examples include smart thermostats, wearable fitness trackers, industrial machinery, and vehicles.
Sensors: Sensors are used to measure various physical parameters like temperature, humidity, light, motion, pressure, and more. They generate data that can be processed and acted upon.
4.2.2. Connectivity
Communication Protocols: IoT devices connect to the internet or other networks using a variety of communication protocols, such as Wi-Fi, Bluetooth, Zigbee, Z-Wave, LoRa, and cellular networks (e.g., 4G/5G). These protocols define how devices transmit and receive data.
Gateways and Hubs: In some IoT systems, devices connect to a central gateway or hub, which acts as an intermediary for data communication. Gateways can also perform edge processing, reducing the load on central servers.
4.2.3. User Interfaces and Applications
User Interfaces: These are the interfaces through which users interact with IoT systems. They can be mobile apps, web dashboards, or other software tools that provide users with data insights, control options, and alerts.
Applications: IoT applications are designed to meet specific use cases, such as home automation, industrial monitoring, or healthcare tracking. They allow users to leverage the data collected by IoT devices to achieve specific outcomes.
4.2.4. Security and Privacy
Security Measures: IoT systems must incorporate security measures to protect against unauthorized access, data breaches, and other threats. This can include encryption, secure authentication, firewalls, and regular software updates.
Privacy Controls: Given the sensitive nature of some IoT data, privacy controls are critical. This involves ensuring that user data is handled securely and that users have control over their data and consent mechanisms.
5. Rise of Iot Cybercrime
The rise of the Internet of Things (IoT) has led to a new set of cybersecurity challenges, as the increased connectivity and complexity of IoT devices create unique vulnerabilities. Cybercriminals are taking advantage of these vulnerabilities, leading to a surge in IoT-related cybercrime. Here are some key factors contributing to the rise of IoT cybercrime:
5.1. Exploitable Vulnerabilities
Weak Security Practices: Many IoT devices are designed with convenience and cost in mind, often at the expense of security. Default passwords, lack of encryption, and unpatched vulnerabilities are common, making them easy targets for hackers.
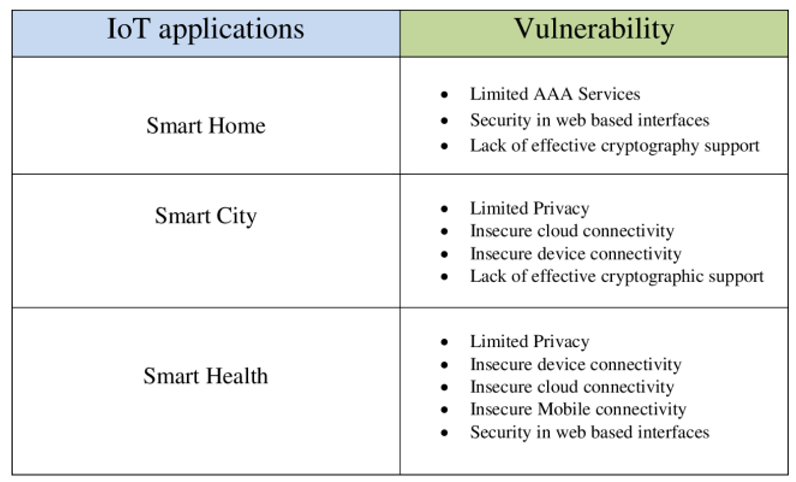
Figure 3.
IoT applications and associated vulnerabilities.
Figure 3.
IoT applications and associated vulnerabilities.
5.2. Botnets and DDoS Attacks
Botnet Formation: Compromised IoT devices can be harnessed to form botnets—networks of devices controlled by cybercriminals. These botnets can be used for malicious purposes, such as launching Distributed Denial of Service (DDoS) attacks to overwhelm websites and networks.
High-Profile Attacks: The 2016 Mirai botnet attack, which used IoT devices to execute a massive DDoS attack on prominent websites, highlighted the potential for IoT-based cybercrime at scale.
5.3. Unauthorized Access and Data Theft
Data Breaches: IoT devices often collect sensitive information, from personal data to financial and health records. Unauthorized access to these devices can lead to data breaches, with attackers stealing valuable information.
Device Hijacking: Attackers can take control of IoT devices, potentially manipulating their functions. This poses serious risks in industrial settings, where device control is critical for safety and operations.
5.4. Privacy Risks
Surveillance and Data Collection: IoT devices are capable of extensive data collection, including location tracking, voice recordings, and video feeds. If compromised, these devices can be used for unauthorized surveillance or data theft.
Lack of User Awareness: Users often do not realize the extent of data collection by IoT devices, leading to privacy risks when devices are hacked or misused.
5.5. Ransomware and Extortion
Ransomware on IoT Devices: Cybercriminals are extending ransomware attacks to IoT devices. Infected devices can be rendered inoperable until a ransom is paid, disrupting business operations or personal lives.
Extortion and Blackmail: With access to sensitive data, attackers can extort individuals or businesses, threatening to release or misuse the data unless a ransom is paid.
6. Vulnerabilities in Iot Ecosystem
The Internet of Things (IoT) ecosystem, with its interconnected devices and systems, presents a wide range of vulnerabilities that can be exploited by attackers. These vulnerabilities can compromise security, privacy, and system integrity. The Internet of Things ecosystem is rife with vulnerabilities that make it an attractive target for cybercriminals. One significant issue is the inherent lack of robust security measures in many IoT devices.
Table 1.
IoT applications and associated vulnerabilities.
Table 1.
IoT applications and associated vulnerabilities.
Manufacturers often prioritize cost-efficiency and rapid market entry over comprehensive security protocols. This results in devices with weak encryption, inadequate authentication processes, and software that is rarely, if ever, updated. As a consequence, these devices can be easily compromised, providing entry points for cyberattacks. Another critical vulnerability is the heterogeneity of the IoT ecosystem. The wide array of devices, each with different operating systems, communication protocols, and security features, creates a fragmented landscape that is challenging to secure uniformly. This diversity makes it difficult to implement standardized security measures, leaving gaps that cybercriminals can exploit.
Interconnectivity, a defining feature of IoT, also exacerbates security risks. Devices often communicate with each other and with central hubs or cloud services, forming extensive networks. A breach in one device can thus propagate through the network, compromising other connected devices. This interconnectedness amplifies the impact of security vulnerabilities, as a single weak link can jeopardize the entire system. Additionally, IoT devices are frequently deployed in environments where traditional security controls are impractical. For instance, sensors in remote or hard-to-reach locations may not receive regular maintenance or updates, leaving them susceptible to long-term exploitation. Similarly, consumer IoT devices in homes often rely on default settings, which are rarely modified by users, further weakening security postures. The absence of stringent regulatory frameworks and industry standards for IoT security compounds these vulnerabilities. While efforts are underway to establish guidelines, the rapid pace of IoT development outstrips these regulatory measures. This regulatory lag leaves many devices operating without clear security benchmarks, increasing the risk of cybercrime. Lastly, the human factor cannot be overlooked. Users often lack awareness of the security risks associated with IoT devices, leading to poor security practices such as using weak passwords or neglecting firmware updates. This human element, combined with the technical vulnerabilities of IoT devices, creates a fertile ground for cybercriminal activities, highlighting the urgent need for enhanced security measures and user education within the IoT ecosystem.
7. Regulatory Framework and Policy Implications
The rapid growth of the Internet of Things (IoT) has created significant policy and regulatory implications for governments, industry stakeholders, and consumers. A robust regulatory framework is essential to address security, privacy, interoperability, and other risks associated with IoT. Establishing minimum security standards for IoT devices ensures that manufacturers incorporate fundamental security measures, such as strong authentication, encryption, and secure firmware updates. Regulatory bodies can create certification programs to ensure IoT devices meet security standards before entering the market. Laws such as the General Data Protection Regulation (GDPR) in the EU and the California Consumer Privacy Act (CCPA) in the US set rules for data collection, processing, and user consent. Similar frameworks can be applied to IoT to ensure privacy protection. Regulations should require IoT manufacturers to obtain user consent before collecting data and to provide mechanisms for users to control their personal information. A regulatory framework should promote interoperability between IoT devices to ensure compatibility and security across platforms. This can help avoid fragmentation and reduce security risks.
Governments can work with industry groups to develop and adopt common standards for IoT devices, promoting a consistent approach to security and interoperability.
Regulations should define the liability of manufacturers for security breaches or privacy violations. This creates an incentive for companies to prioritize security in their product design and operations. Establishing mechanisms for monitoring compliance with IoT regulations ensures that manufacturers and service providers adhere to established rules.
8. Discussion
The findings of this study underscore the pressing need to enhance security practices within IoT systems. The research confirms that IoT devices are increasingly vulnerable to cyberattacks due to their interconnected nature and the prevalence of weak security configurations. This has made IoT an attractive target for cybercriminals, especially in sectors such as healthcare and industrial IoT, where sensitive data and critical infrastructures are at risk. The significance of these findings lies in their contribution to developing a comprehensive security framework that addresses both common and advanced vulnerabilities in IoT networks. By identifying key security weaknesses — such as inadequate encryption, weak authentication methods, and the lack of proper firmware updates — the study provides valuable insights into how these gaps can be exploited by attackers. The proposed solutions, including AI-based intrusion detection, Blockchain technology for decentralized security, and risk management frameworks, offer a multifaceted approach to securing IoT environments. These innovations contribute to IoT security management by addressing the need for scalable, efficient, and adaptable solutions that can be implemented across various industries.
The integration of AI for real-time threat detection adds value by providing a dynamic defense mechanism, capable of identifying new vulnerabilities and potential attacks as they emerge. Likewise, Block chain’s decentralized nature enhances the security of authentication processes, reducing the risk of data tampering and unauthorized access. These technologies, when combined, represent a significant step forward in mitigating cybercrime risks, making IoT systems more resilient to evolving threats.
8.1. Challenges and Limitations
Despite the promising results, this study faced several challenges. One of the primary challenges was the heterogeneity of IoT devices. IoT systems vary widely in terms of device capabilities, communication protocols, and operating environments. This diversity makes it difficult to develop a one-size-fits-all security solution. Low-powered IoT devices, for example, often lack the processing capacity to run sophisticated security protocols, which limits the applicability of certain solutions like AI-based intrusion detection and Blockchain technology. Addressing this limitation requires tailoring security approaches to the specific needs and constraints of different IoT devices, which adds complexity to the implementation process. Another limitation of the proposed approach is the high computational cost associated with Blockchain and AI technologies. While Blockchain offers strong security features, it is often resource-intensive, and IoT systems with limited power and memory might struggle to support Blockchain-based solutions. Similarly, AI-based security solutions require substantial amounts of data and processing power to function effectively. These constraints may prevent some IoT systems from fully adopting the proposed measures, especially in resource-constrained environments. Additionally, the rapid evolution of cybercrime poses a continual challenge. Cybercriminals are developing new techniques to exploit emerging vulnerabilities in IoT systems, making it difficult for security solutions to remain effective over time. This highlights the importance of regularly updating and adapting security measures to address newly identified threats.
8.2. Future Directions
The results of this study open several avenues for future research in IoT security and cybercrime prevention. One potential direction is the development of lightweight security protocols specifically designed for resource-constrained IoT devices. Future research could focus on creating more efficient encryption methods, Blockchain architectures, or AI algorithms that consume less power and memory, making them suitable for a wider range of IoT devices. Another promising area for future research is the integration of edge computing with IoT security. By processing data closer to the devices rather than in centralized servers, edge computing can reduce latency and improve the efficiency of security measures. Research could explore how edge computing can be combined with AI and Blockchain to create a distributed security architecture that enhances real-time threat detection and response capabilities.
Furthermore, user behavior and its impact on IoT security warrant further investigation. Many IoT vulnerabilities arise from human error, such as misconfiguring devices or neglecting to apply security updates. Future research could explore how to design user-friendly interfaces and education tools that encourage users to follow best practices for securing IoT systems.
Lastly, regulatory frameworks and policies are essential for ensuring that IoT manufacturers prioritize security in device design. There is a need for further research into how governments and industry bodies can collaborate to establish and enforce global security standards for IoT devices. These standards could ensure that manufacturers implement baseline security measures, such as encryption and regular firmware updates, before devices are released to the market. while this study has made important contributions to IoT security management, ongoing research is necessary to address its limitations and adapt to the evolving cybercrime landscape. Future advancements in lightweight security technologies, edge computing, user education, and regulatory frameworks will be critical to creating safer IoT ecosystems and preventing cybercrime.
9. Conclusions
This paper has explored the critical security vulnerabilities present in Internet of Things (IoT) systems and their exploitation by cybercriminals, which poses significant risks across multiple industries. Through a detailed analysis of common IoT vulnerabilities and existing security practices, the research highlights the inadequacies of current approaches, particularly in environments with resource-constrained devices. The study emphasizes that while solutions such as encryption, multi-factor authentication, and AI-based intrusion detection systems show promise, they fall short when implemented in isolation and lack scalability across diverse IoT ecosystems. The main findings demonstrate that industrial IoT and healthcare systems, in particular, face heightened vulnerability due to their widespread adoption and the sensitivity of the data they handle. Cybercriminals exploit these weaknesses, targeting IoT networks to launch attacks such as data breaches, ransomware, and distributed denial-of-service (DDoS) attacks, leading to severe economic and operational disruptions. The proposed solutions in this paper — including the integration of AI-based security measures, Blockchain for decentralized authentication, and a comprehensive risk management framework — offer a more robust and scalable approach to mitigating these risks. In the broader field of computer science, this research contributes to the growing body of work on cybersecurity by demonstrating the need for a multi-layered approach to IoT security. The study also underscores the importance of collaboration between device manufacturers, software developers, and policymakers to create and enforce standardized security practices across the IoT landscape. Addressing IoT vulnerabilities is crucial for effective cybercrime prevention. As IoT systems continue to expand globally, the risks associated with insecure devices and networks will also grow, making it essential to develop more resilient, adaptive, and scalable security solutions. By identifying and managing IoT vulnerabilities, this research supports the creation of more secure IoT environments, ensuring that the benefits of IoT innovation are not undermined by increasing cybercrime threats.
References
- Kagita, M.; Thilakarathne, N.N.; Gadekallu, T.R.; Maddikunta, P.K.; Singh, S. A Review on Cyber Crimes on the Internet of Things. arXiv 2020, arXiv:2009.05708.
- Shackelford, S.J. The Internet of Things: What Everyone Needs to Know®; Oxford University Press: 2020.
- Blythe, J.M.; Johnson, S.D. A systematic review of crime facilitated by the consumer Internet of Things. Security Journal 2021, 34, 97-125. [CrossRef]
- Beale, S.S.; Berris, P. Hacking the Internet of Things: Vulnerabilities, dangers, and legal responses. Duke L. & Tech. Rev. 2017, 16, 161.
- Márquez Díaz, J.E. Cybersecurity and Internet of Things. Outlook for this decade. Computación y Sistemas 2022, 26(3), 1201-1214. [CrossRef]
- Montasari, R.; Carroll, F.; Mitchell, I.; Hara, S.; Bolton-King, R. (Eds.) Privacy, security and forensics in the internet of things (IoT). Springer: 2022. [CrossRef]
- Banafa, A. (2018). Secure and Smart Internet of Things (IoT). River Publishers.
- Kagita, M.K.; Thilakarathne, N.; Gadekallu, T.R.; Maddikunta PK, R.; Singh, S. (2022). A review on cyber crimes on the internet of things. Deep Learning for Security and Privacy Preservation in IoT, 83-98. [CrossRef]
- Blythe, J.M.; Johnson, S.D. A systematic review of crime facilitated by the consumer Internet of Things. Security Journal 2021, 34, 97-125. [CrossRef]
- Hilt, S.; Kropotov, V.; Mercês, F.; Rosario, M.; Sancho, D. (2019). The internet of things in the cybercrime underground. Trend Micro Research.
- Almansoori, A.; Ncube, C.; Salloum, S.A. (2021, May). Internet of Things impact on the future of cyber crime in 2050. In The International Conference on Artificial Intelligence and Computer Vision (pp. 643-655). Cham: Springer International Publishing. [CrossRef]
- Hemdan EE, D.; Manjaiah, D.H. (2018). Cybercrimes investigation and intrusion detection in internet of things based on data science methods. Cognitive Computing for Big Data Systems Over IoT: Frameworks, Tools and Applications, 39-62. [CrossRef]
- Alexandrou, A. (2021). Cybercrime and information technology: The computer network infrastructure and computer security, cybersecurity laws, Internet of Things (IoT), and mobile devices. CRC Press.
- Balasaraswathi, M.; Sivasankaran, V.; Akshaya, N.; Baskar, R.; Suganya, E. (2020). Internet of things (Iot) based bio-inspired artificial intelligent technique to combat cybercrimes: a review. Internet of Things in Smart Technologies for Sustainable Urban Development, 141-155. [CrossRef]
- Hilt, S.; Kropotov, V.; Mercês, F.; Rosario, M.; Sancho, D. (2019). The internet of things in the cybercrime underground. Trend Micro Research.
- Kagita, M.K.; Thilakarathne, N.; Gadekallu, T.R.; Maddikunta PK, R.; Singh, S. (2022). A review on cyber crimes on the internet of things. Deep Learning for Security and Privacy Preservation in IoT, 83-98.
- Atlam, H.F.; Alenezi, A.; Alassafi, M.O.; Alshdadi, A.A.; Wills, G.B. (2020). Security, cybercrime and digital forensics for IoT. Principles of internet of things (IoT) ecosystem: Insight paradigm, 551-577. [CrossRef]
- Alex, S.A.; Briyolan, B.G.; Vanadhi, K.R.; Jerlin, J.R.; Mault, S.K. (2023). Smart bin: an IoT-based bin for garbage monitoring. International Conference on Computer Vision and Internet of Things 2023 (ICCVIoT’23). [CrossRef]
- Kanumuri, C.; Torthi, R.; Varma, G.H.; Dilip, M.A.; Maganti, P. (2023). IoT-based user interface in predicting human maladies: a machine learning paradigm. International Conference on Computer Vision and Internet of Things 2023 (ICCVIoT’23). [CrossRef]
- Silva, V.; Akkar, S.; Baker, J.; Bazzurro, P.; Castro, J.M.; Crowley, H., ... & Vamvatsikos, D. (2019). Current Challenges and Future Trends in Analytical Fragility and Vulnerability Modeling. Earthquake Spectra. [CrossRef]
- Vats, A. (2024). Chinese and Russian Cybercrime in Global Racial Orders of Intellectual Property. In Feminist Cyberlaw. [CrossRef]
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).